Internet Technologies Homework: Network Protocols, DHT, and Addressing
VerifiedAdded on 2021/06/18
|12
|2930
|55
Homework Assignment
AI Summary
This assignment solution provides a comprehensive overview of several key concepts in Internet Technologies. It begins with an explanation of TCP and UDP protocols, detailing their data encapsulation, connection-oriented versus connectionless characteristics, and the three-way handshake. The solution then applies Shannon's theorem and Nyquist formula to calculate bit rates and signal levels, followed by a comparison of baseband and broadband transmission methods, highlighting their differences in signaling, bandwidth usage, and topology. Furthermore, it differentiates between IPv6 compatible and mapped addresses, elucidating their roles in the transition to IPv6. The assignment also explores Distributed Hash Tables (DHTs), describing their structure, functionalities, and applications in peer-to-peer networks, including a discussion of Chord's ring topology and its design considerations. Finally, the solution explains how a client finds the IP address and port number of a server, outlining the communication steps involved in establishing a connection. The assignment incorporates relevant figures and references to support the analysis.

Running head: INTERNET TECHNOLOGIES
Internet Technologies
Name of the Student
Name of the University
Author Note
Internet Technologies
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET TECHNOLOGIES
Table of Contents
Answer 1:...................................................................................................................................4
Answer 2:...................................................................................................................................5
Answer 3:...................................................................................................................................5
Answer 4:...................................................................................................................................6
Answer 5:...................................................................................................................................7
Answer 6:...................................................................................................................................9
Bibliography.............................................................................................................................11
Table of Contents
Answer 1:...................................................................................................................................4
Answer 2:...................................................................................................................................5
Answer 3:...................................................................................................................................5
Answer 4:...................................................................................................................................6
Answer 5:...................................................................................................................................7
Answer 6:...................................................................................................................................9
Bibliography.............................................................................................................................11

2INTERNET TECHNOLOGIES
Answer 1:
When an Email is send by the source using the TCP, the data arrive at the transport
layer where the data encapsulation protocol begins. The end result will depend on the
information handle by the TCP or PDU. TCP is a connection-oriented protocol where the
data is a successful deliver at the receiving host. The data that has been received from the
application layer, TCP divides that data into multiple segments and to each segments a header
is attached. The header of the segment contain the ports of the sender and the recipient,
ordering information of the segment and field of data, which is also known as checksum. On
both the hosts of the TCP protocols the checksum data is used and determine that the data
transferred is with error or without error. In order to establish a connection through TCP, the
segments are used by TCP that determine whether the host who will be receiving is ready for
the data to receive. The sending TCP establishes a connections on the host who will be
receiving, that sends a SYN segment to the running peer TCP protocol. The TCP that is
receiving returns an ACK segment and acknowledge the segment receipt successfully. There
is another ACK segment that the sending TCP sends. Such control information that exchange
is referred as three-way handshake.
The PDU protocol is connectionless. The message received from the application layer
is taken by the PDU protocol. It then format into UDP packets. In each of the packet of the
PDU a header is attached in which there is a host port for sending and receiving, a checksum
and a field with packet length. The packet then send by the sending PDU process to the peer
PDU process where the host can receive it. Through application layer it can be determine that
packet was receive by the receiving PDU process. There is no notification requires for the
receipt by the PDU. Moreover, the three-way handshake is not used by the PDU.
Answer 1:
When an Email is send by the source using the TCP, the data arrive at the transport
layer where the data encapsulation protocol begins. The end result will depend on the
information handle by the TCP or PDU. TCP is a connection-oriented protocol where the
data is a successful deliver at the receiving host. The data that has been received from the
application layer, TCP divides that data into multiple segments and to each segments a header
is attached. The header of the segment contain the ports of the sender and the recipient,
ordering information of the segment and field of data, which is also known as checksum. On
both the hosts of the TCP protocols the checksum data is used and determine that the data
transferred is with error or without error. In order to establish a connection through TCP, the
segments are used by TCP that determine whether the host who will be receiving is ready for
the data to receive. The sending TCP establishes a connections on the host who will be
receiving, that sends a SYN segment to the running peer TCP protocol. The TCP that is
receiving returns an ACK segment and acknowledge the segment receipt successfully. There
is another ACK segment that the sending TCP sends. Such control information that exchange
is referred as three-way handshake.
