Internet of Things Assignment: Network Media, Sensors, and Laws
VerifiedAdded on 2020/02/24
|8
|1197
|207
Homework Assignment
AI Summary
This assignment delves into the multifaceted world of the Internet of Things (IoT), exploring key aspects of computer networking and related technologies. The document begins by comparing network media like twisted pair, coaxial, and fiber optic cables, analyzing their bandwidth, coverage, interference, cost, and security features. It then examines different types of sensors, outlining their advantages, disadvantages, and applications, along with an in-depth look at the use of RFID technology for inventory management, including its advantages, disadvantages, and various applications. The assignment also addresses critical IoT security and privacy issues, such as vulnerabilities to hacking, trust considerations, and data protection, while also exploring the implications of data collection, manipulation, and theft. Furthermore, the document provides calculations for round-trip and publish communication models, comparing their performance. Finally, the assignment discusses Nielsen's Law and its relationship with Moore's Law, and their implications in the context of technological advancements.

Running Head: INTERNET OF THINGS
Computer Networking:
[Student Names]
[Institution Name]
Computer Networking:
[Student Names]
[Institution Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTERNET OF THINGS 2
Question two
The network is interconnection of various components in an organization to allow
communication, however there are various media devices that are used that facilitates
transmission of signals from one device to another .Among the media used includes twisted pair
cables, coaxial cables and the fiber –optic cables which has different properties which are
considered while the users need to setup the network (Adam,2015).
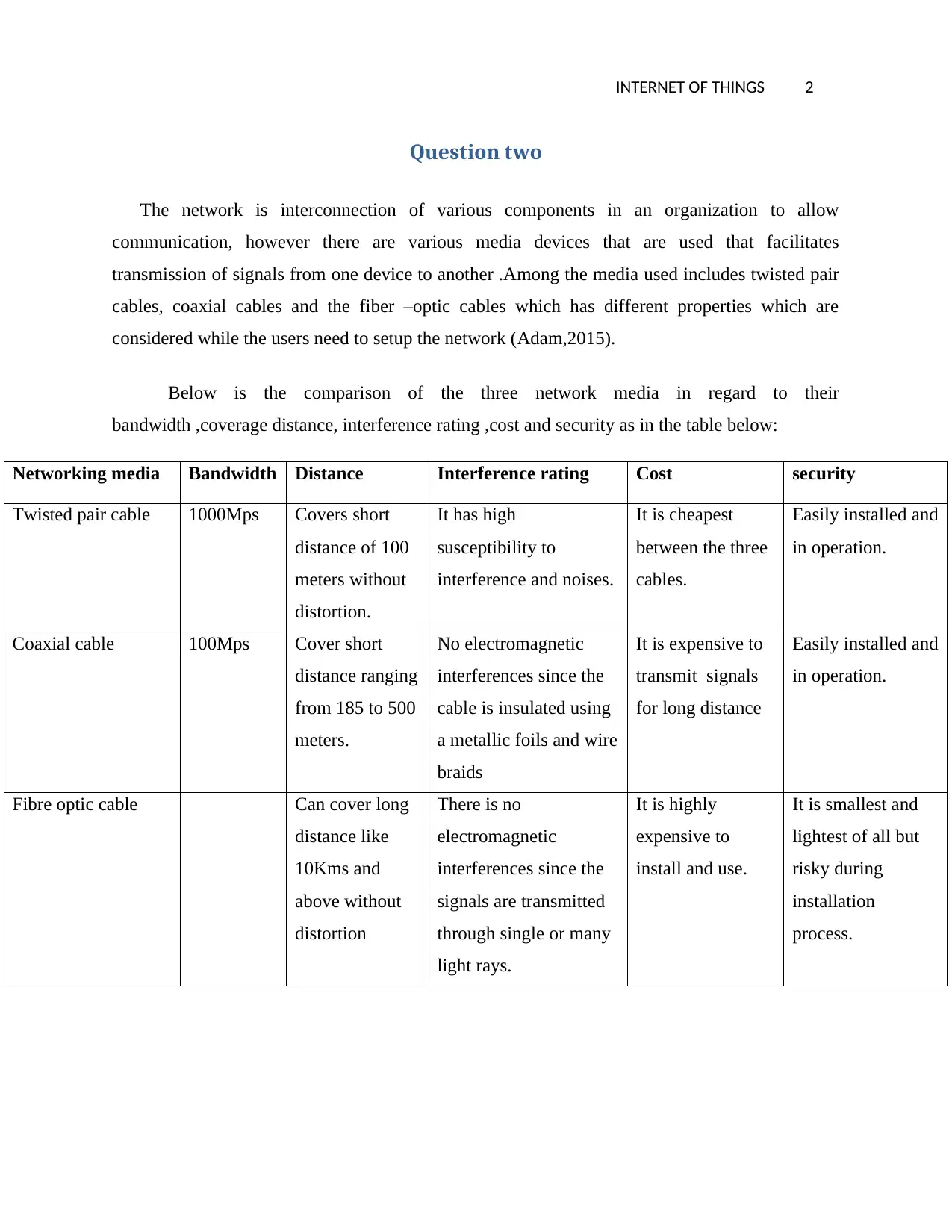
Below is the comparison of the three network media in regard to their
bandwidth ,coverage distance, interference rating ,cost and security as in the table below:
Networking media Bandwidth Distance Interference rating Cost security
Twisted pair cable 1000Mps Covers short
