Information Security Report: Risk-Based Security Evaluation Analysis
VerifiedAdded on 2022/12/26
|13
|3764
|50
Report
AI Summary
This report provides a comprehensive analysis of information security threats, focusing on a personal incident involving the loss of a smartphone, laptop, and wallet. It delves into the potential security breaches, including identity theft and data tampering, and explores the vulnerabilities associated with digital identity cards and mobile devices. The report examines the risks associated with stolen credit card details, compromised personal information, and the potential for misuse of organizational data. It assesses risk probability and impact, and discusses tests for performing security measures, policy, training, and technology. Furthermore, it emphasizes the importance of data security requirements and the implementation of controls to mitigate potential threats, offering insights into creating a robust information security management system (ISMS).

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY 1
Introduction:
Associations of numerous kinds and sizes (counting open and private division,
business and non-benefit) gather, procedure, transmit and store data in numerous structures
including the electronic, physical as well as verbal (for example discussions and
introductions). The estimation of data goes past the composed numbers, words, and pictures:
learning, ideas, thoughts as well as brands are instances of immaterial types of data. In an
world that is interconnected, data and related procedures, frameworks, systems and faculty
engaged with their task, taking care of and assurance are resources that, as other significant
business resources, are important to an association's matter of fact and thus merit or require
insurance against different perils (Baggett and Simpkins, 2018). Resources are liable to both
intentional and incidental dangers while the procedures, frameworks, systems and individuals
that are related, are having innate vulnerabilities. The changes related to the business
procedures and frameworks or other outer changes, (for example, new laws or guidelines)
may make new data security dangers. Along these lines, given the huge number of manners
by which dangers could exploit vulnerabilities to hurt the association, data security dangers
are constantly present. Compelling data security diminishes these dangers by ensuring the
association against dangers and vulnerabilities, and after that lessens effects to its advantages.
The Data security is accomplished via actualizing an arrangement of controls, including
forms, strategies, methods, hierarchical structures as well as programming and capacities that
are equipment. These controls should be actualized, checked, built up, surveyed and
improved, where vital, for guarantee that the security as well as the goals of the business of
the association have been met (Yaokumah and Dawson, 2019). An ISMS, for example, that
predefined in ISO/IEC 27001 takes an all-encompassing, facilitated perspective on the
association's data security chances so as to execute a complete suite of data security controls
under the structure that is general of a rational administration framework. Numerous data
Introduction:
Associations of numerous kinds and sizes (counting open and private division,
business and non-benefit) gather, procedure, transmit and store data in numerous structures
including the electronic, physical as well as verbal (for example discussions and
introductions). The estimation of data goes past the composed numbers, words, and pictures:
learning, ideas, thoughts as well as brands are instances of immaterial types of data. In an
world that is interconnected, data and related procedures, frameworks, systems and faculty
engaged with their task, taking care of and assurance are resources that, as other significant
business resources, are important to an association's matter of fact and thus merit or require
insurance against different perils (Baggett and Simpkins, 2018). Resources are liable to both
intentional and incidental dangers while the procedures, frameworks, systems and individuals
that are related, are having innate vulnerabilities. The changes related to the business
procedures and frameworks or other outer changes, (for example, new laws or guidelines)
may make new data security dangers. Along these lines, given the huge number of manners
by which dangers could exploit vulnerabilities to hurt the association, data security dangers
are constantly present. Compelling data security diminishes these dangers by ensuring the
association against dangers and vulnerabilities, and after that lessens effects to its advantages.
The Data security is accomplished via actualizing an arrangement of controls, including
forms, strategies, methods, hierarchical structures as well as programming and capacities that
are equipment. These controls should be actualized, checked, built up, surveyed and
improved, where vital, for guarantee that the security as well as the goals of the business of
the association have been met (Yaokumah and Dawson, 2019). An ISMS, for example, that
predefined in ISO/IEC 27001 takes an all-encompassing, facilitated perspective on the
association's data security chances so as to execute a complete suite of data security controls
under the structure that is general of a rational administration framework. Numerous data

2INFORMATION SECURITY
frameworks have not been intended to be secure in the feeling of ISO/IEC 27001 and this
standard. The security that can be accomplished through specialized methods is constrained
and ought to be bolstered by fitting administration and techniques. Distinguishing which
controls ought to be set up requires cautious arranging and tender loving care (Cunningham
and Ainsworth, 2018). An effective ISM requires support by all workers in the association. It
can likewise require interest from investors, providers or other outer gatherings. Master
guidance from outer gatherings can likewise be required.
