Nielsen's Law and IoT Applications
VerifiedAdded on 2020/02/24
|12
|2028
|295
AI Summary
This assignment examines Nielsen's Law, which states that user bandwidth increases by an average of 50% annually. It compares this law to Moore's Law and analyzes the implications of Nielsen's Law for the Internet of Things (IoT). The text discusses how sensor technology will contribute to a surge in data streams as sensors become embedded in various aspects of our lives, including homes, cars, and clothing. Additionally, it highlights the potential trend of microchips being integrated directly into body or skin sensors.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INTERNET OF THINGS
INTERNET OF THINGS
Name of the Student
Name of the University
Author Note
INTERNET OF THINGS
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2INTERNET OF THINGS
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................3
Question 3:.......................................................................................................................................4
Question 4........................................................................................................................................6
Question 5........................................................................................................................................6
Question 6........................................................................................................................................8
Reference.........................................................................................................................................9
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................3
Question 3:.......................................................................................................................................4
Question 4........................................................................................................................................6
Question 5........................................................................................................................................6
Question 6........................................................................................................................................8
Reference.........................................................................................................................................9

3INTERNET OF THINGS
Question 1
The real problem that is mainly faced with an interface is basically it is an interface. In
doing any daily task with the interface gets into the way it would be all together a very bad
option. The main focus should be on the task and not on the interface which is related to the task.
The main aspect that should be followed practically is that the mere job is not basically done on
the job or it can be stated that the effort in doing a job is not on the interface it should be putting
effort on a job. When a job is directly related to a interface the main design aspect is related to
the inherent inhuman, unnatural which directly gives a diminishing return. The better aspect in
such a scenario is not putting any emphasis on the interface and full emphasis should be towards
the job which is to be performed.
Example 1:
Bluetooth audio system is in the verge of the latest innovation. The user interface has
been implemented in such a way that compatibility should be achieved in order to access the
output and the input aspect involved in it.(Wollschlaeger, Sauter & Jasperneite, 2017).
Example 2:
Putting emphasis on the Bluetooth aspect the elimination of the user interface would be
directly beneficial from the users point of view. The user interface would always be troublesome
with the prospective of the user and different secyrity issue can arise from its directly
implementation. The elimination of the user interface would also save time
Question 1
The real problem that is mainly faced with an interface is basically it is an interface. In
doing any daily task with the interface gets into the way it would be all together a very bad
option. The main focus should be on the task and not on the interface which is related to the task.
The main aspect that should be followed practically is that the mere job is not basically done on
the job or it can be stated that the effort in doing a job is not on the interface it should be putting
effort on a job. When a job is directly related to a interface the main design aspect is related to
the inherent inhuman, unnatural which directly gives a diminishing return. The better aspect in
such a scenario is not putting any emphasis on the interface and full emphasis should be towards
the job which is to be performed.
Example 1:
Bluetooth audio system is in the verge of the latest innovation. The user interface has
been implemented in such a way that compatibility should be achieved in order to access the
output and the input aspect involved in it.(Wollschlaeger, Sauter & Jasperneite, 2017).
Example 2:
Putting emphasis on the Bluetooth aspect the elimination of the user interface would be
directly beneficial from the users point of view. The user interface would always be troublesome
with the prospective of the user and different secyrity issue can arise from its directly
implementation. The elimination of the user interface would also save time

4INTERNET OF THINGS
Question 2
Specifications of Cables
Co axial cable
The co axial cable is very much similar to the cable type which is used in order to carry
Television signal. The main composition of the wire is a solid wire which is made up of copper
runs down the middle of the wire, around the solid wire is a thin layer of insulation and covering
the insulation are a metal foil and a braided wire. The main role of it is to protect against
interference of magnetic.
Bandwidth: the bandwidth of co axial cable is 1 GHz
Distance: 500m
Interference rating: limited to a distance but least susceptible to interference.
Cost: medium cost than other cables.
Security: The security involved in the wire can be considered as medium
Twisted pair Cable:
The twisted pair cable is the most common type of cable which can be found easily in the local
area network (LAN) networks. The data which is transmitted is from the pair of twisted pair of
wire. The twisting is mainly done in order to protect it from cross talk.
