IT Report: Analysis of Big Data Security and Privacy in the Cloud
VerifiedAdded on 2020/05/28
|15
|4338
|111
Report
AI Summary
This IT report delves into the critical intersection of big data and cloud computing, emphasizing the significant security and privacy challenges that arise. It explores the vulnerabilities associated with outsourcing data, including issues of access control, authentication, and data breaches. The report reviews existing literature and analyzes the various threats, such as network-level, data-level, and authentication-level risks, offering insights into the importance of confidentiality, integrity, and availability (CIA) in data security. The paper discusses the role of third-party networks and the need for careful evaluation of cloud services. It also highlights the advantages of cloud computing while addressing the barriers to its wider adoption, such as complex administration and potential user-side design flaws. The report concludes with a call for enhanced security policies and a focus on protecting sensitive information, providing a robust analysis of the security landscape and vulnerabilities in the cloud environment. This assignment is available on Desklib, a platform offering past papers and solved assignments.

Running head: IT
IT
[Name of the Student]
[Name of the University]
[Author note]
IT
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................2
Literature review:...................................................................................................................2
Analysis of The Outsourcing Data and The Applications:....................................................3
Analysis of The Security and The Privacy Challenges:.........................................................4
Analysis of the method and the material used in this paper:..................................................5
Analysis of the Results:..........................................................................................................5
Method for the Solving of problem:...........................................................................................8
Different evaluation criteria for addressing the Security of the Big Data:................................9
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................2
Literature review:...................................................................................................................2
Analysis of The Outsourcing Data and The Applications:....................................................3
Analysis of The Security and The Privacy Challenges:.........................................................4
Analysis of the method and the material used in this paper:..................................................5
Analysis of the Results:..........................................................................................................5
Method for the Solving of problem:...........................................................................................8
Different evaluation criteria for addressing the Security of the Big Data:................................9
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11

Introduction:
Big Data is considered to be very much important for the IT world. For this reason,
the Big Data cannot be overlooked in the IT world. The main reasons which lies behind this
is the prominent increase in the data along with the services that are related with this data. So
it becomes increasing important to explore this field along with looking into the matter of
improving the ways of Big data analysis especially in the clouds (Purcell 2014). These two
key aspects are the big data and the cloud computing. The Paper “An Evaluation of Major
Threats in Cloud Computing Associated with Big Data” by “Kamalpreet Kaur”, “Ali
Syed”, “Azeem Mohammad”, “Malka N. Halgamuge” states that most of the organisations
relies on the power of the databases. And when the organisations outsources their database in
the form of big data then they transfer all their data to the cloud (Hashem et al. 2015). The
paper also indicates that the security challenges act as one of the most prominent issues
related to the cloud computing and big data. Some of the major issues related to big data
were also observed in this paper. The paper also indicates that due to various security threats
clouds are not getting adopted on a larger scale despite of the presence of various advantages.
The data sources have been analysed in this paper which helped a lot in identification of the
gaps. The report provides the necessary solutions for the issues related to the analysis of the
big data in the cloud.
Discussion:
Literature review:
A very important role is played by the big data in the world of business. this is due to
fact that storing of the complex data in a secure way is one of the crucial aspects of the
corporate operations. Big data refers to the huge amount of data in the structured, semi-
structured, and unstructured form (Ji et al. 2012). There are 3V’s in the Big data and this
Big Data is considered to be very much important for the IT world. For this reason,
the Big Data cannot be overlooked in the IT world. The main reasons which lies behind this
is the prominent increase in the data along with the services that are related with this data. So
it becomes increasing important to explore this field along with looking into the matter of
improving the ways of Big data analysis especially in the clouds (Purcell 2014). These two
key aspects are the big data and the cloud computing. The Paper “An Evaluation of Major
Threats in Cloud Computing Associated with Big Data” by “Kamalpreet Kaur”, “Ali
Syed”, “Azeem Mohammad”, “Malka N. Halgamuge” states that most of the organisations
relies on the power of the databases. And when the organisations outsources their database in
the form of big data then they transfer all their data to the cloud (Hashem et al. 2015). The
paper also indicates that the security challenges act as one of the most prominent issues
related to the cloud computing and big data. Some of the major issues related to big data
were also observed in this paper. The paper also indicates that due to various security threats
clouds are not getting adopted on a larger scale despite of the presence of various advantages.
