Intelligent Management: IT Threats, Analysis, and Solutions
VerifiedAdded on 2020/05/11
|14
|3737
|236
Report
AI Summary
This report provides a comprehensive overview of IT threats in the modern digital landscape, focusing on critical issues such as the loss of Personally Identifiable Information (PII), network degradation, insider attacks, ransomware, and theft of Intellectual Property (IP). It delves into the potential consequences of each threat, including legal ramifications, reputational damage, and financial losses. The report explores various protection strategies, including encryption, endpoint security, data loss prevention, and strict policy compliance. It examines the causes of network degradation, such as propagation delays, malware, and denial-of-service attacks, and offers solutions to mitigate these issues. Furthermore, the report highlights the dangers of insider attacks and IP theft, providing insights into how organizations can fortify their security measures to prevent these threats. The analysis includes a discussion of ransomware, its impact, and preventive measures. This report emphasizes the importance of proactive security measures to safeguard organizational assets and maintain customer trust, offering practical solutions for intelligent management of IT security challenges. The report is contributed by a student to Desklib, a platform providing AI-based study tools.

INTELLIGENT MANAGEMENT
I. Introduction to IT Threats:
In the modern virtual world, one of the major branches of criminal activity is cybercrime. Along with
that, due to the increased dependence of people on machines and virtual storage, there is always a
threat of loss of information, degradation of network and attack of hackers or viruses, all of which
can severely hamper the functions of an organization and invite both legal costs and damage of the
reputation of the organization. Thus, it is necessary for organizations to educate themselves on the
kinds of threat that could attack a network or system and make sure that the threats could be
neutralized before it can damage or hinder the networking procedures of the organization (Berger &
Heath, 2007).
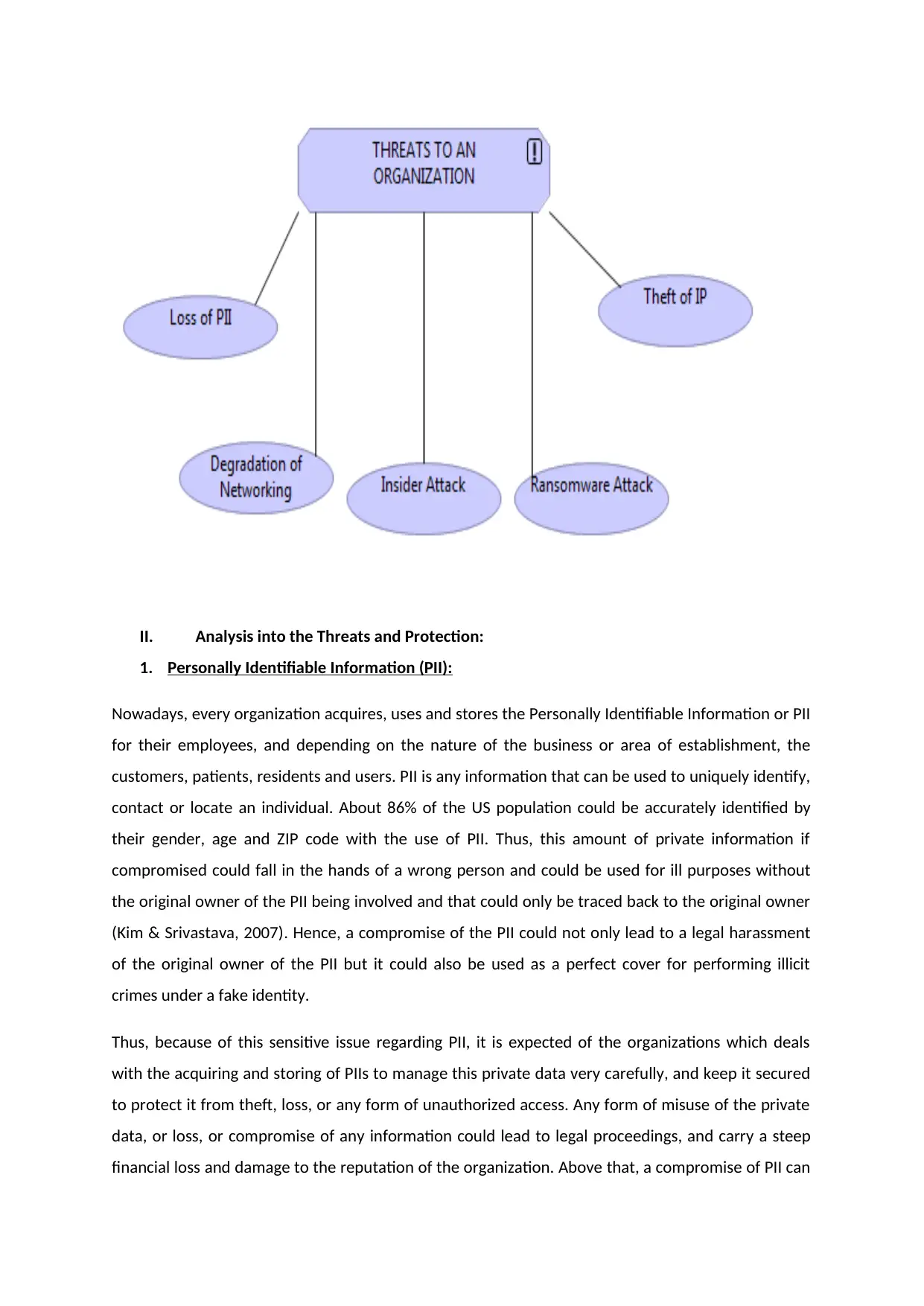
The key threats to an organization are:
Loss of PII: The loss of Personally Identifiable Information which is stored in the organization with a
trust that it will keep it safe contains all the useful information of the owner of the PII that could be
used against him if it is ever compromised. Hence, it is necessary for the organization to keep PII
secure so that it does not damage its reputation or loses the trust of customers and employees due
to negligence and poor security.
