Report on Information Threat Security for Cobweb Company
VerifiedAdded on 2020/01/28
|14
|3214
|48
Report
AI Summary
This report analyzes the information security threats faced by Cobweb, a web development company. It begins by identifying and describing the company's data and information assets, including databases, data files, software, and IT employees. The report then details the potential impact of various threats, such as hacking, data breaches, and employee negligence, on these assets. A vulnerability matrix is presented to illustrate the relationship between assets and threats. The report further calculates risk factors, including hazard, exposure, and probability ratings, to assess the overall risk level. Finally, it proposes suitable countermeasures, such as backup methods and proper system maintenance, along with justifications for their implementation, to mitigate the identified risks and protect Cobweb's valuable data and operations. The report emphasizes the importance of proactive security measures to safeguard against potential threats.

INFORMATION THREAT SECURITY
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction..........................................................................................................................................3
Q.1 Describing the data and information assets associated with Cobweb.......................................3
Q. 2 Describing impact of all threats on the identified data assets.................................................4
Q. 3Examining each asset– threat pairing and produce a vulnerability matrix ..............................5
Q. 4 Assuming there are no specific controls in place to protect the data assets in question. You
may assume general controls such as anti-virus software, logical access controls etc. are already
in place., however for completeness, you may want to list these as well and then ‘cross them off’
as already existing controls..............................................................................................................6
5. Calculation of risk factors ...........................................................................................................7
Q. 6 and 7. Reasonable risk appetite value and propose suitable countermeasures with
justifications ....................................................................................................................................7
Conclusion............................................................................................................................................9
References..........................................................................................................................................10
2
Introduction..........................................................................................................................................3
Q.1 Describing the data and information assets associated with Cobweb.......................................3
Q. 2 Describing impact of all threats on the identified data assets.................................................4
Q. 3Examining each asset– threat pairing and produce a vulnerability matrix ..............................5
Q. 4 Assuming there are no specific controls in place to protect the data assets in question. You
may assume general controls such as anti-virus software, logical access controls etc. are already
in place., however for completeness, you may want to list these as well and then ‘cross them off’
as already existing controls..............................................................................................................6
5. Calculation of risk factors ...........................................................................................................7
Q. 6 and 7. Reasonable risk appetite value and propose suitable countermeasures with
justifications ....................................................................................................................................7
Conclusion............................................................................................................................................9
References..........................................................................................................................................10
2

Illustration Index
Illustration 1: Reasonable risk appetite value.....................................................................................10
3
Illustration 1: Reasonable risk appetite value.....................................................................................10
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Index of Tables
Table 1: Mcleod, 2008Vulnerability matrix.........................................................................................7
Table 2: List of controls........................................................................................................................8
Table 3: Calculation of risk factors ......................................................................................................9
4
Table 1: Mcleod, 2008Vulnerability matrix.........................................................................................7
Table 2: List of controls........................................................................................................................8
Table 3: Calculation of risk factors ......................................................................................................9
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Information security threat is big issue for all IT and other organisations in the world. It
steals important data of company through hacking, security breach, phishing, virus as well as SQL
injection. Cobweb is a web site development company which provides effective IT services to
industrial and domestic consumers in the United Kingdom (Karnouskos, 2011). The present report
describes the data and information assets of organisation. Further, it represents the impact of threats
on the identified data assets of Cobweb firm. In addition to this, it also introduces formula to
evaluate the risk factors for corporation in the market. It suggests proper recommendations to avoid
the information security threats for enterprise.
Q.1 Describing the data and information assets associated with Cobweb
Cobweb has many data and information assets like databases, data files and various types of
software to manage its IT operations in a appropriate manner.
Databases: Database server is valuable asset for organisation which contribute effectively to
store its different type of information for long time. It helps the firm to manage various type
of data in a appropriate manner which help to take effective decision for its more
development. In addition to this, it aids the Cobweb to provide better services as per
demands of the consumers in the IT industry (Bruce and Ho, 2009). Database servers
provides effective security for corporation to save its data from unauthorized users by using
IPV 6 and firewalls. These tools play important role for Cobweb to reduce chances of
hacking. Further, they also provide reliability to management of organisation to handle its
business activities in a better way.
Data files: Data files are important for Cobweb organisation because it stores specific data
of client like coding of websites and their additional information. Along with this, they
contain other data of various types of field like accounts, finance and operations (Dhillon,
2007). So data files are important for Cobweb to reduce redundancy in the work which
contribute effectively to increase its efficiency as well as performance in the market.
Software: Software is valuable assets for Cobweb which helps to feed data into database.
