Administrative Services Department Report 2022
The assignment requires conducting a risk assessment for the Department of Administrative Services (DAS) in an Australian State Government as they transition to a shared services approach.
16 Pages4808 Words23 Views
Added on 2022-09-25
Administrative Services Department Report 2022
The assignment requires conducting a risk assessment for the Department of Administrative Services (DAS) in an Australian State Government as they transition to a shared services approach.
Added on 2022-09-25
ShareRelated Documents
Introduction:
The aim of the report is to evaluate the scenario of the Department of
Administrative Services (DAS) who is responsible for providing many services to
the governmental departments of the Australia. The services provided by them
generally consist of the management over the HR and personnel employee level
authorities. They also contract tendering management which includes contractor
management and their payroll of all the employees including procurement. The
services provided by them are controlled from the data centers of the
Department of Administrative Services.
According to recent changes of the policy declared by the Australian
Government, they are forced to move to a new approach known as the system of
Shared Services. The approach demonstrates about the system that centralizes
numerous services as a whole under The Whole of Government. The result of this
system will force the agencies operating the services for their own users will
have to shift and merge all their information and data under the DAS for
validating the system under the centralized DAS database (Yang et al., 2015).
The government policy that has been declared also imposes the new
approach of the CLOUD FIRST process which is process of updating and getting
services of the software. The DAS has decided to acquire the changes with the
help of the implementation of the SAAS solution which they will buy from a US
based company (Rai, Sahoo & Mehfuz, 2013). The aim of the report is to state
the development and the utilization of the SaaS technology for the management
of the HR and personnel.
The SaaS solutions or the Software as a service solution is the type of the
model which deals with the application of software distribution where a third
party provider is responsible for hosting the applications and making them
available for the clients in an online webpage. Saas is generally one of the most
vital category or characteristics of the Cloud computing technology which the
Australian government has imposed to imply on the system s of the DAS (Safari,
Safari & Hasanzadeh, 2015).
The aim of the report is to discuss the Security and the threats of the data
and information contained in the in house HR database. The existing threats and
the risks in the privacy of the data is also mitigated and analyzed in the report
(Mainka et al., 2014). The security, privacy of employee data along with the
Digital Identity Issues are also discussed in the report.
1. Security of Employee Data
The aim of the report is to evaluate the scenario of the Department of
Administrative Services (DAS) who is responsible for providing many services to
the governmental departments of the Australia. The services provided by them
generally consist of the management over the HR and personnel employee level
authorities. They also contract tendering management which includes contractor
management and their payroll of all the employees including procurement. The
services provided by them are controlled from the data centers of the
Department of Administrative Services.
According to recent changes of the policy declared by the Australian
Government, they are forced to move to a new approach known as the system of
Shared Services. The approach demonstrates about the system that centralizes
numerous services as a whole under The Whole of Government. The result of this
system will force the agencies operating the services for their own users will
have to shift and merge all their information and data under the DAS for
validating the system under the centralized DAS database (Yang et al., 2015).
The government policy that has been declared also imposes the new
approach of the CLOUD FIRST process which is process of updating and getting
services of the software. The DAS has decided to acquire the changes with the
help of the implementation of the SAAS solution which they will buy from a US
based company (Rai, Sahoo & Mehfuz, 2013). The aim of the report is to state
the development and the utilization of the SaaS technology for the management
of the HR and personnel.
The SaaS solutions or the Software as a service solution is the type of the
model which deals with the application of software distribution where a third
party provider is responsible for hosting the applications and making them
available for the clients in an online webpage. Saas is generally one of the most
vital category or characteristics of the Cloud computing technology which the
Australian government has imposed to imply on the system s of the DAS (Safari,
Safari & Hasanzadeh, 2015).
The aim of the report is to discuss the Security and the threats of the data
and information contained in the in house HR database. The existing threats and
the risks in the privacy of the data is also mitigated and analyzed in the report
(Mainka et al., 2014). The security, privacy of employee data along with the
Digital Identity Issues are also discussed in the report.
