MN503 Internetworking: Secure School Network Design with Guest Network
VerifiedAdded on 2023/06/11
|9
|1336
|320
Report
AI Summary
This report details the design and implementation of a network for a primary school, accommodating both authorized users and guest users. The project scope includes creating a secure LAN connection for 50 authorized personnel and a separate, restricted network for 10 guest users. Key requirements involve isolating the guest network from the main LAN, providing FTP access for guests without compromising school data, and ensuring the LAN supports various applications for daily use. The network design incorporates VLANs, subnetting, DHCP configuration, and security measures to manage IP addresses, control access, and protect sensitive information. Routers and switches are configured to block unauthorized access, and a separate subnet is created for the guest network to prevent intrusion into the main LAN. The design aims to support simultaneous use by authorized users and guests, ensuring network performance and security. The document concludes with configuration guidelines for access points and servers, along with security considerations to protect the network from potential threats. Desklib provides this and other solved assignments to aid students in their studies.

OVERVIEW OF INTERNETWORKING
Name of the Student
Name of the University
Author’s Note
Page 1 of 9
Name of the Student
Name of the University
Author’s Note
Page 1 of 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2OVERVIEW OF INTERNETWORKING
Table of Contents
Project Scope:..................................................................................................................................3
Project Requirement:......................................................................................................................3
Network Design:..............................................................................................................................4
IP Addressing Table..........................................................................................................................4
Network Topology Diagram.............................................................................................................5
Switch Configuration.......................................................................................................................5
Router Configuration.......................................................................................................................8
DHCP Configuration.........................................................................................................................8
Access Point, Server Configuration guidelines................................................................................8
Security Configuration.....................................................................................................................9
Bibliography...................................................................................................................................10
Table of Contents
Project Scope:..................................................................................................................................3
Project Requirement:......................................................................................................................3
Network Design:..............................................................................................................................4
IP Addressing Table..........................................................................................................................4
Network Topology Diagram.............................................................................................................5
Switch Configuration.......................................................................................................................5
Router Configuration.......................................................................................................................8
DHCP Configuration.........................................................................................................................8
Access Point, Server Configuration guidelines................................................................................8
Security Configuration.....................................................................................................................9
Bibliography...................................................................................................................................10

3OVERVIEW OF INTERNETWORKING
Project Scope:
Proper network implementation designing is the main scope of this project. The Do’s, Don’ts
and the criteria have to be maintained for project scope design. The implementation purpose of
the network has to be designed. The project will evaluate the creation of user protected LAN
connection that is suitable for using in a small scale business organisation. As per an overall
knowledge, a LAN connection should have to be compatible with 50 authorized user and that of
the 10 guest user. The 50 user are the different authorized personnel of the school and 10
members are the visitor of the school. The requirements of the visitors are that at the time if
visiting they want to download a number of essential files from the online drive of the school
authority. The problem is summarized in that section that, for downloading the file the guest
used have to take entry in the FTP server, through the daily user maintains their connection. If
the user gets authorized to use the same FTP connection, the other information of the school
authority became accessible to them, which have to be stopped.
Project Requirement:
Main business requirements are summarized on the following section:
For accessing the guest user, a different FTP server has to be used. Along with this the
guest server preserved for guest user have to be separate from other network that are
connected through LAN. It would be better if a different LAN network can be used for
guest use [2].
LAN network can be justified in that sector only where the working are compelled in
daily basis. It would be better if the guests are not premised to use the LAN network. At
this decision, the LAN network can be kept protected from the sensitive use of the guest
user.
For daily basis use, the LAN network have to be consists of huge application supported.
Apart from this the activities like file sharing, file receiving, file sending, Email sending
have to be compelled. Activities increasing scope should be elaborated [6].
For designing the above theme, the routers, switches have to be used. It should be
remind that, the configuration of the routers, hubs and the switches can be done
maintaining the blocked user who is out of the reach of the main LAN area.