Generally, it is divided in system and application software which help to manage its
organisational operations. Organisation use DBMS, operating systems, software packages,
development tools and utilities as well as office productivity suites. These approaches help
the management of Cobweb to develop effective website for its clients (Gertz and Jajodia,
2007). In addition to this, corporation also uses enterprise resources planning to access the
fast information which support managers and employees to take fast decision. Further,
5
Information security threat is big issue for all IT and other organisations in the world. It
steals important data of company through hacking, security breach, phishing, virus as well as SQL
injection. Cobweb is a web site development company which provides effective IT services to
industrial and domestic consumers in the United Kingdom (Karnouskos, 2011). The present report
describes the data and information assets of organisation. Further, it represents the impact of threats
on the identified data assets of Cobweb firm. In addition to this, it also introduces formula to
evaluate the risk factors for corporation in the market. It suggests proper recommendations to avoid
the information security threats for enterprise.
Q.1 Describing the data and information assets associated with Cobweb
Cobweb has many data and information assets like databases, data files and various types of
software to manage its IT operations in a appropriate manner.
Databases: Database server is valuable asset for organisation which contribute effectively to
store its different type of information for long time. It helps the firm to manage various type
of data in a appropriate manner which help to take effective decision for its more
development. In addition to this, it aids the Cobweb to provide better services as per
demands of the consumers in the IT industry (Bruce and Ho, 2009). Database servers
provides effective security for corporation to save its data from unauthorized users by using
IPV 6 and firewalls. These tools play important role for Cobweb to reduce chances of
hacking. Further, they also provide reliability to management of organisation to handle its
business activities in a better way.
Data files: Data files are important for Cobweb organisation because it stores specific data
of client like coding of websites and their additional information. Along with this, they
contain other data of various types of field like accounts, finance and operations (Dhillon,
2007). So data files are important for Cobweb to reduce redundancy in the work which
contribute effectively to increase its efficiency as well as performance in the market.
Software: Software is valuable assets for Cobweb which helps to feed data into database.
Generally, it is divided in system and application software which help to manage its
organisational operations. Organisation use DBMS, operating systems, software packages,
development tools and utilities as well as office productivity suites. These approaches help
the management of Cobweb to develop effective website for its clients (Gertz and Jajodia,
2007). In addition to this, corporation also uses enterprise resources planning to access the
fast information which support managers and employees to take fast decision. Further,
5

management of Cobweb gives better IT facilities by developing better websites to its
consumers which fulfil their needs in a better way. (Karnouskos, 2011)
IT employees: They are most important assets for Cobweb to manage its development of
websites. Staff members help the organisation to design various types of websites as per
demand of client with help of development tools. This asset support the corporation to
increase its market growth and share in the IT sector of United Kingdom. In addition to this,
employees of Cobweb also play important role to manage database, data files as well as
software (Identifying and classifying assets. 2010). Further, they provide effective reliability
to expand business activities of organisation in the various areas of UK.
These data and information contribute effective role of Cobweb to secure the information in
a appropriate manner. Organisation can identify these mechanisms through suggestion of IT experts
as well as analysing importance of data assets (Bahl and Wali, 2014).
Q. 2 Describing impact of all threats on the identified data assets
Impact of identified threats of data and information assets can be very high for the
organisation. Due to these reasons, management of corporation can face severe results. Further, it
can also create huge of loss of monetary funds which can create higher complexities to manage the
operations of Cobweb(Katerina and et.al., 2009). Further, these threats produce issues to fulfil needs
of clients by not giving IT services on time.
Threat on the database can create negative on the performance of organisation in the market.
Further, hacking, phishing, trozen, worms as well as viruses also increases issues of Cobweb
to manage development of websites.
These type of hacking can reduces efficiency and performance of database servers of
organization. As a result, it can create complexities to access organisational data in the
Cobweb (Pokorny and et.al., 2011).
Some times, they can delete important data of company which can create problems to
retrieve the important data. Fuhrer, management of Cobweb realise issues to provide better
IT services to its clients.
They can also crash the database which create complexities for organisation to access the
past data. Further, it create problems for Cobweb to meet deadline of clients which increases
the complaints of clients.
Threat on data files can create higher impact on the organisation which can delay work of
clients (Silberschatz, Korth and Sudarshan, 2011). Some times, hackers can steal important
6
consumers which fulfil their needs in a better way. (Karnouskos, 2011)
IT employees: They are most important assets for Cobweb to manage its development of
websites. Staff members help the organisation to design various types of websites as per
demand of client with help of development tools. This asset support the corporation to
increase its market growth and share in the IT sector of United Kingdom. In addition to this,
employees of Cobweb also play important role to manage database, data files as well as
software (Identifying and classifying assets. 2010). Further, they provide effective reliability
to expand business activities of organisation in the various areas of UK.
These data and information contribute effective role of Cobweb to secure the information in
a appropriate manner. Organisation can identify these mechanisms through suggestion of IT experts
as well as analysing importance of data assets (Bahl and Wali, 2014).
