Information System Risk and Technology
VerifiedAdded on 2022/10/19
|11
|2729
|93
AI Summary
This report focuses on the risks associated with Information Systems and Security. The Case Study that will be referred to is that of the City of Melbourne (CoM). CoM is inspecting on the applications of digital technology in its region. The process has been initiated by organizing an event called CoM connect that has brought together thinkers, technologists, urbanists, community leaders, designers and makers to provide their reviews on the topic.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SYSTEM RISK AND TECHNOLOGY
INFORMATION SYSTEM RISK AND TECHNOLOGY
Name of the Student
Name of the university
Author note
INFORMATION SYSTEM RISK AND TECHNOLOGY
Name of the Student
Name of the university
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SYSTEM RISK AND TECHNOLOGY
Table of Contents
Purpose of the report..................................................................................................................3
Value Creation Activities of CoM.............................................................................................3
Key roles and responsibilities....................................................................................................4
Information assets......................................................................................................................6
Identified risks to CoM’s important information asset..............................................................7
Likelihood and impact analyses for CoM’s significant risks.....................................................8
Conclusion..................................................................................................................................9
Table of Contents
Purpose of the report..................................................................................................................3
Value Creation Activities of CoM.............................................................................................3
Key roles and responsibilities....................................................................................................4
Information assets......................................................................................................................6
Identified risks to CoM’s important information asset..............................................................7
Likelihood and impact analyses for CoM’s significant risks.....................................................8
Conclusion..................................................................................................................................9

2INFORMATION SYSTEM RISK AND TECHNOLOGY
Purpose of the report
The report focuses on the risks associated with Information Systems and Security.
The Case Study that will be referred to is that of the City of Melbourne (CoM). CoM is
inspecting on the applications of digital technology in its region. The process has been
initiated by organizing an event called CoM connect that has brought together thinkers,
technologists, urbanists, community leaders, designers and makers to provide their reviews
on the topic. Melbourne city encompasses land area of 36sqkm. The Annual Plan and Budget
mentions the priorities of the Council relating to capital, maintenance and operating programs
in the year 2012-2013. As per the Budget, investment to be done on infrastructure is $110
million and on community service is $365. The main objective of this report is to carry out
the risk assessment audit for the charity.
Value Creation Activities of CoM
CoM actively participates in marketing activities so that its target markets could be
expanded. Social media platforms have been used for web-marketing strategy launching
appeals from the website. Some specific users of social networking sites have been targeted
by the help of web-ad agency launched by CoM. The profile of CoM in social media has been
increasing since its launch and thus the serves as the best platform to create value. A web-
marketing and web-hosting company assists CoM in web-related infrastructures. CoM
launches “knock-on-doors” appeal sending volunteers to communicate with householders and
public to request donations from the society. The donors have the provision to talk to CoM
representatives to make donations using the credit card. Credit card payment facility is a good
strategy to create value and this has contributed almost 80% of the funding of CoM previous
year. The web-initiative taken by CoM allows web-based transactions and it plans to
introduce micro-donation via the social media. It needs to abide by PCIDSS to carry on with
Purpose of the report
The report focuses on the risks associated with Information Systems and Security.
The Case Study that will be referred to is that of the City of Melbourne (CoM). CoM is
inspecting on the applications of digital technology in its region. The process has been
initiated by organizing an event called CoM connect that has brought together thinkers,
technologists, urbanists, community leaders, designers and makers to provide their reviews
on the topic. Melbourne city encompasses land area of 36sqkm. The Annual Plan and Budget
mentions the priorities of the Council relating to capital, maintenance and operating programs
in the year 2012-2013. As per the Budget, investment to be done on infrastructure is $110
million and on community service is $365. The main objective of this report is to carry out
the risk assessment audit for the charity.
