IIL Location Intelligence for Policy Assessment (LIPPA) Project Design
VerifiedAdded on 2023/06/04
|14
|2968
|426
Project
AI Summary
This project presents a system design for Inshore Insurance Ltd's (IIL) Location Intelligence for Policy Profile Assessment (LIPPA) project. The design focuses on providing a high-level analysis and recommendations for an IT solution that addresses IIL's challenges in managing increasing data volumes and capturing the timing and location of accidents and crimes. The solution includes a single storage platform, system architecture, project governance, and IT infrastructure, incorporating data sensitivity measures, capacity requirements, and system interfaces. The design considers constraints such as financial limitations, technological constraints and human resources. It also includes use cases, object collaboration, and non-functional requirements. The proposed system involves various subsystems like finance, claims, and system administration to improve customer satisfaction and company revenue. The document also covers aspects like data solutions, infrastructure security, and application solutions such as the Risk Analysis Product (RAP) to provide a comprehensive system design for IIL's needs. The project excludes detailed technical specifications and software development at this stage.

INFORMATION SYSTEM PROJECT 1
Information system Project
Student Name
Institutional Affiliation
Information system Project
Student Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM PROJECT 2
Table of Contents
1 Introduction..............................................................................................................................3
1.1 Introduction.......................................................................................................................3
1.2 Solution Scope..................................................................................................................3
1.3 Solution Overview............................................................................................................3
1.4 Constraints........................................................................................................................3
1.5 Exclusions.........................................................................................................................5
2 Use Cases.................................................................................................................................5
2.1 Actors................................................................................................................................5
2.2 Use Case Diagrams...........................................................................................................5
3 Design Overview......................................................................................................................6
3.1 Solution Architecture........................................................................................................6
3.1.1 Project Governance Process......................................................................................7
3.1.2 IT Infrastructure Solution..........................................................................................8
3.1.3 Infrastructure Security...............................................................................................8
3.1.4 Application Solution..................................................................................................9
3.1.5 Data Solution.............................................................................................................9
3.2 Capacity Requirements...................................................................................................10
3.3 System Interfaces............................................................................................................10
3.4 Constraints and Assumptions..........................................................................................10
4 System Object Model.............................................................................................................10
4.1 Sub Systems....................................................................................................................10
4.2 Subsystem Interfaces.......................................................................................................11
5 Object Collaboration..............................................................................................................11
5.1 Collaboration Diagrams..................................................................................................11
5.2 Access Model..................................................................................................................11
6 Non Functional Requirements................................................................................................11
6.1 Performance Considerations...........................................................................................11
6.2 Design Constraints..........................................................................................................11
6.3 Test Criteria.....................................................................................................................12
6.4 Proof of Compliance.......................................................................................................12
7 References..............................................................................................................................12
Table of Contents
1 Introduction..............................................................................................................................3
1.1 Introduction.......................................................................................................................3
1.2 Solution Scope..................................................................................................................3
1.3 Solution Overview............................................................................................................3
1.4 Constraints........................................................................................................................3
1.5 Exclusions.........................................................................................................................5
2 Use Cases.................................................................................................................................5
2.1 Actors................................................................................................................................5
2.2 Use Case Diagrams...........................................................................................................5
3 Design Overview......................................................................................................................6
3.1 Solution Architecture........................................................................................................6
3.1.1 Project Governance Process......................................................................................7
3.1.2 IT Infrastructure Solution..........................................................................................8
3.1.3 Infrastructure Security...............................................................................................8
3.1.4 Application Solution..................................................................................................9
3.1.5 Data Solution.............................................................................................................9
3.2 Capacity Requirements...................................................................................................10
3.3 System Interfaces............................................................................................................10
3.4 Constraints and Assumptions..........................................................................................10
4 System Object Model.............................................................................................................10
4.1 Sub Systems....................................................................................................................10
4.2 Subsystem Interfaces.......................................................................................................11
5 Object Collaboration..............................................................................................................11
5.1 Collaboration Diagrams..................................................................................................11
5.2 Access Model..................................................................................................................11
6 Non Functional Requirements................................................................................................11
6.1 Performance Considerations...........................................................................................11
6.2 Design Constraints..........................................................................................................11
6.3 Test Criteria.....................................................................................................................12
6.4 Proof of Compliance.......................................................................................................12
7 References..............................................................................................................................12

INFORMATION SYSTEM PROJECT 3
1 Introduction
1.1 Introduction
Inshore Insurance Ltd (IIL) is a financial profitable organization based in Australia with its head
office in Sydney and other branches in all the other cities. The company wants to invest in an IT
solution that will provide a single storage platform and provides accurate timing and location of
accidents and crimes. This project has been named Location Intelligence for Policy Profile
Assessment (LIPPA) Project. IIL already have some infrastructure in place that it is currently
using such as web enable applications and cloud services that enable the institution to connect
with brokers and customers. The main data center is located in the headquarters and all the
information technology services are managed in-house.