Q. 2 Describing impact of all threats on the identified data assets
Impact of identified threats of data and information assets can be very high for the
organisation. Due to these reasons, management of corporation can face severe results. Further, it
can also create huge of loss of monetary funds which can create higher complexities to manage the
operations of Cobweb(Katerina and et.al., 2009). Further, these threats produce issues to fulfil needs
of clients by not giving IT services on time.
Threat on the database can create negative on the performance of organisation in the market.
Further, hacking, phishing, trozen, worms as well as viruses also increases issues of Cobweb
to manage development of websites.
These type of hacking can reduces efficiency and performance of database servers of
organization. As a result, it can create complexities to access organisational data in the
Cobweb (Pokorny and et.al., 2011).
Some times, they can delete important data of company which can create problems to
retrieve the important data. Fuhrer, management of Cobweb realise issues to provide better
IT services to its clients.
They can also crash the database which create complexities for organisation to access the
past data. Further, it create problems for Cobweb to meet deadline of clients which increases
the complaints of clients.
Threat on data files can create higher impact on the organisation which can delay work of
clients (Silberschatz, Korth and Sudarshan, 2011). Some times, hackers can steal important
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

data files which can leak important and sensitive information of Cobweb. These type of
threat can increase the workload on the employees which can enhances of expenditure of
company.
In addition to this, stealing of data files also break integrity of data which create problems
to continue the further wok in the Cobweb (Fenz, and et.al., 2014).
Threat on software is high for organisation because firm reduces its efficiency and
performance regarding work. Hackers also hack organisational servers to take data of
enterprise which also crash software. Due to this reason, employee are unable to work on
servers which create issues of management of Cobweb to manage the work (Aggeliki
Tsohou and et.al., 2012). In addition to this, it increases work pressure of IT experts to
manage data in a appropriate manner.
Threat on IT experts also create negative impact on the corporation. Information security
threat also increase work on the staff members which reduces overall efficiency of them in
the Cobweb (Sommestad and et.al.,2011).
Q. 3Examining each asset– threat pairing and produce a vulnerability matrix
Generally vulnerability matrix is used to analyse the various type of risks in the
organisation. It helps the firm to develop proper strategies to reduce uncertainties which support to
decrease any kind of loss (Renfroe, 2016). It is described below in the table.
7
threat can increase the workload on the employees which can enhances of expenditure of
company.
In addition to this, stealing of data files also break integrity of data which create problems
to continue the further wok in the Cobweb (Fenz, and et.al., 2014).
Threat on software is high for organisation because firm reduces its efficiency and
performance regarding work. Hackers also hack organisational servers to take data of
