BCO3447 Project: Visitor Management System Design and Implementation
VerifiedAdded on 2022/11/01
|15
|3652
|200
Project
AI Summary
This project report details the design and implementation of a Visitor Management System (VMS) for a building, addressing the limitations of a manual system. The project encompasses IS requirement specifications, including an introduction, purpose, and scope. The report includes a comprehensive business scenario, use case diagrams, data flow diagrams (DFDs) at different levels, and sequence diagrams for login and password recovery processes. It also covers system implementation aspects, such as service-oriented architecture (SOA) and cloud delivery. The project management section outlines planning, approach (Agile framework), and a risk register. The managerial reports section discusses sales and budget reports. The project aims to improve building security, streamline visitor check-in/check-out processes, and enhance overall efficiency through a digital visitor management system. The project also includes a project brief which summarizes the requirements and deliverables of the project. The implementation of this system includes a business process modeling, use case diagrams, data flow diagrams, sequence diagrams, and managerial reports, along with the use of cloud delivery and SOA.

Information Systems Project (BCO3447)
Visitor Management System
Submitted by: Nisha Rani (s4598210)
Anup Lamichhane (s4574625)
Nima Tshering Lama (s4575795)
Submitted to: Mr. Mehdi Nikibin
Visitor Management System
Submitted by: Nisha Rani (s4598210)
Anup Lamichhane (s4574625)
Nima Tshering Lama (s4575795)
Submitted to: Mr. Mehdi Nikibin
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Visitor management system
Table of Contents
1.0 IS requirement specification...................................................................................................................................................................................2
1.1 Introduction........................................................................................................................................................................................................2
1.2 Purpose...............................................................................................................................................................................................................2
1.3 Scope..................................................................................................................................................................................................................2
1.4 Existing manual system......................................................................................................................................................................................2
1.5 Project management...........................................................................................................................................................................................2
1.5.1 Planning.......................................................................................................................................................................................................2
1.5.2 Approach.....................................................................................................................................................................................................2
1.5.3Project Risk Register........................................................................................................................................................................................2
2.0 Information system design.....................................................................................................................................................................................3
2.1 Business Process Modelling...................................................................................................................................................................................3
2.2 Use Case:................................................................................................................................................................................................................3
2.2.1 Visitor Management System:..........................................................................................................................................................................3
2.2.2. Admin Process:..............................................................................................................................................................................................4
2.2.3 Report generation............................................................................................................................................................................................5
2.2.4 Visitor login system........................................................................................................................................................................................6
2.2 Data Flow Diagram:...............................................................................................................................................................................................7
2.2.2. Level 0 DFD of Visitor management system.................................................................................................................................................8
2.2.3. Level 1 DFD of Visitor management system (Visitor)..................................................................................................................................8
2.2.3. Level 1 DFD of Visitor management system (Admin)..................................................................................................................................9
2.3 Sequence diagram..............................................................................................................................................................................................9
2.3.1 Sequence page for login..............................................................................................................................................................................9
2.3.2 Sequence page for forgot password............................................................................................................................................................9
2.6 Managerial Reports..........................................................................................................................................................................................10
2.6.1 Sales Reports.................................................................................................................................................................................................10
2.6.2 Budget Report...............................................................................................................................................................................................10
3.0 System Implementation........................................................................................................................................................................................10
3.1 Service and SOA..............................................................................................................................................................................................10
3.2Use of Cloud Delivery and Platform.................................................................................................................................................................12
4.0 Result Analysis and Conclusion:..........................................................................................................................................................................13
User document........................................................................................................................................................................................................13
Reference....................................................................................................................................................................................................................14
Table of Contents
1.0 IS requirement specification...................................................................................................................................................................................2
1.1 Introduction........................................................................................................................................................................................................2
1.2 Purpose...............................................................................................................................................................................................................2
1.3 Scope..................................................................................................................................................................................................................2
1.4 Existing manual system......................................................................................................................................................................................2
1.5 Project management...........................................................................................................................................................................................2
1.5.1 Planning.......................................................................................................................................................................................................2
1.5.2 Approach.....................................................................................................................................................................................................2
1.5.3Project Risk Register........................................................................................................................................................................................2
2.0 Information system design.....................................................................................................................................................................................3
2.1 Business Process Modelling...................................................................................................................................................................................3
2.2 Use Case:................................................................................................................................................................................................................3
2.2.1 Visitor Management System:..........................................................................................................................................................................3
2.2.2. Admin Process:..............................................................................................................................................................................................4
2.2.3 Report generation............................................................................................................................................................................................5
2.2.4 Visitor login system........................................................................................................................................................................................6
2.2 Data Flow Diagram:...............................................................................................................................................................................................7
2.2.2. Level 0 DFD of Visitor management system.................................................................................................................................................8
2.2.3. Level 1 DFD of Visitor management system (Visitor)..................................................................................................................................8
2.2.3. Level 1 DFD of Visitor management system (Admin)..................................................................................................................................9
2.3 Sequence diagram..............................................................................................................................................................................................9
2.3.1 Sequence page for login..............................................................................................................................................................................9
2.3.2 Sequence page for forgot password............................................................................................................................................................9
2.6 Managerial Reports..........................................................................................................................................................................................10
2.6.1 Sales Reports.................................................................................................................................................................................................10
2.6.2 Budget Report...............................................................................................................................................................................................10
3.0 System Implementation........................................................................................................................................................................................10
3.1 Service and SOA..............................................................................................................................................................................................10
3.2Use of Cloud Delivery and Platform.................................................................................................................................................................12
4.0 Result Analysis and Conclusion:..........................................................................................................................................................................13
User document........................................................................................................................................................................................................13
Reference....................................................................................................................................................................................................................14
1.0 IS requirement specification
1.1 Introduction
In recent times the building security and also the better knowledge about the visitor has become essential for the owner business of the building
and also the client organisations this premium building needs to serve the premium quality service (Pohl, 2010). In this process the fast and
effective visitor information system management is a requirement. The old legacy system is done through human interventions and manual
recording processes. This system increased the cost and was also inefficient. Considering this new system has been envisioned to solve that
problem.
1.2 Purpose
This IS project has been designed to develop a system which would be paper less, less human intervention intensive, fast working and reporting
process driven, more secure (Crawford, 2014). This system would make the total manual process digital and the IT hardware and Application
based system development would help in faster recording of the visitor’s in and out of the business, and the overall tracking of the visitors.
1.3 Scope
This project would be limited to the building sign in and sign out data recording process. Thus now other personal information of the visitors
would be recorded unless the visitor is not regular (Pohl, 2010). The system development would be done through the application of the digital
data base management and recording process.
1.4 Existing manual system
In the existing system the visitors comes to the visitors receptions centre of the building there they develop their identity card through the manual
paper work process and they are permitted entry to the building using that entry card. For the regular visitors this system is developed and a card
is issued. The staffs in this reception would record the sign in and sign out information for the individual regular visitors (Williams, 2013). This
information then is processes through the manual mode to develop a report for the client businesses in the building. The reports are shared
through the printed format and the data is also stored through the similar printed paper mode.
1.5 Project management
1.5.1 Planning
The MS project application based project planning is done. The project would start on 15/10/2019 and would be completed within the 6 month
time period. A proper aims, objective, scope and stakeholder communication plan has been developed for this project. the proper project budget,
project roles and responsibility management are also done. Detailed project work monitoring and control plan has also been developed for this
project.
1.5.2 Approach
In this project development and management process the Agile framework has been used for the best outcome. This methodology of project
planning and execution would be important to continuously include the client suggestions during the development and also developing a
technically soured project (Williams, 2013). The sprint and iteration process has been used for this process. The project monitoring and control
process is using the daily meeting process for 30min and final change and work is also discussed in this meeting.