1.2 Solution Scope
The scope of the LIPPA project is to provide a high level recommendation and analysis of the
proposed IT solution. Risk Analysis Product (RAP) s assumed to provide the functional
processing services required by IIL and has been hosted in the IIL main data center. The IT
solution shall provide a single storage platform to accommodate the vast volume of generated
and primary data from cloud and in-house sources.
1.3 Solution Overview
The IT solution should be able to address the current challenges faced by IIL. The amount of
data that the institution is handling is increasing and thus requires an application that will be able
to store, manage, analyze, and archive the data. The application should also have the capacity to
record the location and time when a crime and accidents occur. It should have the ability to
process low transaction and high volume of data with system access only restricted to thirteen
users (CIO and six other users to access report distribution and six users at the HQ). The IT
solution will provide episodic localized workday.
1.4 Constraints
Data sensitivity is a very crucial aspect especially when it involves private and confidential data.
Data sensitivity is one of the constraints that limits the development of the solution. As such, the
project team should be able to come up with measures to ensure data sensitivity. Benefit
realization plan is very important to ensure that the project adds value to the institution. Benefit
realization plan is important in benefit identification, execution, and sustenance. The threat
1 Introduction
1.1 Introduction
Inshore Insurance Ltd (IIL) is a financial profitable organization based in Australia with its head
office in Sydney and other branches in all the other cities. The company wants to invest in an IT
solution that will provide a single storage platform and provides accurate timing and location of
accidents and crimes. This project has been named Location Intelligence for Policy Profile
Assessment (LIPPA) Project. IIL already have some infrastructure in place that it is currently
using such as web enable applications and cloud services that enable the institution to connect
with brokers and customers. The main data center is located in the headquarters and all the
