Information Systems Design and Development: A Comprehensive Report
VerifiedAdded on 2020/03/28
|17
|4314
|69
Report
AI Summary
This report provides a comprehensive overview of information systems design and development. It begins by outlining the functions of information systems, emphasizing their role in decision-making and business processes. The report then delves into business processes, defining them and providing examples across various sectors, followed by an examination of transaction cycles, including expenditure, conversion, and revenue cycles, and their relationships. The report also covers the mapping and documentation of information systems, detailing techniques like data flow diagrams. Furthermore, it explores the acquisition and deployment of information systems, discussing both external and internal development methods and deployment strategies. Finally, the report addresses ethical issues associated with information systems and concludes with recommendations based on the analysis.

Running head: Information systems design and development 1
Information systems design and development
Name
Affiliate institution
Information systems design and development
Name
Affiliate institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Information systems design and development 2
Table of Contents
Table of Contents.............................................................................................................................2
Introduction......................................................................................................................................3
Functions of Information system.....................................................................................................3
Business process..............................................................................................................................4
Transaction Cycles...........................................................................................................................4
Mapping information system...........................................................................................................7
Documenting Information System...................................................................................................8
Acquisition of information system..................................................................................................9
Deployment of information system...............................................................................................10
Ethical issues.................................................................................................................................12
Conclusion.....................................................................................................................................14
Recommendations..........................................................................................................................14
References......................................................................................................................................15
Table of Contents
Table of Contents.............................................................................................................................2
Introduction......................................................................................................................................3
Functions of Information system.....................................................................................................3
Business process..............................................................................................................................4
Transaction Cycles...........................................................................................................................4
Mapping information system...........................................................................................................7
Documenting Information System...................................................................................................8
Acquisition of information system..................................................................................................9
Deployment of information system...............................................................................................10
Ethical issues.................................................................................................................................12
Conclusion.....................................................................................................................................14
Recommendations..........................................................................................................................14
References......................................................................................................................................15

Running head: Information systems design and development 3
Introduction
Most organizations have refrained from managing their information and data manually. Through
information systems adoption, companies are now able to utilize comprehensive and advanced
databases that contains all required information of the organization. Information system evaluate,
update and stores all organization’s information which is later used to pinpoint current or future
problems’ solution. In addition, integration of data from various sources, outside and inside the
organization ca be enhanced through this system. As such, the company stays updated with the
external risks and opportunities and internal performance. This report outlines functions of
information systems, business processes and transaction cycle, mapping and documentation of
information system, acquisition and deployment of information system, and ethical issues related
to information system.
Functions of Information system
Some of the functions of information systems include;
Decision making- the sufficiency of strategic plan determines the success of an organization in
the long run. Information system is used by the organization management team in formulation of
strategic plans and decision making that enhance prosperity and longevity of the organization.
Information system is also used by the business in information evaluation from all sources
external references like Bloomberg and Reuters included which offer information on the overall
economy. This assessment and market trends comparison aids the company in analyzing the
quality and sufficiency of strategic plans. (Swanson, Swanson, Bowen, Phillips, Gallup, &
Lynes, 2010).
Business Processes- development of bigger number of systems that are value added in the
organization is enhanced through the use Information systems. For instance, an organization can
combine manufacturing cycle with the information systems to make sure that the results
produced matches with the needs of the several standards of quality management. Acquisition of
information systems makes business process simple and eliminates unnecessary operations.
Through information systems employees’ processes are added controls making sure that
operation of specific tasks is done only by users with applicable right. In addition, information
Introduction
Most organizations have refrained from managing their information and data manually. Through
information systems adoption, companies are now able to utilize comprehensive and advanced
databases that contains all required information of the organization. Information system evaluate,
update and stores all organization’s information which is later used to pinpoint current or future
problems’ solution. In addition, integration of data from various sources, outside and inside the
organization ca be enhanced through this system. As such, the company stays updated with the
external risks and opportunities and internal performance. This report outlines functions of
information systems, business processes and transaction cycle, mapping and documentation of
information system, acquisition and deployment of information system, and ethical issues related
to information system.
Functions of Information system
Some of the functions of information systems include;
Decision making- the sufficiency of strategic plan determines the success of an organization in
the long run. Information system is used by the organization management team in formulation of
strategic plans and decision making that enhance prosperity and longevity of the organization.
Information system is also used by the business in information evaluation from all sources
external references like Bloomberg and Reuters included which offer information on the overall
economy. This assessment and market trends comparison aids the company in analyzing the
quality and sufficiency of strategic plans. (Swanson, Swanson, Bowen, Phillips, Gallup, &
Lynes, 2010).
