Analysis of Information Security Concepts: CIA, Biometrics, Encryption
VerifiedAdded on 2023/01/19
|5
|1290
|53
Homework Assignment
AI Summary
This assignment delves into key aspects of information security, beginning with the CIA triad (confidentiality, integrity, and availability) and its application to ATM security, including the permutation calculation of possible PIN attempts. The assignment explores the advantages and disadvantages of biometric identification, including false acceptance and security concerns, and suggests solutions like gradient mean and multi-factor authentication. It also discusses false negatives in biometric systems. The assignment further examines encryption methods, contrasting transposition and substitution ciphers, and provides a detailed example of a transposition cipher, including the encrypted text, key, and decoded plaintext. The provided solution covers various security concepts and includes a reference list.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Information Security
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
INFORMATION SECURITY
1. CIA has been related as a guide that involve concept of availability, confidentiality and
integrity. These have been taken for proper measurement of context in data and information
security. ATM is used as technology for money transaction based on security as an essential role
(Krishna, Reddy, Kiran & Reddy, 2016). The pin number of ATM card has been an essential
security aspect that has been helping in retaining access to illegal users. It helps in securing data
and information stored in the card. The integrity of the ATM pin has been maintaining smart
approach in order to secure information stored in the ATM card.
2. The number of times that a thief is able to put the pin number can be calculated by
permutation method. The thief has already break five keys and rest of five keys have been
available. The ATM pin include 4 digits. However, after entering three unsuccessful attempts,
the ATM card will be blocked. Therefore, the permutation of correct pin is given below:
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
The above results shows that there are only 120 outcomes of opening the pin. After three
ineffectual undertakings, the card get blocked. As such, it might be dismembered that thief has
only three undertakings out of 120 possible outcomes for opening card and later it get blocked.
3. The disadvantages of biometric identification has been given below:
False acceptance: There might be technical errors prevailing in the biometric system. The system
might started accepting false acceptance of illegal users (Jain, Nandakumar & Ross, 2016).
Therefore, the security of data and information in the biometric system might get breached.
Security: Biometric system contain various personal data and information of users. Therefore, it
becomes an unsecured section as most of the hackers might target these biometric systems (Tan
& Yao, 2016).
INFORMATION SECURITY
1. CIA has been related as a guide that involve concept of availability, confidentiality and
integrity. These have been taken for proper measurement of context in data and information
security. ATM is used as technology for money transaction based on security as an essential role
(Krishna, Reddy, Kiran & Reddy, 2016). The pin number of ATM card has been an essential
security aspect that has been helping in retaining access to illegal users. It helps in securing data
and information stored in the card. The integrity of the ATM pin has been maintaining smart
approach in order to secure information stored in the ATM card.
2. The number of times that a thief is able to put the pin number can be calculated by
permutation method. The thief has already break five keys and rest of five keys have been
available. The ATM pin include 4 digits. However, after entering three unsuccessful attempts,
the ATM card will be blocked. Therefore, the permutation of correct pin is given below:
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
The above results shows that there are only 120 outcomes of opening the pin. After three
ineffectual undertakings, the card get blocked. As such, it might be dismembered that thief has
only three undertakings out of 120 possible outcomes for opening card and later it get blocked.
3. The disadvantages of biometric identification has been given below:
False acceptance: There might be technical errors prevailing in the biometric system. The system
might started accepting false acceptance of illegal users (Jain, Nandakumar & Ross, 2016).
Therefore, the security of data and information in the biometric system might get breached.
Security: Biometric system contain various personal data and information of users. Therefore, it
becomes an unsecured section as most of the hackers might target these biometric systems (Tan
& Yao, 2016).

3
INFORMATION SECURITY
Solution to these issues:
Gradient mean: There has been need of three concepts of biometric authentication that help in
increasing the security of the data and information in the system.
Multifactor authentication: There has been a requirement of multifactor authentication including
iris scan, face recognition and fingerprint recognition.
4. A false negative refers to a condition when user of biometric does not have access to biometric
location (Aized Amin Soofi & Rasheed, 2016). False negative has been referring to decoding
session when owners have no access to information. It is found that in the essential condition,
person's identity isn't known anyway in various cases, it can generally make number of troubles
similarly as challenges in character of people can all around get limited in light of various
activities. In the second situation, thought loss in data identity. This all things considered has
been making various challenges similarly as troubles and thusly it has been particularly essential
to consider it. It is critical to have more security-based structure with appropriate element of
organization.
5. Transposition has been an encryption method in which the positions units of plaintext have
been shifted according to a regular system. Therefore, cipher text constitute a permutation of the
plaintext. However, in substitution method, it replaces characters and therefore, it is simpler and
easy to break.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
INFORMATION SECURITY
Solution to these issues:
Gradient mean: There has been need of three concepts of biometric authentication that help in
increasing the security of the data and information in the system.
Multifactor authentication: There has been a requirement of multifactor authentication including
iris scan, face recognition and fingerprint recognition.
