Social Network Sites, Privacy and Data Protection
VerifiedAdded on 2019/10/12
|42
|15288
|349
Essay
AI Summary
The provided assignment content discusses various aspects of privacy and data protection in cyberspace transactions, particularly in social media networks like Facebook. The articles explore concepts such as information privacy, disclosure regulation, and trust on the social web. The Pew Report and other research studies are also mentioned to highlight the importance of reputation management in online communities. Furthermore, the content touches upon the topic of qualitative research methodology in various fields, including marketing, nursing, and management. Overall, the assignment delves into the complex issues surrounding privacy, data protection, and social media interactions.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Introduction
When it comes to privacy and security issues on social networks, "the sites most likely to suffer
from issues are the most popular ones," Graham Cluley, Chief Technology Officer at UK tech
security firm Sophos says. But security issues and privacy issues are entirely two different
beasts. A security issue occurs when a hacker gains unauthorized access to a site's protected
coding or written language. Privacy issues, those involving the unwarranted access of private
information, don't necessarily have to involve security breaches. Someone can gain access to
confidential information by simply watching you type your password. But both types of breaches
are often intertwined on social networks, especially since anyone who breaches a site's security
network opens the door to easy access to private information belonging to any user. But the
potential harm to an individual user really boils down to how much a user engages in a social
networking site, as well as the amount of information they're willing to share. In other words, the
Facebook user with 900 friends and 60 group memberships is a lot more likely to be harmed by a
breach than someone who barely uses the site.
Security lapses on social networks don't necessarily involve the exploitation of a user's private
information. Take, for example, the infamous "Samy" MySpace XSS worm that effectively shut
the site down for a few days in October 2005. The "Samy" virus (named after the virus' creator)
was fairly harmless, and the malware snarkily added the words "Samy Is My Hero" to the top of
every affected user's MySpace profile page. A colossal inconvenience, naturally, but nobody's
identity was stolen and no private information was leaked. In the end, the problem galvanized the
MySpace team to roll up their sleeves and seriously tighten the site's security. Result: no major
break-ins since. Unfortunately, these kinds of breaches, purely for sport in "Samy's" case, are
rare.
The reason social network security and privacy lapses exist results simply from the astronomical
amounts of information the sites process each and every day that end up making it that much
easier to exploit a single flaw in the system. Features that invite user participation — messages,
invitations, photos, open platform applications, etc. — are often the avenues used to gain access
to private information, especially in the case of Facebook. Adrienne Felt, a Ph.D. candidate at
Berkeley, made small headlines last year when she exposed a potentially devastating hole in the
framework of Facebook's third-party application programming interface (API) which allows for
easy theft of private information. Felt and her co-researchers found that third-party platform
applications for Facebook gave developers access to far more information (addresses, pictures,
interests, etc.) than needed to run the app.
This potential privacy breach is actually built into the systematic framework of Facebook, and
unfortunately the flaw renders the system almost indefensible. "The question for social networks
is resolving the difference between mistakes in implementation and what the design of the
application platform is intended to allow," David Evans, Assistant Professor of Computer
Science at the University of Virginia, says. There's also the question of whom we should hold
responsible for the over-sharing of user data? That resolution isn't likely to come anytime soon,
says Evans, because a new, more regulated API would require Facebook "to break a lot of
When it comes to privacy and security issues on social networks, "the sites most likely to suffer
from issues are the most popular ones," Graham Cluley, Chief Technology Officer at UK tech
security firm Sophos says. But security issues and privacy issues are entirely two different
beasts. A security issue occurs when a hacker gains unauthorized access to a site's protected
coding or written language. Privacy issues, those involving the unwarranted access of private
information, don't necessarily have to involve security breaches. Someone can gain access to
confidential information by simply watching you type your password. But both types of breaches
are often intertwined on social networks, especially since anyone who breaches a site's security
network opens the door to easy access to private information belonging to any user. But the
potential harm to an individual user really boils down to how much a user engages in a social
networking site, as well as the amount of information they're willing to share. In other words, the
Facebook user with 900 friends and 60 group memberships is a lot more likely to be harmed by a
breach than someone who barely uses the site.
Security lapses on social networks don't necessarily involve the exploitation of a user's private
information. Take, for example, the infamous "Samy" MySpace XSS worm that effectively shut
the site down for a few days in October 2005. The "Samy" virus (named after the virus' creator)
was fairly harmless, and the malware snarkily added the words "Samy Is My Hero" to the top of
every affected user's MySpace profile page. A colossal inconvenience, naturally, but nobody's
identity was stolen and no private information was leaked. In the end, the problem galvanized the
MySpace team to roll up their sleeves and seriously tighten the site's security. Result: no major
break-ins since. Unfortunately, these kinds of breaches, purely for sport in "Samy's" case, are
rare.
The reason social network security and privacy lapses exist results simply from the astronomical
amounts of information the sites process each and every day that end up making it that much
easier to exploit a single flaw in the system. Features that invite user participation — messages,
invitations, photos, open platform applications, etc. — are often the avenues used to gain access
to private information, especially in the case of Facebook. Adrienne Felt, a Ph.D. candidate at
Berkeley, made small headlines last year when she exposed a potentially devastating hole in the
framework of Facebook's third-party application programming interface (API) which allows for
easy theft of private information. Felt and her co-researchers found that third-party platform
applications for Facebook gave developers access to far more information (addresses, pictures,
interests, etc.) than needed to run the app.
This potential privacy breach is actually built into the systematic framework of Facebook, and
unfortunately the flaw renders the system almost indefensible. "The question for social networks
is resolving the difference between mistakes in implementation and what the design of the
application platform is intended to allow," David Evans, Assistant Professor of Computer
Science at the University of Virginia, says. There's also the question of whom we should hold
responsible for the over-sharing of user data? That resolution isn't likely to come anytime soon,
says Evans, because a new, more regulated API would require Facebook "to break a lot of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

applications, and a lot of companies are trying to make money off applications now." Felt agrees,
noting that now "there are marketing businesses built on top of the idea that third parties can get
access to data on Facebook."
The problems plaguing social network security and privacy issues, for now, can only be resolved
if users take a more careful approach to what they share and how much. With the growth of
social networks, it's becoming harder to effectively monitor and protect site users and their
activity because the tasks of security programmers becomes increasingly spread out. Imagine if a
prison whose inmate count jumped from a few dozen to 250 million in less than five years only
employed 300 guards (in the case of MySpace). In response to the potential threats that users are
expose to, most of the major networks now enable users to set privacy controls for who has the
ability to view their information. But, considering the application loophole in Facebook,
increased privacy settings don't always guarantee privacy. But even when the flawed API was
publicly exposed, "Facebook changed the wording of the user agreement a little bit, but nothing
technically to solve the problem," says Evans. That means if a nefarious application developer
wanted to sell the personal info of people who used his app to advertising companies, he or she
could.
Yet users still post tons of personal data on social networks without batting an eye. It's only
natural. Anonymity and the fact that you're communicating with a machine instead of an actual
person (or people in the case of social networking) makes sharing a lot easier. "People should
just exercise common sense online, but the problem with common sense is that it's not very
common. If you wouldn't invite these people into your house to see your cat, you certainly
wouldn't let them see pictures from holiday," says Cluley.
In the end, the only tried and true solution to social network privacy and security issues is to
limit your presence altogether. Don't post anything you wouldn't mind telling a complete
stranger, because in reality that's the potential for access. Be careful who you add as a "friend,"
because there's simply no way of verifying a user's actual identity online. Cluley compares it to a
rep from your company's IT department calling to ask for your login password — "Most people
will give it over" with no proof of the IT rep actually existing. The caller might be your IT rep,
or she might not. "This kind of scam happens all the time," says Cluley. Friends on social
networks should know that real friends should know personal information already, negating the
need to post it online.
Will there ever be a security breach-free social network? Probably not. "Any complex system has
vulnerabilities in it. It's just the nature of building something above a certain level of
complexity," says Professor Evans. According to Felt, the best idea is a completely private social
network. "It simply requires that there's no gossip in the circle, by which I mean one person who
sets their privacy settings so low that third parties can use them to get to their friends."
"Social networks are great fun, and can be advantageous but people really need to understand
that it's complicated world and you need to step wisely," Cluley says.
noting that now "there are marketing businesses built on top of the idea that third parties can get
access to data on Facebook."
The problems plaguing social network security and privacy issues, for now, can only be resolved
if users take a more careful approach to what they share and how much. With the growth of
social networks, it's becoming harder to effectively monitor and protect site users and their
activity because the tasks of security programmers becomes increasingly spread out. Imagine if a
prison whose inmate count jumped from a few dozen to 250 million in less than five years only
employed 300 guards (in the case of MySpace). In response to the potential threats that users are
expose to, most of the major networks now enable users to set privacy controls for who has the
ability to view their information. But, considering the application loophole in Facebook,
increased privacy settings don't always guarantee privacy. But even when the flawed API was
publicly exposed, "Facebook changed the wording of the user agreement a little bit, but nothing
technically to solve the problem," says Evans. That means if a nefarious application developer
wanted to sell the personal info of people who used his app to advertising companies, he or she
could.
Yet users still post tons of personal data on social networks without batting an eye. It's only
natural. Anonymity and the fact that you're communicating with a machine instead of an actual
person (or people in the case of social networking) makes sharing a lot easier. "People should
just exercise common sense online, but the problem with common sense is that it's not very
common. If you wouldn't invite these people into your house to see your cat, you certainly
wouldn't let them see pictures from holiday," says Cluley.
In the end, the only tried and true solution to social network privacy and security issues is to
limit your presence altogether. Don't post anything you wouldn't mind telling a complete
stranger, because in reality that's the potential for access. Be careful who you add as a "friend,"
because there's simply no way of verifying a user's actual identity online. Cluley compares it to a
rep from your company's IT department calling to ask for your login password — "Most people
will give it over" with no proof of the IT rep actually existing. The caller might be your IT rep,
or she might not. "This kind of scam happens all the time," says Cluley. Friends on social
networks should know that real friends should know personal information already, negating the
need to post it online.
Will there ever be a security breach-free social network? Probably not. "Any complex system has
vulnerabilities in it. It's just the nature of building something above a certain level of
complexity," says Professor Evans. According to Felt, the best idea is a completely private social
network. "It simply requires that there's no gossip in the circle, by which I mean one person who
sets their privacy settings so low that third parties can use them to get to their friends."
"Social networks are great fun, and can be advantageous but people really need to understand
that it's complicated world and you need to step wisely," Cluley says.

LITERATURE REVIEW
Currently, in the era of advanced internet technology, Social Network becomes incredibly
popular tool on the internet and becomes widely used around the world. It is powerful tool in any
ages of people especially among teenagers and young adults in the propose of communication
and self-expression [1], and it is easy mean of sharing information with other users who has a
common interest such as photos, likes, dislikes, interests, relationship status, job details, current
town details, political views, religious views etc. [2] [3] [4].Social networking sites and
associated privacy concerns is one of the most debated topic nowadays as participation in such
sites has increased dramatically. A number of journals and articles come up with this issue that
how the increase in the usage of social networking sites is leading to various online crimes.
Unfortunately, though this technology most of users are not aware of the privacy risk associated
whenever they shared sensitive information in the internet [4], so that privacy concern will be
raised among those online interactions if their personal information has been shared to other
people [3] [5].
Definitions of privacy
The word privacy has many subtly different meanings, ranging from personal privacy (which
includes seclusion and bodily privacy) to information privacy, each with their own definition.
Privacy on the Web in general revolves mostly around Information Privacy, as defined below in
the IITF wording that Kang uses: Information Privacy is “an individual’s claim to control the
terms under which personal information–information identifiable to the individual–is acquired,
disclosed or used.”Palen and Dourish classify three privacy boundaries with which individuals
are struggling. 1. The disclosure boundary (managing the tension between private and public), 2.
The identity boundary (managing self representation with specific audience, e.g. one will behave
differently at work than when among friends), 3. The temporal boundary (managing past actions
with future expectations; user behavior may change over time).
Online personal information privacy
Protecting the privacy of personal information is one of the biggest challenges facing website
developers, especially social network providers. Several researchers have discussed the issue of
privacy. Bae and Kim (2010) suggested that, in order to achieve a high level of privacy, the user
should be given the authority to control the privacy settings when he/she receives or requests a
service related to his/her personal information. The authors noted the importance of designing a
privacy policy to protect personal information by blocking some people from seeing all or part of
the user’s personal information. They also designed a privacy model using mobile agents.
Dötzer (2006, p.4) stated that “once privacy is lost, it is very hard to re-establish that state of
personal rights.” This shows that privacy is essential to the construction of all communication
systems, particularly mobile systems. The concept of self-representation enables users to interact
and introduce themselves based on the data placed on profile pages such as name and pictures
with others. Privacy is an important aspect of self-representation on online social networks since
people share certain information with the public and receive information or comments from
others. The nature and complexity of the Internet cause some threats to web privacy
(Bouguettaya&Eltoweissy 2003). According to Wang and Cui (2008), privacy is a state or
Currently, in the era of advanced internet technology, Social Network becomes incredibly
popular tool on the internet and becomes widely used around the world. It is powerful tool in any
ages of people especially among teenagers and young adults in the propose of communication
and self-expression [1], and it is easy mean of sharing information with other users who has a
common interest such as photos, likes, dislikes, interests, relationship status, job details, current
town details, political views, religious views etc. [2] [3] [4].Social networking sites and
associated privacy concerns is one of the most debated topic nowadays as participation in such
sites has increased dramatically. A number of journals and articles come up with this issue that
how the increase in the usage of social networking sites is leading to various online crimes.
Unfortunately, though this technology most of users are not aware of the privacy risk associated
whenever they shared sensitive information in the internet [4], so that privacy concern will be
raised among those online interactions if their personal information has been shared to other
people [3] [5].
Definitions of privacy
The word privacy has many subtly different meanings, ranging from personal privacy (which
includes seclusion and bodily privacy) to information privacy, each with their own definition.
Privacy on the Web in general revolves mostly around Information Privacy, as defined below in
the IITF wording that Kang uses: Information Privacy is “an individual’s claim to control the
terms under which personal information–information identifiable to the individual–is acquired,
disclosed or used.”Palen and Dourish classify three privacy boundaries with which individuals
are struggling. 1. The disclosure boundary (managing the tension between private and public), 2.
The identity boundary (managing self representation with specific audience, e.g. one will behave
differently at work than when among friends), 3. The temporal boundary (managing past actions
with future expectations; user behavior may change over time).
Online personal information privacy
Protecting the privacy of personal information is one of the biggest challenges facing website
developers, especially social network providers. Several researchers have discussed the issue of
privacy. Bae and Kim (2010) suggested that, in order to achieve a high level of privacy, the user
should be given the authority to control the privacy settings when he/she receives or requests a
service related to his/her personal information. The authors noted the importance of designing a
privacy policy to protect personal information by blocking some people from seeing all or part of
the user’s personal information. They also designed a privacy model using mobile agents.
Dötzer (2006, p.4) stated that “once privacy is lost, it is very hard to re-establish that state of
personal rights.” This shows that privacy is essential to the construction of all communication
systems, particularly mobile systems. The concept of self-representation enables users to interact
and introduce themselves based on the data placed on profile pages such as name and pictures
with others. Privacy is an important aspect of self-representation on online social networks since
people share certain information with the public and receive information or comments from
others. The nature and complexity of the Internet cause some threats to web privacy
(Bouguettaya&Eltoweissy 2003). According to Wang and Cui (2008), privacy is a state or