distance of 100
meters without
distortion.
It has high
susceptibility to
interference and noises.
It is cheapest
between the three
cables.
Easily installed and
in operation.
Coaxial cable 100Mps Cover short
distance ranging
from 185 to 500
meters.
No electromagnetic
interferences since the
cable is insulated using
a metallic foils and wire
braids
It is expensive to
transmit signals
for long distance
Easily installed and
in operation.
Fibre optic cable Can cover long
distance like
10Kms and
above without
distortion
There is no
electromagnetic
interferences since the
signals are transmitted
through single or many
light rays.
It is highly
expensive to
install and use.
It is smallest and
lightest of all but
risky during
installation
process.
Question two
The network is interconnection of various components in an organization to allow
communication, however there are various media devices that are used that facilitates
transmission of signals from one device to another .Among the media used includes twisted pair
cables, coaxial cables and the fiber –optic cables which has different properties which are
considered while the users need to setup the network (Adam,2015).
Below is the comparison of the three network media in regard to their
bandwidth ,coverage distance, interference rating ,cost and security as in the table below:
Networking media Bandwidth Distance Interference rating Cost security
Twisted pair cable 1000Mps Covers short
distance of 100
meters without
distortion.
It has high
susceptibility to
interference and noises.
It is cheapest
between the three
cables.
Easily installed and
in operation.
Coaxial cable 100Mps Cover short
distance ranging
from 185 to 500
meters.
No electromagnetic
interferences since the
cable is insulated using
a metallic foils and wire
braids
It is expensive to
transmit signals
for long distance
Easily installed and
in operation.
Fibre optic cable Can cover long
distance like
10Kms and
above without
distortion
There is no
electromagnetic
interferences since the
signals are transmitted
through single or many
light rays.
It is highly
expensive to
install and use.
It is smallest and
lightest of all but
risky during
installation
process.
