Network Design and Implementation Report for Internetworking Overview
VerifiedAdded on 2023/06/04
|9
|1536
|243
Report
AI Summary
This report presents a comprehensive network design for a firm with five departments, each assigned its own subnet. The project scope includes the creation of VLANs, DHCP configuration for automated IP address assignment, and the analysis of required protocols for network communication. The design incorporates an IP addressing scheme, business rule implementation, and network security measures, including ACL configuration to restrict access. The report details the configuration of switches, routers, and DHCP services, as well as guidelines for access points and server configurations. The network topology is illustrated, and the conclusion highlights how the designed network supports the firm's business requirements, enhancing performance and efficiency. The IP address table and network topology diagram are included for clarity. The report also includes a bibliography with relevant references.

Running head: OVERVIEW OF INTERNETWORKING
Overview of internetworking
Network requirement analysis and plan
Student Name:
University Name:
Overview of internetworking
Network requirement analysis and plan
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
OVERVIEW OF INTERNETWORKING
Table of Contents
1. Project Scope.....................................................................................................................................2
2. Project Requirements........................................................................................................................2
3. Network Design.................................................................................................................................3
4. IP address table.................................................................................................................................3
5. Network Topology Diagram...............................................................................................................3
5.1. Switch Configuration..................................................................................................................3
5.2. Router Configuration..................................................................................................................5
5.3. DHCP Configuration....................................................................................................................6
5.4. Access Point, Server Configuration Guidelines...........................................................................6
5.5. Network Security Configuration.................................................................................................6
6. Conclusion.........................................................................................................................................7
Bibliography...........................................................................................................................................8
OVERVIEW OF INTERNETWORKING
Table of Contents
1. Project Scope.....................................................................................................................................2
2. Project Requirements........................................................................................................................2
3. Network Design.................................................................................................................................3
4. IP address table.................................................................................................................................3
5. Network Topology Diagram...............................................................................................................3
5.1. Switch Configuration..................................................................................................................3
5.2. Router Configuration..................................................................................................................5
5.3. DHCP Configuration....................................................................................................................6
5.4. Access Point, Server Configuration Guidelines...........................................................................6
5.5. Network Security Configuration.................................................................................................6
6. Conclusion.........................................................................................................................................7
Bibliography...........................................................................................................................................8

2
OVERVIEW OF INTERNETWORKING
1. Project Scope
The aim of this project is to develop the network design for the firm having 5 departments with 5
subnets. The scope that has been identified in context to this project on designing network for the
firm are listed as below:
Distribution of the network into five different subnets separately for each department.
Creation of VLAN for each subnet separately and configuration of the router to support
DHCP IP addressing.
DHCP IP addressing will be used for automated assigning of IP address to the different nodes
that are connected to each VLAN.
Analysis of protocol that is required for networking and communication between devices for
designing the network.
Developing an IP addressing scheme to configure interfaces of the networking devices with
required IP address along with the subnetting.
Identifying business rules of the firm and configuring the network as per those rules so that
allow or deny can be implemented for various services.
Documentation of the network configuration and designing prototype for the network in
simulation application to identify errors within configuration of the network.
Determining the number of users that will be enrolled in each subnet and assigning of IP
address for the devices within the determined IP address range.
2. Project Requirements
The requirements of the project that has been determined for development of the network solution
to support operations of the firm are listed as below:
Analysing the suitable technology and designing application for the network so that the aims
and objective of the firm can be met.
Aligning the network for the firm as per the business rules and requirements.
Creation of network design in Netsim Simulator application to implement the devices and
equipment in the network along with identifying the suitable routing protocols to develop
the network.
Detailing of the network configuration along with detailed IP addressing scheme and
troubleshooting of errors in configuration of the devices.
Application of required security measures so that communication between devices can be
kept secure and protect the network from unauthorised access.
Configuring the server with required services so that the business rules and requirements
can be fulfilled.
