Integrating IoT Applications into Web Systems
VerifiedAdded on 2020/03/23
|16
|2667
|110
AI Summary
This assignment delves into the integration of Internet of Things (IoT) applications within web systems. It explores key aspects such as user interactions, cybersecurity considerations in household IoT devices, the emerging model of Sensing as a Service (S2aaS), and the impact of IoT on consumer connectivity and smart products. The provided resources offer insights into various IoT devices, their functionalities, manufacturers, and costs, highlighting the diverse applications and implications of this rapidly evolving field.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: IOT SYSTEMS: POTENTIAL AND APPLICATIONS
STUDENT NAME
NAME OF THE INSTITUTE
STUDENT NAME
NAME OF THE INSTITUTE
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
Contents
1 Introduction..............................................................................................................................3
2 IOT & Home Network.............................................................................................................3
3 Home Networking: My Abode................................................................................................3
1. Lock system........................................................................................................................3
2. Home Lighting systems.....................................................................................................5
3. Thermostat.........................................................................................................................6
4. Smart TV............................................................................................................................7
5. Coffee machine...................................................................................................................8
6. Refrigerator........................................................................................................................9
7. IOT Footwear...................................................................................................................10
8. Smart Toothbrushes........................................................................................................11
4 Conclusion.............................................................................................................................12
5 References..............................................................................................................................13
6 Appendix................................................................................................................................14
2
Contents
1 Introduction..............................................................................................................................3
2 IOT & Home Network.............................................................................................................3
3 Home Networking: My Abode................................................................................................3
1. Lock system........................................................................................................................3
2. Home Lighting systems.....................................................................................................5
3. Thermostat.........................................................................................................................6
4. Smart TV............................................................................................................................7
5. Coffee machine...................................................................................................................8
6. Refrigerator........................................................................................................................9
7. IOT Footwear...................................................................................................................10
8. Smart Toothbrushes........................................................................................................11
4 Conclusion.............................................................................................................................12
5 References..............................................................................................................................13
6 Appendix................................................................................................................................14
2

IOT SYSTEMS: POTENTIAL AND APPLICATIONS 3

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
1 Introduction
The following report intends to describe the prospective of IOT technology from the user end
and its significance for lifestyle in relation to common IOT products that can be used in one’s
day to day life. Apart from that, this report will also discuss the several concerns related to IOT
including data storage, security and control etc. with reflective measures for the same.
2 IOT & Home Network
The Internet of Things (IoT) renovates the physical objects everywhere into a network of
information that quickly modifies our way of life. From refrigerators to cars, to parking spaces
and homes, the IoT is turning every object into the digital world. Our homes could soon keep
track of all our daily activities (Perera 2017), from opening to closing the front door, through
automatic product control when the refrigerator is empty.
Whether we are ready for such a level of automation, or what we want, is a whole other
matter. However, this should quickly become the norm, before a new evolution of technologies
again transforms our way of life.
On the other hand, there are few problems in the smart homes that should be stated. The
broad technological concerns range from interface, privacy, connectivity, security and
convenience.
The diagram of Internet of Things infrastructure of my home can be shown as:
4
1 Introduction
The following report intends to describe the prospective of IOT technology from the user end
and its significance for lifestyle in relation to common IOT products that can be used in one’s
day to day life. Apart from that, this report will also discuss the several concerns related to IOT
including data storage, security and control etc. with reflective measures for the same.
2 IOT & Home Network
The Internet of Things (IoT) renovates the physical objects everywhere into a network of
information that quickly modifies our way of life. From refrigerators to cars, to parking spaces
and homes, the IoT is turning every object into the digital world. Our homes could soon keep
track of all our daily activities (Perera 2017), from opening to closing the front door, through
automatic product control when the refrigerator is empty.
Whether we are ready for such a level of automation, or what we want, is a whole other
matter. However, this should quickly become the norm, before a new evolution of technologies
again transforms our way of life.
On the other hand, there are few problems in the smart homes that should be stated. The
broad technological concerns range from interface, privacy, connectivity, security and
convenience.