Business Processes- development of bigger number of systems that are value added in the
organization is enhanced through the use Information systems. For instance, an organization can
combine manufacturing cycle with the information systems to make sure that the results
produced matches with the needs of the several standards of quality management. Acquisition of
information systems makes business process simple and eliminates unnecessary operations.
Through information systems employees’ processes are added controls making sure that
operation of specific tasks is done only by users with applicable right. In addition, information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Information systems design and development 4
systems increase accuracy and removes tasks that are repetitive permitting employees to focus on
functions that are of high level. Implementation and better project planning through efficient
management is enhanced through the use of information system. (Gelinas, & Dull, 2010)
Business process
A business process is a sequence of steps carried out by stakeholders’ group to obtain a concrete
objective. Multiple users repeat these steps severally in an optimized and standardized way. A
business process can either be automatic or manual. When processes are done manually, there is
no use of assisting technology. Automatic processes on the other hand is when technology is
used to help users in implementing operations in a standardized and accurate manner. A business
process is seen as a flowchart of logical steps. This method is formalized by (BPM). (Draheim,
2010).
The following are some types of business process;
Manufacturing – this is a corrective maintenance, product assembly, and a quality assurance
process.
Finance – this is a risk management, invoicing, and a billing process.
Health – this is a medical evaluation and drug approval process
Banking –this is a client on-boarding and credit check process.
Travel – this is a trip booking, and agent billing process
Defense – this is a situation room and emergency management process
HR – this is a vacation request, leavers and starters process
Public Sector – this is a process that deals with government service application
Compliance – this is a safety audit, and a legal check process
Transaction Cycles
The following are some the transactions cycle that exist in all kinds of businesses: the conversion
cycle, the expenditure cycle, and the revenue cycle. These cycles are present in both profit and
systems increase accuracy and removes tasks that are repetitive permitting employees to focus on
functions that are of high level. Implementation and better project planning through efficient
management is enhanced through the use of information system. (Gelinas, & Dull, 2010)
Business process
A business process is a sequence of steps carried out by stakeholders’ group to obtain a concrete
objective. Multiple users repeat these steps severally in an optimized and standardized way. A
business process can either be automatic or manual. When processes are done manually, there is
no use of assisting technology. Automatic processes on the other hand is when technology is
used to help users in implementing operations in a standardized and accurate manner. A business
process is seen as a flowchart of logical steps. This method is formalized by (BPM). (Draheim,
2010).
The following are some types of business process;
Manufacturing – this is a corrective maintenance, product assembly, and a quality assurance
process.
Finance – this is a risk management, invoicing, and a billing process.
Health – this is a medical evaluation and drug approval process
Banking –this is a client on-boarding and credit check process.
Travel – this is a trip booking, and agent billing process
Defense – this is a situation room and emergency management process
HR – this is a vacation request, leavers and starters process