The PDU protocol is connectionless. The message received from the application layer
is taken by the PDU protocol. It then format into UDP packets. In each of the packet of the
PDU a header is attached in which there is a host port for sending and receiving, a checksum
and a field with packet length. The packet then send by the sending PDU process to the peer
PDU process where the host can receive it. Through application layer it can be determine that
packet was receive by the receiving PDU process. There is no notification requires for the
receipt by the PDU. Moreover, the three-way handshake is not used by the PDU.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INTERNET TECHNOLOGIES
Answer 2:
The formula known to us is bit rate = Bandwidth*log (1+SNR)
It is given that, Bandwidth = 7 x 10^6
SNR = 64
Hence bit rate = 7 x 10^6 log (65) = 7 x 6. 022 x 10^ 6 = 42.154 Mbps
The Shannon formula gives us 42.154 Mbps, the upper limit. For better performance we
choose something lower, 32 Mbps, for example. Then we use the Nyquist formula to find the
number of signal levels.
32 Mbps = 2x 1 MHz x log L
L = 65536
Hence the signal level is 65536
Answer 3:
The comparison of baseband and broadband transmission are as follows.
The baseband transmission uses digital signalling rather than single wire and it is
either in form of light or electrical pulse. The overall bandwidth is occupied by digital signal
that is used in baseband transmission. This is used to transmit an individual data signal. The
communication emerging through baseband is bidirectional that allows computer devices to
use single cable for sending and receiving data. However, in baseband communication, the
data that is sent and received cannot happen at the same time and at the same wire. The
multiplexing is the process used by baseband transmissions to transmit multiple digital
signals on a single wire. The baseband communication uses time division multiplexing where
Answer 2:
The formula known to us is bit rate = Bandwidth*log (1+SNR)
It is given that, Bandwidth = 7 x 10^6
SNR = 64
Hence bit rate = 7 x 10^6 log (65) = 7 x 6. 022 x 10^ 6 = 42.154 Mbps
The Shannon formula gives us 42.154 Mbps, the upper limit. For better performance we
choose something lower, 32 Mbps, for example. Then we use the Nyquist formula to find the
number of signal levels.
32 Mbps = 2x 1 MHz x log L
L = 65536
Hence the signal level is 65536
Answer 3:
The comparison of baseband and broadband transmission are as follows.
The baseband transmission uses digital signalling rather than single wire and it is
either in form of light or electrical pulse. The overall bandwidth is occupied by digital signal
that is used in baseband transmission. This is used to transmit an individual data signal. The
communication emerging through baseband is bidirectional that allows computer devices to
use single cable for sending and receiving data. However, in baseband communication, the
data that is sent and received cannot happen at the same time and at the same wire. The
multiplexing is the process used by baseband transmissions to transmit multiple digital
signals on a single wire. The baseband communication uses time division multiplexing where
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INTERNET TECHNOLOGIES
channels are divided into multiple time slots. The time division multiplexing does not
changes the working of baseband transmission, it only changes the way data is used in cable.
The broadband transmission uses analog signals which is in the form of
electromagnetic waves or optical rays rather than multiple frequencies of transmission. The
transmission media is split into two channels that is used for sending and receiving signals.
There are two cables which are used in broadband to separately send and receive data
transmission. The broadband communication uses frequency division multiplexing where
multiple channels in a broadband system are created. The broadband media is allowed in this
multiplexing process to accommodate traffic that goes in different directions at the same time
on an individual network media.
