Legality of Hacking: A Critical Discussion
Added on 2022-12-28
11 Pages4644 Words27 Views
Introduction
Criminal activities are the acts made by an individual or group of people which is against the
constitutional laws. In our discussions, we saw that there is a difference between traditional and
computer crime activities. In traditional crimes, it clearly shows that foundations of the criminal
laws are effective since the accused persons have the evidence to testify against them. We found
that there is full evidence of the crime in the crime scene because criminals leave tangible evidence
such as fingerprints, photographs or even there documents like identification cards are left in the
crime scene. It, therefore, make the court to prosecute them since there is evidence against them
which testify there activities and such scenarios are clearly stated in actus reus and men's rea
criminal laws. On the other hand, computer crime will be very difficult for actus reus and men's rea
criminal laws to be applied. Everybody would like to hack and hence there is the usefulness of
understanding the hacking. If in-case there is a problem in the company maybe let say an employee
forgot the password then the most important thing is to crack that password and it can be done with
the authorization hence the is not criminal activity. Hackers in companies can hack the systems and
check if there are any vulnerabilities that can be used by other malicious hackers to gain access into
the company's systems and begin to do malicious activities which will cost the company. Hackers
can also check the network security if there is any hole that malicious hackers can gain access and
still passwords though traffics hence it is important to prevent them before it is too late. Therefore,
hacking can be used in a positive way not always in a negative way (Ross, Baji, and Barnett, 2019
p.237).
Criminal activities are the acts made by an individual or group of people which is against the
constitutional laws. In our discussions, we saw that there is a difference between traditional and
computer crime activities. In traditional crimes, it clearly shows that foundations of the criminal
laws are effective since the accused persons have the evidence to testify against them. We found
that there is full evidence of the crime in the crime scene because criminals leave tangible evidence
such as fingerprints, photographs or even there documents like identification cards are left in the
crime scene. It, therefore, make the court to prosecute them since there is evidence against them
which testify there activities and such scenarios are clearly stated in actus reus and men's rea
criminal laws. On the other hand, computer crime will be very difficult for actus reus and men's rea
criminal laws to be applied. Everybody would like to hack and hence there is the usefulness of
understanding the hacking. If in-case there is a problem in the company maybe let say an employee
forgot the password then the most important thing is to crack that password and it can be done with
the authorization hence the is not criminal activity. Hackers in companies can hack the systems and
check if there are any vulnerabilities that can be used by other malicious hackers to gain access into
the company's systems and begin to do malicious activities which will cost the company. Hackers
can also check the network security if there is any hole that malicious hackers can gain access and
still passwords though traffics hence it is important to prevent them before it is too late. Therefore,
hacking can be used in a positive way not always in a negative way (Ross, Baji, and Barnett, 2019
p.237).

TASK 1
A critical discussion on the legality of hacking
Computer Crime
Computer crime is also known as cyber-crime is a major concern in the technology industry.
Computer crime basically means the misuse of computer skills by committing a crime. Crimes such
as terrorism, hacking, viruses, malicious software, among others are the main crimes found all over.
The computer knowledge gained should be used to bring positive impact in the world but there are
few individuals who want to exploits others hard work by just stealing their properties by use of
such skills. Complains as always been launch about cyber-crime all over and it now high time to
make sure they don't bring negative impact again. Businesses, individual and even government
security is in great danger of this computer crime issue. There are rules and regulations governing
the crimes but because technology is growing so faster then such policies should be changed
regularly to ensure that such crimes are eradicated fully (Ross, Baji, and Barnett, 2019 p.237).