4. A false negative refers to a condition when user of biometric does not have access to biometric
location (Aized Amin Soofi & Rasheed, 2016). False negative has been referring to decoding
session when owners have no access to information. It is found that in the essential condition,
person's identity isn't known anyway in various cases, it can generally make number of troubles
similarly as challenges in character of people can all around get limited in light of various
activities. In the second situation, thought loss in data identity. This all things considered has
been making various challenges similarly as troubles and thusly it has been particularly essential
to consider it. It is critical to have more security-based structure with appropriate element of
organization.
5. Transposition has been an encryption method in which the positions units of plaintext have
been shifted according to a regular system. Therefore, cipher text constitute a permutation of the
plaintext. However, in substitution method, it replaces characters and therefore, it is simpler and
easy to break.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
INFORMATION SECURITY
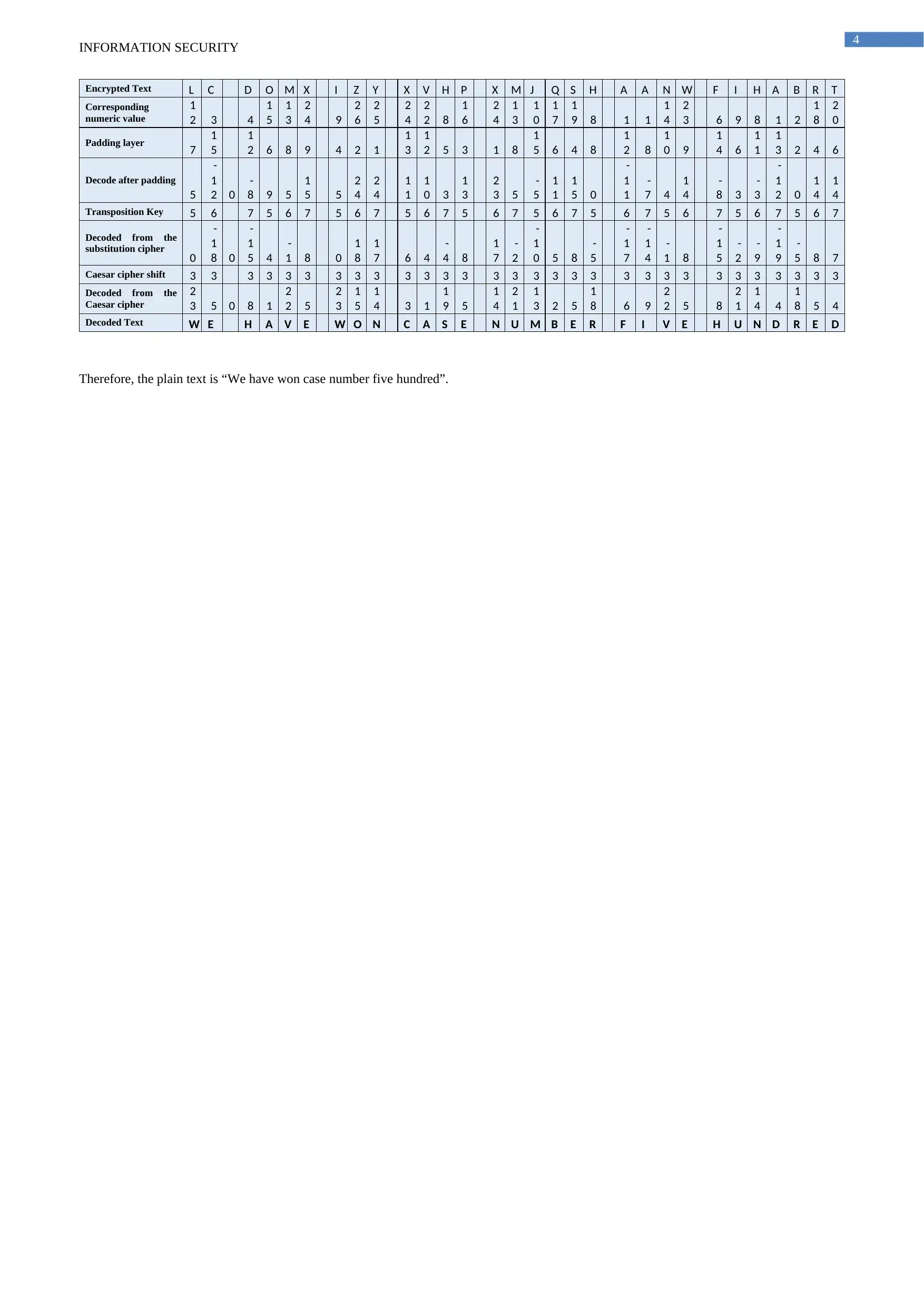
Encrypted Text L C D O M X I Z Y X V H P X M J Q S H A A N W F I H A B R T
Corresponding
numeric value
1
2 3 4
1
5
1
3
2
4 9
2
6
2
5
2
4
2
2 8
1
6
2
4
1
3
1
0
1
7
1
9 8 1 1
1
4
2
3 6 9 8 1 2
1
8
2
0
Padding layer 7
1
5
1
2 6 8 9 4 2 1
1
3
1
2 5 3 1 8
1
5 6 4 8
1
2 8
1
0 9
1
4 6
1
1
1
3 2 4 6
Decode after padding
5
-
1
2 0
-
8 9 5
1
5 5
2
4
2
4
1
1
1
0 3
1
3
2
3 5
-
5
1
1
1
5 0
-
1
1
-
7 4
1
4
-
8 3
-
3
-
1
2 0
1
4
1
4
Transposition Key 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7
Decoded from the
substitution cipher
0
-
1
8 0
-
1
5 4
-
1 8 0
1
8
1
7 6 4
-
4 8
1
7
-
2
-
1
0 5 8
-
5
-
1
7
-
1
4
-
1 8
-
1
5
-
2
-
9
-
1
9
-
5 8 7
Caesar cipher shift 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3
Decoded from the
Caesar cipher
2
3 5 0 8 1
2
2 5
2
3
1
5
1
4 3 1
1
9 5
1
4
2
1
1
3 2 5
1
8 6 9
2
2 5 8
2
1
1
4 4
1
8 5 4
Decoded Text W E H A V E W O N C A S E N U M B E R F I V E H U N D R E D
Therefore, the plain text is “We have won case number five hundred”.