1.5.3Project Risk Register
The aspect of risk management is extremely critical for ensuring the timely and successful implementation of the project and this could be
undertaken through the creation of a risk register. The project risk register would provide a detailed understanding about the various risk factors
which could be encountered during the project implementation phase and this would eventually make the project management and project
implementation team better equipped to tackle and mitigate any risks before they actualise arise in the project (Budzier, 2011).
The risk register has identified five main critical risk factors associated with this project and these are – technical error, over budget, security
attack, systems failure and schedule overrun. These risks are categorised into three sections based on their overall levels of criticality and these
are high, medium and low. The systems failure is the most critical risk factor in this project and so it falls under the category of high risk. The
1.1 Introduction
In recent times the building security and also the better knowledge about the visitor has become essential for the owner business of the building
and also the client organisations this premium building needs to serve the premium quality service (Pohl, 2010). In this process the fast and
effective visitor information system management is a requirement. The old legacy system is done through human interventions and manual
recording processes. This system increased the cost and was also inefficient. Considering this new system has been envisioned to solve that
problem.
1.2 Purpose
This IS project has been designed to develop a system which would be paper less, less human intervention intensive, fast working and reporting
process driven, more secure (Crawford, 2014). This system would make the total manual process digital and the IT hardware and Application
based system development would help in faster recording of the visitor’s in and out of the business, and the overall tracking of the visitors.
1.3 Scope
This project would be limited to the building sign in and sign out data recording process. Thus now other personal information of the visitors
would be recorded unless the visitor is not regular (Pohl, 2010). The system development would be done through the application of the digital
data base management and recording process.
1.4 Existing manual system
In the existing system the visitors comes to the visitors receptions centre of the building there they develop their identity card through the manual
paper work process and they are permitted entry to the building using that entry card. For the regular visitors this system is developed and a card
is issued. The staffs in this reception would record the sign in and sign out information for the individual regular visitors (Williams, 2013). This
information then is processes through the manual mode to develop a report for the client businesses in the building. The reports are shared
through the printed format and the data is also stored through the similar printed paper mode.
1.5 Project management
1.5.1 Planning
The MS project application based project planning is done. The project would start on 15/10/2019 and would be completed within the 6 month
time period. A proper aims, objective, scope and stakeholder communication plan has been developed for this project. the proper project budget,
project roles and responsibility management are also done. Detailed project work monitoring and control plan has also been developed for this
project.
1.5.2 Approach
In this project development and management process the Agile framework has been used for the best outcome. This methodology of project
planning and execution would be important to continuously include the client suggestions during the development and also developing a
technically soured project (Williams, 2013). The sprint and iteration process has been used for this process. The project monitoring and control
process is using the daily meeting process for 30min and final change and work is also discussed in this meeting.
1.5.3Project Risk Register
The aspect of risk management is extremely critical for ensuring the timely and successful implementation of the project and this could be
undertaken through the creation of a risk register. The project risk register would provide a detailed understanding about the various risk factors
which could be encountered during the project implementation phase and this would eventually make the project management and project
implementation team better equipped to tackle and mitigate any risks before they actualise arise in the project (Budzier, 2011).
The risk register has identified five main critical risk factors associated with this project and these are – technical error, over budget, security
attack, systems failure and schedule overrun. These risks are categorised into three sections based on their overall levels of criticality and these
are high, medium and low. The systems failure is the most critical risk factor in this project and so it falls under the category of high risk. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
technical error and security attack falls under the category of moderate risks. The Schedule overrun and over budget falls under the category of
low risks that have little impact on the organisation.
2.0 Information system design
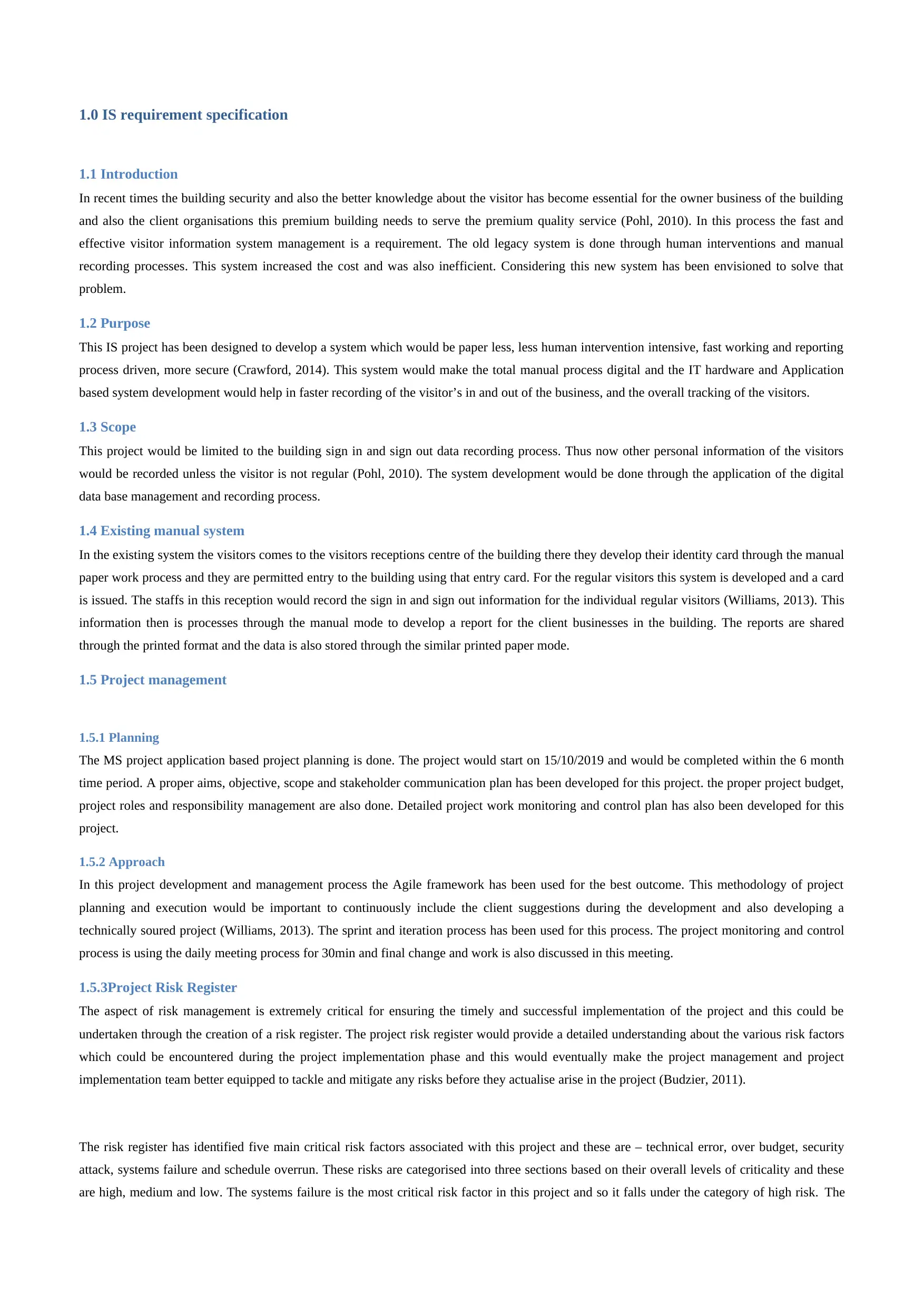
2.1 Business Process Modelling
In this process, the visitor walks inside the building and describe their purpose of visit to one of the receptionist. The receptionist will ask for
their photo ID and checks the history of the visitor. If the visitor is a regular visitor or contractors, she will allow them to sign in from the kiosk
where they need to sign themselves in with the help of their unique login ID. Whereas the new visitors will have to create an account in the
system by providing their detail along with the photo. After creating their account, the system will provide them a temporary login ID that they
use to sign in to enter the building. The system will also verify the login ID side-by-side allowing people with verified login ID to enter inside
the building while the ID that are expired or forgotten will have to check with the reception and create a new login ID. Once the visitor enter the
building the building management team will be notified and have a record who are inside the building. The visitors will visit their respective
office to complete their work and once they are done with the meeting they will have to go sign out from the system.