The data sources have been analysed in this paper which helped a lot in identification of the
gaps. The report provides the necessary solutions for the issues related to the analysis of the
big data in the cloud.
Discussion:
Literature review:
A very important role is played by the big data in the world of business. this is due to
fact that storing of the complex data in a secure way is one of the crucial aspects of the
corporate operations. Big data refers to the huge amount of data in the structured, semi-
structured, and unstructured form (Ji et al. 2012). There are 3V’s in the Big data and this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

mainly includes the high volume of data, high velocity of data and high variety of different
types of information that are in need of getting mined. But the specific quantity of data is not
mentioned anywhere, and the data can be in petabytes or Exabyte (Demirkan and Delen
2013). Peter Skomoroch stated that it was not possible to process the big data due to the
difficulty, proneness to errors, and large time consuming nature of the data. This was difficult
before the invention of the various data technologies like the MapReduce and Hadoop. These
new technologies have greatly helped in the processing of the datasets than the traditional
processing tools.
There are many organisations which are associated with the collection of the complex
data. This data is collected by the doing the worldwide surveys so as to improve the process
of decision making that are extremely important for the sustaining of the healthy future for
the organisation’s business process (Fernández et al. 2014). It can be stated that there are
various security challenges which comes up with the use of the clouds.
Analysis of The Outsourcing Data and The Applications:
Cloud computing is something which is capable of providing access to the data
present in the clouds anytime anywhere. But the challenge remains that is checking of the
authorized entities (Inukollu Arsi and Ravuri 2014). The significant challenges arising due to
the monitoring of the clouds and many more results in the suffering of the cloud computing in
reaching its full potential. So the users have to rely on the third part and the cloud providers
for the purpose of making their data secure along with maintenance of the communication
related to the reliability with the customers. When a user is making use of the cloud for the
purpose of making decisions regarding the complex data and the platforms then it might seem
that there is no other computing which has been done here (Demchenko et al. 2012). This
happens due to the fact that there is no existence of any technical mechanism for the
prevention of the accessing the data of the users unethically by the cloud providers. So the
types of information that are in need of getting mined. But the specific quantity of data is not
mentioned anywhere, and the data can be in petabytes or Exabyte (Demirkan and Delen
2013). Peter Skomoroch stated that it was not possible to process the big data due to the
difficulty, proneness to errors, and large time consuming nature of the data. This was difficult
before the invention of the various data technologies like the MapReduce and Hadoop. These
new technologies have greatly helped in the processing of the datasets than the traditional
processing tools.
There are many organisations which are associated with the collection of the complex
data. This data is collected by the doing the worldwide surveys so as to improve the process
of decision making that are extremely important for the sustaining of the healthy future for
the organisation’s business process (Fernández et al. 2014). It can be stated that there are
various security challenges which comes up with the use of the clouds.
Analysis of The Outsourcing Data and The Applications:
Cloud computing is something which is capable of providing access to the data
present in the clouds anytime anywhere. But the challenge remains that is checking of the
authorized entities (Inukollu Arsi and Ravuri 2014). The significant challenges arising due to
the monitoring of the clouds and many more results in the suffering of the cloud computing in
reaching its full potential. So the users have to rely on the third part and the cloud providers
for the purpose of making their data secure along with maintenance of the communication
related to the reliability with the customers. When a user is making use of the cloud for the
purpose of making decisions regarding the complex data and the platforms then it might seem
that there is no other computing which has been done here (Demchenko et al. 2012). This
happens due to the fact that there is no existence of any technical mechanism for the
prevention of the accessing the data of the users unethically by the cloud providers. So the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

significance of building up a new layer increases for the purpose of supporting a contractual
negotiation phase between the providers of the cloud and the end-users. So it can be
concluded that there is an essential need for the combination of technical as well as non-
technical mechanism for the purpose of gaining the trust towards the use of the cloud
computing environment.
