International Journal of Computer Science & Information Technology Assignment 2022
Added on 2022-06-07
8 Pages4012 Words30 Views
International Journal of Computer Science & Information Technology (IJCSIT) Vol 9, No 6, December 2017
DOI:10.5121/ijcsit.2017.9606 59
DISTRIBUTED SCHEME TO AUTHENTICATE DATA
STORAGE SECURITY IN CLOUD COMPUTING
B. Rakesh1, K. Lalitha1, M. Ismail1 and H. Parveen Sultana2
1 Assistant Professor, Department of CSSE, SVEC (Autonomous)
2 Associate Professor, SCOPE, VIT University, Vellore, India
ABSTRACT
Cloud Computing is the revolution in current generation IT enterprise. Cloud computing displaces
database and application software to the large data centres, where the management of services and data
may not be predictable, where as the conventional solutions, for IT services are under proper logical,
physical and personal controls. This aspect attribute, however comprises different security challenges
which have not been well understood. It concentrates on cloud data storage security which has always been
an important aspect of quality of service (QOS). In this paper, we designed and simulated an adaptable and
efficient scheme to guarantee the correctness of user data stored in the cloud and also with some prominent
features. Homomorphic token is used for distributed verification of erasure – coded data. By using this
scheme, we can identify misbehaving servers. In spite of past works, our scheme supports effective and
secure dynamic operations on data blocks such as data insertion, deletion and modification. In contrast to
traditional solutions, where the IT services are under proper physical, logical and personnel controls,
cloud computing moves the application software and databases to the large data centres, where the data
management and services may not be absolutely truthful. This effective security and performance analysis
describes that the proposed scheme is extremely flexible against malicious data modification, convoluted
failures and server clouding attacks.
KEYWORDS
Cloud Computing, Cloud Storage Security, Homomorphic token, EC2, S3
1.INTRODUCTION
The Cloud Computing provides the service over the internet by using the computing resources i.e.
hardware and software. By using software as a service, users can access software and database in
the business model. The management of infrastructure and platform is done by using Cloud
providers. Sometimes, software as a service is referred to as on-demand software. Because of
that Cloud providers charged on pay per use basis. So this causes proponents to get the
computing resources in Outsourcing manner. That’s why the maintenance of hardware and
software is being reduced for users. Introducing of Cloud Computing avoids direct management
of hardware and it causes great convenience to users. Amazon Elastic Compute Cloud (EC2)
and Amazon Simple Storage Service (S3) are the best examples for initiators of Cloud
Computing. In the Cloud Computing the responsibility of local machines is eliminating due to
computing platform shift. Here in the Cloud Computing, the data is integrated so that’s why the
users are showing kindliness towards the cloud service providers.
Providing security to the data is a very important factor which has always been an important
factor of quality of service. Cloud Computing is exhibiting new challenges due to many reasons.
In Cloud Computing the very important thing is that data should be under the control of user. But
by using the traditional cryptographic techniques the users lose the control of data. So traditional
DOI:10.5121/ijcsit.2017.9606 59
DISTRIBUTED SCHEME TO AUTHENTICATE DATA
STORAGE SECURITY IN CLOUD COMPUTING
B. Rakesh1, K. Lalitha1, M. Ismail1 and H. Parveen Sultana2
1 Assistant Professor, Department of CSSE, SVEC (Autonomous)
2 Associate Professor, SCOPE, VIT University, Vellore, India
ABSTRACT
Cloud Computing is the revolution in current generation IT enterprise. Cloud computing displaces
database and application software to the large data centres, where the management of services and data
may not be predictable, where as the conventional solutions, for IT services are under proper logical,
physical and personal controls. This aspect attribute, however comprises different security challenges
which have not been well understood. It concentrates on cloud data storage security which has always been
an important aspect of quality of service (QOS). In this paper, we designed and simulated an adaptable and
efficient scheme to guarantee the correctness of user data stored in the cloud and also with some prominent
features. Homomorphic token is used for distributed verification of erasure – coded data. By using this
scheme, we can identify misbehaving servers. In spite of past works, our scheme supports effective and
secure dynamic operations on data blocks such as data insertion, deletion and modification. In contrast to
traditional solutions, where the IT services are under proper physical, logical and personnel controls,
cloud computing moves the application software and databases to the large data centres, where the data
management and services may not be absolutely truthful. This effective security and performance analysis
describes that the proposed scheme is extremely flexible against malicious data modification, convoluted
failures and server clouding attacks.