information technology services are managed in-house.
1.2 Solution Scope
The scope of the LIPPA project is to provide a high level recommendation and analysis of the
proposed IT solution. Risk Analysis Product (RAP) s assumed to provide the functional
processing services required by IIL and has been hosted in the IIL main data center. The IT
solution shall provide a single storage platform to accommodate the vast volume of generated
and primary data from cloud and in-house sources.
1.3 Solution Overview
The IT solution should be able to address the current challenges faced by IIL. The amount of
data that the institution is handling is increasing and thus requires an application that will be able
to store, manage, analyze, and archive the data. The application should also have the capacity to
record the location and time when a crime and accidents occur. It should have the ability to
process low transaction and high volume of data with system access only restricted to thirteen
users (CIO and six other users to access report distribution and six users at the HQ). The IT
solution will provide episodic localized workday.
1.4 Constraints
Data sensitivity is a very crucial aspect especially when it involves private and confidential data.
Data sensitivity is one of the constraints that limits the development of the solution. As such, the
project team should be able to come up with measures to ensure data sensitivity. Benefit
realization plan is very important to ensure that the project adds value to the institution. Benefit
realization plan is important in benefit identification, execution, and sustenance. The threat
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SYSTEM PROJECT 4
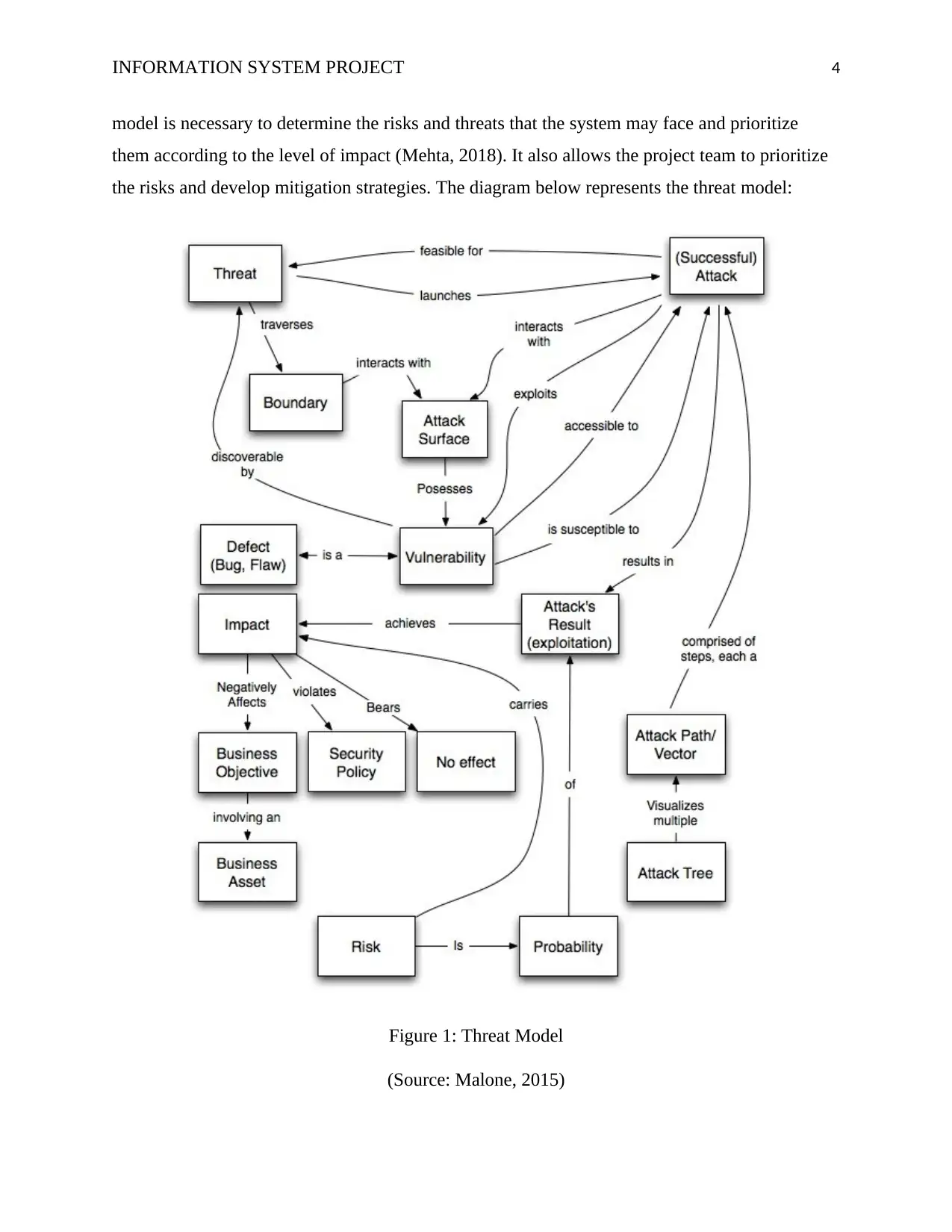
model is necessary to determine the risks and threats that the system may face and prioritize
them according to the level of impact (Mehta, 2018). It also allows the project team to prioritize
the risks and develop mitigation strategies. The diagram below represents the threat model:
Figure 1: Threat Model
(Source: Malone, 2015)
model is necessary to determine the risks and threats that the system may face and prioritize