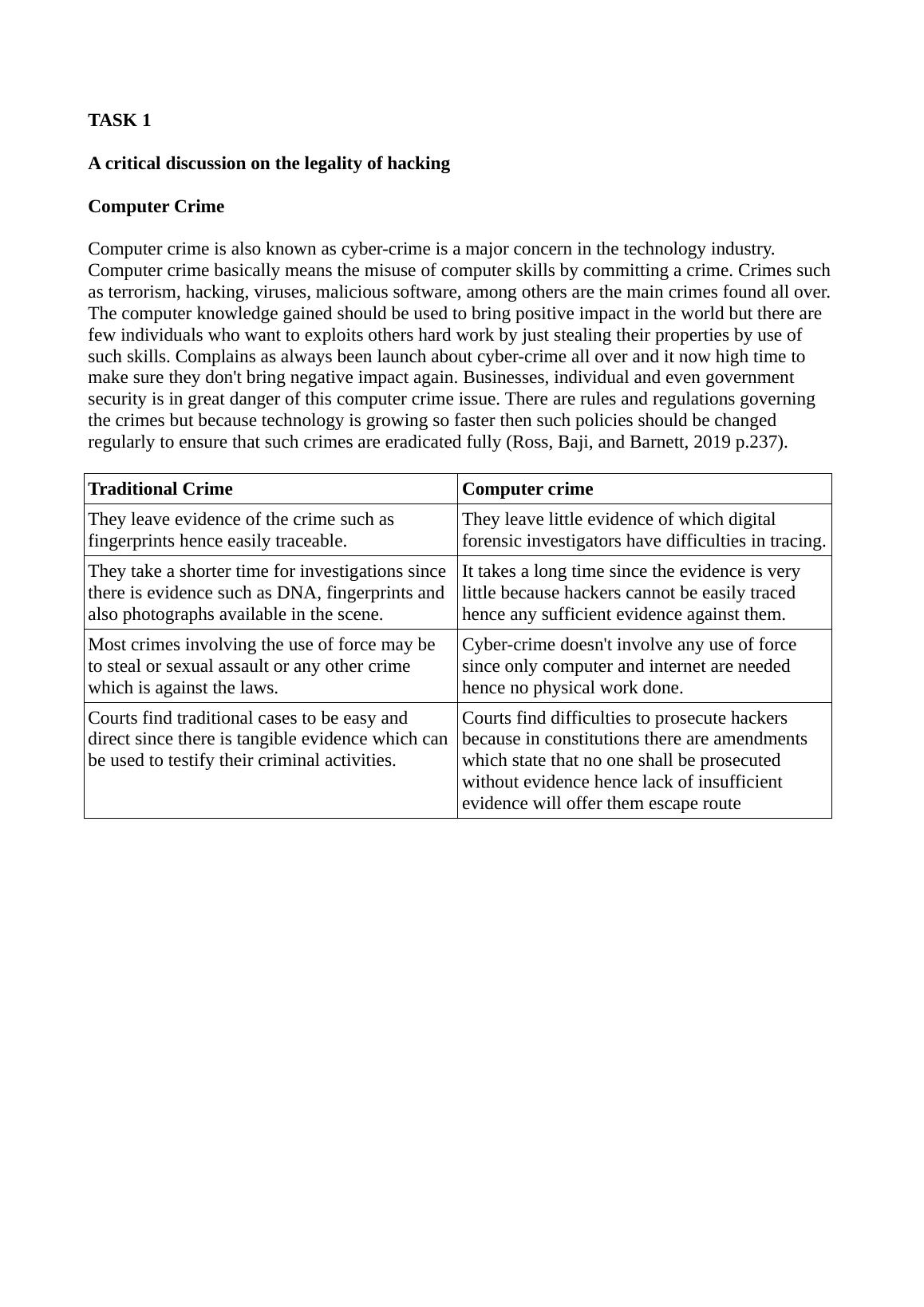
Traditional Crime Computer crime
They leave evidence of the crime such as
fingerprints hence easily traceable.
They leave little evidence of which digital
forensic investigators have difficulties in tracing.
They take a shorter time for investigations since
there is evidence such as DNA, fingerprints and
also photographs available in the scene.
It takes a long time since the evidence is very
little because hackers cannot be easily traced
hence any sufficient evidence against them.
Most crimes involving the use of force may be
to steal or sexual assault or any other crime
which is against the laws.
Cyber-crime doesn't involve any use of force
since only computer and internet are needed
hence no physical work done.
Courts find traditional cases to be easy and
direct since there is tangible evidence which can
be used to testify their criminal activities.