INTERNET OF THINGS 3
Question three
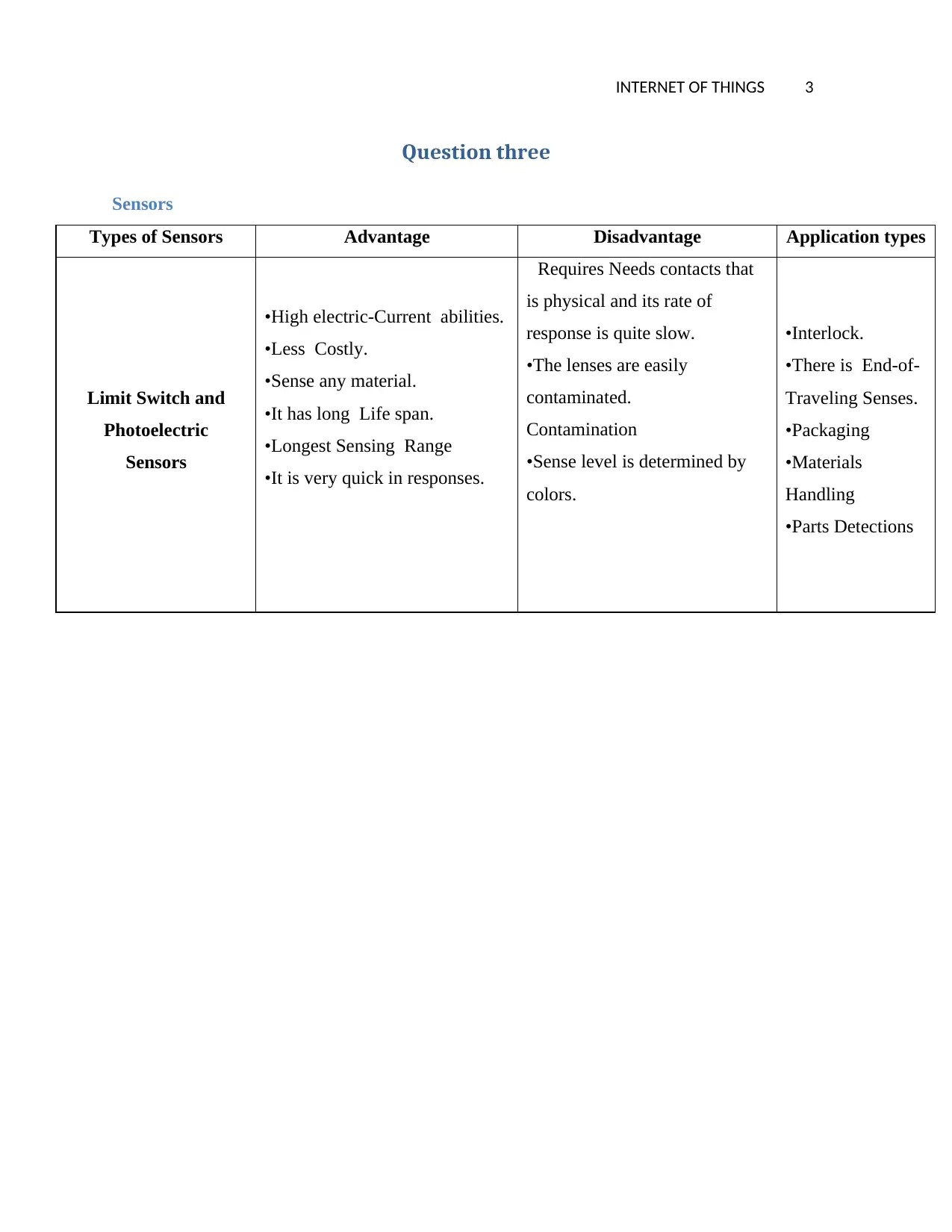
Sensors
Types of Sensors Advantage Disadvantage Application types
Limit Switch and
Photoelectric
Sensors
•High electric-Current abilities.
•Less Costly.
•Sense any material.
•It has long Life span.
•Longest Sensing Range
•It is very quick in responses.
Requires Needs contacts that
is physical and its rate of
response is quite slow.
•The lenses are easily
contaminated.
Contamination
•Sense level is determined by
colors.
•Interlock.
•There is End-of-
Traveling Senses.
•Packaging
•Materials
Handling
•Parts Detections
Question three
Sensors
Types of Sensors Advantage Disadvantage Application types
Limit Switch and
Photoelectric
Sensors
•High electric-Current abilities.
•Less Costly.
•Sense any material.
•It has long Life span.
•Longest Sensing Range
•It is very quick in responses.
Requires Needs contacts that
is physical and its rate of
response is quite slow.
•The lenses are easily
contaminated.
Contamination
•Sense level is determined by
colors.
•Interlock.
•There is End-of-
Traveling Senses.