The baseband transmission works best with bus topology whereas broadband
transmission uses bus and tree topology. The encoding use din broadband communication is
Manchester and differential Manchester encoding whereas in broadband communication,
PSK encoding is used.
The broadband transmission is efficient for short distances whereas baseband
transmission is efficient for long distances. Hence, both are efficient for different purposes.
Answer 4:
The difference between the ipv6 compatible and the mapped addresses are provided
below:
IPv4 (normal legacy internet protocol) uses A (address) records in DNS. IPv6 (the
next generation protocol capable of supporting everyone and everything that wants to get
internet access) uses AAAA records. It’s possible, and quite common, for a system to obtain
IPv6 DNS records over IPv4 and then communicate directly with a host on IPv6. Since DNS
is hierarchical, it is not necessary that all DNS be directly accessible via IPv6 since
channels are divided into multiple time slots. The time division multiplexing does not
changes the working of baseband transmission, it only changes the way data is used in cable.
The broadband transmission uses analog signals which is in the form of
electromagnetic waves or optical rays rather than multiple frequencies of transmission. The
transmission media is split into two channels that is used for sending and receiving signals.
There are two cables which are used in broadband to separately send and receive data
transmission. The broadband communication uses frequency division multiplexing where
multiple channels in a broadband system are created. The broadband media is allowed in this
multiplexing process to accommodate traffic that goes in different directions at the same time
on an individual network media.
The baseband transmission works best with bus topology whereas broadband
transmission uses bus and tree topology. The encoding use din broadband communication is
Manchester and differential Manchester encoding whereas in broadband communication,
PSK encoding is used.
The broadband transmission is efficient for short distances whereas baseband
transmission is efficient for long distances. Hence, both are efficient for different purposes.
Answer 4:
The difference between the ipv6 compatible and the mapped addresses are provided
below:
IPv4 (normal legacy internet protocol) uses A (address) records in DNS. IPv6 (the
next generation protocol capable of supporting everyone and everything that wants to get
internet access) uses AAAA records. It’s possible, and quite common, for a system to obtain
IPv6 DNS records over IPv4 and then communicate directly with a host on IPv6. Since DNS
is hierarchical, it is not necessary that all DNS be directly accessible via IPv6 since

5INTERNET TECHNOLOGIES
intermediate DNS servers can proxy and cache queries. However, the addresses that are
capable of holding IPv4 address and can represent the IPv4 nodes as the IPv6 addresses for
the applications that have the IPv6 addressing enabled in them. This allows the application to
deal with addresses of the IPv6 format only. They make use of the AF_INET6 sockets for
this purpose and also the communications for the applications are done over the IPv6v
networks. The TCP/IP stack is assigned with the task of transformation of the address. The
IPv6 addresses generally have the 80 bits long addresses.
In addition to this, it should also be noted that the IPv6 does not have any specific
hardware requirement. IPv6 is a protocol, so compatibility with IPv6 networking is mainly a
software or firmware issue. The introduction of Classless Inter-Domain Routing (CIDR) in
the routing and IP address allocation for the Internet, and the extensive use of network
address translation (NAT) has delayed the IPv4 address exhaustion however, NAT can be
used to use existing IPv4 address by a large number of devices and the transformation takes
place slowly.
Answer 5:
Distributed Hash Table (DHT) is a kind of dictionary service distributed over the
network which has an access to a shared key>value data store. This keys are distributed over
the nodes containing great scalability and performance. It has a mapping interface with two
main operations that are put (key, value) and get (key). The put function will be storing value
over the network. The get function will retrieve those values that are stored at certain key.
Distributed Hash Table (DHT) is mainly used for their scalability.
DHT is used as a structured overlays in Peer-to-Peer (P2P) network. It stores and
retrieve the efficiency of the data. In the network of DHT P2P, every node has a Globally
unique identifier (GUID) and for the distributed data, this node functions as a container. The
intermediate DNS servers can proxy and cache queries. However, the addresses that are
capable of holding IPv4 address and can represent the IPv4 nodes as the IPv6 addresses for
the applications that have the IPv6 addressing enabled in them. This allows the application to
deal with addresses of the IPv6 format only. They make use of the AF_INET6 sockets for
this purpose and also the communications for the applications are done over the IPv6v
networks. The TCP/IP stack is assigned with the task of transformation of the address. The
IPv6 addresses generally have the 80 bits long addresses.