them according to the level of impact (Mehta, 2018). It also allows the project team to prioritize
the risks and develop mitigation strategies. The diagram below represents the threat model:
Figure 1: Threat Model
(Source: Malone, 2015)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SYSTEM PROJECT 5
1.5 Exclusions
The project only involves the conceptual and logical design and as such the technical
requirements have been excluded. Also, the development of the software is not required at this
stage.
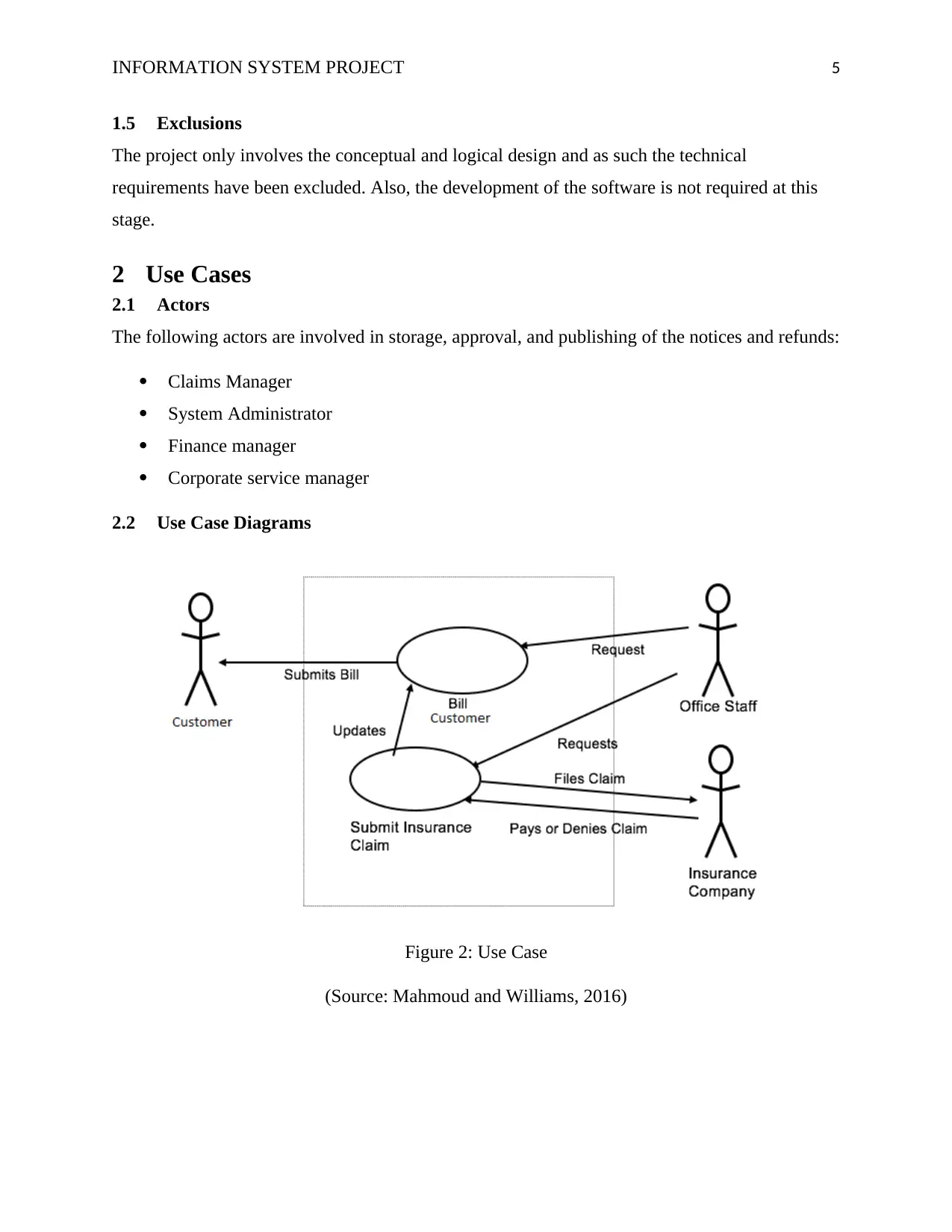
2 Use Cases
2.1 Actors
The following actors are involved in storage, approval, and publishing of the notices and refunds:
Claims Manager
System Administrator
Finance manager
Corporate service manager
2.2 Use Case Diagrams
Figure 2: Use Case
(Source: Mahmoud and Williams, 2016)
1.5 Exclusions
The project only involves the conceptual and logical design and as such the technical
requirements have been excluded. Also, the development of the software is not required at this
stage.
2 Use Cases
2.1 Actors
The following actors are involved in storage, approval, and publishing of the notices and refunds:
Claims Manager
System Administrator
Finance manager
Corporate service manager
2.2 Use Case Diagrams
Figure 2: Use Case
(Source: Mahmoud and Williams, 2016)
INFORMATION SYSTEM PROJECT 6
3 Design Overview
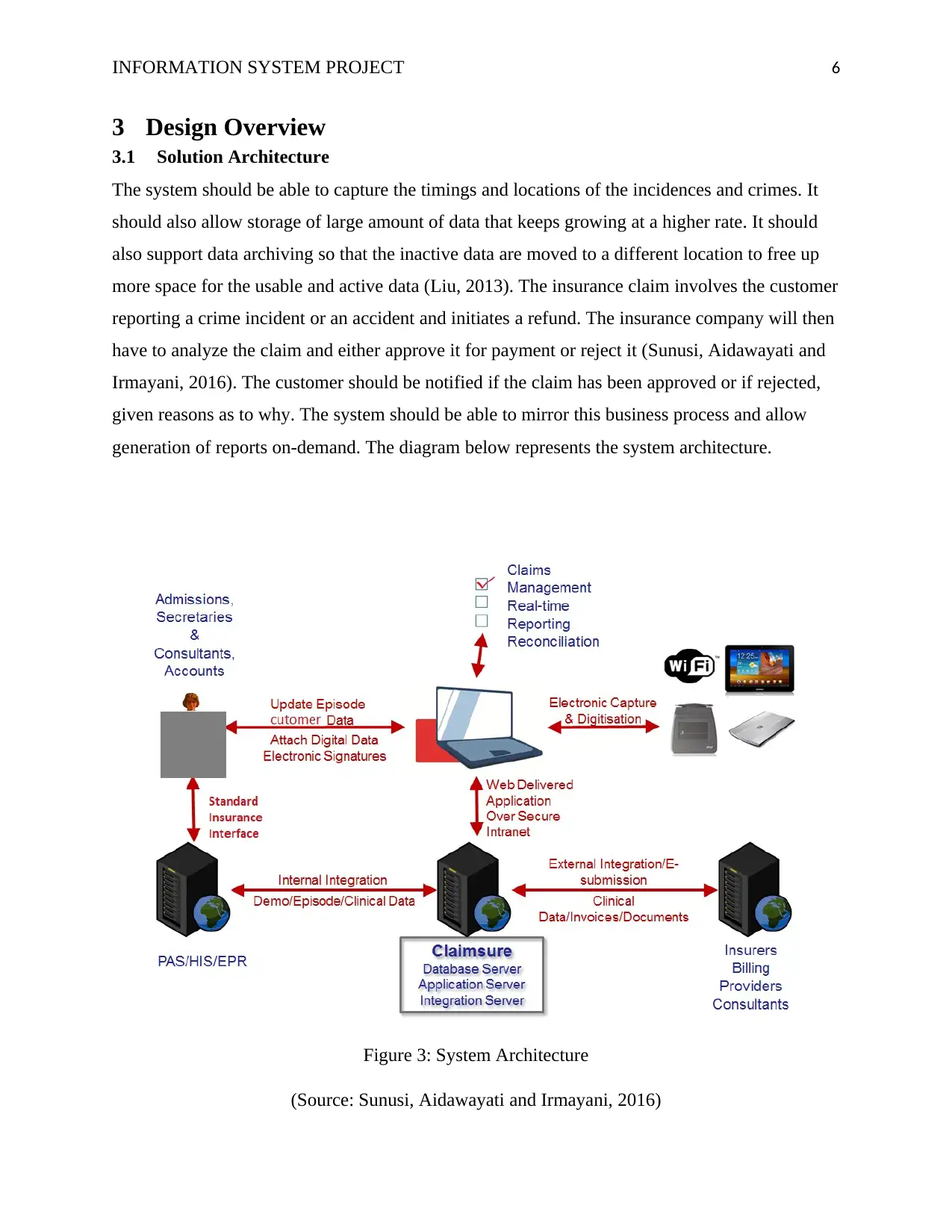
3.1 Solution Architecture
The system should be able to capture the timings and locations of the incidences and crimes. It
should also allow storage of large amount of data that keeps growing at a higher rate. It should
also support data archiving so that the inactive data are moved to a different location to free up
more space for the usable and active data (Liu, 2013). The insurance claim involves the customer
reporting a crime incident or an accident and initiates a refund. The insurance company will then
have to analyze the claim and either approve it for payment or reject it (Sunusi, Aidawayati and
Irmayani, 2016). The customer should be notified if the claim has been approved or if rejected,
given reasons as to why. The system should be able to mirror this business process and allow
generation of reports on-demand. The diagram below represents the system architecture.