Degradation of Networking: Since IT companies run on networking, it is important to keep a track of
the hardware that connects the machines and makes the networking possible. Along with that, it is
also necessary for the software to be updated and to keep a check whether foreign traffic or the
inclusion of hackers is not involving in the degradation of the networking procedures in the
organization (Duan, Gu & Whinston, 2008). Viruses and spywares could also lead to the degradation
of networking and it is necessary to prevent the attack of either of these for the security for the
transfer of the networking packets.
Insider Attack: Insider attack is one of the worst threats that could take place in an organization in
which a trusted employee, or former employee could plant some form of malicious device into the
system that could harm the company or steal sensitive information from the company and use it for
unauthorized purposes for personal gain. Proper security analysis and protected access should be
made to make sure that any former employee could not have access to a data and for that the
I. Introduction to IT Threats:
In the modern virtual world, one of the major branches of criminal activity is cybercrime. Along with
that, due to the increased dependence of people on machines and virtual storage, there is always a
threat of loss of information, degradation of network and attack of hackers or viruses, all of which
can severely hamper the functions of an organization and invite both legal costs and damage of the
reputation of the organization. Thus, it is necessary for organizations to educate themselves on the
kinds of threat that could attack a network or system and make sure that the threats could be
neutralized before it can damage or hinder the networking procedures of the organization (Berger &
Heath, 2007).
The key threats to an organization are:
Loss of PII: The loss of Personally Identifiable Information which is stored in the organization with a
trust that it will keep it safe contains all the useful information of the owner of the PII that could be
used against him if it is ever compromised. Hence, it is necessary for the organization to keep PII
secure so that it does not damage its reputation or loses the trust of customers and employees due
to negligence and poor security.
Degradation of Networking: Since IT companies run on networking, it is important to keep a track of
the hardware that connects the machines and makes the networking possible. Along with that, it is
also necessary for the software to be updated and to keep a check whether foreign traffic or the
inclusion of hackers is not involving in the degradation of the networking procedures in the
organization (Duan, Gu & Whinston, 2008). Viruses and spywares could also lead to the degradation
of networking and it is necessary to prevent the attack of either of these for the security for the
transfer of the networking packets.
Insider Attack: Insider attack is one of the worst threats that could take place in an organization in
which a trusted employee, or former employee could plant some form of malicious device into the
system that could harm the company or steal sensitive information from the company and use it for
unauthorized purposes for personal gain. Proper security analysis and protected access should be
made to make sure that any former employee could not have access to a data and for that the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

protection or the security pattern of an organization should be flexible, that is, it could be
reconstructed and changed when need be.
Ransomware: Ransomware is malicious software which locks the systems and threatens to publish
the victim’s data unless a certain amount of ransom as stated is not paid. The Ransomware has
attacked systems as recently as 2017 and has come into the limelight due to its ability to stay under
the radar of normal antiviruses. The Ransomware software has been known to wreak havoc in any
system and targets IT organization for its purpose. Using advanced malware techniques called
cryptoviral extortions, the software encrypts the victim’s files thereby preventing access to the files
and then demands a ransom for decrypting the files which on receiving they either decrypt or leave
without response (Fisher, 2010). For such a malicious software, it is necessary to keep the virus
information updated and for advanced education into the ransomware software to prevent it from
ever attacking the IT system of an organization.
Theft of IP: The theft of Intellectual Property is a high rising cybercrime where theintellectual
property, that is, the plans, ideas and the creative innovation designs of an organization is stolen
from their databases and used by people that do not have access, permission or ownership of the
said intellectual property (Jansen, Zhang, Sobel & Chowdury, 2009). Hackers are generally guilty of
stealing intellectual property from the organization and selling it in the market or to competitors at
higher prices.
reconstructed and changed when need be.
Ransomware: Ransomware is malicious software which locks the systems and threatens to publish
the victim’s data unless a certain amount of ransom as stated is not paid. The Ransomware has
attacked systems as recently as 2017 and has come into the limelight due to its ability to stay under
the radar of normal antiviruses. The Ransomware software has been known to wreak havoc in any
system and targets IT organization for its purpose. Using advanced malware techniques called
cryptoviral extortions, the software encrypts the victim’s files thereby preventing access to the files
and then demands a ransom for decrypting the files which on receiving they either decrypt or leave
without response (Fisher, 2010). For such a malicious software, it is necessary to keep the virus
information updated and for advanced education into the ransomware software to prevent it from
ever attacking the IT system of an organization.
Theft of IP: The theft of Intellectual Property is a high rising cybercrime where theintellectual
property, that is, the plans, ideas and the creative innovation designs of an organization is stolen
from their databases and used by people that do not have access, permission or ownership of the
said intellectual property (Jansen, Zhang, Sobel & Chowdury, 2009). Hackers are generally guilty of
stealing intellectual property from the organization and selling it in the market or to competitors at
higher prices.
II. Analysis into the Threats and Protection:
1. Personally Identifiable Information (PII):
Nowadays, every organization acquires, uses and stores the Personally Identifiable Information or PII
for their employees, and depending on the nature of the business or area of establishment, the
customers, patients, residents and users. PII is any information that can be used to uniquely identify,
contact or locate an individual. About 86% of the US population could be accurately identified by
their gender, age and ZIP code with the use of PII. Thus, this amount of private information if
compromised could fall in the hands of a wrong person and could be used for ill purposes without
the original owner of the PII being involved and that could only be traced back to the original owner
(Kim & Srivastava, 2007). Hence, a compromise of the PII could not only lead to a legal harassment
of the original owner of the PII but it could also be used as a perfect cover for performing illicit
crimes under a fake identity.