The diagram of Internet of Things infrastructure of my home can be shown as:
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
3 Home Networking: My Abode
The devices in my abode can be discussed as:
1. Lock system
Firms these days have established the digital auto lock systems that are hassle
free, keyless and operate through mobile apps capable of connecting with majorly all
smart devices. With such system, it becomes relatively easier to lock and unlock the
accesses without the need of keys by just operating online. Customized keys could also
be generated and coded for specific visiting hours or days for any guests. Being
extremely useful and keyless Internet operates it all. But certain issues faced are:
Issue Type Comments
5
3 Home Networking: My Abode
The devices in my abode can be discussed as:
1. Lock system
Firms these days have established the digital auto lock systems that are hassle
free, keyless and operate through mobile apps capable of connecting with majorly all
smart devices. With such system, it becomes relatively easier to lock and unlock the
accesses without the need of keys by just operating online. Customized keys could also
be generated and coded for specific visiting hours or days for any guests. Being
extremely useful and keyless Internet operates it all. But certain issues faced are:
Issue Type Comments
5
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
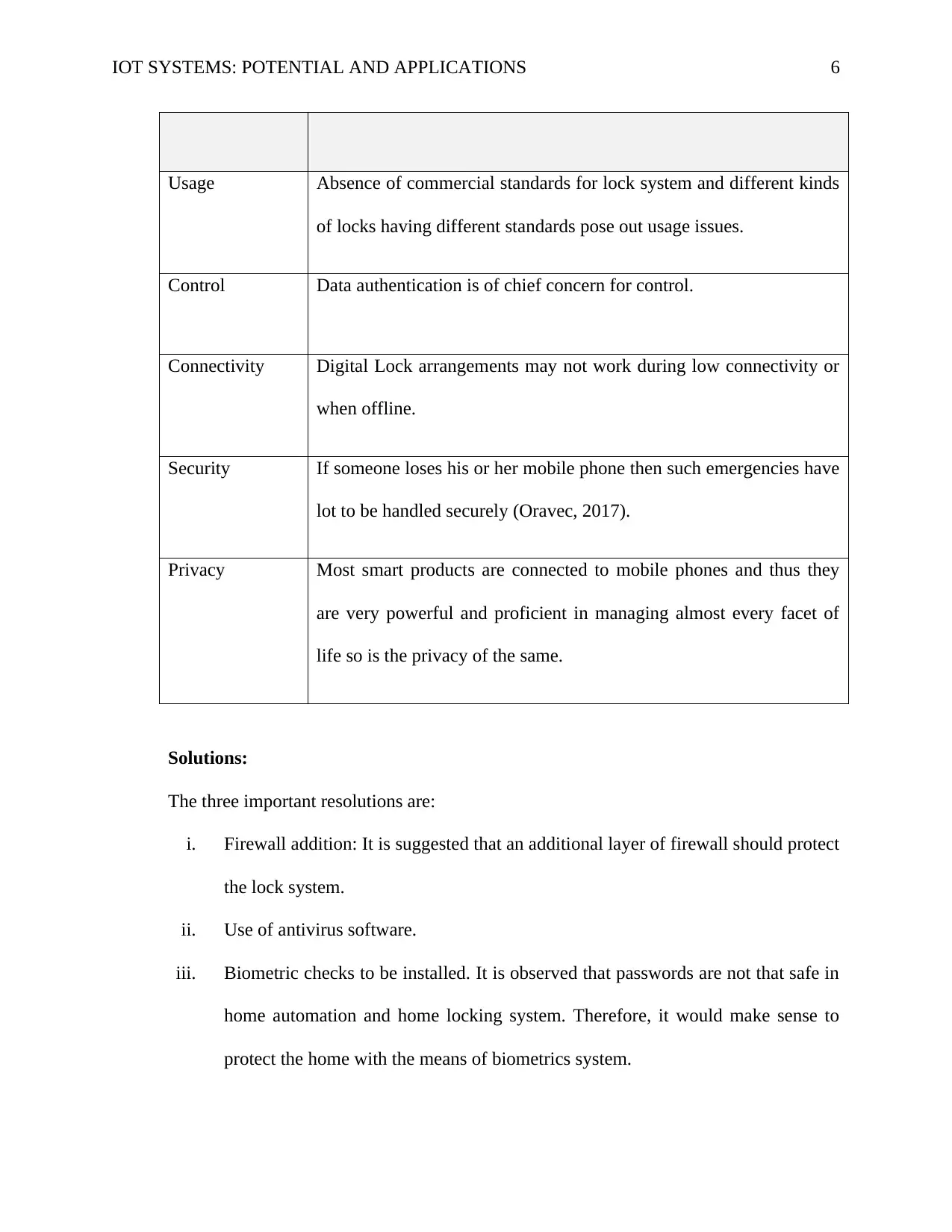
Usage Absence of commercial standards for lock system and different kinds
of locks having different standards pose out usage issues.
Control Data authentication is of chief concern for control.
Connectivity Digital Lock arrangements may not work during low connectivity or
when offline.
Security If someone loses his or her mobile phone then such emergencies have
lot to be handled securely (Oravec, 2017).
Privacy Most smart products are connected to mobile phones and thus they
are very powerful and proficient in managing almost every facet of
life so is the privacy of the same.
Solutions:
The three important resolutions are:
i. Firewall addition: It is suggested that an additional layer of firewall should protect
the lock system.
ii. Use of antivirus software.
iii. Biometric checks to be installed. It is observed that passwords are not that safe in
home automation and home locking system. Therefore, it would make sense to
protect the home with the means of biometrics system.
6
Usage Absence of commercial standards for lock system and different kinds
of locks having different standards pose out usage issues.
Control Data authentication is of chief concern for control.
Connectivity Digital Lock arrangements may not work during low connectivity or
when offline.
Security If someone loses his or her mobile phone then such emergencies have
lot to be handled securely (Oravec, 2017).