•Packaging
•Materials
Handling
•Parts Detections
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTERNET OF THINGS 4
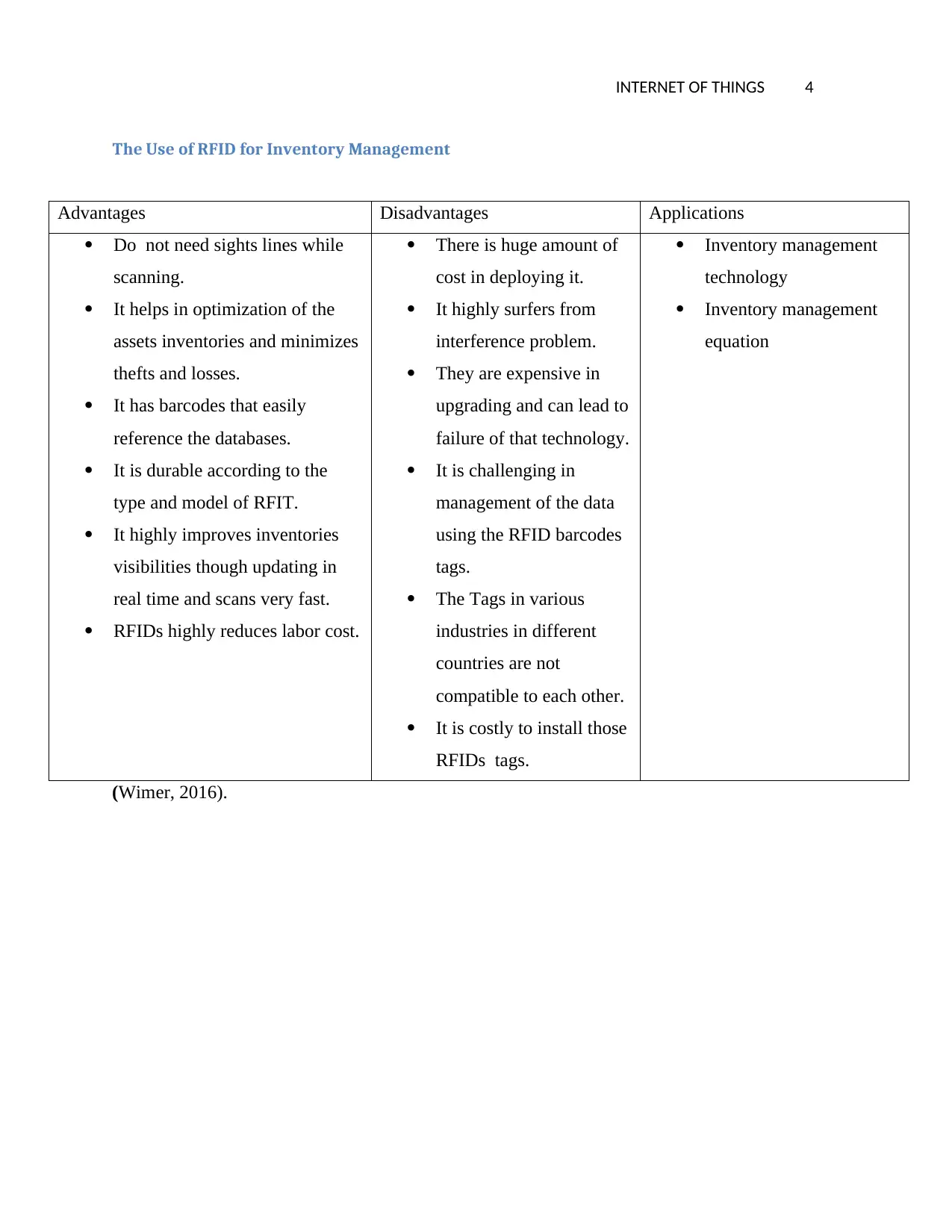
The Use of RFID for Inventory Management
Advantages Disadvantages Applications
Do not need sights lines while
scanning.
It helps in optimization of the
assets inventories and minimizes
thefts and losses.
It has barcodes that easily
reference the databases.
It is durable according to the
type and model of RFIT.