Public Sector – this is a process that deals with government service application
Compliance – this is a safety audit, and a legal check process
Transaction Cycles
The following are some the transactions cycle that exist in all kinds of businesses: the conversion
cycle, the expenditure cycle, and the revenue cycle. These cycles are present in both profit and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: Information systems design and development 5
non-profit organizations. For example, every organization is subjected to expenditures for the
sake
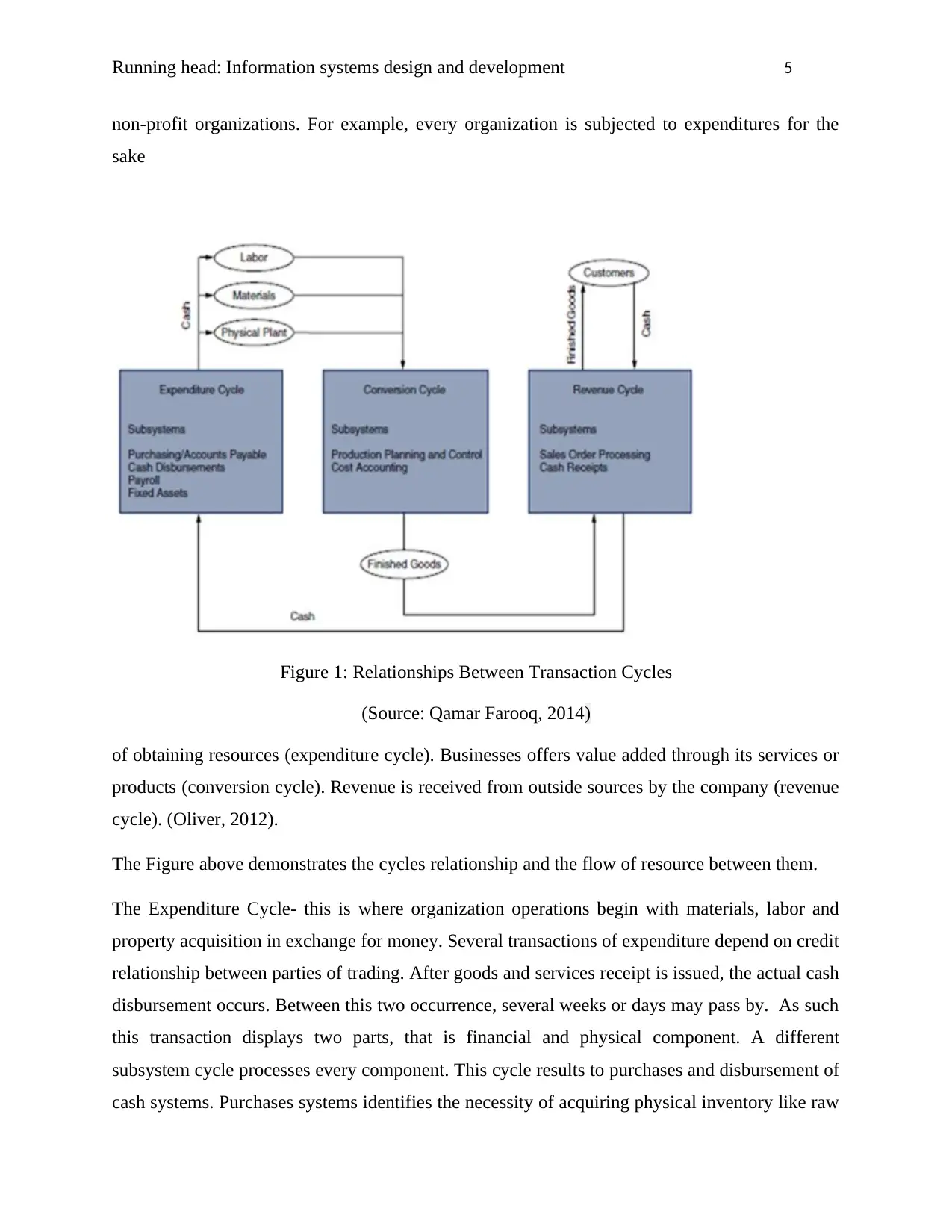
Figure 1: Relationships Between Transaction Cycles
(Source: Qamar Farooq, 2014)
of obtaining resources (expenditure cycle). Businesses offers value added through its services or
products (conversion cycle). Revenue is received from outside sources by the company (revenue
cycle). (Oliver, 2012).
The Figure above demonstrates the cycles relationship and the flow of resource between them.
The Expenditure Cycle- this is where organization operations begin with materials, labor and
property acquisition in exchange for money. Several transactions of expenditure depend on credit
relationship between parties of trading. After goods and services receipt is issued, the actual cash
disbursement occurs. Between this two occurrence, several weeks or days may pass by. As such
this transaction displays two parts, that is financial and physical component. A different
subsystem cycle processes every component. This cycle results to purchases and disbursement of
cash systems. Purchases systems identifies the necessity of acquiring physical inventory like raw
non-profit organizations. For example, every organization is subjected to expenditures for the
sake
Figure 1: Relationships Between Transaction Cycles
(Source: Qamar Farooq, 2014)
of obtaining resources (expenditure cycle). Businesses offers value added through its services or
products (conversion cycle). Revenue is received from outside sources by the company (revenue
cycle). (Oliver, 2012).
The Figure above demonstrates the cycles relationship and the flow of resource between them.
The Expenditure Cycle- this is where organization operations begin with materials, labor and
property acquisition in exchange for money. Several transactions of expenditure depend on credit
relationship between parties of trading. After goods and services receipt is issued, the actual cash
disbursement occurs. Between this two occurrence, several weeks or days may pass by. As such
this transaction displays two parts, that is financial and physical component. A different
subsystem cycle processes every component. This cycle results to purchases and disbursement of
cash systems. Purchases systems identifies the necessity of acquiring physical inventory like raw

Running head: Information systems design and development 6
materials and does placement of an order with the supplier. Purchase systems write down the
event when the goods are obtained by establishing purchases and increasing inventory to be
accounted for at a later date. (Kartseva, 2008).
Cash disbursements system distributes the funds and perform transactions recording after the
responsibility generated by purchase system is ready. Cash distribution system authorizes
payment by minimizing cash and purchases accounts.
Collection of data of labor usage, computation of the payroll and payment disbursements to the
employees is done by payroll system. Payroll is a unique case cash disbursement and purchase
system. Most organizations possess a different payroll processing system due to existence of
accounting complexities. (Gupta, 2011).
Acquisition, disposal and maintenance transactions of fixed assets are processed by fixed asset
system. This items are permanent and represent largest financial investment of an organization.
Examples of these assets include; motor vehicles, land, machinery, buildings, and furniture.