Thus, because of this sensitive issue regarding PII, it is expected of the organizations which deals
with the acquiring and storing of PIIs to manage this private data very carefully, and keep it secured
to protect it from theft, loss, or any form of unauthorized access. Any form of misuse of the private
data, or loss, or compromise of any information could lead to legal proceedings, and carry a steep
financial loss and damage to the reputation of the organization. Above that, a compromise of PII can
1. Personally Identifiable Information (PII):
Nowadays, every organization acquires, uses and stores the Personally Identifiable Information or PII
for their employees, and depending on the nature of the business or area of establishment, the
customers, patients, residents and users. PII is any information that can be used to uniquely identify,
contact or locate an individual. About 86% of the US population could be accurately identified by
their gender, age and ZIP code with the use of PII. Thus, this amount of private information if
compromised could fall in the hands of a wrong person and could be used for ill purposes without
the original owner of the PII being involved and that could only be traced back to the original owner
(Kim & Srivastava, 2007). Hence, a compromise of the PII could not only lead to a legal harassment
of the original owner of the PII but it could also be used as a perfect cover for performing illicit
crimes under a fake identity.
Thus, because of this sensitive issue regarding PII, it is expected of the organizations which deals
with the acquiring and storing of PIIs to manage this private data very carefully, and keep it secured
to protect it from theft, loss, or any form of unauthorized access. Any form of misuse of the private
data, or loss, or compromise of any information could lead to legal proceedings, and carry a steep
financial loss and damage to the reputation of the organization. Above that, a compromise of PII can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
also result in the loss of customer trust, employee dissatisfaction and attrition and clean-up costs
after the breach. As a result, the necessity to keep PII safe and secure from any form of compromise
should be one of the top priorities of an organization (Kim, Le, Lauw, Lim, Liu & Srivastava, 2008).
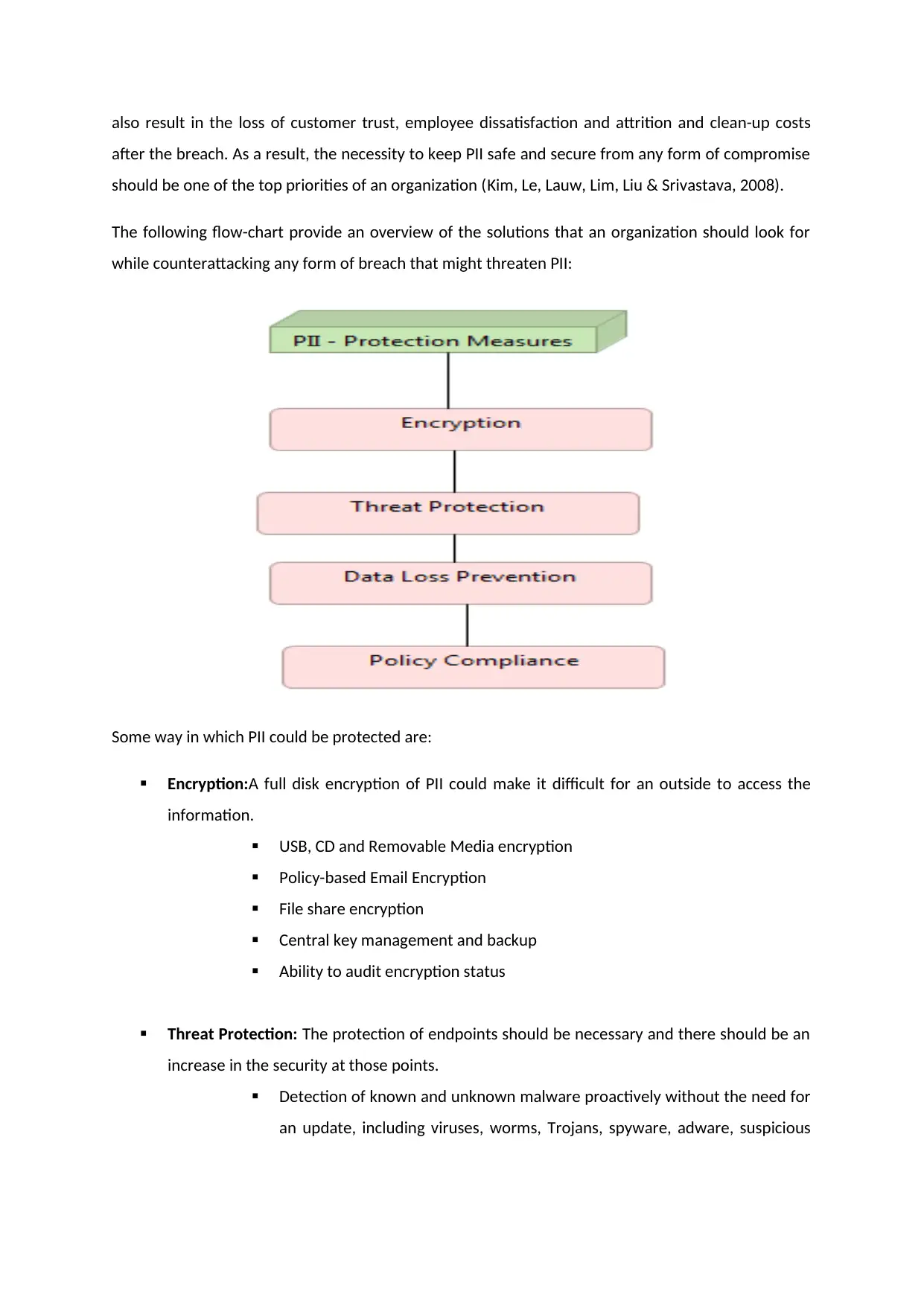
The following flow-chart provide an overview of the solutions that an organization should look for
while counterattacking any form of breach that might threaten PII:
Some way in which PII could be protected are:
Encryption:A full disk encryption of PII could make it difficult for an outside to access the
information.