Privacy Most smart products are connected to mobile phones and thus they
are very powerful and proficient in managing almost every facet of
life so is the privacy of the same.
Solutions:
The three important resolutions are:
i. Firewall addition: It is suggested that an additional layer of firewall should protect
the lock system.
ii. Use of antivirus software.
iii. Biometric checks to be installed. It is observed that passwords are not that safe in
home automation and home locking system. Therefore, it would make sense to
protect the home with the means of biometrics system.
6
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
It would be best if corporate standards were used for the goods (Zahra, Brewer, &
Cooper, 2017). By corporate standards it means that different vendors of lock system and
home system automation should join hands and develop common set of standards. The
common set of standards would ensure that the vulnerabilities in the system are
minimized.
2. Home Lighting systems
Philips new mobile app has a lights control feature thus total regulation of
household switches could be operated. Furthermore, this app can self-diagnose and
maintain schedules as per individual’s usage and involve its acumen to design links as per
generated data. Technology making it same lighting device red, blue yellow or as per the
customization.
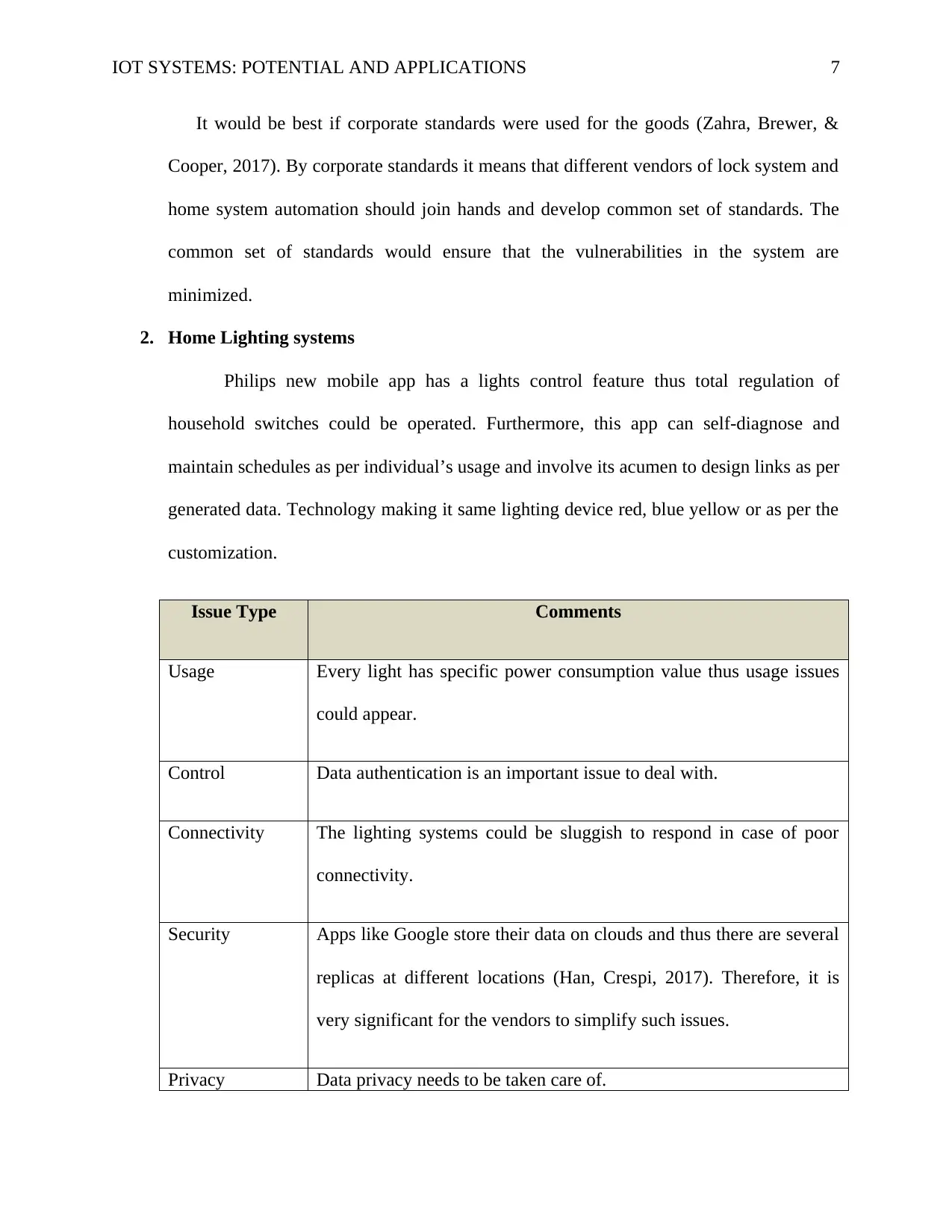
Issue Type Comments
Usage Every light has specific power consumption value thus usage issues
could appear.
Control Data authentication is an important issue to deal with.
Connectivity The lighting systems could be sluggish to respond in case of poor
connectivity.
