(PDF) Overview of Linux Vulnerabilities
4 Pages3364 Words70 Views
Added on 2021-10-01
(PDF) Overview of Linux Vulnerabilities
Added on 2021-10-01
ShareRelated Documents
Overview of Linux Vulnerabilities
Shuangxia Niu
State Grid HAEPC Electric Power Research Institute
Henan, China
e-mail: sxniu wang@163.com
Jiansong Mo
State Grid HAEPC Electric Power Research Institute
Henan EPRI GAOKE Group Co. Ltd
Henan, China
e-mail: jiansong mo@yahoo.com.cn
Zhigang Zhang
State Grid HAEPC Electric Power Research Institute
Henan EPRI GAOKE Group Co. Ltd
Henan, China
e-mail: zhuanzhuan2325@sina.com.cn
Zhuo Lv
State Grid HAEPC Electric Power Research Institute
Henan, China
e-mail: 15838150770@126.com
Abstract—Various advanced key technologies can be
effectively implemented on Linux cause its stability, high
efficiency and open source nature. However, Linux
Operating System(OS) itself and some of the services
Linux-based inevitably have their vulnerability, namely
Linux is not absolutely safe. This paper attempts to review
and discuss the Linux vulnerabilities, which originates from
Linux OS itself and some of the services shipped in Linux,
with related cases presented. And Linux security
enhancements, Linux OS hardening and Linux Security
Modules (LSM),are systematically described and studied.
Keywords-Linux vulnerabilities ;security measures;
harden -ing; LSM
I. INTRODUCTION
Recently Linux OS is widely used from embedded
systems to mainframes, supercomputers and servers, from
education and science research to industry, commerce and
national defense etc. Linux OS, a free and open source
software collaboration: the underlying source code may be
utilized, modified and distributed, by anyone under
licenses such as the GNU General Public License[1],
therefore advanced key technologies can be rapidly
implemented on Linux. However rapid development can
also cause unexpected vulnerabilities which can be abused
by malicious users for their attacks. By this reason, It is
necessary to understand the existing vulnerabilities and
related measures in Linux. Up to now, actually, there are
lots of documents which aimed at a certain type of
vulnerability and related measures in Linux, but few of
them had an overview.
In this paper, the Linux vulnerabilities and related
security measures will be studied, reviewed and discussed
systematically.
II. BACKGROUND
Let’s start by taking a quick look at the volume of
vulnerabilities over the last 26 years, as is shown in Figure
1 below[2][3].
This presents that the number of discovered and
reported vulnerabilities in 2013 has a slight decline than
2012, but is markedly more than any year before 2005.
Surprisely, the Linux kernel was having the most CVE
(Common Vulnerabilities and Exposures ) vulnerabilities
of all other products from 1988 to 2012,and the
distribution in four mainstream LINUX version is
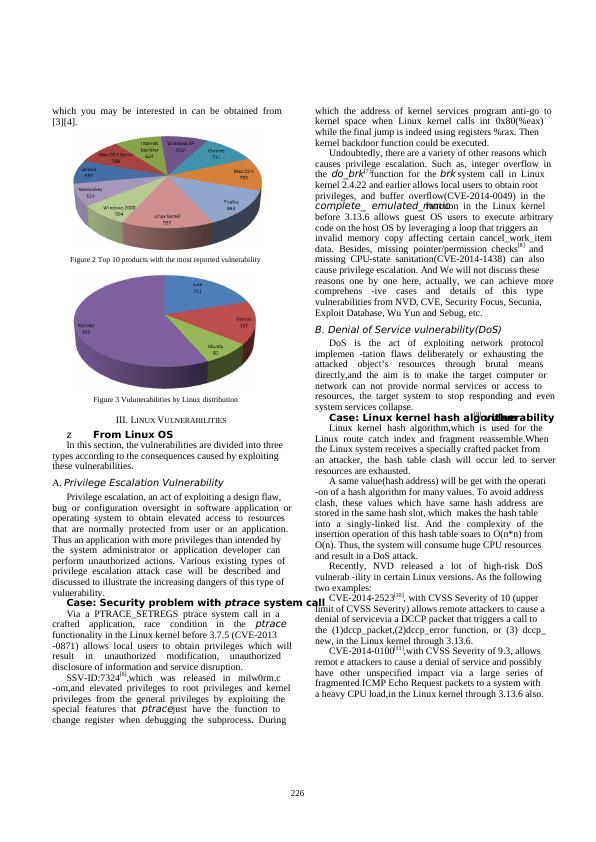
presented, as shown in Figure 2 and 3 [2] respectively. The
following data tells us a few interesting but serious things
worth noting. More vulnerabilities information in 2013
Figure 1 Vulnerabilities by year
International Conference on on Soft Computing in Information Communication Technology (SCICT 2014)
