Comparison of Metasploit and Hydra: Ethical Hacking Tools
9 Pages779 Words70 Views
Added on 2023-01-23
About This Document
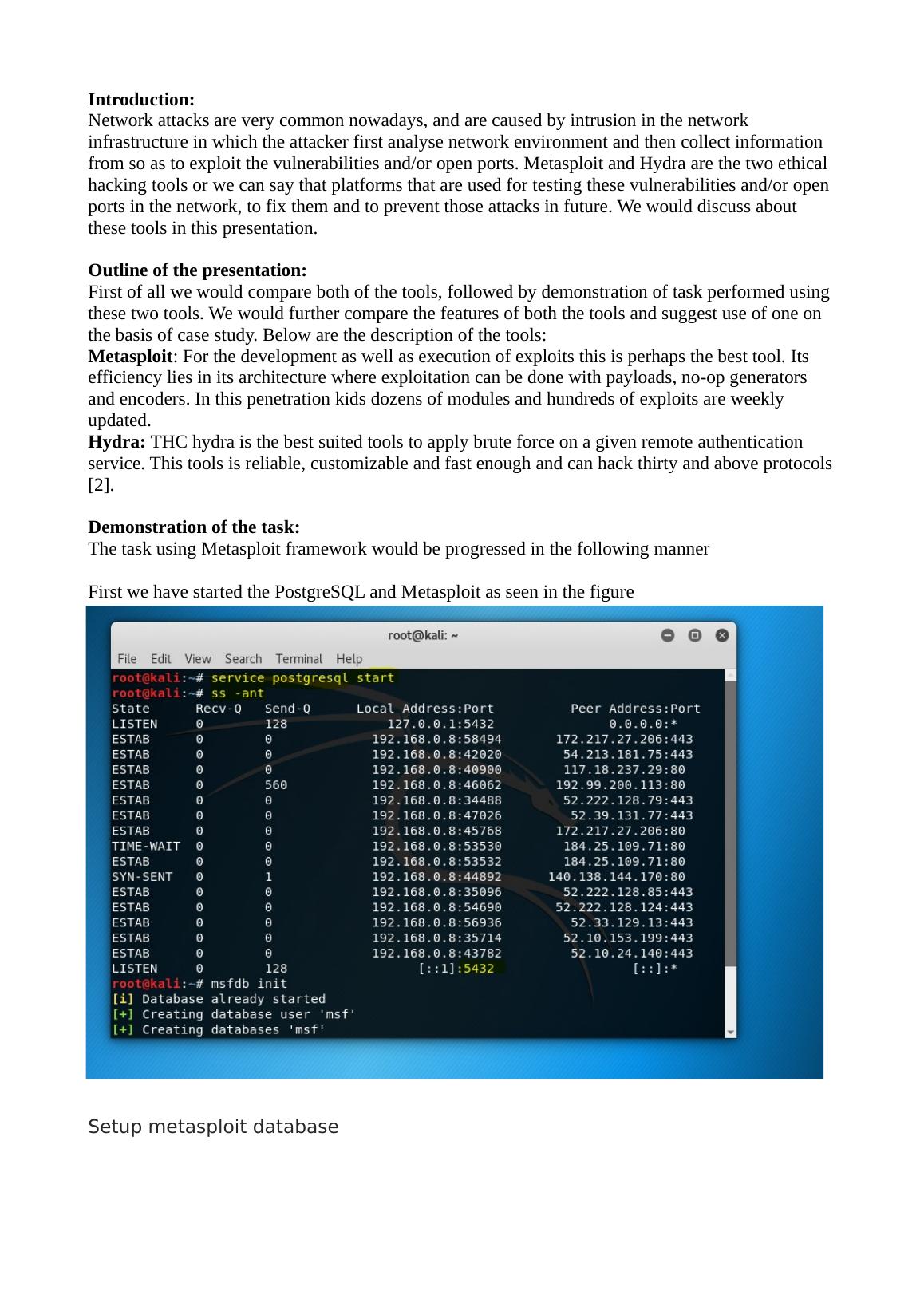
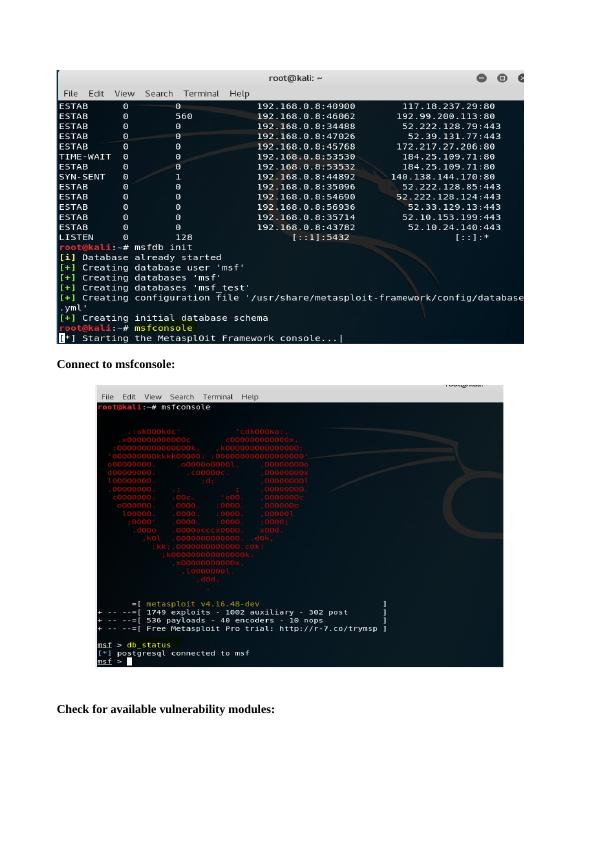
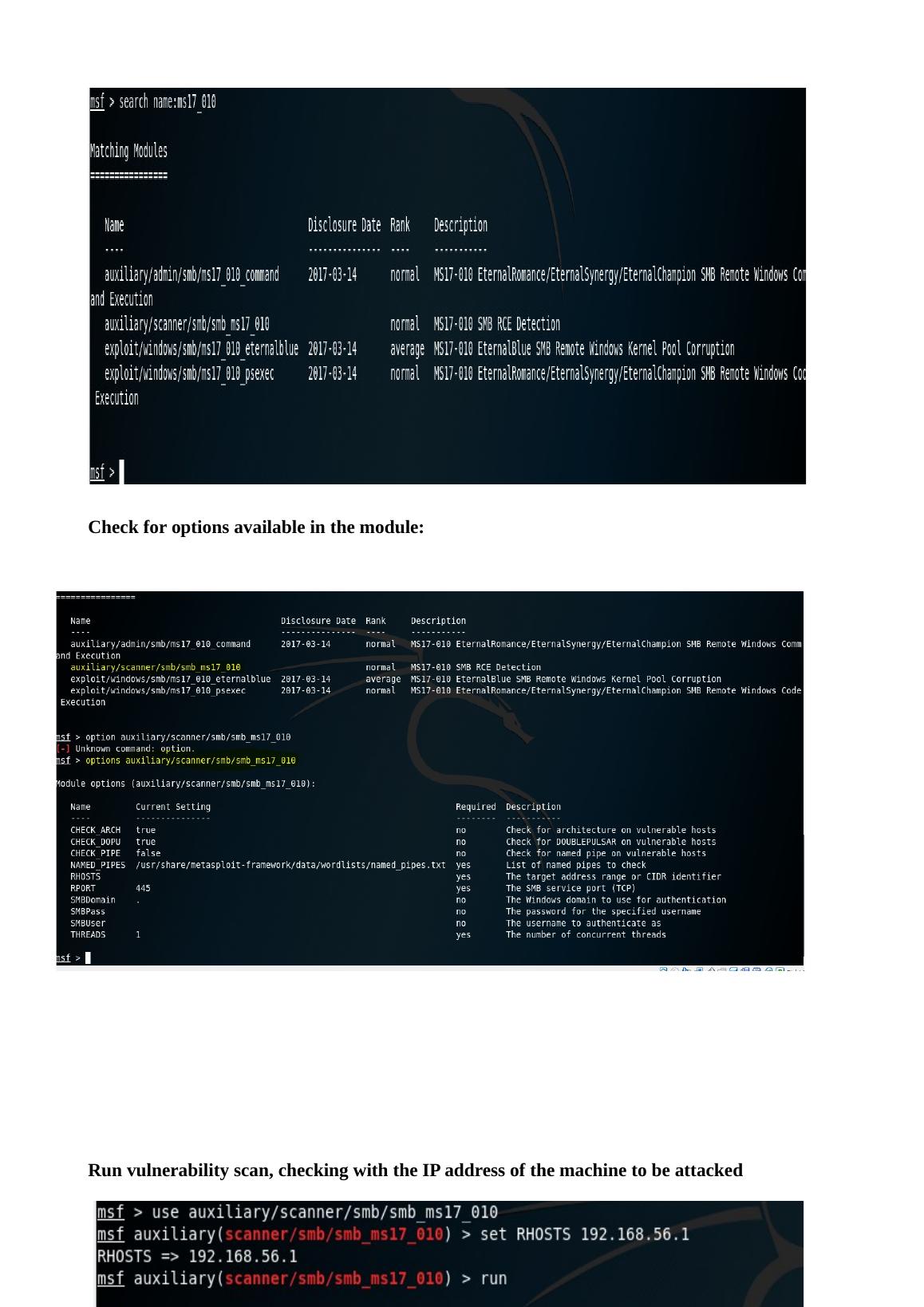
This presentation compares Metasploit and Hydra, two ethical hacking tools used for testing network vulnerabilities. It discusses their features, demonstrates tasks performed using these tools, and provides an analysis of their uses. The conclusion highlights the importance of understanding these tools to defend against network attacks.
Comparison of Metasploit and Hydra: Ethical Hacking Tools
Added on 2023-01-23
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
After attending the meeting
|7
|853
|15
Vulnerability Testing for E-commerce Website using Metasploit
|10
|2032
|115
Hydra: A Comprehensive Guide on Brute Forcing Tool
|13
|2351
|187
Password Testing And Breaking Programs
|2
|655
|19
Metasploit Framework Assignment PDF
|26
|1193
|325
Password Cracking Tools: THC Hydra, John the Ripper, RainbowCrack, and Ophcrack
|16
|2242
|86