ECTE 992: Reviewing State-of-the-Art Internet of Things Technologies
VerifiedAdded on 2023/06/04
|4
|1809
|403
Report
AI Summary
This report provides an overview of the state-of-the-art in Internet of Things (IoT) technologies. It discusses the concept of IoT, its applications in various domains such as smart cities, home automation, healthcare, and industrial control, and the challenges faced in its practical implementation. The report highlights the characteristics of IoT, including comprehensive perception, reliable transmission, and intelligent processing. It also explores the use of expectation maximization indoor localization approach to address environmental impacts and heterogeneous factors. Furthermore, the report discusses energy-saving strategies for wireless communication in IoT and the increasing cyber and security threats, along with an ensemble intrusion detection technique to mitigate malicious events in IoT networks. The references cited provide further reading on the topics discussed.

Introduction:
The Internet of Things (IoT) is a latest communication standard that plays a major role at the
present and also in the near future. The concept of the IOT is to make a connection between a
microcontroller and the objects that we use in our daily life. Here the microcontroller is equipped
with the suitable protocol stacks with the necessary transmitters and receivers for the purpose of
digital communication. This could provide an essential communication between the users and the
peripheral devices through the internet [1]. This technology makes the internet usage more
persistent and immersive. Moreover, we could able to control our normal home appliance
electronic devices such as surveillance cameras, vehicles, switches, actuators etc, that leads to an
advancement and makes use of various devices potentially. IoT will promote the advancement of
a numerous application, which makes use of the huge amount of multiple data obtained from
those objects to promote novice services to citizens, companies, and public administration. We
could also use Internet of Things in various other domains that involve home automation,
healthcare in medical science, Industrial control, Energy management, traffic management, and
smart grids and so on [2].
Proposed state of art section:
IoT could be used for heterogeneous purposes but the challenge arises when it comes to satisfy
the entire proposed requirement that could be tedious. There arises certain difficulty for the
practical implementation of IoT in all the application. Therefore, from a system perspective, the
understanding of an IoT network, with the sufficient backend network services, still lacks an
established greatest practice due to its originality and difficulty. Moreover, there is a hindrance in
the acceptance of the business model for adapting and developing these technologies [3]. In this
situation the usage of IoT for the urban context became a field of interest since it pulls a strong
rush towards adapting the ICT solutions by the government to manage the public interest. This
came to be known by the concept of Smart city [4]. This aims in developing the quality of
service adapted by the citizens thereby utilizing the public resources with the minimum fund
from the administration. The development of urban IoT deals with the communication
infrastructure that offers easy and efficient access to the surplus of public services, thus
discharging possible synergies and maximizing candidness to the people. The development of
this concept could offer a major benefit that deals with the sufficient management and utilization
of services from the public sector in the area of transport, collecting garbage, street lights, and
preservation of public areas.
The general reference framework in designing an urban IoT has been discussed in the paper.
Several characteristic and the general rules for the adaptation of the IoT by the local government
has also been describes in the paper. The general network configuration with the “Padova Smart
City” project has been explained in detail. The Padova is a city in Italy. They have development
of IoT proof-of-concept with the sufficient data network which has been explained, which is
shown in the figure given below.
The Internet of Things (IoT) is a latest communication standard that plays a major role at the
present and also in the near future. The concept of the IOT is to make a connection between a
microcontroller and the objects that we use in our daily life. Here the microcontroller is equipped
with the suitable protocol stacks with the necessary transmitters and receivers for the purpose of
digital communication. This could provide an essential communication between the users and the
peripheral devices through the internet [1]. This technology makes the internet usage more
persistent and immersive. Moreover, we could able to control our normal home appliance
electronic devices such as surveillance cameras, vehicles, switches, actuators etc, that leads to an
advancement and makes use of various devices potentially. IoT will promote the advancement of
a numerous application, which makes use of the huge amount of multiple data obtained from
those objects to promote novice services to citizens, companies, and public administration. We
could also use Internet of Things in various other domains that involve home automation,
healthcare in medical science, Industrial control, Energy management, traffic management, and
smart grids and so on [2].