Value Creation Activities of CoM
CoM actively participates in marketing activities so that its target markets could be
expanded. Social media platforms have been used for web-marketing strategy launching
appeals from the website. Some specific users of social networking sites have been targeted
by the help of web-ad agency launched by CoM. The profile of CoM in social media has been
increasing since its launch and thus the serves as the best platform to create value. A web-
marketing and web-hosting company assists CoM in web-related infrastructures. CoM
launches “knock-on-doors” appeal sending volunteers to communicate with householders and
public to request donations from the society. The donors have the provision to talk to CoM
representatives to make donations using the credit card. Credit card payment facility is a good
strategy to create value and this has contributed almost 80% of the funding of CoM previous
year. The web-initiative taken by CoM allows web-based transactions and it plans to
introduce micro-donation via the social media. It needs to abide by PCIDSS to carry on with

3INFORMATION SYSTEM RISK AND TECHNOLOGY
credit card transactions. The CoM officers handling operations in different parts of the
country are provided with communication devices which include smart phones, satellite
phones and laptop. These are distributed to the local or regional staffs and these staffs have to
report to the regional office on a periodic basis to provide updates relating to Community
Development Authority (CDA), team, communities and themselves. The charter of CoM lays
stress on caring for the ones working for its projects. CoM had allowed its staffs to carry their
own communication devices so that they can work on devices they are familiar with. CoM
understands that the people giving donations want to know how the money they are donating
is being used and thus it had recognized that greater level of transparency and accountability
needs to be introduced in their work.
In situations where the staffs are allowed to bring their own devices gives rise to
operational issues such as compatibility issue that might be the staff is working with a certain
file format and has sent the file to the other staffs without converting it to appropriate format.
Malicious codes introduced in the office systems affected the local operations and the
headquarters have already witnessed disruptions in their work due to this (Senft, Gallegos and
Davis 2016). The web-hosting company which helps the CoM with the website also manages
its payment gateways and customers data. This can be a risk as these are providing services at
low cost or for free so it can be that the customers data is misused in the long run.
Key roles and responsibilities
In a risk management plan four important roles can be identified which are as follows:
1) Anyone who is associated with the project- This includes the staffs of CoM, the project
consultants, suppliers, subcontractors and anyone from the CoM who are related with the
project. To assess risks in a project, the stakeholders can be participants in risk identification.
The stakeholders can notify the project managers if they find out risks in the project
(Hoffmann, Kiedrowicz and Stanik 2016). The stakeholders in this case are CoM staffs and
credit card transactions. The CoM officers handling operations in different parts of the
country are provided with communication devices which include smart phones, satellite
phones and laptop. These are distributed to the local or regional staffs and these staffs have to
report to the regional office on a periodic basis to provide updates relating to Community
Development Authority (CDA), team, communities and themselves. The charter of CoM lays
stress on caring for the ones working for its projects. CoM had allowed its staffs to carry their
own communication devices so that they can work on devices they are familiar with. CoM
understands that the people giving donations want to know how the money they are donating
is being used and thus it had recognized that greater level of transparency and accountability
needs to be introduced in their work.
In situations where the staffs are allowed to bring their own devices gives rise to
operational issues such as compatibility issue that might be the staff is working with a certain
file format and has sent the file to the other staffs without converting it to appropriate format.
Malicious codes introduced in the office systems affected the local operations and the
headquarters have already witnessed disruptions in their work due to this (Senft, Gallegos and
Davis 2016). The web-hosting company which helps the CoM with the website also manages
its payment gateways and customers data. This can be a risk as these are providing services at
low cost or for free so it can be that the customers data is misused in the long run.
Key roles and responsibilities
In a risk management plan four important roles can be identified which are as follows:
1) Anyone who is associated with the project- This includes the staffs of CoM, the project
consultants, suppliers, subcontractors and anyone from the CoM who are related with the
project. To assess risks in a project, the stakeholders can be participants in risk identification.
The stakeholders can notify the project managers if they find out risks in the project
(Hoffmann, Kiedrowicz and Stanik 2016). The stakeholders in this case are CoM staffs and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INFORMATION SYSTEM RISK AND TECHNOLOGY
officers, human resource team consisting of one manager and HR specialists. The companies
assisting CoM in the web based applications are also the stakeholders in this case.