1. Security of Employee Data

S.No Security
Threat/Risk
Description
Likelihoo
d
Impact
Priority Preventive Actions Contingency
Plans
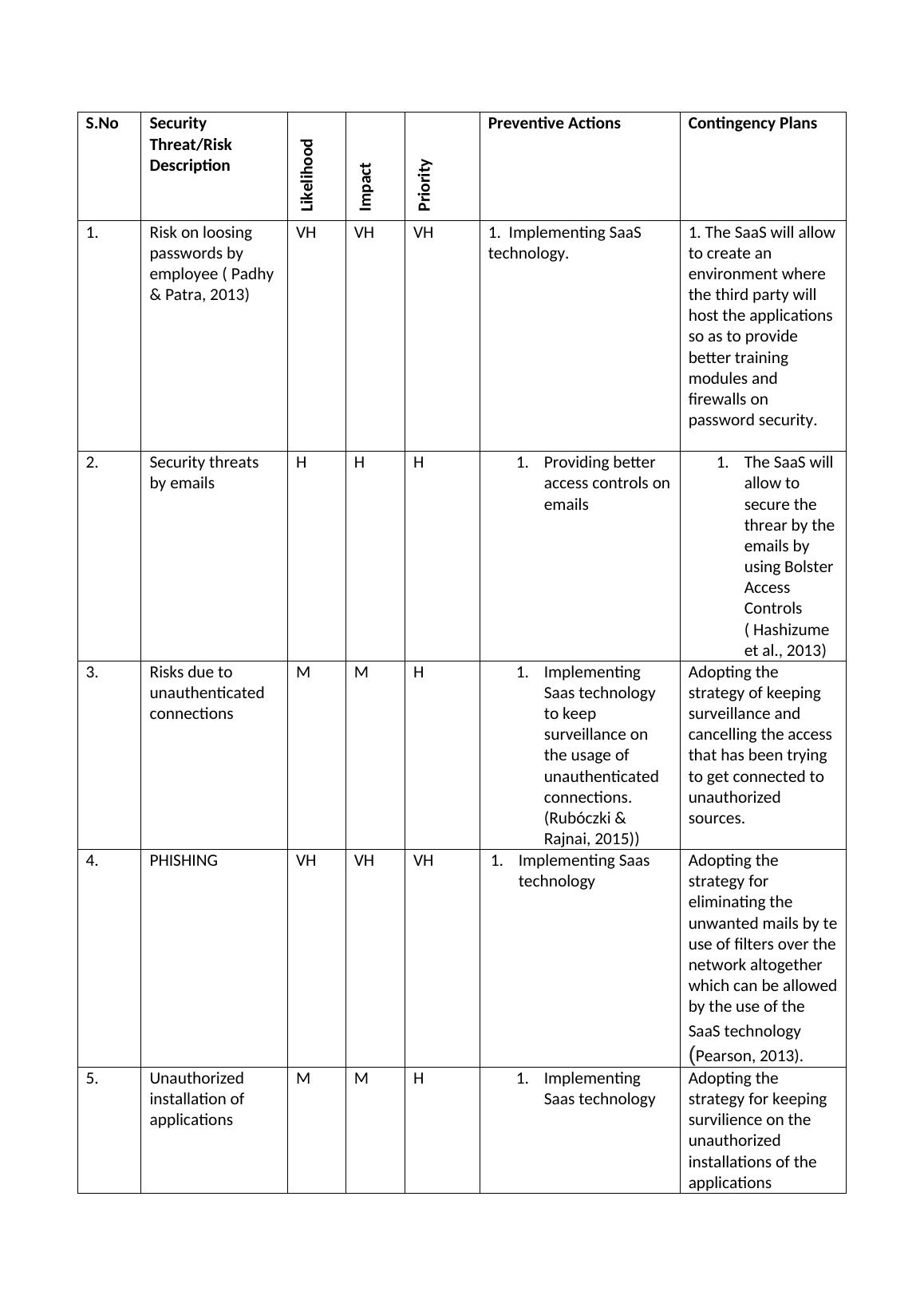
1. Risk on loosing
passwords by
employee
( Padhy &
Patra, 2013)
VH VH VH 1. Implementing
SaaS technology.