The server have to be configured such that requirements of the different departments can
be fulfilled as per their subnet.
Analysis of the guidelines for configuring the servers as well as access points so that the
configurations are as per required standards and specifications.
Creation of policy for network security and rules to configure the firewall so that it will be
able to allow or deny the services as per subnet for each department.
Determining the budget required for design and development of the network along with
detailing the prices for each hardware device in the network.
Configuration of the router having DHCP services so that IP address for the devices can be
assigned automatically.
OVERVIEW OF INTERNETWORKING
1. Project Scope
The aim of this project is to develop the network design for the firm having 5 departments with 5
subnets. The scope that has been identified in context to this project on designing network for the
firm are listed as below:
Distribution of the network into five different subnets separately for each department.
Creation of VLAN for each subnet separately and configuration of the router to support
DHCP IP addressing.
DHCP IP addressing will be used for automated assigning of IP address to the different nodes
that are connected to each VLAN.
Analysis of protocol that is required for networking and communication between devices for
designing the network.
Developing an IP addressing scheme to configure interfaces of the networking devices with
required IP address along with the subnetting.
Identifying business rules of the firm and configuring the network as per those rules so that
allow or deny can be implemented for various services.
Documentation of the network configuration and designing prototype for the network in
simulation application to identify errors within configuration of the network.
Determining the number of users that will be enrolled in each subnet and assigning of IP
address for the devices within the determined IP address range.
2. Project Requirements
The requirements of the project that has been determined for development of the network solution
to support operations of the firm are listed as below:
Analysing the suitable technology and designing application for the network so that the aims