2) Risk Owner- A risk owner is a member of CoM designated by Project Manager to
effectively coordinate the analysis of a certain risk. It is the responsibility of the risk owner to
check that the risk analysis is performed in a proper way, documented and outcomes provided
to the associated project manager in time. The risk owner is responsible to assure that an
active risk is monitored and the project manger notified about the same.
3) Project Manager- The Project Manager is the one responsible for receiving the risks that
have been identified and keeping the records of all risks. The project manager needs to assign
these risks to the risk owner so that the risks can be analyzed and the results of the analysis
reviewed. This in turn helps in developing response recommendations and presents the same
to the sponsors. It is the responsibility of the project manager to check that the risks are
reviewed periodically identifying possible changes or impacts of the identified risks
(Hallowell, Hardison and Desvignes 2016). The project manager is also responsible for
coordinating the changes to the project plans so that the responses can be implemented. The
risk management plan needs to be created and maintained by the project manager. Here in
this case one of the CoM officers can be the project manager and keep a track of the risks and
the ways to mitigate them.
4) Project Sponsor- The project sponsor makes the executive decisions for the project. All
projects involve some or other risks and risk management process help in identifying the
project risks at the same time recommending how resources can be allocated in order to deal
with the same. The sponsors have the authority in determining whether the responses that
have been planned for the recognized risks are appropriate and sufficient. The sponsor then
reviews and gives their approval for the risk responses that have been proposed and
associated changes in the risk responses (Marchewka 2016). The sponsors of the project are
officers, human resource team consisting of one manager and HR specialists. The companies
assisting CoM in the web based applications are also the stakeholders in this case.
2) Risk Owner- A risk owner is a member of CoM designated by Project Manager to
effectively coordinate the analysis of a certain risk. It is the responsibility of the risk owner to
check that the risk analysis is performed in a proper way, documented and outcomes provided
to the associated project manager in time. The risk owner is responsible to assure that an
active risk is monitored and the project manger notified about the same.
3) Project Manager- The Project Manager is the one responsible for receiving the risks that
have been identified and keeping the records of all risks. The project manager needs to assign
these risks to the risk owner so that the risks can be analyzed and the results of the analysis
reviewed. This in turn helps in developing response recommendations and presents the same
to the sponsors. It is the responsibility of the project manager to check that the risks are
reviewed periodically identifying possible changes or impacts of the identified risks
(Hallowell, Hardison and Desvignes 2016). The project manager is also responsible for
coordinating the changes to the project plans so that the responses can be implemented. The
risk management plan needs to be created and maintained by the project manager. Here in
this case one of the CoM officers can be the project manager and keep a track of the risks and
the ways to mitigate them.
4) Project Sponsor- The project sponsor makes the executive decisions for the project. All
projects involve some or other risks and risk management process help in identifying the
project risks at the same time recommending how resources can be allocated in order to deal
with the same. The sponsors have the authority in determining whether the responses that
have been planned for the recognized risks are appropriate and sufficient. The sponsor then
reviews and gives their approval for the risk responses that have been proposed and
associated changes in the risk responses (Marchewka 2016). The sponsors of the project are

5INFORMATION SYSTEM RISK AND TECHNOLOGY
responsible for reviewing for prioritizing the identified risks. In this scenario the sponsors are
the donors and they have all right to know the risks related to the project they are donating
for. Transparency and accountability needs to be incorporated in the project.