condition of limited access to a person. Privacy regulations can be defined as a set of rules or
policies set by users to achieve a certain level of privacy. In terms of location privacy, privacy
regulations restrict access to information on a user’s location. Each privacy rule or policy can
include some restrictions (Sadeh& Hong 2009). Although there is no policy mandating online
personal information privacy, some types of privacy solutions do exist (Passant et al. 2009).
These solutions can be classified into: protective technologies, social awareness and legislative
support. Protective technologies, such as strong authentication and access control, have
developed quickly and have evolved over time. These rely on encryption as a way to solve
privacy concerns. The second type of solution, social awareness, involves educating people
about the possible risks of personal information misuse when they provide data such as their
home address and mobile phone number. Lastly, legislation can be enacted to clarify aspects of
the agreement with users to protect the collection of personal information under the framework
of the law (Campisi, Maiorana&Neri 2009).
Since the inception of the first social networking site, SixDegrees.com at 1997 (Boyd and
Ellison, 2008), the social networking craze has grown beyond all expectations. Data privacy is a
fundamental problem in today's information era. Enormous amounts of data are collected by
government agencies, search engines, social networking systems, hospitals, financial institutions,
and other organizations, and are stored in databases. Those stored information is very crucial for
individuals, people might misuse this information. The problems that exist in the real world such
as theft, fraud, vandalism also exists in online Web 2 environments an identity thief.
According to consumer security risks survey 2014, is done by B2B International in conjunction
with Kaspersky Lab shown that even using social networking is worldwide, but however there
are minority of them understanding the risks of using social networking especially in terms of
using mobile device to access the sites. Correspondingly, more than 78% of correspondents did
not concern their information to be targeted by cyber-attacks or cyber-crime and they though that
no any dangerous with any activities on their social network. The survey also found that one of
ten has ever conversed to anonymous person about personal information, while 15% sending
personal information which has not been exposed anywhere before through social network.
Furthermore, 12 % of correspondents using public Wi-Fi to fill online account information, but
only 18% of them who concerned that their personal information disclosure is excessive or not
and 7% seriously considered their communicating through social networking is one of major
factor which information will be lose [6]. Every social network sites ask users to accomplish a
profile which contains privacy information including name, address, email and so on. Through
this information is claim to be danger which can be easily accessed by unexpected person [7] [8],
but what is happening today, most of social network users tend to public real identity and post
private information where privacy will be raised [9]. Accordingly, [3] [4] [7] [8] [10], they
described that online social networking data is of great help to the researchers, analysts, and any
kind of third party who has opportunity to mine and use data for particular purposes such as
spamming, fishing, targeted advertising and so on [4]. This is because sensitive information and
their interaction are stored in social OSN server are not always honest and transparent due to the
nature of OSN allows third parties to collect and analyze easily [9]. Raji and her colleagues
demonstrated that there are some principle privacy problems in social network like Facebook.
policies set by users to achieve a certain level of privacy. In terms of location privacy, privacy
regulations restrict access to information on a user’s location. Each privacy rule or policy can
include some restrictions (Sadeh& Hong 2009). Although there is no policy mandating online
personal information privacy, some types of privacy solutions do exist (Passant et al. 2009).
These solutions can be classified into: protective technologies, social awareness and legislative
support. Protective technologies, such as strong authentication and access control, have
developed quickly and have evolved over time. These rely on encryption as a way to solve
privacy concerns. The second type of solution, social awareness, involves educating people
about the possible risks of personal information misuse when they provide data such as their
home address and mobile phone number. Lastly, legislation can be enacted to clarify aspects of
the agreement with users to protect the collection of personal information under the framework
of the law (Campisi, Maiorana&Neri 2009).
Since the inception of the first social networking site, SixDegrees.com at 1997 (Boyd and
Ellison, 2008), the social networking craze has grown beyond all expectations. Data privacy is a
fundamental problem in today's information era. Enormous amounts of data are collected by
government agencies, search engines, social networking systems, hospitals, financial institutions,
and other organizations, and are stored in databases. Those stored information is very crucial for
individuals, people might misuse this information. The problems that exist in the real world such
as theft, fraud, vandalism also exists in online Web 2 environments an identity thief.
According to consumer security risks survey 2014, is done by B2B International in conjunction
with Kaspersky Lab shown that even using social networking is worldwide, but however there
are minority of them understanding the risks of using social networking especially in terms of
using mobile device to access the sites. Correspondingly, more than 78% of correspondents did
not concern their information to be targeted by cyber-attacks or cyber-crime and they though that
no any dangerous with any activities on their social network. The survey also found that one of
ten has ever conversed to anonymous person about personal information, while 15% sending
personal information which has not been exposed anywhere before through social network.
Furthermore, 12 % of correspondents using public Wi-Fi to fill online account information, but
only 18% of them who concerned that their personal information disclosure is excessive or not
and 7% seriously considered their communicating through social networking is one of major
factor which information will be lose [6]. Every social network sites ask users to accomplish a
profile which contains privacy information including name, address, email and so on. Through
this information is claim to be danger which can be easily accessed by unexpected person [7] [8],
but what is happening today, most of social network users tend to public real identity and post
private information where privacy will be raised [9]. Accordingly, [3] [4] [7] [8] [10], they
described that online social networking data is of great help to the researchers, analysts, and any
kind of third party who has opportunity to mine and use data for particular purposes such as
spamming, fishing, targeted advertising and so on [4]. This is because sensitive information and
their interaction are stored in social OSN server are not always honest and transparent due to the
nature of OSN allows third parties to collect and analyze easily [9]. Raji and her colleagues
demonstrated that there are some principle privacy problems in social network like Facebook.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

For instance, Users used their real information to create an account profile to the rest of the
Facebook users, The default privacy settings are not enough in Facebook, so users expose too
much information to others users, Users do not change the OSN default privacy settings that are
provided, and Sometime it is unavailable to adjust the privacy setting which is offered by
Facebook such as the users can see the whole his or her shared information whenever users add
his or her to be in friend list [9].
However, sometime there is a must to users to reveal personal information in particular reason,
as demonstrated by [7]. They also illustrated that users have to reveal the personal information
on social network in order to be effective and do this for maturing their identities. In reality,
online communication can bring them to be intensive revelation compared to face to face
communication. Furthermore, in the face of information of behavior of users are able to
conceptualize as continuum which describes as information privacy protection behavior. This
means information can disclose accurately in one side, but it is not for other sides. By the way,
users can participate all and can protecting their personal information at the same time by partly
disclosing of them.
A blog in a website DashBurst clearly mentions that “with the rise of social media, privacy
concerns have taken a backseat in recent years (Trenchard, 2013).” It talks about the potential
dangers that a young user may likely face while using the social networking site. Thus it
becomes very important for one to read the privacy policies and measures offered by these sites
in order to have a safe online networking. Further, the blog also states the privacy policy changes
brought out by the popular sites like Facebook and Twitter and how it has affected the users. One
of the main reasons cited by experts and research studies for such tremendous popularity of the
social networking sites is the emergence of sites that offer the scope of connectivity in this
virtual world almost at any time of the day. People get in touch with near and dear ones with the
services like Facebook, Twitter, Orkut, LinkedIn, MySpace, etc (Dutton, 2004). In social
networking sites, sharing of private information and giving updates of day to day happening is a
latest trend. These sites heavily caters to the young brigade especially the age group between 15
to 25 years. Sometimes it has been observed that youngsters use these sites for sharing news or
any information rather than sharing it personally. Even if they meet in the morning in college,
information is shared mostly through the social media sites. It shows the growing dependency on
such sites (Kabay, 2010). It is strange enough to note that communication process is hugely
getting affected through the advancement of the internet. With the controversial changes made
by the popular social networking site Facebook in 2009, it had beome quite impossible to
maintain a safe invisible account (Trenchard, 2013). By analysing the personal information
revelation behaviour of the users, it has been mainly found out that this factor mainly revolves
around hobbies and interests although it also has other directions. Like for insance, semi-public
information may include schooling or employment details, whereas personal information may
include drinking or drug habits or sexual orientation, etc (Gross & Acquisti, 2005). The apparent
openness of users of the social networking sites calls for unncessary attention from strangers
quite possibly leading to online victimization. It is very easy to join a social networking site. But
without proper knowledge of the security measures, one can be a easy trap for the third parties
like the hackers (Gross & Acquisti, 2005).
Facebook users, The default privacy settings are not enough in Facebook, so users expose too
much information to others users, Users do not change the OSN default privacy settings that are
provided, and Sometime it is unavailable to adjust the privacy setting which is offered by
Facebook such as the users can see the whole his or her shared information whenever users add
his or her to be in friend list [9].
However, sometime there is a must to users to reveal personal information in particular reason,
as demonstrated by [7]. They also illustrated that users have to reveal the personal information
on social network in order to be effective and do this for maturing their identities. In reality,
online communication can bring them to be intensive revelation compared to face to face
communication. Furthermore, in the face of information of behavior of users are able to
conceptualize as continuum which describes as information privacy protection behavior. This
means information can disclose accurately in one side, but it is not for other sides. By the way,
users can participate all and can protecting their personal information at the same time by partly
disclosing of them.
A blog in a website DashBurst clearly mentions that “with the rise of social media, privacy
concerns have taken a backseat in recent years (Trenchard, 2013).” It talks about the potential
dangers that a young user may likely face while using the social networking site. Thus it
becomes very important for one to read the privacy policies and measures offered by these sites
in order to have a safe online networking. Further, the blog also states the privacy policy changes
brought out by the popular sites like Facebook and Twitter and how it has affected the users. One
of the main reasons cited by experts and research studies for such tremendous popularity of the
social networking sites is the emergence of sites that offer the scope of connectivity in this
virtual world almost at any time of the day. People get in touch with near and dear ones with the
services like Facebook, Twitter, Orkut, LinkedIn, MySpace, etc (Dutton, 2004). In social
networking sites, sharing of private information and giving updates of day to day happening is a
latest trend. These sites heavily caters to the young brigade especially the age group between 15
to 25 years. Sometimes it has been observed that youngsters use these sites for sharing news or
any information rather than sharing it personally. Even if they meet in the morning in college,
information is shared mostly through the social media sites. It shows the growing dependency on
such sites (Kabay, 2010). It is strange enough to note that communication process is hugely
getting affected through the advancement of the internet. With the controversial changes made
by the popular social networking site Facebook in 2009, it had beome quite impossible to
maintain a safe invisible account (Trenchard, 2013). By analysing the personal information
revelation behaviour of the users, it has been mainly found out that this factor mainly revolves
around hobbies and interests although it also has other directions. Like for insance, semi-public
information may include schooling or employment details, whereas personal information may
include drinking or drug habits or sexual orientation, etc (Gross & Acquisti, 2005). The apparent
openness of users of the social networking sites calls for unncessary attention from strangers
quite possibly leading to online victimization. It is very easy to join a social networking site. But
without proper knowledge of the security measures, one can be a easy trap for the third parties
like the hackers (Gross & Acquisti, 2005).

Most social networks offer privacy settings that are simple to use, but coarse. They often require
the user to set the visibility for each profile item to either private, friends only, or public.
Sometimes a few more options are given. In the end it boils down to a list of items and check
boxes to either opt-in or opt-out of disclosing these items to certain groups, limiting user control.
Gross and Acquisti show in a case study that most users do not change the default privacy
settings as provided by the OSN. Furthermore these users share a large amount of information on
their profile. Tufecki [27] concludes in his case study that privacy-aware users are more reluctant
to join social networks. However once a privacy aware user joins he is willing to disclose a lot of
information and a user’s privacy is regulated mostly through visibility, i.e. the privacy settings of
the OSN (Online Social Networks). This privacy aware user aims to remain in control.
Furthermore users are more pre-occupied with the current visibility of their information and do
not look towards future implications. It seems that users implicitly trust social network providers
to handle user data in a fair and conscientious way.
Ahern, Eckles et al. (2007: 357) analysing the issue and conducting studies on Privacy Patterns
and Considerations in online and mobile photo sharing claim: The growing amount of online
personal content exposes users to a new set of privacy concerns. Digital cameras, and lately, a
new class of camera phone applications that can upload photos or video content directly to the
web, make publishing of personal content increasingly easy. Privacy concerns are especially
acute in the case of multimedia collections, as they could reveal much of the user’s personal and
social environment.[9]
Online social network privacy
George (2006) cited the case of US college athletes whose pictures, which they posted online,
were misused by a website, which publishes stories about scandals in sport. The author pointed
out that the issue of privacy has not gone unnoticed by social network providers. Gross and
Acquisti (2005) conducted a study on a sample of 4,000 students from Carnegie Mellon
University who use social network accounts. They found that a large proportion of students did
not care about the privacy risks that might increase the chance of a third party misusing a
student’s personal information. Another study by the same authors claimed that more than 77
percent of the respondents did not read privacy policies (Acquisti& Gross 2006). The ability to
control privacy options is essential to increasing the users’ confidence in their social network
providers. Since Internet users represent a range of different cultures and ages, privacy options
should be clear, simple and easy to use. Users must have the ability to control their privacy
options at any time. These privacy options allow users to accept or reject the dissemination of
their information to others. For example, some users do not want to publish sensitive information
such as health or medical information (Samavi&Consens 2010). These users are aware that
people with less than honourable intentions can harm adults or children by misusing their
personal information. A study conducted by Casarosa (2010) found that minors are interested in
new technologies and the Internet, and can be contacted by strangers online asking to form a
friendship. When a website publishes the personal information of a minor without giving the
child’s parents (or the child’s guardian) the authority to select privacy options, potential
predators can use some of the minor’s personal information, such as a mobile phone number, to
engage in sexual contact (Casarosa 2010).
the user to set the visibility for each profile item to either private, friends only, or public.
Sometimes a few more options are given. In the end it boils down to a list of items and check
boxes to either opt-in or opt-out of disclosing these items to certain groups, limiting user control.
Gross and Acquisti show in a case study that most users do not change the default privacy
settings as provided by the OSN. Furthermore these users share a large amount of information on
their profile. Tufecki [27] concludes in his case study that privacy-aware users are more reluctant
to join social networks. However once a privacy aware user joins he is willing to disclose a lot of
information and a user’s privacy is regulated mostly through visibility, i.e. the privacy settings of
the OSN (Online Social Networks). This privacy aware user aims to remain in control.
Furthermore users are more pre-occupied with the current visibility of their information and do
not look towards future implications. It seems that users implicitly trust social network providers
to handle user data in a fair and conscientious way.
Ahern, Eckles et al. (2007: 357) analysing the issue and conducting studies on Privacy Patterns
and Considerations in online and mobile photo sharing claim: The growing amount of online
personal content exposes users to a new set of privacy concerns. Digital cameras, and lately, a
new class of camera phone applications that can upload photos or video content directly to the
web, make publishing of personal content increasingly easy. Privacy concerns are especially
acute in the case of multimedia collections, as they could reveal much of the user’s personal and
social environment.[9]
Online social network privacy
George (2006) cited the case of US college athletes whose pictures, which they posted online,
were misused by a website, which publishes stories about scandals in sport. The author pointed
out that the issue of privacy has not gone unnoticed by social network providers. Gross and
Acquisti (2005) conducted a study on a sample of 4,000 students from Carnegie Mellon
University who use social network accounts. They found that a large proportion of students did
not care about the privacy risks that might increase the chance of a third party misusing a
student’s personal information. Another study by the same authors claimed that more than 77
percent of the respondents did not read privacy policies (Acquisti& Gross 2006). The ability to
control privacy options is essential to increasing the users’ confidence in their social network
providers. Since Internet users represent a range of different cultures and ages, privacy options
should be clear, simple and easy to use. Users must have the ability to control their privacy
options at any time. These privacy options allow users to accept or reject the dissemination of
their information to others. For example, some users do not want to publish sensitive information
such as health or medical information (Samavi&Consens 2010). These users are aware that
people with less than honourable intentions can harm adults or children by misusing their
personal information. A study conducted by Casarosa (2010) found that minors are interested in
new technologies and the Internet, and can be contacted by strangers online asking to form a
friendship. When a website publishes the personal information of a minor without giving the
child’s parents (or the child’s guardian) the authority to select privacy options, potential
predators can use some of the minor’s personal information, such as a mobile phone number, to
engage in sexual contact (Casarosa 2010).