It highly improves inventories
visibilities though updating in
real time and scans very fast.
RFIDs highly reduces labor cost.
There is huge amount of
cost in deploying it.
It highly surfers from
interference problem.
They are expensive in
upgrading and can lead to
failure of that technology.
It is challenging in
management of the data
using the RFID barcodes
tags.
The Tags in various
industries in different
countries are not
compatible to each other.
It is costly to install those
RFIDs tags.
Inventory management
technology
Inventory management
equation
(Wimer, 2016).
The Use of RFID for Inventory Management
Advantages Disadvantages Applications
Do not need sights lines while
scanning.
It helps in optimization of the
assets inventories and minimizes
thefts and losses.
It has barcodes that easily
reference the databases.
It is durable according to the
type and model of RFIT.
It highly improves inventories
visibilities though updating in
real time and scans very fast.
RFIDs highly reduces labor cost.
There is huge amount of
cost in deploying it.
It highly surfers from
interference problem.
They are expensive in
upgrading and can lead to
failure of that technology.
It is challenging in
management of the data
using the RFID barcodes
tags.
The Tags in various
industries in different
countries are not
compatible to each other.
It is costly to install those
RFIDs tags.
Inventory management
technology
Inventory management
equation
(Wimer, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTERNET OF THINGS 5
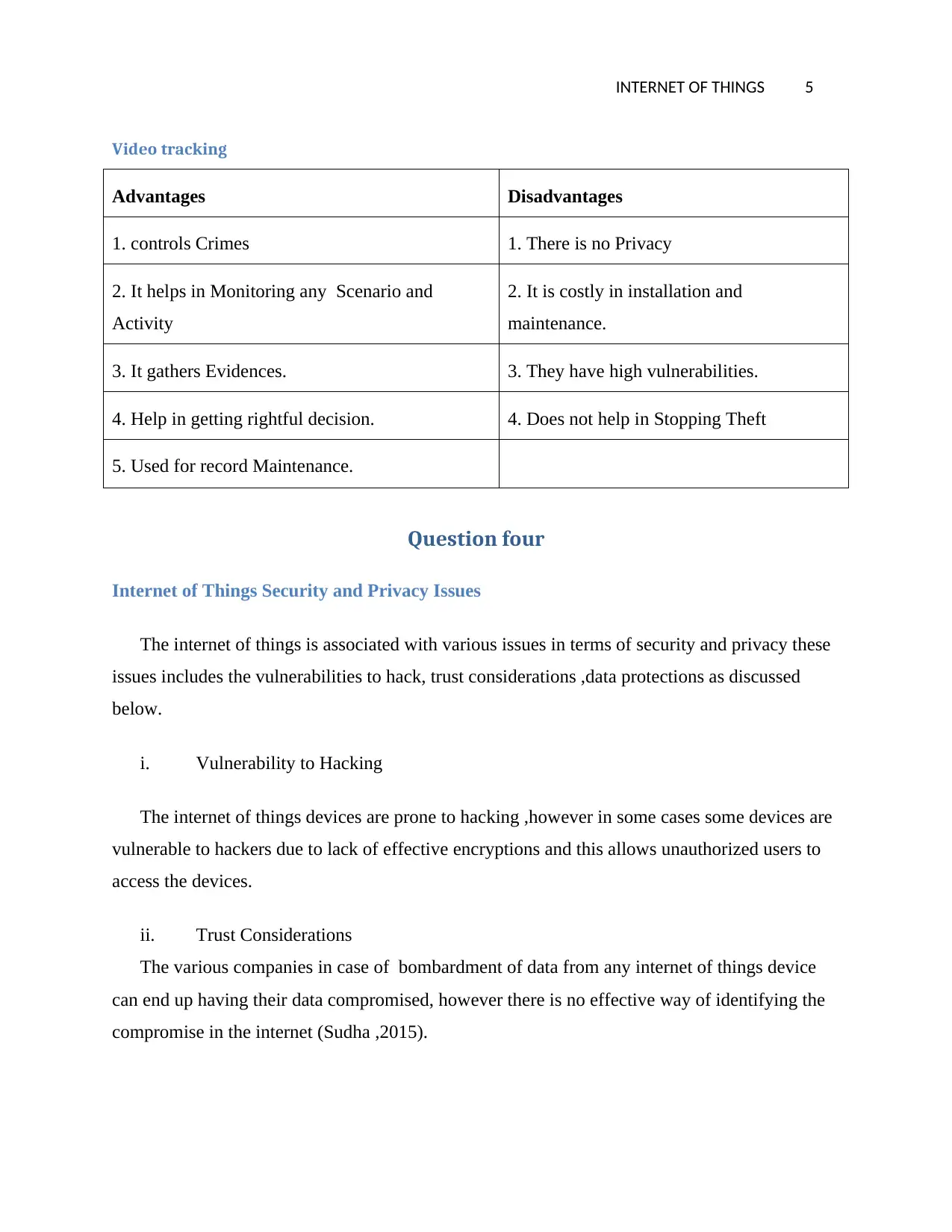
Video tracking
Advantages Disadvantages
1. controls Crimes 1. There is no Privacy
2. It helps in Monitoring any Scenario and
Activity
2. It is costly in installation and
maintenance.