Review:
When one loses mobile phone, laptop and wallet, the person faces severe security
threats. The incident where I lost my belonging that is my smart phone, laptop and wallet, the
situation created major security threats for me. I lost my belongings while I travelling to the
countryside and I cannot possibly have any idea who stole my belonging. My wallet had my
two credit cards from two different banks, identity proof, cash and company security card. I
kept my mobile phone and wallet in my laptop bag. My laptop bag was stolen, and with it
went away my smart phone and wallet. Later on returning home from my travel, I received a
call from my bank to let me know that the bank has noticed suspicious activities against my
accounts. Both the accounts showed suspicious activity and there has been further developing
activity in those accounts. My credit card rating has significantly dropped to credit warning
as the bank informed me that several personal loan application have been filed by my name. I
realized my identity was stolen as my digital identity card was there in the wallet. Another
objective that can be understood from the whole incident is that, the people who stole my
belongings are technically competent and have garnered all my sensitive information from
the same.
frameworks have not been intended to be secure in the feeling of ISO/IEC 27001 and this
standard. The security that can be accomplished through specialized methods is constrained
and ought to be bolstered by fitting administration and techniques. Distinguishing which
controls ought to be set up requires cautious arranging and tender loving care (Cunningham
and Ainsworth, 2018). An effective ISM requires support by all workers in the association. It
can likewise require interest from investors, providers or other outer gatherings. Master
guidance from outer gatherings can likewise be required.
Review:
When one loses mobile phone, laptop and wallet, the person faces severe security
threats. The incident where I lost my belonging that is my smart phone, laptop and wallet, the
situation created major security threats for me. I lost my belongings while I travelling to the
countryside and I cannot possibly have any idea who stole my belonging. My wallet had my
two credit cards from two different banks, identity proof, cash and company security card. I
kept my mobile phone and wallet in my laptop bag. My laptop bag was stolen, and with it
went away my smart phone and wallet. Later on returning home from my travel, I received a
call from my bank to let me know that the bank has noticed suspicious activities against my
accounts. Both the accounts showed suspicious activity and there has been further developing
activity in those accounts. My credit card rating has significantly dropped to credit warning
as the bank informed me that several personal loan application have been filed by my name. I
realized my identity was stolen as my digital identity card was there in the wallet. Another
objective that can be understood from the whole incident is that, the people who stole my
belongings are technically competent and have garnered all my sensitive information from
the same.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
The perpetrator has used the digital identity card to foster and pull out every minute
personal detail. Details include, bank detail, biometric (DNA fingerprints), serial numbers,
linked accounts, work history, savings, loans taken, places travelled, mobile details. Digital
identity security breach forms two kinds of threats, identity theft and identity tampering
(Grassi, Garcia and Fenton 2017). The perpetrators use the identity that is digital of other
identity for impersonating him or her. This kind of threat is called phishing. Phishing is
malicious attempt to acquire information by masquerading as a trustworthy entity. It can be
said that the perpetrators were phishing on the details to use it injudiciously. The digital
identity card has all the information regarding an individual, from the nation security number
to their bank details. Getting hand on the digital identity card, the attackers easily drew out all
the information from the card. This could be understood as they used the information to file
personal loan applications from the bank. Without the personal details and bank details, the
attackers could have not filed for loans. The attackers can easily use the detail they harvested
from the digital identity card to get cash transferred from one account to the other (Grassi
2017). The attackers have all the details and resources to get easily by pass the authentication
stage. The authentication consists into the verification progress of the digitally converted
identity of the entity. Four of the classes of authentication are defined usually: what is known
by the entity, what she or he is what he or she possesses and what she or he does (McCormac
2018). For the authenticatication of the the entity for presenting a digital identity, one of the
subset of the claims composing the digital identity have to be belong to one or more of those
classes. The next activity recognized is tempering of identity. The bank noticed suspicious
activity as they found data was being modified in the accounts. The next probable threat
could be that the money and assets will be transferred to another account by all means.
Losing of the digital identity and data posses significant threats.