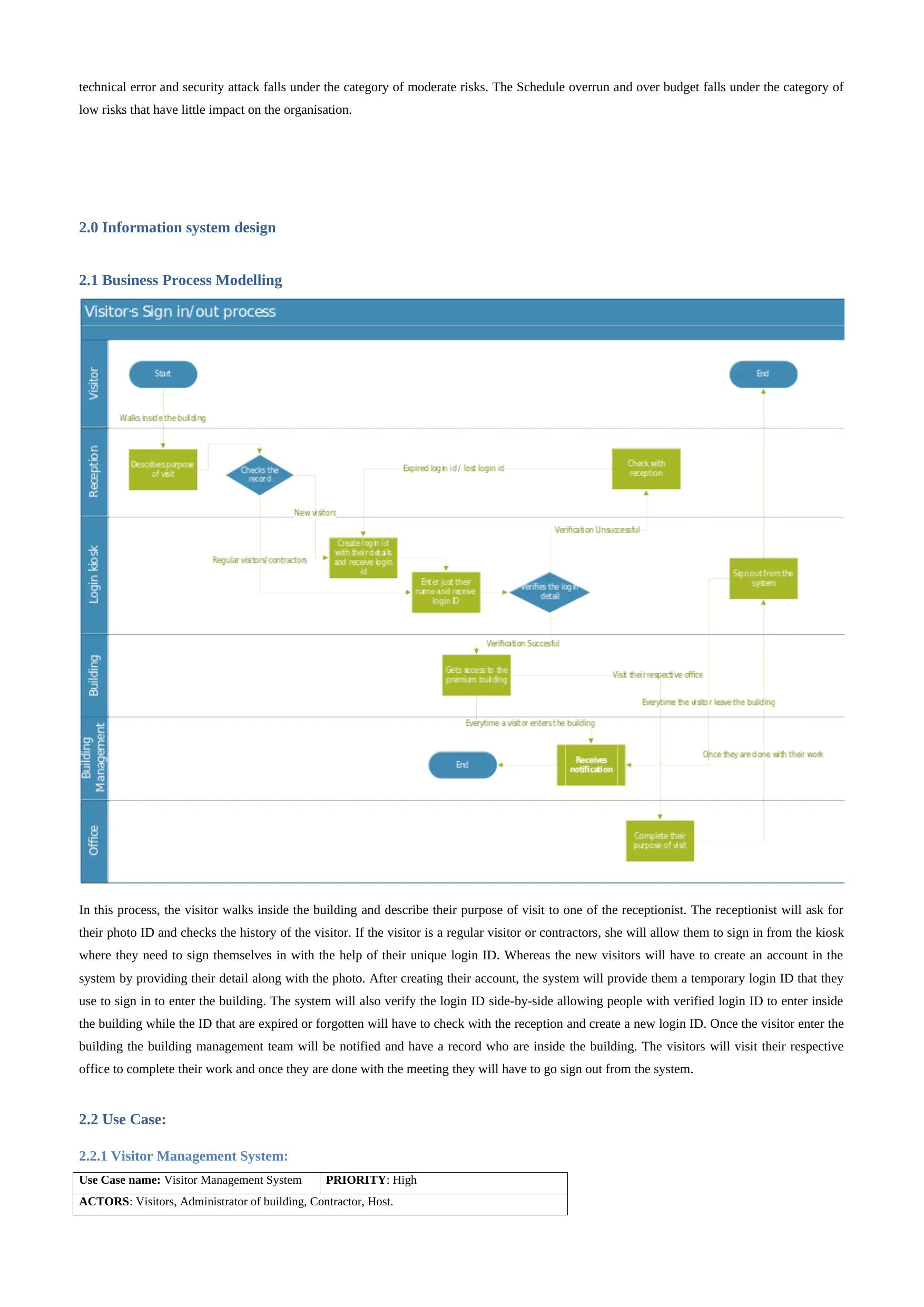
2.2 Use Case:
2.2.1 Visitor Management System:
Use Case name: Visitor Management System PRIORITY: High
ACTORS: Visitors, Administrator of building, Contractor, Host.
low risks that have little impact on the organisation.
2.0 Information system design
2.1 Business Process Modelling
In this process, the visitor walks inside the building and describe their purpose of visit to one of the receptionist. The receptionist will ask for
their photo ID and checks the history of the visitor. If the visitor is a regular visitor or contractors, she will allow them to sign in from the kiosk
where they need to sign themselves in with the help of their unique login ID. Whereas the new visitors will have to create an account in the
system by providing their detail along with the photo. After creating their account, the system will provide them a temporary login ID that they
use to sign in to enter the building. The system will also verify the login ID side-by-side allowing people with verified login ID to enter inside
the building while the ID that are expired or forgotten will have to check with the reception and create a new login ID. Once the visitor enter the
building the building management team will be notified and have a record who are inside the building. The visitors will visit their respective
office to complete their work and once they are done with the meeting they will have to go sign out from the system.
2.2 Use Case:
2.2.1 Visitor Management System:
Use Case name: Visitor Management System PRIORITY: High
ACTORS: Visitors, Administrator of building, Contractor, Host.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
BRIEF DESCRIPTION:
The system is intended to provide a secure system to avoid any kind of unwanted visitors into the
200 George Street, Sydney, one of the premium building jointly owned by Mirvac and AMP
Capital. At present the visitor management is managed by using manual register which is insecure
due to lack of verification of identity. The current system is time consuming and there is possibility
of losing the records.
On the other hand, the proposed system works in digital mode that provides unique sign in code.
The system also saves time and helps to track the record of the contractors. The digital system
(visitor management system) is designed to accesses only the verified individuals and report are
created on real time basis which is more secured that paper based solution.
Purpose of the system:
The system is intended to track accurate working hours and also strengthened the security of the
building. With the help of this system, the cost can be reduce by eliminating the cost of paper .
finally the system can able to generate comprehensive report with the help of efficiency graphic
system
TRIGGER: efficient login system allows authentic person only.
TYPE: Internal and external
PRECONDITIONS: Visitors need to provide valid information while log-in.
Normal Course
Visitor need to login through the application by providing ID and password.
The system provides the dashboard where the visitor can enter the purpose of visit to the building.
The system can automatically update the time of sign-in and sign-out.
Admin can track the visitor register at any point of time.
Post Conditions
Visitorwill require providing valid information to login.
Exceptions
During the time of update of maintenance of the system, the system might be hold for some time.