© 2014. The authors - Published by Atlantis Press 225
Shuangxia Niu
State Grid HAEPC Electric Power Research Institute
Henan, China
e-mail: sxniu wang@163.com
Jiansong Mo
State Grid HAEPC Electric Power Research Institute
Henan EPRI GAOKE Group Co. Ltd
Henan, China
e-mail: jiansong mo@yahoo.com.cn
Zhigang Zhang
State Grid HAEPC Electric Power Research Institute
Henan EPRI GAOKE Group Co. Ltd
Henan, China
e-mail: zhuanzhuan2325@sina.com.cn
Zhuo Lv
State Grid HAEPC Electric Power Research Institute
Henan, China
e-mail: 15838150770@126.com
Abstract—Various advanced key technologies can be
effectively implemented on Linux cause its stability, high
efficiency and open source nature. However, Linux
Operating System(OS) itself and some of the services
Linux-based inevitably have their vulnerability, namely
Linux is not absolutely safe. This paper attempts to review
and discuss the Linux vulnerabilities, which originates from
Linux OS itself and some of the services shipped in Linux,
with related cases presented. And Linux security
enhancements, Linux OS hardening and Linux Security
Modules (LSM),are systematically described and studied.
Keywords-Linux vulnerabilities ;security measures;
harden -ing; LSM
I. INTRODUCTION
Recently Linux OS is widely used from embedded
systems to mainframes, supercomputers and servers, from
education and science research to industry, commerce and
national defense etc. Linux OS, a free and open source
software collaboration: the underlying source code may be
utilized, modified and distributed, by anyone under
licenses such as the GNU General Public License[1],
therefore advanced key technologies can be rapidly
implemented on Linux. However rapid development can
also cause unexpected vulnerabilities which can be abused
by malicious users for their attacks. By this reason, It is
necessary to understand the existing vulnerabilities and
related measures in Linux. Up to now, actually, there are
lots of documents which aimed at a certain type of
vulnerability and related measures in Linux, but few of
them had an overview.
In this paper, the Linux vulnerabilities and related
security measures will be studied, reviewed and discussed
systematically.
II. BACKGROUND
Let’s start by taking a quick look at the volume of
vulnerabilities over the last 26 years, as is shown in Figure
1 below[2][3].
This presents that the number of discovered and
reported vulnerabilities in 2013 has a slight decline than
2012, but is markedly more than any year before 2005.
Surprisely, the Linux kernel was having the most CVE
(Common Vulnerabilities and Exposures ) vulnerabilities
of all other products from 1988 to 2012,and the
distribution in four mainstream LINUX version is
presented, as shown in Figure 2 and 3 [2] respectively. The
following data tells us a few interesting but serious things
worth noting. More vulnerabilities information in 2013
Figure 1 Vulnerabilities by year
International Conference on on Soft Computing in Information Communication Technology (SCICT 2014)
© 2014. The authors - Published by Atlantis Press 225

which you may be interested in can be obtained from
[3][4].