The perpetrator has used the digital identity card to foster and pull out every minute
personal detail. Details include, bank detail, biometric (DNA fingerprints), serial numbers,
linked accounts, work history, savings, loans taken, places travelled, mobile details. Digital
identity security breach forms two kinds of threats, identity theft and identity tampering
(Grassi, Garcia and Fenton 2017). The perpetrators use the identity that is digital of other
identity for impersonating him or her. This kind of threat is called phishing. Phishing is
malicious attempt to acquire information by masquerading as a trustworthy entity. It can be
said that the perpetrators were phishing on the details to use it injudiciously. The digital
identity card has all the information regarding an individual, from the nation security number
to their bank details. Getting hand on the digital identity card, the attackers easily drew out all
the information from the card. This could be understood as they used the information to file
personal loan applications from the bank. Without the personal details and bank details, the
attackers could have not filed for loans. The attackers can easily use the detail they harvested
from the digital identity card to get cash transferred from one account to the other (Grassi
2017). The attackers have all the details and resources to get easily by pass the authentication
stage. The authentication consists into the verification progress of the digitally converted
identity of the entity. Four of the classes of authentication are defined usually: what is known
by the entity, what she or he is what he or she possesses and what she or he does (McCormac
2018). For the authenticatication of the the entity for presenting a digital identity, one of the
subset of the claims composing the digital identity have to be belong to one or more of those
classes. The next activity recognized is tempering of identity. The bank noticed suspicious
activity as they found data was being modified in the accounts. The next probable threat
could be that the money and assets will be transferred to another account by all means.
Losing of the digital identity and data posses significant threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
The loosing of the mobile phone added extra threats to the situation as a whole. The
mobile contained all the relevant information about work and other significant details. The
mobile had numerous personal pictures and details which created severe threat. Credit card
details are saved on the mobile phone. Both the card number and their pins are saved for easy
transaction at the time of online purchase. The card details are saved at almost all purchasing
sites on the phone. The attackers can easily use the information to gain access to the cards
and make purchases (Khalilzadeh, Ozturk and Bilgihan 2017). Having the mobile, as they are
competent technicians, they have easily breached the security wall of the phone to gain
access. Once the security wall is access and removed, the phone is vulnerable to the attackers
(Oliveira 2016). Any bank transaction can be easily made as now they can easily get the OTP
(one time password) to make any kind of purchase or transfers (Wang, Hahn and Sutrave
2016). Other personal details on the phone can be used unethically to advantage of the
perpetrators. The mobile can be used to extract information from other devices, as when the
path of the attack will be mapped, the investigators will not have much proof to blame the
attackers. The Bluetooth and .Wi-Fi function of the mobile phone can be used to discover
other devices nearby and impose attack on the devices to draw information from them. After
the work is, done data can be easily erased from the device and damaged.
The laptop, which was also stolen, can create potential security threats. The device
can be used to gather more information and used them against the owner. Additional threats
can like infecting other devices with malware, viruses from a distant (He, Chan and Guizani
2015). The laptop contained important and confidential organizational data, if misused will
prove to be a major threat for the organization. The attackers can use the information to
surreptitiously infect the organization’s network and harvest additional sensitive data from
the company server which can be used to create potential damage of the company’s asset
(Roman Lopez and Mambo 2018). The laptop contains client details and business data. These
The loosing of the mobile phone added extra threats to the situation as a whole. The
mobile contained all the relevant information about work and other significant details. The
mobile had numerous personal pictures and details which created severe threat. Credit card
details are saved on the mobile phone. Both the card number and their pins are saved for easy
transaction at the time of online purchase. The card details are saved at almost all purchasing
sites on the phone. The attackers can easily use the information to gain access to the cards
and make purchases (Khalilzadeh, Ozturk and Bilgihan 2017). Having the mobile, as they are
competent technicians, they have easily breached the security wall of the phone to gain
access. Once the security wall is access and removed, the phone is vulnerable to the attackers
(Oliveira 2016). Any bank transaction can be easily made as now they can easily get the OTP
(one time password) to make any kind of purchase or transfers (Wang, Hahn and Sutrave
2016). Other personal details on the phone can be used unethically to advantage of the
perpetrators. The mobile can be used to extract information from other devices, as when the
path of the attack will be mapped, the investigators will not have much proof to blame the
attackers. The Bluetooth and .Wi-Fi function of the mobile phone can be used to discover
other devices nearby and impose attack on the devices to draw information from them. After
the work is, done data can be easily erased from the device and damaged.
The laptop, which was also stolen, can create potential security threats. The device
can be used to gather more information and used them against the owner. Additional threats
can like infecting other devices with malware, viruses from a distant (He, Chan and Guizani
2015). The laptop contained important and confidential organizational data, if misused will
prove to be a major threat for the organization. The attackers can use the information to
surreptitiously infect the organization’s network and harvest additional sensitive data from
the company server which can be used to create potential damage of the company’s asset
(Roman Lopez and Mambo 2018). The laptop contains client details and business data. These
5INFORMATION SECURITY
data can be used to cause risks for the clients and hamper their assets as well. The laptop can
be used to download malicious software and attack other devices nearby. There runs potential
risks of the perpetrators using the laptop to attack other organizations as the time stamp and
network map will provide information about the owner of the laptop. The laptop contains
additional information and bank statements if used can posses’ serious threats. The
information can be used to access related bank accounts as the laptop contains bank statement
of the organization. Handling of these assets is important to stop further creation of threats.
