Internet of Things Applications and Communication
VerifiedAdded on 2020/03/01
|8
|1979
|38
AI Summary
This assignment delves into the realm of Internet of Things (IoT) applications and their communication mechanisms. It examines two primary paradigms: Request-Response and Publish-Subscribe. The Request-Response approach is analyzed in the context of a water level controlling application, considering factors such as sensor response time, application processing, and message transmission delay. The assignment further discusses the advantages of the Publish-Subscribe paradigm for supporting mobility and asynchronous event notification in IoT systems. Finally, it explores the strengths and weaknesses of both paradigms and proposes an abstract communication model to facilitate their seamless integration.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Internet of Things
8/26/2017
8/26/2017
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Solution 1:-.................................................................................................................................3
Solution 2:-.................................................................................................................................3
Solution 3:-.................................................................................................................................3
Solution 4:-.................................................................................................................................7
Solution 5:-.................................................................................................................................8
Solution 6:-.................................................................................................................................9
Solution 1:-.................................................................................................................................3
Solution 2:-.................................................................................................................................3
Solution 3:-.................................................................................................................................3
Solution 4:-.................................................................................................................................7
Solution 5:-.................................................................................................................................8
Solution 6:-.................................................................................................................................9

Solution 1:-
The concept of User Interface has benefited from closer attentions to the detail towards technology
industries and the AV is no exception. User Interfaces and by the extension User Experiences have
become a whole genre into itself with the some of tech giant buildings their business off back of a
successful UI. The Apple companies have taken UI to next levels and made it marks across the range
of market. The industries owner is focusing on the phrase “the best UI is no UI” and has studied that
how peoples collaborate naturally. (Golden krishna)
Using conventions we can commence to refocus on the user and the experience.
1. Encircle typical processes rather of screens. Build experiences that do not demand users to
introduce use of their phone in point where they would not use their phone otherway. (Golden
krishna)
2. Create computers work for us rather of requiring us to work the computer. Permit the
technology to administer a seamless experiences beyond us requiring to access in the way.
(Golden krishna)
Solution 2:-
Twisted pair Cable Coaxial Cable Fiber Optical Cable
communication of signals
taking place in the electrical
system over metallic
conducting wires.
communication of signals
taking place in the electrical
system over inner conductor of
cable.
Signal communication taking
place in an optical system over
a glass fiber.
In this approach the noise
resistance is low
Coaxial is having more noise
resistance than twisted pair
cable.
Optical fiber have the highest
noise reistance as the light rays
are unaffected by the electrical
noise.
Twisted pair wire could be
troubled due to outmost
magnetic field.
Coaxial cable is less troubled
due to outmost magnetic field.
Not troubled by the outmost
magnetic field.
Economical medium. Moderately costly Costly
The concept of User Interface has benefited from closer attentions to the detail towards technology
industries and the AV is no exception. User Interfaces and by the extension User Experiences have
become a whole genre into itself with the some of tech giant buildings their business off back of a
successful UI. The Apple companies have taken UI to next levels and made it marks across the range
of market. The industries owner is focusing on the phrase “the best UI is no UI” and has studied that
how peoples collaborate naturally. (Golden krishna)
Using conventions we can commence to refocus on the user and the experience.
1. Encircle typical processes rather of screens. Build experiences that do not demand users to
introduce use of their phone in point where they would not use their phone otherway. (Golden
krishna)
2. Create computers work for us rather of requiring us to work the computer. Permit the
technology to administer a seamless experiences beyond us requiring to access in the way.
(Golden krishna)
Solution 2:-
Twisted pair Cable Coaxial Cable Fiber Optical Cable
communication of signals
taking place in the electrical
system over metallic
conducting wires.
communication of signals
taking place in the electrical
system over inner conductor of
cable.
Signal communication taking
place in an optical system over
a glass fiber.
In this approach the noise
resistance is low
Coaxial is having more noise
resistance than twisted pair
cable.
Optical fiber have the highest
noise reistance as the light rays
are unaffected by the electrical
noise.
Twisted pair wire could be
troubled due to outmost
magnetic field.
Coaxial cable is less troubled
due to outmost magnetic field.
Not troubled by the outmost
magnetic field.
