Comprehensive Analysis of Internet Technology Concepts and Protocols
VerifiedAdded on 2020/05/28
|12
|2047
|84
Homework Assignment
AI Summary
This assignment solution delves into core concepts of Internet Technology, beginning with a detailed explanation of the file transfer process across the TCP/IP model, breaking down the roles of each layer (Application, Transport, Network-Interface, Data-Link, and Physical Network layers). It then applies Shannon's and Nyquist's theorems to calculate system capacity and signal levels. The solution also differentiates between IPv4 and IPv6 addressing, including link-local, unique local unicast, and global unicast addresses, as well as public and private IPv4 addresses. Furthermore, it explains the iterative and recursive resolution methods of DNS, and compares persistent and non-persistent HTTP connections. Finally, it addresses the workings of trackless BitTorrent, explaining the distributed hash table technology used for file downloads. The document references several sources to support the analysis.

1
Internet Technology
Internet Technology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Contents
Internet Technology...................................................................................................................1
Question 1:.................................................................................................................................4
Application Layer...................................................................................................................4
Initiation of connection between the client and the server.................................................4
Transport Layer......................................................................................................................4
Data encapsulation starts....................................................................................................4
Network-Interface Layer........................................................................................................5
The file is prepared for transfer..........................................................................................5
Data-Link Layer.....................................................................................................................5
Framing of file....................................................................................................................5
Physical Network Layer.........................................................................................................5
Prepares the file for transmission.......................................................................................5
Receiver’s end........................................................................................................................5
Question 2:.................................................................................................................................6
Question 3:.................................................................................................................................7
Link Local addresses..............................................................................................................7
Unique Local Unicast addresses............................................................................................7
Global Unicast addresses.......................................................................................................8
Private IPv4 address...............................................................................................................8
Public IPv4 address................................................................................................................9
Question 4:.................................................................................................................................9
Iterative resolution.................................................................................................................9
Recursive resolution...............................................................................................................9
Question 5:...............................................................................................................................10
Persistent HTTP connections...............................................................................................10
Non-persistent HTTP connections.......................................................................................10
Question 6:...............................................................................................................................11
References................................................................................................................................12
Contents
Internet Technology...................................................................................................................1
Question 1:.................................................................................................................................4
Application Layer...................................................................................................................4
Initiation of connection between the client and the server.................................................4
Transport Layer......................................................................................................................4
Data encapsulation starts....................................................................................................4
Network-Interface Layer........................................................................................................5
The file is prepared for transfer..........................................................................................5
Data-Link Layer.....................................................................................................................5
Framing of file....................................................................................................................5
Physical Network Layer.........................................................................................................5
Prepares the file for transmission.......................................................................................5
Receiver’s end........................................................................................................................5