Figure 3: System Architecture
(Source: Sunusi, Aidawayati and Irmayani, 2016)
3 Design Overview
3.1 Solution Architecture
The system should be able to capture the timings and locations of the incidences and crimes. It
should also allow storage of large amount of data that keeps growing at a higher rate. It should
also support data archiving so that the inactive data are moved to a different location to free up
more space for the usable and active data (Liu, 2013). The insurance claim involves the customer
reporting a crime incident or an accident and initiates a refund. The insurance company will then
have to analyze the claim and either approve it for payment or reject it (Sunusi, Aidawayati and
Irmayani, 2016). The customer should be notified if the claim has been approved or if rejected,
given reasons as to why. The system should be able to mirror this business process and allow
generation of reports on-demand. The diagram below represents the system architecture.
Figure 3: System Architecture
(Source: Sunusi, Aidawayati and Irmayani, 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SYSTEM PROJECT 7
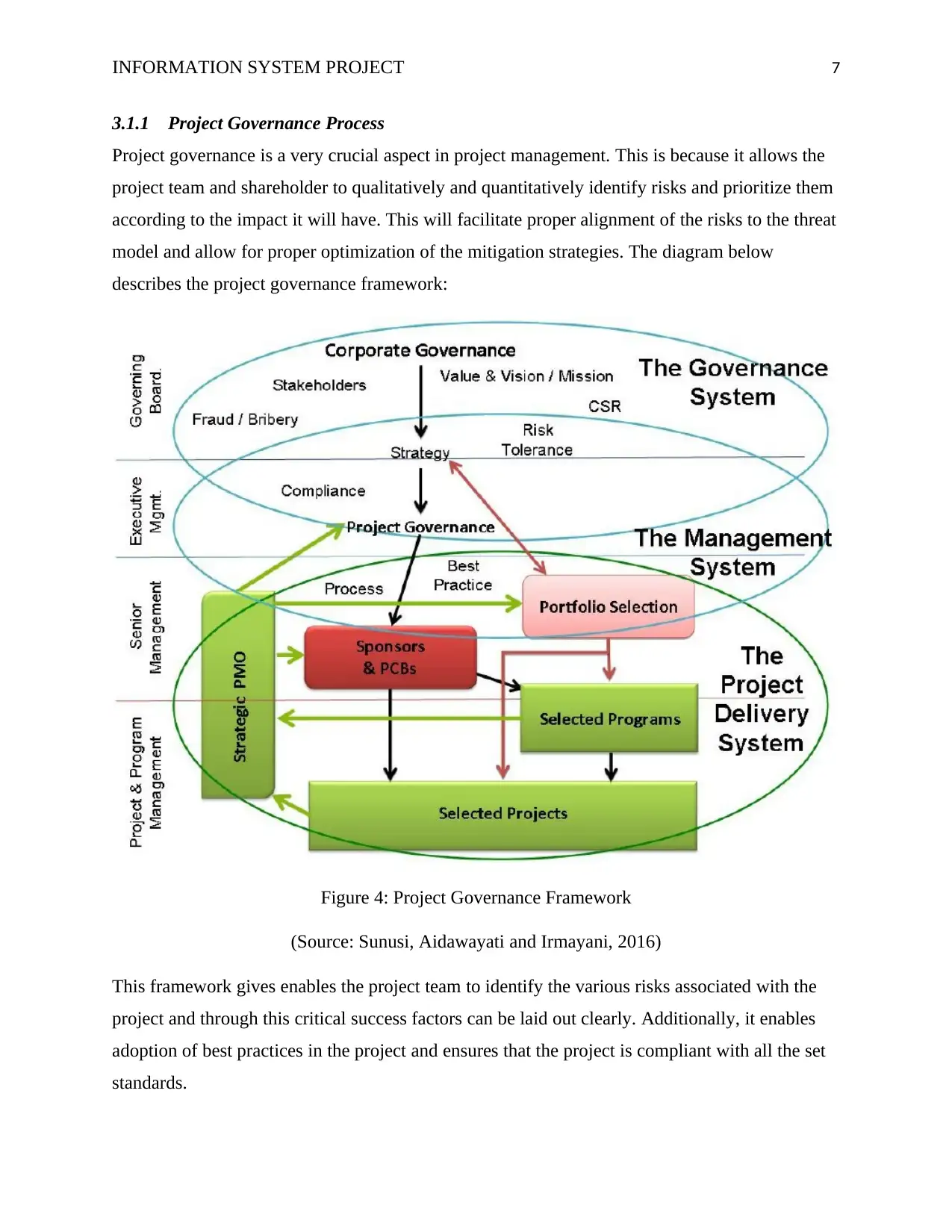
3.1.1 Project Governance Process
Project governance is a very crucial aspect in project management. This is because it allows the
project team and shareholder to qualitatively and quantitatively identify risks and prioritize them
according to the impact it will have. This will facilitate proper alignment of the risks to the threat
model and allow for proper optimization of the mitigation strategies. The diagram below
describes the project governance framework:
Figure 4: Project Governance Framework
(Source: Sunusi, Aidawayati and Irmayani, 2016)
This framework gives enables the project team to identify the various risks associated with the
project and through this critical success factors can be laid out clearly. Additionally, it enables
adoption of best practices in the project and ensures that the project is compliant with all the set
standards.
3.1.1 Project Governance Process
Project governance is a very crucial aspect in project management. This is because it allows the
project team and shareholder to qualitatively and quantitatively identify risks and prioritize them
according to the impact it will have. This will facilitate proper alignment of the risks to the threat
model and allow for proper optimization of the mitigation strategies. The diagram below
describes the project governance framework:
Figure 4: Project Governance Framework
(Source: Sunusi, Aidawayati and Irmayani, 2016)
This framework gives enables the project team to identify the various risks associated with the
project and through this critical success factors can be laid out clearly. Additionally, it enables
adoption of best practices in the project and ensures that the project is compliant with all the set
standards.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM PROJECT 8
3.1.2 IT Infrastructure Solution
The IT infrastructure is the backbone to any IT solution. As such, the system architects should
ensure that a proper logical design have been created before it is implemented. The process starts
with conceptualization where the conceptual design or idea is out on the table. However, the
conceptual design has less details and the users and other stakeholders are only given the general