Courts find difficulties to prosecute hackers
because in constitutions there are amendments
which state that no one shall be prosecuted
without evidence hence lack of insufficient
evidence will offer them escape route
A critical discussion on the legality of hacking
Computer Crime
Computer crime is also known as cyber-crime is a major concern in the technology industry.
Computer crime basically means the misuse of computer skills by committing a crime. Crimes such
as terrorism, hacking, viruses, malicious software, among others are the main crimes found all over.
The computer knowledge gained should be used to bring positive impact in the world but there are
few individuals who want to exploits others hard work by just stealing their properties by use of
such skills. Complains as always been launch about cyber-crime all over and it now high time to
make sure they don't bring negative impact again. Businesses, individual and even government
security is in great danger of this computer crime issue. There are rules and regulations governing
the crimes but because technology is growing so faster then such policies should be changed
regularly to ensure that such crimes are eradicated fully (Ross, Baji, and Barnett, 2019 p.237).
Traditional Crime Computer crime
They leave evidence of the crime such as
fingerprints hence easily traceable.
They leave little evidence of which digital
forensic investigators have difficulties in tracing.
They take a shorter time for investigations since
there is evidence such as DNA, fingerprints and
also photographs available in the scene.
It takes a long time since the evidence is very
little because hackers cannot be easily traced
hence any sufficient evidence against them.
Most crimes involving the use of force may be
to steal or sexual assault or any other crime
which is against the laws.
Cyber-crime doesn't involve any use of force
since only computer and internet are needed
hence no physical work done.
Courts find traditional cases to be easy and
direct since there is tangible evidence which can
be used to testify their criminal activities.
Courts find difficulties to prosecute hackers
because in constitutions there are amendments
which state that no one shall be prosecuted
without evidence hence lack of insufficient
evidence will offer them escape route
Criminal Activities
Actus reus and men's rea are the foundations of criminal laws. It is, however, important to judge
criminal activities basing on the guidelines of these foundations.
Criminal activities are the acts made by an individual or group of people which is against the
constitutional laws. In our discussions, we saw that there is a difference between traditional and
computer crime activities. In traditional crimes, it clearly shows that foundations of the criminal
laws are effective since the accused persons have the evidence to testify against them. We found
that there is full evidence of the crime in the crime scene because criminals leave tangible evidence
such as fingerprints, photographs or even there documents like identification cards are left in the
crime scene. It, therefore, makes the court to prosecute them since there is evidence against them
which testify there activities and such scenarios are clearly stated in actus reus and men's rea
criminal laws. On the other hand, computer crime will be very difficult for actus reus and men's rea
criminal laws to be applied. First, there are no tangle evidence because hackers will before there
activities and leave the crime scene without any evidence because the delete and destroy all the
evidence because technology can be done everything according to the will of the person provided
that they have sufficient skills to do them (Li, Furlong, Yorio, and Portnoff, 2019).
Hacking
Hacking is an unauthorized intrusion into a network or computer systems. Hacking has been always
misunderstood by many to be a criminal activity. Hackers are the professionals who practice
hacking and they can be white hat, back hat, and red hat hackers. White hat hackers are
professionals who operate hacking legally for the benefit of the business or organizations. They
normally hack computer systems and networks with permissions to check the vulnerabilities which
might be available and hence they have to solve them before malicious hackers use such
vulnerabilities to exploit the systems. This is a legal activity and every organization's and business
must have a group of hackers to always survey their infrastructure before they are destroyed. Black
hat is professional hackers who use their skills to hack systems and exploit them for their personal
interests. They are bad guys who run businesses and an organization's systems. Red hat hackers are
the professionals who use their skills either for benefits of organization's or business or for
malicious intentions. They are middle guys. Hackers activities are to crack the password,
vulnerability scanning, packet sniffing, spoofing attack among other activities. Such activities will
always depend on the intentions of the hackers hence hacking activities are not always used
maliciously (Kachhwaha and Purohit, 2019 pp. 41-51).