Project Scope:
Proper network implementation designing is the main scope of this project. The Do’s, Don’ts
and the criteria have to be maintained for project scope design. The implementation purpose of
the network has to be designed. The project will evaluate the creation of user protected LAN
connection that is suitable for using in a small scale business organisation. As per an overall
knowledge, a LAN connection should have to be compatible with 50 authorized user and that of
the 10 guest user. The 50 user are the different authorized personnel of the school and 10
members are the visitor of the school. The requirements of the visitors are that at the time if
visiting they want to download a number of essential files from the online drive of the school
authority. The problem is summarized in that section that, for downloading the file the guest
used have to take entry in the FTP server, through the daily user maintains their connection. If
the user gets authorized to use the same FTP connection, the other information of the school
authority became accessible to them, which have to be stopped.
Project Requirement:
Main business requirements are summarized on the following section:
For accessing the guest user, a different FTP server has to be used. Along with this the
guest server preserved for guest user have to be separate from other network that are
connected through LAN. It would be better if a different LAN network can be used for
guest use [2].
LAN network can be justified in that sector only where the working are compelled in
daily basis. It would be better if the guests are not premised to use the LAN network. At
this decision, the LAN network can be kept protected from the sensitive use of the guest
user.
For daily basis use, the LAN network have to be consists of huge application supported.
Apart from this the activities like file sharing, file receiving, file sending, Email sending
have to be compelled. Activities increasing scope should be elaborated [6].
For designing the above theme, the routers, switches have to be used. It should be
remind that, the configuration of the routers, hubs and the switches can be done
maintaining the blocked user who is out of the reach of the main LAN area.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4OVERVIEW OF INTERNETWORKING
For designing the guest network, a separate subnet has to be created, that consists of
different configuration so that, from that, the main LAN connection can be tracked. The
user should have to facilitate for accessing the FTP server. Other from the FRP server the
user can be never use the LAN network. It should have to be blocked to the end user.
For designing if this type of network, some assumption have to be made. The assumptions are
described in the following section:
The LAN connection, have to so much effective that, at most 50 user can uses it
simultaneously with different type of working through the network.
Along with the normal user, the FTP section of the LAN network has to be compelled
with 10 guest user. The building sections have to be strong of that much level so that,
the coming and leaving of a user cannot affect the other user of the network [3].
Use to Dynamic IP is too much essential for this section. Only the internet connection of
the DHCP should be used. This application includes the file servers, email servers and
rest other kind of service.
At the end it can be said that, the accuracy of the LAN connection should be too much
compact. The different between the guest and the daily user should be like wired and
wireless connection. The FRT sections have to be fully separated from the LAN system.
Network Design:
According to the given rule the system principally contains subnet that is essentially utilized offering
help to expansive number of visitor client on the server. It is principally utilized for getting to different
For designing the guest network, a separate subnet has to be created, that consists of
different configuration so that, from that, the main LAN connection can be tracked. The
user should have to facilitate for accessing the FTP server. Other from the FRP server the
user can be never use the LAN network. It should have to be blocked to the end user.
For designing if this type of network, some assumption have to be made. The assumptions are
described in the following section:
The LAN connection, have to so much effective that, at most 50 user can uses it
simultaneously with different type of working through the network.
Along with the normal user, the FTP section of the LAN network has to be compelled
with 10 guest user. The building sections have to be strong of that much level so that,
the coming and leaving of a user cannot affect the other user of the network [3].
Use to Dynamic IP is too much essential for this section. Only the internet connection of
the DHCP should be used. This application includes the file servers, email servers and
rest other kind of service.
At the end it can be said that, the accuracy of the LAN connection should be too much
compact. The different between the guest and the daily user should be like wired and
wireless connection. The FRT sections have to be fully separated from the LAN system.
Network Design:
According to the given rule the system principally contains subnet that is essentially utilized offering
help to expansive number of visitor client on the server. It is principally utilized for getting to different
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5OVERVIEW OF INTERNETWORKING
sorts of records that is primarily present in different sort of FTP server. It is for the most part involving
confining the FTP server so one can't get any sort of access to this documents. Countless should be
legitimately done before appropriate making of system and different presumption related with it.