picture of how the final product works or looks like. Logical design is an enhanced conceptual
design and gives more in-depth details of how the system operates and work. The diagram below
further illustrates the logical design:
Figure 5: Logical Design
(Source: Strauss, 2015)
3.1.3 Infrastructure Security
Infrastructure security is a very crucial aspect in ensuring the security of data and other digital
resources. It is a vital area that is concerned with network, systems, and assets protection. It
requires different expertise and skills so as to understand how the infrastructure work, possible
threats and security issues, and best practices to enforce security measures. There exist several It
infrastructure security measure including firewalls, access control, antiviruses, encryption among
others (Eden, 2018). Firewall is the first line defense for a network, it analyzes the network
traffic that gets into or out of the network and checks for any malicious or unwanted traffic end
prevents it from getting into the company network. This ensures that any unwanted traffic that
3.1.2 IT Infrastructure Solution
The IT infrastructure is the backbone to any IT solution. As such, the system architects should
ensure that a proper logical design have been created before it is implemented. The process starts
with conceptualization where the conceptual design or idea is out on the table. However, the
conceptual design has less details and the users and other stakeholders are only given the general
picture of how the final product works or looks like. Logical design is an enhanced conceptual
design and gives more in-depth details of how the system operates and work. The diagram below
further illustrates the logical design:
Figure 5: Logical Design
(Source: Strauss, 2015)
3.1.3 Infrastructure Security
Infrastructure security is a very crucial aspect in ensuring the security of data and other digital
resources. It is a vital area that is concerned with network, systems, and assets protection. It
requires different expertise and skills so as to understand how the infrastructure work, possible
threats and security issues, and best practices to enforce security measures. There exist several It
infrastructure security measure including firewalls, access control, antiviruses, encryption among
others (Eden, 2018). Firewall is the first line defense for a network, it analyzes the network
traffic that gets into or out of the network and checks for any malicious or unwanted traffic end
prevents it from getting into the company network. This ensures that any unwanted traffic that

INFORMATION SYSTEM PROJECT 9
targets the company network is prevented. Another security measure is access control where the
company devices password policies and access level restrictions. This will ensure that only
authorized users are able to access the system and all their activities are monitored to detect any
malicious activities by the users. Additionally, having a password policy is important to allow
users to create strong passwords to make it hard for attackers to guess. Encryption is a very
crucial aspect because it allows the users to send information in an encoded manner and thus the
cyber criminals will not be able to decode the information ensuring that privacy and integrity of
the information sent is maintained (Rouse, 2018).