Analysis of The Security and The Privacy Challenges:
Cloud computing consists of a service level agreement which is a contractual
agreement used for the building up of new layers for the purpose of supporting a contractual
negotiation phase. This phase mainly exists between the cloud customers and the cloud
providers. Still the difficulty of bargaining remains regarding the security, privacy, as well as
the trust (Zissis and Lekkas 2012). Despite of all this there are still some ways in which can
be used for the purpose of assuring the customers. This assurance is mainly given for the
purpose of making the customers understand that the cloud service providers provides
services which is subjected to the contractual agreement initially this makes the process
difficult.
Access control: The need of credential based access control is increasing in cloud
computing. The main reason for the existence of this for the accessing the control and
the services so as to make sure that the important as well as the provenance
information of the customer does not get leaked (Hashizume et al. 2013).
Trust management: There are various way of managing the trust with the customers.
there is an essential need of building up new policies for access control (Chen and
Zhao 2012). This should be done instead of telling the customers that their data will
never get breached for the purpose of management of the trust among the customers.
Authentication and identity management: The main reason lying behind the use of
identity management is for the purpose of determining an authenticate user along with
negotiation phase between the providers of the cloud and the end-users. So it can be
concluded that there is an essential need for the combination of technical as well as non-
technical mechanism for the purpose of gaining the trust towards the use of the cloud
computing environment.
Analysis of The Security and The Privacy Challenges:
Cloud computing consists of a service level agreement which is a contractual
agreement used for the building up of new layers for the purpose of supporting a contractual
negotiation phase. This phase mainly exists between the cloud customers and the cloud
providers. Still the difficulty of bargaining remains regarding the security, privacy, as well as
the trust (Zissis and Lekkas 2012). Despite of all this there are still some ways in which can
be used for the purpose of assuring the customers. This assurance is mainly given for the
purpose of making the customers understand that the cloud service providers provides
services which is subjected to the contractual agreement initially this makes the process
difficult.
Access control: The need of credential based access control is increasing in cloud
computing. The main reason for the existence of this for the accessing the control and
the services so as to make sure that the important as well as the provenance
information of the customer does not get leaked (Hashizume et al. 2013).
Trust management: There are various way of managing the trust with the customers.
there is an essential need of building up new policies for access control (Chen and
Zhao 2012). This should be done instead of telling the customers that their data will
never get breached for the purpose of management of the trust among the customers.
Authentication and identity management: The main reason lying behind the use of
identity management is for the purpose of determining an authenticate user along with

the services (Ren Wang and Wang 2012). This is mainly based upon the credentials
and the characteristics of the users.
Privacy and protection of the data: Among the discussed challenges privacy is one of
the biggest issue. There are many organisations which are not comfortable with the
storing of their confidential data outside their premises. By use of the outsourcing data
shared infrastructure, there is a risk of putting the customers background information
at risk (Almorsy Grundy and Müller 2016). This is mainly used for various purposes
and this mainly includes the auditing, tracing back along with the historically based
access control. Along with this it also shows the balance that exists between the
personal information of the client and the privacy. This is one of the biggest drawback
that exists in the cloud environment.
Analysis of the method and the material used in this paper:
The research method that has been used in this paper for the purpose of interpreting
the trends of the data sourced is by analysing the contents. This analysis is mainly done so as
to find out the various proceedings along with measuring the processes so as to assist in the
solving of the perplexing and the complex issues (Ryan 2013). A historic logic method has
been used in this research. This will be greatly helping in assisting the interpretation of the
findings regarding the security matters in the cloud computing that has discovered in the
previous researches. By the process of evaluation of the gathered information and opinions
form the experts has greatly helped in the study so as to shed a light in the area of cloud
computing for further developments.
Analysis of the Results:
The results help in concluding that there are various domains in the cloud
environment and these domains faces various security as well as privacy challenges. For this
reason, there is an essential need for the users to thing before migrating their data to the cloud
and the characteristics of the users.