and objective of the firm can be met.
Aligning the network for the firm as per the business rules and requirements.
Creation of network design in Netsim Simulator application to implement the devices and
equipment in the network along with identifying the suitable routing protocols to develop
the network.
Detailing of the network configuration along with detailed IP addressing scheme and
troubleshooting of errors in configuration of the devices.
Application of required security measures so that communication between devices can be
kept secure and protect the network from unauthorised access.
Configuring the server with required services so that the business rules and requirements
can be fulfilled.
The server have to be configured such that requirements of the different departments can
be fulfilled as per their subnet.
Analysis of the guidelines for configuring the servers as well as access points so that the
configurations are as per required standards and specifications.
Creation of policy for network security and rules to configure the firewall so that it will be
able to allow or deny the services as per subnet for each department.
Determining the budget required for design and development of the network along with
detailing the prices for each hardware device in the network.
Configuration of the router having DHCP services so that IP address for the devices can be
assigned automatically.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
OVERVIEW OF INTERNETWORKING
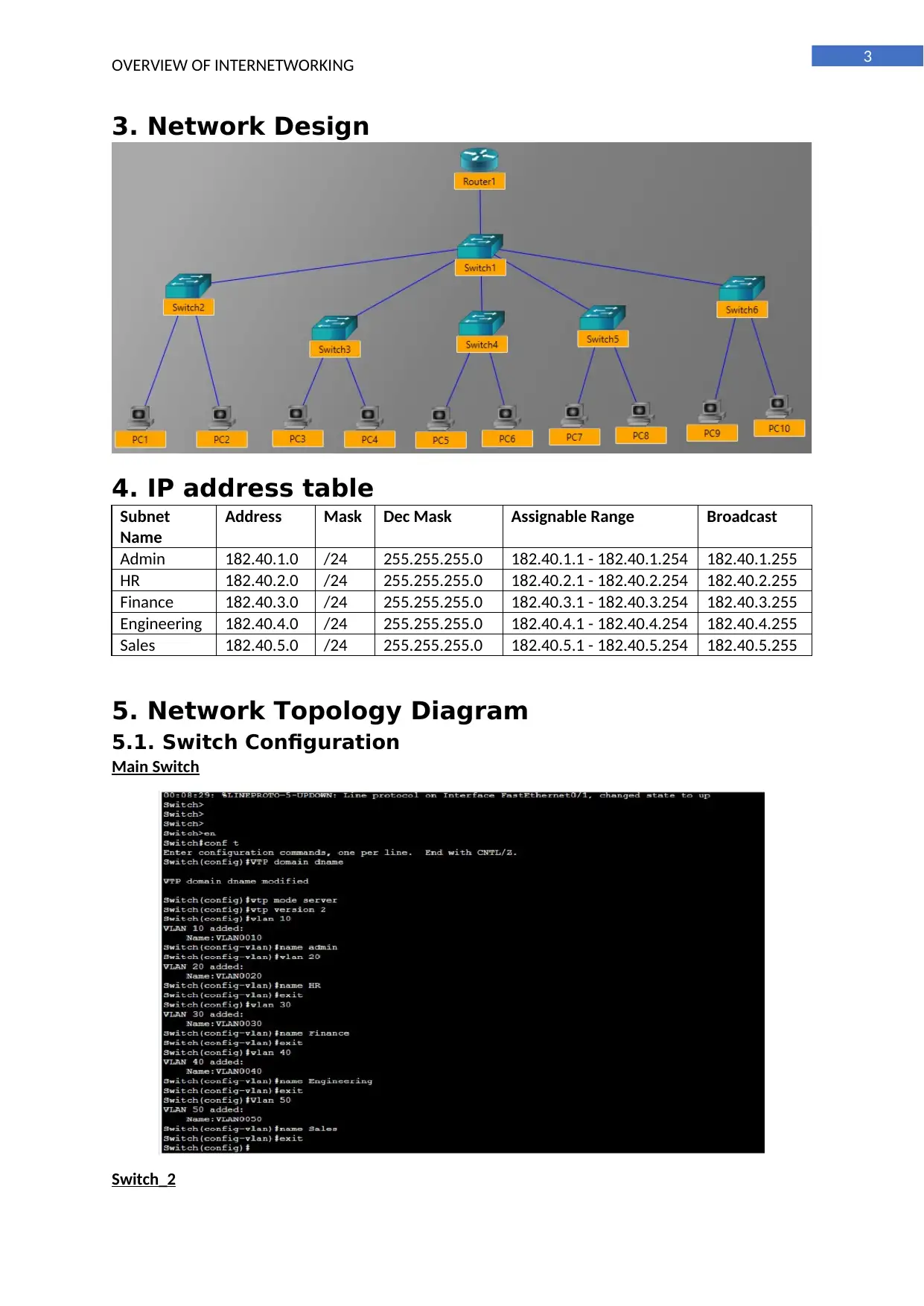
3. Network Design
4. IP address table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
Admin 182.40.1.0 /24 255.255.255.0 182.40.1.1 - 182.40.1.254 182.40.1.255
HR 182.40.2.0 /24 255.255.255.0 182.40.2.1 - 182.40.2.254 182.40.2.255
Finance 182.40.3.0 /24 255.255.255.0 182.40.3.1 - 182.40.3.254 182.40.3.255
Engineering 182.40.4.0 /24 255.255.255.0 182.40.4.1 - 182.40.4.254 182.40.4.255
Sales 182.40.5.0 /24 255.255.255.0 182.40.5.1 - 182.40.5.254 182.40.5.255
5. Network Topology Diagram
5.1. Switch Configuration
Main Switch
Switch_2
OVERVIEW OF INTERNETWORKING
3. Network Design
4. IP address table
Subnet
Name
Address Mask Dec Mask Assignable Range Broadcast
Admin 182.40.1.0 /24 255.255.255.0 182.40.1.1 - 182.40.1.254 182.40.1.255
HR 182.40.2.0 /24 255.255.255.0 182.40.2.1 - 182.40.2.254 182.40.2.255