1. The SaaS will
allow to create
an environment
where the third
party will host
the applications
so as to provide
better training
modules and
firewalls on
password
security.
2. Security
threats by
emails
H H H 1. Providing
better access
controls on
emails
1. The SaaS
will allow
to secure
the threar
by the
emails by
using
Bolster
Access
Controls
( Hashizu
me et al.,
2013)
3. Risks due to
unauthenticat
ed
connections
M M H 1. Implementing
Saas
technology to
keep
surveillance
on the usage
of
unauthenticat
ed
connections.
(Rubóczki &
Rajnai, 2015))
Adopting the
strategy of
keeping
surveillance and
cancelling the
access that has
been trying to
get connected to
unauthorized
sources.
4. PHISHING VH VH VH 1. Implementing
Saas technology
Adopting the
strategy for
eliminating the
unwanted mails
by te use of
filters over the
network
altogether which
can be allowed
by the use of the
Threat/Risk
Description
Likelihoo
d
Impact
Priority Preventive Actions Contingency
Plans
1. Risk on loosing
passwords by
employee
( Padhy &
Patra, 2013)
VH VH VH 1. Implementing
SaaS technology.
1. The SaaS will
allow to create
an environment
where the third
party will host
the applications
so as to provide
better training
modules and
firewalls on
password
security.
2. Security
threats by
emails
H H H 1. Providing
better access
controls on
emails
1. The SaaS
will allow
to secure
the threar
by the
emails by
using
Bolster
Access
Controls
( Hashizu
me et al.,
2013)
3. Risks due to
unauthenticat
ed
connections
M M H 1. Implementing
Saas
technology to
keep
surveillance
on the usage
of
unauthenticat
ed
connections.
(Rubóczki &
Rajnai, 2015))
Adopting the
strategy of
keeping
surveillance and
cancelling the
access that has
been trying to
get connected to
unauthorized
sources.
4. PHISHING VH VH VH 1. Implementing
Saas technology
Adopting the
strategy for
eliminating the
unwanted mails
by te use of