Question 2:.................................................................................................................................6
Question 3:.................................................................................................................................7
Link Local addresses..............................................................................................................7
Unique Local Unicast addresses............................................................................................7
Global Unicast addresses.......................................................................................................8
Private IPv4 address...............................................................................................................8
Public IPv4 address................................................................................................................9
Question 4:.................................................................................................................................9
Iterative resolution.................................................................................................................9
Recursive resolution...............................................................................................................9
Question 5:...............................................................................................................................10
Persistent HTTP connections...............................................................................................10
Non-persistent HTTP connections.......................................................................................10
Question 6:...............................................................................................................................11
References................................................................................................................................12

3
Figure 1:TCP/IP Encapsulation..................................................................................................4
Figure 2: Process of transfer......................................................................................................6
Figure 3: Link Local Address....................................................................................................8
Figure 4: Unicast Local address.................................................................................................8
Figure 5: Global Local address..................................................................................................8
Figure 6: Resolutions...............................................................................................................10
Figure 1:TCP/IP Encapsulation..................................................................................................4
Figure 2: Process of transfer......................................................................................................6
Figure 3: Link Local Address....................................................................................................8
Figure 4: Unicast Local address.................................................................................................8
Figure 5: Global Local address..................................................................................................8
Figure 6: Resolutions...............................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
Question 1:
To transfer a file from one PC the steps taken are,
The client uploads the file and requests for a connection
The server accepts the requests and creates a port
The data encapsulation process begins
The file is framed and delivered
The connection is terminated (Forouzan & Fegan, 2007)
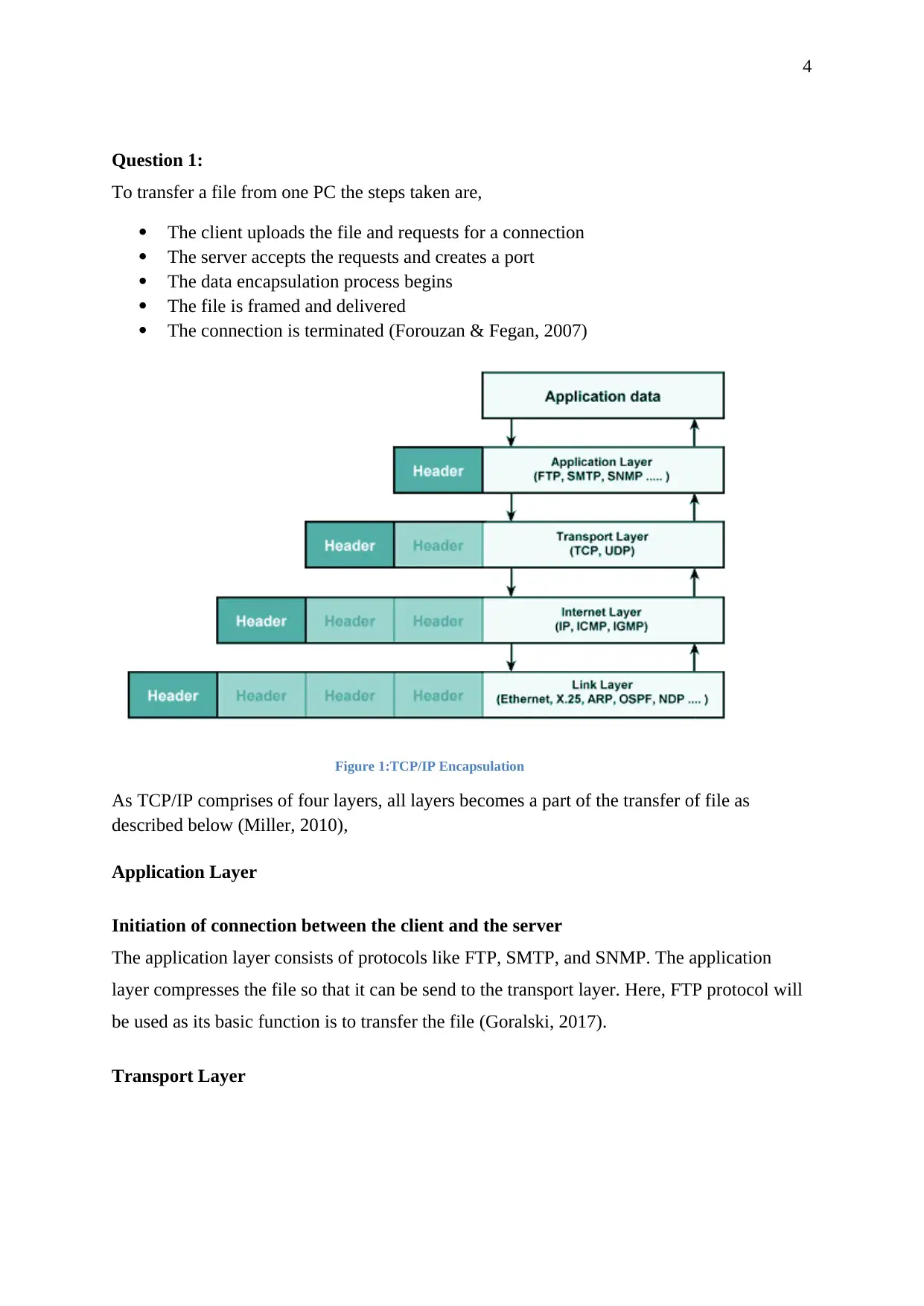
Figure 1:TCP/IP Encapsulation
As TCP/IP comprises of four layers, all layers becomes a part of the transfer of file as
described below (Miller, 2010),
Application Layer
Initiation of connection between the client and the server
The application layer consists of protocols like FTP, SMTP, and SNMP. The application
layer compresses the file so that it can be send to the transport layer. Here, FTP protocol will
be used as its basic function is to transfer the file (Goralski, 2017).
Transport Layer
Question 1:
To transfer a file from one PC the steps taken are,
The client uploads the file and requests for a connection
The server accepts the requests and creates a port
The data encapsulation process begins
The file is framed and delivered
The connection is terminated (Forouzan & Fegan, 2007)
Figure 1:TCP/IP Encapsulation
As TCP/IP comprises of four layers, all layers becomes a part of the transfer of file as
described below (Miller, 2010),
Application Layer
Initiation of connection between the client and the server
The application layer consists of protocols like FTP, SMTP, and SNMP. The application
layer compresses the file so that it can be send to the transport layer. Here, FTP protocol will
be used as its basic function is to transfer the file (Goralski, 2017).
Transport Layer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
Data encapsulation starts
The transport layer consists of protocols like UDP, TCP. At this layer, the data encapsulation
process begins. It adds a header to the file and gives the port number to the file. The
connection between the client and the server enables flow of information between them. At
times, TCP also checks the data for errors with the help of checksum data.
Network-Interface Layer
The file is prepared for transfer
This layer consists of protocols like IP, ICMP and IGMP. The header is still attached with the
file. The IP protocol arranges the file into units which are known as IP datagrams. Then the
IP address for these datagrams is determined so that the delivery process becomes easy. The
header comprises of the IP addresses, datagram sequence order and the datagram length.
Data-Link Layer
Framing of file
This layer consists of protocols like ARP, OSPF, Ethernet, etc. Here, footer is also attached
along with the header to the frame. There is a field in the header known as the cyclic
redundancy check (CRC) which is responsible for checking the errors over the network
media (Oracle, 2010).
Physical Network Layer
Prepares the file for transmission
This layer is not a part of the TCP/IP model but the data link layer sends the file to the
physical layer. Here, the IP addresses are changed into the hardware addresses. After
everything is done the file is send to other client.