In addition to this, it should also be noted that the IPv6 does not have any specific
hardware requirement. IPv6 is a protocol, so compatibility with IPv6 networking is mainly a
software or firmware issue. The introduction of Classless Inter-Domain Routing (CIDR) in
the routing and IP address allocation for the Internet, and the extensive use of network
address translation (NAT) has delayed the IPv4 address exhaustion however, NAT can be
used to use existing IPv4 address by a large number of devices and the transformation takes
place slowly.
Answer 5:
Distributed Hash Table (DHT) is a kind of dictionary service distributed over the
network which has an access to a shared key>value data store. This keys are distributed over
the nodes containing great scalability and performance. It has a mapping interface with two
main operations that are put (key, value) and get (key). The put function will be storing value
over the network. The get function will retrieve those values that are stored at certain key.
Distributed Hash Table (DHT) is mainly used for their scalability.
DHT is used as a structured overlays in Peer-to-Peer (P2P) network. It stores and
retrieve the efficiency of the data. In the network of DHT P2P, every node has a Globally
unique identifier (GUID) and for the distributed data, this node functions as a container. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
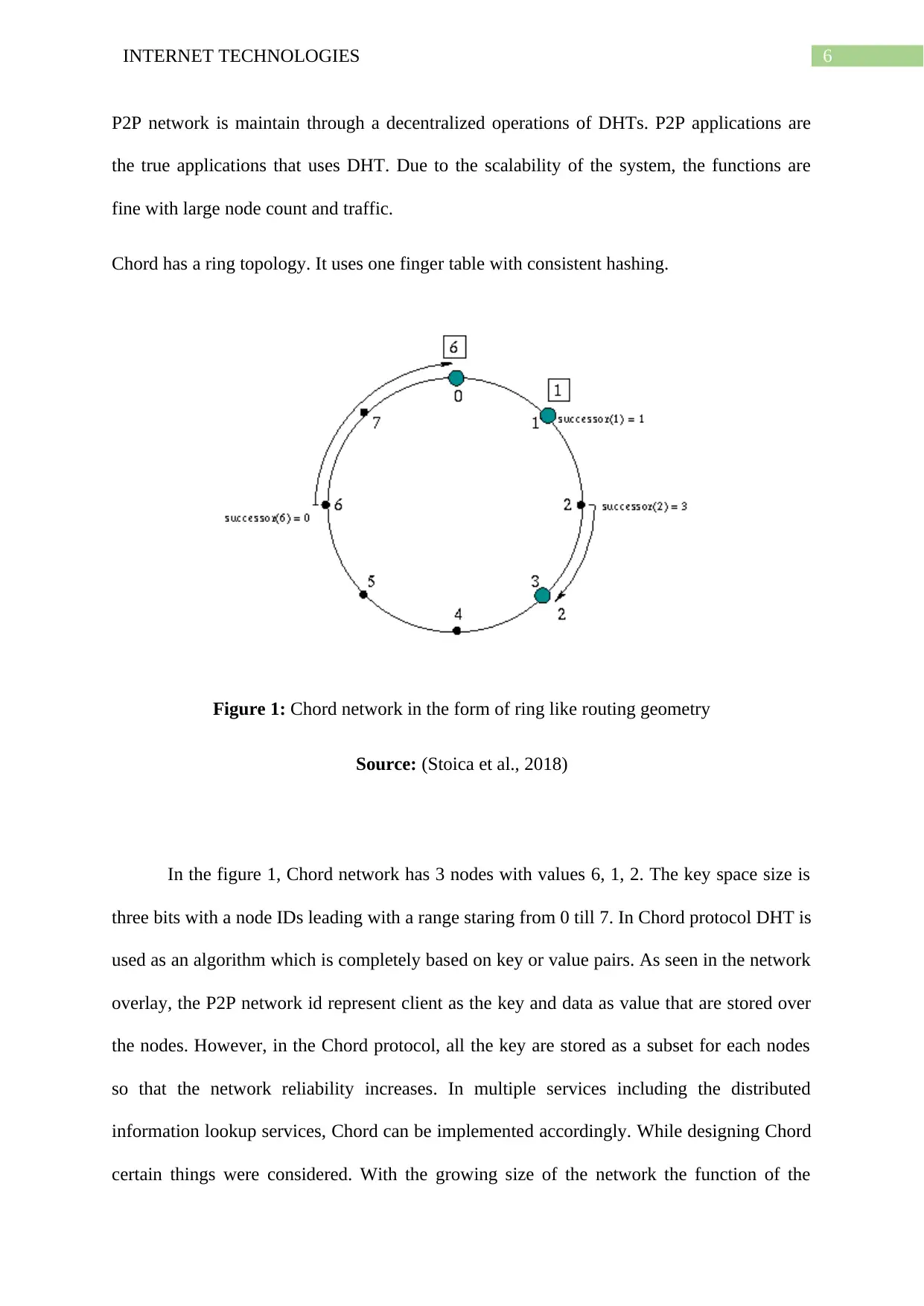
6INTERNET TECHNOLOGIES
P2P network is maintain through a decentralized operations of DHTs. P2P applications are
the true applications that uses DHT. Due to the scalability of the system, the functions are
fine with large node count and traffic.
Chord has a ring topology. It uses one finger table with consistent hashing.
Figure 1: Chord network in the form of ring like routing geometry
Source: (Stoica et al., 2018)
In the figure 1, Chord network has 3 nodes with values 6, 1, 2. The key space size is
three bits with a node IDs leading with a range staring from 0 till 7. In Chord protocol DHT is
used as an algorithm which is completely based on key or value pairs. As seen in the network
overlay, the P2P network id represent client as the key and data as value that are stored over
the nodes. However, in the Chord protocol, all the key are stored as a subset for each nodes