Figure 2 Top 10 products with the most reported vulnerability
Figure 3 Vulunerabilities by Linux distribution
III. LINUX VULNERABILITIES
z From Linux OS
In this section, the vulnerabilities are divided into three
types according to the consequences caused by exploiting
these vulnerabilities.
A. Privilege Escalation Vulnerability
Privilege escalation, an act of exploiting a design flaw,
bug or configuration oversight in software application or
operating system to obtain elevated access to resources
that are normally protected from user or an application.
Thus an application with more privileges than intended by
the system administrator or application developer can
perform unauthorized actions. Various existing types of
privilege escalation attack case will be described and
discussed to illustrate the increasing dangers of this type of
vulnerability.
Case: Security problem with ptrace system call
Via a PTRACE_SETREGS ptrace system call in a
crafted application, race condition in the ptrace
functionality in the Linux kernel before 3.7.5 (CVE-2013
-0871) allows local users to obtain privileges which will
result in unauthorized modification, unauthorized
disclosure of information and service disruption.
SSV-ID:7324[6],which was released in milw0rm.c
-om,and elevated privileges to root privileges and kernel
privileges from the general privileges by exploiting the
special features that ptrace just have the function to
change register when debugging the subprocess. During
which the address of kernel services program anti-go to
kernel space when Linux kernel calls int 0x80(%eax)
while the final jump is indeed using registers %rax. Then
kernel backdoor function could be executed.
Undoubtedly, there are a variety of other reasons which
causes privilege escalation. Such as, integer overflow in
the do_brk [7]function for the brk system call in Linux
kernel 2.4.22 and earlier allows local users to obtain root
privileges, and buffer overflow(CVE-2014-0049) in the
complete_ emulated_mmio function in the Linux kernel
before 3.13.6 allows guest OS users to execute arbitrary
code on the host OS by leveraging a loop that triggers an
invalid memory copy affecting certain cancel_work_item
data. Besides, missing pointer/permission checks[8] and
missing CPU-state sanitation(CVE-2014-1438) can also
cause privilege escalation. And We will not discuss these
reasons one by one here, actually, we can achieve more
comprehens -ive cases and details of this type
vulnerabilities from NVD, CVE, Security Focus, Secunia,
Exploit Database, Wu Yun and Sebug, etc.
B. Denial of Service vulnerability(DoS)
DoS is the act of exploiting network protocol
implemen -tation flaws deliberately or exhausting the
attacked object’s resources through brutal means
directly,and the aim is to make the target computer or
network can not provide normal services or access to
resources, the target system to stop responding and even
system services collapse.
Case: Linux kernel hash algorithm[9] vulnerability
Linux kernel hash algorithm,which is used for the
Linux route catch index and fragment reassemble.When
the Linux system receives a specially crafted packet from
an attacker, the hash table clash will occur led to server
resources are exhausted.
A same value(hash address) will be get with the operati
-on of a hash algorithm for many values. To avoid address
clash, these values which have same hash address are
stored in the same hash slot, which makes the hash table
into a singly-linked list. And the complexity of the
insertion operation of this hash table soars to O(n*n) from
O(n). Thus, the system will consume huge CPU resources
and result in a DoS attack.
Recently, NVD released a lot of high-risk DoS
vulnerab -ility in certain Linux versions. As the following
two examples:
CVE-2014-2523[10], with CVSS Severity of 10 (upper
limit of CVSS Severity) allows remote attackers to cause a
denial of servicevia a DCCP packet that triggers a call to
the (1)dccp_packet,(2)dccp_error function, or (3) dccp_
new, in the Linux kernel through 3.13.6.
CVE-2014-0100[11],with CVSS Severity of 9.3, allows
remot e attackers to cause a denial of service and possibly
have other unspecified impact via a large series of
fragmented ICMP Echo Request packets to a system with
a heavy CPU load,in the Linux kernel through 3.13.6 also.
226
[3][4].