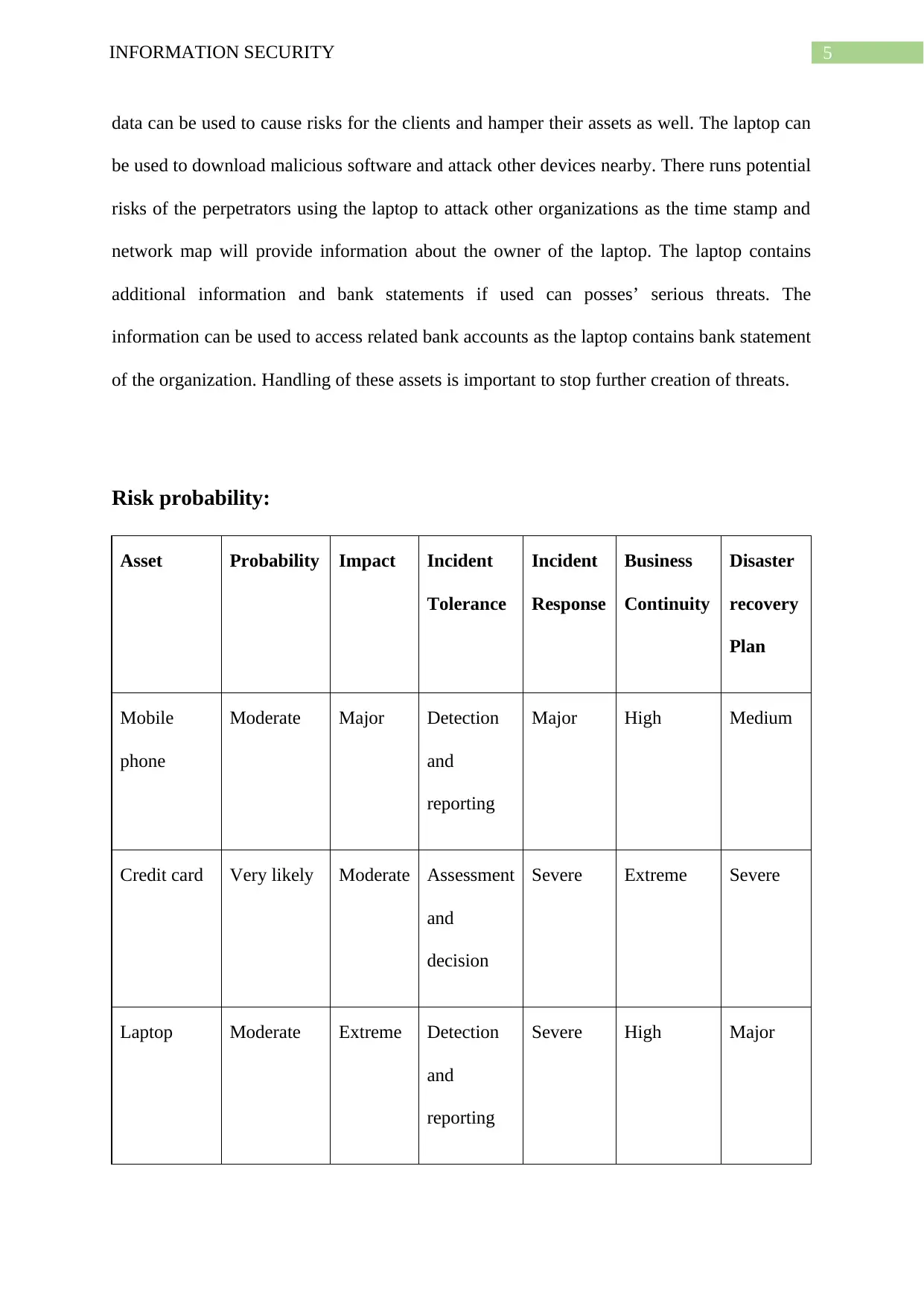
Risk probability:
Asset Probability Impact Incident
Tolerance
Incident
Response
Business
Continuity
Disaster
recovery
Plan
Mobile
phone
Moderate Major Detection
and
reporting
Major High Medium
Credit card Very likely Moderate Assessment
and
decision
Severe Extreme Severe
Laptop Moderate Extreme Detection
and
reporting
Severe High Major
data can be used to cause risks for the clients and hamper their assets as well. The laptop can
be used to download malicious software and attack other devices nearby. There runs potential
risks of the perpetrators using the laptop to attack other organizations as the time stamp and
network map will provide information about the owner of the laptop. The laptop contains
additional information and bank statements if used can posses’ serious threats. The
information can be used to access related bank accounts as the laptop contains bank statement
of the organization. Handling of these assets is important to stop further creation of threats.