The following links highlight some of the privacy issues that have highlighted the need for a
decentralised privacy aware social networking tool.
• Facebook’s Bewildering Privacy Policy An article by the NY Times, highlighting how
confusing Facebook’s privacy settings are http://www.nytimes.com/
interactive/2010/05/12/business/facebook-privacy.html and convoluted their privacy policy
actually is.
• Facebook’s Opengraph The following blog post http://zestyping.livejournal .com/257224.html
highlights the privacy implications of Facebook’s Open Graph Protocol [20]. Illustrated by the
web-service http://zesty.ca/facebook/
• Application that searches public Facebook wall posts The example webservice call
http://willmoffat.github.com/FacebookSearch/?q=Stupid+boss&gender=any highlights the
information that is accessible via Facebook’s Graph API [21]. It should be noted that the wall
posts shown in the aforementioned web-service call, are not apparently visible to the Web if one
simply visits an exposed user’s public profile page.
• The Evolution of Facebook’s Privacy Policy The following visualisation shows how
Facebook’s privacy policy has changed over time http://mattmckeon.com/facebookprivacy/. This
change in policy, is the main reason why there has been a sudden desire for the development of a
decentralised social network, removing the need for a central service that accumulates personal
information.
In order for any decentralised social networking service to be a success, the service’s privacy
policy with respect to the information it holds regarding its users must appeal to the privacy
aware masses. A report undertaken by Joseph Bonneau, Sren Preibusch from the Cambridge
University entitled “The Privacy Jungle: On the Market for Data Protection in Social
Networks”[22] details the findings of a study of privacy policies for popular social networking
sites, and presents best practises when it comes to creation of privacy policies [23].
Youth and the Concept of Privacy
In January 2010, Facebook’s Mark Zuckerberg told TechCrunch’s Mike Arrington [24] in a live
interview that he thought the concept of privacy no longer applies to the modern day [25]. Since
this claim the below studies have attempted to understand people’s feelings towards privacy: •
Pew Report on Online Reputation Pew Research, a US based research firm, recently conducted a
report detailing peoples attitudes to privacy, and online reputation. The report entitled
“Reputation, Management, and Social Media” [26], found that young adults are more likely than
older users to try and limit the amount of information available about them online. dannah boyd
from Microsoft research presents an overview of the research on her blog [27]. • Youth do care
about privacy A secondly unrelated piece of research undertaken by academics at University of
California Berkley, entitled “How Different are Young Adults from Older Adults When it Comes
to Information Privacy Attitudes and Policies?” [28] can be summarised in the below bullet
points: – Young Adults vs Adults The study did not find significant differences between young
or older adults regarding privacy, everyone seemed to be equally concerned and acknowledge it
as an issue. – Young American were uneducated towards issues relating to privacy 42 percent of
decentralised privacy aware social networking tool.
• Facebook’s Bewildering Privacy Policy An article by the NY Times, highlighting how
confusing Facebook’s privacy settings are http://www.nytimes.com/
interactive/2010/05/12/business/facebook-privacy.html and convoluted their privacy policy
actually is.
• Facebook’s Opengraph The following blog post http://zestyping.livejournal .com/257224.html
highlights the privacy implications of Facebook’s Open Graph Protocol [20]. Illustrated by the
web-service http://zesty.ca/facebook/
• Application that searches public Facebook wall posts The example webservice call
http://willmoffat.github.com/FacebookSearch/?q=Stupid+boss&gender=any highlights the
information that is accessible via Facebook’s Graph API [21]. It should be noted that the wall
posts shown in the aforementioned web-service call, are not apparently visible to the Web if one
simply visits an exposed user’s public profile page.
• The Evolution of Facebook’s Privacy Policy The following visualisation shows how
Facebook’s privacy policy has changed over time http://mattmckeon.com/facebookprivacy/. This
change in policy, is the main reason why there has been a sudden desire for the development of a
decentralised social network, removing the need for a central service that accumulates personal
information.
In order for any decentralised social networking service to be a success, the service’s privacy
policy with respect to the information it holds regarding its users must appeal to the privacy
aware masses. A report undertaken by Joseph Bonneau, Sren Preibusch from the Cambridge
University entitled “The Privacy Jungle: On the Market for Data Protection in Social
Networks”[22] details the findings of a study of privacy policies for popular social networking
sites, and presents best practises when it comes to creation of privacy policies [23].
Youth and the Concept of Privacy
In January 2010, Facebook’s Mark Zuckerberg told TechCrunch’s Mike Arrington [24] in a live
interview that he thought the concept of privacy no longer applies to the modern day [25]. Since
this claim the below studies have attempted to understand people’s feelings towards privacy: •
Pew Report on Online Reputation Pew Research, a US based research firm, recently conducted a
report detailing peoples attitudes to privacy, and online reputation. The report entitled
“Reputation, Management, and Social Media” [26], found that young adults are more likely than
older users to try and limit the amount of information available about them online. dannah boyd
from Microsoft research presents an overview of the research on her blog [27]. • Youth do care
about privacy A secondly unrelated piece of research undertaken by academics at University of
California Berkley, entitled “How Different are Young Adults from Older Adults When it Comes
to Information Privacy Attitudes and Policies?” [28] can be summarised in the below bullet
points: – Young Adults vs Adults The study did not find significant differences between young
or older adults regarding privacy, everyone seemed to be equally concerned and acknowledge it
as an issue. – Young American were uneducated towards issues relating to privacy 42 percent of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
young Americans answered all of our five online privacy questions *incorrectly*. 88 percent
answered only two or fewer correctly. The problem is even more pronounced when presented
with offline privacy issues – post hoc analysis showed that young Americans were more likely to
answer no questions correctly than any other age group.
An Aspiration for increased Privacy The report concludes that young-adult Americans have “an
aspiration for increased privacy” even though they enjoy participating in social online activities.
An aspiration for privacy, with a distinct lack of education with regards to the issues surrounding
it. From an educational point of view, the previous two chapters present insight into the world of
social networking and privacy policies. The creation of a privacy aware decentralised social
network, such as a future POAF system, is presented as a field where the BBC can innovate in
terms of ownership of data, empowering future generations with the right to hold onto and share
their personal data, in an informed manner. A final piece of work, which might motivate the
POAF service is a recent PhD thesis by Elza Dunkels entitled “Bridging the distance: children’s
strategies on the internet”[29] which shows how children develop their own safety strategies
when it comes to working online. The work presents findings that show how children tend to
create strategies for circumventing guidelines made by organisations such as Family Online
Safety Institute (FOSI)[30] which in turn make it near on impossible for children to have any
social interactions in the digital world. This notion is presented as another motivating factor for
the development of a privacy aware social networking service. It should be noted that FOSI’s
approach is slightly different from that taken by the Child Exploitation and Online Protection
Centre (CEOP) in the UK, whereby their attempt to introduce the “panic button”[31], a method
of allowing children to get advice, help, and to report incidents to the police if they feel
threatened online, insofar as they produce guidelines about how children should use the Web, as
apposed to allowing children to use the Web, but giving them a simple way to report abuse/get
help. As it stands out of the major social networking sites, only Bebo [32] has chosen to host
CEOP’s panic button [33].
Online privacy risks
There are several risks surrounding the posting of personal information details on social
networks. These threats can be caused by hackers or spammers who obtain users’ personal
information details. Identity theft is one of the major risks that users face (Williams et al. 2009).
Access to sensitive information may also lead to terrorism risks, financial risks and physical or
sexual extortion (Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach
attacks in online social networks. First, users usually upload their personal information when
they trust the service provider. However, the provider can use these details for business purposes
such as advertising. In addition, it is not only the service providers who can see the users’
personal information. Some online social networks provide users with policies to determine the
list of authorized persons who can see their personal information. These policies vary from one
provider to another; some providers give users more flexibility than others and some provide
encryption for their data. The second privacy breach can be caused by the user’s friends, who can
share the user’s personal information details with others. Friends who have access to the user’s
personal information can copy and publish this information. The third breach is due to
spammers. When spammers see the user’s friend list, they can see other users’ personal
answered only two or fewer correctly. The problem is even more pronounced when presented
with offline privacy issues – post hoc analysis showed that young Americans were more likely to
answer no questions correctly than any other age group.
An Aspiration for increased Privacy The report concludes that young-adult Americans have “an
aspiration for increased privacy” even though they enjoy participating in social online activities.
An aspiration for privacy, with a distinct lack of education with regards to the issues surrounding
it. From an educational point of view, the previous two chapters present insight into the world of
social networking and privacy policies. The creation of a privacy aware decentralised social
network, such as a future POAF system, is presented as a field where the BBC can innovate in
terms of ownership of data, empowering future generations with the right to hold onto and share
their personal data, in an informed manner. A final piece of work, which might motivate the
POAF service is a recent PhD thesis by Elza Dunkels entitled “Bridging the distance: children’s
strategies on the internet”[29] which shows how children develop their own safety strategies
when it comes to working online. The work presents findings that show how children tend to
create strategies for circumventing guidelines made by organisations such as Family Online
Safety Institute (FOSI)[30] which in turn make it near on impossible for children to have any
social interactions in the digital world. This notion is presented as another motivating factor for
the development of a privacy aware social networking service. It should be noted that FOSI’s
approach is slightly different from that taken by the Child Exploitation and Online Protection
Centre (CEOP) in the UK, whereby their attempt to introduce the “panic button”[31], a method
of allowing children to get advice, help, and to report incidents to the police if they feel
threatened online, insofar as they produce guidelines about how children should use the Web, as
apposed to allowing children to use the Web, but giving them a simple way to report abuse/get
help. As it stands out of the major social networking sites, only Bebo [32] has chosen to host
CEOP’s panic button [33].
Online privacy risks
There are several risks surrounding the posting of personal information details on social
networks. These threats can be caused by hackers or spammers who obtain users’ personal
information details. Identity theft is one of the major risks that users face (Williams et al. 2009).
Access to sensitive information may also lead to terrorism risks, financial risks and physical or
sexual extortion (Gharibi&Shaabi 2012). Gao et al. (2011) discussed the common privacy breach
attacks in online social networks. First, users usually upload their personal information when
they trust the service provider. However, the provider can use these details for business purposes
such as advertising. In addition, it is not only the service providers who can see the users’
personal information. Some online social networks provide users with policies to determine the
list of authorized persons who can see their personal information. These policies vary from one
provider to another; some providers give users more flexibility than others and some provide
encryption for their data. The second privacy breach can be caused by the user’s friends, who can
share the user’s personal information details with others. Friends who have access to the user’s
personal information can copy and publish this information. The third breach is due to
spammers. When spammers see the user’s friend list, they can see other users’ personal

information by sending them a friend request, impersonating one of his/her friends by using the
friend’s name or picture. Lastly, breaches can be caused by third party applications installed by
users. These applications can be a threat to users, especially if they are not from a trusted
provider. When the application accesses the users’ personal information, others can obtain this
information. Novak and Li (2012) also claimed that privacy breaches can be caused by friends,
applications, and exploitation of personal information details by the service providers for
advertising. The authors added that understanding privacy settings is not enough to protect users,
especially from friends and other online social network users. Thus, social networking websites
such as Facebook prioritize the development of tools to protect privacy. This is manifested in the
social network providers’ requests for new users to create new privacy settings. However, some
users do not realize the risk of leakage of personal information (Lee et al. 2011). Therefore,
sensitive information such as home address and date of birth should not be published online in
order to avoid risks to online privacy. Increasing user awareness of these risks, providing a
privacy management system for users to control their personal information details, and
constantly updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online
Privacy: Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are
alert and cautious when using the social networking sites. However, Facebook users are not
completely informed or aware of all activities concerning privacy on the social networking sites.
Though, low trust levels to date have not hindered activity on Facebook and membership
continues to rise. Facebook users seem willing to push aside trust issues to achieve social
interaction. The importance of trust in a social networking context is clearly questionable and
perhaps different determinants for online activity exist in different online environments. There
are a number of barriers to trust in the online environment. These barriers include perceived risk,
website design and content, the user themselves and privacy concerns. Privacy concerns are
considered the greatest barrier of them all because ‘the internet, by design, lacks unified
provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection
techniques such as cookie technology involving extreme surveillance. The use and analysis of
data are also a concern due to unethical merging and data mining practices to profile customers.
The instant recording and permanence of activity, loss of control and ownership of data also
creates barriers to online activity (Tavani, 2011). Social networking users claim to be concerned
about risks to privacy, yet do little to safeguard their information (Dwyer et al., 2007). Often
users openly disclose detailed and personal information on these networks, comfortable living a
part of their lives online (Rosenblum, 2007). However, Facebook has continually introduced new
features and services including the Newsfeed, Facebook Beacon, Facebook Advertisements and
Facebook Platform, which subsequently lead to changes in the privacy settings and the privacy
policy (less privacy) (Fletcher, 2010). With each additional expansion to the website has come a
growing level of discontent and concern and a general feeling that ‘the company was eroding
privacy and making substantial information public’ (Rothery, 2010).
friend’s name or picture. Lastly, breaches can be caused by third party applications installed by
users. These applications can be a threat to users, especially if they are not from a trusted
provider. When the application accesses the users’ personal information, others can obtain this
information. Novak and Li (2012) also claimed that privacy breaches can be caused by friends,
applications, and exploitation of personal information details by the service providers for
advertising. The authors added that understanding privacy settings is not enough to protect users,
especially from friends and other online social network users. Thus, social networking websites
such as Facebook prioritize the development of tools to protect privacy. This is manifested in the
social network providers’ requests for new users to create new privacy settings. However, some
users do not realize the risk of leakage of personal information (Lee et al. 2011). Therefore,
sensitive information such as home address and date of birth should not be published online in
order to avoid risks to online privacy. Increasing user awareness of these risks, providing a
privacy management system for users to control their personal information details, and
constantly updating privacy policies can lead to a decline of these risks (Gharibi&Shaabi 2012).
In addition, O’Brien and Torres 2012 wrote an article named Social Networking and Online
Privacy: Facebook Users’ Perceptions. As a result, the researchers found that Facebook users are
alert and cautious when using the social networking sites. However, Facebook users are not
completely informed or aware of all activities concerning privacy on the social networking sites.
Though, low trust levels to date have not hindered activity on Facebook and membership
continues to rise. Facebook users seem willing to push aside trust issues to achieve social
interaction. The importance of trust in a social networking context is clearly questionable and
perhaps different determinants for online activity exist in different online environments. There
are a number of barriers to trust in the online environment. These barriers include perceived risk,
website design and content, the user themselves and privacy concerns. Privacy concerns are
considered the greatest barrier of them all because ‘the internet, by design, lacks unified
provisions for identifying who communicates with whom; it lacks a well-designed identity
infrastructure’ (Leenes et al., 2008). Privacy concerns include online information collection
techniques such as cookie technology involving extreme surveillance. The use and analysis of
data are also a concern due to unethical merging and data mining practices to profile customers.
The instant recording and permanence of activity, loss of control and ownership of data also
creates barriers to online activity (Tavani, 2011). Social networking users claim to be concerned
about risks to privacy, yet do little to safeguard their information (Dwyer et al., 2007). Often
users openly disclose detailed and personal information on these networks, comfortable living a
part of their lives online (Rosenblum, 2007). However, Facebook has continually introduced new
features and services including the Newsfeed, Facebook Beacon, Facebook Advertisements and
Facebook Platform, which subsequently lead to changes in the privacy settings and the privacy
policy (less privacy) (Fletcher, 2010). With each additional expansion to the website has come a
growing level of discontent and concern and a general feeling that ‘the company was eroding
privacy and making substantial information public’ (Rothery, 2010).

Online privacy protection
Privacy settings, that allow the user to control the profile view and distribution of personal data,
vary across social networking websites, and there is no privacy standard for controlling the
user’s personal information settings. Although privacy settings should be chosen carefully, most
online social network providers have complex privacy settings (Novak & Li 2012). These
complex privacy settings may cause confusion among users (Gundecha, Barbier& Liu 2011).
Different techniques have been designed to increase personal information privacy protection.
Williams et al. (2009) listed some steps for online social network users to stay safe. These
included: being aware of the risks of social networks, limiting the posting of personal
information details, and being careful when dealing with strangers online or when reading any
information from any sender. Most social networking sites have given their users more authority
to control privacy settings. Users of some social networking sites are now able to classify their
friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010)
designed a privacy recommendation wizard based on user inputs to help users classify their
friend list into sub-lists. The wizard gives the user two options: to allow the friends in their sub-
list to see their personal information, or to deny them access to this information. Configuring
privacy settings so that only friends can see your posts is not enough to defend oneself from
other attacks such as applications and advertisements (Stutzman& Kramer-Duffield 2010).
Lipford, Besmer and Watson (2008) found that showing an example of privacy settings
International Journal of Security, Privacy and Trust Management ( IJSPTM) vol 2, No 2, April
2013 6 will enable users to understand their privacy settings better. It will also help them find out
who can see their personal information. For instance, Facebook allows users to see their profiles
from their friends’ point of view; this allows users to see what personal information their friends
can see. This technique helps users understand privacy settings but does not provide security to
protect them from neighbourhood attacks or other types of attacks such as viruses or spam. Fang
and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions.
It guides users in choosing privacy settings for group or individual users by allowing the users to
see or hide an item. For example, if Alice is Bob’s friend, then Bob can identify which items of
his profile Alice can see. Bob can hide some details such as his date of birth and mobile number
from Alice, and can do the same for his other friends.
There has been some previous work attempting to apply nudging to computer security. For
instance, Brustoloni et al. developed security dialogs in which users were held accountable for
their decisions to open email attachments. Those who took unjustified risks could be “subject to
a variety of sanctions, such as being unable to use the application for increasing periods of
time...” A user study found that these dialogs resulted in significantly fewer unjustified risks
[35]. An approach similar to nudging can be found in persuasive computing, a sub-field of
computer science concerned with systems intentionally designed to “change a person’s attitude
or behavior in a predetermined way” [37]. Persuasive technologies have been applied in specific
domains including computer security. For instance, Forget et al. built a text password system that
encourages users to create stronger text password [38]. A number of mechanisms have been
Privacy settings, that allow the user to control the profile view and distribution of personal data,
vary across social networking websites, and there is no privacy standard for controlling the
user’s personal information settings. Although privacy settings should be chosen carefully, most
online social network providers have complex privacy settings (Novak & Li 2012). These
complex privacy settings may cause confusion among users (Gundecha, Barbier& Liu 2011).
Different techniques have been designed to increase personal information privacy protection.
Williams et al. (2009) listed some steps for online social network users to stay safe. These
included: being aware of the risks of social networks, limiting the posting of personal
information details, and being careful when dealing with strangers online or when reading any
information from any sender. Most social networking sites have given their users more authority
to control privacy settings. Users of some social networking sites are now able to classify their
friend list into sub-lists, which allows some personal information details, such as birthday or
relationship status, to be visible to one sub-list and hidden from others. Fang et al. (2010)
designed a privacy recommendation wizard based on user inputs to help users classify their
friend list into sub-lists. The wizard gives the user two options: to allow the friends in their sub-
list to see their personal information, or to deny them access to this information. Configuring
privacy settings so that only friends can see your posts is not enough to defend oneself from
other attacks such as applications and advertisements (Stutzman& Kramer-Duffield 2010).
Lipford, Besmer and Watson (2008) found that showing an example of privacy settings
International Journal of Security, Privacy and Trust Management ( IJSPTM) vol 2, No 2, April
2013 6 will enable users to understand their privacy settings better. It will also help them find out
who can see their personal information. For instance, Facebook allows users to see their profiles
from their friends’ point of view; this allows users to see what personal information their friends
can see. This technique helps users understand privacy settings but does not provide security to
protect them from neighbourhood attacks or other types of attacks such as viruses or spam. Fang
and Lefevre (2010) designed a privacy wizard system to make it easier for users to control their
privacy settings. It was designed based on friends classification to groups and asking questions.
It guides users in choosing privacy settings for group or individual users by allowing the users to
see or hide an item. For example, if Alice is Bob’s friend, then Bob can identify which items of
his profile Alice can see. Bob can hide some details such as his date of birth and mobile number
from Alice, and can do the same for his other friends.
There has been some previous work attempting to apply nudging to computer security. For
instance, Brustoloni et al. developed security dialogs in which users were held accountable for
their decisions to open email attachments. Those who took unjustified risks could be “subject to
a variety of sanctions, such as being unable to use the application for increasing periods of
time...” A user study found that these dialogs resulted in significantly fewer unjustified risks
[35]. An approach similar to nudging can be found in persuasive computing, a sub-field of
computer science concerned with systems intentionally designed to “change a person’s attitude
or behavior in a predetermined way” [37]. Persuasive technologies have been applied in specific
domains including computer security. For instance, Forget et al. built a text password system that
encourages users to create stronger text password [38]. A number of mechanisms have been
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

proposed to help users better protect their privacy in social media. Fang et al. designed a privacy
wizard that asks users to iterate over privacy settings for some of their friends. Based on this
information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact
settings in the form of expandable grids to visual policies. They found that both alternatives were
usable, but different users appreciated them for different reasons [40]. While most previous work
on privacy protections for social media has focused on helping users adjust their settings up
front, our work employs tools that encourage real-time adjustments during or immediately
following the composition of a Facebook post.
wizard that asks users to iterate over privacy settings for some of their friends. Based on this
information, a classifier could be built automatically to categorize the remaining friends [36].
Lipford et al. investigated interfaces for social network privacy controls, comparing compact
settings in the form of expandable grids to visual policies. They found that both alternatives were
usable, but different users appreciated them for different reasons [40]. While most previous work
on privacy protections for social media has focused on helping users adjust their settings up
front, our work employs tools that encourage real-time adjustments during or immediately
following the composition of a Facebook post.