Hacking is not a criminal activity
Hacking is not a criminal activity since it is always advisable for the managers and CEO's of the
companies to learn to hack. Everybody would like to hack and hence there is the usefulness of
understanding the hacking. If in-case there is a problem in the company maybe let say an employee
forgot the password then the most important thing is to crack that password and it can be done with
the authorization hence the is not criminal activity. Hackers in companies can hack the systems and
check if there are any vulnerabilities that can be used by other malicious hackers to gain access into
the company's systems and begin to do malicious activities which will cost the company. Hackers
can also check the network security if there is any hole that malicious hackers can gain access and
still passwords though traffics hence it is important to prevent them before it is too late. Therefore,
hacking can be used in a positive way not always in a negative way (Ross, Baji, and Barnett, 2019
p.237).
Actus reus and men's rea are the foundations of criminal laws. It is, however, important to judge
criminal activities basing on the guidelines of these foundations.
Criminal activities are the acts made by an individual or group of people which is against the
constitutional laws. In our discussions, we saw that there is a difference between traditional and
computer crime activities. In traditional crimes, it clearly shows that foundations of the criminal
laws are effective since the accused persons have the evidence to testify against them. We found
that there is full evidence of the crime in the crime scene because criminals leave tangible evidence
such as fingerprints, photographs or even there documents like identification cards are left in the
crime scene. It, therefore, makes the court to prosecute them since there is evidence against them
which testify there activities and such scenarios are clearly stated in actus reus and men's rea
criminal laws. On the other hand, computer crime will be very difficult for actus reus and men's rea
criminal laws to be applied. First, there are no tangle evidence because hackers will before there
activities and leave the crime scene without any evidence because the delete and destroy all the
evidence because technology can be done everything according to the will of the person provided
that they have sufficient skills to do them (Li, Furlong, Yorio, and Portnoff, 2019).
Hacking
Hacking is an unauthorized intrusion into a network or computer systems. Hacking has been always
misunderstood by many to be a criminal activity. Hackers are the professionals who practice
hacking and they can be white hat, back hat, and red hat hackers. White hat hackers are
professionals who operate hacking legally for the benefit of the business or organizations. They
normally hack computer systems and networks with permissions to check the vulnerabilities which
might be available and hence they have to solve them before malicious hackers use such
vulnerabilities to exploit the systems. This is a legal activity and every organization's and business
must have a group of hackers to always survey their infrastructure before they are destroyed. Black
hat is professional hackers who use their skills to hack systems and exploit them for their personal
interests. They are bad guys who run businesses and an organization's systems. Red hat hackers are
the professionals who use their skills either for benefits of organization's or business or for
malicious intentions. They are middle guys. Hackers activities are to crack the password,
vulnerability scanning, packet sniffing, spoofing attack among other activities. Such activities will
always depend on the intentions of the hackers hence hacking activities are not always used
maliciously (Kachhwaha and Purohit, 2019 pp. 41-51).
Hacking is not a criminal activity
Hacking is not a criminal activity since it is always advisable for the managers and CEO's of the
companies to learn to hack. Everybody would like to hack and hence there is the usefulness of
understanding the hacking. If in-case there is a problem in the company maybe let say an employee
forgot the password then the most important thing is to crack that password and it can be done with
the authorization hence the is not criminal activity. Hackers in companies can hack the systems and
check if there are any vulnerabilities that can be used by other malicious hackers to gain access into
the company's systems and begin to do malicious activities which will cost the company. Hackers
can also check the network security if there is any hole that malicious hackers can gain access and
still passwords though traffics hence it is important to prevent them before it is too late. Therefore,
hacking can be used in a positive way not always in a negative way (Ross, Baji, and Barnett, 2019
p.237).

TASK 2
Penetration Testing (PenTest)
Penetration testing is a scenario where vulnerabilities are investigated to have full information on
how the systems can be compromised in-case of any attacker either legitimate or malicious attack. It
mainly involves the exploitation of the networks, firewalls, and computers among other devices and
systems. This will lead to checking the vulnerabilities that are available (Lasser, Xm Cyber Ltd and
XM Ltd, 2019).