For creation and categorization of the network, VLAN network, different types of subnet are
required. In the normal school network, different IP addresses are tracked for server and the
guest. The use of subnet-ing also reduces the bulky work of the network administrator. It is too
much helpful for network management. The configuration of DHCP is done in the router by
categorizing the sub parts in to different interface and by categorized assigning of the user
interface if the IP address. For interface configuration, the starting IP address is assembled
within a specific range. The main application of the process can be determined at that time
when, the communication is placed between two or more PCs.
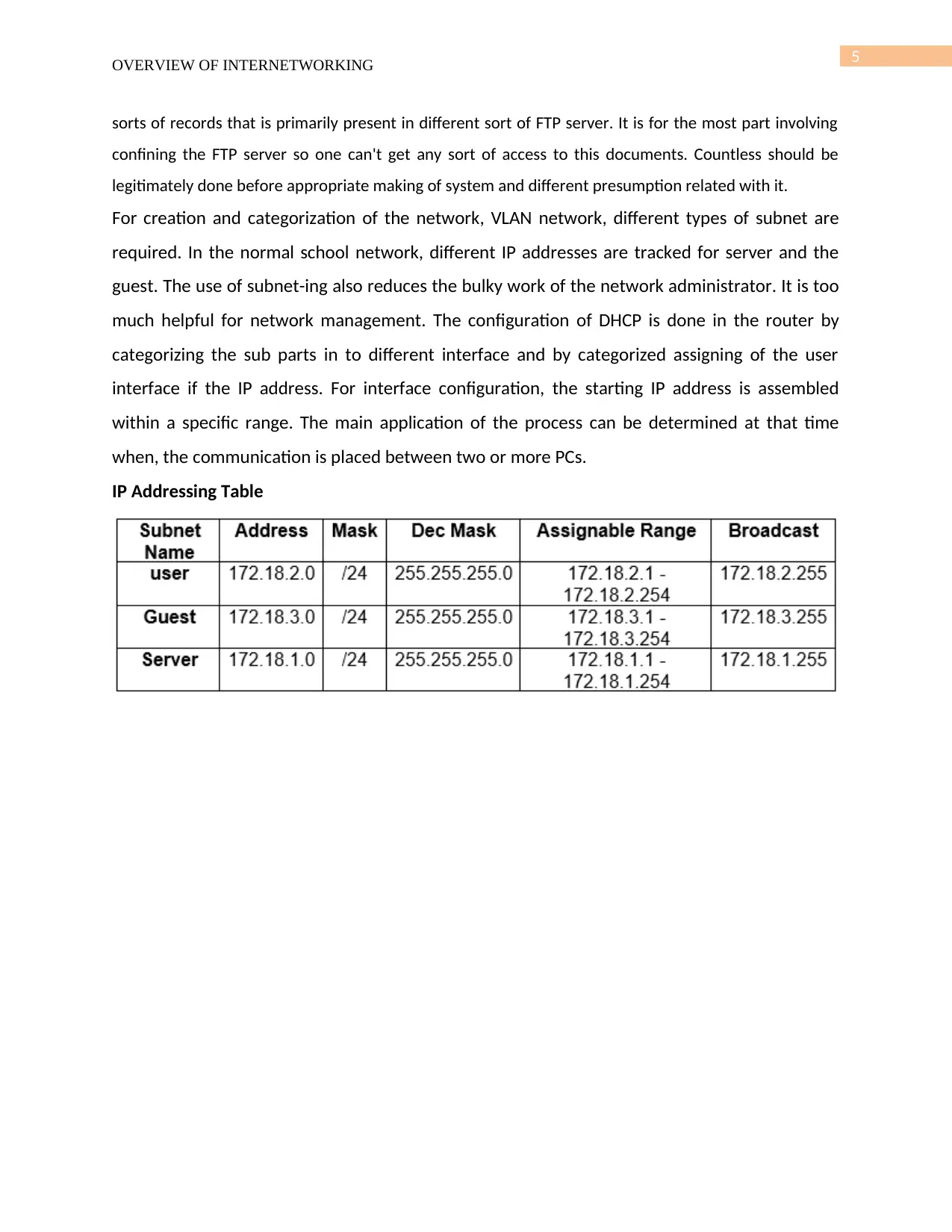
IP Addressing Table
sorts of records that is primarily present in different sort of FTP server. It is for the most part involving
confining the FTP server so one can't get any sort of access to this documents. Countless should be
legitimately done before appropriate making of system and different presumption related with it.