Proposed state of art section:
IoT could be used for heterogeneous purposes but the challenge arises when it comes to satisfy
the entire proposed requirement that could be tedious. There arises certain difficulty for the
practical implementation of IoT in all the application. Therefore, from a system perspective, the
understanding of an IoT network, with the sufficient backend network services, still lacks an
established greatest practice due to its originality and difficulty. Moreover, there is a hindrance in
the acceptance of the business model for adapting and developing these technologies [3]. In this
situation the usage of IoT for the urban context became a field of interest since it pulls a strong
rush towards adapting the ICT solutions by the government to manage the public interest. This
came to be known by the concept of Smart city [4]. This aims in developing the quality of
service adapted by the citizens thereby utilizing the public resources with the minimum fund
from the administration. The development of urban IoT deals with the communication
infrastructure that offers easy and efficient access to the surplus of public services, thus
discharging possible synergies and maximizing candidness to the people. The development of
this concept could offer a major benefit that deals with the sufficient management and utilization
of services from the public sector in the area of transport, collecting garbage, street lights, and
preservation of public areas.
The general reference framework in designing an urban IoT has been discussed in the paper.
Several characteristic and the general rules for the adaptation of the IoT by the local government
has also been describes in the paper. The general network configuration with the “Padova Smart
City” project has been explained in detail. The Padova is a city in Italy. They have development
of IoT proof-of-concept with the sufficient data network which has been explained, which is
shown in the figure given below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
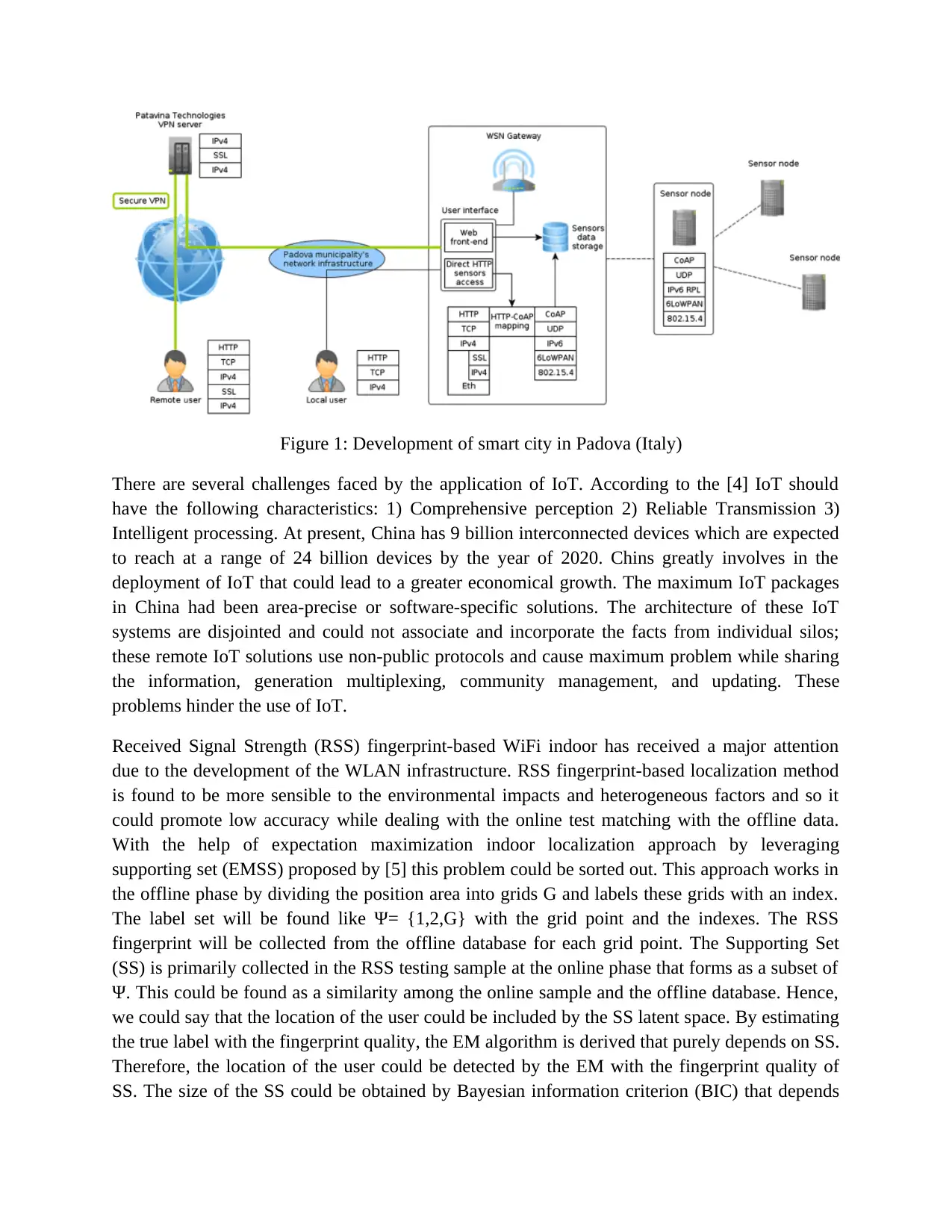
Figure 1: Development of smart city in Padova (Italy)
There are several challenges faced by the application of IoT. According to the [4] IoT should
have the following characteristics: 1) Comprehensive perception 2) Reliable Transmission 3)
Intelligent processing. At present, China has 9 billion interconnected devices which are expected
to reach at a range of 24 billion devices by the year of 2020. Chins greatly involves in the
deployment of IoT that could lead to a greater economical growth. The maximum IoT packages
in China had been area-precise or software-specific solutions. The architecture of these IoT
systems are disjointed and could not associate and incorporate the facts from individual silos;
these remote IoT solutions use non-public protocols and cause maximum problem while sharing
the information, generation multiplexing, community management, and updating. These
problems hinder the use of IoT.
Received Signal Strength (RSS) fingerprint-based WiFi indoor has received a major attention
due to the development of the WLAN infrastructure. RSS fingerprint-based localization method
is found to be more sensible to the environmental impacts and heterogeneous factors and so it