so that the network reliability increases. In multiple services including the distributed
information lookup services, Chord can be implemented accordingly. While designing Chord
certain things were considered. With the growing size of the network the function of the
P2P network is maintain through a decentralized operations of DHTs. P2P applications are
the true applications that uses DHT. Due to the scalability of the system, the functions are
fine with large node count and traffic.
Chord has a ring topology. It uses one finger table with consistent hashing.
Figure 1: Chord network in the form of ring like routing geometry
Source: (Stoica et al., 2018)
In the figure 1, Chord network has 3 nodes with values 6, 1, 2. The key space size is
three bits with a node IDs leading with a range staring from 0 till 7. In Chord protocol DHT is
used as an algorithm which is completely based on key or value pairs. As seen in the network
overlay, the P2P network id represent client as the key and data as value that are stored over
the nodes. However, in the Chord protocol, all the key are stored as a subset for each nodes
so that the network reliability increases. In multiple services including the distributed
information lookup services, Chord can be implemented accordingly. While designing Chord
certain things were considered. With the growing size of the network the function of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INTERNET TECHNOLOGIES
system was efficient which indicates that the system is Scalable. In some situation the nodes
fail or it may happen that the system even function during network partitions. This means the
availability of the system is fine. With the use of DHT algorithm, Updatability increases
which means data can be easily updated. The operation of Load-Balanced has key or value
pairs that are distributed evenly in the system. Based on the proximity, data are fetched from
the query originating node were the search value is stored. The design of Chord do not render
the network partitions. In each node the Chord maintains a table of location. The function of
the table is like a cache that contains the recent nodes. The routing table is basically a cache
in which the identifiers of the node are map with respect to the ports and the IP-addresses.