3. It gathers Evidences. 3. They have high vulnerabilities.
4. Help in getting rightful decision. 4. Does not help in Stopping Theft
5. Used for record Maintenance.
Question four
Internet of Things Security and Privacy Issues
The internet of things is associated with various issues in terms of security and privacy these
issues includes the vulnerabilities to hack, trust considerations ,data protections as discussed
below.
i. Vulnerability to Hacking
The internet of things devices are prone to hacking ,however in some cases some devices are
vulnerable to hackers due to lack of effective encryptions and this allows unauthorized users to
access the devices.
ii. Trust Considerations
The various companies in case of bombardment of data from any internet of things device
can end up having their data compromised, however there is no effective way of identifying the
compromise in the internet (Sudha ,2015).
Video tracking
Advantages Disadvantages
1. controls Crimes 1. There is no Privacy
2. It helps in Monitoring any Scenario and
Activity
2. It is costly in installation and
maintenance.
3. It gathers Evidences. 3. They have high vulnerabilities.
4. Help in getting rightful decision. 4. Does not help in Stopping Theft
5. Used for record Maintenance.
Question four
Internet of Things Security and Privacy Issues
The internet of things is associated with various issues in terms of security and privacy these
issues includes the vulnerabilities to hack, trust considerations ,data protections as discussed
below.
i. Vulnerability to Hacking
The internet of things devices are prone to hacking ,however in some cases some devices are
vulnerable to hackers due to lack of effective encryptions and this allows unauthorized users to
access the devices.
ii. Trust Considerations
The various companies in case of bombardment of data from any internet of things device
can end up having their data compromised, however there is no effective way of identifying the
compromise in the internet (Sudha ,2015).

INTERNET OF THINGS 6
iii. Big Data Collection, Protection and Privacy
The collection of data gathers important information but there lacks enough security to
secure the data not to interfere with through hacking maliciously (Daniel , 2014).
However the internet of things device can produce huge amount of data and therefore
pausing more risks like:
Stilling of data and identities.
Devices manipulations.
Falsifying the data.
Stealing of the IP addresses and network manipulations.
Question five
For round-trip.
Application request time = 1s.
Sensors Delays time = 12s .
Sensors process time = 3ms
Application response time= 2ms
Total time=1s+12s+3ms+2ms=13.5s
For publish communication model.
Application request time = 1s.
Sensors Delays time = 0s .
Sensors process time = 3ms
Application response time= 2ms
Total time=1s+0s+3ms+2ms=1.5s
iii. Big Data Collection, Protection and Privacy
The collection of data gathers important information but there lacks enough security to
secure the data not to interfere with through hacking maliciously (Daniel , 2014).
However the internet of things device can produce huge amount of data and therefore
pausing more risks like:
Stilling of data and identities.
Devices manipulations.
Falsifying the data.
Stealing of the IP addresses and network manipulations.
Question five
For round-trip.