The Conversion Cycle- cost accounting and production system are the two major subsystem in
conversion cycle. Production systems consist of control, planning and scheduling physical goods
through the process of manufacturing. This involves determining the requirements of raw
materials, authorizing performance of activities, releasing raw materials into production, and
instructing on the work-in-process direction through various manufacturing stages. The cost
accounting systems on the other hand manages cost information flows associated to production.
Information produced by this system helps in performance reporting, inventory valuation, cost
control, budgeting and management decisions like buy or make decisions. (Goyal, 2014)
Formal conversion cycle helps manufacturing organizations in converting raw materials into
finished goods. Although this cycle is not formal, service observant and establishments in retails,
organizations still engage in its operations that enhance culmination of salable goods and service
development. These operations include; products and services readying and resources allocation
like prepaid expenses, depreciation and building amortization to the appropriate accounting time.
Merchandizing organizations however, do not use subsystem of conversion cycle to process their
operations. (Weske, 2012).
materials and does placement of an order with the supplier. Purchase systems write down the
event when the goods are obtained by establishing purchases and increasing inventory to be
accounted for at a later date. (Kartseva, 2008).
Cash disbursements system distributes the funds and perform transactions recording after the
responsibility generated by purchase system is ready. Cash distribution system authorizes
payment by minimizing cash and purchases accounts.
Collection of data of labor usage, computation of the payroll and payment disbursements to the
employees is done by payroll system. Payroll is a unique case cash disbursement and purchase
system. Most organizations possess a different payroll processing system due to existence of
accounting complexities. (Gupta, 2011).
Acquisition, disposal and maintenance transactions of fixed assets are processed by fixed asset
system. This items are permanent and represent largest financial investment of an organization.
Examples of these assets include; motor vehicles, land, machinery, buildings, and furniture.
The Conversion Cycle- cost accounting and production system are the two major subsystem in
conversion cycle. Production systems consist of control, planning and scheduling physical goods
through the process of manufacturing. This involves determining the requirements of raw
materials, authorizing performance of activities, releasing raw materials into production, and
instructing on the work-in-process direction through various manufacturing stages. The cost
accounting systems on the other hand manages cost information flows associated to production.
Information produced by this system helps in performance reporting, inventory valuation, cost
control, budgeting and management decisions like buy or make decisions. (Goyal, 2014)
Formal conversion cycle helps manufacturing organizations in converting raw materials into
finished goods. Although this cycle is not formal, service observant and establishments in retails,
organizations still engage in its operations that enhance culmination of salable goods and service
development. These operations include; products and services readying and resources allocation
like prepaid expenses, depreciation and building amortization to the appropriate accounting time.
Merchandizing organizations however, do not use subsystem of conversion cycle to process their
operations. (Weske, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Information systems design and development 7
The Revenue Cycle- this cycle helps organizations sell their finished products to clients. It
involves receipt, cash and credit sales processing. Sales order and cash receipts processing are
the physical and financial component of transactions of revenue cycle that are separately
processed.
Sales order processing- most sales of business are created on credit and consist of duties like
transaction recording in the accounts, preparing orders of sales, billing customers, granting
credit, and products shipping to the client.
Cash receipts- days and weeks passes between sale and cash receipt point. Processing of cash
receipts include; cash collection, cash depositing in the bank, and writing down these
occurrences in the accounts. (Harmon, 2007).
Mapping information system
Decision support system- decision making is enhanced through working and evaluating data that
can create data techniques and projection of statistics. This system does not replace judgement of
the manager, instead it supports it while enhancing quality improvement of his or her decision.
Transaction processing systems- these systems offers a way of collection, processing, storage,
modification displays or transaction cancellation. Multiple transaction in these systems occurs
simultaneously. Data collected is kept in the databases which is later used in production of
reports like check registers, billings, schedules, wages, manufacturing, inventory and summaries.
(Sample, & Ioup, 2010)
Information systems in organization-these systems involves collection, storage and processing of
data that gives the usefulness and accuracy of the information to the organization. Information
systems involves information gathering from machines and individuals that receive data, enhance
its processing, output it and then store. It also involves networks that sent and collect data and
the processes that controls how data is managed. (Waldron, 2014)
Management information systems-these system utilizes the data received from transaction
processing systems and generate reports used in making business decisions by managers to solve
problems. Some of the reports created by these information systems include; ad hoc, summary
and exception reports. This help to increase the effectiveness of managerial operations.
The Revenue Cycle- this cycle helps organizations sell their finished products to clients. It
involves receipt, cash and credit sales processing. Sales order and cash receipts processing are
the physical and financial component of transactions of revenue cycle that are separately
processed.
Sales order processing- most sales of business are created on credit and consist of duties like
transaction recording in the accounts, preparing orders of sales, billing customers, granting
credit, and products shipping to the client.