3.1.4 Application Solution
The Risk Analysis Product (RAP) can be scaled in future to add more functionalities that are
relevant to the increasing requirements of the company. More functionalities can be integrated to
achieve maximum benefits from the system through process automation. Users should be able to
make their claims without visiting the company offices and provide enough information that can
be used to assess the claim. Additionally, the system should enable the users to generate reports
regarding the various aspects of the business such as financial reports, claim reports, incident and
crime reports among others. The reports should provide detailed information regarding the
specific function or process.
3.1.5 Data Solution
Data is a very critical resource to any business and therefore extreme care should be taken while
handling it. It should be defined, classified, and properly structured to allow easy management
and analysis. The new IT solution should be able to populate the data by categorizing the data
into various identifiable categories so as to allow easy analysis, search, and retrieval.
Additionally, the application should facilitate automated data archiving every five years to
ensure that data that is no longer being used is moved to create more space for the active data.
Archiving data is very essential because it allows most recent information to be used in decision
making and processing claims (Bojmaeh, 2015). It is recommended to archive data rather than
destroying it because it can be used in future for references on cases that may arise and needs old
data to arrive at a decision or a conclusion. It can also serve as evidence for the decisions made.
targets the company network is prevented. Another security measure is access control where the
company devices password policies and access level restrictions. This will ensure that only
authorized users are able to access the system and all their activities are monitored to detect any
malicious activities by the users. Additionally, having a password policy is important to allow
users to create strong passwords to make it hard for attackers to guess. Encryption is a very
crucial aspect because it allows the users to send information in an encoded manner and thus the
cyber criminals will not be able to decode the information ensuring that privacy and integrity of
the information sent is maintained (Rouse, 2018).
3.1.4 Application Solution
The Risk Analysis Product (RAP) can be scaled in future to add more functionalities that are
relevant to the increasing requirements of the company. More functionalities can be integrated to
achieve maximum benefits from the system through process automation. Users should be able to
make their claims without visiting the company offices and provide enough information that can
be used to assess the claim. Additionally, the system should enable the users to generate reports
regarding the various aspects of the business such as financial reports, claim reports, incident and
crime reports among others. The reports should provide detailed information regarding the
specific function or process.
3.1.5 Data Solution
Data is a very critical resource to any business and therefore extreme care should be taken while
handling it. It should be defined, classified, and properly structured to allow easy management
and analysis. The new IT solution should be able to populate the data by categorizing the data
into various identifiable categories so as to allow easy analysis, search, and retrieval.
Additionally, the application should facilitate automated data archiving every five years to
ensure that data that is no longer being used is moved to create more space for the active data.
Archiving data is very essential because it allows most recent information to be used in decision
making and processing claims (Bojmaeh, 2015). It is recommended to archive data rather than
destroying it because it can be used in future for references on cases that may arise and needs old
data to arrive at a decision or a conclusion. It can also serve as evidence for the decisions made.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEM PROJECT 10
3.2 Capacity Requirements
The performance of the system depends on capacity requirements. The overall productivity of
the system depends on various factors including hard disk capacity, RAM, processor type and
speed, operating system used in clients’ computers, and network speed (Flanigan and Brouse,
2012). As such, the minimum requirements should be clearly layout to enable users take
advantage of the system performance and productivity and allow them to carry out their daily
responsibilities with ease.
3.3 System Interfaces
System interface is a very critical aspect in any IT solution because it dictates if the product will
be accepted by users. The interface should be easy to use and uses icons and wordings that are
familiar to the users. This will allow the users to carry out their tasks with minimal help from the
system administrators. The interface should provide the users with options for searching,
generating and printing reports, and data archiving. By giving users more select and click options
over issuing commands through typing improves the productivity of the users.
3.4 Constraints and Assumptions
The IT solution will have several constraints including financial constraints, technological
constraints, limited time and human resource. These are scarce resources and therefore, they
should be used sparingly. The assumption made is that the IIL has the necessary infrastructure
for system implementation and that the users have proficient computer knowledge.
4 System Object Model
4.1 Sub Systems
The system will have various subsystem that will be integrated together to achieve the common
goal of customer satisfaction and increasing company productivity and revenue. Some of the
subsystems include finance module, claims module, sales and marketing module, data archiving
module, and system administrator module. These subsystems will work together in processing
customer claims. The database will be stored in the IIL data center in the head office while the
backup will be hosted in the cloud. The system administrator will have access to all these
subsystems in order to monitor users’ actions and troubleshoot any problems that may emerge.