Security Apps like Google store their data on clouds and thus there are several
replicas at different locations (Han, Crespi, 2017). Therefore, it is
very significant for the vendors to simplify such issues.
Privacy Data privacy needs to be taken care of.
7
It would be best if corporate standards were used for the goods (Zahra, Brewer, &
Cooper, 2017). By corporate standards it means that different vendors of lock system and
home system automation should join hands and develop common set of standards. The
common set of standards would ensure that the vulnerabilities in the system are
minimized.
2. Home Lighting systems
Philips new mobile app has a lights control feature thus total regulation of
household switches could be operated. Furthermore, this app can self-diagnose and
maintain schedules as per individual’s usage and involve its acumen to design links as per
generated data. Technology making it same lighting device red, blue yellow or as per the
customization.
Issue Type Comments
Usage Every light has specific power consumption value thus usage issues
could appear.
Control Data authentication is an important issue to deal with.
Connectivity The lighting systems could be sluggish to respond in case of poor
connectivity.
Security Apps like Google store their data on clouds and thus there are several
replicas at different locations (Han, Crespi, 2017). Therefore, it is
very significant for the vendors to simplify such issues.
Privacy Data privacy needs to be taken care of.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
Solutions:
The key measures to be taken are as follows:
i. Protection through strong passwords. At the same time, it is recommended that
users should change the password on regular time interval.
ii. Antivirus Systems to be installed with lighting systems software. At the same
time, it is recommended that the antivirus system should be updated on regular
time interval.
Philips Light systems should integrate with all the coffee machines irrespective of the
brand. Nike has launched their smart watch only on iOs and not on Android and it may
result in multi levels of collaboration.
3. Thermostat
IOT enabled thermostat was primarily created by Nest however it was later
acquired by Google. These thermostats can be operated online from any location using
desired application before reaching home to make more comfortable prior the entry.
These technically adapted thermostats do not require any temperature settings, they
automatically behave as per the weather conditions and time of day with easily
customizable features that too with voice over. It is self-maintaining and improvises itself
every time with required substantial data.
Issue Type Comments
Usage Different devices have different thermostats with individual power
8
Solutions:
The key measures to be taken are as follows:
i. Protection through strong passwords. At the same time, it is recommended that
users should change the password on regular time interval.
ii. Antivirus Systems to be installed with lighting systems software. At the same
time, it is recommended that the antivirus system should be updated on regular
time interval.