PenTest Methodology
PenTest have different methods which might be categorized on the basis of knowledge of the target
or position of the penetration tester. The following are among such methods:
1. Black Box, Gray Box, and White Box:
White box PenTest is basically when the penetration tester is given the full knowledge of the target
systems before the attack is initiated. Such information includes IP addresses, code samples, among
other needed information. On the other hand, the black box is a scenario where the attacker doesn't
have any knowledge of the target hence the attacker will have to do more to gain the necessary
information. Finally, gray box is a situation where the tester can have information that is publicly
available about the target hence this little information can help attacker launch their attacks, such
information are URLs, IP address, etc. This method of boxes will determine the attacker's approach
and also the techniques to use (Li, Furlong, Yorio, and Portnoff, 2019).
2. Internal and External PenTest
PenTest can be done either inside or outside the network. External PenTest is an approach that is
initiated from the outside the network and is attackers uses so many techniques to launch the attack
since they don't understand the network structure. Internal PenTest, on the other hand, is an attacker
that is done by the internal person who understands the network structure and all the systems.
Hence internal attacker will have more impact as compared to external (Kachhwaha and Purohit,
2019 pp. 41-51).
3. In-house and Third party PenTest
Company may decide to conduct penetration testing by use of in-house security team or hire a third-
party organization to conduct such test hence they are called in-house PenTest and third-party
PenTest respectively (Lasser, Xm Cyber Ltd and XM Ltd, 2019).
4. Blind and Double-Blind PenTest
Blind PenTest is a penetration test where the tester doesn't give any information except only
organizations name. Therefore, all the work will be done by the tester just like the authorized
attacker performs there work. This will be time-consuming but the results are always close to the
practical work. A double-blind test is a scenario where the test is done when the security experts
don't know anything but the senior staffs have the information when the test should be carried. This
kind of test will always alert and make sure that the security team aware when the attack is real
attacks can occur (Holsapple, Smoot, and Evert, 2019).
Penetration Testing (PenTest)
Penetration testing is a scenario where vulnerabilities are investigated to have full information on
how the systems can be compromised in-case of any attacker either legitimate or malicious attack. It
mainly involves the exploitation of the networks, firewalls, and computers among other devices and
systems. This will lead to checking the vulnerabilities that are available (Lasser, Xm Cyber Ltd and
XM Ltd, 2019).
PenTest Methodology
PenTest have different methods which might be categorized on the basis of knowledge of the target
or position of the penetration tester. The following are among such methods:
1. Black Box, Gray Box, and White Box:
White box PenTest is basically when the penetration tester is given the full knowledge of the target
systems before the attack is initiated. Such information includes IP addresses, code samples, among
other needed information. On the other hand, the black box is a scenario where the attacker doesn't
have any knowledge of the target hence the attacker will have to do more to gain the necessary
information. Finally, gray box is a situation where the tester can have information that is publicly
available about the target hence this little information can help attacker launch their attacks, such
information are URLs, IP address, etc. This method of boxes will determine the attacker's approach
and also the techniques to use (Li, Furlong, Yorio, and Portnoff, 2019).
2. Internal and External PenTest
PenTest can be done either inside or outside the network. External PenTest is an approach that is
initiated from the outside the network and is attackers uses so many techniques to launch the attack
since they don't understand the network structure. Internal PenTest, on the other hand, is an attacker
that is done by the internal person who understands the network structure and all the systems.
Hence internal attacker will have more impact as compared to external (Kachhwaha and Purohit,
2019 pp. 41-51).
3. In-house and Third party PenTest
Company may decide to conduct penetration testing by use of in-house security team or hire a third-
party organization to conduct such test hence they are called in-house PenTest and third-party
PenTest respectively (Lasser, Xm Cyber Ltd and XM Ltd, 2019).
4. Blind and Double-Blind PenTest
Blind PenTest is a penetration test where the tester doesn't give any information except only
organizations name. Therefore, all the work will be done by the tester just like the authorized
attacker performs there work. This will be time-consuming but the results are always close to the
practical work. A double-blind test is a scenario where the test is done when the security experts
don't know anything but the senior staffs have the information when the test should be carried. This
kind of test will always alert and make sure that the security team aware when the attack is real
attacks can occur (Holsapple, Smoot, and Evert, 2019).

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Computer Crime: Definition, Correlation, and Criminal Activitylg...
|6
|1263
|88