Thus, in the whole process of Chord protocol works though a DHT algorithm.
Answer 6:
The client need to either know the IP address in which they will be sending the port
number. The client first sends the port number to the server, the server checks the address
whether it matches with the IP address of the server, if not the server rejects the address send
by the client stating that the address does not match server address. The client then again send
another IP address to the server one after the other until it matches one IP address.
The client first make a request for the connection. For that a particular port number
will be bound by the server which is a listening process only for the server. Here only the
server will be listening to the connection that is incoming. There is no need of binding with
the client side. The server than keep on checking with the port number. At this point connect
() request will be send by the client. The server then will accept the request by using the
function accept (). When the server cannot used same port number for the process of sending
and listening as the previous port that is send, the server is still listening to it for the new
connection. The point at which the server accept the request of the client then and there the
kernel decide to allocates a port number that is random for the server for the process of
system was efficient which indicates that the system is Scalable. In some situation the nodes
fail or it may happen that the system even function during network partitions. This means the
availability of the system is fine. With the use of DHT algorithm, Updatability increases
which means data can be easily updated. The operation of Load-Balanced has key or value
pairs that are distributed evenly in the system. Based on the proximity, data are fetched from
the query originating node were the search value is stored. The design of Chord do not render
the network partitions. In each node the Chord maintains a table of location. The function of
the table is like a cache that contains the recent nodes. The routing table is basically a cache
in which the identifiers of the node are map with respect to the ports and the IP-addresses.
Thus, in the whole process of Chord protocol works though a DHT algorithm.
Answer 6:
The client need to either know the IP address in which they will be sending the port
number. The client first sends the port number to the server, the server checks the address
whether it matches with the IP address of the server, if not the server rejects the address send
by the client stating that the address does not match server address. The client then again send
another IP address to the server one after the other until it matches one IP address.
The client first make a request for the connection. For that a particular port number
will be bound by the server which is a listening process only for the server. Here only the
server will be listening to the connection that is incoming. There is no need of binding with
the client side. The server than keep on checking with the port number. At this point connect
() request will be send by the client. The server then will accept the request by using the
function accept (). When the server cannot used same port number for the process of sending
and listening as the previous port that is send, the server is still listening to it for the new
connection. The point at which the server accept the request of the client then and there the
kernel decide to allocates a port number that is random for the server for the process of

8INTERNET TECHNOLOGIES
sending and receiving using the function send () and receive (). The server if wanted to find
what port the client has to receive, the answer to it is simple. The client will think of sending
the segment of TCP with a source port. Another way in which the client can find the IP
address or the port number is that if they know the server name and then decide to use the
DNS which is the Domain Name System and try to map the name with the IP address. The
next thing is that for the corresponding server process, the client has to know what the port
number is. Thus, in this way the IP address and the port number will be easily found by the
client that has to insert in the address of the remote socket.
sending and receiving using the function send () and receive (). The server if wanted to find
what port the client has to receive, the answer to it is simple. The client will think of sending
the segment of TCP with a source port. Another way in which the client can find the IP
address or the port number is that if they know the server name and then decide to use the
DNS which is the Domain Name System and try to map the name with the IP address. The
next thing is that for the corresponding server process, the client has to know what the port
number is. Thus, in this way the IP address and the port number will be easily found by the
client that has to insert in the address of the remote socket.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET TECHNOLOGIES
Bibliography
Albkerat, A., & Issac, B. (2014). Analysis of IPv6 transition technologies. arXiv preprint
arXiv:1410.2013.
Alotaibi, A. M., Alrashidi, B. F., Naz, S., & Parveen, Z. (2017). Security issues in Protocols
of TCP/IP Model at Layers Level. International Journal of Computer Networks and
Communications Security, 5(5), 96.
Boes, F., Messinger, T., Antes, J., Meier, D., Tessmann, A., Inam, A., & Kallfass, I. (2014,
September). Ultra-broadband MMIC-based wireless link at 240 GHz enabled by
64GS/s DAC. In Infrared, Millimeter, and Terahertz waves (IRMMW-THz), 2014
39th International Conference on (pp. 1-2). IEEE.