Information assets
CoM-ONE is a corporate system that is operated by CoM. CoM-ONE is custom-made
system which was designed and implemented in the year 1990. Though the system has been a
robust system, there has been difficulty in maintaining the system since the last 5 years. The
growth in the operations has led to patches as well as extensions of the system. These patches
and extensions have no integration with CoM-ONE but certainly have the ability to feed data
and draw data from the primary database as well. In the process of development of the
various extensions, CoM has worked with many number of software vendors and these
vendors provide free services to the firm. The services are being provided for free so that they
can build their credibility. There have been many numbers of business and associated project
initiatives that were delayed as CoM-ONE was incapable of to meet the requirements of the
project. The problem here is that the Board is well aware of the issues of CoM-ONE but still
the IS/IT issue was ignored. The reason which was cited was that IT being an operational
aspect does not require to be discussed with the Board of Directors. CFO supports this and is
the one who normally breaks down the IS/IT issues to financial figures. There is neither any
IS/IT representative nor anyone reporting to the board. The Business Information Systems
Manager explores the possibility of replacing CoM-ONE with another similar corporate
system that is suitable for growth of the organization in future. The CoM officers handling
operations in different countries have equipments that are a set of mobile communication
devices including some of short range communication devices. Smart phones, satellite phones
and laptops are distributed amidst the staffs. The details of the short range communication
devices been given to staffs needs to be kept so that the devices are not misplaced. Risk
responsible for reviewing for prioritizing the identified risks. In this scenario the sponsors are
the donors and they have all right to know the risks related to the project they are donating
for. Transparency and accountability needs to be incorporated in the project.
Information assets
CoM-ONE is a corporate system that is operated by CoM. CoM-ONE is custom-made
system which was designed and implemented in the year 1990. Though the system has been a
robust system, there has been difficulty in maintaining the system since the last 5 years. The
growth in the operations has led to patches as well as extensions of the system. These patches
and extensions have no integration with CoM-ONE but certainly have the ability to feed data
and draw data from the primary database as well. In the process of development of the
various extensions, CoM has worked with many number of software vendors and these
vendors provide free services to the firm. The services are being provided for free so that they
can build their credibility. There have been many numbers of business and associated project
initiatives that were delayed as CoM-ONE was incapable of to meet the requirements of the
project. The problem here is that the Board is well aware of the issues of CoM-ONE but still
the IS/IT issue was ignored. The reason which was cited was that IT being an operational
aspect does not require to be discussed with the Board of Directors. CFO supports this and is
the one who normally breaks down the IS/IT issues to financial figures. There is neither any
IS/IT representative nor anyone reporting to the board. The Business Information Systems
Manager explores the possibility of replacing CoM-ONE with another similar corporate
system that is suitable for growth of the organization in future. The CoM officers handling
operations in different countries have equipments that are a set of mobile communication
devices including some of short range communication devices. Smart phones, satellite phones
and laptops are distributed amidst the staffs. The details of the short range communication
devices been given to staffs needs to be kept so that the devices are not misplaced. Risk

6INFORMATION SYSTEM RISK AND TECHNOLOGY
management information system is an information system that provides assistance in policies,
informations, claims and other consolidated property values. These help in tracking as well as
managing the reporting capabilities enabling the users to monitor and control the total cost of
risk management (Pimchangthong and Boonjing 2017). In case of CoM risk management
information system can help in managing the risk data and information thereby ensuring that
project is a success. These risk management information systems will support expert advice
and at the same time be cost effective in information management solutions aiding processes
such as risk identification, control and financing. CoM receives donations from public
through different modes and donors have the facility to pay via credit cards. The documents
recording the donations been made are information assets. The credit card informations are
information assets as well. The details of the donors are also a vital information asset for
CoM. The data related to CCOIP sales that include transactional data from the donors, the list
of donors, information of the donors and project related information.
Identified risks to CoM’s important information asset
CoM’s important information assets are the details of the credit card transactions and
the records of the data related to donations being made. The web-hosting company manages
the payment gateways and the volumes of data of the customers captured form the web
platform of CoM. CoM-ONE has the ability to feed or draw information from the main
database of CoM which can lead to privacy issues of data stored. The information related to
the credit card details can be misused in various if they go into the wrong hands. The credit
card has huge cash limits and criminals getting hold of these data can misuse the same to
draw cash from the cards (Schwalbe 2015). The information drawn from the main database of
CoM are important informations related to the donors and other informations regarding the
identity of the donors can be misused by persons wanting to disrupt the system. The HR
manager at CoM plans to move operations of the HR department to the cloud and an US
management information system is an information system that provides assistance in policies,
informations, claims and other consolidated property values. These help in tracking as well as
managing the reporting capabilities enabling the users to monitor and control the total cost of
risk management (Pimchangthong and Boonjing 2017). In case of CoM risk management
information system can help in managing the risk data and information thereby ensuring that
project is a success. These risk management information systems will support expert advice
and at the same time be cost effective in information management solutions aiding processes
such as risk identification, control and financing. CoM receives donations from public
through different modes and donors have the facility to pay via credit cards. The documents
recording the donations been made are information assets. The credit card informations are
information assets as well. The details of the donors are also a vital information asset for
CoM. The data related to CCOIP sales that include transactional data from the donors, the list
of donors, information of the donors and project related information.