enterprise which also crash software. Due to this reason, employee are unable to work on
servers which create issues of management of Cobweb to manage the work (Aggeliki
Tsohou and et.al., 2012). In addition to this, it increases work pressure of IT experts to
manage data in a appropriate manner.
Threat on IT experts also create negative impact on the corporation. Information security
threat also increase work on the staff members which reduces overall efficiency of them in
the Cobweb (Sommestad and et.al.,2011).
Q. 3Examining each asset– threat pairing and produce a vulnerability matrix
Generally vulnerability matrix is used to analyse the various type of risks in the
organisation. It helps the firm to develop proper strategies to reduce uncertainties which support to
decrease any kind of loss (Renfroe, 2016). It is described below in the table.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
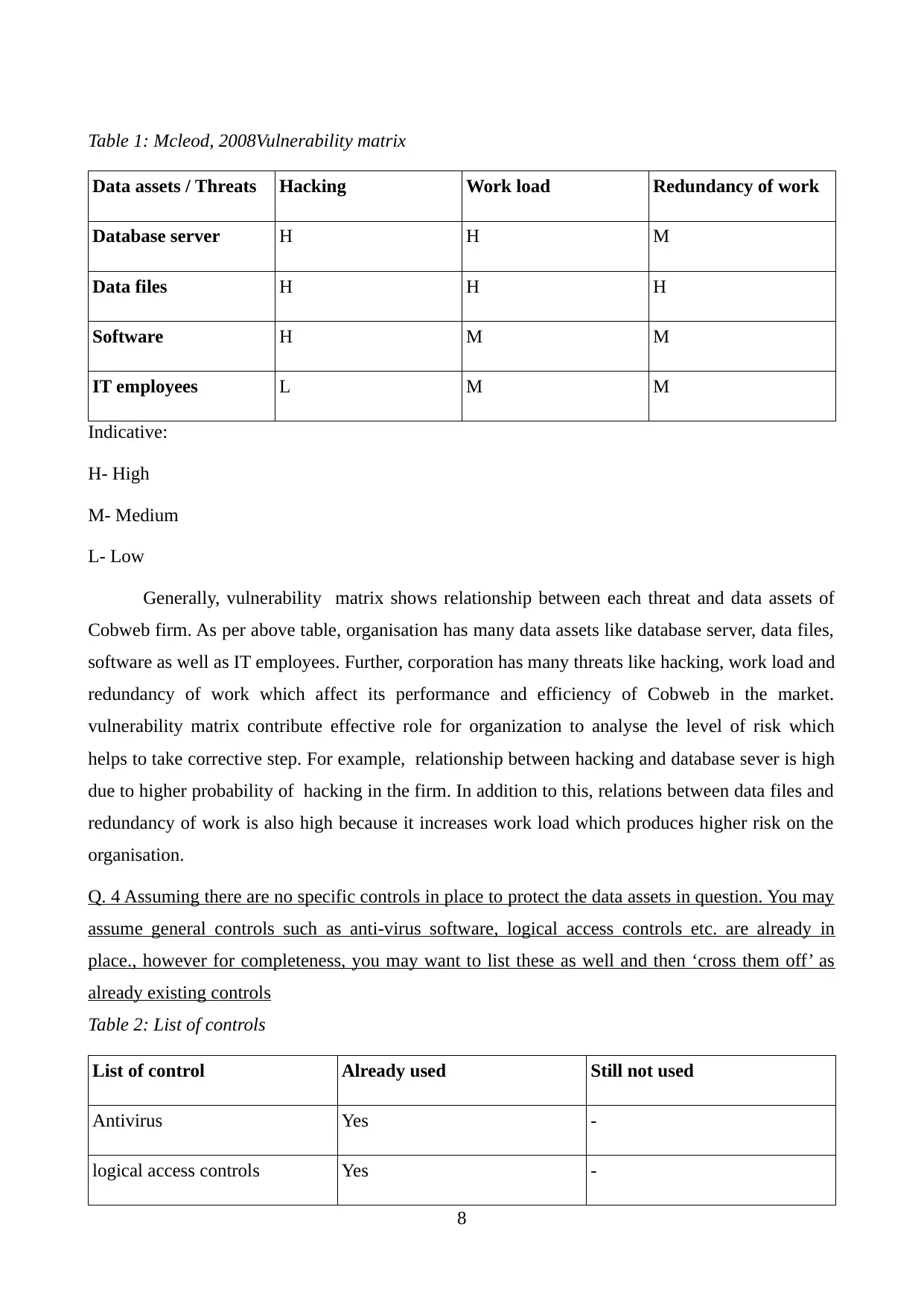
Table 1: Mcleod, 2008Vulnerability matrix
Data assets / Threats Hacking Work load Redundancy of work
Database server H H M
Data files H H H
Software H M M
IT employees L M M
Indicative:
H- High
M- Medium
L- Low
Generally, vulnerability matrix shows relationship between each threat and data assets of
Cobweb firm. As per above table, organisation has many data assets like database server, data files,
software as well as IT employees. Further, corporation has many threats like hacking, work load and
redundancy of work which affect its performance and efficiency of Cobweb in the market.
vulnerability matrix contribute effective role for organization to analyse the level of risk which
helps to take corrective step. For example, relationship between hacking and database sever is high
due to higher probability of hacking in the firm. In addition to this, relations between data files and
redundancy of work is also high because it increases work load which produces higher risk on the
organisation.
Q. 4 Assuming there are no specific controls in place to protect the data assets in question. You may
assume general controls such as anti-virus software, logical access controls etc. are already in
place., however for completeness, you may want to list these as well and then ‘cross them off’ as
already existing controls
Table 2: List of controls
List of control Already used Still not used
Antivirus Yes -
logical access controls Yes -
8
Data assets / Threats Hacking Work load Redundancy of work
Database server H H M
Data files H H H
Software H M M
IT employees L M M
Indicative:
H- High
M- Medium
L- Low
Generally, vulnerability matrix shows relationship between each threat and data assets of
Cobweb firm. As per above table, organisation has many data assets like database server, data files,
software as well as IT employees. Further, corporation has many threats like hacking, work load and
redundancy of work which affect its performance and efficiency of Cobweb in the market.
vulnerability matrix contribute effective role for organization to analyse the level of risk which
helps to take corrective step. For example, relationship between hacking and database sever is high
due to higher probability of hacking in the firm. In addition to this, relations between data files and
redundancy of work is also high because it increases work load which produces higher risk on the
organisation.