Receiver’s end
At the receiver’s end, the file again travels from the TCP/IP protocol stack but in a reverse
order. Each and every protocol removes the header.
Data encapsulation starts
The transport layer consists of protocols like UDP, TCP. At this layer, the data encapsulation
process begins. It adds a header to the file and gives the port number to the file. The
connection between the client and the server enables flow of information between them. At
times, TCP also checks the data for errors with the help of checksum data.
Network-Interface Layer
The file is prepared for transfer
This layer consists of protocols like IP, ICMP and IGMP. The header is still attached with the
file. The IP protocol arranges the file into units which are known as IP datagrams. Then the
IP address for these datagrams is determined so that the delivery process becomes easy. The
header comprises of the IP addresses, datagram sequence order and the datagram length.
Data-Link Layer
Framing of file
This layer consists of protocols like ARP, OSPF, Ethernet, etc. Here, footer is also attached
along with the header to the frame. There is a field in the header known as the cyclic
redundancy check (CRC) which is responsible for checking the errors over the network
media (Oracle, 2010).
Physical Network Layer
Prepares the file for transmission
This layer is not a part of the TCP/IP model but the data link layer sends the file to the
physical layer. Here, the IP addresses are changed into the hardware addresses. After
everything is done the file is send to other client.
Receiver’s end
At the receiver’s end, the file again travels from the TCP/IP protocol stack but in a reverse
order. Each and every protocol removes the header.
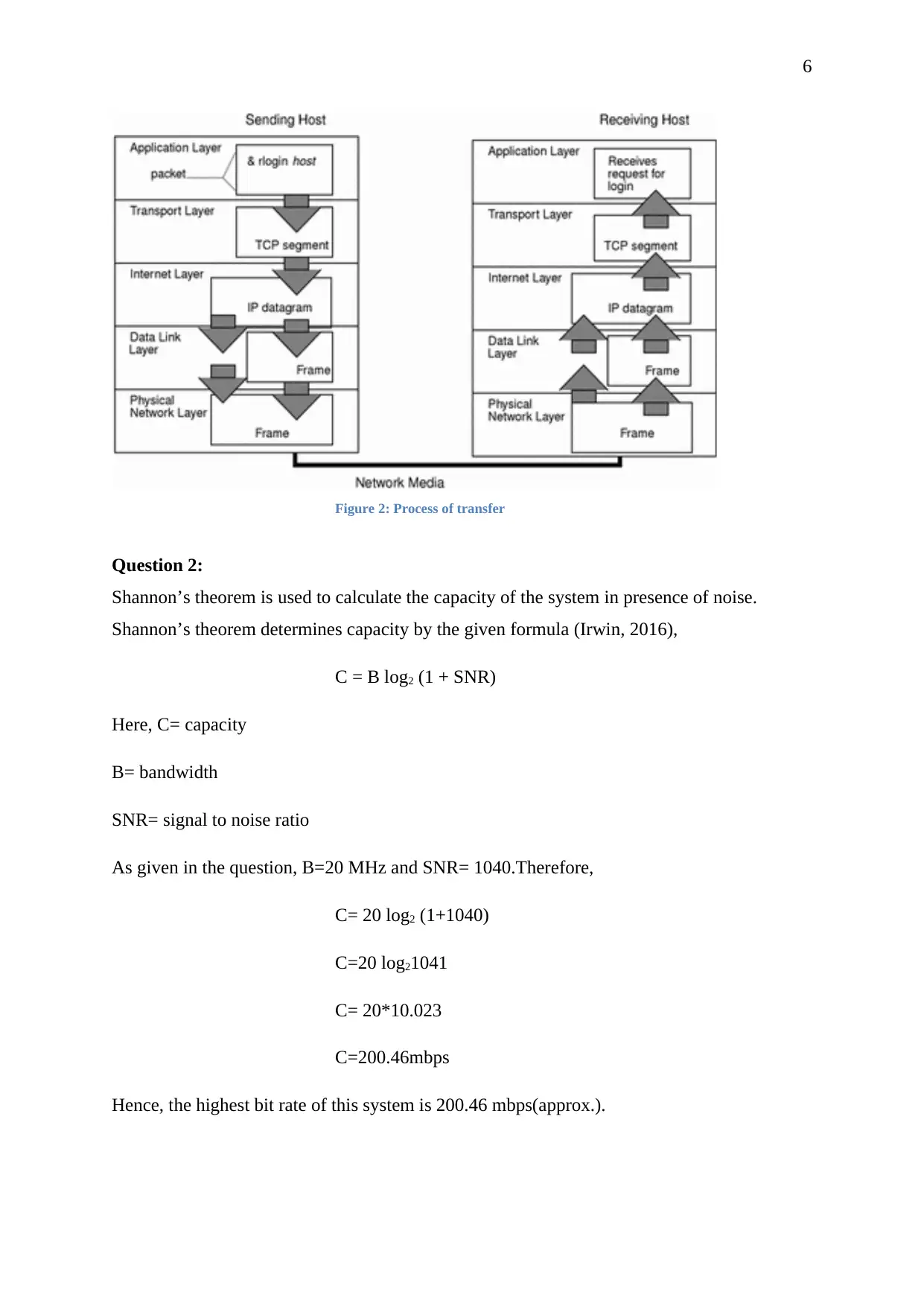
6
Figure 2: Process of transfer
Question 2:
Shannon’s theorem is used to calculate the capacity of the system in presence of noise.