Philips Light systems should integrate with all the coffee machines irrespective of the
brand. Nike has launched their smart watch only on iOs and not on Android and it may
result in multi levels of collaboration.
3. Thermostat
IOT enabled thermostat was primarily created by Nest however it was later
acquired by Google. These thermostats can be operated online from any location using
desired application before reaching home to make more comfortable prior the entry.
These technically adapted thermostats do not require any temperature settings, they
automatically behave as per the weather conditions and time of day with easily
customizable features that too with voice over. It is self-maintaining and improvises itself
every time with required substantial data.
Issue Type Comments
Usage Different devices have different thermostats with individual power
8
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
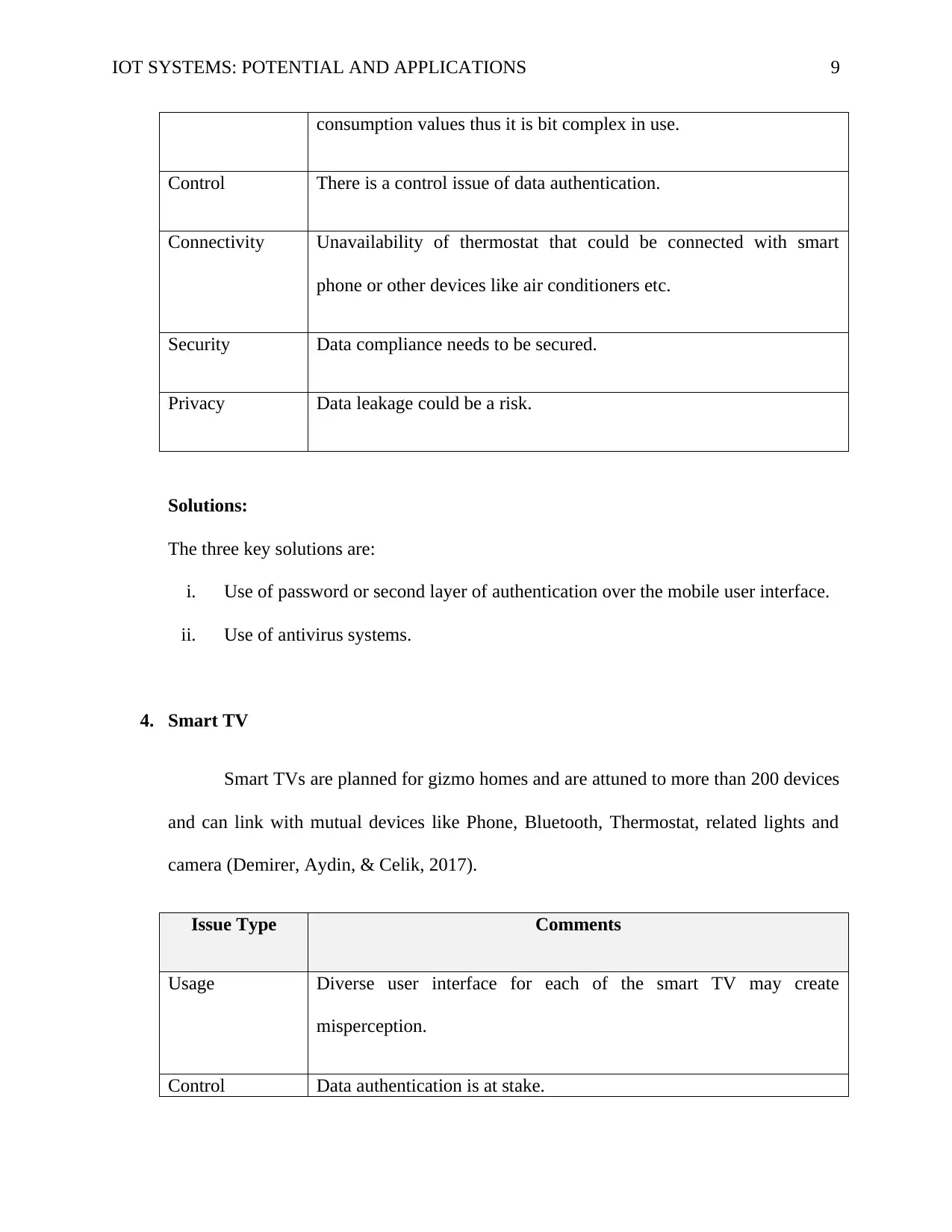
consumption values thus it is bit complex in use.
Control There is a control issue of data authentication.
Connectivity Unavailability of thermostat that could be connected with smart
phone or other devices like air conditioners etc.
Security Data compliance needs to be secured.
Privacy Data leakage could be a risk.
Solutions:
The three key solutions are:
i. Use of password or second layer of authentication over the mobile user interface.
ii. Use of antivirus systems.
4. Smart TV
Smart TVs are planned for gizmo homes and are attuned to more than 200 devices
and can link with mutual devices like Phone, Bluetooth, Thermostat, related lights and
camera (Demirer, Aydin, & Celik, 2017).
Issue Type Comments
Usage Diverse user interface for each of the smart TV may create
misperception.
Control Data authentication is at stake.
9
consumption values thus it is bit complex in use.
Control There is a control issue of data authentication.
Connectivity Unavailability of thermostat that could be connected with smart
phone or other devices like air conditioners etc.
Security Data compliance needs to be secured.
Privacy Data leakage could be a risk.
Solutions:
The three key solutions are:
i. Use of password or second layer of authentication over the mobile user interface.
ii. Use of antivirus systems.
4. Smart TV
Smart TVs are planned for gizmo homes and are attuned to more than 200 devices
and can link with mutual devices like Phone, Bluetooth, Thermostat, related lights and
camera (Demirer, Aydin, & Celik, 2017).
Issue Type Comments
Usage Diverse user interface for each of the smart TV may create
misperception.
Control Data authentication is at stake.
9
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
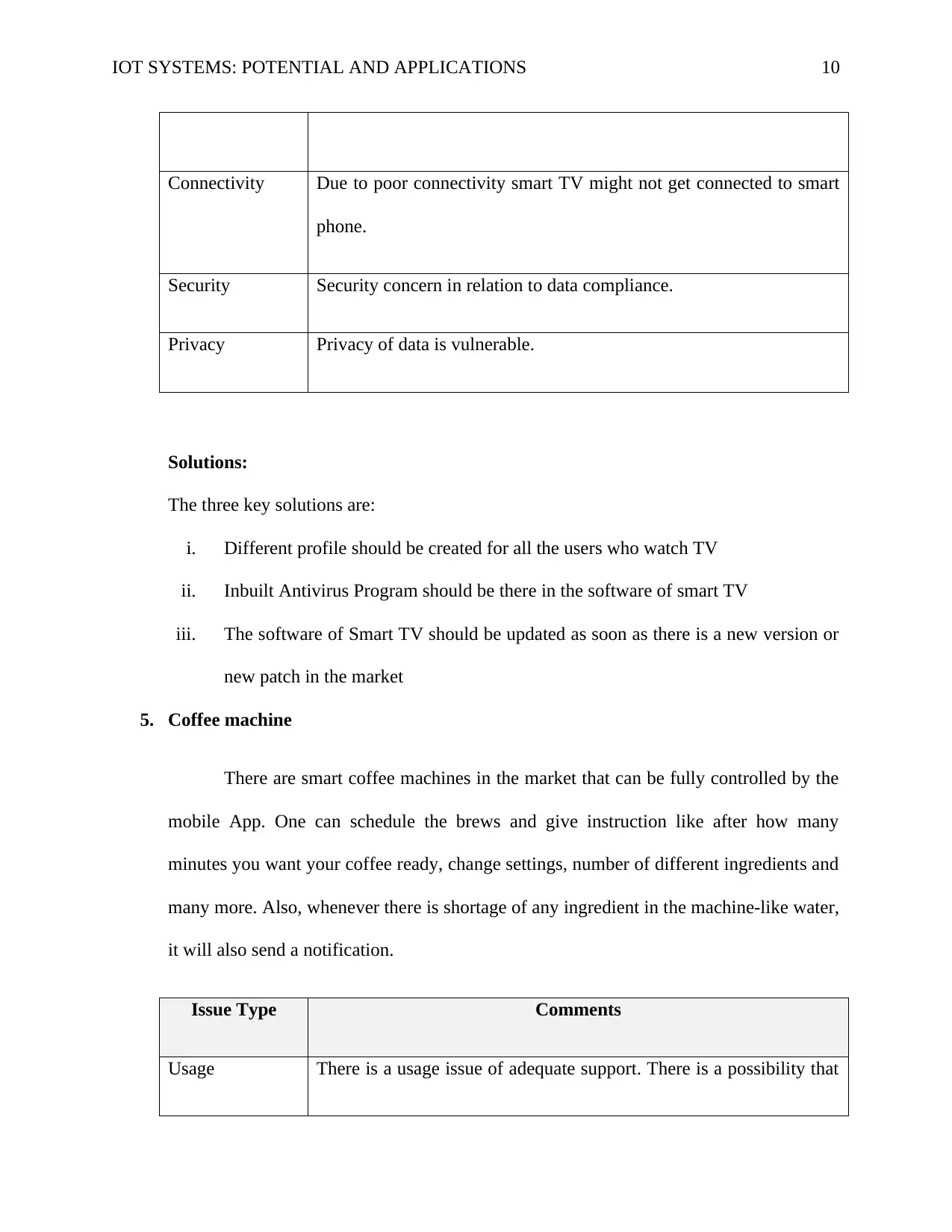
Connectivity Due to poor connectivity smart TV might not get connected to smart
phone.
Security Security concern in relation to data compliance.
Privacy Privacy of data is vulnerable.
Solutions:
The three key solutions are:
i. Different profile should be created for all the users who watch TV
ii. Inbuilt Antivirus Program should be there in the software of smart TV
iii. The software of Smart TV should be updated as soon as there is a new version or
new patch in the market