Q. 4 Assuming there are no specific controls in place to protect the data assets in question. You may
assume general controls such as anti-virus software, logical access controls etc. are already in
place., however for completeness, you may want to list these as well and then ‘cross them off’ as
already existing controls
Table 2: List of controls
List of control Already used Still not used
Antivirus Yes -
logical access controls Yes -
8
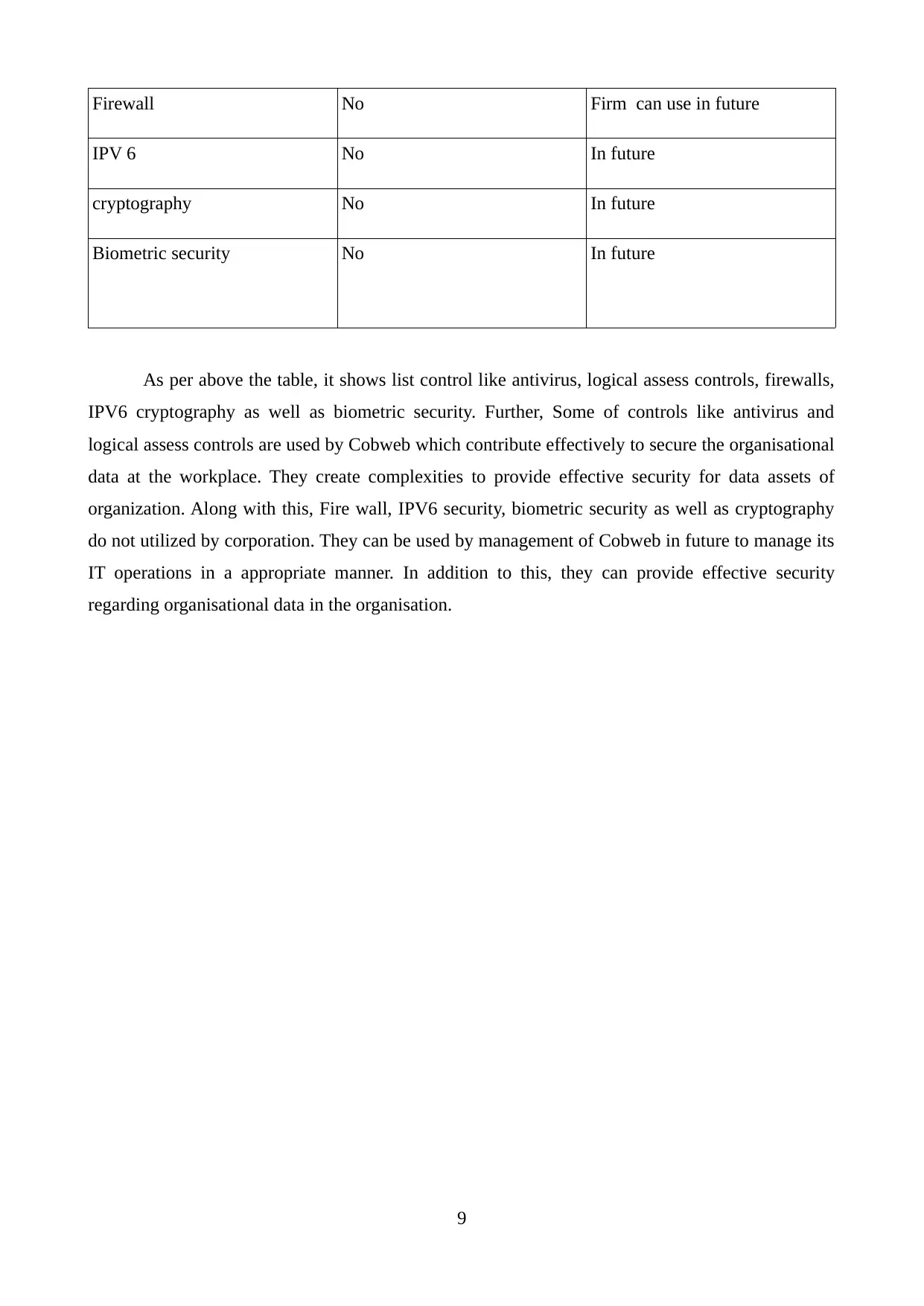
Firewall No Firm can use in future
IPV 6 No In future
cryptography No In future
Biometric security No In future
As per above the table, it shows list control like antivirus, logical assess controls, firewalls,
IPV6 cryptography as well as biometric security. Further, Some of controls like antivirus and
logical assess controls are used by Cobweb which contribute effectively to secure the organisational
data at the workplace. They create complexities to provide effective security for data assets of
organization. Along with this, Fire wall, IPV6 security, biometric security as well as cryptography
do not utilized by corporation. They can be used by management of Cobweb in future to manage its
IT operations in a appropriate manner. In addition to this, they can provide effective security
regarding organisational data in the organisation.