Cash receipts- days and weeks passes between sale and cash receipt point. Processing of cash
receipts include; cash collection, cash depositing in the bank, and writing down these
occurrences in the accounts. (Harmon, 2007).
Mapping information system
Decision support system- decision making is enhanced through working and evaluating data that
can create data techniques and projection of statistics. This system does not replace judgement of
the manager, instead it supports it while enhancing quality improvement of his or her decision.
Transaction processing systems- these systems offers a way of collection, processing, storage,
modification displays or transaction cancellation. Multiple transaction in these systems occurs
simultaneously. Data collected is kept in the databases which is later used in production of
reports like check registers, billings, schedules, wages, manufacturing, inventory and summaries.
(Sample, & Ioup, 2010)
Information systems in organization-these systems involves collection, storage and processing of
data that gives the usefulness and accuracy of the information to the organization. Information
systems involves information gathering from machines and individuals that receive data, enhance
its processing, output it and then store. It also involves networks that sent and collect data and
the processes that controls how data is managed. (Waldron, 2014)
Management information systems-these system utilizes the data received from transaction
processing systems and generate reports used in making business decisions by managers to solve
problems. Some of the reports created by these information systems include; ad hoc, summary
and exception reports. This help to increase the effectiveness of managerial operations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Information systems design and development 8
Neutral networks and expert systems- an expert system also referred to as knowledge-based
system is a system of a computer that is structured to evaluate data and generate
recommendations, controlled decisions and diagnosis. A neutral system on the other hand, uses
computers to nurture information processing, learning and remembrance through a human being
brains. (In Brocke, & In Rosemann, 2014).
Documenting Information System
The goal of documenting information system is to help users to analyze, understand, explain and
improve internal controls, business processes and information systems that are complex. It also
helps in personnel training. (Information Resources Management Association, 2011).
Data flow diagram – this is a system graphical representation. It shows components of a system;
flow of data among the components; and the data sources, storage and destinations.
Data flow Diagram Symbols- the following are some diagram that shows data flow;
Bubble symbol – this shows an entity within which flows of data that is incoming are completely
changed into outgoing flows of data.
Data flow symbol – represents a data pathway.
external entity symbol- –it shows data destination or source outside the system.
Neutral networks and expert systems- an expert system also referred to as knowledge-based
system is a system of a computer that is structured to evaluate data and generate
recommendations, controlled decisions and diagnosis. A neutral system on the other hand, uses
computers to nurture information processing, learning and remembrance through a human being
brains. (In Brocke, & In Rosemann, 2014).
Documenting Information System
The goal of documenting information system is to help users to analyze, understand, explain and
improve internal controls, business processes and information systems that are complex. It also
helps in personnel training. (Information Resources Management Association, 2011).
Data flow diagram – this is a system graphical representation. It shows components of a system;
flow of data among the components; and the data sources, storage and destinations.
Data flow Diagram Symbols- the following are some diagram that shows data flow;
Bubble symbol – this shows an entity within which flows of data that is incoming are completely
changed into outgoing flows of data.
Data flow symbol – represents a data pathway.
external entity symbol- –it shows data destination or source outside the system.

Running head: Information systems design and development 9
Data store symbol – represents the location of data storage.
Acquisition of information system
External Sources- organizations may decide to obtain a system buying a proprietary package
from a supplier under a license and have the system personalized either internally or externally
by the suppliers or any other outsider contractor. Enterprise system are normally bought in this
way. Another option is to redistribute application of an open source which has a free program
code and is open for modification under distinct kinds of license that forces application openness
in perpetuity. In general, usage cost of software of the open source involves technical support
from unique suppliers. (Camenisch, Fischer-Hübner, Murayama, Portmann, & Rieder, 2011).