USB, CD and Removable Media encryption
Policy-based Email Encryption
File share encryption
Central key management and backup
Ability to audit encryption status
Threat Protection: The protection of endpoints should be necessary and there should be an
increase in the security at those points.
Detection of known and unknown malware proactively without the need for
an update, including viruses, worms, Trojans, spyware, adware, suspicious
after the breach. As a result, the necessity to keep PII safe and secure from any form of compromise
should be one of the top priorities of an organization (Kim, Le, Lauw, Lim, Liu & Srivastava, 2008).
The following flow-chart provide an overview of the solutions that an organization should look for
while counterattacking any form of breach that might threaten PII:
Some way in which PII could be protected are:
Encryption:A full disk encryption of PII could make it difficult for an outside to access the
information.
USB, CD and Removable Media encryption
Policy-based Email Encryption
File share encryption
Central key management and backup
Ability to audit encryption status
Threat Protection: The protection of endpoints should be necessary and there should be an
increase in the security at those points.
Detection of known and unknown malware proactively without the need for
an update, including viruses, worms, Trojans, spyware, adware, suspicious
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

files, suspicious behaviour, potentially unwanted applications (PUAs) and
more
Antivirus, firewall, application and device control in a single agent
Defending all platforms (Windows, Mac, Linux, UNIX)
Data Loss Prevention: Prevention of data loss by scanning repeatedly the storage places of
data and keeping the data stored in several other as backup that should be maintained
properly (Leitner & Grechenig, 2008).
File matching rule: Specified action should be taken based on name or type
of file a user is attempting to access or transfer
Content rule: Contains one or more data definitions and specifies the action
taken if a user attempts to transfer data that matches those definitions
Policy Compliance: There should be a strict policy of the organization which should be
followed while any kind of data is stored in the organization’s storage system. Lists should be
maintained and the frequent synchronization and updates should take place to keep the
security system active and able to tackle with increasing and modern attackers and their
tactics (Leitner & Grechenig, 2009).
2. Degradation of Network:
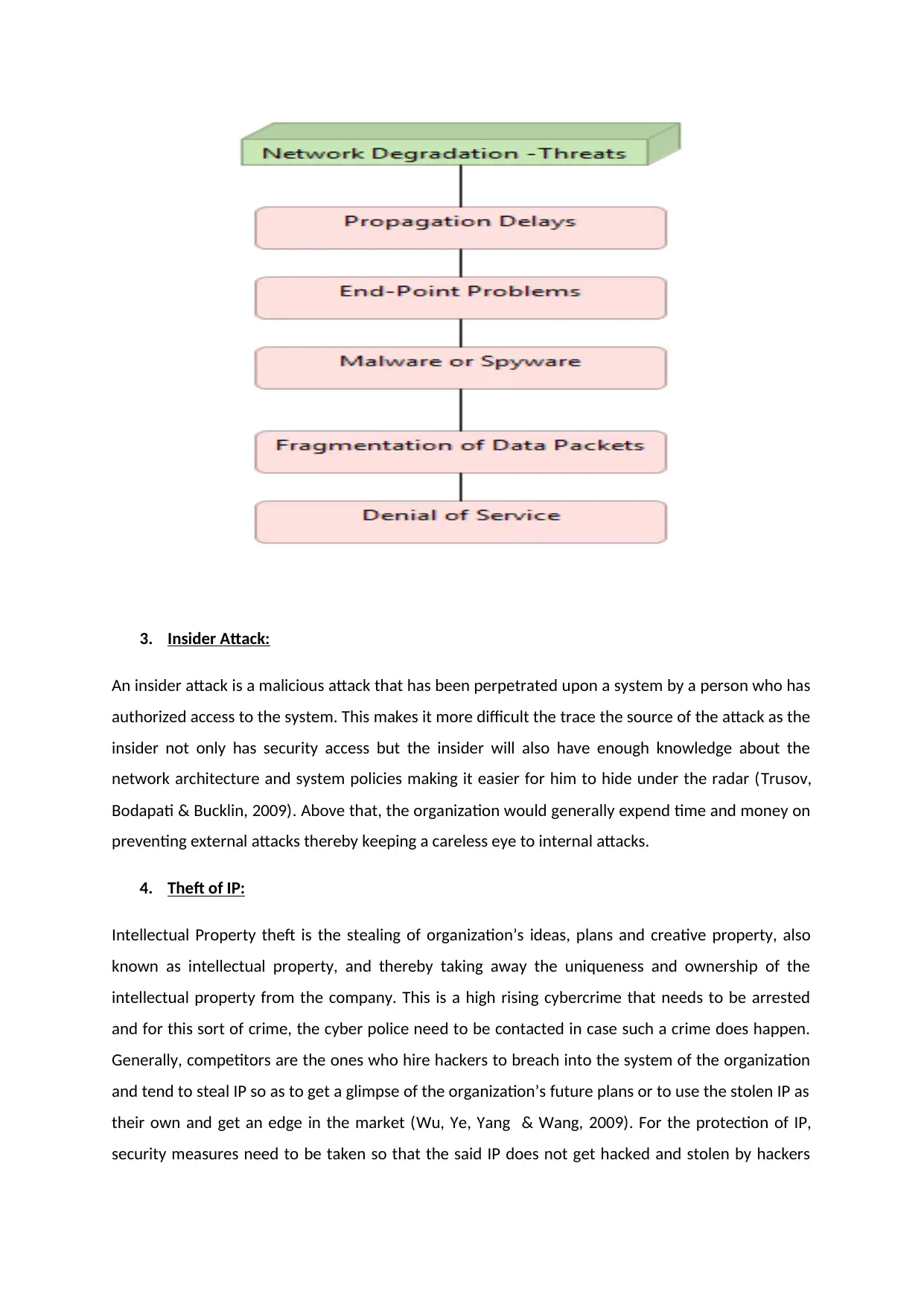
Network Degradation refers to the decrease in the connectivity of a network or the response time of
response speed of a network. This severely hampers the working of an organization and it could lead
to packets of data being lost in transmission which will only slow down the function of the
organization and enable outsiders to steal packets and information (Lorenzo, Constantinides, Geurts
& Gómez, 2007). Diagnosing network performances and tracing back the reason for the slowing
down of network performance is necessary and for that an education into the types of network
performances should be conducted.