3.2 Capacity Requirements
The performance of the system depends on capacity requirements. The overall productivity of
the system depends on various factors including hard disk capacity, RAM, processor type and
speed, operating system used in clients’ computers, and network speed (Flanigan and Brouse,
2012). As such, the minimum requirements should be clearly layout to enable users take
advantage of the system performance and productivity and allow them to carry out their daily
responsibilities with ease.
3.3 System Interfaces
System interface is a very critical aspect in any IT solution because it dictates if the product will
be accepted by users. The interface should be easy to use and uses icons and wordings that are
familiar to the users. This will allow the users to carry out their tasks with minimal help from the
system administrators. The interface should provide the users with options for searching,
generating and printing reports, and data archiving. By giving users more select and click options
over issuing commands through typing improves the productivity of the users.
3.4 Constraints and Assumptions
The IT solution will have several constraints including financial constraints, technological
constraints, limited time and human resource. These are scarce resources and therefore, they
should be used sparingly. The assumption made is that the IIL has the necessary infrastructure
for system implementation and that the users have proficient computer knowledge.
4 System Object Model
4.1 Sub Systems
The system will have various subsystem that will be integrated together to achieve the common
goal of customer satisfaction and increasing company productivity and revenue. Some of the
subsystems include finance module, claims module, sales and marketing module, data archiving
module, and system administrator module. These subsystems will work together in processing
customer claims. The database will be stored in the IIL data center in the head office while the
backup will be hosted in the cloud. The system administrator will have access to all these
subsystems in order to monitor users’ actions and troubleshoot any problems that may emerge.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM PROJECT 11
4.2 Subsystem Interfaces
The system will have several interfaces including:
Finance interface to allow the finance department users to make payments
Customer interface to allow users make claims and check status
Claims modules for the claim manager to analyze customer claims and either reject or
approve them for payment
System administrator interface to enable the system admins monitor and troubleshoot the
system.
5 Object Collaboration
5.1 Collaboration Diagrams
The system should allow several processes to collaborate for instance, when a customer makes a
claim the claim manager, customer relationship manager, and the finance manager are notified.
The claim manager analyzes the claim raised by the customer then the claim is approved and sent
to the finance manager to make payments. If it is rejected the customer relationship manager is
notified to get in touch with the customer to communicate why the claim was rejected.
5.2 Access Model
Access control system is very crucial in order to control the access to system resources. The
company should come with policies and regulations such as password policies to restrict access.
Additionally, it is important to implement access control measures such as two-factor
authentication to ensure that only authorized users have access to the system.
6 Non Functional Requirements
6.1 Performance Considerations
Users expect the system to process their request using the shortest time possible. As such, it is
important to pay attention to system security, network connectivity, cost, hard disk capacity,
RAM size, and processing speed (Shuaib, Khalil and Abdel-Hafez, 2013).
6.2 Design Constraints
There are several design constraint including usability, cost constraints, technological
constraints, integration, functional requirements, and non-functional requirements (Kim, 2014).
4.2 Subsystem Interfaces
The system will have several interfaces including:
Finance interface to allow the finance department users to make payments
Customer interface to allow users make claims and check status
Claims modules for the claim manager to analyze customer claims and either reject or
approve them for payment
System administrator interface to enable the system admins monitor and troubleshoot the
system.
5 Object Collaboration
5.1 Collaboration Diagrams
The system should allow several processes to collaborate for instance, when a customer makes a
claim the claim manager, customer relationship manager, and the finance manager are notified.
The claim manager analyzes the claim raised by the customer then the claim is approved and sent
to the finance manager to make payments. If it is rejected the customer relationship manager is
notified to get in touch with the customer to communicate why the claim was rejected.
5.2 Access Model
Access control system is very crucial in order to control the access to system resources. The
company should come with policies and regulations such as password policies to restrict access.
Additionally, it is important to implement access control measures such as two-factor
authentication to ensure that only authorized users have access to the system.
6 Non Functional Requirements
6.1 Performance Considerations
Users expect the system to process their request using the shortest time possible. As such, it is
important to pay attention to system security, network connectivity, cost, hard disk capacity,
RAM size, and processing speed (Shuaib, Khalil and Abdel-Hafez, 2013).
6.2 Design Constraints
There are several design constraint including usability, cost constraints, technological
constraints, integration, functional requirements, and non-functional requirements (Kim, 2014).

INFORMATION SYSTEM PROJECT 12
6.3 Test Criteria
The system will undergo several test criteria including unit testing, user acceptance testing, white
box testing, black box testing, integration testing, and fault tolerance testing (Spillner, 2013).
6.4 Proof of Compliance
Before the system is developed all the required compliance certificates will be acquired and it is
the responsibility of all the stakeholders to ensure that the system does not infringe on users right
or break any law.
6.3 Test Criteria
The system will undergo several test criteria including unit testing, user acceptance testing, white
box testing, black box testing, integration testing, and fault tolerance testing (Spillner, 2013).
6.4 Proof of Compliance
Before the system is developed all the required compliance certificates will be acquired and it is
the responsibility of all the stakeholders to ensure that the system does not infringe on users right
or break any law.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