For creation and categorization of the network, VLAN network, different types of subnet are
required. In the normal school network, different IP addresses are tracked for server and the
guest. The use of subnet-ing also reduces the bulky work of the network administrator. It is too
much helpful for network management. The configuration of DHCP is done in the router by
categorizing the sub parts in to different interface and by categorized assigning of the user
interface if the IP address. For interface configuration, the starting IP address is assembled
within a specific range. The main application of the process can be determined at that time
when, the communication is placed between two or more PCs.
IP Addressing Table
6OVERVIEW OF INTERNETWORKING
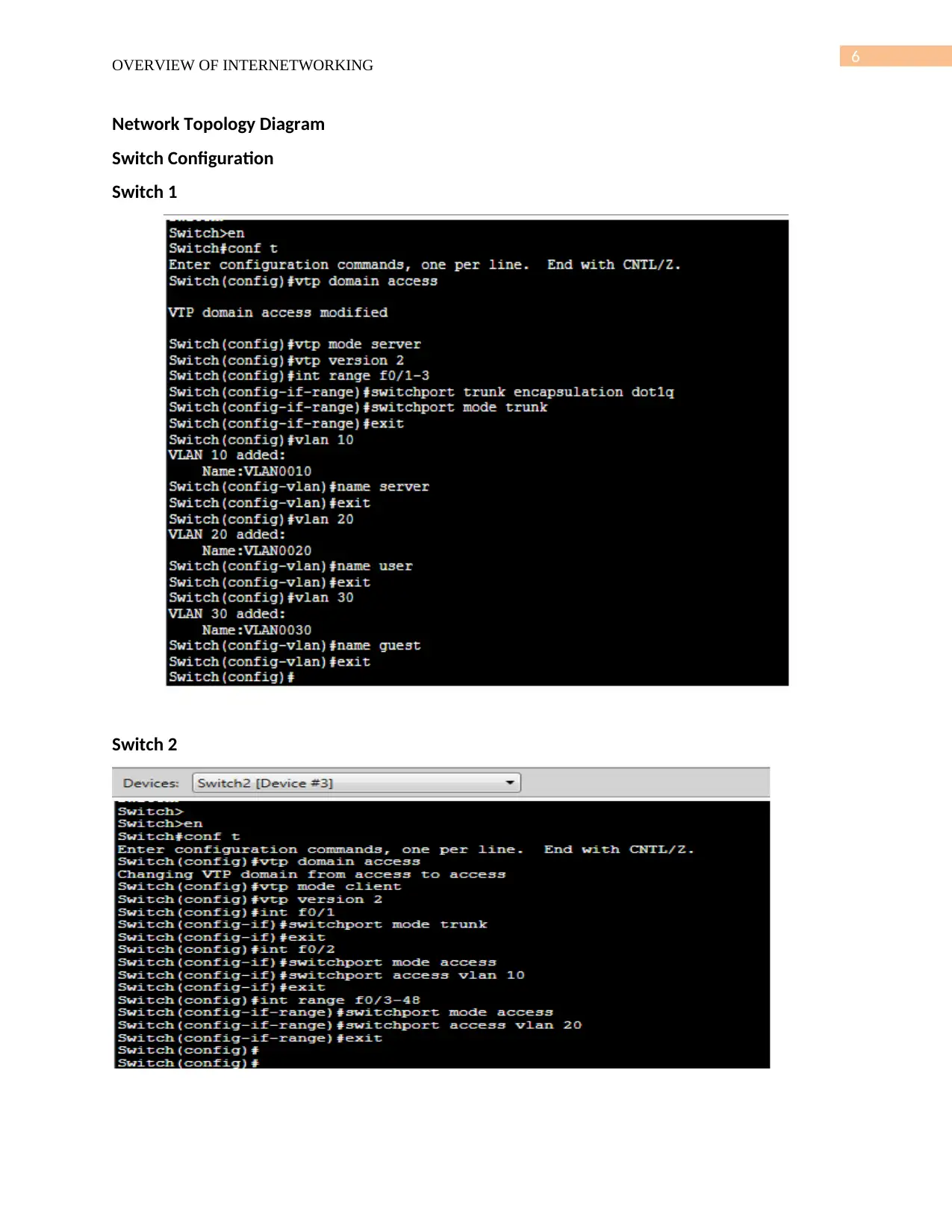
Network Topology Diagram
Switch Configuration
Switch 1
Switch 2
Network Topology Diagram
Switch Configuration
Switch 1