Figure 1:- Use case diagram Visitor management system
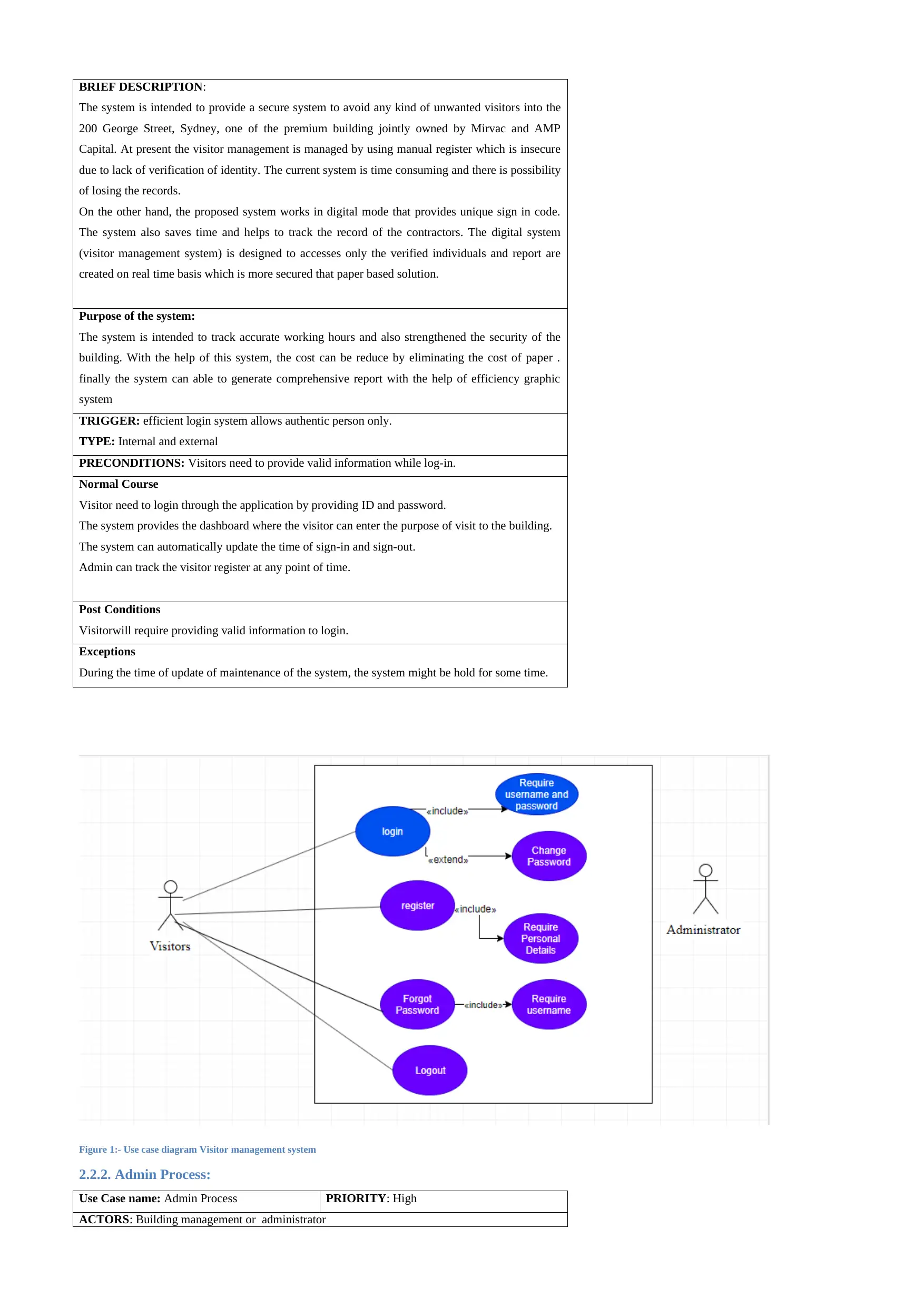
2.2.2. Admin Process:
Use Case name: Admin Process PRIORITY: High
ACTORS: Building management or administrator
The system is intended to provide a secure system to avoid any kind of unwanted visitors into the
200 George Street, Sydney, one of the premium building jointly owned by Mirvac and AMP
Capital. At present the visitor management is managed by using manual register which is insecure
due to lack of verification of identity. The current system is time consuming and there is possibility
of losing the records.
On the other hand, the proposed system works in digital mode that provides unique sign in code.
The system also saves time and helps to track the record of the contractors. The digital system
(visitor management system) is designed to accesses only the verified individuals and report are
created on real time basis which is more secured that paper based solution.
Purpose of the system:
The system is intended to track accurate working hours and also strengthened the security of the
building. With the help of this system, the cost can be reduce by eliminating the cost of paper .
finally the system can able to generate comprehensive report with the help of efficiency graphic
system
TRIGGER: efficient login system allows authentic person only.
TYPE: Internal and external
PRECONDITIONS: Visitors need to provide valid information while log-in.
Normal Course
Visitor need to login through the application by providing ID and password.
The system provides the dashboard where the visitor can enter the purpose of visit to the building.
The system can automatically update the time of sign-in and sign-out.
Admin can track the visitor register at any point of time.
Post Conditions
Visitorwill require providing valid information to login.
Exceptions
During the time of update of maintenance of the system, the system might be hold for some time.
Figure 1:- Use case diagram Visitor management system
2.2.2. Admin Process:
Use Case name: Admin Process PRIORITY: High
ACTORS: Building management or administrator
BRIEF DESCRIPTION:
System administrator is basically the management of the building who tracks the record of visitors
and creates a report at the end of the day, week or month.
TRIGGER: The system is to improve the security of building.
TYPE: Internal
PRECONDITIONS: Proper information during login must be input by the visitors.
Normal Course
Visitors need to login through the application.
Post Conditions
System will allow only authenticate person and generate report of daily in and out.
Exceptions
During the time of update of maintenance of the system, the system might be hold for some time.
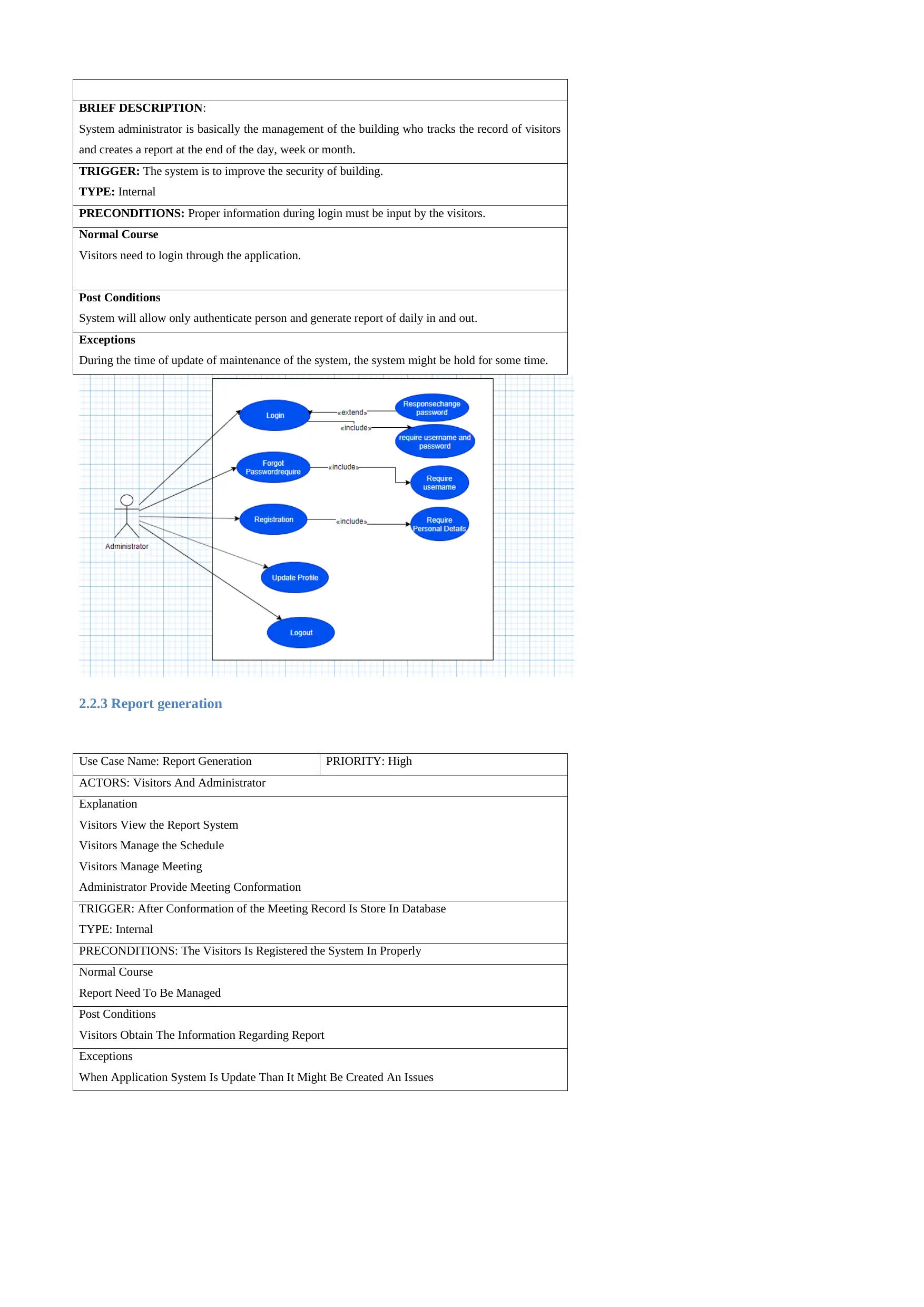
2.2.3 Report generation
Use Case Name: Report Generation PRIORITY: High
ACTORS: Visitors And Administrator
Explanation
Visitors View the Report System
Visitors Manage the Schedule
Visitors Manage Meeting
Administrator Provide Meeting Conformation
TRIGGER: After Conformation of the Meeting Record Is Store In Database
TYPE: Internal
PRECONDITIONS: The Visitors Is Registered the System In Properly
Normal Course
Report Need To Be Managed
Post Conditions
Visitors Obtain The Information Regarding Report
Exceptions
When Application System Is Update Than It Might Be Created An Issues
System administrator is basically the management of the building who tracks the record of visitors
and creates a report at the end of the day, week or month.