The types of threats that presented in a network are:
Propagation Delays: Propagation delays can generally occur when there is a problem with
routing which results in a delay in the transportation of data from one point of the network
to the other. A proper analysis of the causes of delays could prevent this problem.
more
Antivirus, firewall, application and device control in a single agent
Defending all platforms (Windows, Mac, Linux, UNIX)
Data Loss Prevention: Prevention of data loss by scanning repeatedly the storage places of
data and keeping the data stored in several other as backup that should be maintained
properly (Leitner & Grechenig, 2008).
File matching rule: Specified action should be taken based on name or type
of file a user is attempting to access or transfer
Content rule: Contains one or more data definitions and specifies the action
taken if a user attempts to transfer data that matches those definitions
Policy Compliance: There should be a strict policy of the organization which should be
followed while any kind of data is stored in the organization’s storage system. Lists should be
maintained and the frequent synchronization and updates should take place to keep the
security system active and able to tackle with increasing and modern attackers and their
tactics (Leitner & Grechenig, 2009).
2. Degradation of Network:
Network Degradation refers to the decrease in the connectivity of a network or the response time of
response speed of a network. This severely hampers the working of an organization and it could lead
to packets of data being lost in transmission which will only slow down the function of the
organization and enable outsiders to steal packets and information (Lorenzo, Constantinides, Geurts
& Gómez, 2007). Diagnosing network performances and tracing back the reason for the slowing
down of network performance is necessary and for that an education into the types of network
performances should be conducted.
The types of threats that presented in a network are:
Propagation Delays: Propagation delays can generally occur when there is a problem with
routing which results in a delay in the transportation of data from one point of the network
to the other. A proper analysis of the causes of delays could prevent this problem.

End-Point Problems: This problem tends to occur at the end points that is the terminals or
work station which are data destinations and they may experience delays due to insufficient
memory or processing capacity. Engineers and developers should consider if there is a fault
in the system and try to repair it.
Malware or Spyware: The breach of malware or spyware into the system can severely lower
the speed of the transfer of data and can infect the packets of data that are moving along in
the network traffic. For this problem, a proper antivirus or security measures should be
taken to prevent breach of malware or spyware into the system.
Fragmentation of the Data Packets: A lot of fragmentation of the data packets can lead to
the slowing down of network and the free transfer of data could be hampered because of
increases fragmentation (Palmer, 2008). This depresses the functionality of the network at
work. Developers should make sure that the data packets are fragmented reasonably so that
too much of network degradation does not take place.
Denial of Service: Various kinds of outside hacking can lead to the complete denial of service
if the hacker has gained control over the system, thus leading to the termination of work on
that data unless the hacker is weeded out of the system. Steps should be taken to increase
the security of the system to prevent hackers from entering into the network (Stephen &
Toubia, 2009). For this, penetration testers should be hired to detect weaknesses in the
system and thereby, strengthen security.
work station which are data destinations and they may experience delays due to insufficient
memory or processing capacity. Engineers and developers should consider if there is a fault
in the system and try to repair it.
Malware or Spyware: The breach of malware or spyware into the system can severely lower
the speed of the transfer of data and can infect the packets of data that are moving along in
the network traffic. For this problem, a proper antivirus or security measures should be
taken to prevent breach of malware or spyware into the system.
Fragmentation of the Data Packets: A lot of fragmentation of the data packets can lead to
the slowing down of network and the free transfer of data could be hampered because of
increases fragmentation (Palmer, 2008). This depresses the functionality of the network at
work. Developers should make sure that the data packets are fragmented reasonably so that
too much of network degradation does not take place.
Denial of Service: Various kinds of outside hacking can lead to the complete denial of service
if the hacker has gained control over the system, thus leading to the termination of work on
that data unless the hacker is weeded out of the system. Steps should be taken to increase
the security of the system to prevent hackers from entering into the network (Stephen &
Toubia, 2009). For this, penetration testers should be hired to detect weaknesses in the
system and thereby, strengthen security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3. Insider Attack:
An insider attack is a malicious attack that has been perpetrated upon a system by a person who has
authorized access to the system. This makes it more difficult the trace the source of the attack as the
insider not only has security access but the insider will also have enough knowledge about the
network architecture and system policies making it easier for him to hide under the radar (Trusov,
Bodapati & Bucklin, 2009). Above that, the organization would generally expend time and money on
preventing external attacks thereby keeping a careless eye to internal attacks.