9
IPV 6 No In future
cryptography No In future
Biometric security No In future
As per above the table, it shows list control like antivirus, logical assess controls, firewalls,
IPV6 cryptography as well as biometric security. Further, Some of controls like antivirus and
logical assess controls are used by Cobweb which contribute effectively to secure the organisational
data at the workplace. They create complexities to provide effective security for data assets of
organization. Along with this, Fire wall, IPV6 security, biometric security as well as cryptography
do not utilized by corporation. They can be used by management of Cobweb in future to manage its
IT operations in a appropriate manner. In addition to this, they can provide effective security
regarding organisational data in the organisation.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
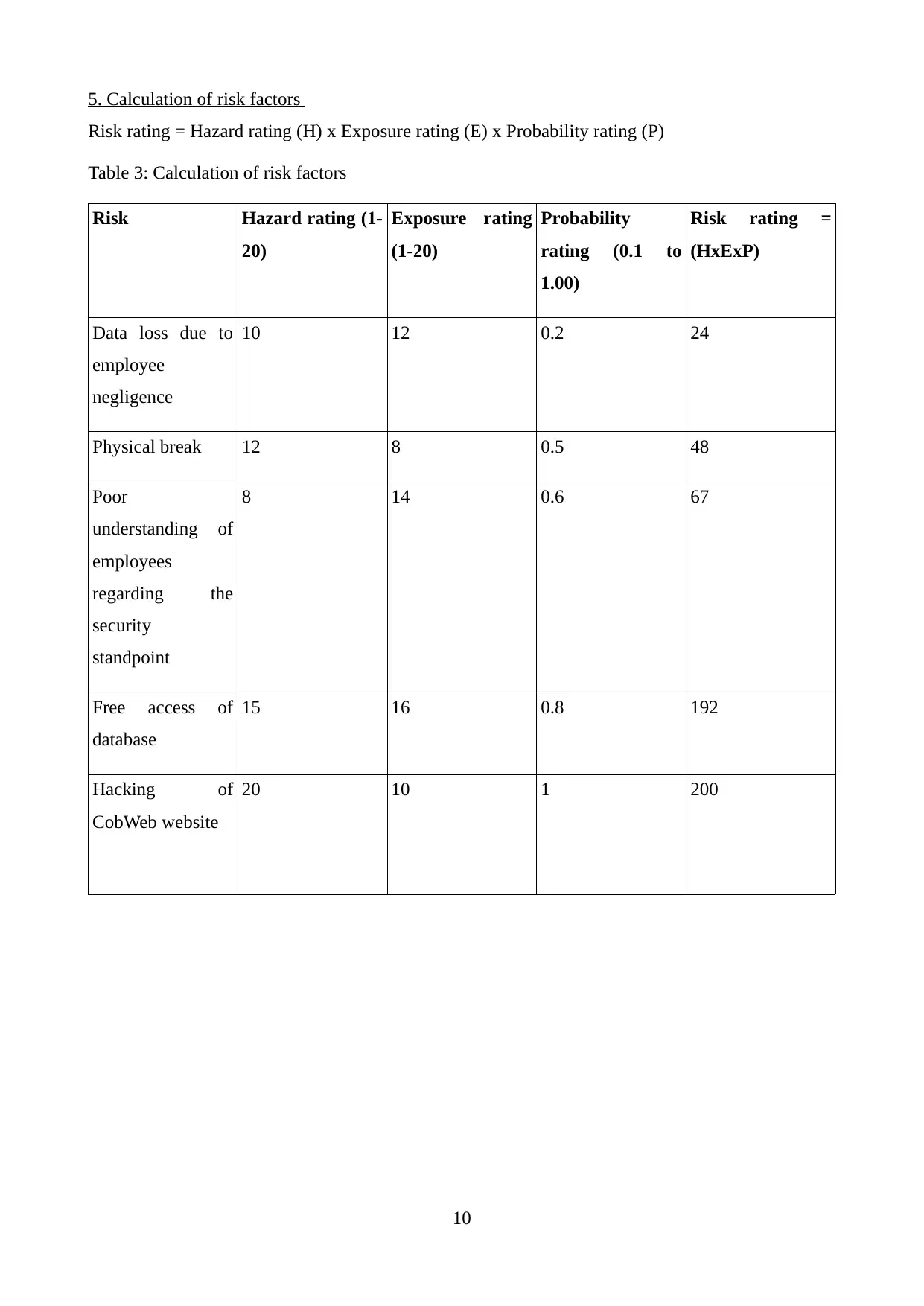
5. Calculation of risk factors
Risk rating = Hazard rating (H) x Exposure rating (E) x Probability rating (P)
Table 3: Calculation of risk factors
Risk Hazard rating (1-
20)
Exposure rating
(1-20)
Probability
rating (0.1 to
1.00)
Risk rating =
(HxExP)
Data loss due to
employee
negligence
10 12 0.2 24
Physical break 12 8 0.5 48
Poor