TRIGGER: The system is to improve the security of building.
TYPE: Internal
PRECONDITIONS: Proper information during login must be input by the visitors.
Normal Course
Visitors need to login through the application.
Post Conditions
System will allow only authenticate person and generate report of daily in and out.
Exceptions
During the time of update of maintenance of the system, the system might be hold for some time.
2.2.3 Report generation
Use Case Name: Report Generation PRIORITY: High
ACTORS: Visitors And Administrator
Explanation
Visitors View the Report System
Visitors Manage the Schedule
Visitors Manage Meeting
Administrator Provide Meeting Conformation
TRIGGER: After Conformation of the Meeting Record Is Store In Database
TYPE: Internal
PRECONDITIONS: The Visitors Is Registered the System In Properly
Normal Course
Report Need To Be Managed
Post Conditions
Visitors Obtain The Information Regarding Report
Exceptions
When Application System Is Update Than It Might Be Created An Issues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
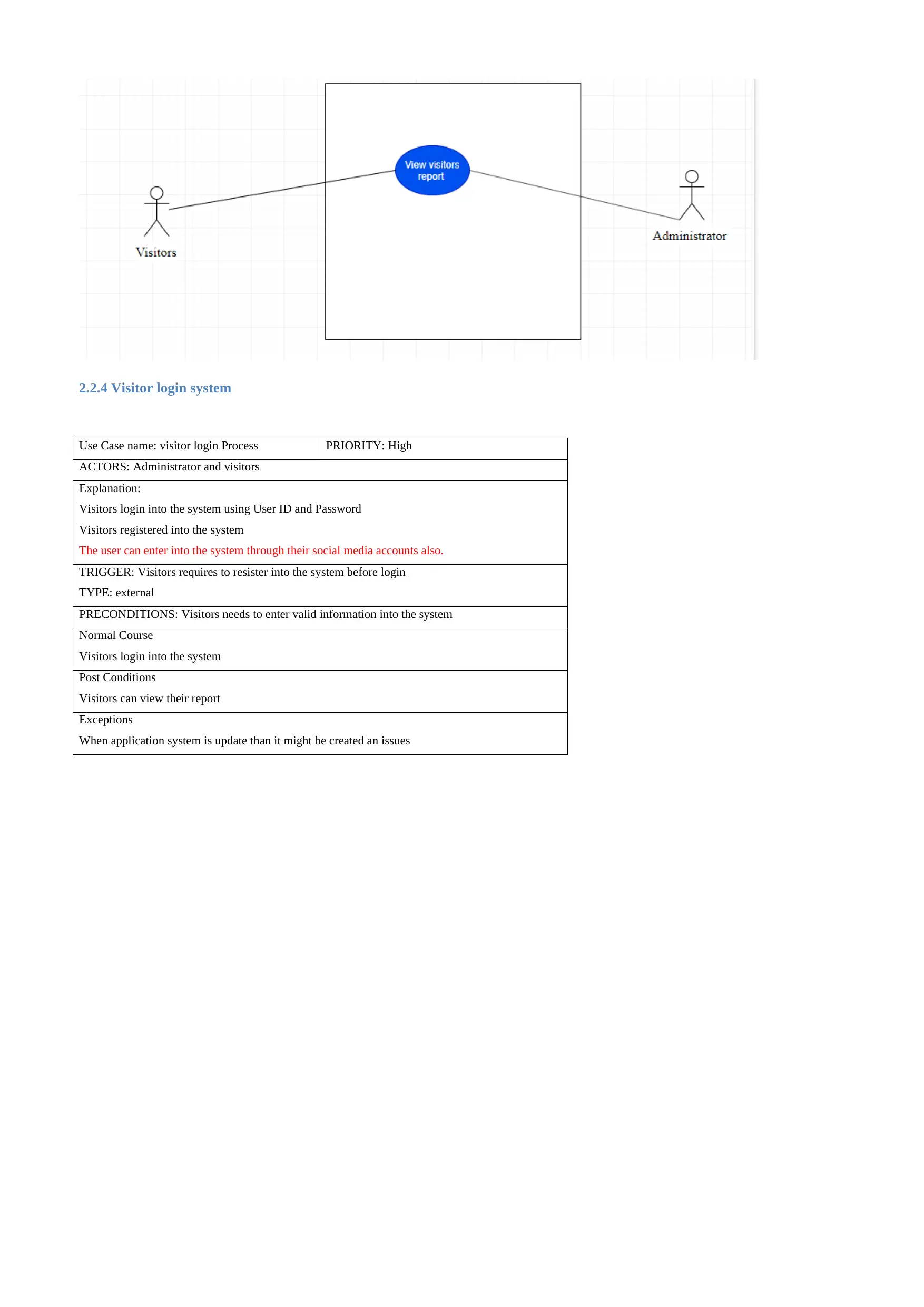
2.2.4 Visitor login system
Use Case name: visitor login Process PRIORITY: High
ACTORS: Administrator and visitors
Explanation:
Visitors login into the system using User ID and Password
Visitors registered into the system
The user can enter into the system through their social media accounts also.
TRIGGER: Visitors requires to resister into the system before login
TYPE: external
PRECONDITIONS: Visitors needs to enter valid information into the system
Normal Course
Visitors login into the system
Post Conditions
Visitors can view their report
Exceptions
When application system is update than it might be created an issues
Use Case name: visitor login Process PRIORITY: High
ACTORS: Administrator and visitors
Explanation:
Visitors login into the system using User ID and Password
Visitors registered into the system
The user can enter into the system through their social media accounts also.