4. Theft of IP:
Intellectual Property theft is the stealing of organization’s ideas, plans and creative property, also
known as intellectual property, and thereby taking away the uniqueness and ownership of the
intellectual property from the company. This is a high rising cybercrime that needs to be arrested
and for this sort of crime, the cyber police need to be contacted in case such a crime does happen.
Generally, competitors are the ones who hire hackers to breach into the system of the organization
and tend to steal IP so as to get a glimpse of the organization’s future plans or to use the stolen IP as
their own and get an edge in the market (Wu, Ye, Yang & Wang, 2009). For the protection of IP,
security measures need to be taken so that the said IP does not get hacked and stolen by hackers
An insider attack is a malicious attack that has been perpetrated upon a system by a person who has
authorized access to the system. This makes it more difficult the trace the source of the attack as the
insider not only has security access but the insider will also have enough knowledge about the
network architecture and system policies making it easier for him to hide under the radar (Trusov,
Bodapati & Bucklin, 2009). Above that, the organization would generally expend time and money on
preventing external attacks thereby keeping a careless eye to internal attacks.
4. Theft of IP:
Intellectual Property theft is the stealing of organization’s ideas, plans and creative property, also
known as intellectual property, and thereby taking away the uniqueness and ownership of the
intellectual property from the company. This is a high rising cybercrime that needs to be arrested
and for this sort of crime, the cyber police need to be contacted in case such a crime does happen.
Generally, competitors are the ones who hire hackers to breach into the system of the organization
and tend to steal IP so as to get a glimpse of the organization’s future plans or to use the stolen IP as
their own and get an edge in the market (Wu, Ye, Yang & Wang, 2009). For the protection of IP,
security measures need to be taken so that the said IP does not get hacked and stolen by hackers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and so proper firewalls against malware and spyware needs to be put into place. The ownership of
the intellectual property should not be compromised for the future benefit of any organization.
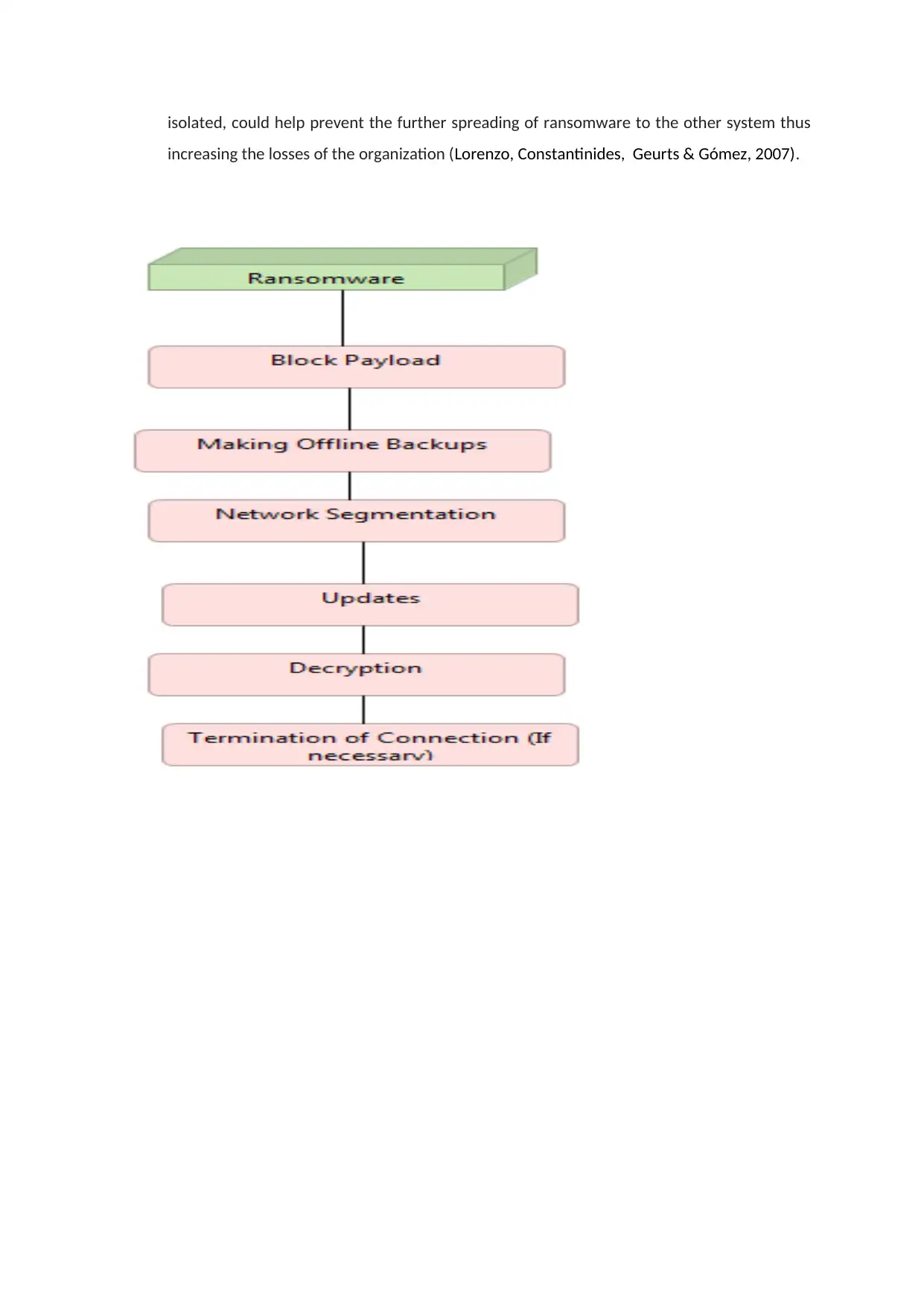
5. Ransomware Software:
Ransomware software is a malicious programme that breaches into the software of a computer,
takes control of the files, encrypts the file to prevent user access and demands ransom in exchange
of decrypting the said files, or demands ransom so that the private information of the user is not
published publicly (Yang, Dia, Cheng & Lin, 2006). The Ukraine attack of 2017 and other previously
documented attacks have brought ransomware into limelight and it has been charged of invisible
notoriety.