Bandwidth: the bandwidth of co axial cable is 1 MHz
Distance: 100m
Question 2
Specifications of Cables
Co axial cable
The co axial cable is very much similar to the cable type which is used in order to carry
Television signal. The main composition of the wire is a solid wire which is made up of copper
runs down the middle of the wire, around the solid wire is a thin layer of insulation and covering
the insulation are a metal foil and a braided wire. The main role of it is to protect against
interference of magnetic.
Bandwidth: the bandwidth of co axial cable is 1 GHz
Distance: 500m
Interference rating: limited to a distance but least susceptible to interference.
Cost: medium cost than other cables.
Security: The security involved in the wire can be considered as medium
Twisted pair Cable:
The twisted pair cable is the most common type of cable which can be found easily in the local
area network (LAN) networks. The data which is transmitted is from the pair of twisted pair of
wire. The twisting is mainly done in order to protect it from cross talk.
Bandwidth: the bandwidth of co axial cable is 1 MHz
Distance: 100m
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5INTERNET OF THINGS
Interference rating: limited to a distance but least susceptible to interference
Cost: it is very much cheaper than other cables.
Security: the security aspect lags behind in this category of cable.
Optical fiber cabling
The optical fiber cable mainly uses a optical fiber that mainly carry data signal which is in the
digital form in the form of pulses which are modulated. The main composition of the cable is that
it consist of an extremely thin cylinder which is referred to as core, the core is surrounded by a
concentrate layer of glass which is termed as cladding.
Bandwidth: the bandwidth of co axial cable is 75 THz
Distance: (single mode) – 10Km, (multi node) – 2Km
Interference rating: the cable is not susceptible to EMI
Cost: This category of cable is consider to be very much expensive
Security: this category of cable is imposed with high security aspects.
Question 3:
Summarized Table of Advantages, Disadvantages and Application of IoT
IoT Devices Advantages Disadvantages Application
Sensors * effect of dust, rain and snow is
limited
* signal which are
reflected form curves
can be difficult to
*Smart sleep system.
*Smart washing
Interference rating: limited to a distance but least susceptible to interference
Cost: it is very much cheaper than other cables.
Security: the security aspect lags behind in this category of cable.
Optical fiber cabling
The optical fiber cable mainly uses a optical fiber that mainly carry data signal which is in the
digital form in the form of pulses which are modulated. The main composition of the cable is that
it consist of an extremely thin cylinder which is referred to as core, the core is surrounded by a
concentrate layer of glass which is termed as cladding.
Bandwidth: the bandwidth of co axial cable is 75 THz
Distance: (single mode) – 10Km, (multi node) – 2Km
Interference rating: the cable is not susceptible to EMI
Cost: This category of cable is consider to be very much expensive
Security: this category of cable is imposed with high security aspects.
Question 3:
Summarized Table of Advantages, Disadvantages and Application of IoT
IoT Devices Advantages Disadvantages Application
Sensors * effect of dust, rain and snow is
limited
* signal which are
reflected form curves
can be difficult to
*Smart sleep system.
*Smart washing
6INTERNET OF THINGS
*The working is limited and would
work properly if and only if proper
power supply is given to it.
achieve. machine.
*Smart lightning.
*Weather monitoring.
*Blood Pressure
monitoring (Tozlu et al.,
2012).
Smart internet mirror.
RFID * 100% security is assured with tag
data where data cannot be
duplicated.
* large number of sizes, different
types and different materials are
appropriately available
*costly than barcode
* Barcode labels are
longer.
* used in tracking of
product which is mainly
used in jeweler tracking
airlines baggage (Gubbi
et al., 2013).
Video
Tracking
*Communication achieves devices.
* is another advantage of video
tracking is monitoring (Singh,
Tripathi and jara, 2014).
*Better quality of livelihood.
*international standard
compatibility is not
given
*Privacy and security
both will be exposed.
*Human-computer
interaction.
*Augmentation of
reality.
*Medical imaging.
*Video communication.
Question 4
The internet of things promises to provide ubiquitous and unprecedented access to any
device that can easily make up for anything with regards to health, wellness devices and
assembly lines. The different aspects which can be related are to the security issue. The internet
of things can provide different advantage as well as disadvantage added to it (Wollschlaeger,
Sauter & Jasperneite, 2017)..
*The working is limited and would
work properly if and only if proper
power supply is given to it.
achieve. machine.
*Smart lightning.
*Weather monitoring.
*Blood Pressure
monitoring (Tozlu et al.,
2012).
Smart internet mirror.
RFID * 100% security is assured with tag
data where data cannot be
duplicated.