5. Coffee machine
There are smart coffee machines in the market that can be fully controlled by the
mobile App. One can schedule the brews and give instruction like after how many
minutes you want your coffee ready, change settings, number of different ingredients and
many more. Also, whenever there is shortage of any ingredient in the machine-like water,
it will also send a notification.
Issue Type Comments
Usage There is a usage issue of adequate support. There is a possibility that
10
Connectivity Due to poor connectivity smart TV might not get connected to smart
phone.
Security Security concern in relation to data compliance.
Privacy Privacy of data is vulnerable.
Solutions:
The three key solutions are:
i. Different profile should be created for all the users who watch TV
ii. Inbuilt Antivirus Program should be there in the software of smart TV
iii. The software of Smart TV should be updated as soon as there is a new version or
new patch in the market
5. Coffee machine
There are smart coffee machines in the market that can be fully controlled by the
mobile App. One can schedule the brews and give instruction like after how many
minutes you want your coffee ready, change settings, number of different ingredients and
many more. Also, whenever there is shortage of any ingredient in the machine-like water,
it will also send a notification.
Issue Type Comments
Usage There is a usage issue of adequate support. There is a possibility that
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
coffee machine does not support all the functions over a mobile app.
Control Data authentication needs have Control
Connectivity There is a connectivity concern related to setup.
Security Data Compliance and its security to be taken care of.
Privacy Privacy of data to be looked after.
Solutions:
The main resolutions are:
i. Password Protection
ii. Antivirus Installation
6. Refrigerator
Smart and Connected refrigerators are built with complex system of actuators and
sensors that have predictive analysis in relation to shortage of inventory, placing orders to
the closest outlets (Verhoef, et al., 2017). Though these characteristics are primarily
unrealistic, but with smart approach and regular improvisations its easily getting
importance in our lives.
Issue Type Comments
Usage Refrigerator may not upkeep all the functions over a mobile
application.
Control Data validation could generate control concerns.
11
coffee machine does not support all the functions over a mobile app.
Control Data authentication needs have Control
Connectivity There is a connectivity concern related to setup.
Security Data Compliance and its security to be taken care of.
Privacy Privacy of data to be looked after.
Solutions:
The main resolutions are:
i. Password Protection
ii. Antivirus Installation
6. Refrigerator
Smart and Connected refrigerators are built with complex system of actuators and
sensors that have predictive analysis in relation to shortage of inventory, placing orders to
the closest outlets (Verhoef, et al., 2017). Though these characteristics are primarily
unrealistic, but with smart approach and regular improvisations its easily getting
importance in our lives.