Privacy and protection of the data: Among the discussed challenges privacy is one of
the biggest issue. There are many organisations which are not comfortable with the
storing of their confidential data outside their premises. By use of the outsourcing data
shared infrastructure, there is a risk of putting the customers background information
at risk (Almorsy Grundy and Müller 2016). This is mainly used for various purposes
and this mainly includes the auditing, tracing back along with the historically based
access control. Along with this it also shows the balance that exists between the
personal information of the client and the privacy. This is one of the biggest drawback
that exists in the cloud environment.
Analysis of the method and the material used in this paper:
The research method that has been used in this paper for the purpose of interpreting
the trends of the data sourced is by analysing the contents. This analysis is mainly done so as
to find out the various proceedings along with measuring the processes so as to assist in the
solving of the perplexing and the complex issues (Ryan 2013). A historic logic method has
been used in this research. This will be greatly helping in assisting the interpretation of the
findings regarding the security matters in the cloud computing that has discovered in the
previous researches. By the process of evaluation of the gathered information and opinions
form the experts has greatly helped in the study so as to shed a light in the area of cloud
computing for further developments.
Analysis of the Results:
The results help in concluding that there are various domains in the cloud
environment and these domains faces various security as well as privacy challenges. For this
reason, there is an essential need for the users to thing before migrating their data to the cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(Srinivasan et al. 2012). The challenges regarding the security can be categorised into various
type and this includes the “network level”, “data level”, “authentication level” and many
more. The major concern beside all this is the security of the sensitive information. For the
purpose of enhancing the security it is becomes necessarily important to provide the access
control along with the authentication and authorisation of the data that are to be stored in the
clouds. CIA or “Confidentiality”, “Integrity” and “Availability” are the three major elements
involved in the information security (Behl and Behl 2012). Along with this it should also be
ensured that these three elements are being provided to the customers by the cloud providers.
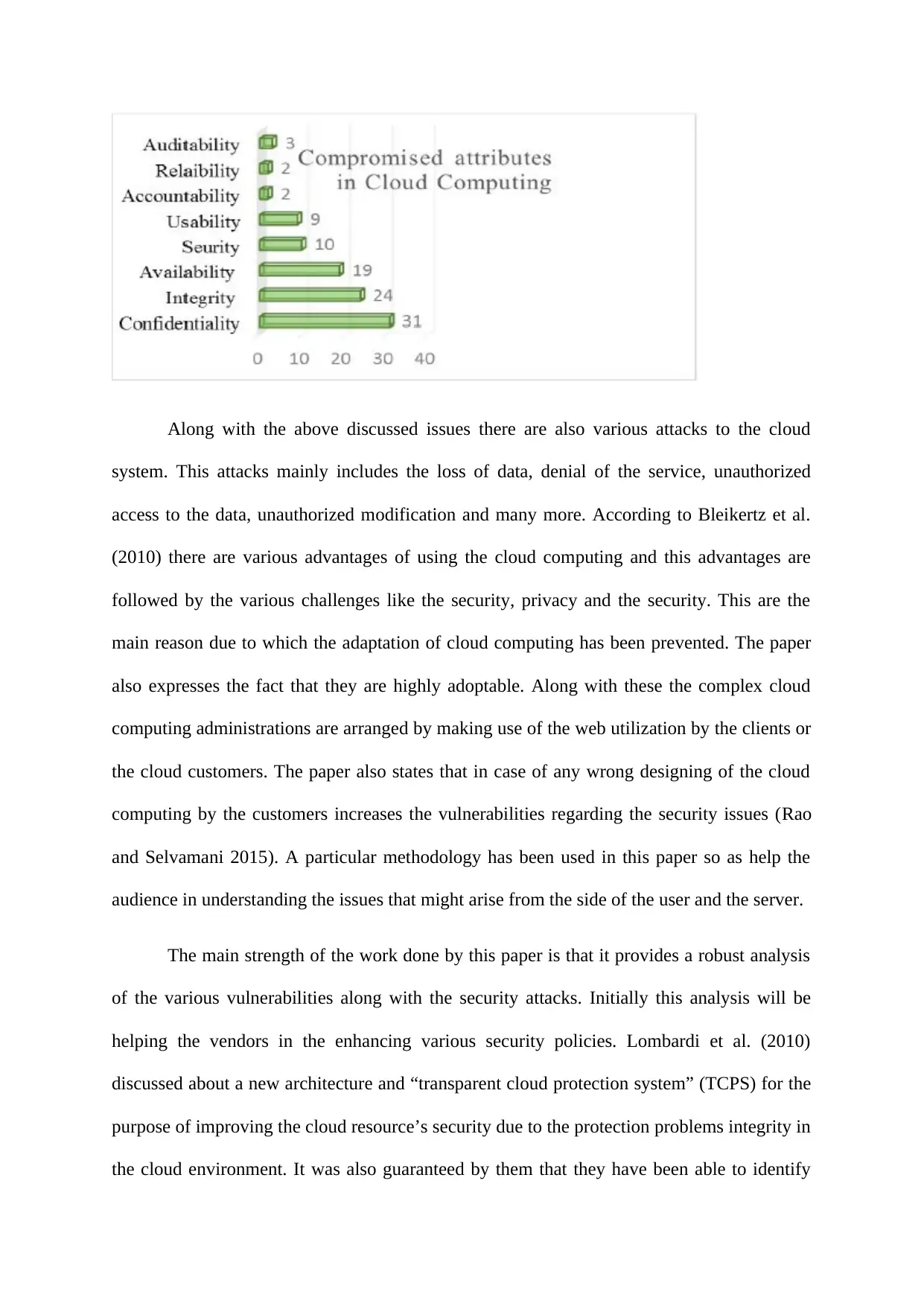
The paper also provides a figure which shows that the level of integrity is 24%, level of
confidentiality is 31% and the level of availability is 19%. This results to be most threatening
attributes when compared with the other attributes. The other attributes mainly include the