Internal information systems development- life cycle or rapid application development is used
by a company to develop information system internally. Same techniques are used by vendors of
the system which requires to offer customized and more general system. Systems of large
organization like enterprise systems are normally created and controlled through a process that is
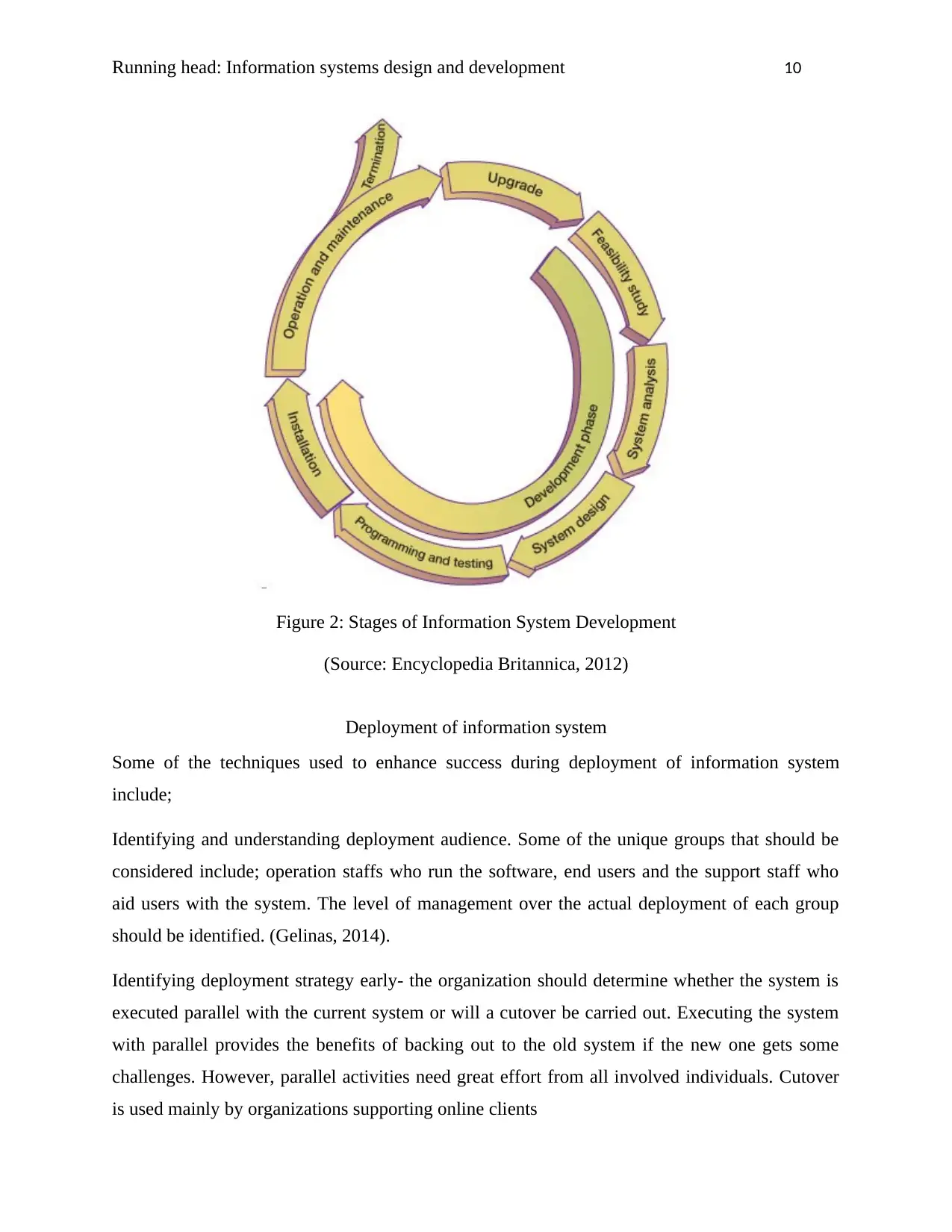
systematic referred to as system life cycle. This system involves six stages; system design,
feasibility study, programming and testing, installation, system analysis, and operation and
maintenance. The five stages that is feasibility study, system design, installation, system analysis
and programming and testing are used in system development and the last stage which is
operation and maintenance is the exploitation of the long term. In regard to the usage period,
information system may be upgraded or phased out. A system enters another life cycle
development in case there is need of a major upgrade. The diagram below shows the six stages;
Data store symbol – represents the location of data storage.
Acquisition of information system
External Sources- organizations may decide to obtain a system buying a proprietary package
from a supplier under a license and have the system personalized either internally or externally
by the suppliers or any other outsider contractor. Enterprise system are normally bought in this
way. Another option is to redistribute application of an open source which has a free program
code and is open for modification under distinct kinds of license that forces application openness
in perpetuity. In general, usage cost of software of the open source involves technical support
from unique suppliers. (Camenisch, Fischer-Hübner, Murayama, Portmann, & Rieder, 2011).
Internal information systems development- life cycle or rapid application development is used
by a company to develop information system internally. Same techniques are used by vendors of
the system which requires to offer customized and more general system. Systems of large
organization like enterprise systems are normally created and controlled through a process that is
systematic referred to as system life cycle. This system involves six stages; system design,
feasibility study, programming and testing, installation, system analysis, and operation and
maintenance. The five stages that is feasibility study, system design, installation, system analysis
and programming and testing are used in system development and the last stage which is
operation and maintenance is the exploitation of the long term. In regard to the usage period,
information system may be upgraded or phased out. A system enters another life cycle
development in case there is need of a major upgrade. The diagram below shows the six stages;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: Information systems design and development 10
Figure 2: Stages of Information System Development
(Source: Encyclopedia Britannica, 2012)
Deployment of information system
Some of the techniques used to enhance success during deployment of information system
include;
Identifying and understanding deployment audience. Some of the unique groups that should be
considered include; operation staffs who run the software, end users and the support staff who
aid users with the system. The level of management over the actual deployment of each group
should be identified. (Gelinas, 2014).