Shannon’s theorem determines capacity by the given formula (Irwin, 2016),
C = B log2 (1 + SNR)
Here, C= capacity
B= bandwidth
SNR= signal to noise ratio
As given in the question, B=20 MHz and SNR= 1040.Therefore,
C= 20 log2 (1+1040)
C=20 log21041
C= 20*10.023
C=200.46mbps
Hence, the highest bit rate of this system is 200.46 mbps(approx.).
Figure 2: Process of transfer
Question 2:
Shannon’s theorem is used to calculate the capacity of the system in presence of noise.
Shannon’s theorem determines capacity by the given formula (Irwin, 2016),
C = B log2 (1 + SNR)
Here, C= capacity
B= bandwidth
SNR= signal to noise ratio
As given in the question, B=20 MHz and SNR= 1040.Therefore,
C= 20 log2 (1+1040)
C=20 log21041
C= 20*10.023
C=200.46mbps
Hence, the highest bit rate of this system is 200.46 mbps(approx.).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
Nyquist Theorem is used for a noiseless channel but it also calculates the number of signals
levels. Nyquist Theorem calculates the number of signal levels by the given formula,
C=2Blog2M
Here, C= capacity calculated
B= bandwidth
M= no of signal levels
From the above answer we see, C=200.46, B=20Mhz.By substituting the values in the
formula,
200.46=2*20log2M
Log2M=5.0115
M=32.25(approx.)
It can be concluded that 32 signal levels will be required.
Question 3:
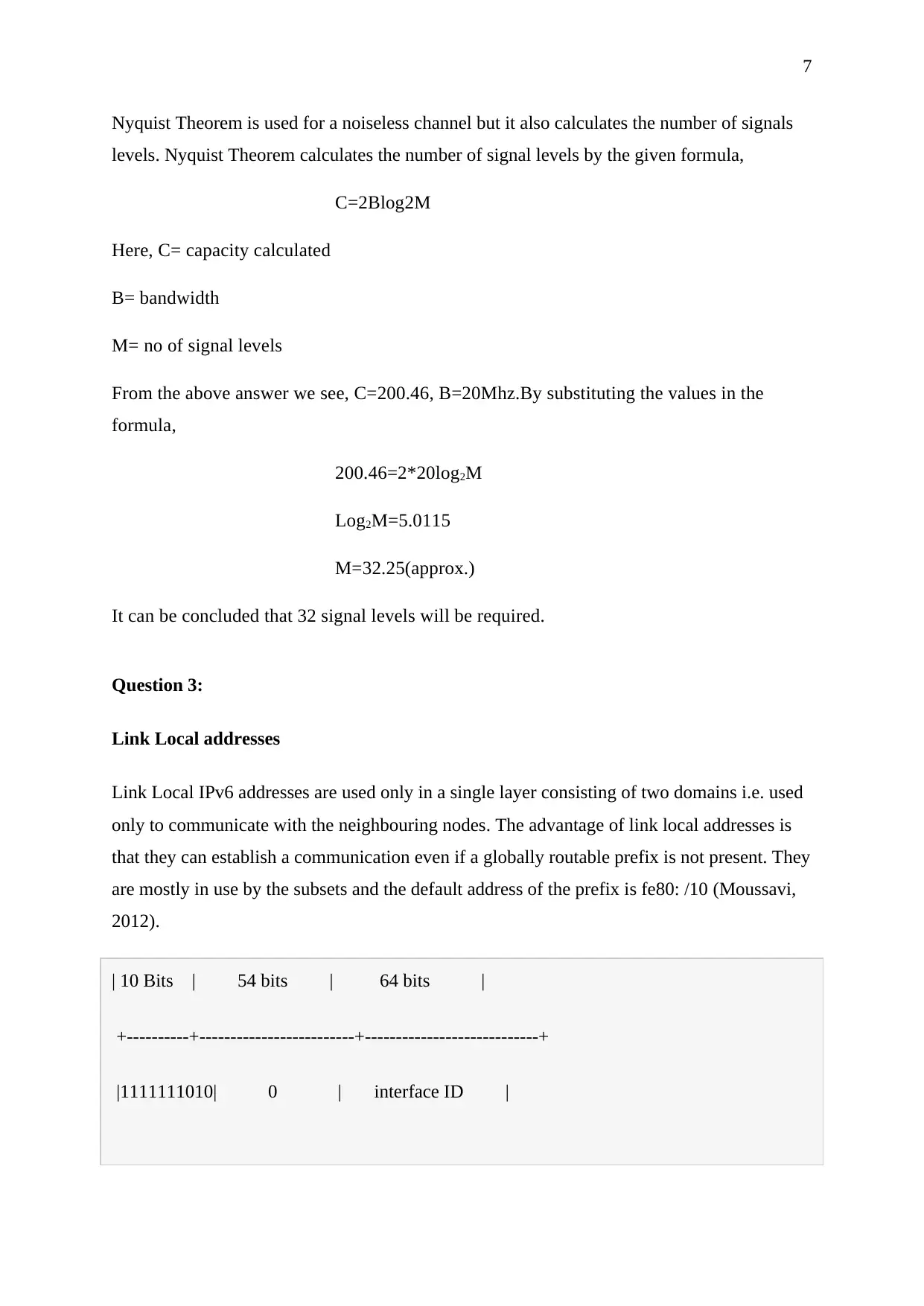
Link Local addresses
Link Local IPv6 addresses are used only in a single layer consisting of two domains i.e. used
only to communicate with the neighbouring nodes. The advantage of link local addresses is
that they can establish a communication even if a globally routable prefix is not present. They
are mostly in use by the subsets and the default address of the prefix is fe80: /10 (Moussavi,
2012).