Risk probability:
Asset Probability Impact Incident
Tolerance
Incident
Response
Business
Continuity
Disaster
recovery
Plan
Mobile
phone
Moderate Major Detection
and
reporting
Major High Medium
Credit card Very likely Moderate Assessment
and
decision
Severe Extreme Severe
Laptop Moderate Extreme Detection
and
reporting
Severe High Major
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
Tests for performing:
Against infection programming, firewalls, representative preparing, and plain
presence of mind can go far to ensure the user’s client database and to shield shoppers from
misfortune and wholesale fraud. Nevertheless, on the off chance that the user leave the
entryway open, enabling by and by recognizable data to be stolen or modified, the user have
not carried out the user’s responsibility as a protection and security officer (Forbes, 2018).
What's more, the user have traded off the trust between the user and the user’s client. Lose
that trust, and purchasers will deny the user the data the user have to fabricate a decent
showcasing relationship. There could be lawful implications also.
Security is a substantial duty, yet it is not advanced science. There are steps the user can go
out on a limb of information misfortune. Reacting to a suggestion to take action from the
Federal Trade Commission for all significant exchange relationship to address the security of
information, the Data and Marketing Association endorsed security rules for its individuals.
All individuals must pursue four explicit moral rules to keep data about purchasers secure.
The DMA urges the user to pursue this agenda (Jasińska and Kaczmarski, 2018). While these
agendas are not comprehensive for the user’s specific circumstance, they are valuable
advisers for help the user make the best decision for shoppers and the user’s organization.
FTC Mascot Dewie the Turtle is the wellbeing and security image for purchasers.
Security:
Stage 1. Have a Policy for security.
Stage 2. Supervise and Train for Security.
Stage 3. Utilize Available Technology for protecting Personal Data.
Tests for performing:
Against infection programming, firewalls, representative preparing, and plain
presence of mind can go far to ensure the user’s client database and to shield shoppers from
misfortune and wholesale fraud. Nevertheless, on the off chance that the user leave the
entryway open, enabling by and by recognizable data to be stolen or modified, the user have
not carried out the user’s responsibility as a protection and security officer (Forbes, 2018).
What's more, the user have traded off the trust between the user and the user’s client. Lose
that trust, and purchasers will deny the user the data the user have to fabricate a decent
showcasing relationship. There could be lawful implications also.
Security is a substantial duty, yet it is not advanced science. There are steps the user can go
out on a limb of information misfortune. Reacting to a suggestion to take action from the
Federal Trade Commission for all significant exchange relationship to address the security of
information, the Data and Marketing Association endorsed security rules for its individuals.
All individuals must pursue four explicit moral rules to keep data about purchasers secure.
The DMA urges the user to pursue this agenda (Jasińska and Kaczmarski, 2018). While these
agendas are not comprehensive for the user’s specific circumstance, they are valuable
advisers for help the user make the best decision for shoppers and the user’s organization.
FTC Mascot Dewie the Turtle is the wellbeing and security image for purchasers.
Security:
Stage 1. Have a Policy for security.
Stage 2. Supervise and Train for Security.
Stage 3. Utilize Available Technology for protecting Personal Data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
Stage 4. Illuminate Business Partners and Data Suppliers of their Responsibilities for Meeting
the user’s Security Specifications.
Data security requirement:
It is basic that an association recognizes its necessities of the security. There are 3
principle wellsprings of security necessities:
a) The evaluation of dangers to the company, by considering the association's general
business methodology and targets (Martínez et al., 2015). Through an appraisal that is
hazard, dangers to resources are recognized, powerlessness to and probability of event is also
assessed as well as potential effect is evaluated;
b) The legitimate, statutory, administrative and legally binding prerequisites that an
association, its exchanging accomplices, contractual workers and specialist organizations
need to fulfil, and their socio cultural condition
c) The arrangement of standards, destinations and business necessities for data dealing with,
handling, putting away, imparting and chronicling that an association has created to help its
tasks. Assets utilized in actualizing controls should be adjusted against the business hurt
prone to result from security issues without those controls (Von and Van, 2013). The
consequences of a hazard appraisal will help direct and decide the suitable administration
activity and needs for overseeing data security dangers and for actualizing controls chose to
ensure against these dangers.