could promote low accuracy while dealing with the online test matching with the offline data.
With the help of expectation maximization indoor localization approach by leveraging
supporting set (EMSS) proposed by [5] this problem could be sorted out. This approach works in
the offline phase by dividing the position area into grids G and labels these grids with an index.
The label set will be found like Ψ= {1,2,G} with the grid point and the indexes. The RSS
fingerprint will be collected from the offline database for each grid point. The Supporting Set
(SS) is primarily collected in the RSS testing sample at the online phase that forms as a subset of
Ψ. This could be found as a similarity among the online sample and the offline database. Hence,
we could say that the location of the user could be included by the SS latent space. By estimating
the true label with the fingerprint quality, the EM algorithm is derived that purely depends on SS.
Therefore, the location of the user could be detected by the EM with the fingerprint quality of
SS. The size of the SS could be obtained by Bayesian information criterion (BIC) that depends
There are several challenges faced by the application of IoT. According to the [4] IoT should
have the following characteristics: 1) Comprehensive perception 2) Reliable Transmission 3)
Intelligent processing. At present, China has 9 billion interconnected devices which are expected
to reach at a range of 24 billion devices by the year of 2020. Chins greatly involves in the
deployment of IoT that could lead to a greater economical growth. The maximum IoT packages
in China had been area-precise or software-specific solutions. The architecture of these IoT
systems are disjointed and could not associate and incorporate the facts from individual silos;
these remote IoT solutions use non-public protocols and cause maximum problem while sharing
the information, generation multiplexing, community management, and updating. These
problems hinder the use of IoT.
Received Signal Strength (RSS) fingerprint-based WiFi indoor has received a major attention
due to the development of the WLAN infrastructure. RSS fingerprint-based localization method
is found to be more sensible to the environmental impacts and heterogeneous factors and so it
could promote low accuracy while dealing with the online test matching with the offline data.
With the help of expectation maximization indoor localization approach by leveraging
supporting set (EMSS) proposed by [5] this problem could be sorted out. This approach works in
the offline phase by dividing the position area into grids G and labels these grids with an index.
The label set will be found like Ψ= {1,2,G} with the grid point and the indexes. The RSS
fingerprint will be collected from the offline database for each grid point. The Supporting Set
(SS) is primarily collected in the RSS testing sample at the online phase that forms as a subset of
Ψ. This could be found as a similarity among the online sample and the offline database. Hence,
we could say that the location of the user could be included by the SS latent space. By estimating
the true label with the fingerprint quality, the EM algorithm is derived that purely depends on SS.