| 10 Bits | 54 bits | 64 bits |
+----------+-------------------------+----------------------------+
|1111111010| 0 | interface ID |
Nyquist Theorem is used for a noiseless channel but it also calculates the number of signals
levels. Nyquist Theorem calculates the number of signal levels by the given formula,
C=2Blog2M
Here, C= capacity calculated
B= bandwidth
M= no of signal levels
From the above answer we see, C=200.46, B=20Mhz.By substituting the values in the
formula,
200.46=2*20log2M
Log2M=5.0115
M=32.25(approx.)
It can be concluded that 32 signal levels will be required.
Question 3:
Link Local addresses
Link Local IPv6 addresses are used only in a single layer consisting of two domains i.e. used
only to communicate with the neighbouring nodes. The advantage of link local addresses is
that they can establish a communication even if a globally routable prefix is not present. They
are mostly in use by the subsets and the default address of the prefix is fe80: /10 (Moussavi,
2012).
| 10 Bits | 54 bits | 64 bits |
+----------+-------------------------+----------------------------+
|1111111010| 0 | interface ID |
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
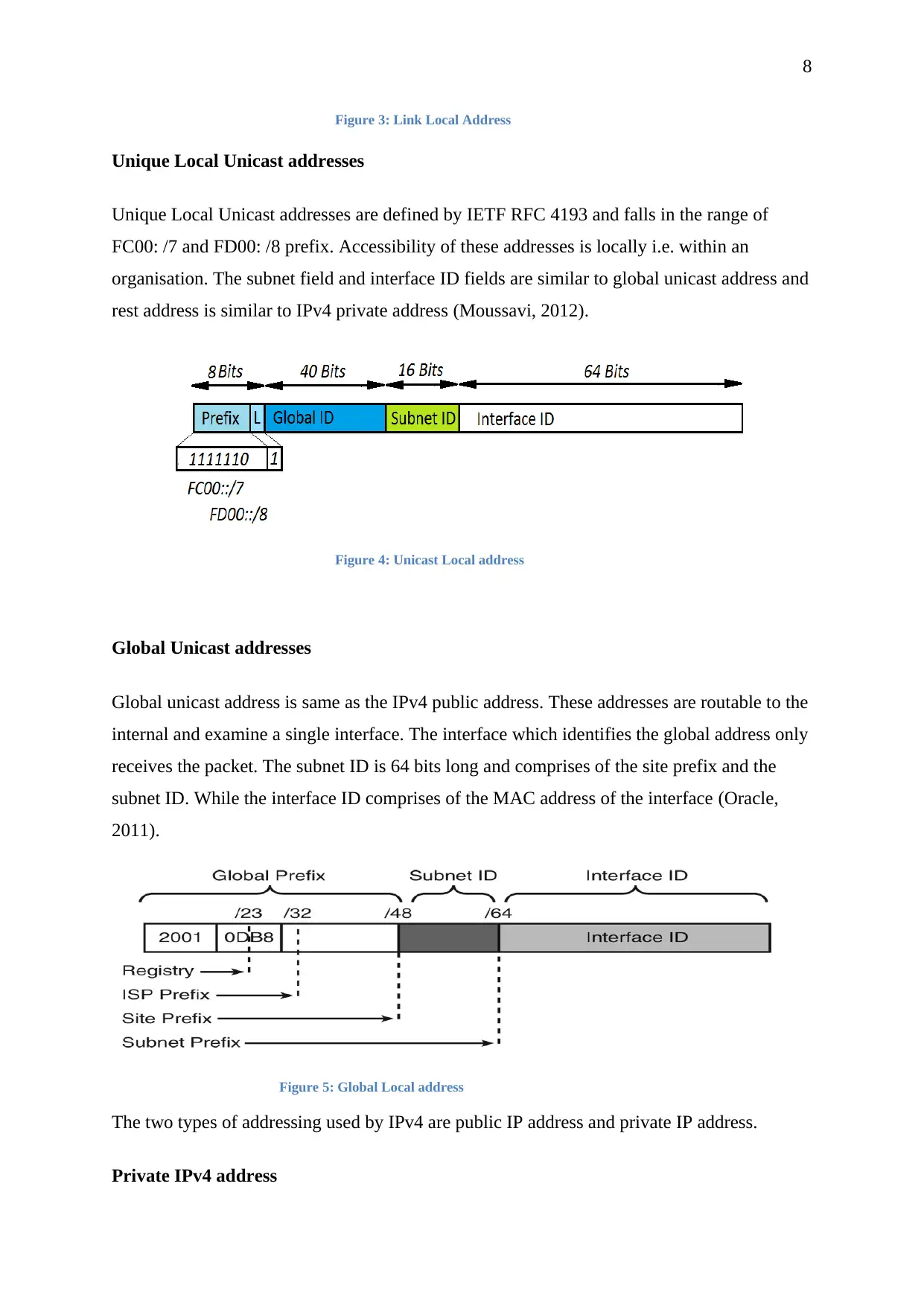
Figure 3: Link Local Address
Unique Local Unicast addresses
Unique Local Unicast addresses are defined by IETF RFC 4193 and falls in the range of
FC00: /7 and FD00: /8 prefix. Accessibility of these addresses is locally i.e. within an
organisation. The subnet field and interface ID fields are similar to global unicast address and
rest address is similar to IPv4 private address (Moussavi, 2012).