Steps to secure:
1) Establish and uphold a demonstrated secret key procedure. Utilize genuinely
passwords that are complex also change those passwords within or before each 90
days. Don’t utilize straightforward passwords like "Password01" or "Admin1."
Stage 4. Illuminate Business Partners and Data Suppliers of their Responsibilities for Meeting
the user’s Security Specifications.
Data security requirement:
It is basic that an association recognizes its necessities of the security. There are 3
principle wellsprings of security necessities:
a) The evaluation of dangers to the company, by considering the association's general
business methodology and targets (Martínez et al., 2015). Through an appraisal that is
hazard, dangers to resources are recognized, powerlessness to and probability of event is also
assessed as well as potential effect is evaluated;
b) The legitimate, statutory, administrative and legally binding prerequisites that an
association, its exchanging accomplices, contractual workers and specialist organizations
need to fulfil, and their socio cultural condition
c) The arrangement of standards, destinations and business necessities for data dealing with,
handling, putting away, imparting and chronicling that an association has created to help its
tasks. Assets utilized in actualizing controls should be adjusted against the business hurt
prone to result from security issues without those controls (Von and Van, 2013). The
consequences of a hazard appraisal will help direct and decide the suitable administration
activity and needs for overseeing data security dangers and for actualizing controls chose to
ensure against these dangers.
Steps to secure:
1) Establish and uphold a demonstrated secret key procedure. Utilize genuinely
passwords that are complex also change those passwords within or before each 90
days. Don’t utilize straightforward passwords like "Password01" or "Admin1."

8INFORMATION SECURITY
Systems that are Microsoft based, Active Directory will enable the user to supersede
the suggested phrase conventions that are secret. (On the off chance that the user are
not required to change the user’s phrase that is secret each quarter, this component
will have been killed.)
2) Use a reinforcement plan that is safe. As of now It should be a key piece of the user’s
IT technique. Secure reinforcements help the user endure everything from incidental
record erasure to sea tempest demolition. Those equivalent reinforcements can
likewise enable the user to endure cyber blackmail (Rantos et al., 2018). On the off
chance that a cybercriminal takes steps to erase the user’s information, the user can
have it back online very quickly utilizing the user’s reinforcement framework. As a
best practice, reinforcement information ought to be put away in a protected, remote
area far from the user’s essential spot of business. This shields the user’s information
from both physical and digital dangers.
3) Purchase at least one insurance. There are several demonstrated sellers who are able
to give firewalls, malware blocking, spam sifting, phishing blocking, infection
security, and interruption location programming (Sennewald and Baillie, 2015). These
organizations have practical experience in system insurance and can give information
security that addresses the issues and spending plans of generally organizations.
4) Create a culture of the security in the organization. At last, each who is having at
least one client name and secret phrase is in charge of keeping organization
information secure. Intermittently remind the user’s directors and workers that it is
Systems that are Microsoft based, Active Directory will enable the user to supersede
the suggested phrase conventions that are secret. (On the off chance that the user are
not required to change the user’s phrase that is secret each quarter, this component
will have been killed.)
2) Use a reinforcement plan that is safe. As of now It should be a key piece of the user’s
IT technique. Secure reinforcements help the user endure everything from incidental
record erasure to sea tempest demolition. Those equivalent reinforcements can
likewise enable the user to endure cyber blackmail (Rantos et al., 2018). On the off
chance that a cybercriminal takes steps to erase the user’s information, the user can
have it back online very quickly utilizing the user’s reinforcement framework. As a
best practice, reinforcement information ought to be put away in a protected, remote
area far from the user’s essential spot of business. This shields the user’s information
from both physical and digital dangers.
3) Purchase at least one insurance. There are several demonstrated sellers who are able
to give firewalls, malware blocking, spam sifting, phishing blocking, infection
security, and interruption location programming (Sennewald and Baillie, 2015). These
organizations have practical experience in system insurance and can give information
security that addresses the issues and spending plans of generally organizations.
4) Create a culture of the security in the organization. At last, each who is having at
least one client name and secret phrase is in charge of keeping organization
information secure. Intermittently remind the user’s directors and workers that it is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
imperative to the organization's future that they do not share sign in data. Urge them
to be increasingly careful with verifying their passwords (Rittinghouse and Ransome,
2017). Composing passwords on a sticky note set under a console or in, a record
saved money on a PC ought to be restricted. Pay attention to interior information
security conventions. A 2013 Coreo ponder uncovered where 43% of the main
systems are hacked, they were assaulted utilizing the culprits who are verified inside
the organization.