Therefore, the location of the user could be detected by the EM with the fingerprint quality of
SS. The size of the SS could be obtained by Bayesian information criterion (BIC) that depends

on the optimal size selection (OSS) algorithm that is also proposed in [5]. With the help of this
approach we could be able to deal with the environment impact with the heterogeneous hardware
that could also be practically implemented. The accuracy of this EMSS approach is found be
higher when compared to the other fingerprint approach.
In order to prolong the life of IoT for several years it is necessary to make the the wireless
protocols more energy-efficient for the IoT communication. There are two energy-saving
strategies for wireless communication that are used widely in the IoT domain: sleepy devices and
radio duty cycling. The evaluation was made in [6] that show the sufficient method for the
energy saving in the IoT domain. For this category, Lightweight Machine to Machine (LwM2M)
protocol has been used [7] since this protocol operates at standard Constrained Application
Protocol (CoAP) that operates at queue mode for the sleepy devices. The Queue mode should be
necessarily both at the server as well as the client side. The mode could be further improved for
the better performance. The evaluation in [8] deals with the comparison of characteristic and
performance of Queue mode that runs with LwM2M with the standard Time-Slotted Channel
Hopping (TSCH) in a stack network. The analysis shows the strategy of the energy-saving with
the empirical model, which has several pros and cons based on the data traffic and situation.
Based on the application, it is necessary to choose the sufficient energy-saving model by
referring the guidelines.
The advancement of IoT has been sufficiently increased that also increases the cyber and security
threats in the services. The vulnerable action could be carried out by the attackers that could
disturb the application of the protocols, which includes Name System (DNS), Hyper Text
Transfer Protocol (HTTP) and Message Queue Telemetry Transport (MQTT). These are
essential protocols that interact with the database system at the backend. The exploitation in
these could cause data leakage that causes major threats. In order to avoid this, an ensemble
intrusion detection technique has been proposed in [9]. This could alleviate malicious events in
the DNS, HTTP and MQTT protocols utilized in IoT networks [10].
References:
Atzori, A. Iera, G. Morabito, "The internet of things: A survey", Comput. Netw., vol. 54, no. 15,
pp. 2787-2805, 2010.
P. Bellavista, G. Cardone, A. Corradi, L. Foschini, "Convergence of MANET and WSN in IoT
urban scenarios", IEEE Sens. J., IEEE, vol. 13, no. 10, pp. 3558-3567, Oct. 2013.
A. Laya, V. I. Bratu, J. Markendahl, "Who is investing in machine-to-machine
communications?", Proc. 24th Eur. Reg. ITS Conf., pp. 20-23, Oct. 2013.
T. Liu, D. Lu, "The application and development of IoT", Proc. Int. Symp. Inf. Technol. Med.
Educ. (ITME), vol. 2, pp. 991-994, 2012.
approach we could be able to deal with the environment impact with the heterogeneous hardware
that could also be practically implemented. The accuracy of this EMSS approach is found be
higher when compared to the other fingerprint approach.
In order to prolong the life of IoT for several years it is necessary to make the the wireless
protocols more energy-efficient for the IoT communication. There are two energy-saving
strategies for wireless communication that are used widely in the IoT domain: sleepy devices and
radio duty cycling. The evaluation was made in [6] that show the sufficient method for the
energy saving in the IoT domain. For this category, Lightweight Machine to Machine (LwM2M)
protocol has been used [7] since this protocol operates at standard Constrained Application
Protocol (CoAP) that operates at queue mode for the sleepy devices. The Queue mode should be
necessarily both at the server as well as the client side. The mode could be further improved for
the better performance. The evaluation in [8] deals with the comparison of characteristic and
performance of Queue mode that runs with LwM2M with the standard Time-Slotted Channel
Hopping (TSCH) in a stack network. The analysis shows the strategy of the energy-saving with
the empirical model, which has several pros and cons based on the data traffic and situation.
Based on the application, it is necessary to choose the sufficient energy-saving model by
referring the guidelines.