Ransomware could be prevented from affecting the system by:
Block Payload: Software should be installed which could block known payloads that could
transmit the malware into the system, thereby preventing the breach of ransomware into
the system.
Updates: Repeated updates of virus definitions to include new forms of malware and their
varieties should be made to mitigate any vulnerability present in the system.
Offline Backups: Offline backups should be kept of the necessary files in external storage
drives or devices, that is, locations that do not have any access to any network and thus will
say safe from the attach of ransomware.
Network Segmentation: Network Segmentation is the act of splitting the network of a
computer into different subnetworks which are called network segments. This helps in
boosting performance and in increased security.
Decryption: Since Ransomware works by encrypting the data of a specific system, it is
necessary for software to try and decrypt the encrypted data thereby reversing the attack of
ransomware.
Termination of Connection: This is the optional step that needs to be taken if the
ransomware had spread out in a specific system beyond redemption and as a result the
entire infected system needs to be plugged out or to be completely disconnected from the
network so as to prevent the spreading of the malware into other systems. when the
ransomware has spread out beyond repair in one system a complete termination of that
system from the network, excluding it from the working of the organization and keeping it
the intellectual property should not be compromised for the future benefit of any organization.
5. Ransomware Software:
Ransomware software is a malicious programme that breaches into the software of a computer,
takes control of the files, encrypts the file to prevent user access and demands ransom in exchange
of decrypting the said files, or demands ransom so that the private information of the user is not
published publicly (Yang, Dia, Cheng & Lin, 2006). The Ukraine attack of 2017 and other previously
documented attacks have brought ransomware into limelight and it has been charged of invisible
notoriety.
Ransomware could be prevented from affecting the system by:
Block Payload: Software should be installed which could block known payloads that could
transmit the malware into the system, thereby preventing the breach of ransomware into
the system.
Updates: Repeated updates of virus definitions to include new forms of malware and their
varieties should be made to mitigate any vulnerability present in the system.
Offline Backups: Offline backups should be kept of the necessary files in external storage
drives or devices, that is, locations that do not have any access to any network and thus will
say safe from the attach of ransomware.
Network Segmentation: Network Segmentation is the act of splitting the network of a
computer into different subnetworks which are called network segments. This helps in
boosting performance and in increased security.
Decryption: Since Ransomware works by encrypting the data of a specific system, it is
necessary for software to try and decrypt the encrypted data thereby reversing the attack of
ransomware.
Termination of Connection: This is the optional step that needs to be taken if the
ransomware had spread out in a specific system beyond redemption and as a result the
entire infected system needs to be plugged out or to be completely disconnected from the
network so as to prevent the spreading of the malware into other systems. when the
ransomware has spread out beyond repair in one system a complete termination of that
system from the network, excluding it from the working of the organization and keeping it
isolated, could help prevent the further spreading of ransomware to the other system thus
increasing the losses of the organization (Lorenzo, Constantinides, Geurts & Gómez, 2007).
increasing the losses of the organization (Lorenzo, Constantinides, Geurts & Gómez, 2007).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

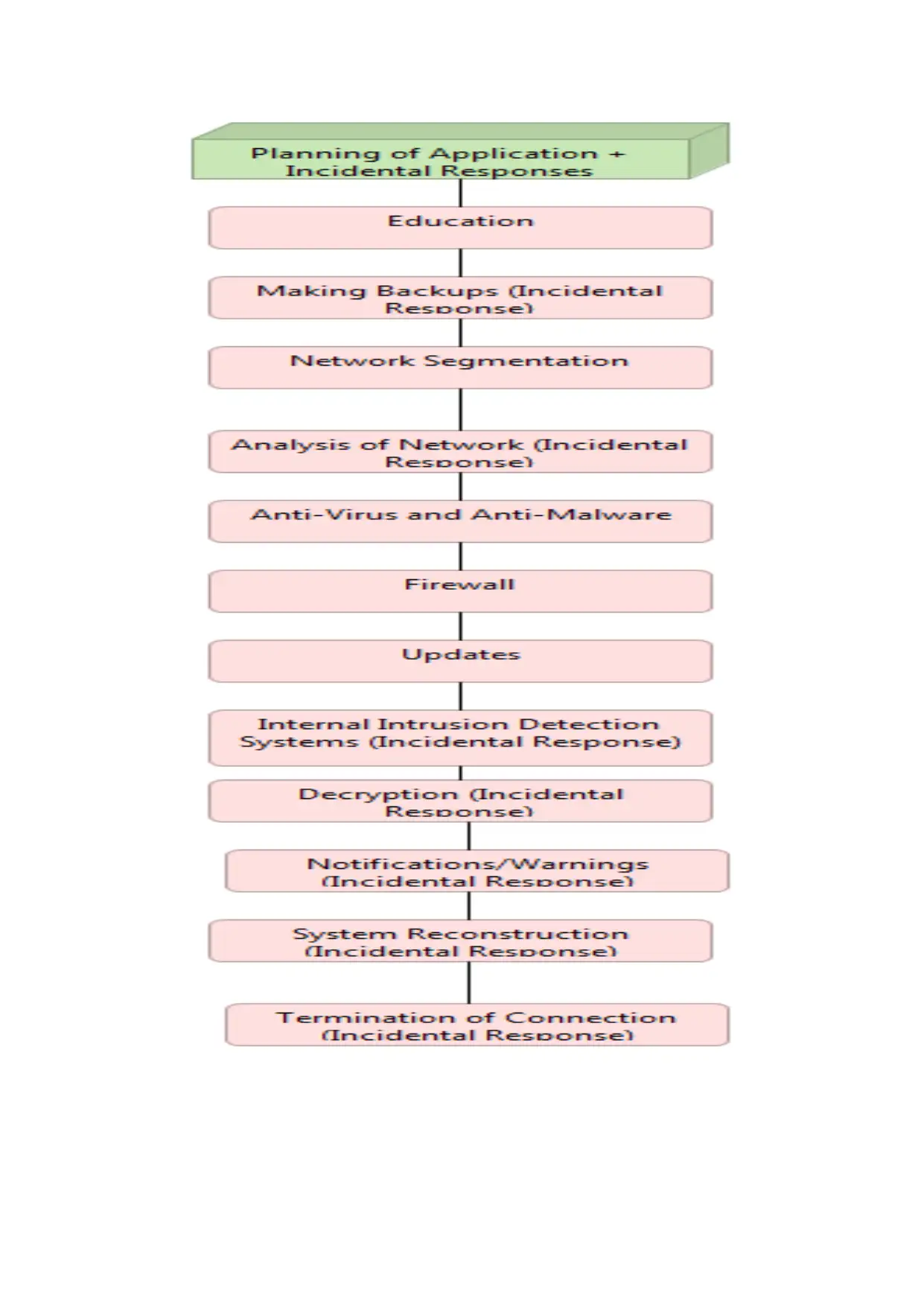
III. Necessary inclusions for designing the Security Application:
Hence, from the above examination of the kinds of threat that an IT company could face and the
cybercrimes that are rampant in the world of today, it is necessary to include certain aspects into the
application product so that it could successfully keep the threat in check, keeping updated with the
latest virus definitions and keep all the information of a company secured (Palmer, 2008). This
should also have an incident response time so that it can either notify and act accordingly and
instantly when a cyber incident occurs.