Identified risks to CoM’s important information asset
CoM’s important information assets are the details of the credit card transactions and
the records of the data related to donations being made. The web-hosting company manages
the payment gateways and the volumes of data of the customers captured form the web
platform of CoM. CoM-ONE has the ability to feed or draw information from the main
database of CoM which can lead to privacy issues of data stored. The information related to
the credit card details can be misused in various if they go into the wrong hands. The credit
card has huge cash limits and criminals getting hold of these data can misuse the same to
draw cash from the cards (Schwalbe 2015). The information drawn from the main database of
CoM are important informations related to the donors and other informations regarding the
identity of the donors can be misused by persons wanting to disrupt the system. The HR
manager at CoM plans to move operations of the HR department to the cloud and an US
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION SYSTEM RISK AND TECHNOLOGY
based SaaS provider had also been consulted. The informations are sensitive relating to credit
cards and details of donors which are vulnerable to attacks if the cloud based services are
incorporated. The data related to CCOIP (Critical Communication over IP) sales are vital and
their privacy should be maintained. The data backup is provided by a startup company which
can make it vulnerable to risks. CoM should not trust a startup company with sensitive data.
A well known company should have been given the responsibility of handling these data as
startups are new established companies. CoM has moved its backup to the new company as
the previous company has started charging fees. This can be a negative aspect as the old
company could be trusted with the data as CoM had been working with it for long. Startup
companies usually require financial assistance and thus these data can be mishandled by the
company to support its financial conditions. The ISO27k standards are aligned to the risks
that are the companies are encouraged to assess the risks so that these can be mitigated in
numerous ways (Taylor 2015). CoM provides certain guidelines for information security risk