Economical medium. Moderately costly Costly
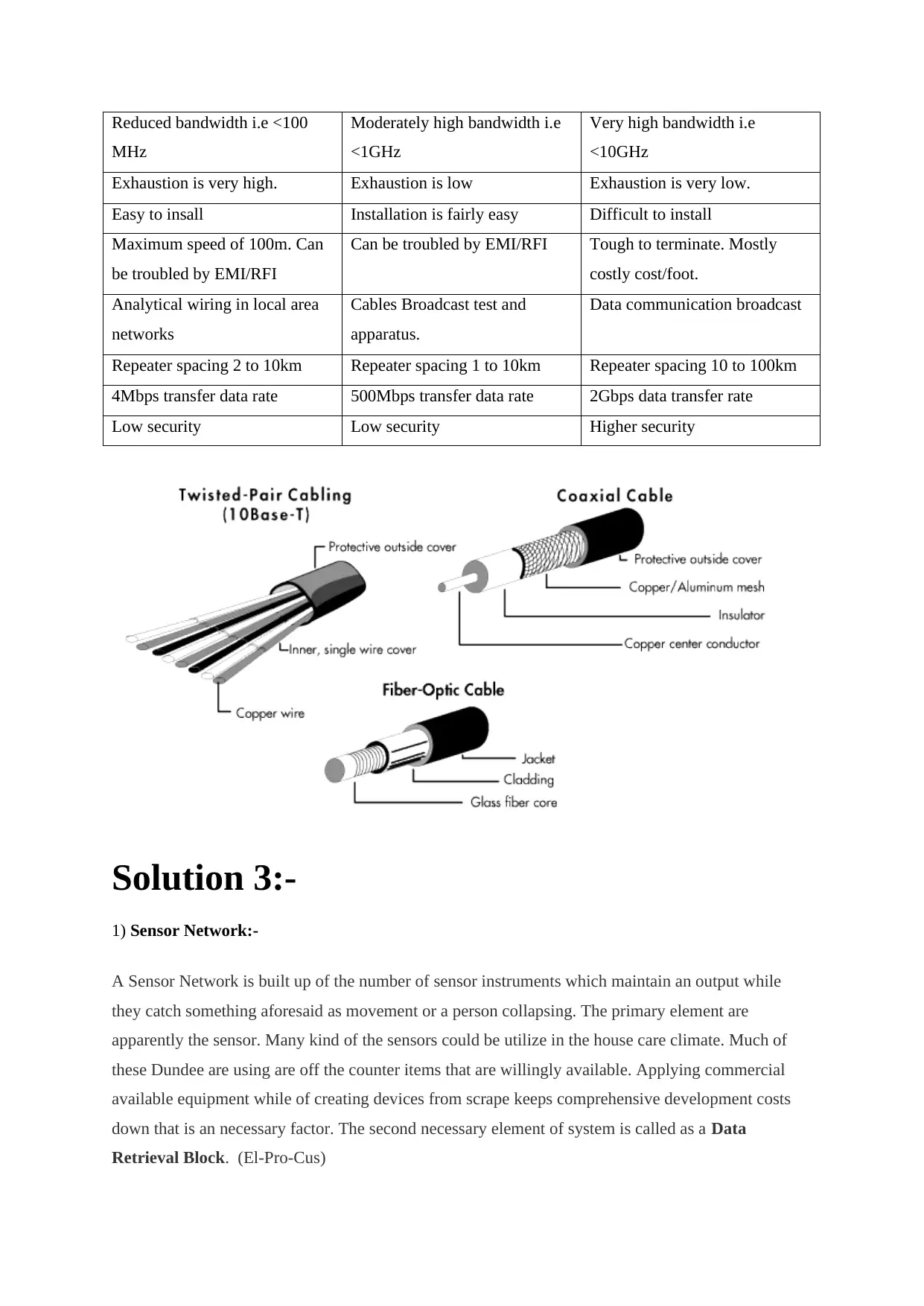
Reduced bandwidth i.e <100
MHz
Moderately high bandwidth i.e
<1GHz
Very high bandwidth i.e
<10GHz
Exhaustion is very high. Exhaustion is low Exhaustion is very low.
Easy to insall Installation is fairly easy Difficult to install
Maximum speed of 100m. Can
be troubled by EMI/RFI
Can be troubled by EMI/RFI Tough to terminate. Mostly
costly cost/foot.
Analytical wiring in local area
networks
Cables Broadcast test and
apparatus.