usability, accountability, security and reliability. The biggest risk included in cloud
computing are the “security of the data”, “integrity” and “recovery”. Along with this it is also
important to know about the location in which the data is being stored and what are things
that are being done with the stored data (Ali Khan and Vasilakos 2015). Besides all this it is
also important to know what will happen if the cloud fails and if the data are being backed up
or not. Third party networks are used by the cloud computing technology for the purpose of
accessing the cloud services. This gives arise to various risks while accessing the services in
the clouds. The users need to compare the various cloud services before moving into the
cloud. The cloud services are becoming much more popular as they are much more
convenient along with being affordable and provide a space for storage.
type and this includes the “network level”, “data level”, “authentication level” and many
more. The major concern beside all this is the security of the sensitive information. For the
purpose of enhancing the security it is becomes necessarily important to provide the access
control along with the authentication and authorisation of the data that are to be stored in the
clouds. CIA or “Confidentiality”, “Integrity” and “Availability” are the three major elements
involved in the information security (Behl and Behl 2012). Along with this it should also be
ensured that these three elements are being provided to the customers by the cloud providers.
The paper also provides a figure which shows that the level of integrity is 24%, level of
confidentiality is 31% and the level of availability is 19%. This results to be most threatening
attributes when compared with the other attributes. The other attributes mainly include the
usability, accountability, security and reliability. The biggest risk included in cloud
computing are the “security of the data”, “integrity” and “recovery”. Along with this it is also
important to know about the location in which the data is being stored and what are things
that are being done with the stored data (Ali Khan and Vasilakos 2015). Besides all this it is
also important to know what will happen if the cloud fails and if the data are being backed up
or not. Third party networks are used by the cloud computing technology for the purpose of
accessing the cloud services. This gives arise to various risks while accessing the services in
the clouds. The users need to compare the various cloud services before moving into the
cloud. The cloud services are becoming much more popular as they are much more
convenient along with being affordable and provide a space for storage.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Along with the above discussed issues there are also various attacks to the cloud
system. This attacks mainly includes the loss of data, denial of the service, unauthorized
access to the data, unauthorized modification and many more. According to Bleikertz et al.