filters over the
network
altogether which
can be allowed
by the use of the
SaaS technology
(Pearson, 2013).
5. Unauthorized
installation of
applications
M M H 1. Implementing
Saas
technology
Adopting the
strategy for
keeping
survilience on
the unauthorized
installations of
the applications
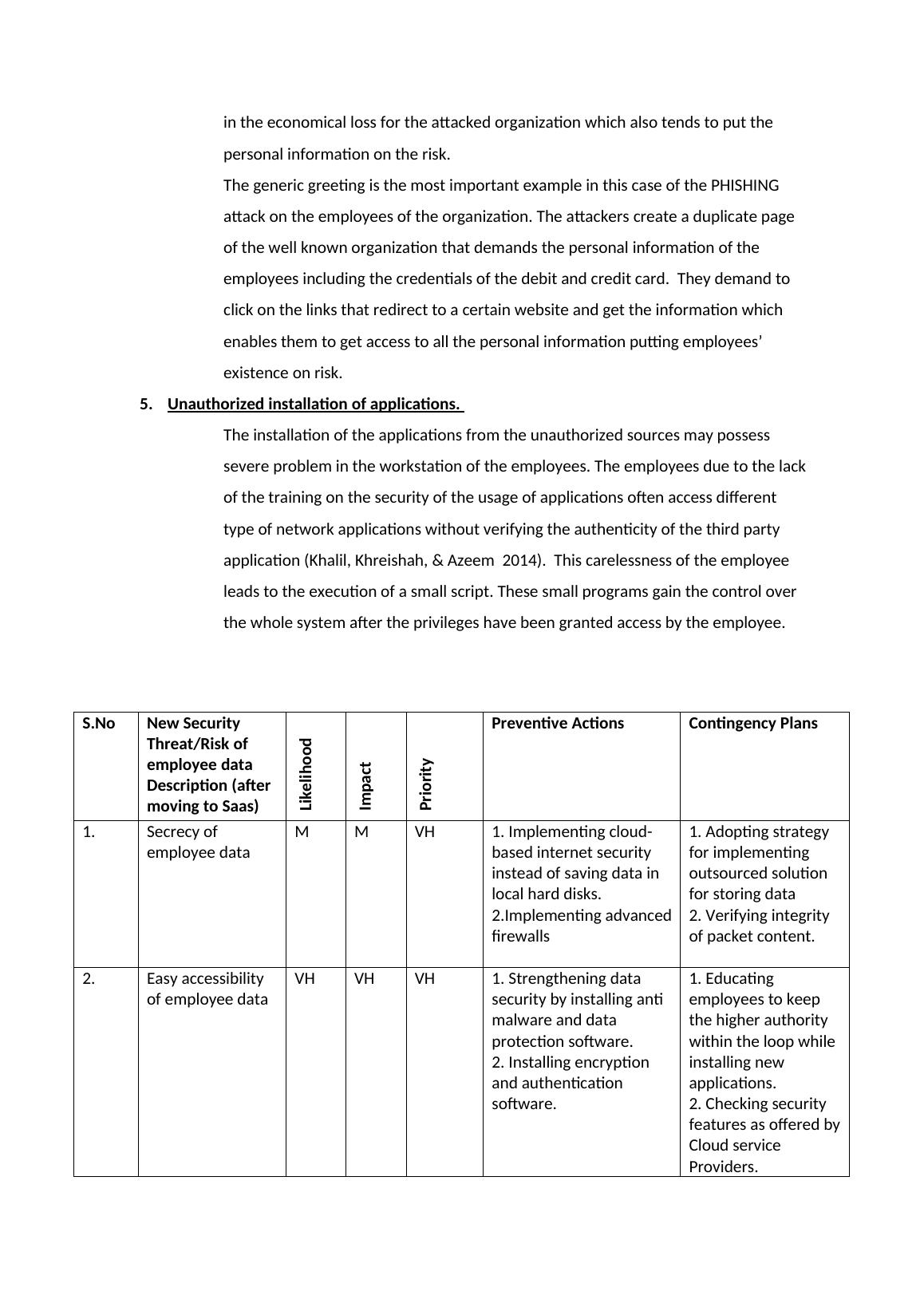
o Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues
1. Risks on losing passwords by the employees.
The risks can affect both the physical workstations within the same
organization and its location. It has been noted that maximum
number of employees discloses their password to the other
employees for personal reasons as well as official reasons. The risk
can be severe at times as the passwords can be misused and used
for illegal transactions (Chou, 2013). The Ransom ware attackers
look for the accounts of the employee of the organizations as it
makes an easy way to restore the bugs in the network of the
organization and create a mess by blocking the network which
hampers the business of the organization for the day.
2. Security threats by emails
The maximum communication in the corporate sectors is done
through the emails in the organization and also outside the
organization. The threat has been estimated up to 91% that is
sourced from the email in the organization. The fraudulent links are
often forwarded to the employees of the organization in their official
mail chains (Kshetri, 2013). The lack of the security training to the
employees results in accessing those links and creating an open
source for the attackers if the hackers to enter inside the web
network of the organization.
3. Risks due to unauthenticated connections
The utilization of the trusted secured connections like the wifi
connections or the LAN connections of the company keeps the
network safe. Often it has been observed that the employees gets
(Pearson, 2013).