Research Methodology
In this chapter, the research objective, process, research approach, methods, and instruments
used for selection of respondents and data analysis of this research are described.
Research objectives
This report is an attempt to understand how the public sector applies TM practices and initiatives
in UAE.
Many business leaders in the Middle East now understands the significance of talents in the
organization, hence, in order to be able to manage them properly, they need to put them in their
top agenda priorities. This study aims to understand how TM is perceived in the UAE and what
are the initiatives and practice that are currently undertaken. The study focuses on the public
sector organization. Moreover, the research will provide a response to the research questions in
chapter 1 of the introduction.
Purpose of research
The UAE is considered one of the preferred locations for expatriate, and since the number of
UAE nationals is increasing in the market, there is a need to manage and develop talent in the
UAE. This is considered a major push for this report.
The aim of writing a research is either to discover a new phenomenon or provide an
understanding of existing complex phenomena. Research questions determine the research
direction whether it need to describe phenomena, quantify or analyze correlations, hence the
researcher need to select the appropriate research method to adapt the purpose (Peter Strang,
2000).
In this chapter, the research objective, process, research approach, methods, and instruments
used for selection of respondents and data analysis of this research are described.
Research objectives
This report is an attempt to understand how the public sector applies TM practices and initiatives
in UAE.
Many business leaders in the Middle East now understands the significance of talents in the
organization, hence, in order to be able to manage them properly, they need to put them in their
top agenda priorities. This study aims to understand how TM is perceived in the UAE and what
are the initiatives and practice that are currently undertaken. The study focuses on the public
sector organization. Moreover, the research will provide a response to the research questions in
chapter 1 of the introduction.
Purpose of research
The UAE is considered one of the preferred locations for expatriate, and since the number of
UAE nationals is increasing in the market, there is a need to manage and develop talent in the
UAE. This is considered a major push for this report.
The aim of writing a research is either to discover a new phenomenon or provide an
understanding of existing complex phenomena. Research questions determine the research
direction whether it need to describe phenomena, quantify or analyze correlations, hence the
researcher need to select the appropriate research method to adapt the purpose (Peter Strang,
2000).

3.3 Scope of research
This research is implemented especially in UAE.
Talent is an important thing to be managed by companies all over the world. The productivity of
employees and business competitiveness determines the sustainability of nation in the long term.
When companies adopt best practices of talent management along with local knowledge, then it
can attract more people, retain them and motivate them. This is practiced with both the domestic
employees and expatriates. So, it is challenging for companies in UAE to acquire the right
people so they should attract quality employees because UAE is considered one of the preferred
locations for expatriate and since the number of UAE nationals is increasing in the market there
is a need to manage and develop talent in the UAE. They must select the best person available
and fill the critical roles of business first. The businesses of UAE need to be good in selecting
people, staffing them and training them. Those people should be recruited who are willing to
share their values and adopt new ways of working. Talent management fails when people in the
organisations are not aligned with their critical roles and as per the strategic priorities, and hence,
the rewards are not properly aligned (SME Advisor Middle East, 2013). The working people of
UAE are diverse, and they are drawn from throughout the world. The local businesses in UAE
invest in people, lead them properly and manage them effectively so that an efficient and
productive organisation can be built. The HR budgets in the companies of UAE are often
imbalanced; they focus on those initiatives that address the under-performance of employees and
not on the long-term investments on people development. The organisations who give rewards to
employees for their correct behaviour as a tool for performance management are one of the most
successful companies. One more challenge is faced by the companies in UAE that is to find ways
by which they can combine the traditional process of decision making with the governance
standards internationally (SME Advisor Middle East, 2013). The companies in Emirates have
the capability to improve their decision making. To manage the talent in UAE, the companies
adopt two types of strategies, both for short-term and for the long-term. In the short term,
monetary benefits are provided to employees for their performance and in the long term, the
growth of the organisation is emphasised in which the employees are given job security so that
when the company grows, the workforce does not cut down.
Hence, this research will give a perspective to UAE about how the public sector applies TM
practices and initiatives and where is the scope for improvements.
Research Design
There are two main research methods quantitative and qualitative. Each research method has its
own feature which justifies the purpose and outcome of the study (David Trafimow, 2014). For
this study, a qualitative approach was implemented based on the nature of the study and required
data. In-depth interviews were conducted to gain an understating towards the core beliefs and
philosophy that is currently running in the public sector. The researcher was able to
communicate directly with the participants and allowed them to respond in their own words
which reflected their experience and feelings. Burges (1982) cited that in-depth interviews
This research is implemented especially in UAE.
Talent is an important thing to be managed by companies all over the world. The productivity of
employees and business competitiveness determines the sustainability of nation in the long term.
When companies adopt best practices of talent management along with local knowledge, then it
can attract more people, retain them and motivate them. This is practiced with both the domestic
employees and expatriates. So, it is challenging for companies in UAE to acquire the right
people so they should attract quality employees because UAE is considered one of the preferred
locations for expatriate and since the number of UAE nationals is increasing in the market there
is a need to manage and develop talent in the UAE. They must select the best person available
and fill the critical roles of business first. The businesses of UAE need to be good in selecting
people, staffing them and training them. Those people should be recruited who are willing to
share their values and adopt new ways of working. Talent management fails when people in the
organisations are not aligned with their critical roles and as per the strategic priorities, and hence,
the rewards are not properly aligned (SME Advisor Middle East, 2013). The working people of
UAE are diverse, and they are drawn from throughout the world. The local businesses in UAE
invest in people, lead them properly and manage them effectively so that an efficient and
productive organisation can be built. The HR budgets in the companies of UAE are often
imbalanced; they focus on those initiatives that address the under-performance of employees and
not on the long-term investments on people development. The organisations who give rewards to
employees for their correct behaviour as a tool for performance management are one of the most
successful companies. One more challenge is faced by the companies in UAE that is to find ways
by which they can combine the traditional process of decision making with the governance
standards internationally (SME Advisor Middle East, 2013). The companies in Emirates have
the capability to improve their decision making. To manage the talent in UAE, the companies
adopt two types of strategies, both for short-term and for the long-term. In the short term,
monetary benefits are provided to employees for their performance and in the long term, the
growth of the organisation is emphasised in which the employees are given job security so that
when the company grows, the workforce does not cut down.
Hence, this research will give a perspective to UAE about how the public sector applies TM
practices and initiatives and where is the scope for improvements.
Research Design
There are two main research methods quantitative and qualitative. Each research method has its
own feature which justifies the purpose and outcome of the study (David Trafimow, 2014). For
this study, a qualitative approach was implemented based on the nature of the study and required
data. In-depth interviews were conducted to gain an understating towards the core beliefs and
philosophy that is currently running in the public sector. The researcher was able to
communicate directly with the participants and allowed them to respond in their own words
which reflected their experience and feelings. Burges (1982) cited that in-depth interviews
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

method is considered one of the main methods of the qualitative approach as it has been referred
as the form of conversations. Sidney and Beatrice also refer to it as conversations with purpose
(Webb, 1930). The difference between the normal conversation and the interviews is that the
interviews are based on objectives (Kvale, 1996, Rubin and Rubin, 1995). However in some
cases, it tends to be little resemblance to everyday conversation.
as the form of conversations. Sidney and Beatrice also refer to it as conversations with purpose
(Webb, 1930). The difference between the normal conversation and the interviews is that the
interviews are based on objectives (Kvale, 1996, Rubin and Rubin, 1995). However in some
cases, it tends to be little resemblance to everyday conversation.

Research Methods
The ongoing changes in the technology and sociology and anthropology context have emerges
the need to find an alternative research method for the management research (Pettigrew, 1990).
However in order to find a permanent solution for these challenges new research method needs
to be developed to address such complex issues, and for such complexity the qualitative research
is essential (Gummesson, 2006, pp. 170-171). The qualitative method is available for the social
and human scientist for years (Creswell. J W, 2003).
Pope and Mays (1995) stated that the qualitative research can accomplish objectives that cannot
be met by the other research methods. It aims to answer the question that is related to ‘what,'
‘how' and ‘who' of the phenomena (Green & Thorogood, 2004). Although the qualitative is
difficult (Hitchcock& Hughes, 1995. pp 26) to be defined a generic definition has been formed
by Denzin and Lincoln (2005a, p.3) Qualitative research is a "situated activity that locates the
observer in the world. It consists of a set of interpretive, material practices that make the world
visible. These practices transform the world. They turn the world into a series of representations,
including field notes, interviews, conversations, photographs, recordings, and memos to the self".
At this level, qualitative research involves an interpretive, naturalistic approach to the world.
This means that the qualitative researches study things in their natural settings, attempting to
make sense of, or interpret, phenomena in terms of the meaning people bring to them’.
Some of the important features of the qualitative approach are that does not base the analysis
based on the researcher experience (Mills, 1959, pp.195-226). Thus, all the gathered data are in
the natural setting similar to the actual or real life situation, rather that collecting the information
through mail or phone (Miles and Huberman, 1994 .pp 10). Therefore, this is the preferred
method for management researches such as social sciences studies such as sociology
anthropology, linguistics, and history (Sanday, 1979; Van Maanen, 1988; Manning, 1979;
Tuchman, 1994).
On the other hand, the quantitative research method is emerged in the last three decades
(Creswell. J W, 2003). It can be defined as the method that explains phenomena is a numerical
data which is later analyzed by mathematically based methods such as statistics (Creswell, 1994;
Gary&Airasian, 2000). Hence, the participant's responses are analyzed in a statistical
aggregation. Normally for this research close-ended questions are ideal as they can help in
identifying the pattern in the participant's responses and understand the participant's reactions.
When discussing the characteristics of the quantitative and qualitative research tools, there are
four different research process elements that need to be addressed such as epistemology,
theoretical perspective, methodology and methods (Crotty.1998). When conducted a study there
are four issues that structure the designs the research, which are the paradigm, what or who will
be studied, the strategies used and the selected tool (Denzin and Lincoln, 1998). Both types of
research methods are different in terms of their epistemological, theoretical and methodological
substructures. The quantitative research method is usually informed by objective epistemology
thus it intends to discuss social behaviors by measuring it statistically and analysis the
The ongoing changes in the technology and sociology and anthropology context have emerges
the need to find an alternative research method for the management research (Pettigrew, 1990).
However in order to find a permanent solution for these challenges new research method needs
to be developed to address such complex issues, and for such complexity the qualitative research
is essential (Gummesson, 2006, pp. 170-171). The qualitative method is available for the social
and human scientist for years (Creswell. J W, 2003).
Pope and Mays (1995) stated that the qualitative research can accomplish objectives that cannot
be met by the other research methods. It aims to answer the question that is related to ‘what,'
‘how' and ‘who' of the phenomena (Green & Thorogood, 2004). Although the qualitative is
difficult (Hitchcock& Hughes, 1995. pp 26) to be defined a generic definition has been formed
by Denzin and Lincoln (2005a, p.3) Qualitative research is a "situated activity that locates the
observer in the world. It consists of a set of interpretive, material practices that make the world
visible. These practices transform the world. They turn the world into a series of representations,
including field notes, interviews, conversations, photographs, recordings, and memos to the self".
At this level, qualitative research involves an interpretive, naturalistic approach to the world.
This means that the qualitative researches study things in their natural settings, attempting to
make sense of, or interpret, phenomena in terms of the meaning people bring to them’.
Some of the important features of the qualitative approach are that does not base the analysis
based on the researcher experience (Mills, 1959, pp.195-226). Thus, all the gathered data are in
the natural setting similar to the actual or real life situation, rather that collecting the information
through mail or phone (Miles and Huberman, 1994 .pp 10). Therefore, this is the preferred
method for management researches such as social sciences studies such as sociology
anthropology, linguistics, and history (Sanday, 1979; Van Maanen, 1988; Manning, 1979;
Tuchman, 1994).
On the other hand, the quantitative research method is emerged in the last three decades
(Creswell. J W, 2003). It can be defined as the method that explains phenomena is a numerical
data which is later analyzed by mathematically based methods such as statistics (Creswell, 1994;
Gary&Airasian, 2000). Hence, the participant's responses are analyzed in a statistical
aggregation. Normally for this research close-ended questions are ideal as they can help in
identifying the pattern in the participant's responses and understand the participant's reactions.
When discussing the characteristics of the quantitative and qualitative research tools, there are
four different research process elements that need to be addressed such as epistemology,
theoretical perspective, methodology and methods (Crotty.1998). When conducted a study there
are four issues that structure the designs the research, which are the paradigm, what or who will
be studied, the strategies used and the selected tool (Denzin and Lincoln, 1998). Both types of
research methods are different in terms of their epistemological, theoretical and methodological
substructures. The quantitative research method is usually informed by objective epistemology
thus it intends to discuss social behaviors by measuring it statistically and analysis the

relationship between the variables in a framework that is value free, logical, deterministic.
Therefore, there is a distance between the researcher and what is being studied.
However, the qualitative is based on a constructivist epistemology that explores the social
reality in a framework that is value based, flexible, holistic and context sensitive. Therefore, the
description of the phenomena is from the people perspective who are involved study. Therefore,
the researcher builds a close or empathic relationship with the subject that are studied (Bergman,
Data collection:
Data was collected using primary and secondary sources. In a primary method, 14 face to face
interviews are conducted in a government organization (GHA), the responses were recorded and
analyzed. Also, various secondary sources were used to journals, articles, books, and thesis or
research work published by various researchers (mentioned in the literature review).
Therefore, there is a distance between the researcher and what is being studied.
However, the qualitative is based on a constructivist epistemology that explores the social
reality in a framework that is value based, flexible, holistic and context sensitive. Therefore, the
description of the phenomena is from the people perspective who are involved study. Therefore,
the researcher builds a close or empathic relationship with the subject that are studied (Bergman,
Data collection:
Data was collected using primary and secondary sources. In a primary method, 14 face to face
interviews are conducted in a government organization (GHA), the responses were recorded and
analyzed. Also, various secondary sources were used to journals, articles, books, and thesis or
research work published by various researchers (mentioned in the literature review).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
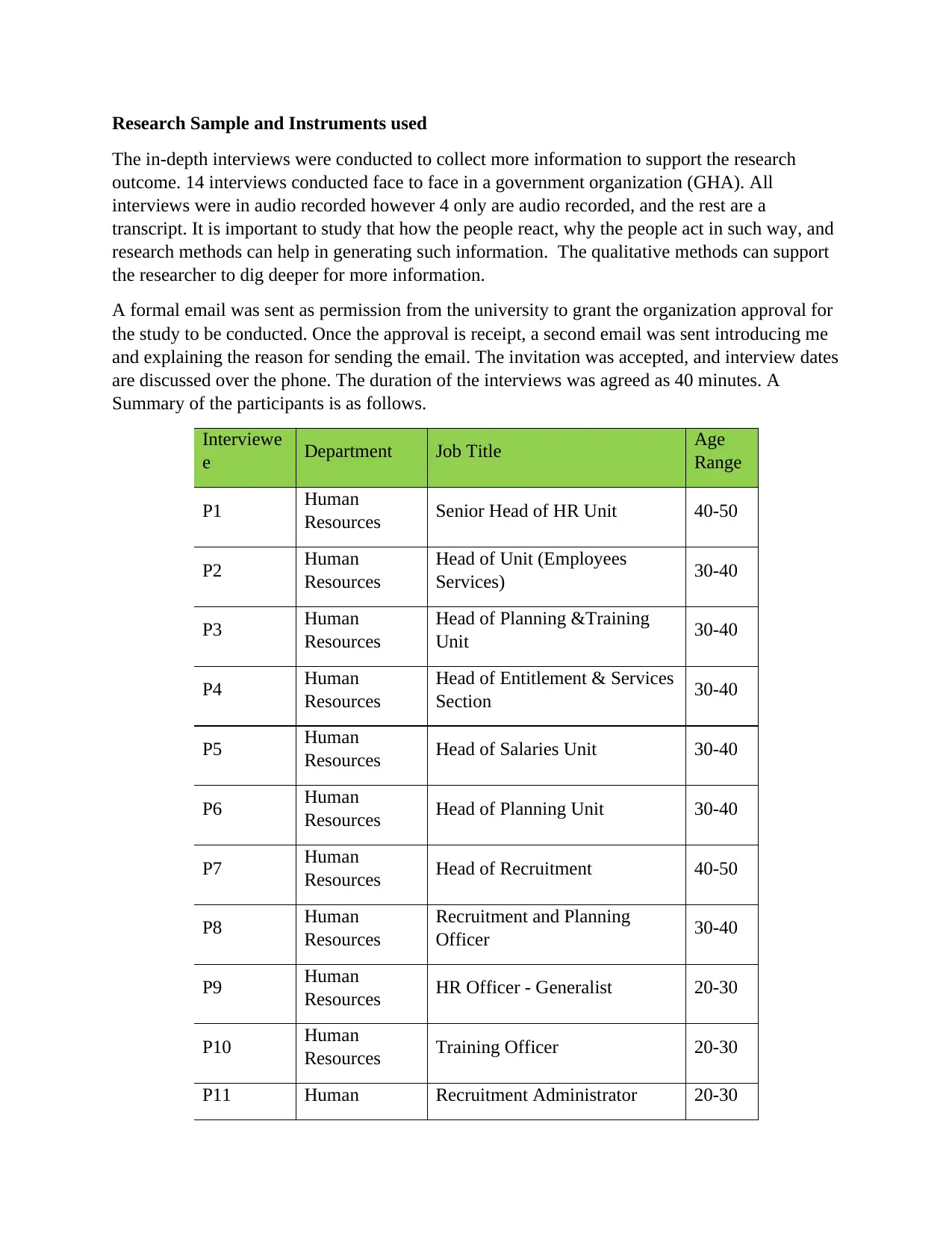
Research Sample and Instruments used
The in-depth interviews were conducted to collect more information to support the research
outcome. 14 interviews conducted face to face in a government organization (GHA). All
interviews were in audio recorded however 4 only are audio recorded, and the rest are a
transcript. It is important to study that how the people react, why the people act in such way, and
research methods can help in generating such information. The qualitative methods can support
the researcher to dig deeper for more information.
A formal email was sent as permission from the university to grant the organization approval for
the study to be conducted. Once the approval is receipt, a second email was sent introducing me
and explaining the reason for sending the email. The invitation was accepted, and interview dates
are discussed over the phone. The duration of the interviews was agreed as 40 minutes. A
Summary of the participants is as follows.
Interviewe
e Department Job Title Age
Range
P1 Human
Resources Senior Head of HR Unit 40-50
P2 Human
Resources
Head of Unit (Employees
Services) 30-40
P3 Human
Resources
Head of Planning &Training
Unit 30-40
P4 Human
Resources
Head of Entitlement & Services
Section 30-40
P5 Human
Resources Head of Salaries Unit 30-40
P6 Human
Resources Head of Planning Unit 30-40
P7 Human
Resources Head of Recruitment 40-50
P8 Human
Resources
Recruitment and Planning
Officer 30-40
P9 Human
Resources HR Officer - Generalist 20-30
P10 Human
Resources Training Officer 20-30
P11 Human Recruitment Administrator 20-30
The in-depth interviews were conducted to collect more information to support the research
outcome. 14 interviews conducted face to face in a government organization (GHA). All
interviews were in audio recorded however 4 only are audio recorded, and the rest are a
transcript. It is important to study that how the people react, why the people act in such way, and
research methods can help in generating such information. The qualitative methods can support
the researcher to dig deeper for more information.
A formal email was sent as permission from the university to grant the organization approval for
the study to be conducted. Once the approval is receipt, a second email was sent introducing me
and explaining the reason for sending the email. The invitation was accepted, and interview dates
are discussed over the phone. The duration of the interviews was agreed as 40 minutes. A
Summary of the participants is as follows.
Interviewe
e Department Job Title Age
Range
P1 Human
Resources Senior Head of HR Unit 40-50
P2 Human
Resources
Head of Unit (Employees
Services) 30-40
P3 Human
Resources
Head of Planning &Training
Unit 30-40
P4 Human
Resources
Head of Entitlement & Services
Section 30-40
P5 Human
Resources Head of Salaries Unit 30-40
P6 Human
Resources Head of Planning Unit 30-40
P7 Human
Resources Head of Recruitment 40-50
P8 Human
Resources
Recruitment and Planning
Officer 30-40
P9 Human
Resources HR Officer - Generalist 20-30
P10 Human
Resources Training Officer 20-30
P11 Human Recruitment Administrator 20-30
Resources
P12 Human
Resources Recruitment Administrator 30-40
P13 Human
Resources Administrator Scrutinize 20-30
P14 Human
Resources Administrator Recruitment Unit 20-30
Data analysis technique
Data was analyzed using the findings and conclusion of the following studies conducted in
similar area in UAE and by personal judgments and observations from the interviews conducted.
In a study conducted by Towers Watson and Oxford Economics (Talent 2021), it was found that
the Middle East will grow more than 13 percent in terms of volume of talent that will be
demanded the companies in that region. The rapid globalisation and changing models of business
have impacted the organisations and the needs of people. With all these changes happening, the
demand for more talent is growing in UAE too. The companies need to address the loyalty of
employees and their engagement so that they don't export their skills to other markets and the
competitors. New skills are required at the time when business is transforming. Transformation
happens as companies rethink about their global strategies, they wish to change their business
models, and they take different organisational approaches. While transforming, the company
need to reposition the skills of employees and manage the varied talents across all seniority
levels. Organisations also address the miss-match between the talents within the company. In this
developed world, talent shortages are persisting especially in the managerial and technical areas
and thus companies have to think more explicitly about whether to outsource the work, offshore
the employees or retrain the workers. The source of talents and expectations related to the
requirements of talent is also evolving. The emphasis to work in different countries has increased
because of the career that people take up. There is a shift in the place where the talent works and
the way he works; there is the higher frequency of alternate work schedules and locations of
work that may also include virtual workplaces.
Hay group which is a popular company has a separate policy for talent management. The
company says that the cost per employee with high potential is huge. The business of leadership
and development is also costly (Haygroup.com, 2016). Whatever the company invests in the
talent of people, it does not get proper returns. To earn proper ROI, the companies must assure
the development is building the capabilities of people that are required to fill most critical roles
in the organizations. Organization poorly manages the talent when they don't understand the
roles of people properly and for what development experiences they are destined. This leads to
wastage of development budget, and the high potentials are not prepared adequately. Hay group
has designed a mission critical career path which helps in targeting the right people for right
jobs. Future leaders are built who possess correct skill set required at the right time. This enables
P12 Human
Resources Recruitment Administrator 30-40
P13 Human
Resources Administrator Scrutinize 20-30
P14 Human
Resources Administrator Recruitment Unit 20-30
Data analysis technique
Data was analyzed using the findings and conclusion of the following studies conducted in
similar area in UAE and by personal judgments and observations from the interviews conducted.
In a study conducted by Towers Watson and Oxford Economics (Talent 2021), it was found that
the Middle East will grow more than 13 percent in terms of volume of talent that will be
demanded the companies in that region. The rapid globalisation and changing models of business
have impacted the organisations and the needs of people. With all these changes happening, the
demand for more talent is growing in UAE too. The companies need to address the loyalty of
employees and their engagement so that they don't export their skills to other markets and the
competitors. New skills are required at the time when business is transforming. Transformation
happens as companies rethink about their global strategies, they wish to change their business
models, and they take different organisational approaches. While transforming, the company
need to reposition the skills of employees and manage the varied talents across all seniority
levels. Organisations also address the miss-match between the talents within the company. In this
developed world, talent shortages are persisting especially in the managerial and technical areas
and thus companies have to think more explicitly about whether to outsource the work, offshore
the employees or retrain the workers. The source of talents and expectations related to the
requirements of talent is also evolving. The emphasis to work in different countries has increased
because of the career that people take up. There is a shift in the place where the talent works and
the way he works; there is the higher frequency of alternate work schedules and locations of
work that may also include virtual workplaces.
Hay group which is a popular company has a separate policy for talent management. The
company says that the cost per employee with high potential is huge. The business of leadership
and development is also costly (Haygroup.com, 2016). Whatever the company invests in the
talent of people, it does not get proper returns. To earn proper ROI, the companies must assure
the development is building the capabilities of people that are required to fill most critical roles
in the organizations. Organization poorly manages the talent when they don't understand the
roles of people properly and for what development experiences they are destined. This leads to
wastage of development budget, and the high potentials are not prepared adequately. Hay group
has designed a mission critical career path which helps in targeting the right people for right
jobs. Future leaders are built who possess correct skill set required at the right time. This enables