KEYWORDS
Cloud Computing, Cloud Storage Security, Homomorphic token, EC2, S3
1.INTRODUCTION
The Cloud Computing provides the service over the internet by using the computing resources i.e.
hardware and software. By using software as a service, users can access software and database in
the business model. The management of infrastructure and platform is done by using Cloud
providers. Sometimes, software as a service is referred to as on-demand software. Because of
that Cloud providers charged on pay per use basis. So this causes proponents to get the
computing resources in Outsourcing manner. That’s why the maintenance of hardware and
software is being reduced for users. Introducing of Cloud Computing avoids direct management
of hardware and it causes great convenience to users. Amazon Elastic Compute Cloud (EC2)
and Amazon Simple Storage Service (S3) are the best examples for initiators of Cloud
Computing. In the Cloud Computing the responsibility of local machines is eliminating due to
computing platform shift. Here in the Cloud Computing, the data is integrated so that’s why the
users are showing kindliness towards the cloud service providers.
Providing security to the data is a very important factor which has always been an important
factor of quality of service. Cloud Computing is exhibiting new challenges due to many reasons.
In Cloud Computing the very important thing is that data should be under the control of user. But
by using the traditional cryptographic techniques the users lose the control of data. So traditional

International Journal of Computer Science & Information Technology (IJCSIT) Vol 9, No 6, December 2017
60
Cryptographic primitives cannot be adopted directly. If we use the traditional Cryptographic
primitives directly, we will have conduct the verification for correctness of data stored in the
cloud without having the proper knowledge about the whole data. It is even more challenging
that to provide the continuous assurance of the data safety, if we store different categories of data
stored by different users.
The users are updating the data continuously stored in the cloud. The updation of the data
includes insertion, deletion, modification, appending, reordering etc. During the dynamic data
updation it is very important task that to assure the storage correctness of data. Techniques which
are used can be useful to give assurance to storage correctness without possessing data of user,
where it cannot addresses all the security threat of data storage in cloud, since they all
concentrating on single server situation and a large portion of them don't consider dynamic
operations on data. As a balancing approach, researchers have also proposed protocols which are
distributed for ensuring storage correctness data throughout multiple servers or peers. Again, in
these no distributed schemes is conscious about operations on dynamic data. As a result, their
applicability on cloud data storage can be considerably limited.
In this paper, we present a viable and flexible distributed scheme with dynamic data support
explicitly to verify the user’s data correctness in the cloud. We rely on erasure correcting code in
the file distribution preparation to provide redundancies and guarantee the data dependability.
This development radically diminishes the communication and storage overhead when contrasted
with the conventional techniques of replication-based file distribution. Utilization of
homomorphic token with distributed verification of erasure-coded data, this scheme achieves the
storage correctness insurance as well as data error localization: whenever data corruption has
been identified during the verification of storage correctness, this scheme can localize the data
errors concurrently, i.e., the identification of the misbehaving server(s).
• Compared to many of its predecessors, which only provide binary results about the
storage state across the distributed servers, the challenge-response protocol in our work
further provides the localization of data error.
• Dislike past works for guaranteeing data integrity remotely, on data blocks the new
scheme supports efficient and secure dynamic operations, which includes update, delete
and append.
• The highly efficient security and performance analysis shows that the proposed scheme is
extremely efficient and rigid against Byzantine failure, server colluding attack, , and even
malicious data modification attacks.
1.1 Cloud Data Storage Architecture
The network architecture for cloud data storage is as represented in the figure1. The architecture
is consisting of three different network modules as represented below:
Users: There are different categories of users. The users consisting of both organizations and
individual users. The users are having the data to store in the cloud. The users must have the trust
on the cloud computation.
Cloud Service Provider (CSP) : A cloud service provider has the knowledge and important
resources in building and managing distributed cloud storage servers. A cloud service provider
poses and operates live Cloud Computing systems.
Third Party Auditor (TPA): An optional TPA, who has expertise and capabilities that users may
not have, ills trusted to assess and expose risk of cloud storage services on behalf of the users
60
Cryptographic primitives cannot be adopted directly. If we use the traditional Cryptographic
primitives directly, we will have conduct the verification for correctness of data stored in the
cloud without having the proper knowledge about the whole data. It is even more challenging
that to provide the continuous assurance of the data safety, if we store different categories of data
stored by different users.