* large number of sizes, different
types and different materials are
appropriately available
*costly than barcode
* Barcode labels are
longer.
* used in tracking of
product which is mainly
used in jeweler tracking
airlines baggage (Gubbi
et al., 2013).
Video
Tracking
*Communication achieves devices.
* is another advantage of video
tracking is monitoring (Singh,
Tripathi and jara, 2014).
*Better quality of livelihood.
*international standard
compatibility is not
given
*Privacy and security
both will be exposed.
*Human-computer
interaction.
*Augmentation of
reality.
*Medical imaging.
*Video communication.
Question 4
The internet of things promises to provide ubiquitous and unprecedented access to any
device that can easily make up for anything with regards to health, wellness devices and
assembly lines. The different aspects which can be related are to the security issue. The internet
of things can provide different advantage as well as disadvantage added to it (Wollschlaeger,
Sauter & Jasperneite, 2017)..

7INTERNET OF THINGS
In general the security and the protection of data are considered complimentary
requirement when it is related to Internet of Things services. Security can be related to anything
that involves various aspect of putting the data in a secured environment. There can be many
justifications and security aspects that can be involved in the security of the data in an internet of
things (IoT) service. When it comes to data one of the basic aspects that comes into play is
keeping the data secured from a variety of security breaches which are into active part now.
Putting emphasis on information security, it is regarded as preserving the confidentiality,
availability and integrity (Kranz, 2016). The security plays a vital role in every aspect putting
limelight on both the aspects for the organization itself and the benefits of the citizens. The most
important challenge is to ensure the availability and continuity prospective with the provision of
the services which are served by the Internet of Things, with it the main aspect of avoiding the
potential failure which are associated with interruptions and operational failure (Tozlu et al.,
2012) .
Question 5
Blocking Mode:
As peer the blocking phase, the guarantee which is achieved with the generation of the point
which is considered to be the end point will to gave in order to get the appropriate respond of the
request made with the initialization of the point which is considered as the end point and with
regards to its completion which is long and which can be referred to as waiting point with
emphasis on the originator (Wollschlaeger, Sauter & Jasperneite, 2017) being synchronous
asynchronous message would be received by the originator
Publish/Subscribe Paradigm:
In general the security and the protection of data are considered complimentary
requirement when it is related to Internet of Things services. Security can be related to anything
that involves various aspect of putting the data in a secured environment. There can be many
justifications and security aspects that can be involved in the security of the data in an internet of
things (IoT) service. When it comes to data one of the basic aspects that comes into play is
keeping the data secured from a variety of security breaches which are into active part now.