Finance 182.40.3.0 /24 255.255.255.0 182.40.3.1 - 182.40.3.254 182.40.3.255
Engineering 182.40.4.0 /24 255.255.255.0 182.40.4.1 - 182.40.4.254 182.40.4.255
Sales 182.40.5.0 /24 255.255.255.0 182.40.5.1 - 182.40.5.254 182.40.5.255
5. Network Topology Diagram
5.1. Switch Configuration
Main Switch
Switch_2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
OVERVIEW OF INTERNETWORKING
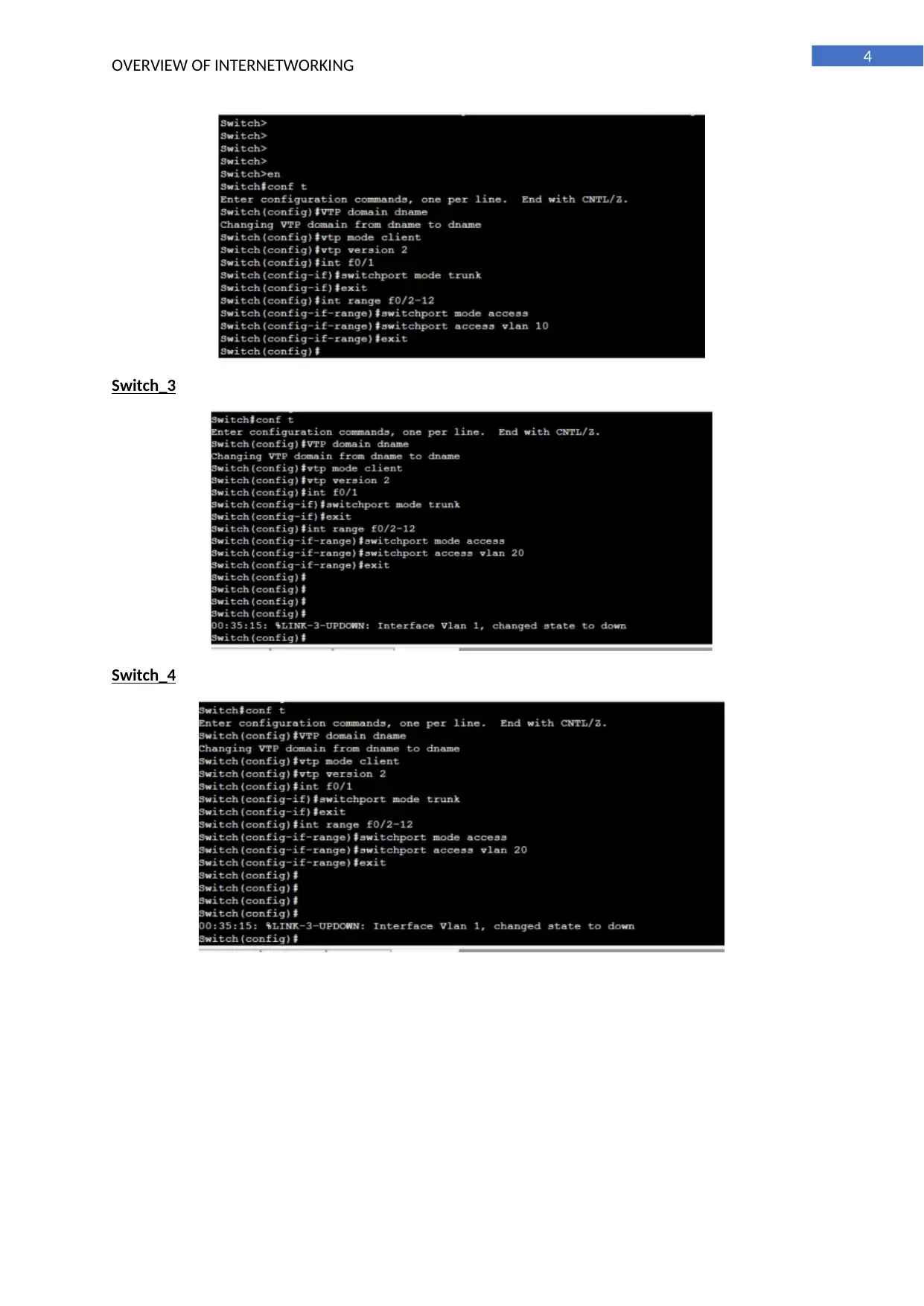
Switch_3
Switch_4
OVERVIEW OF INTERNETWORKING
Switch_3
Switch_4
5
OVERVIEW OF INTERNETWORKING
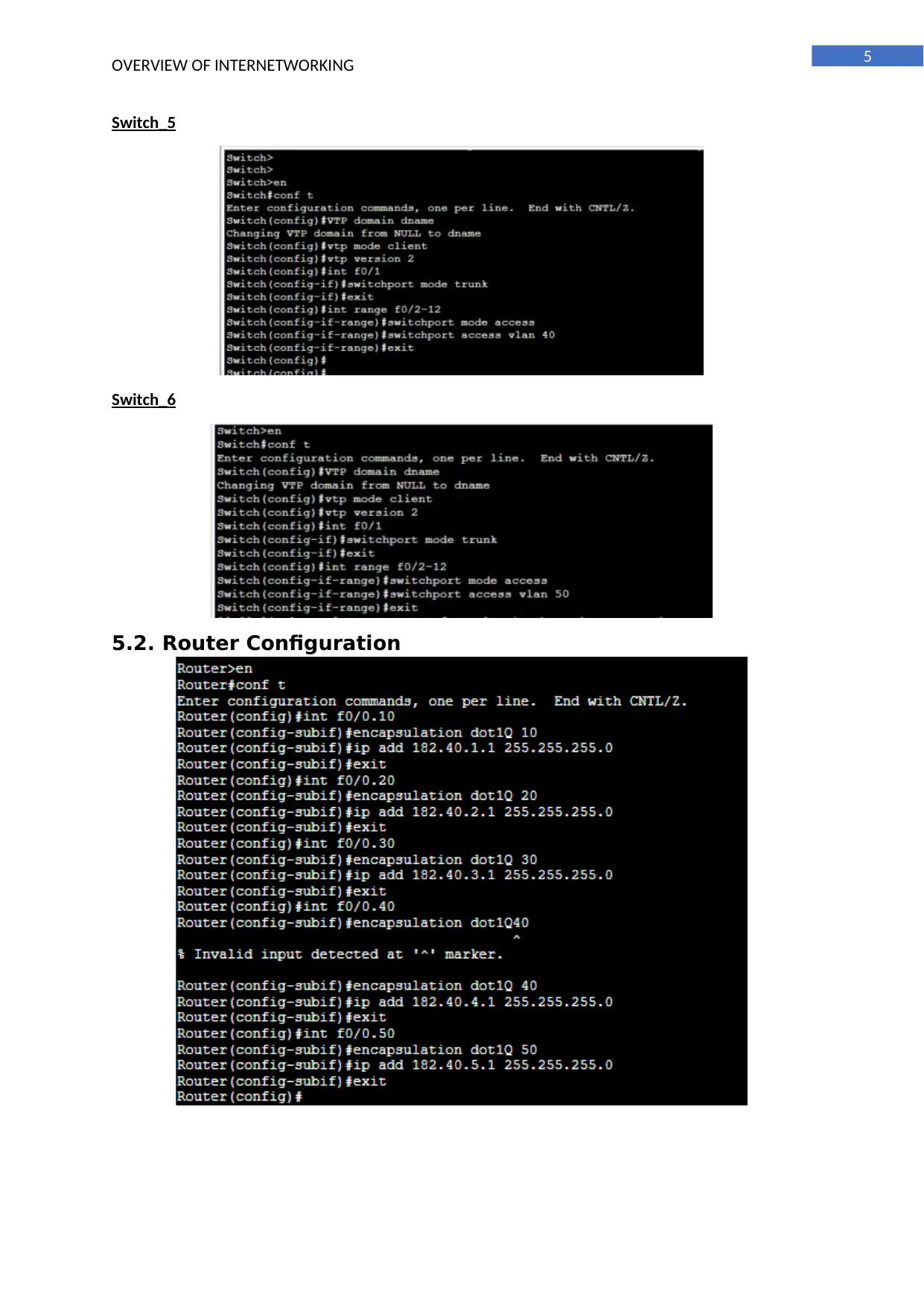
Switch_5
Switch_6
5.2. Router Configuration
OVERVIEW OF INTERNETWORKING
Switch_5
Switch_6
5.2. Router Configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
OVERVIEW OF INTERNETWORKING
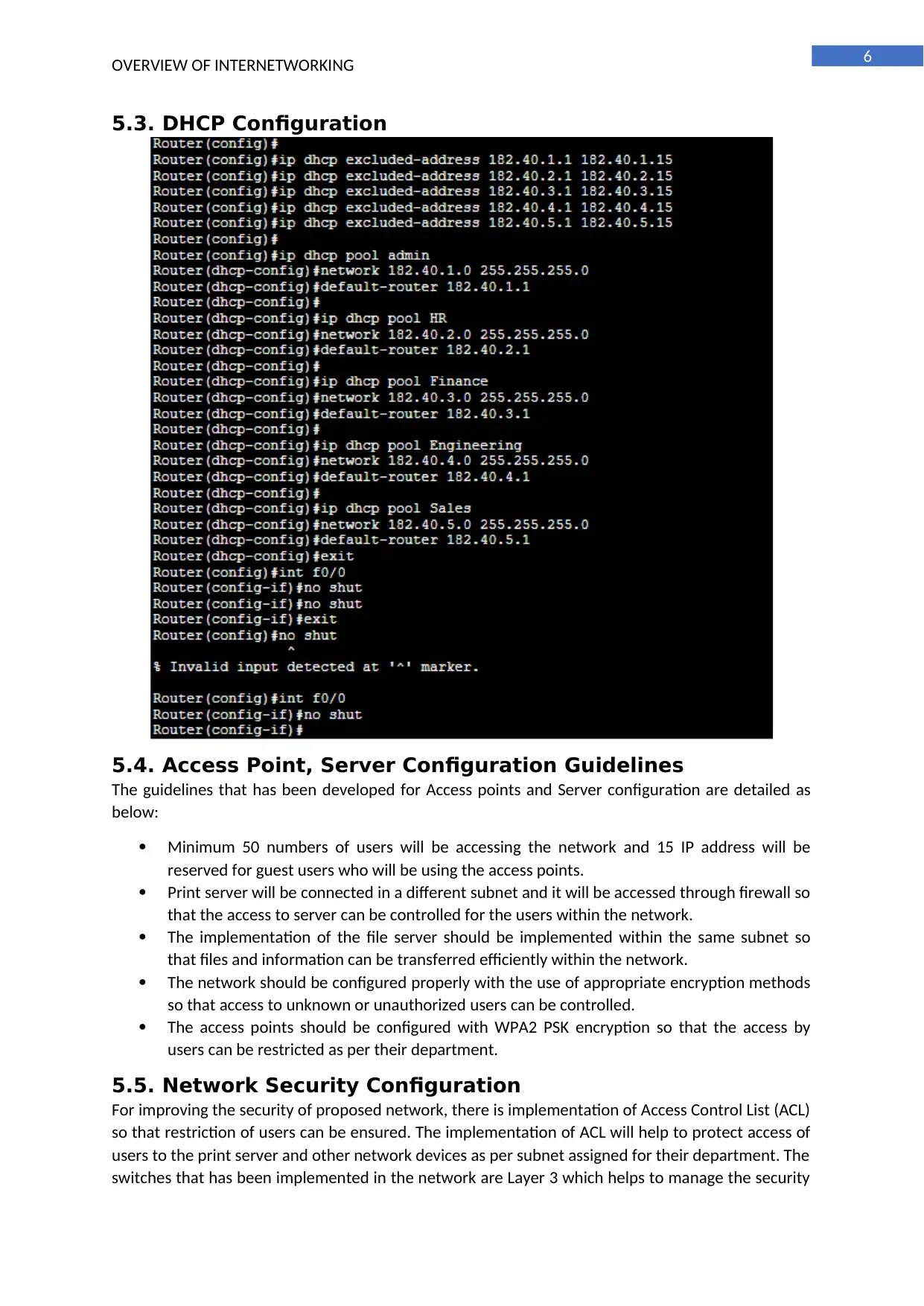
5.3. DHCP Configuration
5.4. Access Point, Server Configuration Guidelines
The guidelines that has been developed for Access points and Server configuration are detailed as
below:
Minimum 50 numbers of users will be accessing the network and 15 IP address will be
reserved for guest users who will be using the access points.