the people to get clear about what roles are critical in the company, what are the career
accelerators that prepare employees for some roles quickly and efficiently. To manage the talent
in an effective manner, the company has identified destination roles which are the most
important roles to drive the strategy of the company; they have defined the career experiences of
people and the skills that are required to move people in these key roles. The company has
mapped the career paths which helped the high potentials to move smoothly from earlier roles to
destination roles. The company has created some development programs to support the
employees with highest potential to move on their journey of a career (Haygroup.com, 2016).
The government organizations in UAE have been facing a war over talent, but when TM occurs,
the competitive advantage of companies in the market improves. Hence, it is necessary for
companies to transform and make use of TM extensively. It can retain the talents by rewarding
them appropriately, providing those with benefits, identifying and developing proper career paths
for them and by doing proper succession planning. Companies need to conduct a performance
management exercise so that different issues can be identified and individual talents can be
determined too. There are various recruitment events in which more talent can be attracted like
career fairs which also helps in increasing the pool for selection of high potential candidates.
These were the main researches that were reviewed to reach the findings of the current study and
the interview analysis is discussed in the data analysis part where some graphs and bar charts
were used to display the results.
accelerators that prepare employees for some roles quickly and efficiently. To manage the talent
in an effective manner, the company has identified destination roles which are the most
important roles to drive the strategy of the company; they have defined the career experiences of
people and the skills that are required to move people in these key roles. The company has
mapped the career paths which helped the high potentials to move smoothly from earlier roles to
destination roles. The company has created some development programs to support the
employees with highest potential to move on their journey of a career (Haygroup.com, 2016).
The government organizations in UAE have been facing a war over talent, but when TM occurs,
the competitive advantage of companies in the market improves. Hence, it is necessary for
companies to transform and make use of TM extensively. It can retain the talents by rewarding
them appropriately, providing those with benefits, identifying and developing proper career paths
for them and by doing proper succession planning. Companies need to conduct a performance
management exercise so that different issues can be identified and individual talents can be
determined too. There are various recruitment events in which more talent can be attracted like
career fairs which also helps in increasing the pool for selection of high potential candidates.
These were the main researches that were reviewed to reach the findings of the current study and
the interview analysis is discussed in the data analysis part where some graphs and bar charts
were used to display the results.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Limitations
Although this study yielded some preliminary findings, there are some limitations of this study.
1. The first limitation is the concerns the organization due to the sensitivity of the
information and since there were under restructuring progress. Hence there was lack of
trust and willingness to share information in details as this might be the first time for
them to have someone from university. However, in each interview I have given a brief
of my study and the purpose of it which at least helped me to conduct the interviews with
all the participants.
2. The second limitation is the number of participants were small as it did not make sense to
interview other department which are not related to the subject I am studying.
3. The third limitation was the language there was a language barriers as all the participants
wanted the interviews to be conducted in Arabic so I had to translate the questions and in
which more explanation of the term was required, in the Arabic language the term talent
have many different meaning in which it had confused the participants while answering
the questions. The third limitation was the term Talent Management is new in the UAE
hence there are many organizations which are not yet familiar with this term in which this
effected the outcome of the study.
Although this study yielded some preliminary findings, there are some limitations of this study.
1. The first limitation is the concerns the organization due to the sensitivity of the
information and since there were under restructuring progress. Hence there was lack of
trust and willingness to share information in details as this might be the first time for
them to have someone from university. However, in each interview I have given a brief
of my study and the purpose of it which at least helped me to conduct the interviews with
all the participants.
2. The second limitation is the number of participants were small as it did not make sense to
interview other department which are not related to the subject I am studying.
3. The third limitation was the language there was a language barriers as all the participants
wanted the interviews to be conducted in Arabic so I had to translate the questions and in
which more explanation of the term was required, in the Arabic language the term talent
have many different meaning in which it had confused the participants while answering
the questions. The third limitation was the term Talent Management is new in the UAE
hence there are many organizations which are not yet familiar with this term in which this
effected the outcome of the study.
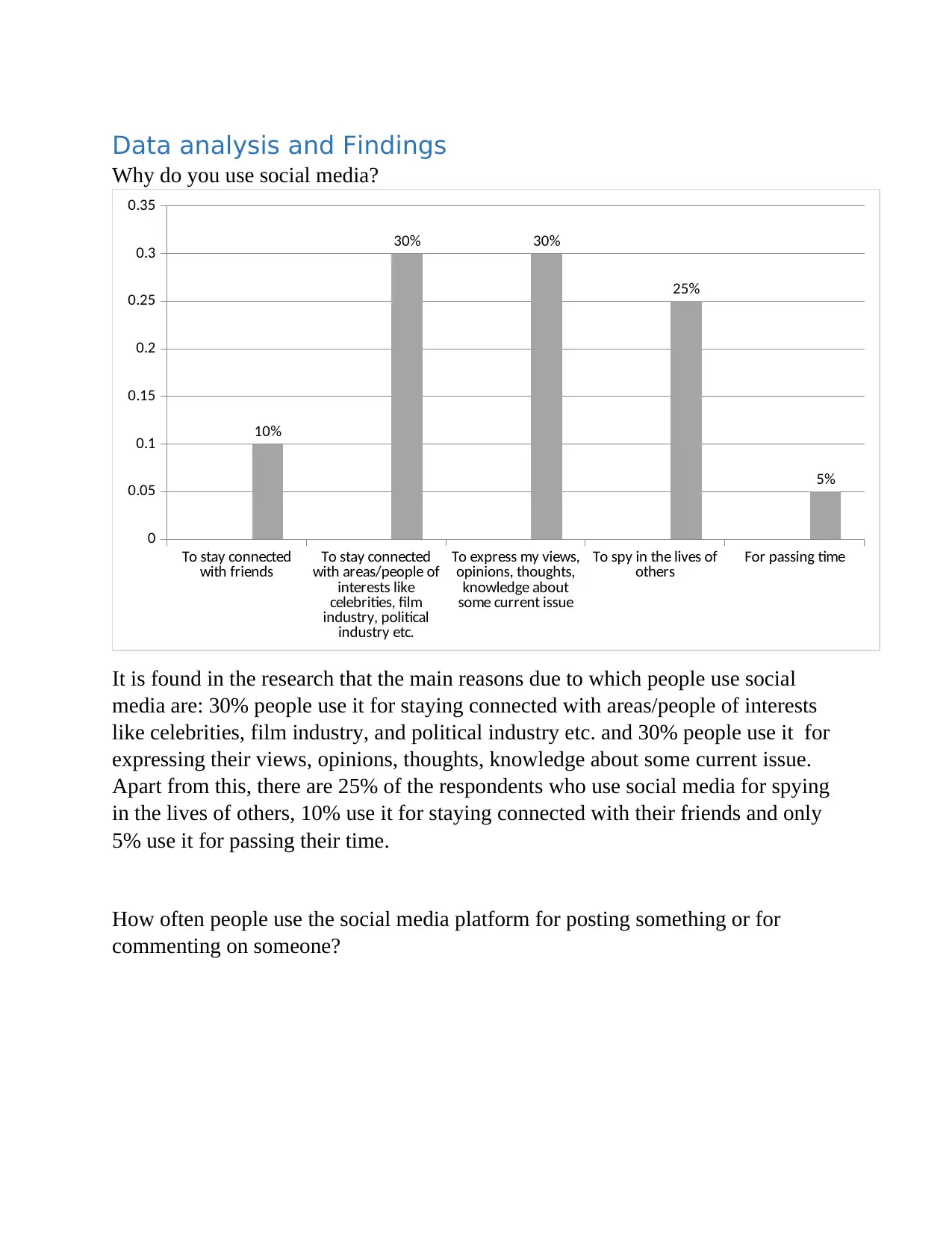
Data analysis and Findings
Why do you use social media?
To stay connected
with friends To stay connected
with areas/people of
interests like
celebrities, film
industry, political
industry etc.
To express my views,
opinions, thoughts,
knowledge about
some current issue
To spy in the lives of
others For passing time
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
10%
30% 30%
25%
5%
It is found in the research that the main reasons due to which people use social
media are: 30% people use it for staying connected with areas/people of interests
like celebrities, film industry, and political industry etc. and 30% people use it for
expressing their views, opinions, thoughts, knowledge about some current issue.
Apart from this, there are 25% of the respondents who use social media for spying
in the lives of others, 10% use it for staying connected with their friends and only
5% use it for passing their time.
How often people use the social media platform for posting something or for
commenting on someone?
Why do you use social media?
To stay connected
with friends To stay connected
with areas/people of
interests like
celebrities, film
industry, political
industry etc.
To express my views,
opinions, thoughts,
knowledge about
some current issue
To spy in the lives of
others For passing time
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
10%
30% 30%
25%
5%
It is found in the research that the main reasons due to which people use social
media are: 30% people use it for staying connected with areas/people of interests
like celebrities, film industry, and political industry etc. and 30% people use it for
expressing their views, opinions, thoughts, knowledge about some current issue.
Apart from this, there are 25% of the respondents who use social media for spying
in the lives of others, 10% use it for staying connected with their friends and only
5% use it for passing their time.
How often people use the social media platform for posting something or for
commenting on someone?
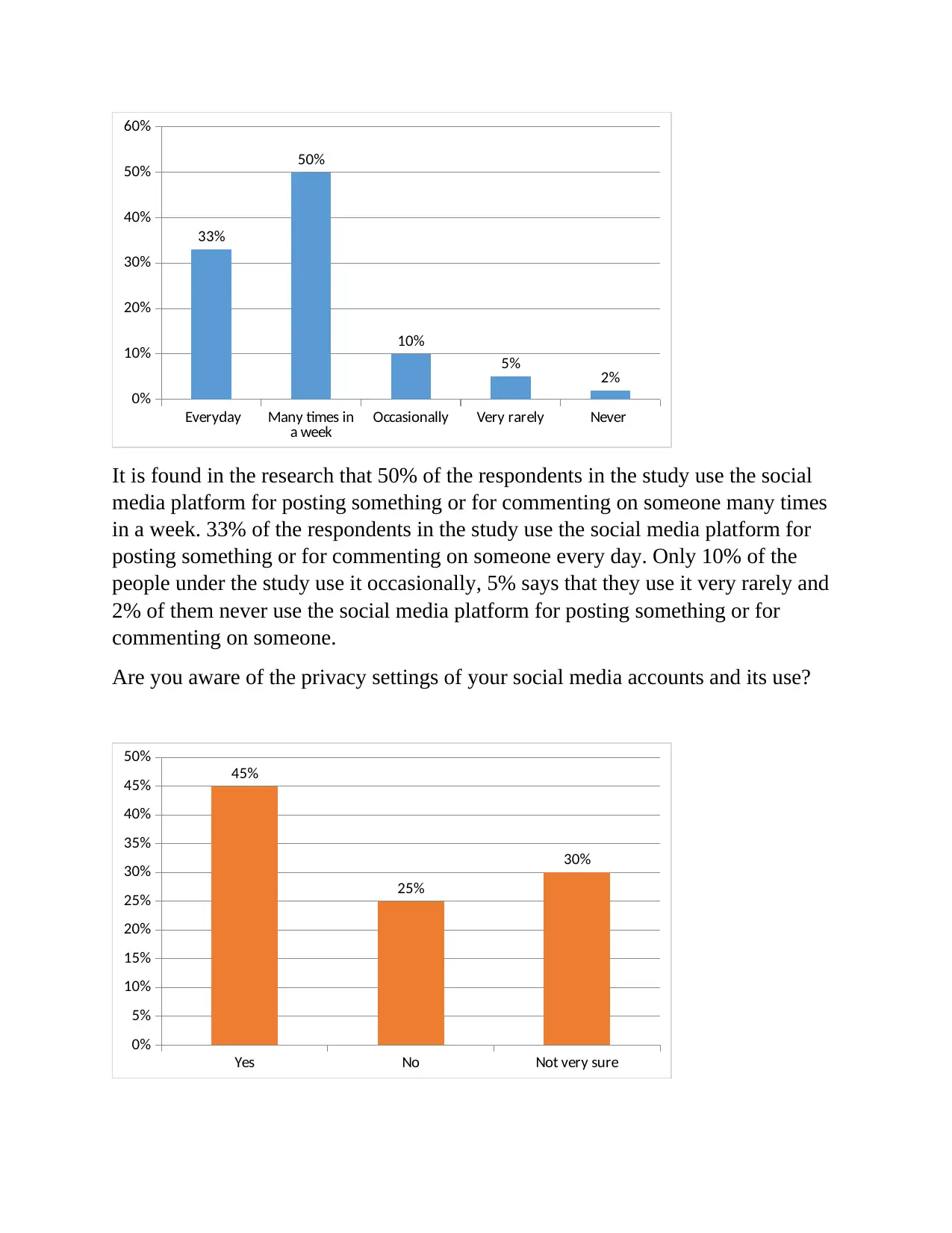
Everyday Many times in
a week Occasionally Very rarely Never
0%
10%
20%
30%
40%
50%
60%
33%
50%
10%
5% 2%
It is found in the research that 50% of the respondents in the study use the social
media platform for posting something or for commenting on someone many times
in a week. 33% of the respondents in the study use the social media platform for
posting something or for commenting on someone every day. Only 10% of the
people under the study use it occasionally, 5% says that they use it very rarely and
2% of them never use the social media platform for posting something or for
commenting on someone.
Are you aware of the privacy settings of your social media accounts and its use?
Yes No Not very sure
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
45%
25%
30%
a week Occasionally Very rarely Never
0%
10%
20%
30%
40%
50%
60%
33%
50%
10%
5% 2%
It is found in the research that 50% of the respondents in the study use the social
media platform for posting something or for commenting on someone many times
in a week. 33% of the respondents in the study use the social media platform for
posting something or for commenting on someone every day. Only 10% of the
people under the study use it occasionally, 5% says that they use it very rarely and
2% of them never use the social media platform for posting something or for
commenting on someone.
Are you aware of the privacy settings of your social media accounts and its use?
Yes No Not very sure
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
45%
25%
30%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
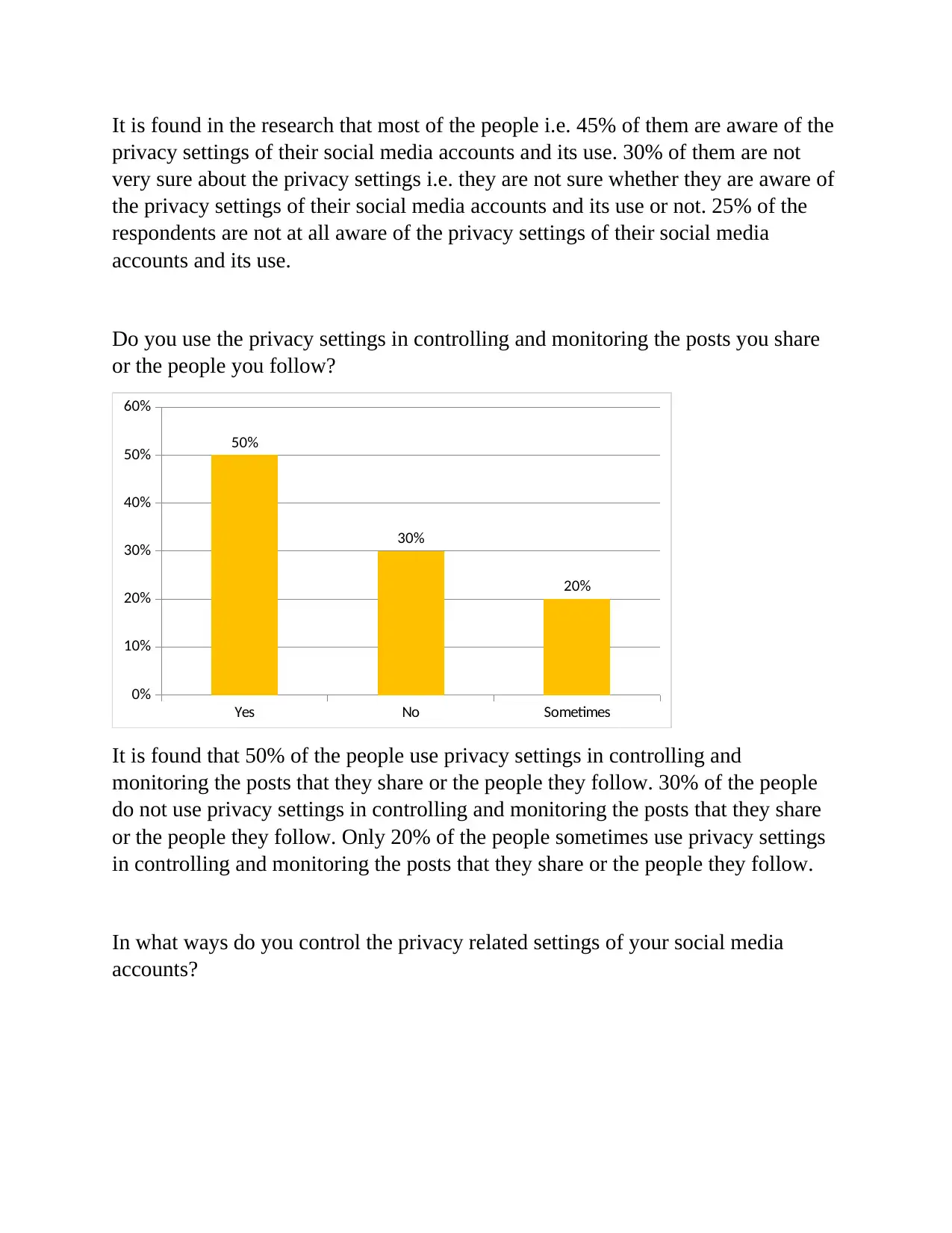
It is found in the research that most of the people i.e. 45% of them are aware of the
privacy settings of their social media accounts and its use. 30% of them are not
very sure about the privacy settings i.e. they are not sure whether they are aware of
the privacy settings of their social media accounts and its use or not. 25% of the
respondents are not at all aware of the privacy settings of their social media
accounts and its use.
Do you use the privacy settings in controlling and monitoring the posts you share
or the people you follow?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
30%
20%
It is found that 50% of the people use privacy settings in controlling and
monitoring the posts that they share or the people they follow. 30% of the people
do not use privacy settings in controlling and monitoring the posts that they share
or the people they follow. Only 20% of the people sometimes use privacy settings
in controlling and monitoring the posts that they share or the people they follow.
In what ways do you control the privacy related settings of your social media
accounts?
privacy settings of their social media accounts and its use. 30% of them are not
very sure about the privacy settings i.e. they are not sure whether they are aware of
the privacy settings of their social media accounts and its use or not. 25% of the
respondents are not at all aware of the privacy settings of their social media
accounts and its use.
Do you use the privacy settings in controlling and monitoring the posts you share
or the people you follow?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
30%
20%
It is found that 50% of the people use privacy settings in controlling and
monitoring the posts that they share or the people they follow. 30% of the people
do not use privacy settings in controlling and monitoring the posts that they share