Felber, P., Kropf, P., Schiller, E., & Serbu, S. (2014). Survey on load balancing in peer-to-
peer distributed hash tables. IEEE Communications Surveys & Tutorials, 16(1), 473-
492.
Fifield, D., Geana, A., MartinGarcia, L., Morbitzer, M., & Tygar, J. D. (2015, October).
Remote operating system classification over IPv6. In Proceedings of the 8th ACM
Workshop on Artificial Intelligence and Security (pp. 57-67). ACM.
Grasa, E., Bergesio, L., Tarzan, M., Trouva, E., Gaston, B., Salvestrini, F., ... & Colle, D.
(2016). Recursive InterNetwork Architecture, Investigating RINA as an Alternative to
TCP/IP (IRATI). In Building the Future Internet through FIRE (pp. 491-520).
Hudlička, M., Salhi, M., Kleine-Ostmann, T., & Schrader, T. (2017). Characterization of a
300-GHz Transmission System for Digital Communications. Journal of Infrared,
Millimeter, and Terahertz Waves, 38(8), 1004-1018.
Bibliography
Albkerat, A., & Issac, B. (2014). Analysis of IPv6 transition technologies. arXiv preprint
arXiv:1410.2013.
Alotaibi, A. M., Alrashidi, B. F., Naz, S., & Parveen, Z. (2017). Security issues in Protocols
of TCP/IP Model at Layers Level. International Journal of Computer Networks and
Communications Security, 5(5), 96.
Boes, F., Messinger, T., Antes, J., Meier, D., Tessmann, A., Inam, A., & Kallfass, I. (2014,
September). Ultra-broadband MMIC-based wireless link at 240 GHz enabled by
64GS/s DAC. In Infrared, Millimeter, and Terahertz waves (IRMMW-THz), 2014
39th International Conference on (pp. 1-2). IEEE.
Felber, P., Kropf, P., Schiller, E., & Serbu, S. (2014). Survey on load balancing in peer-to-
peer distributed hash tables. IEEE Communications Surveys & Tutorials, 16(1), 473-
492.
Fifield, D., Geana, A., MartinGarcia, L., Morbitzer, M., & Tygar, J. D. (2015, October).
Remote operating system classification over IPv6. In Proceedings of the 8th ACM
Workshop on Artificial Intelligence and Security (pp. 57-67). ACM.
Grasa, E., Bergesio, L., Tarzan, M., Trouva, E., Gaston, B., Salvestrini, F., ... & Colle, D.
(2016). Recursive InterNetwork Architecture, Investigating RINA as an Alternative to
TCP/IP (IRATI). In Building the Future Internet through FIRE (pp. 491-520).
Hudlička, M., Salhi, M., Kleine-Ostmann, T., & Schrader, T. (2017). Characterization of a
300-GHz Transmission System for Digital Communications. Journal of Infrared,
Millimeter, and Terahertz Waves, 38(8), 1004-1018.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INTERNET TECHNOLOGIES
Lebrun, D., Jadin, M., Clad, F., Filsfils, C., & Bonaventure, O. (2018, March). Software
Resolved Networks: Rethinking Enterprise Networks with IPv6 Segment Routing.
In Proceedings of the Symposium on SDN Research (p. 6). ACM.
Lemos, J. S., Monteiro, F. A., Sousa, I., & Rodrigues, A. (2015). Recursive least squares self-
interference mitigation in broadband MIMO full-duplex relays. arXiv preprint arXiv:
1505.00850.
Liao, L., Henson, B., & Zakharov, Y. (2017, September). Grid Waymark baseband
underwater acoustic transmission model. In Underwater Acoustics Conference and
Exhibition (pp. 343-350).