Figure 4: Unicast Local address
Global Unicast addresses
Global unicast address is same as the IPv4 public address. These addresses are routable to the
internal and examine a single interface. The interface which identifies the global address only
receives the packet. The subnet ID is 64 bits long and comprises of the site prefix and the
subnet ID. While the interface ID comprises of the MAC address of the interface (Oracle,
2011).
Figure 5: Global Local address
The two types of addressing used by IPv4 are public IP address and private IP address.
Private IPv4 address
Figure 3: Link Local Address
Unique Local Unicast addresses
Unique Local Unicast addresses are defined by IETF RFC 4193 and falls in the range of
FC00: /7 and FD00: /8 prefix. Accessibility of these addresses is locally i.e. within an
organisation. The subnet field and interface ID fields are similar to global unicast address and
rest address is similar to IPv4 private address (Moussavi, 2012).
Figure 4: Unicast Local address
Global Unicast addresses
Global unicast address is same as the IPv4 public address. These addresses are routable to the
internal and examine a single interface. The interface which identifies the global address only
receives the packet. The subnet ID is 64 bits long and comprises of the site prefix and the
subnet ID. While the interface ID comprises of the MAC address of the interface (Oracle,
2011).
Figure 5: Global Local address
The two types of addressing used by IPv4 are public IP address and private IP address.
Private IPv4 address

9
The private IPv4 address is assigned by the router using DHCP to the organisations. These
addresses are reserved for NAT for class A, class B and class C range. With the use of private
address there is no need of connecting to the internet and continue the communication. They
are mostly used inside a home or small business network to develop their own network by
InterNIC (Fisher, 2017).
Public IPv4 address
The public IPv4 address is assigned by InterNIC to connect globally with the internet. These
addresses consists of class-based network IDs and the destined on the internet. To make the
traffic reach the destination, routes are designed in the routers of the Internet (Microsoft,
2018).
Question 4:
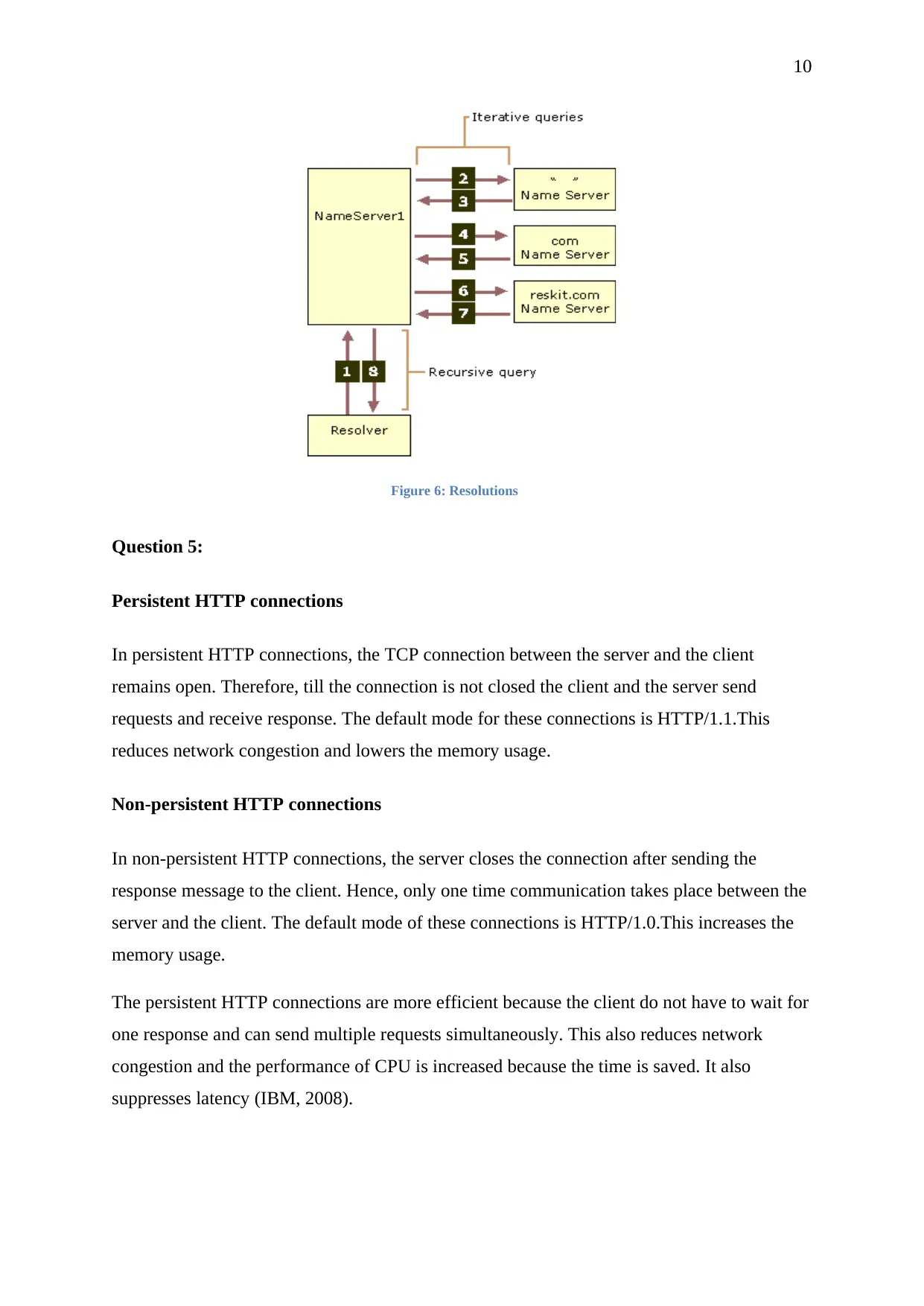
The basic function of Domain Name System is to conclude a fully qualified domain name
(FQDN) into an IP address. There are two by which DNS resolves a domain name described
as follows,
Iterative resolution
In iterative resolution, a query is not answered in one go i.e. the server returns the client, IP
address of the server. The DNS server tries to find the query only in its local cache. When the
client receives the information and gets to know that the answer is not completely answered
he again makes a query but now with another server. This process continues till exact answer
is not received or time-out condition comes (Daemon, 2013).
Recursive resolution
In recursive resolution, the client receives the answer to the query at once i.e. when the DNS
serves receives the query it searches it in its own database and in its local cache. After that,
the server goes through the DNS tree and finds the answer. The DNS server also queries with
the other DNS servers. This is a short process and the client gets the answer easily
(Microsoft, 2018).
The private IPv4 address is assigned by the router using DHCP to the organisations. These
addresses are reserved for NAT for class A, class B and class C range. With the use of private
address there is no need of connecting to the internet and continue the communication. They
are mostly used inside a home or small business network to develop their own network by
InterNIC (Fisher, 2017).
Public IPv4 address