The users are updating the data continuously stored in the cloud. The updation of the data
includes insertion, deletion, modification, appending, reordering etc. During the dynamic data
updation it is very important task that to assure the storage correctness of data. Techniques which
are used can be useful to give assurance to storage correctness without possessing data of user,
where it cannot addresses all the security threat of data storage in cloud, since they all
concentrating on single server situation and a large portion of them don't consider dynamic
operations on data. As a balancing approach, researchers have also proposed protocols which are
distributed for ensuring storage correctness data throughout multiple servers or peers. Again, in
these no distributed schemes is conscious about operations on dynamic data. As a result, their
applicability on cloud data storage can be considerably limited.
In this paper, we present a viable and flexible distributed scheme with dynamic data support
explicitly to verify the user’s data correctness in the cloud. We rely on erasure correcting code in
the file distribution preparation to provide redundancies and guarantee the data dependability.
This development radically diminishes the communication and storage overhead when contrasted
with the conventional techniques of replication-based file distribution. Utilization of
homomorphic token with distributed verification of erasure-coded data, this scheme achieves the
storage correctness insurance as well as data error localization: whenever data corruption has
been identified during the verification of storage correctness, this scheme can localize the data
errors concurrently, i.e., the identification of the misbehaving server(s).
• Compared to many of its predecessors, which only provide binary results about the
storage state across the distributed servers, the challenge-response protocol in our work
further provides the localization of data error.
• Dislike past works for guaranteeing data integrity remotely, on data blocks the new
scheme supports efficient and secure dynamic operations, which includes update, delete
and append.
• The highly efficient security and performance analysis shows that the proposed scheme is
extremely efficient and rigid against Byzantine failure, server colluding attack, , and even
malicious data modification attacks.
1.1 Cloud Data Storage Architecture
The network architecture for cloud data storage is as represented in the figure1. The architecture
is consisting of three different network modules as represented below:
Users: There are different categories of users. The users consisting of both organizations and
individual users. The users are having the data to store in the cloud. The users must have the trust
on the cloud computation.
Cloud Service Provider (CSP) : A cloud service provider has the knowledge and important
resources in building and managing distributed cloud storage servers. A cloud service provider
poses and operates live Cloud Computing systems.
Third Party Auditor (TPA): An optional TPA, who has expertise and capabilities that users may
not have, ills trusted to assess and expose risk of cloud storage services on behalf of the users

International Journal of Computer Science & Information Technology (IJCSIT) Vol 9, No 6, December 2017
61
upon request. In cloud data storage, a user stores his data through a CSP into a set of cloud
servers, which are running in a simultaneous, cooperated and distributed manner. Redundancy of
data redundancy can be engaged with technique of erasure-correcting code to tolerate server crash