(2010) there are various advantages of using the cloud computing and this advantages are
followed by the various challenges like the security, privacy and the security. This are the
main reason due to which the adaptation of cloud computing has been prevented. The paper
also expresses the fact that they are highly adoptable. Along with these the complex cloud
computing administrations are arranged by making use of the web utilization by the clients or
the cloud customers. The paper also states that in case of any wrong designing of the cloud
computing by the customers increases the vulnerabilities regarding the security issues (Rao
and Selvamani 2015). A particular methodology has been used in this paper so as help the
audience in understanding the issues that might arise from the side of the user and the server.
The main strength of the work done by this paper is that it provides a robust analysis
of the various vulnerabilities along with the security attacks. Initially this analysis will be
helping the vendors in the enhancing various security policies. Lombardi et al. (2010)
discussed about a new architecture and “transparent cloud protection system” (TCPS) for the
purpose of improving the cloud resource’s security due to the protection problems integrity in
the cloud environment. It was also guaranteed by them that they have been able to identify
system. This attacks mainly includes the loss of data, denial of the service, unauthorized
access to the data, unauthorized modification and many more. According to Bleikertz et al.
(2010) there are various advantages of using the cloud computing and this advantages are
followed by the various challenges like the security, privacy and the security. This are the
main reason due to which the adaptation of cloud computing has been prevented. The paper
also expresses the fact that they are highly adoptable. Along with these the complex cloud
computing administrations are arranged by making use of the web utilization by the clients or
the cloud customers. The paper also states that in case of any wrong designing of the cloud
computing by the customers increases the vulnerabilities regarding the security issues (Rao
and Selvamani 2015). A particular methodology has been used in this paper so as help the
audience in understanding the issues that might arise from the side of the user and the server.
The main strength of the work done by this paper is that it provides a robust analysis
of the various vulnerabilities along with the security attacks. Initially this analysis will be
helping the vendors in the enhancing various security policies. Lombardi et al. (2010)
discussed about a new architecture and “transparent cloud protection system” (TCPS) for the
purpose of improving the cloud resource’s security due to the protection problems integrity in
the cloud environment. It was also guaranteed by them that they have been able to identify

the problems related to integrity protection along with addressing the issues related to
integrity. They have also proposed a framework in which the TCPS can be utilized for the
purpose of watching the integrity of the visitor along with keeping of honesty and
virtualization. For the purpose of managing the image system in TCPS, the image filters have
been used by them along with the scanners so as to detect the malicious image in order to
prevent them from vulnerabilities and the security attacks. The main strength of the work
done by Lombardi et al. is that it has proposed instrument that provides an enhanced rate of
security, transparency and interrupt identification system. Along with this the limitation of
this work is that they have not tested it to an expert cloud computing situation nor they
haven’t accepted their work.
Method for the Solving of problem:
Some of the suggested method related to the solving of the issues during the use of
big data in the clouds are listed below:
Shipping of the Disk Drives to the Clouds: The problems related to problems in the
plumbing can be solved by shipping the disk drives to the cloud environment. This
will be helping a lot.
Use of Data Mining techniques: The problem related to the malware diffusion can be
tackled by making use of the data mining technique. This technique will greatly help
in the identification of the malware in the cloud and eliminate the treats by the cyber
criminals which happens to be a threat regarding the security and privacy of the
customers (Bhadauria and Sanyal 2012).
Use of the Access Control Techniques: For the purpose of securing the infrastructure
of the big data systems there is a need of securing the distributed computation as well
as the data stored. For the purpose of securing the data itself the information
integrity. They have also proposed a framework in which the TCPS can be utilized for the
purpose of watching the integrity of the visitor along with keeping of honesty and
virtualization. For the purpose of managing the image system in TCPS, the image filters have
been used by them along with the scanners so as to detect the malicious image in order to
prevent them from vulnerabilities and the security attacks. The main strength of the work
done by Lombardi et al. is that it has proposed instrument that provides an enhanced rate of
security, transparency and interrupt identification system. Along with this the limitation of
this work is that they have not tested it to an expert cloud computing situation nor they
haven’t accepted their work.