Identifying deployment strategy early- the organization should determine whether the system is
executed parallel with the current system or will a cutover be carried out. Executing the system
with parallel provides the benefits of backing out to the old system if the new one gets some
challenges. However, parallel activities need great effort from all involved individuals. Cutover
is used mainly by organizations supporting online clients
Figure 2: Stages of Information System Development
(Source: Encyclopedia Britannica, 2012)
Deployment of information system
Some of the techniques used to enhance success during deployment of information system
include;
Identifying and understanding deployment audience. Some of the unique groups that should be
considered include; operation staffs who run the software, end users and the support staff who
aid users with the system. The level of management over the actual deployment of each group
should be identified. (Gelinas, 2014).
Identifying deployment strategy early- the organization should determine whether the system is
executed parallel with the current system or will a cutover be carried out. Executing the system
with parallel provides the benefits of backing out to the old system if the new one gets some
challenges. However, parallel activities need great effort from all involved individuals. Cutover
is used mainly by organizations supporting online clients
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: Information systems design and development 11
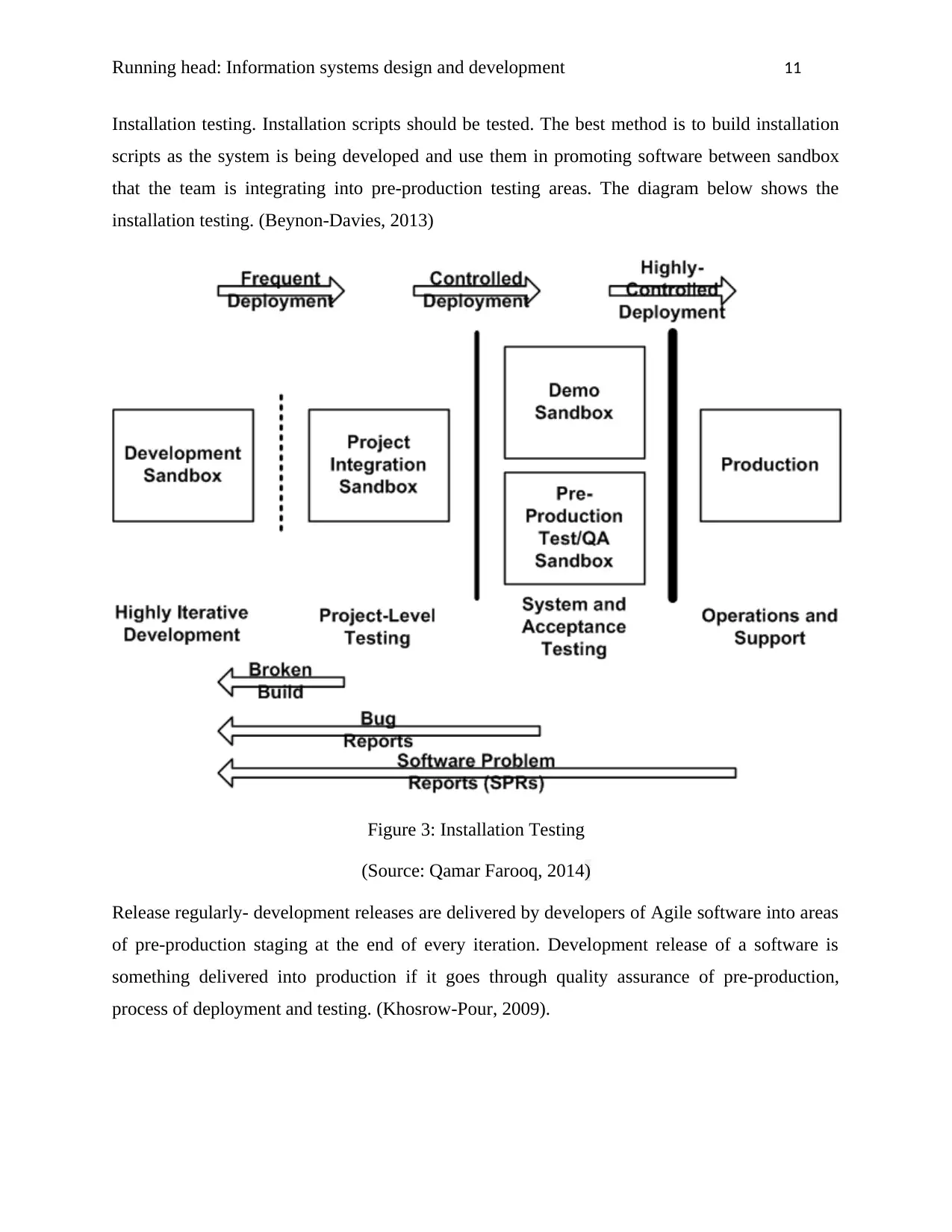
Installation testing. Installation scripts should be tested. The best method is to build installation
scripts as the system is being developed and use them in promoting software between sandbox
that the team is integrating into pre-production testing areas. The diagram below shows the
installation testing. (Beynon-Davies, 2013)
Figure 3: Installation Testing
(Source: Qamar Farooq, 2014)
Release regularly- development releases are delivered by developers of Agile software into areas
of pre-production staging at the end of every iteration. Development release of a software is
something delivered into production if it goes through quality assurance of pre-production,
process of deployment and testing. (Khosrow-Pour, 2009).