Education: The first necessity of the application should be to educate the user of its uses and
how it works.
Making Backups – A security application should create offline backups in external storage
drives or devices that do not have any access to the internet or network during a sudden
cyber incident.
Network Segmentation – Splitting the network into segments increases performance and
security and so the application should be able to maintain segments of network.
Analysis of Network: The application could be able to analyse and detect internal problems
or the source of cyber incidents in the network and notify them to the authorities
(Xinogalos, Psannis and Sifaleras, 2012).
Anti-Virus and Anti- Malware – The application should have properties of anti-virus and
anti-malware to prevent it from entering or working in the network.
Firewall – A strong firewall should be put in place so that any form of threat is immediately
blocked from entering.
Updates –Virus definitions should be updated all the time to keep up with the times.
Internal Intrusion Detection Systems –Installing Internal Intrusion Detection Systems to
detect any form of internal intrusion and create an instant incident notification and reset if
necessary.
Decryption –The application should have the capability to decrypt any form of encrypted
files that had been hacked or infected by ransomware.
Notifications/Warning –Any threat of breach by hackers or outsiders should trigger a
warning or notification mechanism so that the authorities are notified of the external
interference (Stephen & Toubia, 2009).
System Reconstruction – The application should be intelligent enough to request password
changes or system reconstruction where necessary and if permitted by the admin as a
response to a cyber incident.
Hence, from the above examination of the kinds of threat that an IT company could face and the
cybercrimes that are rampant in the world of today, it is necessary to include certain aspects into the
application product so that it could successfully keep the threat in check, keeping updated with the
latest virus definitions and keep all the information of a company secured (Palmer, 2008). This
should also have an incident response time so that it can either notify and act accordingly and
instantly when a cyber incident occurs.
Education: The first necessity of the application should be to educate the user of its uses and
how it works.
Making Backups – A security application should create offline backups in external storage
drives or devices that do not have any access to the internet or network during a sudden
cyber incident.
Network Segmentation – Splitting the network into segments increases performance and
security and so the application should be able to maintain segments of network.
Analysis of Network: The application could be able to analyse and detect internal problems
or the source of cyber incidents in the network and notify them to the authorities
(Xinogalos, Psannis and Sifaleras, 2012).
Anti-Virus and Anti- Malware – The application should have properties of anti-virus and
anti-malware to prevent it from entering or working in the network.
Firewall – A strong firewall should be put in place so that any form of threat is immediately
blocked from entering.
Updates –Virus definitions should be updated all the time to keep up with the times.
Internal Intrusion Detection Systems –Installing Internal Intrusion Detection Systems to
detect any form of internal intrusion and create an instant incident notification and reset if
necessary.
Decryption –The application should have the capability to decrypt any form of encrypted
files that had been hacked or infected by ransomware.
Notifications/Warning –Any threat of breach by hackers or outsiders should trigger a
warning or notification mechanism so that the authorities are notified of the external
interference (Stephen & Toubia, 2009).
System Reconstruction – The application should be intelligent enough to request password
changes or system reconstruction where necessary and if permitted by the admin as a
response to a cyber incident.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Termination of Connection –The application should be able to isolate a system from the
network if it has been infected so that the infection does not spread, however, after
notifying and seeking permission from the admin or the authorities as a reaction to a cyber
incident.
network if it has been infected so that the infection does not spread, however, after
notifying and seeking permission from the admin or the authorities as a reaction to a cyber
incident.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