management and also supports some of the concepts that have been specified in the ISO/IEC
27001. This will help CoM in assisting the implementation of information security system
that is based on risk management approaches.
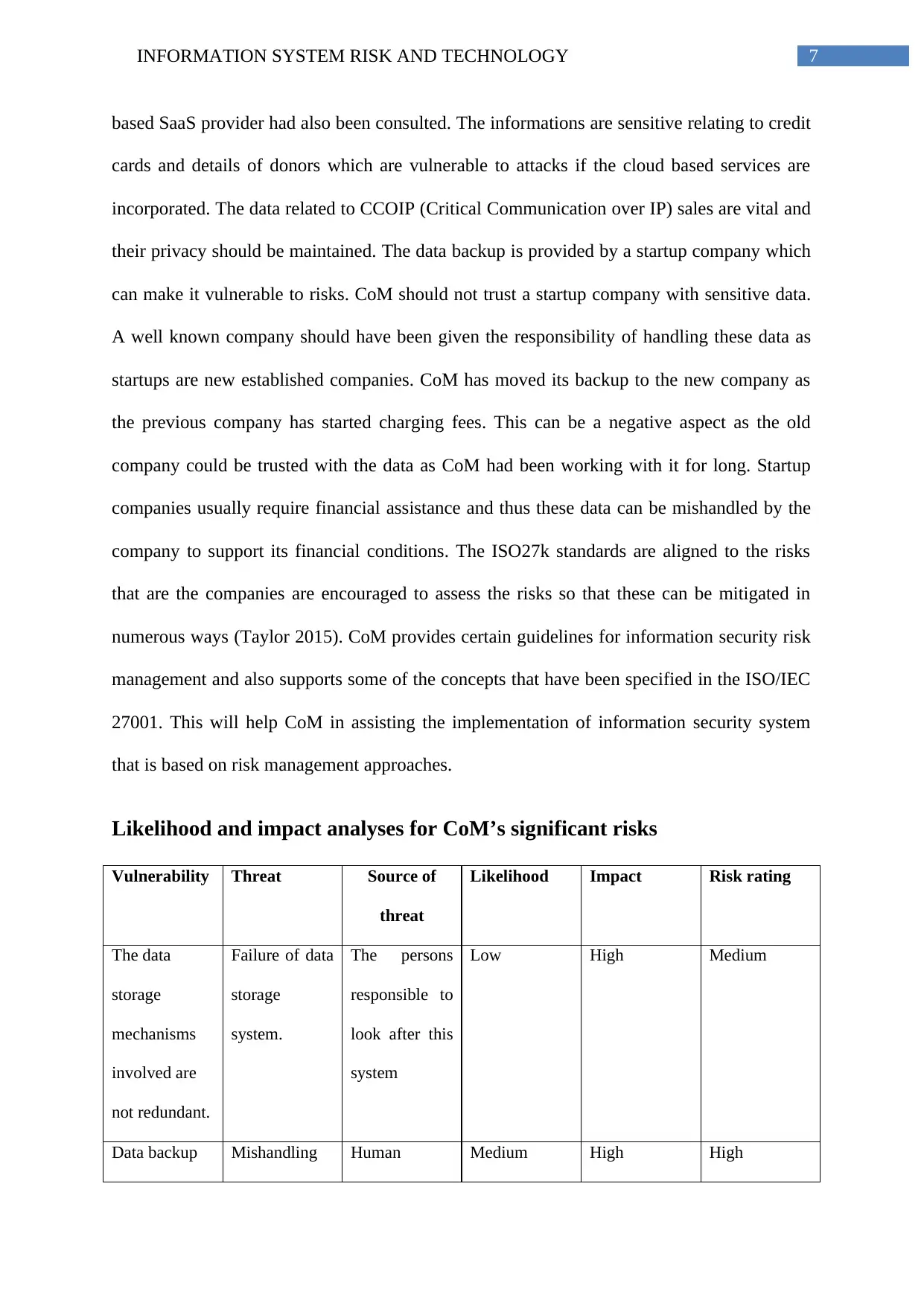
Likelihood and impact analyses for CoM’s significant risks
Vulnerability Threat Source of
threat
Likelihood Impact Risk rating
The data
storage
mechanisms
involved are
not redundant.
Failure of data
storage
system.
The persons
responsible to
look after this
system
Low High Medium
Data backup Mishandling Human Medium High High
based SaaS provider had also been consulted. The informations are sensitive relating to credit
cards and details of donors which are vulnerable to attacks if the cloud based services are
incorporated. The data related to CCOIP (Critical Communication over IP) sales are vital and
their privacy should be maintained. The data backup is provided by a startup company which
can make it vulnerable to risks. CoM should not trust a startup company with sensitive data.
A well known company should have been given the responsibility of handling these data as
startups are new established companies. CoM has moved its backup to the new company as
the previous company has started charging fees. This can be a negative aspect as the old
company could be trusted with the data as CoM had been working with it for long. Startup
companies usually require financial assistance and thus these data can be mishandled by the
company to support its financial conditions. The ISO27k standards are aligned to the risks
that are the companies are encouraged to assess the risks so that these can be mitigated in
numerous ways (Taylor 2015). CoM provides certain guidelines for information security risk
management and also supports some of the concepts that have been specified in the ISO/IEC
27001. This will help CoM in assisting the implementation of information security system
that is based on risk management approaches.
Likelihood and impact analyses for CoM’s significant risks
Vulnerability Threat Source of
threat
Likelihood Impact Risk rating
The data
storage
mechanisms
involved are
not redundant.
Failure of data
storage
system.