Method for the Solving of problem:
Some of the suggested method related to the solving of the issues during the use of
big data in the clouds are listed below:
Shipping of the Disk Drives to the Clouds: The problems related to problems in the
plumbing can be solved by shipping the disk drives to the cloud environment. This
will be helping a lot.
Use of Data Mining techniques: The problem related to the malware diffusion can be
tackled by making use of the data mining technique. This technique will greatly help
in the identification of the malware in the cloud and eliminate the treats by the cyber
criminals which happens to be a threat regarding the security and privacy of the
customers (Bhadauria and Sanyal 2012).
Use of the Access Control Techniques: For the purpose of securing the infrastructure
of the big data systems there is a need of securing the distributed computation as well
as the data stored. For the purpose of securing the data itself the information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

dissemination should be preserving the privacy along with this the sensitive data
should be also protected by the use of cryptography and granular access control
techniques (Modi et al. 2013). Enormous volume of the data necessities needs to be
managed which are scalable along with the enabling of the “efficient audits” as well
as the “data provenance”.
Modelling: There is a need of validating the threat models which will be mainly
covering the various types of cyber-attacks or any kind of data leakages which are
mainly caused by the cybercriminals.
Possible solutions: After the formalization of the threat model there is an essential
need of finding the tractable solution.
Implementation: The solution that are found out are to be implemented in the existing
technologies and the infrastructure which will be initially followed by the comparison
of the solutions with the different types of threat models.
Different evaluation criteria for addressing the Security of the Big Data:
After analyzing the security challenges related to big data the following solutions can
be applied so as to eliminate all the risks. Some of the solutions are listed below:
One of the major thing that is to be included in the new security solution is the
extension of the secure perimeter of the big data from the enterprise to the public
cloud (Puthal et al. 2015). By adopting this method, a new trustful data provenance
mechanism will be created that will be initially helping in the mitigation of the risks
related to the DDoS attacks which are mainly launched against the infrastructures of
the big data.
There is a mandatory need of addressing the legal requirements by the mechanisms
regarding the handling of the data. One of the best way of securing the big data is by
should be also protected by the use of cryptography and granular access control
techniques (Modi et al. 2013). Enormous volume of the data necessities needs to be
managed which are scalable along with the enabling of the “efficient audits” as well
as the “data provenance”.
Modelling: There is a need of validating the threat models which will be mainly
covering the various types of cyber-attacks or any kind of data leakages which are
mainly caused by the cybercriminals.
Possible solutions: After the formalization of the threat model there is an essential
need of finding the tractable solution.
Implementation: The solution that are found out are to be implemented in the existing
technologies and the infrastructure which will be initially followed by the comparison
of the solutions with the different types of threat models.
Different evaluation criteria for addressing the Security of the Big Data:
After analyzing the security challenges related to big data the following solutions can
be applied so as to eliminate all the risks. Some of the solutions are listed below:
One of the major thing that is to be included in the new security solution is the
extension of the secure perimeter of the big data from the enterprise to the public
cloud (Puthal et al. 2015). By adopting this method, a new trustful data provenance
mechanism will be created that will be initially helping in the mitigation of the risks
related to the DDoS attacks which are mainly launched against the infrastructures of
the big data.
There is a mandatory need of addressing the legal requirements by the mechanisms
regarding the handling of the data. One of the best way of securing the big data is by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the implementation of the secure Information technology. This encryption technology
is mainly used for the purpose of securing the confidential data and this might include
the PII, PHI, IP along with various encryption keys and many more (Arora Parashar
and Transforming 2013). This need to be done so as put the correct locking and
unlocking mechanism for the data. For this process to become successful there is an
essential need for making this mechanism transparent to the end-user along with
having a low impact of the performance and scalability of the data as well.
Beside the security recommendations there is an essential need for considering the
security of the IT infrastructure itself. The common practice regarding the security
includes placing of the security controls at the very edge of the network. In case if the
security perimeter is violated by the attacker then all the data present inside will be
accessed very easily (Ahmed and Hossain 2014). This leads to the need of new
security measures which can be done by moving the security controls near the big
data. By proper monitoring, analyzing and learning of the usage of the data along with
the access which is one of the important aspect for the continual improvement of the
security of the infrastructure that is holding the data. This will also leverage the
security measures that are existing right now.