Installation testing. Installation scripts should be tested. The best method is to build installation
scripts as the system is being developed and use them in promoting software between sandbox
that the team is integrating into pre-production testing areas. The diagram below shows the
installation testing. (Beynon-Davies, 2013)
Figure 3: Installation Testing
(Source: Qamar Farooq, 2014)
Release regularly- development releases are delivered by developers of Agile software into areas
of pre-production staging at the end of every iteration. Development release of a software is
something delivered into production if it goes through quality assurance of pre-production,
process of deployment and testing. (Khosrow-Pour, 2009).

Running head: Information systems design and development 12
Start planning early. In order to be successful planning early is required as deployment process
can be complex, especially when there is a variety of configurations in the system or if the user is
physically distributed.
Acknowledge deployment is harder than it seems- several operations should be considered
before system is deployed into production. Planning of an agile strategy should be enhanced.
Plans should be kept at high level first targeting on the main dependencies. (National Research
Council, 2010).
Reduce efforts of pre-production testing safely with time - amount of time taken in pre-
production testing efforts can be minimized by agility, thus increasing the speed of deployment.
Agility offers artifacts of high quality and consists of suite of regression test to show that the
system is functioning well.
Deployment is easier if software are Well-tested – organization must perform even if it is a
difficult and complex endeavor. Testing should be done early and more often.
reflection of organizational culture through planning- the organization should determine the
individuals whom the system is deployed to, their daily roles and policies, willingness to tolerate
the amount of change to be enhanced, and the impact of the system once deployed. (Wiley,
2017).
Ethical issues
EB ay, google and Facebook are among the businesses that have become successful through the
use of information systems. However, inappropriate use of information system can generate
issues for the employees and companies. Loss of finances to individuals or financial institute can
occur due access gained by criminals to information of the credit card. Lawsuits and business
loss can occur if individuals post improper details on twitter or Facebook using organizations’
account. (Schweiger, 2011).
Cyber-crime- this is committing crimes using information systems. Cyber can start simply with
annoying users of computer, then progress to losses of huge finances, and maybe cause loss of
life. Some of things that have led to cyber-crime growth are smartphones and other high-end
mobile machines growth. Types of cyber-crimes include;
Start planning early. In order to be successful planning early is required as deployment process
can be complex, especially when there is a variety of configurations in the system or if the user is
physically distributed.
Acknowledge deployment is harder than it seems- several operations should be considered
before system is deployed into production. Planning of an agile strategy should be enhanced.
Plans should be kept at high level first targeting on the main dependencies. (National Research
Council, 2010).
Reduce efforts of pre-production testing safely with time - amount of time taken in pre-
production testing efforts can be minimized by agility, thus increasing the speed of deployment.
Agility offers artifacts of high quality and consists of suite of regression test to show that the
system is functioning well.
Deployment is easier if software are Well-tested – organization must perform even if it is a
difficult and complex endeavor. Testing should be done early and more often.
reflection of organizational culture through planning- the organization should determine the
individuals whom the system is deployed to, their daily roles and policies, willingness to tolerate
the amount of change to be enhanced, and the impact of the system once deployed. (Wiley,
2017).
Ethical issues
EB ay, google and Facebook are among the businesses that have become successful through the
use of information systems. However, inappropriate use of information system can generate
issues for the employees and companies. Loss of finances to individuals or financial institute can
occur due access gained by criminals to information of the credit card. Lawsuits and business
loss can occur if individuals post improper details on twitter or Facebook using organizations’
account. (Schweiger, 2011).
Cyber-crime- this is committing crimes using information systems. Cyber can start simply with
annoying users of computer, then progress to losses of huge finances, and maybe cause loss of
life. Some of things that have led to cyber-crime growth are smartphones and other high-end
mobile machines growth. Types of cyber-crimes include;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