Print server will be connected in a different subnet and it will be accessed through firewall so
that the access to server can be controlled for the users within the network.
The implementation of the file server should be implemented within the same subnet so
that files and information can be transferred efficiently within the network.
The network should be configured properly with the use of appropriate encryption methods
so that access to unknown or unauthorized users can be controlled.
The access points should be configured with WPA2 PSK encryption so that the access by
users can be restricted as per their department.
5.5. Network Security Configuration
For improving the security of proposed network, there is implementation of Access Control List (ACL)
so that restriction of users can be ensured. The implementation of ACL will help to protect access of
users to the print server and other network devices as per subnet assigned for their department. The
switches that has been implemented in the network are Layer 3 which helps to manage the security
OVERVIEW OF INTERNETWORKING
5.3. DHCP Configuration
5.4. Access Point, Server Configuration Guidelines
The guidelines that has been developed for Access points and Server configuration are detailed as
below:
Minimum 50 numbers of users will be accessing the network and 15 IP address will be
reserved for guest users who will be using the access points.
Print server will be connected in a different subnet and it will be accessed through firewall so
that the access to server can be controlled for the users within the network.
The implementation of the file server should be implemented within the same subnet so
that files and information can be transferred efficiently within the network.
The network should be configured properly with the use of appropriate encryption methods
so that access to unknown or unauthorized users can be controlled.
The access points should be configured with WPA2 PSK encryption so that the access by
users can be restricted as per their department.
5.5. Network Security Configuration
For improving the security of proposed network, there is implementation of Access Control List (ACL)
so that restriction of users can be ensured. The implementation of ACL will help to protect access of
users to the print server and other network devices as per subnet assigned for their department. The
switches that has been implemented in the network are Layer 3 which helps to manage the security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
OVERVIEW OF INTERNETWORKING
during flow of information or data packets. ACL (Access Control List) has been implemented in the
network for restricting the access of file and print server according to the subnet for each
department. The image attached below presents the configuration of ACL and the application of it in
VLAN to block the access of different departments as per the rules being set in their subnet.
6. Conclusion
From the overall analysis and design of the network, it can be said that the network prototype being
designed for the firm will help to support the business rules and requirements of the firm. The
detailed analysis of the configuration and services that will be implemented in the network devices
has been presented in this report. The interface of the router “fast Ethernet 0/0” has been divided
into five virtual interfaces that is fa 0/0.1, fa 0/0.02, fa 0/0.03, fa 0/0.4 and fa 0/0.05 for the five
departments in five different subnets. The main router has been configures using DHCP so that IP
addresses can be automatically assigned to the network devices within firm. For configuring the
gateway address of the network, the last IP address has been used that is shown in column
assignable range of the IP address table. The designing the proposed network solution will help the
increase performance and efficiency of the existing network within the firm.
OVERVIEW OF INTERNETWORKING
during flow of information or data packets. ACL (Access Control List) has been implemented in the
network for restricting the access of file and print server according to the subnet for each
department. The image attached below presents the configuration of ACL and the application of it in
VLAN to block the access of different departments as per the rules being set in their subnet.