Conclusion:
This report helps a lot in identifying the various gaps along with the various security
challenges that are related big data in the clouds. The report also helps in understanding the
fact that cloud computing is one of the emerging technology which is being adopted by
various organizations. This organizations design and develop their system for the purpose of
stay ahead in the market of competition. Besides the security challenges there are also other
technologies that are very much problematic and this includes the database, networking,
virtualization and also the operating system as well. This paper has used different studies for
is mainly used for the purpose of securing the confidential data and this might include
the PII, PHI, IP along with various encryption keys and many more (Arora Parashar
and Transforming 2013). This need to be done so as put the correct locking and
unlocking mechanism for the data. For this process to become successful there is an
essential need for making this mechanism transparent to the end-user along with
having a low impact of the performance and scalability of the data as well.
Beside the security recommendations there is an essential need for considering the
security of the IT infrastructure itself. The common practice regarding the security
includes placing of the security controls at the very edge of the network. In case if the
security perimeter is violated by the attacker then all the data present inside will be
accessed very easily (Ahmed and Hossain 2014). This leads to the need of new
security measures which can be done by moving the security controls near the big
data. By proper monitoring, analyzing and learning of the usage of the data along with
the access which is one of the important aspect for the continual improvement of the
security of the infrastructure that is holding the data. This will also leverage the
security measures that are existing right now.
Conclusion:
This report helps a lot in identifying the various gaps along with the various security
challenges that are related big data in the clouds. The report also helps in understanding the
fact that cloud computing is one of the emerging technology which is being adopted by
various organizations. This organizations design and develop their system for the purpose of
stay ahead in the market of competition. Besides the security challenges there are also other
technologies that are very much problematic and this includes the database, networking,
virtualization and also the operating system as well. This paper has used different studies for

the identification of the major problems related to the research. Along with this it also helps
in identifying the major things that are to be taken into account so as to make sure that the big
data are being moved toward the success. The report also helps in concluding that in the
Relational Database Management RDBM the problem regarding the protection of the system
from any kind of attack by making use of the resources along with which the only one
important problem is the mitigation of the risks. Various mitigation problems have been
discussed in this report and by the adaptation of this methods a great amount of risk will be
eliminated.
References:
Ahmed, M. and Hossain, M.A., 2014. Cloud computing and security issues in the
cloud. International Journal of Network Security & Its Applications, 6(1), p.25.
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities
and challenges. Information Sciences, 305, pp.357-383.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing
using encryption algorithms. International journal of engineering research and
applications, 3(4), pp.1922-1926.
Behl, A. and Behl, K., 2012, October. An analysis of cloud computing security issues.
In Information and Communication Technologies (WICT), 2012 World Congress on (pp. 109-
114). IEEE.
in identifying the major things that are to be taken into account so as to make sure that the big
data are being moved toward the success. The report also helps in concluding that in the
Relational Database Management RDBM the problem regarding the protection of the system
from any kind of attack by making use of the resources along with which the only one
important problem is the mitigation of the risks. Various mitigation problems have been
discussed in this report and by the adaptation of this methods a great amount of risk will be
eliminated.
References:
Ahmed, M. and Hossain, M.A., 2014. Cloud computing and security issues in the
cloud. International Journal of Network Security & Its Applications, 6(1), p.25.
Ali, M., Khan, S.U. and Vasilakos, A.V., 2015. Security in cloud computing: Opportunities
and challenges. Information Sciences, 305, pp.357-383.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Arora, R., Parashar, A. and Transforming, C.C.I., 2013. Secure user data in cloud computing
using encryption algorithms. International journal of engineering research and
applications, 3(4), pp.1922-1926.
Behl, A. and Behl, K., 2012, October. An analysis of cloud computing security issues.
In Information and Communication Technologies (WICT), 2012 World Congress on (pp. 109-
114). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