TRIGGER: Visitors requires to resister into the system before login
TYPE: external
PRECONDITIONS: Visitors needs to enter valid information into the system
Normal Course
Visitors login into the system
Post Conditions
Visitors can view their report
Exceptions
When application system is update than it might be created an issues
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
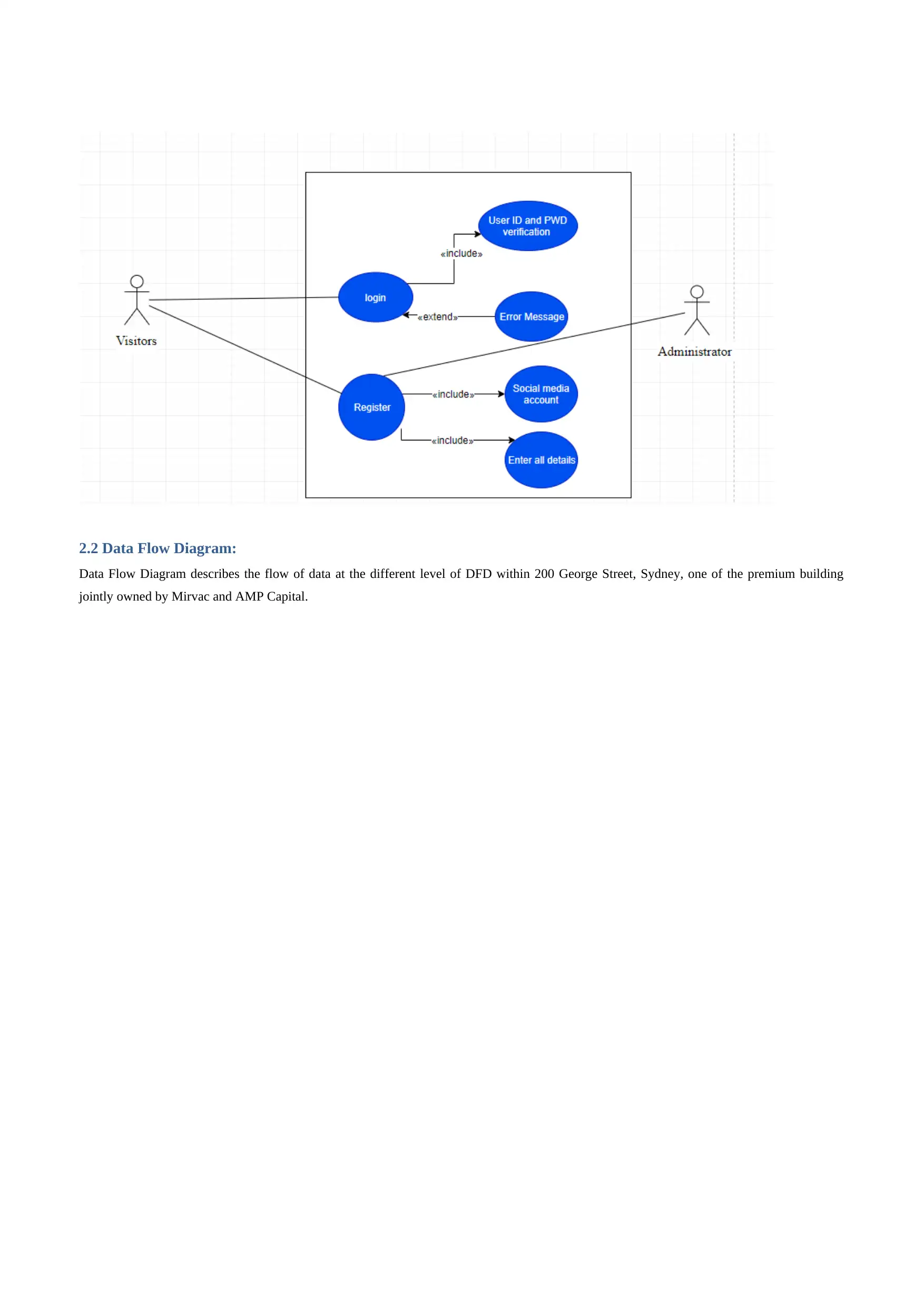
2.2 Data Flow Diagram:
Data Flow Diagram describes the flow of data at the different level of DFD within 200 George Street, Sydney, one of the premium building
jointly owned by Mirvac and AMP Capital.
Data Flow Diagram describes the flow of data at the different level of DFD within 200 George Street, Sydney, one of the premium building
jointly owned by Mirvac and AMP Capital.
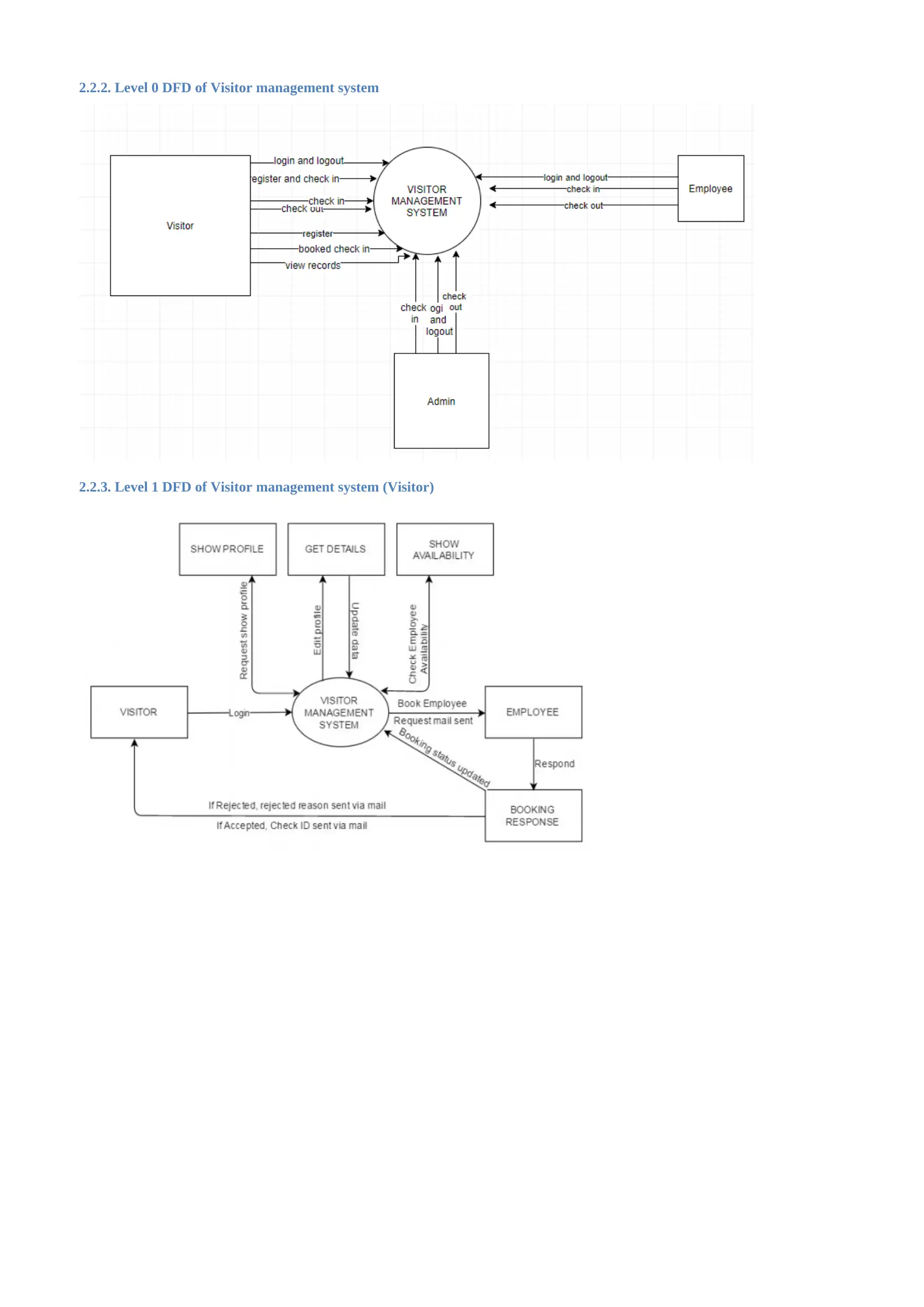
2.2.2. Level 0 DFD of Visitor management system
2.2.3. Level 1 DFD of Visitor management system (Visitor)
2.2.3. Level 1 DFD of Visitor management system (Visitor)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
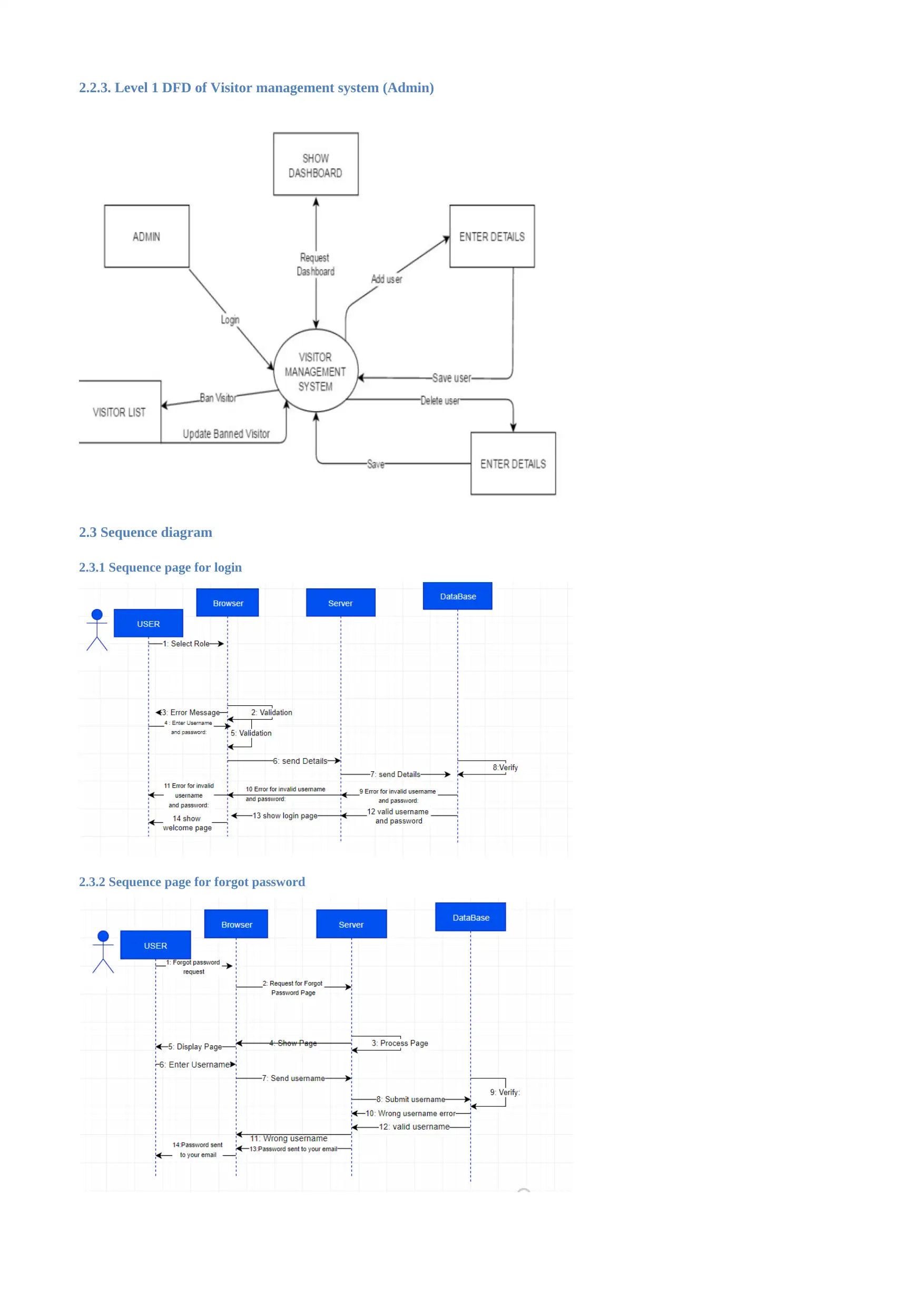
2.2.3. Level 1 DFD of Visitor management system (Admin)
2.3 Sequence diagram
2.3.1 Sequence page for login
2.3.2 Sequence page for forgot password
2.3 Sequence diagram
2.3.1 Sequence page for login
2.3.2 Sequence page for forgot password
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2.6 Managerial Reports
The new proposed online visitor management systems aims to further optimise the process of visitor check-ins and check-outs and eventually
make it more efficient and streamlined in nature. Furthermore, it would allow the management of the organisation to keep a continuous track on
the people coming in and going out of the building and this would help in ensuring better monitoring of the activities of the people inside the
building premises.
2.6.1 Sales Reports