The persons
responsible to
look after this
system
Low High Medium
Data backup Mishandling Human Medium High High
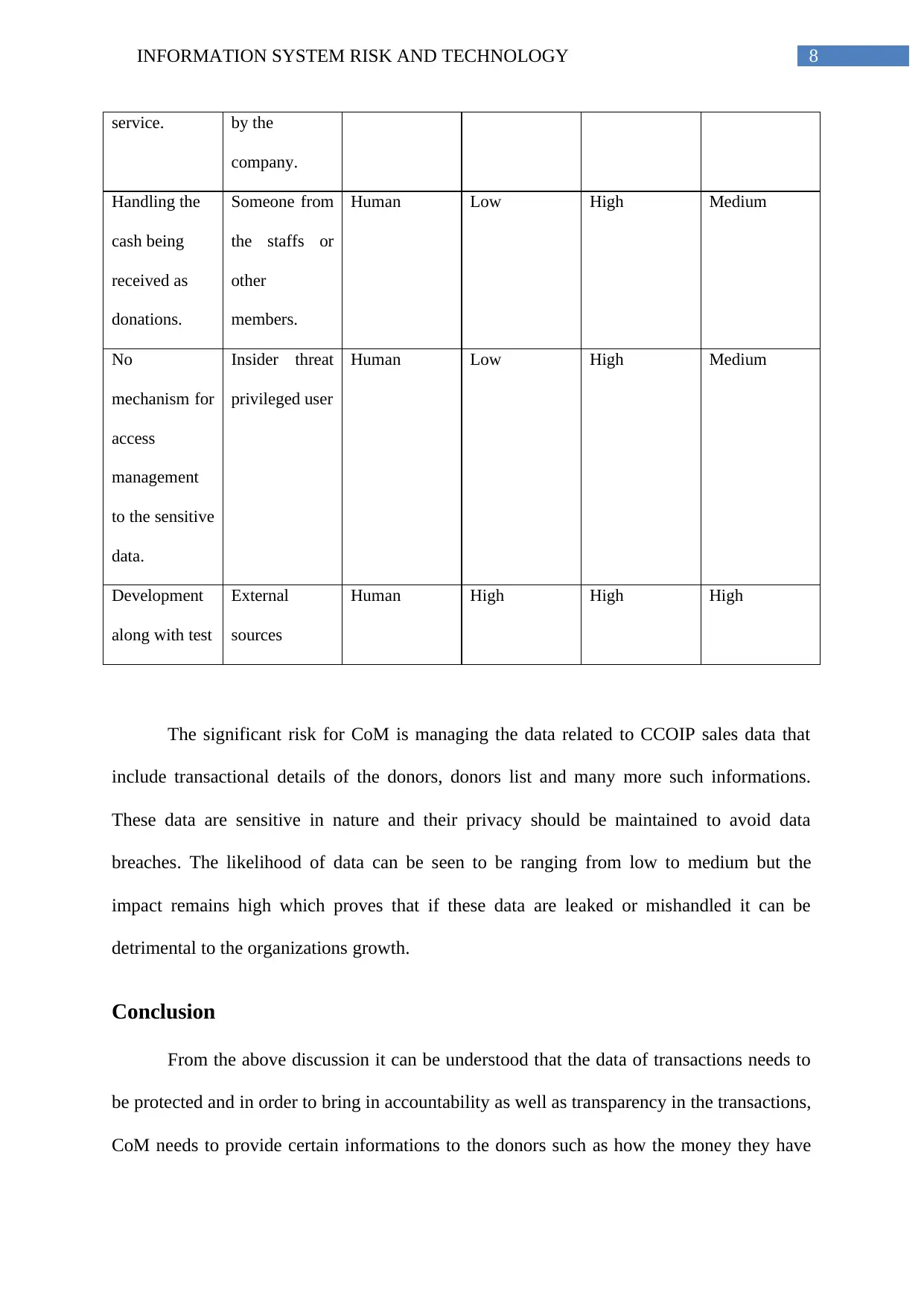
8INFORMATION SYSTEM RISK AND TECHNOLOGY
service. by the
company.
Handling the
cash being
received as
donations.
Someone from
the staffs or
other
members.
Human Low High Medium
No
mechanism for
access
management
to the sensitive
data.
Insider threat
privileged user
Human Low High Medium
Development
along with test
External
sources
Human High High High
The significant risk for CoM is managing the data related to CCOIP sales data that
include transactional details of the donors, donors list and many more such informations.