Switch 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7OVERVIEW OF INTERNETWORKING
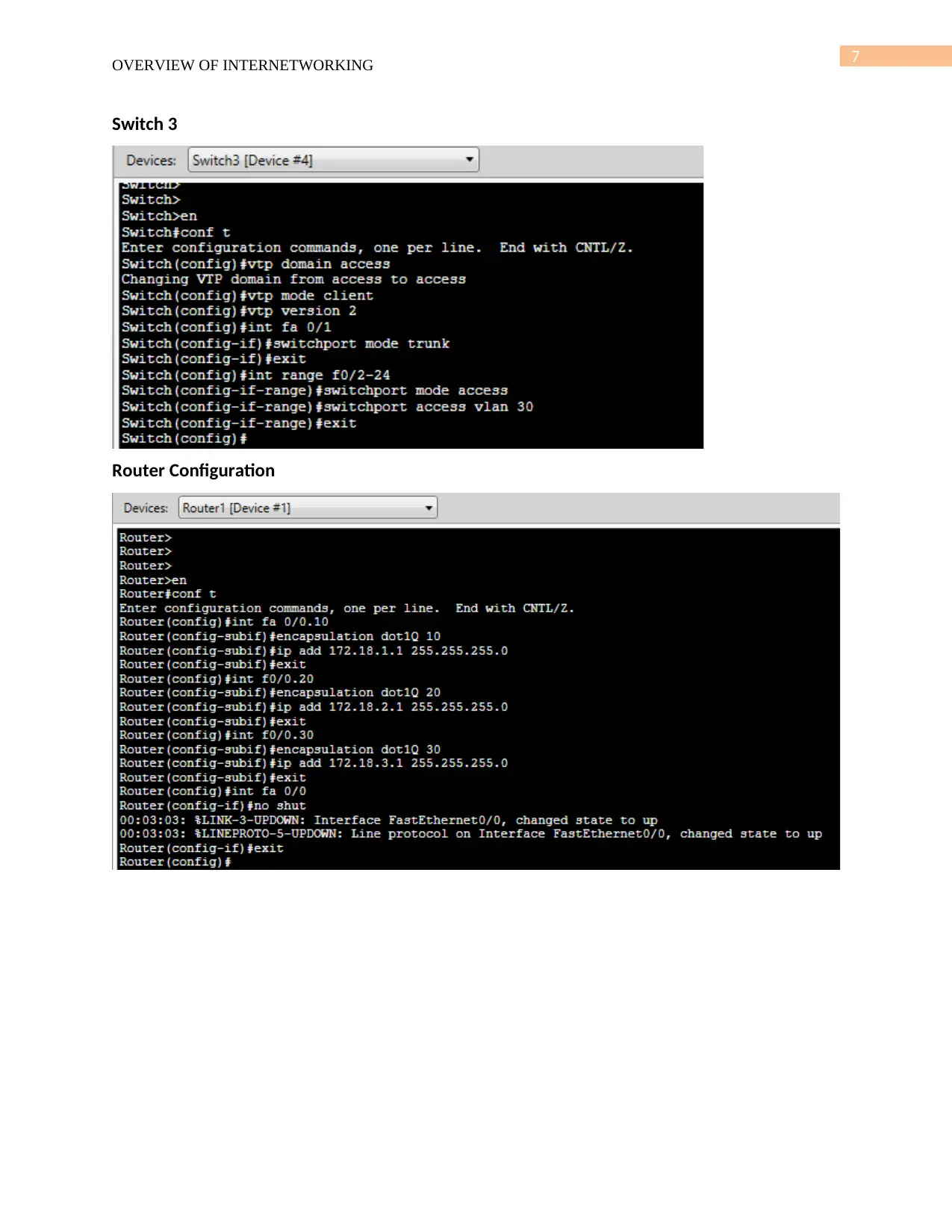
Switch 3
Router Configuration
Switch 3
Router Configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8OVERVIEW OF INTERNETWORKING
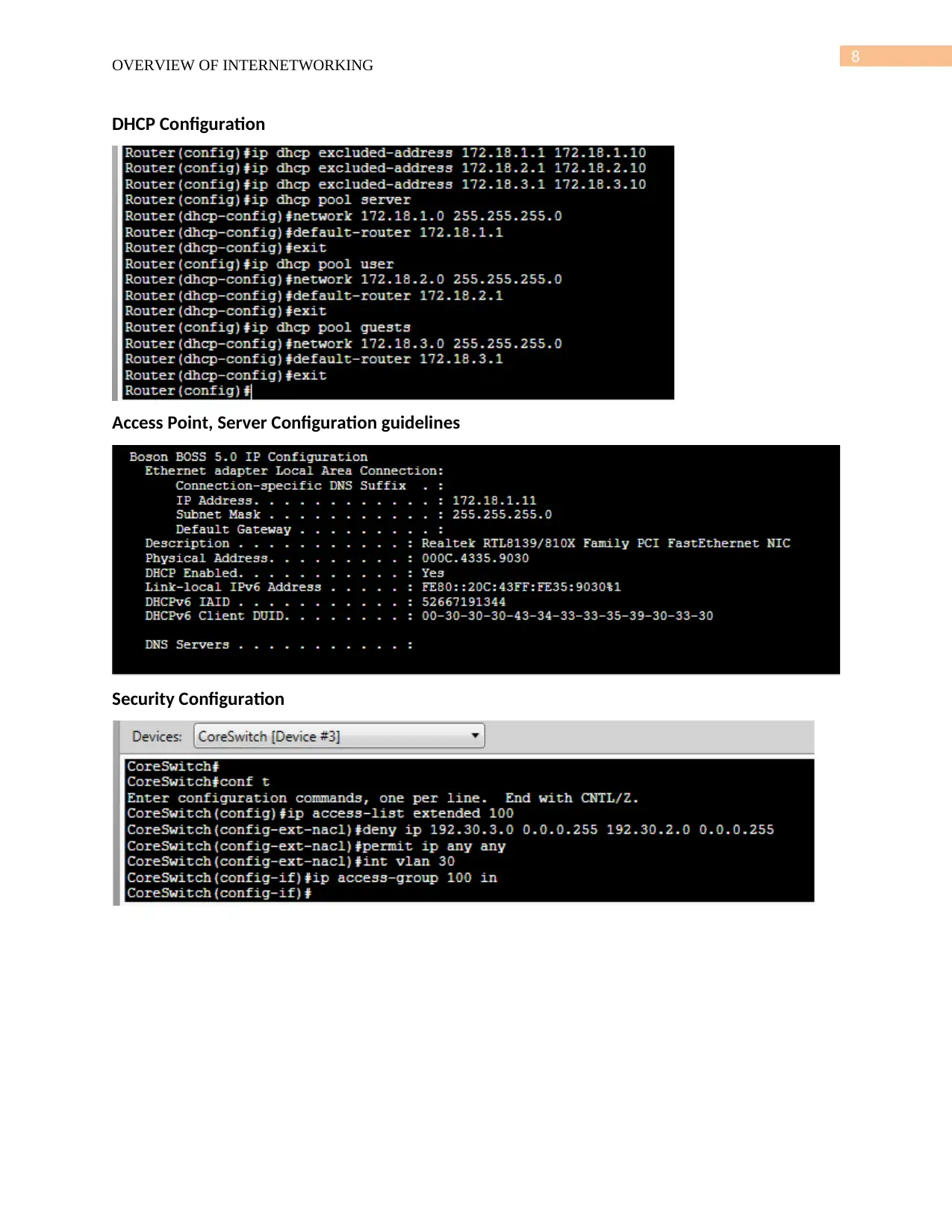
DHCP Configuration
Access Point, Server Configuration guidelines
Security Configuration
DHCP Configuration
Access Point, Server Configuration guidelines
Security Configuration

9OVERVIEW OF INTERNETWORKING
Bibliography
[1] D. Richter, K. Riemer, and J. vomBrocke, “Internet Social Networking,” Bus. Inf. Syst.
Eng., 2011.
[2] Open Networking Foundation, “SDN Architecture Overview (HPE),” White Pap., 2013
[3] J. C. Warren, “Industrial networking,” IEEE Ind. Appl. Mag., 2011.
[4] R. B. Al Anderson, Head First Networking. 2014
[5] J. F. Kurose and K. W. Ross, Computer Networking A Top-Down Approach. 2013.