Putting emphasis on information security, it is regarded as preserving the confidentiality,
availability and integrity (Kranz, 2016). The security plays a vital role in every aspect putting
limelight on both the aspects for the organization itself and the benefits of the citizens. The most
important challenge is to ensure the availability and continuity prospective with the provision of
the services which are served by the Internet of Things, with it the main aspect of avoiding the
potential failure which are associated with interruptions and operational failure (Tozlu et al.,
2012) .
Question 5
Blocking Mode:
As peer the blocking phase, the guarantee which is achieved with the generation of the point
which is considered to be the end point will to gave in order to get the appropriate respond of the
request made with the initialization of the point which is considered as the end point and with
regards to its completion which is long and which can be referred to as waiting point with
emphasis on the originator (Wollschlaeger, Sauter & Jasperneite, 2017) being synchronous
asynchronous message would be received by the originator
Publish/Subscribe Paradigm:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
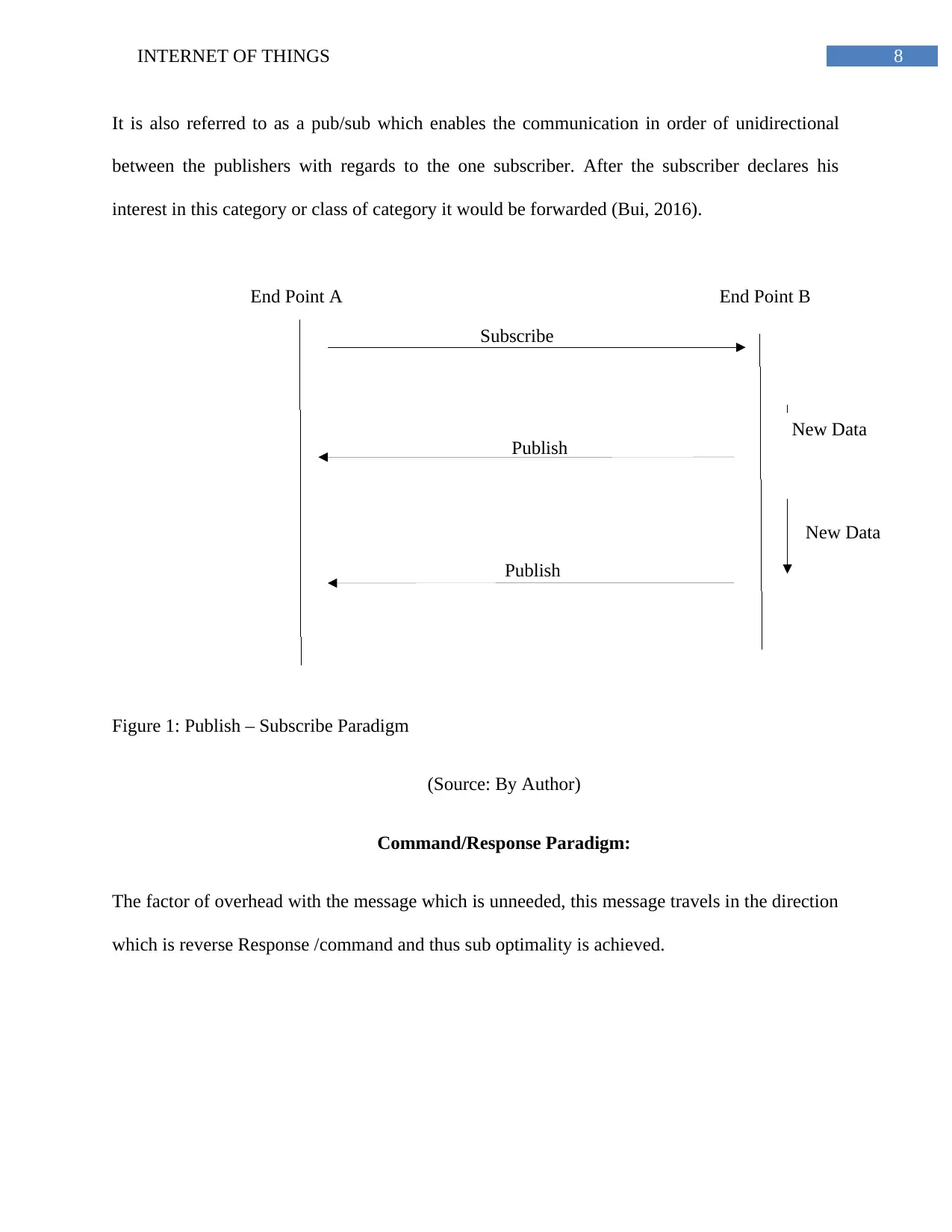
8INTERNET OF THINGS
Publish
Publish
Subscribe
End Point BEnd Point A
New Data
It is also referred to as a pub/sub which enables the communication in order of unidirectional
between the publishers with regards to the one subscriber. After the subscriber declares his
interest in this category or class of category it would be forwarded (Bui, 2016).
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
Command/Response Paradigm:
The factor of overhead with the message which is unneeded, this message travels in the direction
which is reverse Response /command and thus sub optimality is achieved.
New Data
Publish
Publish
Subscribe
End Point BEnd Point A
New Data
It is also referred to as a pub/sub which enables the communication in order of unidirectional
between the publishers with regards to the one subscriber. After the subscriber declares his
interest in this category or class of category it would be forwarded (Bui, 2016).
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
Command/Response Paradigm:
The factor of overhead with the message which is unneeded, this message travels in the direction
which is reverse Response /command and thus sub optimality is achieved.
New Data

9INTERNET OF THINGS
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 2: Command/Response paradigm
(Source: By Author)
Question 6
Neilson’s Law: Comparing to Moore’s law the user bandwidth increases by almost 60%
in every year which is very much less. The time period of 1989 to 2016 is the best fitted period
of the law. The law wis directly related to the bandwidth with regards to the internet and mainly
states that a user connection which is estimated to be on the higher end , the speed grows to an
average of 50% every year.(Wollschlaeger, Sauter & Jasperneite, 2017).
Moore’s law is same as the Neilson’s law but the law which is stated by Neilson is more
established. Moore stated that “computer double in capabilities every 18 months”, which is
related with 60% of annual growth (Kumar et al., 2017).