understanding of
employees
regarding the
security
standpoint
8 14 0.6 67
Free access of
database
15 16 0.8 192
Hacking of
CobWeb website
20 10 1 200
10
Risk rating = Hazard rating (H) x Exposure rating (E) x Probability rating (P)
Table 3: Calculation of risk factors
Risk Hazard rating (1-
20)
Exposure rating
(1-20)
Probability
rating (0.1 to
1.00)
Risk rating =
(HxExP)
Data loss due to
employee
negligence
10 12 0.2 24
Physical break 12 8 0.5 48
Poor
understanding of
employees
regarding the
security
standpoint
8 14 0.6 67
Free access of
database
15 16 0.8 192
Hacking of
CobWeb website
20 10 1 200
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
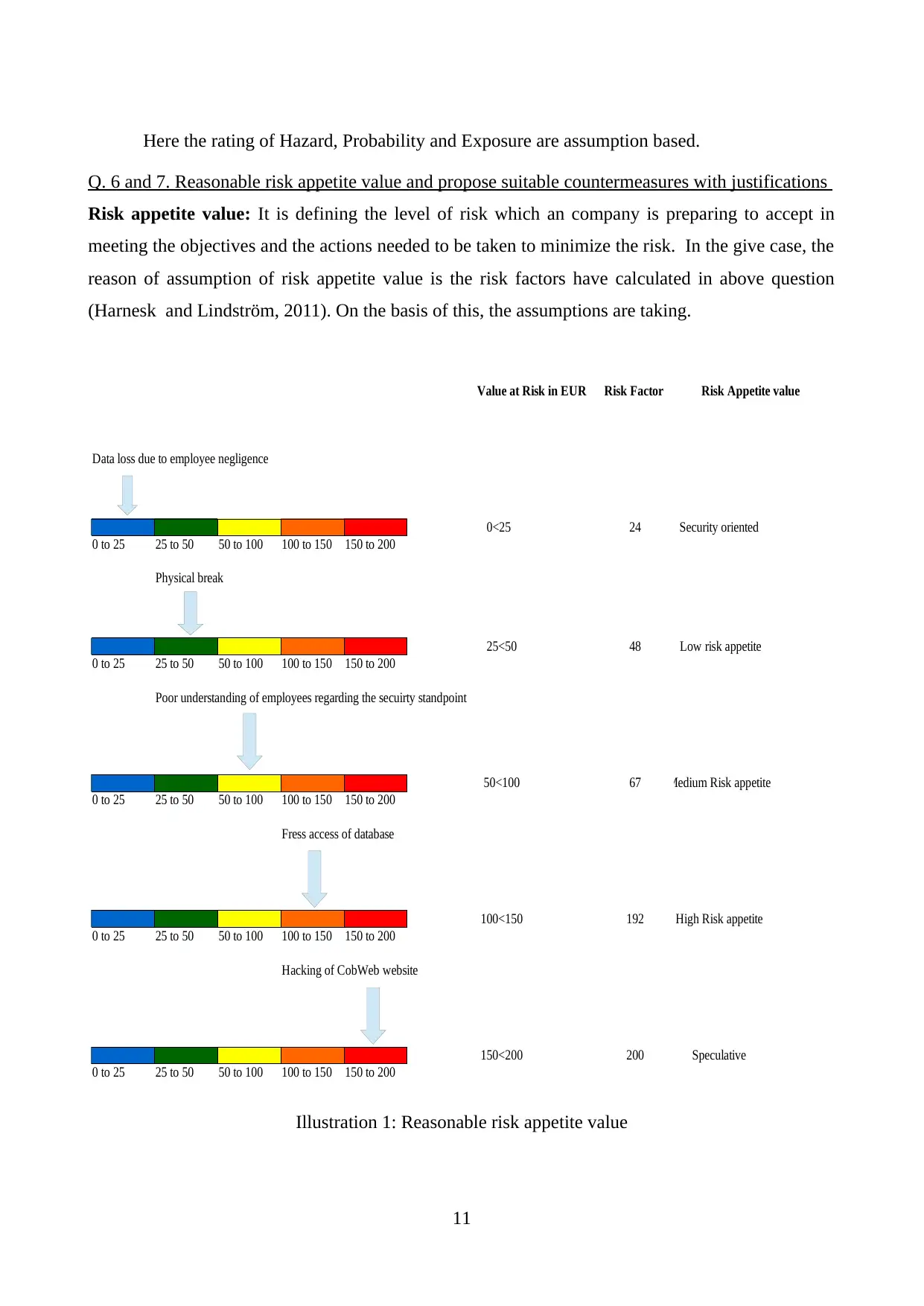
Here the rating of Hazard, Probability and Exposure are assumption based.
Q. 6 and 7. Reasonable risk appetite value and propose suitable countermeasures with justifications
Risk appetite value: It is defining the level of risk which an company is preparing to accept in
meeting the objectives and the actions needed to be taken to minimize the risk. In the give case, the
reason of assumption of risk appetite value is the risk factors have calculated in above question
(Harnesk and Lindström, 2011). On the basis of this, the assumptions are taking.