Data communication broadcast
Repeater spacing 2 to 10km Repeater spacing 1 to 10km Repeater spacing 10 to 100km
4Mbps transfer data rate 500Mbps transfer data rate 2Gbps data transfer rate
Low security Low security Higher security
Solution 3:-
1) Sensor Network:-
A Sensor Network is built up of the number of sensor instruments which maintain an output while
they catch something aforesaid as movement or a person collapsing. The primary element are
apparently the sensor. Many kind of the sensors could be utilize in the house care climate. Much of
these Dundee are using are off the counter items that are willingly available. Applying commercial
available equipment while of creating devices from scrape keeps comprehensive development costs
down that is an necessary factor. The second necessary element of system is called as a Data
Retrieval Block. (El-Pro-Cus)
MHz
Moderately high bandwidth i.e
<1GHz
Very high bandwidth i.e
<10GHz
Exhaustion is very high. Exhaustion is low Exhaustion is very low.
Easy to insall Installation is fairly easy Difficult to install
Maximum speed of 100m. Can
be troubled by EMI/RFI
Can be troubled by EMI/RFI Tough to terminate. Mostly
costly cost/foot.
Analytical wiring in local area
networks
Cables Broadcast test and
apparatus.
Data communication broadcast
Repeater spacing 2 to 10km Repeater spacing 1 to 10km Repeater spacing 10 to 100km
4Mbps transfer data rate 500Mbps transfer data rate 2Gbps data transfer rate
Low security Low security Higher security
Solution 3:-
1) Sensor Network:-
A Sensor Network is built up of the number of sensor instruments which maintain an output while
they catch something aforesaid as movement or a person collapsing. The primary element are
apparently the sensor. Many kind of the sensors could be utilize in the house care climate. Much of
these Dundee are using are off the counter items that are willingly available. Applying commercial
available equipment while of creating devices from scrape keeps comprehensive development costs
down that is an necessary factor. The second necessary element of system is called as a Data
Retrieval Block. (El-Pro-Cus)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Advantages
Sensors circuitry permits a system to be broden from one with required functions to one that
could acquire and act on facts about the climate it operates in.
Sensors like as PIR detectors are comparatively cheap if applying wired versions. (El-Pro-
Cus)
Disadvantages
Users require to conclude attentively if they prefer to be monitored 24 hours a day by a
computers system. (El-Pro-Cus)
A Sensor web may need a lots of increased wiring to be installed over the home to permit
sensors to works except the sensors recyled are wireless.
Applications to Home Care
The main use for a Sensor Network within the home will be to gather data on the user
unobtrusively. Sensor Networks have proven to be use for home care only when they are used
in combination with a multitude of sensors. (El-Pro-Cus)
2) RFID:-
With the Radio Frequency Identification (RFID) each entity could be chunk of the computer web. An
RFID chip looks alike the postage stamp sized stickler that can be joined to or fixed in an entity so
that it could be recorded. The entity might be a cow, a passport, a book or the shipping pallet. The
chip subsist of a little microchip with a different identifier and an antenna that accepts radio
transmissions. RFID readers equipped at tracking points catch tags when they appear into range and
investigate them for information. Applications comprise checking identities, managing the supply
chain, timing race and replacing barcodes. (EPC RFID INFO)
Advantages of RFID
Following are the advantages of RFID:
➨RFID entity and reader could not be in LOS to built the system work.
➨RFID technology is adaptable in nature and so lesser and larger RFID equipment are accessible as
per application. (EPC RFID INFO)
Sensors circuitry permits a system to be broden from one with required functions to one that
could acquire and act on facts about the climate it operates in.
Sensors like as PIR detectors are comparatively cheap if applying wired versions. (El-Pro-
Cus)
Disadvantages
Users require to conclude attentively if they prefer to be monitored 24 hours a day by a
computers system. (El-Pro-Cus)
A Sensor web may need a lots of increased wiring to be installed over the home to permit
sensors to works except the sensors recyled are wireless.
Applications to Home Care
The main use for a Sensor Network within the home will be to gather data on the user
unobtrusively. Sensor Networks have proven to be use for home care only when they are used
in combination with a multitude of sensors. (El-Pro-Cus)
2) RFID:-
With the Radio Frequency Identification (RFID) each entity could be chunk of the computer web. An
RFID chip looks alike the postage stamp sized stickler that can be joined to or fixed in an entity so
that it could be recorded. The entity might be a cow, a passport, a book or the shipping pallet. The
chip subsist of a little microchip with a different identifier and an antenna that accepts radio
transmissions. RFID readers equipped at tracking points catch tags when they appear into range and
investigate them for information. Applications comprise checking identities, managing the supply
chain, timing race and replacing barcodes. (EPC RFID INFO)
Advantages of RFID
Following are the advantages of RFID:
➨RFID entity and reader could not be in LOS to built the system work.