These data are sensitive in nature and their privacy should be maintained to avoid data
breaches. The likelihood of data can be seen to be ranging from low to medium but the
impact remains high which proves that if these data are leaked or mishandled it can be
detrimental to the organizations growth.
Conclusion
From the above discussion it can be understood that the data of transactions needs to
be protected and in order to bring in accountability as well as transparency in the transactions,
CoM needs to provide certain informations to the donors such as how the money they have
service. by the
company.
Handling the
cash being
received as
donations.
Someone from
the staffs or
other
members.
Human Low High Medium
No
mechanism for
access
management
to the sensitive
data.
Insider threat
privileged user
Human Low High Medium
Development
along with test
External
sources
Human High High High
The significant risk for CoM is managing the data related to CCOIP sales data that
include transactional details of the donors, donors list and many more such informations.
These data are sensitive in nature and their privacy should be maintained to avoid data
breaches. The likelihood of data can be seen to be ranging from low to medium but the
impact remains high which proves that if these data are leaked or mishandled it can be
detrimental to the organizations growth.
Conclusion
From the above discussion it can be understood that the data of transactions needs to
be protected and in order to bring in accountability as well as transparency in the transactions,
CoM needs to provide certain informations to the donors such as how the money they have

9INFORMATION SYSTEM RISK AND TECHNOLOGY
donated is supporting cause and many more. The impact of data mishandling is high and thus
in order to implement digital technology to the Melbourne City, CoM requires to protect the
data of its donors and implement proper accessibility controls to the data. The risk assessment
revealed that the main risk in the above project is handling the newly developed data centre
and thus data here play a vital role and its safety should be assured.
donated is supporting cause and many more. The impact of data mishandling is high and thus
in order to implement digital technology to the Melbourne City, CoM requires to protect the
data of its donors and implement proper accessibility controls to the data. The risk assessment
revealed that the main risk in the above project is handling the newly developed data centre
and thus data here play a vital role and its safety should be assured.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10INFORMATION SYSTEM RISK AND TECHNOLOGY
References
Hallowell, M.R., Hardison, D. and Desvignes, M., 2016. Information technology and safety:
Integrating empirical safety risk data with building information modeling, sensing, and
visualization technologies. Construction innovation, 16(3), pp.323-347.
Hoffmann, R., Kiedrowicz, M. and Stanik, J., 2016. Risk management system as the basic
paradigm of the information security management system in an organization. In MATEC Web
of Conferences (Vol. 76, p. 04010). EDP Sciences.
Marchewka, J.T., 2016. Information technology project management: Providing measurable
organizational value. John Wiley & Sons.
Pimchangthong, D. and Boonjing, V., 2017. Effects of risk management practices on IT
project success. Management and production engineering review, 8(1), pp.30-37.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Senft, S., Gallegos, F. and Davis, A., 2016. Information technology control and audit.
Auerbach publications.
Taylor, R.G., 2015. Potential problems with information security risk
assessments. Information Security Journal: A Global Perspective, 24(4-6), pp.177-184.
References
Hallowell, M.R., Hardison, D. and Desvignes, M., 2016. Information technology and safety:
Integrating empirical safety risk data with building information modeling, sensing, and
visualization technologies. Construction innovation, 16(3), pp.323-347.
Hoffmann, R., Kiedrowicz, M. and Stanik, J., 2016. Risk management system as the basic
paradigm of the information security management system in an organization. In MATEC Web
of Conferences (Vol. 76, p. 04010). EDP Sciences.
Marchewka, J.T., 2016. Information technology project management: Providing measurable
organizational value. John Wiley & Sons.
Pimchangthong, D. and Boonjing, V., 2017. Effects of risk management practices on IT
project success. Management and production engineering review, 8(1), pp.30-37.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Senft, S., Gallegos, F. and Davis, A., 2016. Information technology control and audit.
Auerbach publications.
Taylor, R.G., 2015. Potential problems with information security risk
assessments. Information Security Journal: A Global Perspective, 24(4-6), pp.177-184.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