or the people they follow. Only 20% of the people sometimes use privacy settings
in controlling and monitoring the posts that they share or the people they follow.
In what ways do you control the privacy related settings of your social media
accounts?
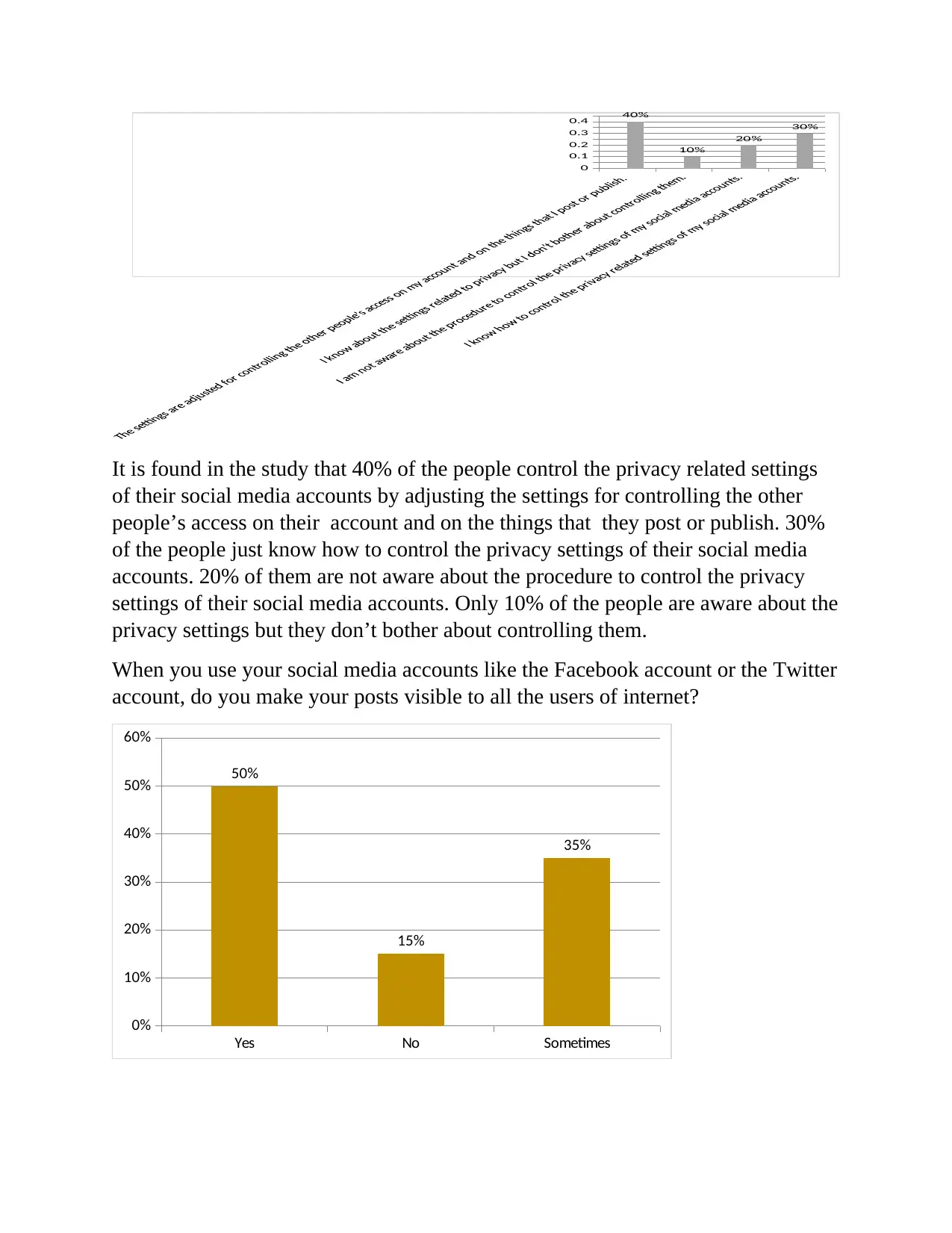
0
0.1
0.2
0.3
0.4 40%
10%
20%
30%
It is found in the study that 40% of the people control the privacy related settings
of their social media accounts by adjusting the settings for controlling the other
people’s access on their account and on the things that they post or publish. 30%
of the people just know how to control the privacy settings of their social media
accounts. 20% of them are not aware about the procedure to control the privacy
settings of their social media accounts. Only 10% of the people are aware about the
privacy settings but they don’t bother about controlling them.
When you use your social media accounts like the Facebook account or the Twitter
account, do you make your posts visible to all the users of internet?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
15%
35%
0.1
0.2
0.3
0.4 40%
10%
20%
30%
It is found in the study that 40% of the people control the privacy related settings
of their social media accounts by adjusting the settings for controlling the other
people’s access on their account and on the things that they post or publish. 30%
of the people just know how to control the privacy settings of their social media
accounts. 20% of them are not aware about the procedure to control the privacy
settings of their social media accounts. Only 10% of the people are aware about the
privacy settings but they don’t bother about controlling them.
When you use your social media accounts like the Facebook account or the Twitter
account, do you make your posts visible to all the users of internet?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
15%
35%
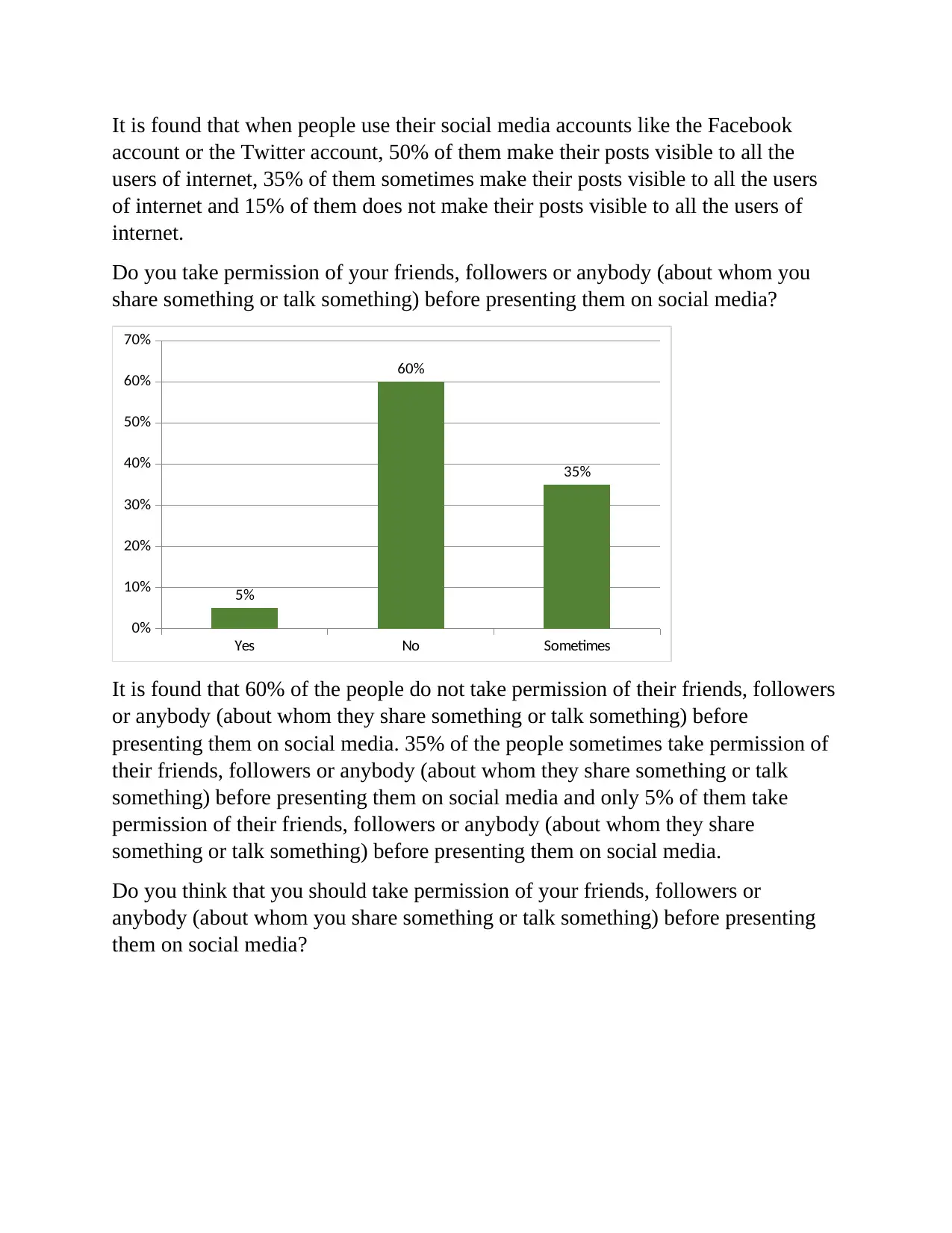
It is found that when people use their social media accounts like the Facebook
account or the Twitter account, 50% of them make their posts visible to all the
users of internet, 35% of them sometimes make their posts visible to all the users
of internet and 15% of them does not make their posts visible to all the users of
internet.
Do you take permission of your friends, followers or anybody (about whom you
share something or talk something) before presenting them on social media?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
70%
5%
60%
35%
It is found that 60% of the people do not take permission of their friends, followers
or anybody (about whom they share something or talk something) before
presenting them on social media. 35% of the people sometimes take permission of
their friends, followers or anybody (about whom they share something or talk
something) before presenting them on social media and only 5% of them take
permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media.
Do you think that you should take permission of your friends, followers or
anybody (about whom you share something or talk something) before presenting
them on social media?
account or the Twitter account, 50% of them make their posts visible to all the
users of internet, 35% of them sometimes make their posts visible to all the users
of internet and 15% of them does not make their posts visible to all the users of
internet.
Do you take permission of your friends, followers or anybody (about whom you
share something or talk something) before presenting them on social media?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
70%
5%
60%
35%
It is found that 60% of the people do not take permission of their friends, followers
or anybody (about whom they share something or talk something) before
presenting them on social media. 35% of the people sometimes take permission of
their friends, followers or anybody (about whom they share something or talk
something) before presenting them on social media and only 5% of them take
permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media.
Do you think that you should take permission of your friends, followers or
anybody (about whom you share something or talk something) before presenting
them on social media?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
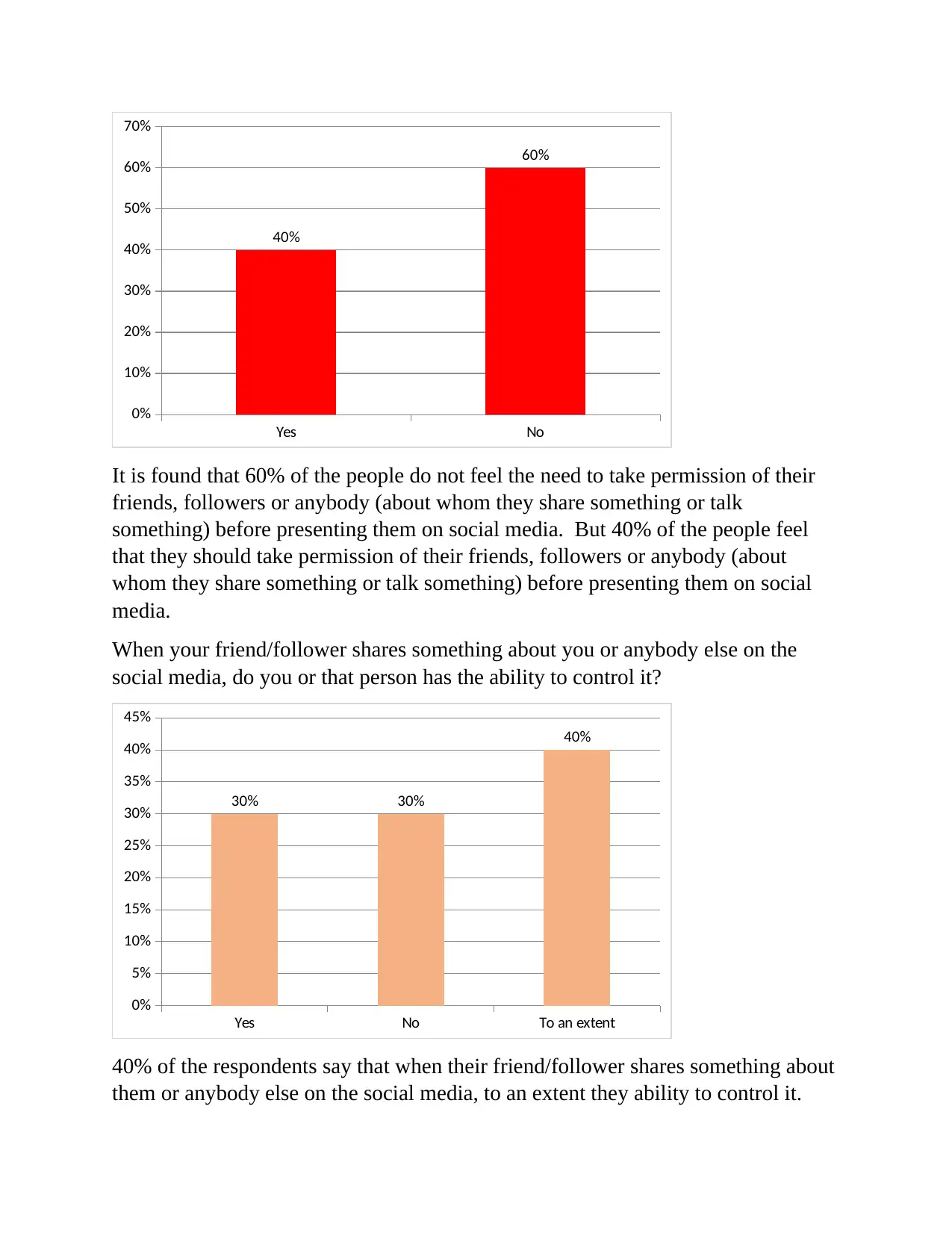
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
40%
60%
It is found that 60% of the people do not feel the need to take permission of their
friends, followers or anybody (about whom they share something or talk
something) before presenting them on social media. But 40% of the people feel
that they should take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social
media.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the ability to control it?
Yes No To an extent
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30% 30%
40%
40% of the respondents say that when their friend/follower shares something about
them or anybody else on the social media, to an extent they ability to control it.
0%
10%
20%
30%
40%
50%
60%
70%
40%
60%
It is found that 60% of the people do not feel the need to take permission of their
friends, followers or anybody (about whom they share something or talk
something) before presenting them on social media. But 40% of the people feel
that they should take permission of their friends, followers or anybody (about
whom they share something or talk something) before presenting them on social
media.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the ability to control it?
Yes No To an extent
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30% 30%
40%
40% of the respondents say that when their friend/follower shares something about
them or anybody else on the social media, to an extent they ability to control it.
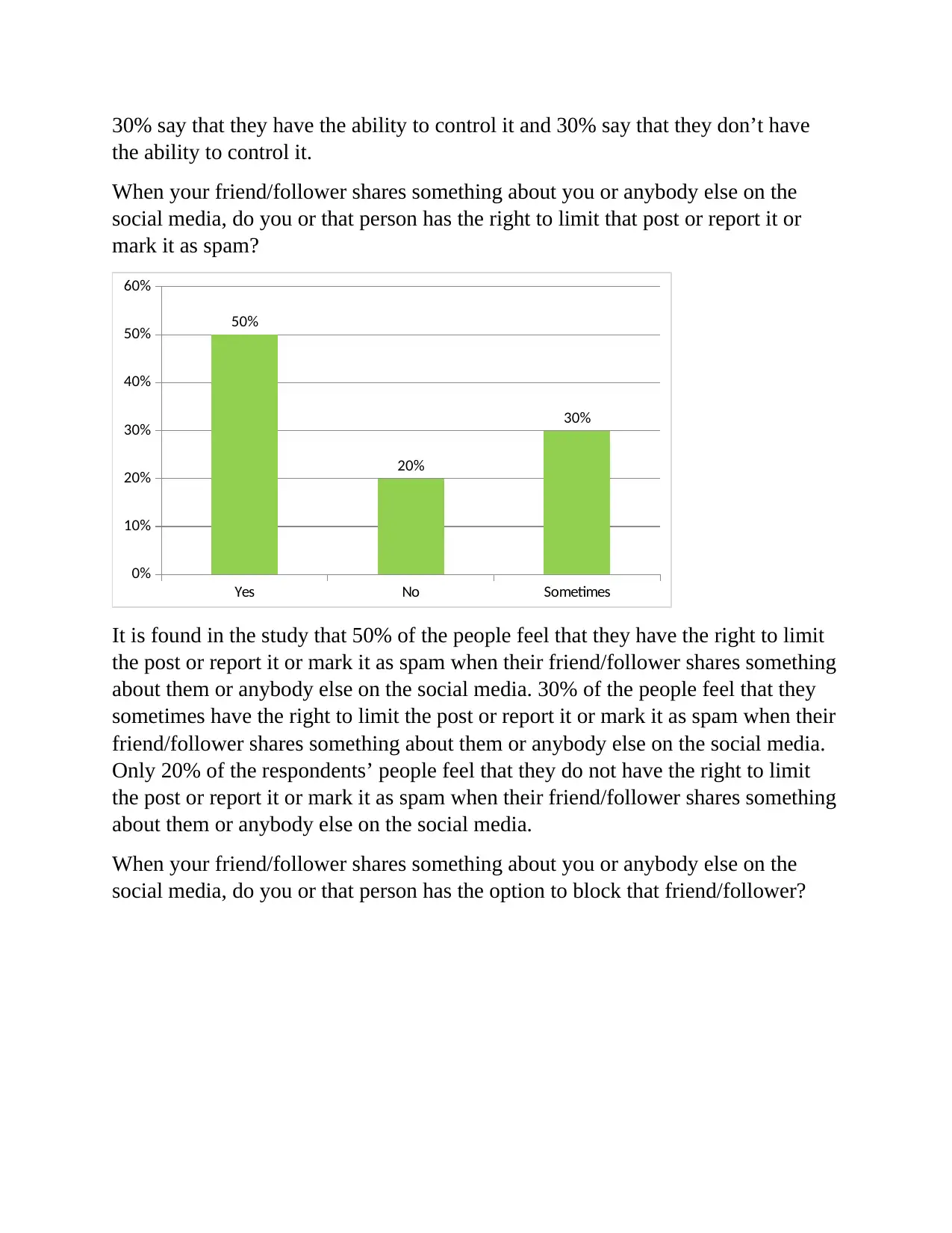
30% say that they have the ability to control it and 30% say that they don’t have
the ability to control it.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the right to limit that post or report it or
mark it as spam?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
20%
30%
It is found in the study that 50% of the people feel that they have the right to limit
the post or report it or mark it as spam when their friend/follower shares something
about them or anybody else on the social media. 30% of the people feel that they
sometimes have the right to limit the post or report it or mark it as spam when their
friend/follower shares something about them or anybody else on the social media.
Only 20% of the respondents’ people feel that they do not have the right to limit
the post or report it or mark it as spam when their friend/follower shares something
about them or anybody else on the social media.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the option to block that friend/follower?
the ability to control it.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the right to limit that post or report it or
mark it as spam?
Yes No Sometimes
0%
10%
20%
30%
40%
50%
60%
50%
20%
30%
It is found in the study that 50% of the people feel that they have the right to limit
the post or report it or mark it as spam when their friend/follower shares something
about them or anybody else on the social media. 30% of the people feel that they
sometimes have the right to limit the post or report it or mark it as spam when their
friend/follower shares something about them or anybody else on the social media.
Only 20% of the respondents’ people feel that they do not have the right to limit
the post or report it or mark it as spam when their friend/follower shares something
about them or anybody else on the social media.
When your friend/follower shares something about you or anybody else on the
social media, do you or that person has the option to block that friend/follower?
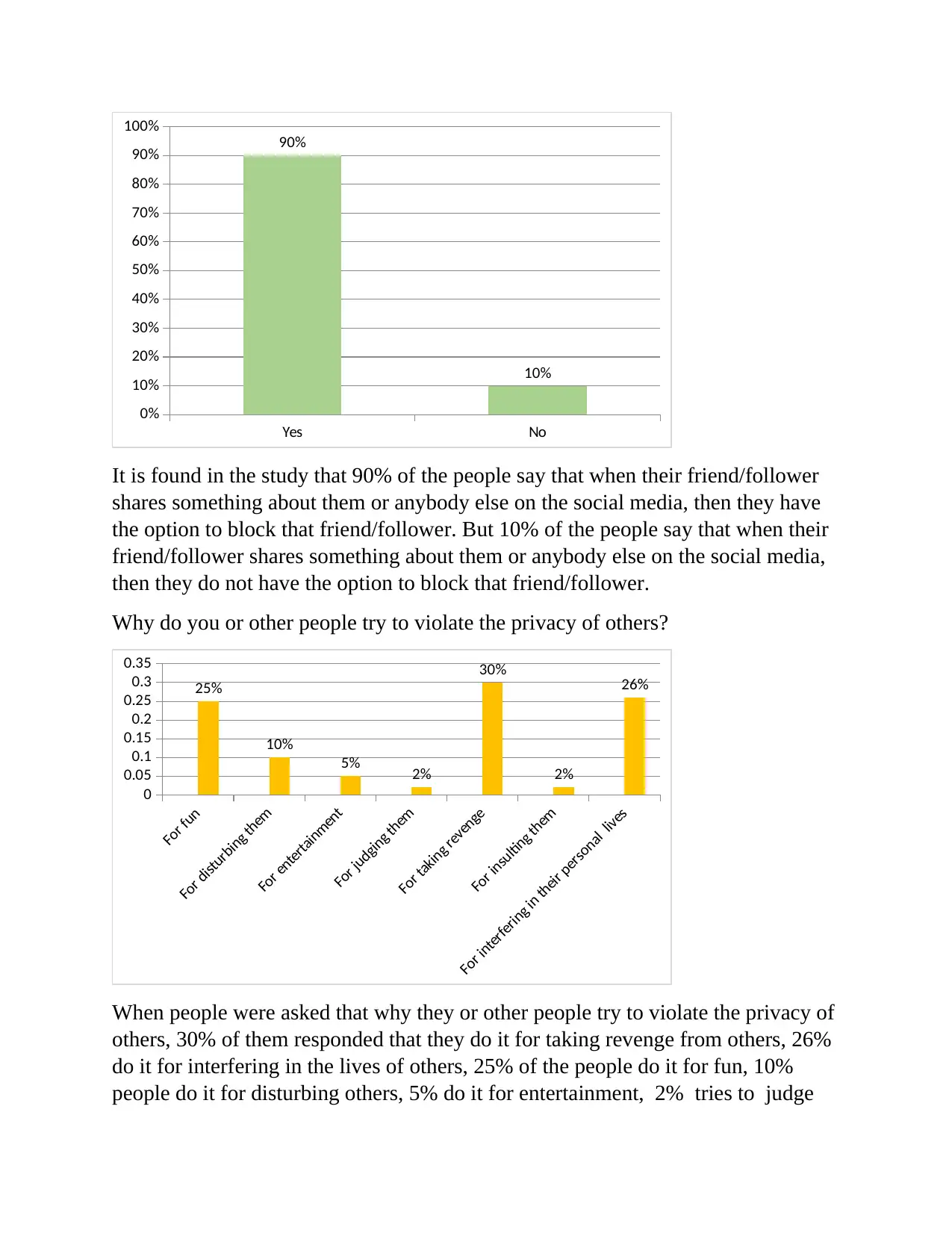
Yes No
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
90%
10%
It is found in the study that 90% of the people say that when their friend/follower
shares something about them or anybody else on the social media, then they have
the option to block that friend/follower. But 10% of the people say that when their
friend/follower shares something about them or anybody else on the social media,
then they do not have the option to block that friend/follower.
Why do you or other people try to violate the privacy of others?
For fun
For disturbing them
For entertainment
For judging them
For taking revenge
For insulting them
For interfering in their personal lives
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
25%
10%
5% 2%
30%
2%
26%
When people were asked that why they or other people try to violate the privacy of
others, 30% of them responded that they do it for taking revenge from others, 26%
do it for interfering in the lives of others, 25% of the people do it for fun, 10%
people do it for disturbing others, 5% do it for entertainment, 2% tries to judge
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
90%
10%
It is found in the study that 90% of the people say that when their friend/follower
shares something about them or anybody else on the social media, then they have
the option to block that friend/follower. But 10% of the people say that when their
friend/follower shares something about them or anybody else on the social media,
then they do not have the option to block that friend/follower.
Why do you or other people try to violate the privacy of others?
For fun
For disturbing them
For entertainment
For judging them
For taking revenge
For insulting them
For interfering in their personal lives
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
25%
10%
5% 2%
30%
2%
26%
When people were asked that why they or other people try to violate the privacy of
others, 30% of them responded that they do it for taking revenge from others, 26%
do it for interfering in the lives of others, 25% of the people do it for fun, 10%
people do it for disturbing others, 5% do it for entertainment, 2% tries to judge
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
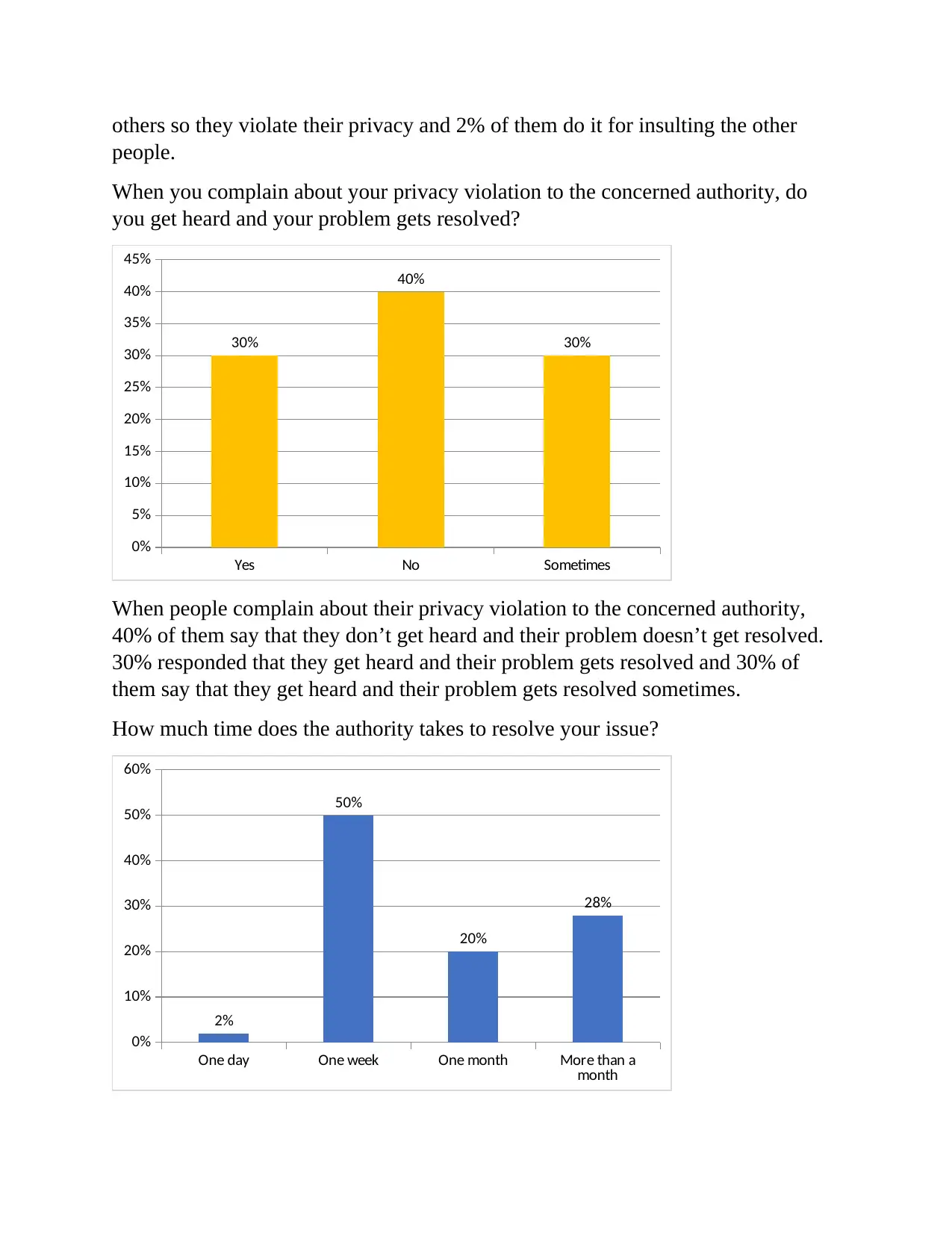
others so they violate their privacy and 2% of them do it for insulting the other
people.
When you complain about your privacy violation to the concerned authority, do
you get heard and your problem gets resolved?
Yes No Sometimes
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30%
40%
30%
When people complain about their privacy violation to the concerned authority,
40% of them say that they don’t get heard and their problem doesn’t get resolved.
30% responded that they get heard and their problem gets resolved and 30% of
them say that they get heard and their problem gets resolved sometimes.
How much time does the authority takes to resolve your issue?
One day One week One month More than a
month
0%
10%
20%
30%
40%
50%
60%
2%
50%
20%
28%
people.
When you complain about your privacy violation to the concerned authority, do
you get heard and your problem gets resolved?
Yes No Sometimes
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
30%
40%
30%
When people complain about their privacy violation to the concerned authority,
40% of them say that they don’t get heard and their problem doesn’t get resolved.
30% responded that they get heard and their problem gets resolved and 30% of
them say that they get heard and their problem gets resolved sometimes.
How much time does the authority takes to resolve your issue?
One day One week One month More than a
month
0%
10%
20%
30%
40%
50%
60%
2%
50%
20%
28%