INFORMATION SECURITY
Encrypted Text L C D O M X I Z Y X V H P X M J Q S H A A N W F I H A B R T
Corresponding
numeric value
1
2 3 4
1
5
1
3
2
4 9
2
6
2
5
2
4
2
2 8
1
6
2
4
1
3
1
0
1
7
1
9 8 1 1
1
4
2
3 6 9 8 1 2
1
8
2
0
Padding layer 7
1
5
1
2 6 8 9 4 2 1
1
3
1
2 5 3 1 8
1
5 6 4 8
1
2 8
1
0 9
1
4 6
1
1
1
3 2 4 6
Decode after padding
5
-
1
2 0
-
8 9 5
1
5 5
2
4
2
4
1
1
1
0 3
1
3
2
3 5
-
5
1
1
1
5 0
-
1
1
-
7 4
1
4
-
8 3
-
3
-
1
2 0
1
4
1
4
Transposition Key 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7 5 6 7
Decoded from the
substitution cipher
0
-
1
8 0
-
1
5 4
-
1 8 0
1
8
1
7 6 4
-
4 8
1
7
-
2
-
1
0 5 8
-
5
-
1
7
-
1
4
-
1 8
-
1
5
-
2
-
9
-
1
9
-
5 8 7
Caesar cipher shift 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3 3
Decoded from the
Caesar cipher
2
3 5 0 8 1
2
2 5
2
3
1
5
1
4 3 1
1
9 5
1
4
2
1
1
3 2 5
1
8 6 9
2
2 5 8
2
1
1
4 4
1
8 5 4
Decoded Text W E H A V E W O N C A S E N U M B E R F I V E H U N D R E D
Therefore, the plain text is “We have won case number five hundred”.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
INFORMATION SECURITY
References
Aized Amin Soofi, I. R., & Rasheed, U. (2016). An enhanced vigenere cipher for data
security. International Journal Of Scientific & Technology Research, 5(03).
Jain, A. K., Nandakumar, K., & Ross, A. (2016). 50 years of biometric research:
Accomplishments, challenges, and opportunities. Pattern Recognition Letters, 79, 80-
105.
Krishna, B. H., Reddy, I. R. S., Kiran, S., & Reddy, R. P. K. (2016, March). Multiple text
encryption, key entrenched, distributed cipher using pairing functions and transposition
ciphers. In 2016 International Conference on Wireless Communications, Signal
Processing and Networking (WiSPNET) (pp. 1059-1061). IEEE.
Tan, C., Li, Y., & Yao, S. (2016, December). A Novel Identification Approach to Encryption
Mode of Block Cipher. In 2016 4th International Conference on Sensors, Mechatronics
and Automation (ICSMA 2016). Atlantis Press.
INFORMATION SECURITY
References
Aized Amin Soofi, I. R., & Rasheed, U. (2016). An enhanced vigenere cipher for data
security. International Journal Of Scientific & Technology Research, 5(03).
Jain, A. K., Nandakumar, K., & Ross, A. (2016). 50 years of biometric research:
Accomplishments, challenges, and opportunities. Pattern Recognition Letters, 79, 80-
105.
Krishna, B. H., Reddy, I. R. S., Kiran, S., & Reddy, R. P. K. (2016, March). Multiple text
encryption, key entrenched, distributed cipher using pairing functions and transposition
ciphers. In 2016 International Conference on Wireless Communications, Signal
Processing and Networking (WiSPNET) (pp. 1059-1061). IEEE.
Tan, C., Li, Y., & Yao, S. (2016, December). A Novel Identification Approach to Encryption
Mode of Block Cipher. In 2016 4th International Conference on Sensors, Mechatronics
and Automation (ICSMA 2016). Atlantis Press.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