Figure 2 Top 10 products with the most reported vulnerability
Figure 3 Vulunerabilities by Linux distribution
III. LINUX VULNERABILITIES
z From Linux OS
In this section, the vulnerabilities are divided into three
types according to the consequences caused by exploiting
these vulnerabilities.
A. Privilege Escalation Vulnerability
Privilege escalation, an act of exploiting a design flaw,
bug or configuration oversight in software application or
operating system to obtain elevated access to resources
that are normally protected from user or an application.
Thus an application with more privileges than intended by
the system administrator or application developer can
perform unauthorized actions. Various existing types of
privilege escalation attack case will be described and
discussed to illustrate the increasing dangers of this type of
vulnerability.
Case: Security problem with ptrace system call
Via a PTRACE_SETREGS ptrace system call in a
crafted application, race condition in the ptrace
functionality in the Linux kernel before 3.7.5 (CVE-2013
-0871) allows local users to obtain privileges which will
result in unauthorized modification, unauthorized
disclosure of information and service disruption.
SSV-ID:7324[6],which was released in milw0rm.c
-om,and elevated privileges to root privileges and kernel
privileges from the general privileges by exploiting the
special features that ptrace just have the function to
change register when debugging the subprocess. During
which the address of kernel services program anti-go to
kernel space when Linux kernel calls int 0x80(%eax)
while the final jump is indeed using registers %rax. Then
kernel backdoor function could be executed.
Undoubtedly, there are a variety of other reasons which
causes privilege escalation. Such as, integer overflow in
the do_brk [7]function for the brk system call in Linux
kernel 2.4.22 and earlier allows local users to obtain root
privileges, and buffer overflow(CVE-2014-0049) in the
complete_ emulated_mmio function in the Linux kernel
before 3.13.6 allows guest OS users to execute arbitrary
code on the host OS by leveraging a loop that triggers an
invalid memory copy affecting certain cancel_work_item
data. Besides, missing pointer/permission checks[8] and
missing CPU-state sanitation(CVE-2014-1438) can also
cause privilege escalation. And We will not discuss these
reasons one by one here, actually, we can achieve more
comprehens -ive cases and details of this type
vulnerabilities from NVD, CVE, Security Focus, Secunia,
Exploit Database, Wu Yun and Sebug, etc.
B. Denial of Service vulnerability(DoS)
DoS is the act of exploiting network protocol
implemen -tation flaws deliberately or exhausting the
attacked object’s resources through brutal means
directly,and the aim is to make the target computer or
network can not provide normal services or access to
resources, the target system to stop responding and even
system services collapse.
Case: Linux kernel hash algorithm[9] vulnerability
Linux kernel hash algorithm,which is used for the
Linux route catch index and fragment reassemble.When
the Linux system receives a specially crafted packet from
an attacker, the hash table clash will occur led to server
resources are exhausted.
A same value(hash address) will be get with the operati
-on of a hash algorithm for many values. To avoid address
clash, these values which have same hash address are
stored in the same hash slot, which makes the hash table
into a singly-linked list. And the complexity of the
insertion operation of this hash table soars to O(n*n) from
O(n). Thus, the system will consume huge CPU resources
and result in a DoS attack.
Recently, NVD released a lot of high-risk DoS
vulnerab -ility in certain Linux versions. As the following
two examples:
CVE-2014-2523[10], with CVSS Severity of 10 (upper
limit of CVSS Severity) allows remote attackers to cause a
denial of servicevia a DCCP packet that triggers a call to
the (1)dccp_packet,(2)dccp_error function, or (3) dccp_
new, in the Linux kernel through 3.13.6.
CVE-2014-0100[11],with CVSS Severity of 9.3, allows
remot e attackers to cause a denial of service and possibly
have other unspecified impact via a large series of
fragmented ICMP Echo Request packets to a system with
a heavy CPU load,in the Linux kernel through 3.13.6 also.
226
End of preview
Want to access all the pages? Upload your documents or become a member.