➨RFID technology is adaptable in nature and so lesser and larger RFID equipment are accessible as
per application. (EPC RFID INFO)

Disadvantages of RFID
Following are the disadvantages of RFID:
➨Effective RFID is expensive expected to use of batteries.
➨Benefit of RFID technology at the inventory control and for other similar applications direct to loss
of jobs for incompetent labourer. (EPC RFID INFO)
3) VIDEO TRACKING:-
System Controls provide a multitude of advanced Video Tracking Systems & video tracking
techniques designed to allow to zoom in and out which helps to precisely track distant boats,
aircrafts, vehicles or so on. Video tracking system is accomplice target things in consecutively video
frames. The connectivity can be complex when entity are walking fast relative to frame rate. Another
position is that which raise the complication of the problem is when the tracked things changes
direction after some time. For these positions video tracking systems added by us which usually
engage a motion model which characterize the image of the target might shift for different available
motions of the things. Video Tracking Systems analyze the subsequent video frames and outputs the
alteration of targets between the frames. (Golden krishna)
Applications:-
An preliminary Video Tracking System have been designed by Aviation Research and Development
Service of FAA for applying in the control of aircraft operating in Transition Terminal areas.
Solution 4:-
IoT Security Issues
1. Public Approach: If IoT is constantly flowing to be truly takes off this require to be the first trouble
that the Manufacturers address. (Stephenson, 2013)
2. Vulnerabe to Hacking: Researcher have been capable to drudge into actually on the market
equipments with the extra time and power that means drudger would likely be capable to clone their
effort.(Stephenson, 2013)
3. Are Companies Ready?: AT&T's Cyber security observation report overlooked more than the 5,000
enterprise over the worlds and find that 85% of the enterprises are in charge of or willing to deploys
IoT devices. (Stephenson, 2013)
IoT Privacy Issues
1. Too Much Data: The absolute quantity of facts that IoT equipment can produce is
astounding. We analyses and research that the smaller than 10,000 households could produce
Following are the disadvantages of RFID:
➨Effective RFID is expensive expected to use of batteries.
➨Benefit of RFID technology at the inventory control and for other similar applications direct to loss
of jobs for incompetent labourer. (EPC RFID INFO)
3) VIDEO TRACKING:-
System Controls provide a multitude of advanced Video Tracking Systems & video tracking
techniques designed to allow to zoom in and out which helps to precisely track distant boats,
aircrafts, vehicles or so on. Video tracking system is accomplice target things in consecutively video
frames. The connectivity can be complex when entity are walking fast relative to frame rate. Another
position is that which raise the complication of the problem is when the tracked things changes
direction after some time. For these positions video tracking systems added by us which usually
engage a motion model which characterize the image of the target might shift for different available
motions of the things. Video Tracking Systems analyze the subsequent video frames and outputs the
alteration of targets between the frames. (Golden krishna)
Applications:-
An preliminary Video Tracking System have been designed by Aviation Research and Development
Service of FAA for applying in the control of aircraft operating in Transition Terminal areas.
Solution 4:-
IoT Security Issues
1. Public Approach: If IoT is constantly flowing to be truly takes off this require to be the first trouble
that the Manufacturers address. (Stephenson, 2013)
2. Vulnerabe to Hacking: Researcher have been capable to drudge into actually on the market
equipments with the extra time and power that means drudger would likely be capable to clone their
effort.(Stephenson, 2013)
3. Are Companies Ready?: AT&T's Cyber security observation report overlooked more than the 5,000
enterprise over the worlds and find that 85% of the enterprises are in charge of or willing to deploys
IoT devices. (Stephenson, 2013)
IoT Privacy Issues
1. Too Much Data: The absolute quantity of facts that IoT equipment can produce is
astounding. We analyses and research that the smaller than 10,000 households could produce

150 million distinct data points every day. This produces extra entry points for the hackers
and leaves complex information vulnerables. (Hajar mousannif, 2016)
2. Unwanted Public Profile: You had undoubtedly agree to the terms of the services at some
point but has you ever really read through an entire document? We has found that
organizations should use gathered facts that the buyer willingly offer to make the
employments decisions. (Hajar mousannif, 2016)
3. Eavesdropping: Producers and hacker could really uses a linked device to virtually invades
a persons house. By preventing the uncoded data from an smart meters device to determines
what television shows someone were watching at that point. (Hajar mousannif, 2016)
Solution 5:-
An IoT water level controlling application needs updates from a sensor sequentially using the
command and response paradigm. The application prompt a request every 1s. The round trip
reproduction delay between the application and sensor is 12 ms. On average the sensor utilizes 3 ms
to the process each request. The application utilizes 2 ms to transmit or accept any message. If the
application slab on every request to sensor then it took. The Request Response approach is widely
used in ubiquitous system to transform data in a secure, reliable and timely manner.