11
Value at Risk in EUR Risk Factor Risk Appetite value
Data loss due to employee negligence
0<25 24 Security oriented
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Physical break
25<50 48 Low risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Poor understanding of employees regarding the secuirty standpoint
50<100 67 Medium Risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Fress access of database
100<150 192 High Risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Hacking of CobWeb website
150<200 200 Speculative
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Illustration 1: Reasonable risk appetite value
Q. 6 and 7. Reasonable risk appetite value and propose suitable countermeasures with justifications
Risk appetite value: It is defining the level of risk which an company is preparing to accept in
meeting the objectives and the actions needed to be taken to minimize the risk. In the give case, the
reason of assumption of risk appetite value is the risk factors have calculated in above question
(Harnesk and Lindström, 2011). On the basis of this, the assumptions are taking.
11
Value at Risk in EUR Risk Factor Risk Appetite value
Data loss due to employee negligence
0<25 24 Security oriented
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Physical break
25<50 48 Low risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Poor understanding of employees regarding the secuirty standpoint
50<100 67 Medium Risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Fress access of database
100<150 192 High Risk appetite
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Hacking of CobWeb website
150<200 200 Speculative
0 to 25 25 to 50 50 to 100 100 to 150 150 to 200
Illustration 1: Reasonable risk appetite value

Suitable countermeasures for the accessing risk
Backup method: Data loss due to employee negligence is a big thing for every organization. To
solve this problem, the IT security professional of CobWeb has to create the awareness in the
employees to save every data and information (Järveläinen, 2012). Along with this, he should be
adopt different backup methods so that the automatic backup can be start within a give time frame.
It will save all the data automatic on the server if some time staff show negligence behaviour.
Proper maintenance : Physical break of a system is a major risk which has affected the working of
the CobWeb because the breakdown in machines has slow down all the process (Ngoqo and
Flowerday, 2015). To overcome the appearance of this situation again and again, IT professional
should ensure the proper maintenance of the systems and other hardware. By doing this, it will easy
to resolve the continuous problem of system breakdown and save then data secure and safe.
Training: Most of the time, employees complain that they do not understand what is expected of
them from a security standpoint (Pathari and Sonar, 2013). In this situation, It professional of
CobWeb should give training to the employees. It will assist them to learn the different software and
their working. By thing, they will able to understand the security aspect and gain the knowledge to
work on the security methods.
Use security code on networks: Network administrator of CobWeb complains that the company
allows free access to anything on the network for every employee. It has increased the risk of data
loss and use it for the personal benefits (Shaaban. and Conrad, 2013). To minimize this risk, IT
professional of the company should apply some security codes on the data and the password only
give to some responsible persons. By limited access, the staff members will not easily access the
information and it will save the data for the long time.
CONCLUSION
From the report, it is found that IT employees, database, data files as well as software help the
organisation to manage its operations. Further, effect of threat on identified data assets creates bad
impact on the performance and efficiency of organisation. In addition to this, Vulnerability matrix
contribute effective role for Cobweb to analyse its risks in a appropriate manner. It has been found
that there are different kinds of assets for the company. But the threats have affected these data
assets in negative manner. With the help of various type of control measure, the threats can be
minimized.
12
Backup method: Data loss due to employee negligence is a big thing for every organization. To
solve this problem, the IT security professional of CobWeb has to create the awareness in the
employees to save every data and information (Järveläinen, 2012). Along with this, he should be
adopt different backup methods so that the automatic backup can be start within a give time frame.
It will save all the data automatic on the server if some time staff show negligence behaviour.
Proper maintenance : Physical break of a system is a major risk which has affected the working of
the CobWeb because the breakdown in machines has slow down all the process (Ngoqo and
Flowerday, 2015). To overcome the appearance of this situation again and again, IT professional
should ensure the proper maintenance of the systems and other hardware. By doing this, it will easy
to resolve the continuous problem of system breakdown and save then data secure and safe.
Training: Most of the time, employees complain that they do not understand what is expected of
them from a security standpoint (Pathari and Sonar, 2013). In this situation, It professional of
CobWeb should give training to the employees. It will assist them to learn the different software and
their working. By thing, they will able to understand the security aspect and gain the knowledge to
work on the security methods.
Use security code on networks: Network administrator of CobWeb complains that the company
allows free access to anything on the network for every employee. It has increased the risk of data
loss and use it for the personal benefits (Shaaban. and Conrad, 2013). To minimize this risk, IT
professional of the company should apply some security codes on the data and the password only
give to some responsible persons. By limited access, the staff members will not easily access the
information and it will save the data for the long time.
CONCLUSION
From the report, it is found that IT employees, database, data files as well as software help the
organisation to manage its operations. Further, effect of threat on identified data assets creates bad
impact on the performance and efficiency of organisation. In addition to this, Vulnerability matrix
contribute effective role for Cobweb to analyse its risks in a appropriate manner. It has been found
that there are different kinds of assets for the company. But the threats have affected these data
assets in negative manner. With the help of various type of control measure, the threats can be
minimized.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