Issue Type Comments
Usage Refrigerator may not upkeep all the functions over a mobile
application.
Control Data validation could generate control concerns.
11
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
Connectivity If connectivity gets lost then data calculation could be faulty.
Security Data maintenance could be loose.
Privacy Data discretion might be at stake.
Solutions:
The three key way outs are:
i. Password protection
ii. Antivirus Protection
7. IOT Footwear
Primarily, Ducere Techologies has developed sensor induced footwear for
visually impaired people. These shoes act as guide in the direction of the destination with
the help of vibrations in shoes operated with Lechal app. Presently, Nike has also
introduced IOT enabled shoes which are connected with Apple smart watch and iPhones.
These shoes can gauge the travelled distance, running speed, calories burnt and several
other characteristics by estimating an individual’s pattern.
Issue Type Comments
Usage There is a usage issue of adequate support.
Control There is a control issue of data authentication.
Connectivity Infrastructure Connectivity.
12
Connectivity If connectivity gets lost then data calculation could be faulty.
Security Data maintenance could be loose.
Privacy Data discretion might be at stake.
Solutions:
The three key way outs are:
i. Password protection
ii. Antivirus Protection
7. IOT Footwear
Primarily, Ducere Techologies has developed sensor induced footwear for
visually impaired people. These shoes act as guide in the direction of the destination with
the help of vibrations in shoes operated with Lechal app. Presently, Nike has also
introduced IOT enabled shoes which are connected with Apple smart watch and iPhones.
These shoes can gauge the travelled distance, running speed, calories burnt and several
other characteristics by estimating an individual’s pattern.
Issue Type Comments
Usage There is a usage issue of adequate support.
Control There is a control issue of data authentication.
Connectivity Infrastructure Connectivity.
12
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
Security Data compliance required with any risks.
Privacy Data Privacy needs to be strong.
Solutions:
The three key measures are:
i. Firewall Protected.
ii. Antivirus Protected.
iii. Biometric Authentication.
8. Smart Toothbrushes
Philips and Kolibree are two major companies dealing in smart toothbrushes.
These products are a direct competition to the dentists providing easier and reasonable
oral healthcare routines with features to analyze brushing duration, frequency and ignored
oral and dental areas. They will also convey performance charts and scheduled reminders
for regular activity thus promoting better dental hygiene of an individual.
Issue Type Comments
Usage There is a usage issue of sufficient provision. There is a likelihood all
the functions might be unsupportable over a mobile app.
Control Biometric authentication might be erroneous.
Connectivity Connectivity arrangement could come up as an issue.
13
Security Data compliance required with any risks.
Privacy Data Privacy needs to be strong.
Solutions:
The three key measures are:
i. Firewall Protected.
ii. Antivirus Protected.
iii. Biometric Authentication.
8. Smart Toothbrushes
Philips and Kolibree are two major companies dealing in smart toothbrushes.
These products are a direct competition to the dentists providing easier and reasonable
oral healthcare routines with features to analyze brushing duration, frequency and ignored
oral and dental areas. They will also convey performance charts and scheduled reminders
for regular activity thus promoting better dental hygiene of an individual.
Issue Type Comments
Usage There is a usage issue of sufficient provision. There is a likelihood all
the functions might be unsupportable over a mobile app.
Control Biometric authentication might be erroneous.
Connectivity Connectivity arrangement could come up as an issue.
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
Security There is a security problem of information compliance.
Privacy There is a grave concern of data privacy at stake.
Solutions:
The major solutions are:
i. The second level of authentication like face detection of fingerprint can be used to
provide access to toothbrush.
ii. The software of the toothbrush should be updated on regular time interval.
4 Conclusion
More and more objects are connected to the Internet and applications are endless, ranging
from monitoring machines to massive transfer of information. All kinds of machines ranging
from gigantic digitally operated aircrafts to small handheld devices are monitored in the real
time. IOT industry is fairly divided as of now and there are enormous organizations, which
are involved in IOT related products. Philips, Nike, Google, Apple, Schneider are all open to
IOT product development, organizations such as GE, ABB, CISCO, IBM are manufacturing
IOT products which can be used in various sectors like retail, automotive and education.
High-tech giants like Google, Cisco, and IBM are working on IT aspects of these Internet
based communication products (Olsson, Bosch, & Katumba, 2016).
14
Security There is a security problem of information compliance.
Privacy There is a grave concern of data privacy at stake.
Solutions:
The major solutions are:
i. The second level of authentication like face detection of fingerprint can be used to
provide access to toothbrush.
ii. The software of the toothbrush should be updated on regular time interval.
4 Conclusion
More and more objects are connected to the Internet and applications are endless, ranging
from monitoring machines to massive transfer of information. All kinds of machines ranging
from gigantic digitally operated aircrafts to small handheld devices are monitored in the real
time. IOT industry is fairly divided as of now and there are enormous organizations, which
are involved in IOT related products. Philips, Nike, Google, Apple, Schneider are all open to
IOT product development, organizations such as GE, ABB, CISCO, IBM are manufacturing
IOT products which can be used in various sectors like retail, automotive and education.