6. Conclusion
From the overall analysis and design of the network, it can be said that the network prototype being
designed for the firm will help to support the business rules and requirements of the firm. The
detailed analysis of the configuration and services that will be implemented in the network devices
has been presented in this report. The interface of the router “fast Ethernet 0/0” has been divided
into five virtual interfaces that is fa 0/0.1, fa 0/0.02, fa 0/0.03, fa 0/0.4 and fa 0/0.05 for the five
departments in five different subnets. The main router has been configures using DHCP so that IP
addresses can be automatically assigned to the network devices within firm. For configuring the
gateway address of the network, the last IP address has been used that is shown in column
assignable range of the IP address table. The designing the proposed network solution will help the
increase performance and efficiency of the existing network within the firm.

8
OVERVIEW OF INTERNETWORKING
Bibliography
[1.] Agarwal, R., Shukla, P.K. and Goyal, S., 2017. A Practical Approach of Network Simulation.
In Detecting and Mitigating Robotic Cyber Security Risks (pp. 12-27). IGI Global.
[2.] Ashraf, A.W.U., Budka, M. and Musial, K., 2018. NetSim--The framework for complex network
generator. arXiv preprint arXiv:1805.10520.
[3.] Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I., 2017, August. Live Lesson: Netsim:
Network simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}.
[4.] Castro, L.E., Dong, X. and Shaikh, N.I., 2018. Efficient simulation and analysis of mid-sized
networks. Computers & Industrial Engineering, 119, pp.273-288.
[5.] Hsin, W.J., 2015, February. Learning computer networking through illustration. In Proceedings of
the 46th ACM Technical Symposium on Computer Science Education (pp. 515-515). ACM.
[6.] Mahapatra, N., Sahu, N., Nanda, S., Kaur, G. and Prahar, M., 2017. Unit-3 Networking Concepts.
[7.] Nayyar, A. and Singh, R., 2015. A comprehensive review of simulation tools for wireless sensor
networks (WSNs). Journal of Wireless Networking and Communications, 5(1), pp.19-47.
[8.] Singh, G., Cheema, A.K. and Kapoor, N., 2017. Performance Evaluation of Routing Protocol in
Internet of Things using Netsim. International Journal of Advanced Research in Computer
Science, 8(3).
OVERVIEW OF INTERNETWORKING
Bibliography
[1.] Agarwal, R., Shukla, P.K. and Goyal, S., 2017. A Practical Approach of Network Simulation.
In Detecting and Mitigating Robotic Cyber Security Risks (pp. 12-27). IGI Global.
[2.] Ashraf, A.W.U., Budka, M. and Musial, K., 2018. NetSim--The framework for complex network
generator. arXiv preprint arXiv:1805.10520.
[3.] Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I., 2017, August. Live Lesson: Netsim:
Network simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}.
[4.] Castro, L.E., Dong, X. and Shaikh, N.I., 2018. Efficient simulation and analysis of mid-sized
networks. Computers & Industrial Engineering, 119, pp.273-288.
[5.] Hsin, W.J., 2015, February. Learning computer networking through illustration. In Proceedings of
the 46th ACM Technical Symposium on Computer Science Education (pp. 515-515). ACM.
[6.] Mahapatra, N., Sahu, N., Nanda, S., Kaur, G. and Prahar, M., 2017. Unit-3 Networking Concepts.
[7.] Nayyar, A. and Singh, R., 2015. A comprehensive review of simulation tools for wireless sensor
networks (WSNs). Journal of Wireless Networking and Communications, 5(1), pp.19-47.
[8.] Singh, G., Cheema, A.K. and Kapoor, N., 2017. Performance Evaluation of Routing Protocol in
Internet of Things using Netsim. International Journal of Advanced Research in Computer
Science, 8(3).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