Application request time = 1s.
Sensors Delays time = 12s .
Sensors process time = 3ms
Application response time= 2ms
Total time=1s+12s+3ms+2ms=13.5s
For publish communication model.
Application request time = 1s.
Sensors Delays time = 0s .
Sensors process time = 3ms
Application response time= 2ms
Total time=1s+0s+3ms+2ms=1.5s
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNET OF THINGS 7
Time saved = 13.5s-1.5s=12s
Question six
Nielson’s law
This is a law that was introduced by Jacob Nielsen back in 1998 ,which states that
bandwidths that are available to high ends broadband connection grows at a rate of 50% yearly ,
that consequently leads to 57 times compound growth in capacities in every decade, however the
model’s strength is determined after fifteen years (Valencia,2015).
Relationship between Nielson’s law and Moore’s law.
Unlike the Nielson’s law the Moore’s law its state that in every silicon chips will have
doubled number of transistors after every two years ,however this leads to increase in the level of
computer’s performances which has been applicable for more than fifty years which leads to
improvement in terms of technological aspect despite the speed, sizes and costs.
The Nielson’s law implications
As the computers gets old quickly the new computers becomes cheaper, however the
growth in terms Nielsen’s law is slow compared to the Moore’s Law which makes the users
experiences becomes the bandwidth-bound (Erik , 2014).
.
Time saved = 13.5s-1.5s=12s
Question six
Nielson’s law
This is a law that was introduced by Jacob Nielsen back in 1998 ,which states that
bandwidths that are available to high ends broadband connection grows at a rate of 50% yearly ,
that consequently leads to 57 times compound growth in capacities in every decade, however the
model’s strength is determined after fifteen years (Valencia,2015).
Relationship between Nielson’s law and Moore’s law.
Unlike the Nielson’s law the Moore’s law its state that in every silicon chips will have
doubled number of transistors after every two years ,however this leads to increase in the level of
computer’s performances which has been applicable for more than fifty years which leads to
improvement in terms of technological aspect despite the speed, sizes and costs.
The Nielson’s law implications
As the computers gets old quickly the new computers becomes cheaper, however the
growth in terms Nielsen’s law is slow compared to the Moore’s Law which makes the users
experiences becomes the bandwidth-bound (Erik , 2014).
.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS 8
REFERENCES
Erik ,B. (2014). The Second Machine Age: Work, Progress and Prosperity in a Time of Brilliant
Technologies . United States of America: W. W. Norton & Company.
Valencia, R. (2015). Getting Started with the Internet of Things : Connecting Sensors and
Microcontrollers to the Cloud. United States: O'Reilly Media, Inc, USA.
Daniel ,K. (2014). The Silent Intelligence: The Internet of Things Paperback. Washington, DC:
Lightning Source Inc.
Sudha ,J. (2015). IoT Disruptions: The Internet of Things - Innovations & Jobs Kindle Edition.
USA:Amazon Digital Services LLC.
Wimer, H. (2016). Meta Products: Building the Internet of Things Paperback. Japan: BIS
Publishers.
Adam, G. (2015). Everyware: The Dawning Age of Ubiquitous Computing Paperback. Asia:
New Riders.
REFERENCES
Erik ,B. (2014). The Second Machine Age: Work, Progress and Prosperity in a Time of Brilliant
Technologies . United States of America: W. W. Norton & Company.
Valencia, R. (2015). Getting Started with the Internet of Things : Connecting Sensors and
Microcontrollers to the Cloud. United States: O'Reilly Media, Inc, USA.
Daniel ,K. (2014). The Silent Intelligence: The Internet of Things Paperback. Washington, DC:
Lightning Source Inc.
Sudha ,J. (2015). IoT Disruptions: The Internet of Things - Innovations & Jobs Kindle Edition.
USA:Amazon Digital Services LLC.
Wimer, H. (2016). Meta Products: Building the Internet of Things Paperback. Japan: BIS
Publishers.
Adam, G. (2015). Everyware: The Dawning Age of Ubiquitous Computing Paperback. Asia:
New Riders.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