Nonetheles there is also an appearing need for adopting the Publish Subscribe (PubSub)
approach in this type of systems due to advantages that this approach offers in the supporting
mobility by means of asynchronous non-blocking and one to many message distribution
semantics for event notification. This paper evaluates the strengths and weaknesses of both
the RR and PubSub approaches to support communication in the ubiquitous systems and
advises an abstract communication model in order to the enable their seamless integration.
Solution 6:-
Nielson's Law:- Nielsen’s Law of Internet Bandwidth to perform historical broadband Internet speeds
and to anticipation upcoming broadband Internet speeds. Mr. Nielsen anticipate many years ago the
high end users follwing connection speed produces by approximately 50% admixture annual growth
rate (CAGR). In existance actual peak service tiers allowed by service providers along the years may
be closer to 60% compound annual growth rate. Nielsen's law is identical to more settled Moore's law.
Unsuccessfully analyzing the two laws represents that bandwidth increases lesser than computer
power. Moore's law tells that computers double in potentials every 18 months which coincide to about
60% annual growth. As bandwidth will continue the gating factor in experienced quality of utilizing
and leaves complex information vulnerables. (Hajar mousannif, 2016)
2. Unwanted Public Profile: You had undoubtedly agree to the terms of the services at some
point but has you ever really read through an entire document? We has found that
organizations should use gathered facts that the buyer willingly offer to make the
employments decisions. (Hajar mousannif, 2016)
3. Eavesdropping: Producers and hacker could really uses a linked device to virtually invades
a persons house. By preventing the uncoded data from an smart meters device to determines
what television shows someone were watching at that point. (Hajar mousannif, 2016)
Solution 5:-
An IoT water level controlling application needs updates from a sensor sequentially using the
command and response paradigm. The application prompt a request every 1s. The round trip
reproduction delay between the application and sensor is 12 ms. On average the sensor utilizes 3 ms
to the process each request. The application utilizes 2 ms to transmit or accept any message. If the
application slab on every request to sensor then it took. The Request Response approach is widely
used in ubiquitous system to transform data in a secure, reliable and timely manner.
Nonetheles there is also an appearing need for adopting the Publish Subscribe (PubSub)
approach in this type of systems due to advantages that this approach offers in the supporting
mobility by means of asynchronous non-blocking and one to many message distribution
semantics for event notification. This paper evaluates the strengths and weaknesses of both
the RR and PubSub approaches to support communication in the ubiquitous systems and
advises an abstract communication model in order to the enable their seamless integration.
Solution 6:-
Nielson's Law:- Nielsen’s Law of Internet Bandwidth to perform historical broadband Internet speeds
and to anticipation upcoming broadband Internet speeds. Mr. Nielsen anticipate many years ago the
high end users follwing connection speed produces by approximately 50% admixture annual growth
rate (CAGR). In existance actual peak service tiers allowed by service providers along the years may
be closer to 60% compound annual growth rate. Nielsen's law is identical to more settled Moore's law.
Unsuccessfully analyzing the two laws represents that bandwidth increases lesser than computer
power. Moore's law tells that computers double in potentials every 18 months which coincide to about
60% annual growth. As bandwidth will continue the gating factor in experienced quality of utilizing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
the internet medium. Like Moore’s Law, Nielsen’s Law is a measurement of the leading edge
capabilities. In reference to the Moore’s Law there is confirmation of a design gap that continues
since we can not directly use all of the available transistors provided on each leading process node. By
analogy, Nielsen’s Law addresses the fastest speeds available for high-end Internet users.
capabilities. In reference to the Moore’s Law there is confirmation of a design gap that continues
since we can not directly use all of the available transistors provided on each leading process node. By
analogy, Nielsen’s Law addresses the fastest speeds available for high-end Internet users.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