Methodology:
Data security hazard the executives (ISRM) is known as the way toward
distinguishing, understanding, evaluating and alleviating hazard together with basic
vulnerabilities as well as the effect to the data, data systems as well as the organizations
depend upon the data for the tasks of them. Notwithstanding by recognizing the troubles as
well as the activities that hazard alleviation, a hazard the board technique and procedure will
distinguish basic data resources - a hazard the board program can be reached out to likewise
distinguish basic individuals, business procedures and innovation. The ISRM is one of the
pieces of the hazard that is general, the board of an association, so this thing ought to be lined
up with the abnormal and general, state chance for the strategy of administration (Rienzo et
al., 2018). The acknowledgment of the objective that are previously mentioned, of data
security is reliant on the data security chance administration strategy; arrangement and
techniques, procedure and partners. Danger, powerlessness, resources, result and effect are
known as data security hazard (ISR) segments. The most significant part in ISR is the
advantages. Resources comprise of data, procedure or innovation that was influenced by the
hazard. Not all segments in ISR can be controlled aside from defencelessness.
imperative to the organization's future that they do not share sign in data. Urge them
to be increasingly careful with verifying their passwords (Rittinghouse and Ransome,
2017). Composing passwords on a sticky note set under a console or in, a record
saved money on a PC ought to be restricted. Pay attention to interior information
security conventions. A 2013 Coreo ponder uncovered where 43% of the main
systems are hacked, they were assaulted utilizing the culprits who are verified inside
the organization.
Methodology:
Data security hazard the executives (ISRM) is known as the way toward
distinguishing, understanding, evaluating and alleviating hazard together with basic
vulnerabilities as well as the effect to the data, data systems as well as the organizations
depend upon the data for the tasks of them. Notwithstanding by recognizing the troubles as
well as the activities that hazard alleviation, a hazard the board technique and procedure will
distinguish basic data resources - a hazard the board program can be reached out to likewise
distinguish basic individuals, business procedures and innovation. The ISRM is one of the
pieces of the hazard that is general, the board of an association, so this thing ought to be lined
up with the abnormal and general, state chance for the strategy of administration (Rienzo et
al., 2018). The acknowledgment of the objective that are previously mentioned, of data
security is reliant on the data security chance administration strategy; arrangement and
techniques, procedure and partners. Danger, powerlessness, resources, result and effect are
known as data security hazard (ISR) segments. The most significant part in ISR is the
advantages. Resources comprise of data, procedure or innovation that was influenced by the
hazard. Not all segments in ISR can be controlled aside from defencelessness.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY
References:
Baggett, R.K. and Simpkins, B.K., 2018. Homeland security and critical infrastructure
protection. ABC-CLIO.
Cunningham, J. and Ainsworth, J., 2018. Enabling patient control of personal electronic
health records through distributed ledger technology. Stud Health Technol Inform, 245,
pp.45-48.
Forbes-Mewett, H., 2018. Personal Security. In The New Security (pp. 217-237). Palgrave
Macmillan, London.
Grassi, P., Fenton, J., Lefkovitz, N., Danker, J., Choong, Y.Y., Greene, K. and Theofanos,
M., 2017. Digital Identity Guidelines: Enrollment and Identity Proofing (No. NIST Special
Publication (SP) 800-63A (Withdrawn)). National Institute of Standards and Technology.
Grassi, P., Garcia, M. and Fenton, J., 2017. Digital identity guidelines (No. NIST Special
Publication (SP) 800-63-3 (Draft)). National Institute of Standards and Technology.
He, D., Chan, S. and Guizani, M., 2015. Mobile application security: malware threats and
defenses. IEEE Wireless Communications, 22(1), pp.138-144.
Jasińska, K. and Kaczmarski, M., 2018. Management of Security of the Business Information
as Exemplified by the National Debt Register of the Business Information Bureau
JSC. Management Sciences. Nauki o Zarządzaniu, 23(1), pp.27-36.
Khalilzadeh, J., Ozturk, A.B. and Bilgihan, A., 2017. Security-related factors in extended
UTAUT model for NFC based mobile payment in the restaurant industry. Computers in
Human Behavior, 70, pp.460-474.
References:
Baggett, R.K. and Simpkins, B.K., 2018. Homeland security and critical infrastructure
protection. ABC-CLIO.
Cunningham, J. and Ainsworth, J., 2018. Enabling patient control of personal electronic
health records through distributed ledger technology. Stud Health Technol Inform, 245,
pp.45-48.
Forbes-Mewett, H., 2018. Personal Security. In The New Security (pp. 217-237). Palgrave
Macmillan, London.