It is found that 50% of the people say that it takes one week for the authority to
resolve their issue, 28% say that it takes more than a month week for the authority
to resolve their issue, 20% say that it takes a month for the authority to resolve
their issue and only 2% say that it takes a day for the authority to resolve their
issue.
resolve their issue, 28% say that it takes more than a month week for the authority
to resolve their issue, 20% say that it takes a month for the authority to resolve
their issue and only 2% say that it takes a day for the authority to resolve their
issue.

Findings related to the ethical code of conduct or legal framework to regulate the
use of social media in violating privacy of others
There is a right in UK known as the ‘Right to Privacy’. This right gives the privacy
rights against the misuse of the information about the state and the private persons
which is confidential. The rights given in this right protects the people from all
types of social media activities even the photographs posting, no matter the
information underlying it may be effectively commercial in nature. This right is not
mentioned in the constitution of UK, but it has incorporated the European
Convention on Human Rights into its national law, which provides for a limited
right of respect towards an individual’s privacy and family life (Edwards, 2013). In
social media, there are also laws related to protection of data and it enables people
to get protection from the information that is posted on the social media (Adelola,
2015).
The ‘Data Protection Act, 1998’ was enacted to take care of the personal
information of the people that was being processed. The personal information of
the people is protected from being disclosed, obtained, held and used (Council,
2015).
Research analysis and results
1. The findings show that mainly, the people use social media for staying
connected with areas/people of interests like celebrities, film industry, and
political industry etc. and for expressing their views, opinions, thoughts,
knowledge about some current issue. So, it can be analysed that people like to
look into the world around them and they like to know that what is happening
in the industries around them especially the film and political world. Also, they
like to share their views on the current issues because they have the freedom of
speech and they want the world to know that what are their opinions and views.
They also encourage others to talk about the issues and give their views so that
they can hold a debate on a topic and talk about it in detail. It has also been
found that some people use social media for spying in the lives of others, they
do this because they like to comment on the life and instances of others. There
were very few people who wanted to stay connected with their friends and few
of them used it for passing their time. This means that people are not using
media for their personal things like chatting with friends or for leisure; they are
just using it to peep in the lives of others and for interfering with their issues.
use of social media in violating privacy of others
There is a right in UK known as the ‘Right to Privacy’. This right gives the privacy
rights against the misuse of the information about the state and the private persons
which is confidential. The rights given in this right protects the people from all
types of social media activities even the photographs posting, no matter the
information underlying it may be effectively commercial in nature. This right is not
mentioned in the constitution of UK, but it has incorporated the European
Convention on Human Rights into its national law, which provides for a limited
right of respect towards an individual’s privacy and family life (Edwards, 2013). In
social media, there are also laws related to protection of data and it enables people
to get protection from the information that is posted on the social media (Adelola,
2015).
The ‘Data Protection Act, 1998’ was enacted to take care of the personal
information of the people that was being processed. The personal information of
the people is protected from being disclosed, obtained, held and used (Council,
2015).
Research analysis and results
1. The findings show that mainly, the people use social media for staying
connected with areas/people of interests like celebrities, film industry, and
political industry etc. and for expressing their views, opinions, thoughts,
knowledge about some current issue. So, it can be analysed that people like to
look into the world around them and they like to know that what is happening
in the industries around them especially the film and political world. Also, they
like to share their views on the current issues because they have the freedom of
speech and they want the world to know that what are their opinions and views.
They also encourage others to talk about the issues and give their views so that
they can hold a debate on a topic and talk about it in detail. It has also been
found that some people use social media for spying in the lives of others, they
do this because they like to comment on the life and instances of others. There
were very few people who wanted to stay connected with their friends and few
of them used it for passing their time. This means that people are not using
media for their personal things like chatting with friends or for leisure; they are
just using it to peep in the lives of others and for interfering with their issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Though this is not incorrect in the sense that people should give their opinion
and views if they feel something but that should not lead to insulting someone
or it should not breach the privacy of others. That is considered unethical when
people do this and they misuse the social media for breaching the privacy of
others.
2. The findings show that most of the respondents in the study use the social
media platform for posting something or for commenting on someone many
times in a week. This shows that the people are very active on the social media
platforms and they use their social media accounts very extensively. Even there
were people in large number who post something on the platform of social
media daily. This shows that social media has become very popular among the
people and it is used on regular basis by the people. The people comment on
the social media sites in regular manner and they like to talk on these websites
very much. They have not set any limits of using social media for themselves,
they are using it as and when they feel to. There are very few people who are
not using social media on regular basis. One reason of this may be that they are
of older generation and they are not very tech savvy to use such things, or they
may just not be interested to become social.
3. The findings show that most of the people are aware of the privacy settings of
their social media accounts and its use. This means that they know about the
privacy of social media accounts and they know how to use it. The awareness
about privacy settings is there in the people and they are well-equipped to use
it. There were few people who were not at all aware of the privacy settings of
their social media accounts and its use. This may be due to the reason that they
were not properly educated or may be because they were indulged in the breach
of privacy of others so they never bothered to learn about the privacy settings.
4. The findings show that most of the people use privacy settings in controlling
and monitoring the posts that they share or the people they follow. These are
not indulged in violation of privacy of others as they know how to limit the
audience of their post. But there are many other people who do not use privacy
settings in controlling and monitoring the posts that they share or the people
they follow. They are the ones who don’t know their limits while using social
media and they cause privacy violation in social media accounts of others.
They do something and others suffer due to that, for example they share some
post or photo and it is visible to everyone on the internet, so there is risk to the
privacy of others. There are other people also, who sometimes use privacy
and views if they feel something but that should not lead to insulting someone
or it should not breach the privacy of others. That is considered unethical when
people do this and they misuse the social media for breaching the privacy of
others.
2. The findings show that most of the respondents in the study use the social
media platform for posting something or for commenting on someone many
times in a week. This shows that the people are very active on the social media
platforms and they use their social media accounts very extensively. Even there
were people in large number who post something on the platform of social
media daily. This shows that social media has become very popular among the
people and it is used on regular basis by the people. The people comment on
the social media sites in regular manner and they like to talk on these websites
very much. They have not set any limits of using social media for themselves,
they are using it as and when they feel to. There are very few people who are
not using social media on regular basis. One reason of this may be that they are
of older generation and they are not very tech savvy to use such things, or they
may just not be interested to become social.
3. The findings show that most of the people are aware of the privacy settings of
their social media accounts and its use. This means that they know about the
privacy of social media accounts and they know how to use it. The awareness
about privacy settings is there in the people and they are well-equipped to use
it. There were few people who were not at all aware of the privacy settings of
their social media accounts and its use. This may be due to the reason that they
were not properly educated or may be because they were indulged in the breach
of privacy of others so they never bothered to learn about the privacy settings.
4. The findings show that most of the people use privacy settings in controlling
and monitoring the posts that they share or the people they follow. These are
not indulged in violation of privacy of others as they know how to limit the
audience of their post. But there are many other people who do not use privacy
settings in controlling and monitoring the posts that they share or the people
they follow. They are the ones who don’t know their limits while using social
media and they cause privacy violation in social media accounts of others.
They do something and others suffer due to that, for example they share some
post or photo and it is visible to everyone on the internet, so there is risk to the
privacy of others. There are other people also, who sometimes use privacy