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 2: Command/Response paradigm
(Source: By Author)
Question 6
Neilson’s Law: Comparing to Moore’s law the user bandwidth increases by almost 60%
in every year which is very much less. The time period of 1989 to 2016 is the best fitted period
of the law. The law wis directly related to the bandwidth with regards to the internet and mainly
states that a user connection which is estimated to be on the higher end , the speed grows to an
average of 50% every year.(Wollschlaeger, Sauter & Jasperneite, 2017).
Moore’s law is same as the Neilson’s law but the law which is stated by Neilson is more
established. Moore stated that “computer double in capabilities every 18 months”, which is
related with 60% of annual growth (Kumar et al., 2017).

10INTERNET OF THINGS
Implication of Nelson’s law in IoT
In around 2024 it can be expected that with the implementation of the sensor technology
it will break through the “trillion sensor” by which the creating of data stream with every
surround surface can be achieved. Sensors will be very much soon embedded in various fields
such as houses, cars and even in the clothing. Microchip will be a part of the trending approach
with its direct implementation in body or skin sensor. This implementation can be a trend in the
near future. (Bonomi et al., 2017).
Implication of Nelson’s law in IoT
In around 2024 it can be expected that with the implementation of the sensor technology
it will break through the “trillion sensor” by which the creating of data stream with every
surround surface can be achieved. Sensors will be very much soon embedded in various fields
such as houses, cars and even in the clothing. Microchip will be a part of the trending approach
with its direct implementation in body or skin sensor. This implementation can be a trend in the
near future. (Bonomi et al., 2017).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11INTERNET OF THINGS
Reference
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2017, August). Fog computing and its role in
the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile
cloud computing (pp. 13-16). ACM.
Bui, N. (2016). Internet of Things.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-
68). Palgrave Macmillan, London.
Kranz, M. (2016). Building the Internet of Things: Implement New Business Models, Disrupt
Competitors, Transform Your Industry. John Wiley & Sons.
Kumar, M., Bhaskar, M. S., Padmanaban, S., Siano, P., Blaabjerg, F., & Leonowicz, Z. (2017,
June). Electric field analysis of extra high voltage (EHV) underground cables using finite
element method. In Environment and Electrical Engineering and 2017 IEEE Industrial
and Commercial Power Systems Europe (EEEIC/I&CPS Europe), 2017 IEEE
International Conference on (pp. 1-4). IEEE.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
McKernan, K. J. (2016). The chloroplast genome hidden in plain sight, open access publishing
and anti-fragile distributed data sources. Mitochondrial DNA Part A, 27(6), 4518-4519.
Mulani, T. T., & Pingle, S. V. (2016). Internet of things. International Research Journal of
Multidisciplinary Studies, 2(3).
Reference
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2017, August). Fog computing and its role in
the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile
cloud computing (pp. 13-16). ACM.
Bui, N. (2016). Internet of Things.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-
68). Palgrave Macmillan, London.
Kranz, M. (2016). Building the Internet of Things: Implement New Business Models, Disrupt
Competitors, Transform Your Industry. John Wiley & Sons.
Kumar, M., Bhaskar, M. S., Padmanaban, S., Siano, P., Blaabjerg, F., & Leonowicz, Z. (2017,
June). Electric field analysis of extra high voltage (EHV) underground cables using finite
element method. In Environment and Electrical Engineering and 2017 IEEE Industrial
and Commercial Power Systems Europe (EEEIC/I&CPS Europe), 2017 IEEE
International Conference on (pp. 1-4). IEEE.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
McKernan, K. J. (2016). The chloroplast genome hidden in plain sight, open access publishing
and anti-fragile distributed data sources. Mitochondrial DNA Part A, 27(6), 4518-4519.
Mulani, T. T., & Pingle, S. V. (2016). Internet of things. International Research Journal of
Multidisciplinary Studies, 2(3).

12INTERNET OF THINGS
Wollschlaeger, M., Sauter, T., & Jasperneite, J. (2017). The future of industrial communication:
Automation networks in the era of the internet of things and industry 4.0. IEEE Industrial
Electronics Magazine, 11(1), 17-27.
Wollschlaeger, M., Sauter, T., & Jasperneite, J. (2017). The future of industrial communication:
Automation networks in the era of the internet of things and industry 4.0. IEEE Industrial
Electronics Magazine, 11(1), 17-27.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