Grassi, P., Fenton, J., Lefkovitz, N., Danker, J., Choong, Y.Y., Greene, K. and Theofanos,
M., 2017. Digital Identity Guidelines: Enrollment and Identity Proofing (No. NIST Special
Publication (SP) 800-63A (Withdrawn)). National Institute of Standards and Technology.
Grassi, P., Garcia, M. and Fenton, J., 2017. Digital identity guidelines (No. NIST Special
Publication (SP) 800-63-3 (Draft)). National Institute of Standards and Technology.
He, D., Chan, S. and Guizani, M., 2015. Mobile application security: malware threats and
defenses. IEEE Wireless Communications, 22(1), pp.138-144.
Jasińska, K. and Kaczmarski, M., 2018. Management of Security of the Business Information
as Exemplified by the National Debt Register of the Business Information Bureau
JSC. Management Sciences. Nauki o Zarządzaniu, 23(1), pp.27-36.
Khalilzadeh, J., Ozturk, A.B. and Bilgihan, A., 2017. Security-related factors in extended
UTAUT model for NFC based mobile payment in the restaurant industry. Computers in
Human Behavior, 70, pp.460-474.

11INFORMATION SECURITY
Martínez-Pérez, B., De La Torre-Díez, I. and López-Coronado, M., 2015. Privacy and
security in mobile health apps: a review and recommendations. Journal of medical
systems, 39(1), p.181.
McCormac, A., Calic, D., Parsons, K., Butavicius, M., Pattinson, M. and Lillie, M., 2018.
The effect of resilience and job stress on information security awareness. Information &
Computer Security, 26(3), pp.277-289.
Oliveira, T., Thomas, M., Baptista, G. and Campos, F., 2016. Mobile payment:
Understanding the determinants of customer adoption and intention to recommend the
technology. Computers in Human Behavior, 61, pp.404-414.
Rantos, K., Drosatos, G., Demertzis, K., Ilioudis, C. and Papanikolaou, A., 2018. Blockchain-
based consents management for personal data processing in the IoT ecosystem.
In proceedings of the 15th International Conference on Security and Cryptography
(SECRYPT 2018), part of ICETE (pp. 572-577).
Rienzo, A., Bustamante, M., Aravena, C. and Lefranc, G., 2018, October. Evaluation of the
Degree of Knowledge and Implementation of Information Security Management Systems,
based of the NCh-ISO 27001 Standard, in Health Institutions. In 2018 IEEE International
Conference on Automation/XXIII Congress of the Chilean Association of Automatic Control
(ICA-ACCA) (pp. 1-6). IEEE.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation,
management, and security. CRC press.
Roman, R., Lopez, J. and Mambo, M., 2018. Mobile edge computing, fog et al.: A survey and
analysis of security threats and challenges. Future Generation Computer Systems, 78, pp.680-
698.
Martínez-Pérez, B., De La Torre-Díez, I. and López-Coronado, M., 2015. Privacy and
security in mobile health apps: a review and recommendations. Journal of medical
systems, 39(1), p.181.
McCormac, A., Calic, D., Parsons, K., Butavicius, M., Pattinson, M. and Lillie, M., 2018.
The effect of resilience and job stress on information security awareness. Information &
Computer Security, 26(3), pp.277-289.
Oliveira, T., Thomas, M., Baptista, G. and Campos, F., 2016. Mobile payment:
Understanding the determinants of customer adoption and intention to recommend the
technology. Computers in Human Behavior, 61, pp.404-414.
Rantos, K., Drosatos, G., Demertzis, K., Ilioudis, C. and Papanikolaou, A., 2018. Blockchain-
based consents management for personal data processing in the IoT ecosystem.
In proceedings of the 15th International Conference on Security and Cryptography
(SECRYPT 2018), part of ICETE (pp. 572-577).
Rienzo, A., Bustamante, M., Aravena, C. and Lefranc, G., 2018, October. Evaluation of the
Degree of Knowledge and Implementation of Information Security Management Systems,
based of the NCh-ISO 27001 Standard, in Health Institutions. In 2018 IEEE International
Conference on Automation/XXIII Congress of the Chilean Association of Automatic Control
(ICA-ACCA) (pp. 1-6). IEEE.
Rittinghouse, J.W. and Ransome, J.F., 2017. Cloud computing: implementation,
management, and security. CRC press.
Roman, R., Lopez, J. and Mambo, M., 2018. Mobile edge computing, fog et al.: A survey and
analysis of security threats and challenges. Future Generation Computer Systems, 78, pp.680-
698.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.