The public IPv4 address is assigned by InterNIC to connect globally with the internet. These
addresses consists of class-based network IDs and the destined on the internet. To make the
traffic reach the destination, routes are designed in the routers of the Internet (Microsoft,
2018).
Question 4:
The basic function of Domain Name System is to conclude a fully qualified domain name
(FQDN) into an IP address. There are two by which DNS resolves a domain name described
as follows,
Iterative resolution
In iterative resolution, a query is not answered in one go i.e. the server returns the client, IP
address of the server. The DNS server tries to find the query only in its local cache. When the
client receives the information and gets to know that the answer is not completely answered
he again makes a query but now with another server. This process continues till exact answer
is not received or time-out condition comes (Daemon, 2013).
Recursive resolution
In recursive resolution, the client receives the answer to the query at once i.e. when the DNS
serves receives the query it searches it in its own database and in its local cache. After that,
the server goes through the DNS tree and finds the answer. The DNS server also queries with
the other DNS servers. This is a short process and the client gets the answer easily
(Microsoft, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
Figure 6: Resolutions
Question 5:
Persistent HTTP connections
In persistent HTTP connections, the TCP connection between the server and the client
remains open. Therefore, till the connection is not closed the client and the server send
requests and receive response. The default mode for these connections is HTTP/1.1.This
reduces network congestion and lowers the memory usage.
Non-persistent HTTP connections
In non-persistent HTTP connections, the server closes the connection after sending the
response message to the client. Hence, only one time communication takes place between the
server and the client. The default mode of these connections is HTTP/1.0.This increases the
memory usage.
The persistent HTTP connections are more efficient because the client do not have to wait for
one response and can send multiple requests simultaneously. This also reduces network
congestion and the performance of CPU is increased because the time is saved. It also
suppresses latency (IBM, 2008).
Figure 6: Resolutions
Question 5:
Persistent HTTP connections
In persistent HTTP connections, the TCP connection between the server and the client
remains open. Therefore, till the connection is not closed the client and the server send
requests and receive response. The default mode for these connections is HTTP/1.1.This
reduces network congestion and lowers the memory usage.
Non-persistent HTTP connections
In non-persistent HTTP connections, the server closes the connection after sending the
response message to the client. Hence, only one time communication takes place between the
server and the client. The default mode of these connections is HTTP/1.0.This increases the
memory usage.
The persistent HTTP connections are more efficient because the client do not have to wait for
one response and can send multiple requests simultaneously. This also reduces network
congestion and the performance of CPU is increased because the time is saved. It also
suppresses latency (IBM, 2008).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
Question 6:
Trackless Bit Torrent is a part of bit torrent which shows the list of people who are
downloading the same torrent. It is described inside the network of peer downloaders and do
not hold a central tracker. With the help of this, if the user knows one node on the network
eventually he will know all the nodes (Loewenstern, 2017).