A sales report provides a proper overview about the present situation of business and this provides an accurate understanding about how
efficiently the business functionalities have been carried out by the organisation. The sales reports would provide a clear understanding about the
daily sales proceeds generated by the organisation from their customers and this would enable the management to get a proper understanding
about the customer footfalls generated on a daily basis (Ingram et al., 2015). This would allow the management of the organisation to develop
their online visitor management system in a proper and appropriate manner so that it is able to handle the daily customer rush without crashing.
They would be able to design and develop a rigid and efficient visitor management system that would allow them to continuously track down
and monitor the activities of the people inside the organisation and this would enable them to ensure greater safety within the organisation
(Moutot and Bascoul, 2008).
2.6.2 Budget Report
The budget report provides a better understanding and information about the control of cash flow within the business. It would help the
management to get accurate insights about the shoddy monetary transactions and exercises that are taking place within their business and how it
is eventually impacting upon the organisational bottom-line. The budget reports allow the organisation to ensure an effective resource allocation
process and this eventually helps the organisation to get access to the necessary financial resources that would allow them to design, develop and
integrate the online visitor management system in a timely and successful manner. The budget report would also provide a structured
representation about the various cost factors associated with the project and this would help in ensuring that unnecessary expenses are minimised
(Timms and Treasury, 2010).