or faults as data of the user grows in importance and also size.
After that for the purpose of application, the user interacts with the cloud servers via Cloud
Service Provider (CSP) to retrieve or access his data. In some cases, block level operations has
been performed by user on his data.
Fig 1: Cloud Data Storage Architecture
Most general styles are block insert, delete, update and append are different operations. As
users now not possess their knowledge for data locality, it’s of critical importance to guarantee
users that their data are being properly stored and maintained. That is, users ought to be equipped
with security means that in order that they'll build continuous correctness assurance of their data
stored in cloud even without existence of copy of data locally.
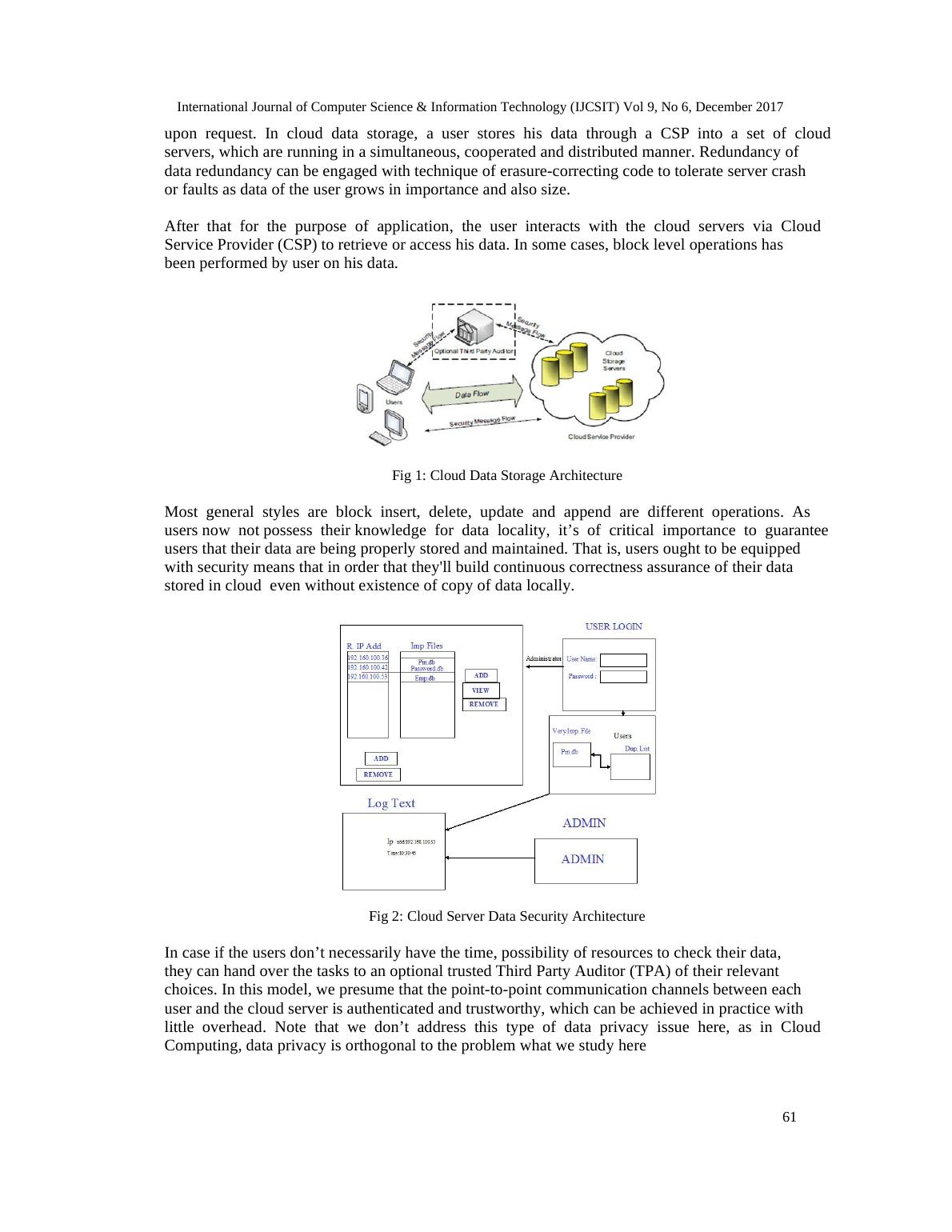
Fig 2: Cloud Server Data Security Architecture
In case if the users don’t necessarily have the time, possibility of resources to check their data,
they can hand over the tasks to an optional trusted Third Party Auditor (TPA) of their relevant
choices. In this model, we presume that the point-to-point communication channels between each
user and the cloud server is authenticated and trustworthy, which can be achieved in practice with
little overhead. Note that we don’t address this type of data privacy issue here, as in Cloud
Computing, data privacy is orthogonal to the problem what we study here
61
upon request. In cloud data storage, a user stores his data through a CSP into a set of cloud
servers, which are running in a simultaneous, cooperated and distributed manner. Redundancy of
data redundancy can be engaged with technique of erasure-correcting code to tolerate server crash
or faults as data of the user grows in importance and also size.
After that for the purpose of application, the user interacts with the cloud servers via Cloud
Service Provider (CSP) to retrieve or access his data. In some cases, block level operations has
been performed by user on his data.
Fig 1: Cloud Data Storage Architecture
Most general styles are block insert, delete, update and append are different operations. As
users now not possess their knowledge for data locality, it’s of critical importance to guarantee
users that their data are being properly stored and maintained. That is, users ought to be equipped
with security means that in order that they'll build continuous correctness assurance of their data
stored in cloud even without existence of copy of data locally.
Fig 2: Cloud Server Data Security Architecture
In case if the users don’t necessarily have the time, possibility of resources to check their data,
they can hand over the tasks to an optional trusted Third Party Auditor (TPA) of their relevant
choices. In this model, we presume that the point-to-point communication channels between each
user and the cloud server is authenticated and trustworthy, which can be achieved in practice with
little overhead. Note that we don’t address this type of data privacy issue here, as in Cloud
Computing, data privacy is orthogonal to the problem what we study here
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Summary of Amazon EC2lg...
|13
|2756
|393
Cloud Service Providers: A Comparison of AWS, Microsoft Azure, Google Cloud Platform, and IBM Cloudlg...
|26
|3925
|310
Introduction to Cloud Computing Introduction 3 Main Body3 Approaches: 5 Demonstration and Evaluationlg...
|14
|5243
|273
Development of Cloud Computing - PDFlg...
|15
|4861
|117
Cloud Computing for DTGOVlg...
|14
|852
|73
Amazon Web Services (AWS) | Assignmentlg...
|4
|1024
|308