Perta, V. C., Barbera, M. V., Tyson, G., Haddadi, H., & Mei, A. (2015). A glance through the
VPN looking glass: IPv6 leakage and DNS hijacking in commercial VPN
clients. Proceedings on Privacy Enhancing Technologies, 2015(1), 77-91.
Pujol, E., Richter, P., & Feldmann, A. (2017, March). Understanding the Share of IPv6
Traffic in a Dual-stack ISP. In International Conference on Passive and Active
Network Measurement (pp. 3-16). Springer, Cham.
Sha, F., Chen, X., Ye, R., Wu, M., Zhang, Z., & Cai, W. (2017, May). A communication
method between IPv4 server and IPv6 network in virtual machine environment.
In Computer and Information Science (ICIS), 2017 IEEE/ACIS 16th International
Conference on (pp. 885-888). IEEE.
Shojafar, M., Abawajy, J. H., Delkhah, Z., Ahmadi, A., Pooranian, Z., & Abraham, A.
(2015). An efficient and distributed file search in unstructured peer-to-peer
networks. Peer-to-peer networking and applications, 8(1), 120-136.
Lebrun, D., Jadin, M., Clad, F., Filsfils, C., & Bonaventure, O. (2018, March). Software
Resolved Networks: Rethinking Enterprise Networks with IPv6 Segment Routing.
In Proceedings of the Symposium on SDN Research (p. 6). ACM.
Lemos, J. S., Monteiro, F. A., Sousa, I., & Rodrigues, A. (2015). Recursive least squares self-
interference mitigation in broadband MIMO full-duplex relays. arXiv preprint arXiv:
1505.00850.
Liao, L., Henson, B., & Zakharov, Y. (2017, September). Grid Waymark baseband
underwater acoustic transmission model. In Underwater Acoustics Conference and
Exhibition (pp. 343-350).
Perta, V. C., Barbera, M. V., Tyson, G., Haddadi, H., & Mei, A. (2015). A glance through the
VPN looking glass: IPv6 leakage and DNS hijacking in commercial VPN
clients. Proceedings on Privacy Enhancing Technologies, 2015(1), 77-91.
Pujol, E., Richter, P., & Feldmann, A. (2017, March). Understanding the Share of IPv6
Traffic in a Dual-stack ISP. In International Conference on Passive and Active
Network Measurement (pp. 3-16). Springer, Cham.
Sha, F., Chen, X., Ye, R., Wu, M., Zhang, Z., & Cai, W. (2017, May). A communication
method between IPv4 server and IPv6 network in virtual machine environment.
In Computer and Information Science (ICIS), 2017 IEEE/ACIS 16th International
Conference on (pp. 885-888). IEEE.
Shojafar, M., Abawajy, J. H., Delkhah, Z., Ahmadi, A., Pooranian, Z., & Abraham, A.
(2015). An efficient and distributed file search in unstructured peer-to-peer
networks. Peer-to-peer networking and applications, 8(1), 120-136.

11INTERNET TECHNOLOGIES
Stoica et al. (2018). Chord Implementation [Image]. Retrieved from
http://www.dcs.ed.ac.uk/teaching/cs3/ipse/successor.gif
Zuo, X., & Iamnitchi, A. (2016). A survey of socially aware peer-to-peer systems. ACM
Computing Surveys (CSUR), 49(1), 9.
Zuo, X., & Iamnitchi, A. (2016). A survey of socially aware peer-to-peer systems. ACM
Computing Surveys (CSUR), 49(1), 9.
Stoica et al. (2018). Chord Implementation [Image]. Retrieved from
http://www.dcs.ed.ac.uk/teaching/cs3/ipse/successor.gif
Zuo, X., & Iamnitchi, A. (2016). A survey of socially aware peer-to-peer systems. ACM
Computing Surveys (CSUR), 49(1), 9.
Zuo, X., & Iamnitchi, A. (2016). A survey of socially aware peer-to-peer systems. ACM
Computing Surveys (CSUR), 49(1), 9.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