3.0 System Implementation
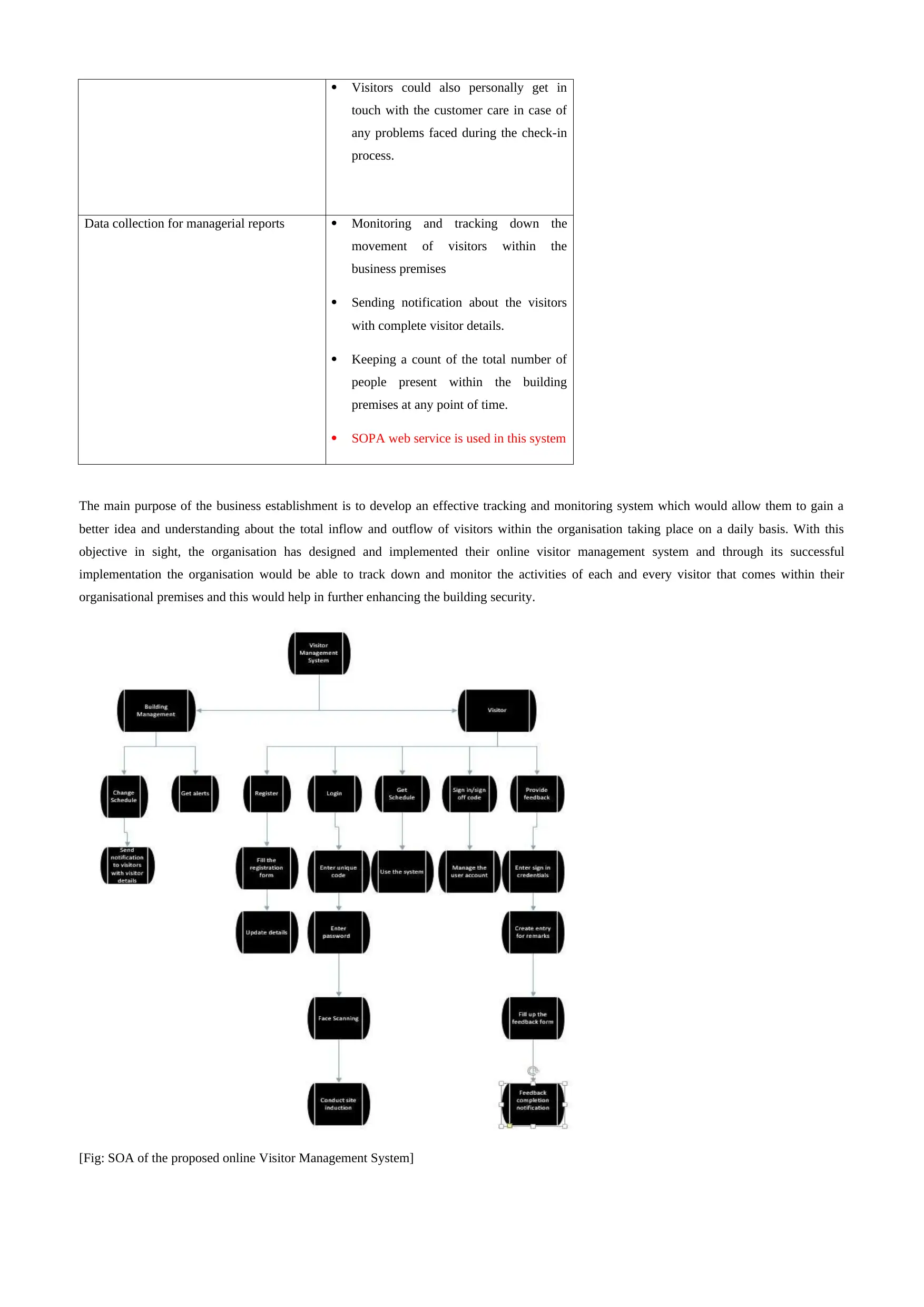
3.1 Service and SOA
The Service Oriented Architecture (SOA) is the illustrative design which provides a detailed and comprehensive understanding about the inner
functionalities that are incorporated within a particular system. This helps in understanding how the different components of the system work
together in a cohesive manner and eventually make the system perform its desired tasks. With the help of the SOA, the designers and engineers
who are responsible for system implementation are able to work on the various aspects of system independently and this allows them to
undertake necessary changes and modifications on the system based on the eventual organisational needs and requirements (MacKenzie et al.,
2006). This eventually helps in the creation of a thorough and robust online visitor management system that would eventually serve the main
purpose and objective of the organisation.
Functionality Services
Visitor Login/ Registration Personal Information Identity
Email Id
Password
OTP Authentication
Product detail Visitor Registration
Visitor Check-In
Visitor Check-Out
Customer support Visitors could leave their feedback and
comments
The new proposed online visitor management systems aims to further optimise the process of visitor check-ins and check-outs and eventually
make it more efficient and streamlined in nature. Furthermore, it would allow the management of the organisation to keep a continuous track on
the people coming in and going out of the building and this would help in ensuring better monitoring of the activities of the people inside the
building premises.
2.6.1 Sales Reports
A sales report provides a proper overview about the present situation of business and this provides an accurate understanding about how
efficiently the business functionalities have been carried out by the organisation. The sales reports would provide a clear understanding about the
daily sales proceeds generated by the organisation from their customers and this would enable the management to get a proper understanding
about the customer footfalls generated on a daily basis (Ingram et al., 2015). This would allow the management of the organisation to develop
their online visitor management system in a proper and appropriate manner so that it is able to handle the daily customer rush without crashing.
They would be able to design and develop a rigid and efficient visitor management system that would allow them to continuously track down
and monitor the activities of the people inside the organisation and this would enable them to ensure greater safety within the organisation
(Moutot and Bascoul, 2008).
2.6.2 Budget Report
The budget report provides a better understanding and information about the control of cash flow within the business. It would help the
management to get accurate insights about the shoddy monetary transactions and exercises that are taking place within their business and how it
is eventually impacting upon the organisational bottom-line. The budget reports allow the organisation to ensure an effective resource allocation
process and this eventually helps the organisation to get access to the necessary financial resources that would allow them to design, develop and
integrate the online visitor management system in a timely and successful manner. The budget report would also provide a structured
representation about the various cost factors associated with the project and this would help in ensuring that unnecessary expenses are minimised
(Timms and Treasury, 2010).
3.0 System Implementation
3.1 Service and SOA
The Service Oriented Architecture (SOA) is the illustrative design which provides a detailed and comprehensive understanding about the inner
functionalities that are incorporated within a particular system. This helps in understanding how the different components of the system work
together in a cohesive manner and eventually make the system perform its desired tasks. With the help of the SOA, the designers and engineers
who are responsible for system implementation are able to work on the various aspects of system independently and this allows them to
undertake necessary changes and modifications on the system based on the eventual organisational needs and requirements (MacKenzie et al.,
2006). This eventually helps in the creation of a thorough and robust online visitor management system that would eventually serve the main
purpose and objective of the organisation.
Functionality Services
Visitor Login/ Registration Personal Information Identity
Email Id
Password
OTP Authentication
Product detail Visitor Registration
Visitor Check-In
Visitor Check-Out
Customer support Visitors could leave their feedback and
comments
Visitors could also personally get in
touch with the customer care in case of
any problems faced during the check-in
process.
Data collection for managerial reports Monitoring and tracking down the
movement of visitors within the
business premises
Sending notification about the visitors
with complete visitor details.
Keeping a count of the total number of
people present within the building
premises at any point of time.
SOPA web service is used in this system
The main purpose of the business establishment is to develop an effective tracking and monitoring system which would allow them to gain a
better idea and understanding about the total inflow and outflow of visitors within the organisation taking place on a daily basis. With this
objective in sight, the organisation has designed and implemented their online visitor management system and through its successful
implementation the organisation would be able to track down and monitor the activities of each and every visitor that comes within their
organisational premises and this would help in further enhancing the building security.
[Fig: SOA of the proposed online Visitor Management System]
touch with the customer care in case of
any problems faced during the check-in
process.
Data collection for managerial reports Monitoring and tracking down the
movement of visitors within the
business premises
Sending notification about the visitors
with complete visitor details.
Keeping a count of the total number of
people present within the building
premises at any point of time.
SOPA web service is used in this system
The main purpose of the business establishment is to develop an effective tracking and monitoring system which would allow them to gain a
better idea and understanding about the total inflow and outflow of visitors within the organisation taking place on a daily basis. With this
objective in sight, the organisation has designed and implemented their online visitor management system and through its successful
implementation the organisation would be able to track down and monitor the activities of each and every visitor that comes within their
organisational premises and this would help in further enhancing the building security.
[Fig: SOA of the proposed online Visitor Management System]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