[6] R. Van Meter, Quantum Networking. 2014.
[7] J. Davies, Understanding IPv6: Your Essential Guide to IPv6 on Windows Networks, 3rd Ed. 2012.
[8] L. Zhang, A. Afanasyev, J. Burke, V. Jacobson, kc claffy, P. Crowley, C. Papadopoulos, L. Wang,
and B. Zhang, “Named data networking,” ACM SIGCOMMComput. Commun. Rev., 2014.
[9]. Pavon-Marino, P., & Izquierdo-Zaragoza, J. L. Net2plan: an open source network
planning tool for bridging the gap between academia and industry. IEEE Network, 29(5), 90-96,
2015).
[10]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic
Influenza A (H1N1) using Social Network Analysis and cloud computing. Journal of
Computational Science, 12, pp.11-22., 2016.
Bibliography
[1] D. Richter, K. Riemer, and J. vomBrocke, “Internet Social Networking,” Bus. Inf. Syst.
Eng., 2011.
[2] Open Networking Foundation, “SDN Architecture Overview (HPE),” White Pap., 2013
[3] J. C. Warren, “Industrial networking,” IEEE Ind. Appl. Mag., 2011.
[4] R. B. Al Anderson, Head First Networking. 2014
[5] J. F. Kurose and K. W. Ross, Computer Networking A Top-Down Approach. 2013.
[6] R. Van Meter, Quantum Networking. 2014.
[7] J. Davies, Understanding IPv6: Your Essential Guide to IPv6 on Windows Networks, 3rd Ed. 2012.
[8] L. Zhang, A. Afanasyev, J. Burke, V. Jacobson, kc claffy, P. Crowley, C. Papadopoulos, L. Wang,
and B. Zhang, “Named data networking,” ACM SIGCOMMComput. Commun. Rev., 2014.
[9]. Pavon-Marino, P., & Izquierdo-Zaragoza, J. L. Net2plan: an open source network
planning tool for bridging the gap between academia and industry. IEEE Network, 29(5), 90-96,
2015).
[10]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic
Influenza A (H1N1) using Social Network Analysis and cloud computing. Journal of
Computational Science, 12, pp.11-22., 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