High-tech giants like Google, Cisco, and IBM are working on IT aspects of these Internet
based communication products (Olsson, Bosch, & Katumba, 2016).
14

IOT SYSTEMS: POTENTIAL AND APPLICATIONS
5 References
Abou-Zahra, S., Brewer, J., & Cooper, M. (2017). Web Standards to Enable an Accessible and
Inclusive Internet of Things (IoT).
Demirer, V., Aydın, B., & Çelik, Ş. B. (2017). Exploring the Educational Potential of Internet of
Things (IoT) in Seamless Learning. The Internet of Things: Breakthroughs in Research and
Practice: Breakthroughs in Research and Practice, 1.
Han, S. N., & Crespi, N. (2017). Semantic service provisioning for smart objects: Integrating IoT
applications into the web. Future Generation Computer Systems.
Olsson, H. H., Bosch, J., & Katumba, B. (2016). Exploring IoT User Dimensions: A Multi-case
Study on User Interactions in ‘Internet of Things’ Systems. In Product-Focused Software
Process Improvement: 17th International Conference, PROFES 2016, Trondheim, Norway,
November 22-24, 2016, Proceedings 17 (pp. 477-484). Springer International Publishing.
Oravec, J. A. (2017). Kill switches, remote deletion, and intelligent agents: Framing everyday
household cybersecurity in the internet of things. Technology in Society.
Perera, C. (2017). Sensing as a Service (S2aaS): Buying and Selling IoT Data. arXiv preprint
arXiv:1702.02380.
Verhoef, P. C., Stephen, A. T., Kannan, P. K., Luo, X., Abhishek, V., Andrews, M., ... & Hu, M.
(2017). Consumer Connectivity in a Complex, Technology-Enabled, and Mobile-Oriented
World with Smart Products.
15
5 References
Abou-Zahra, S., Brewer, J., & Cooper, M. (2017). Web Standards to Enable an Accessible and
Inclusive Internet of Things (IoT).
Demirer, V., Aydın, B., & Çelik, Ş. B. (2017). Exploring the Educational Potential of Internet of
Things (IoT) in Seamless Learning. The Internet of Things: Breakthroughs in Research and
Practice: Breakthroughs in Research and Practice, 1.
Han, S. N., & Crespi, N. (2017). Semantic service provisioning for smart objects: Integrating IoT
applications into the web. Future Generation Computer Systems.
Olsson, H. H., Bosch, J., & Katumba, B. (2016). Exploring IoT User Dimensions: A Multi-case
Study on User Interactions in ‘Internet of Things’ Systems. In Product-Focused Software
Process Improvement: 17th International Conference, PROFES 2016, Trondheim, Norway,
November 22-24, 2016, Proceedings 17 (pp. 477-484). Springer International Publishing.
Oravec, J. A. (2017). Kill switches, remote deletion, and intelligent agents: Framing everyday
household cybersecurity in the internet of things. Technology in Society.
Perera, C. (2017). Sensing as a Service (S2aaS): Buying and Selling IoT Data. arXiv preprint
arXiv:1702.02380.
Verhoef, P. C., Stephen, A. T., Kannan, P. K., Luo, X., Abhishek, V., Andrews, M., ... & Hu, M.
(2017). Consumer Connectivity in a Complex, Technology-Enabled, and Mobile-Oriented
World with Smart Products.
15
IOT SYSTEMS: POTENTIAL AND APPLICATIONS
6 Appendix
IOT Device Function Manufacturer Cost
Lock system Locking and unlocking via mobile
application without the need to have
any keys.
August systems 400 dollars
Lighting
system
Lights that can be controlled from
anywhere using a mobile and also
they can have customised settings
and display lights accordingly.
Philips There are
several
products in
this range
beginning
from 50
dollars
Thermostat Nest Heating 900 AUD
Television Television connectivity with other
electronic devices like usb drives,
camera, mobile phones etc.
Samsung Models
starting
from 1800
AUD
Coffee
machine
Coffee machine which can be
managed by a mobile phone and
notify in case of unavailability of any
Aria Systems 600 AUD
16
6 Appendix
IOT Device Function Manufacturer Cost
Lock system Locking and unlocking via mobile
application without the need to have
any keys.
August systems 400 dollars
Lighting
system
Lights that can be controlled from
anywhere using a mobile and also
they can have customised settings
and display lights accordingly.
Philips There are
several
products in
this range
beginning
from 50
dollars
Thermostat Nest Heating 900 AUD
Television Television connectivity with other
electronic devices like usb drives,
camera, mobile phones etc.
Samsung Models
starting
from 1800
AUD
Coffee
machine
Coffee machine which can be
managed by a mobile phone and
notify in case of unavailability of any
Aria Systems 600 AUD
16
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