The advancement of IoT has been sufficiently increased that also increases the cyber and security
threats in the services. The vulnerable action could be carried out by the attackers that could
disturb the application of the protocols, which includes Name System (DNS), Hyper Text
Transfer Protocol (HTTP) and Message Queue Telemetry Transport (MQTT). These are
essential protocols that interact with the database system at the backend. The exploitation in
these could cause data leakage that causes major threats. In order to avoid this, an ensemble
intrusion detection technique has been proposed in [9]. This could alleviate malicious events in
the DNS, HTTP and MQTT protocols utilized in IoT networks [10].
References:
Atzori, A. Iera, G. Morabito, "The internet of things: A survey", Comput. Netw., vol. 54, no. 15,
pp. 2787-2805, 2010.
P. Bellavista, G. Cardone, A. Corradi, L. Foschini, "Convergence of MANET and WSN in IoT
urban scenarios", IEEE Sens. J., IEEE, vol. 13, no. 10, pp. 3558-3567, Oct. 2013.
A. Laya, V. I. Bratu, J. Markendahl, "Who is investing in machine-to-machine
communications?", Proc. 24th Eur. Reg. ITS Conf., pp. 20-23, Oct. 2013.
T. Liu, D. Lu, "The application and development of IoT", Proc. Int. Symp. Inf. Technol. Med.
Educ. (ITME), vol. 2, pp. 991-994, 2012.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

X. Guo, L. Li, F. Xu and N. Ansari, "Expectation Maximization Indoor Localization Utilizing
Supporting Set for Internet of Things," in IEEE Internet of Things Journal.
doi: 10.1109/JIOT.2018.2871831
N. Moustafa, B. Turnbull and K. R. Choo, "An Ensemble Intrusion Detection Technique based
on proposed Statistical Flow Features for Protecting Network Traffic of Internet of Things,"
in IEEE Internet of Things Journal
Chen, S.-L., Chang, S.-K. and Chen, “Development of a multisensor embedded intelligent home
environment monitoring system based on digital signal processor and Wi-Fi,” in Int. J. Distrib.
Sens. Netw, 2015.
M.S. Nguyen, and Q. Le-Trung, “Low-Power and Cost-Effective WiFi Sensor Motes for
Wireless Embedded Internet Applications” In 2014 Int. Conf. on Advanced Technologies for
Communications (ATC 2014), October, pp. 441–445.
N. Moustafa, B. Turnbull and K. R. Choo, "An Ensemble Intrusion Detection Technique based
on proposed Statistical Flow Features for Protecting Network Traffic of Internet of Things,"
in IEEE Internet of Things Journal.
doi: 10.1109/JIOT.2018.2871719
L. Zhi-Gang, and H. Wei, “The Design of Smart Home System Based on Wi-Fi”, In Int. Conf.
Computational Problem-Solving (ICCP), October, pp. 454–456.
Supporting Set for Internet of Things," in IEEE Internet of Things Journal.
doi: 10.1109/JIOT.2018.2871831
N. Moustafa, B. Turnbull and K. R. Choo, "An Ensemble Intrusion Detection Technique based
on proposed Statistical Flow Features for Protecting Network Traffic of Internet of Things,"
in IEEE Internet of Things Journal
Chen, S.-L., Chang, S.-K. and Chen, “Development of a multisensor embedded intelligent home
environment monitoring system based on digital signal processor and Wi-Fi,” in Int. J. Distrib.
Sens. Netw, 2015.
M.S. Nguyen, and Q. Le-Trung, “Low-Power and Cost-Effective WiFi Sensor Motes for
Wireless Embedded Internet Applications” In 2014 Int. Conf. on Advanced Technologies for
Communications (ATC 2014), October, pp. 441–445.
N. Moustafa, B. Turnbull and K. R. Choo, "An Ensemble Intrusion Detection Technique based
on proposed Statistical Flow Features for Protecting Network Traffic of Internet of Things,"
in IEEE Internet of Things Journal.
doi: 10.1109/JIOT.2018.2871719
L. Zhi-Gang, and H. Wei, “The Design of Smart Home System Based on Wi-Fi”, In Int. Conf.
Computational Problem-Solving (ICCP), October, pp. 454–456.
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