The technology used in trackless Bit Torrent is Distributed Hash Table which downloads a
file. The steps to download a file are,
1. To get the tracker URL inside a file the client looks for that .torrent file.
2. The client then communicates with this tracker and gets the list of peers.
3. After receiving the list of peers, the respective file is downloaded.
4. When the .torrent file is downloaded, the client finds the key from this file.
5. The Distributed Hash Table is now looked up with the help of this key to get the node.
6. From this table a peer list is again received and the client downloads the file.
Question 6:
Trackless Bit Torrent is a part of bit torrent which shows the list of people who are
downloading the same torrent. It is described inside the network of peer downloaders and do
not hold a central tracker. With the help of this, if the user knows one node on the network
eventually he will know all the nodes (Loewenstern, 2017).
The technology used in trackless Bit Torrent is Distributed Hash Table which downloads a
file. The steps to download a file are,
1. To get the tracker URL inside a file the client looks for that .torrent file.
2. The client then communicates with this tracker and gets the list of peers.
3. After receiving the list of peers, the respective file is downloaded.
4. When the .torrent file is downloaded, the client finds the key from this file.
5. The Distributed Hash Table is now looked up with the help of this key to get the node.
6. From this table a peer list is again received and the client downloads the file.

12
References
Daemon, I. (2013). Iterative Resolution. Retrieved from
http://www.inetdaemon.com/tutorials/internet/dns/servers/iterative.shtml
Fisher, T. (2017). Everything You Need to Know About Private IP Addresses. Retrieved from
https://www.lifewire.com/what-is-a-private-ip-address-2625970
Forouzan, B., & Fegan, S. (2007). Data communications and networking. New York:
McGraw-Hill Higher Education.
Goralski, W. (2017). The illustrated network. USA: Elseiver Inc.
IBM (2008). Types and Categories of IPv6 Addresses. Retrieved from
https://www.ibm.com/support/knowledgecenter/SSB27U_5.4.0/com.ibm.zvm.v54.kijl0/
hcsk7b3014.htm
Irwin, J., & Wu, C. (2016). Introduction to Computer Networks and Cybersecurity. Florida:
CRC Press.
Loewenstern, A.(2017).BitTorrent.org. Retrieved from
http://www.bittorrent.org/beps/bep_0005.html
Microsoft (2018).Recursive and Iterative Queries. Retrieved from
https://technet.microsoft.com/en-us/library/cc961401.aspx
Microsoft (2018).Public and Private Addresses. Retrieved from
https://technet.microsoft.com/en-us/library/cc958825.aspx
Miller, P. (2010). TCP/IP. Boca Raton, Fla.: Brown Walker Press.
Moussavi, M. (2012). Data communication and networking. Clifton Park, N.Y.: Delmar.
Oracle. (2011). System Administration Guide: IP Services. Retrieved from
https://docs.oracle.com/cd/E18752_01/html/816-4554/docinfo.html
Oracle. (2010). Chapter 4 Overview of TCP/IP (System Administration Guide, Volume 3).
Retrieved from https://docs.oracle.com/cd/E19455-01/806-0916/6ja85398k/index.html
References
Daemon, I. (2013). Iterative Resolution. Retrieved from
http://www.inetdaemon.com/tutorials/internet/dns/servers/iterative.shtml
Fisher, T. (2017). Everything You Need to Know About Private IP Addresses. Retrieved from
https://www.lifewire.com/what-is-a-private-ip-address-2625970
Forouzan, B., & Fegan, S. (2007). Data communications and networking. New York:
McGraw-Hill Higher Education.
Goralski, W. (2017). The illustrated network. USA: Elseiver Inc.
IBM (2008). Types and Categories of IPv6 Addresses. Retrieved from
https://www.ibm.com/support/knowledgecenter/SSB27U_5.4.0/com.ibm.zvm.v54.kijl0/
hcsk7b3014.htm
Irwin, J., & Wu, C. (2016). Introduction to Computer Networks and Cybersecurity. Florida:
CRC Press.
Loewenstern, A.(2017).BitTorrent.org. Retrieved from
http://www.bittorrent.org/beps/bep_0005.html
Microsoft (2018).Recursive and Iterative Queries. Retrieved from
https://technet.microsoft.com/en-us/library/cc961401.aspx
Microsoft (2018).Public and Private Addresses. Retrieved from
https://technet.microsoft.com/en-us/library/cc958825.aspx
Miller, P. (2010). TCP/IP. Boca Raton, Fla.: Brown Walker Press.
Moussavi, M. (2012). Data communication and networking. Clifton Park, N.Y.: Delmar.
Oracle. (2011). System Administration Guide: IP Services. Retrieved from
https://docs.oracle.com/cd/E18752_01/html/816-4554/docinfo.html
Oracle. (2010). Chapter 4 Overview of TCP/IP (System Administration Guide, Volume 3).
Retrieved from https://docs.oracle.com/cd/E19455-01/806-0916/6ja85398k/index.html
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