5. Unauthorized
installation of
applications
M M H 1. Implementing
Saas
technology
Adopting the
strategy for
keeping
survilience on
the unauthorized
installations of
the applications
o Existing security threats to Employee data
Likelihood - VL, L,M, H, VH
Impact- - VL, L,M, H, VH
Priority- - VL, L, M,H, VH
Explain issues
1. Risks on losing passwords by the employees.
The risks can affect both the physical workstations within the same
organization and its location. It has been noted that maximum
number of employees discloses their password to the other
employees for personal reasons as well as official reasons. The risk
can be severe at times as the passwords can be misused and used
for illegal transactions (Chou, 2013). The Ransom ware attackers
look for the accounts of the employee of the organizations as it
makes an easy way to restore the bugs in the network of the
organization and create a mess by blocking the network which
hampers the business of the organization for the day.
2. Security threats by emails
The maximum communication in the corporate sectors is done
through the emails in the organization and also outside the
organization. The threat has been estimated up to 91% that is
sourced from the email in the organization. The fraudulent links are
often forwarded to the employees of the organization in their official
mail chains (Kshetri, 2013). The lack of the security training to the
employees results in accessing those links and creating an open
source for the attackers if the hackers to enter inside the web
network of the organization.
3. Risks due to unauthenticated connections
The utilization of the trusted secured connections like the wifi
connections or the LAN connections of the company keeps the
network safe. Often it has been observed that the employees gets

access to the unauthenticated data sources or connect their smart
devices with the connection of the organization. The employees
often tend to download from the links using the network connection
of the organization which makes it more vulnerable to the
attackers.
4. PHISHING
The PHISHING attacks are a great threat to the organization
infrastructure which directly includes the business infrastructure of
the organization. The PHISHING attacks are directly imposed on the
financial infrastructure of the company. It results in the economical
loss for the attacked organization which also tends to put the
personal information on the risk.
The generic greeting is the most important example in this case of
the PHISHING attack on the employees of the organization. The
attackers create a duplicate page of the well known organization
that demands the personal information of the employees including
the credentials of the debit and credit card. They demand to click
on the links that redirect to a certain website and get the
information which enables them to get access to all the personal
information putting employees’ existence on risk.
5. Unauthorized installation of applications.
The installation of the applications from the unauthorized sources
may possess severe problem in the workstation of the employees.
The employees due to the lack of the training on the security of the
usage of applications often access different type of network
applications without verifying the authenticity of the third party
application (Khalil, Khreishah, & Azeem 2014). This carelessness of
the employee leads to the execution of a small script. These small
programs gain the control over the whole system after the
privileges have been granted access by the employee.
devices with the connection of the organization. The employees
often tend to download from the links using the network connection
of the organization which makes it more vulnerable to the
attackers.
4. PHISHING
The PHISHING attacks are a great threat to the organization
infrastructure which directly includes the business infrastructure of
the organization. The PHISHING attacks are directly imposed on the
financial infrastructure of the company. It results in the economical
loss for the attacked organization which also tends to put the
personal information on the risk.
The generic greeting is the most important example in this case of
the PHISHING attack on the employees of the organization. The
attackers create a duplicate page of the well known organization
that demands the personal information of the employees including
the credentials of the debit and credit card. They demand to click
on the links that redirect to a certain website and get the
information which enables them to get access to all the personal
information putting employees’ existence on risk.
5. Unauthorized installation of applications.
The installation of the applications from the unauthorized sources
may possess severe problem in the workstation of the employees.
The employees due to the lack of the training on the security of the
usage of applications often access different type of network
applications without verifying the authenticity of the third party
application (Khalil, Khreishah, & Azeem 2014). This carelessness of
the employee leads to the execution of a small script. These small
programs gain the control over the whole system after the
privileges have been granted access by the employee.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Report | Cloud Computing in DASlg...
|22
|5610
|356
Cloud Security - ITC 568 | Assignmentlg...
|12
|2975
|261
Security and Privacy of Employee Data | Reportlg...
|34
|6311
|63
DAS and Shared Service Approach: Security Threats and Contingency Planslg...
|20
|1852
|194
Cloud Security Report 2022lg...
|23
|6412
|11
Security of Employee Data Report 2022lg...
|15
|4031
|18