settings in controlling and monitoring the posts that they share or the people
they follow. This shows that they use these settings only when they feel that
some post is not for everyone on the internet but these people may also cause a
threat to the privacy of others.
5. The findings show that most of the people control the privacy related settings
of their social media accounts by adjusting the settings for controlling the other
people’s access on their account and on the things that they post or publish.
This shows that they are concerned about their privacy a lot. They don’t want
others to peep in their personal lives and comment on what they share but this
does not confirm that they feel the same for the others too. There are other
people too who don’t care about the control on the privacy settings and they are
not even aware about the settings.
6. The findings show that most of the people make their posts visible to all the
users of internet. This means that they have no limits on the use of social
media. They are open to all the people and they allow others to violate their
privacy. They are very few people who do not do this.
7. There are many people in the study who do not take permission of their friends,
followers or anybody (about whom they share something or talk something)
before presenting them on social media. This shows that they are not concerned
about their privacy and they don’t leave them secured. They are giving others a
chance to breach and violate the privacy of their friends and they themselves
are doing the same if they are not taking permission. Very few of them take
permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. These
are the ones who are concerned about privacy violation issues in social media
but they are very limited in number.
8. Earlier it was found that people don’t take permission of their friends, followers
or anybody (about whom they share something or talk something) before
presenting them on social media, but here it is found that they don’t even feel
the need to do so. Most of the people under this study do not feel the need to
take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. This
shows that the level of awareness among people is less and the concern about
privacy issues is also less. Though there are people who still feel that they
should take permission of their friends, followers or anybody (about whom
they follow. This shows that they use these settings only when they feel that
some post is not for everyone on the internet but these people may also cause a
threat to the privacy of others.
5. The findings show that most of the people control the privacy related settings
of their social media accounts by adjusting the settings for controlling the other
people’s access on their account and on the things that they post or publish.
This shows that they are concerned about their privacy a lot. They don’t want
others to peep in their personal lives and comment on what they share but this
does not confirm that they feel the same for the others too. There are other
people too who don’t care about the control on the privacy settings and they are
not even aware about the settings.
6. The findings show that most of the people make their posts visible to all the
users of internet. This means that they have no limits on the use of social
media. They are open to all the people and they allow others to violate their
privacy. They are very few people who do not do this.
7. There are many people in the study who do not take permission of their friends,
followers or anybody (about whom they share something or talk something)
before presenting them on social media. This shows that they are not concerned
about their privacy and they don’t leave them secured. They are giving others a
chance to breach and violate the privacy of their friends and they themselves
are doing the same if they are not taking permission. Very few of them take
permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. These
are the ones who are concerned about privacy violation issues in social media
but they are very limited in number.
8. Earlier it was found that people don’t take permission of their friends, followers
or anybody (about whom they share something or talk something) before
presenting them on social media, but here it is found that they don’t even feel
the need to do so. Most of the people under this study do not feel the need to
take permission of their friends, followers or anybody (about whom they share
something or talk something) before presenting them on social media. This
shows that the level of awareness among people is less and the concern about
privacy issues is also less. Though there are people who still feel that they
should take permission of their friends, followers or anybody (about whom

they share something or talk something) before presenting them on social
media. But these are less in number than the former ones.
9. It is difficult for most of the people to control what their friend/follower shares
something about them or anybody else on the social media. This means that
they have less control on their security. It is very little that they can do to
control their own privacy. Thus, there is a threat to privacy of people. But few
of the people also feel that they have the ability to control it and don’t have the
ability to control it. The people are not safe in the use of social media of they
cannot control their own privacy settings and the posts about them that others
share.
10.The study shows that large number of the people feel that they have the right to
limit the post or report it or mark it as spam when their friend/follower shares
something about them or anybody else on the social media. This means that
even if something is posted or written against them, they can rectify it and
remove it or they don’t like it or it breaches their privacy on social media.
Others said that they sometimes have the right which means that they cannot
always limit what others post because others may have not allowed us to look
at their post but they have the right to post anything about anyone. Few people
also feel that they do not have the right to limit the post or report it or mark it as
spam when their friend/follower shares something about them or anybody else
on the social media. This is due to the same reason that they may not have the
access to other people’s accounts.
11.A positive thing that was found related to security on the social media is that
most of the people, almost 90% of the people say that when their
friend/follower shares something about them or anybody else on the social
media, then they have the option to block that friend/follower. This means that
the people have the option to get secured from the person forever but it may
happen that the person violates the privacy by making a fake account or by any
other means. So, still the privacy may be violated due to use of social media.
12.The main factors due to which people violate other’s privacy is that they do it
for taking revenge from others, 26% do it for interfering in the lives of others,
25% of the people do it for fun, 10% people do it for disturbing others, 5% do it
for entertainment, 2% tries to judge others so they violate their privacy and 2%
of them do it for insulting the other people. This means that jealousy,
competition, and negative thoughts makes people violate others privacy and
media. But these are less in number than the former ones.
9. It is difficult for most of the people to control what their friend/follower shares
something about them or anybody else on the social media. This means that
they have less control on their security. It is very little that they can do to
control their own privacy. Thus, there is a threat to privacy of people. But few
of the people also feel that they have the ability to control it and don’t have the
ability to control it. The people are not safe in the use of social media of they
cannot control their own privacy settings and the posts about them that others
share.
10.The study shows that large number of the people feel that they have the right to
limit the post or report it or mark it as spam when their friend/follower shares
something about them or anybody else on the social media. This means that
even if something is posted or written against them, they can rectify it and
remove it or they don’t like it or it breaches their privacy on social media.
Others said that they sometimes have the right which means that they cannot
always limit what others post because others may have not allowed us to look
at their post but they have the right to post anything about anyone. Few people
also feel that they do not have the right to limit the post or report it or mark it as
spam when their friend/follower shares something about them or anybody else
on the social media. This is due to the same reason that they may not have the
access to other people’s accounts.
11.A positive thing that was found related to security on the social media is that
most of the people, almost 90% of the people say that when their
friend/follower shares something about them or anybody else on the social
media, then they have the option to block that friend/follower. This means that
the people have the option to get secured from the person forever but it may
happen that the person violates the privacy by making a fake account or by any
other means. So, still the privacy may be violated due to use of social media.
12.The main factors due to which people violate other’s privacy is that they do it
for taking revenge from others, 26% do it for interfering in the lives of others,
25% of the people do it for fun, 10% people do it for disturbing others, 5% do it
for entertainment, 2% tries to judge others so they violate their privacy and 2%
of them do it for insulting the other people. This means that jealousy,
competition, and negative thoughts makes people violate others privacy and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

some people like to know what others are doing and they are interested in
disturbing their personal lives so they violate their privacy. Some do it for fun
as they find it funny to disturb others and bother them.
13.Most of the people find the authorities to be incompetent to resolve their issues.
This may be due to the fact they might have had a bad experience in the past
and they might have complained it to the authorities earlier but they were not
heard. This shows that even if their privacy is violated, they don’t get justice
and resolution of the same. But there were few people too who were positive
about the resolution of their problems. This may be due to their experience was
good in the past. So, the people who got their issues resolved in the past found
the authorities to be competent enough to solve their problems and vice-versa.
14.The respondents say that the authorities take one week to resolve their issue,
though the time taken is not long but in some cases the issue might be urgent so
in that case, one week is a long time. The issue should get resolved as per the
urgency of the work. But in some cases the authorities even take a month to
resolve their issue. This response was based on the experience of the
respondents.
15.Lastly, it has been found that the country has some laws, regulations, rights and
legal framework to protect the people from privacy violation in the social
media. These have been used to regulate the use of social media in violating
privacy of others. But then also, there are issues in this area and the people are
not satisfied by the regulations etc. that is why they keep on complaining about
such issues and the authorities also get reports on such matters.
disturbing their personal lives so they violate their privacy. Some do it for fun
as they find it funny to disturb others and bother them.
13.Most of the people find the authorities to be incompetent to resolve their issues.
This may be due to the fact they might have had a bad experience in the past
and they might have complained it to the authorities earlier but they were not
heard. This shows that even if their privacy is violated, they don’t get justice
and resolution of the same. But there were few people too who were positive
about the resolution of their problems. This may be due to their experience was
good in the past. So, the people who got their issues resolved in the past found
the authorities to be competent enough to solve their problems and vice-versa.
14.The respondents say that the authorities take one week to resolve their issue,
though the time taken is not long but in some cases the issue might be urgent so
in that case, one week is a long time. The issue should get resolved as per the
urgency of the work. But in some cases the authorities even take a month to
resolve their issue. This response was based on the experience of the
respondents.
15.Lastly, it has been found that the country has some laws, regulations, rights and
legal framework to protect the people from privacy violation in the social
media. These have been used to regulate the use of social media in violating
privacy of others. But then also, there are issues in this area and the people are
not satisfied by the regulations etc. that is why they keep on complaining about
such issues and the authorities also get reports on such matters.


REFERENCES
[1] Blackboxsocialmedia, "blackboxsocialmedia," [Online]. Available:
http://blackboxsocialmedia.com/social-networking/. [Accessed 25 December 2014].
[2] L. A. Cutillo and R. Molva, "Safebook: A Privacy-Preserving Online Social Network
Leveraging on Real-Life Trust," IEEE, pp. 94-101, 2009.
[3] A. Srivastava and G. Geethakumari, "A Framework to Customize Privacy Settings of Online
Social Network Users," IEEE Recent Advances in Intelligent Computational Systems (RAICS),
pp. 187-192, 2013.
[4] A. Srivastava and G. Geethakumari, "Measuring Privacy Leaks in Online Social Networks,"
International Conference on Advances in Computing, Communications and Informatics
(ICACCI), pp. 2095-2100, 2013.
[5] A. Dhami, N. Agarwal, T. K. Chakraborty, B. P. Singh and J. Minj, "Impact of trust, security
and privacy concerns in social networking: An exploratory study to understand the pattern of
information revelation in Facebook," 3rd IEEE International Advance Computing Conference
(IACC), pp. 465-469, 2013.
[6] B2BInternationalInConjunction and KasperskyLab, "CONSUMER SECURITY RISKS
SURVEY 2014: MULTI-DEVICE THREATS IN A MULTI-DEVICE WORLD," Kaspersky
Lab, 2014.
[7] W. Binden, M. Jormae, Z. Zain and J. Ibrahim, "Employing Information Security Awareness
to Minimize Over-Exposure of Average Internet User on Social Networks," International Journal
of Scientific and Research Publications, vol. 4, no. 1, pp. 1-6, 2014.
[8] X. Chen and S. Shi, "A Literature Review of Privacy Research on Social Network Sites,"
International Conference on Multimedia Information Networking and Security, pp. 93-97, 2009.
[9] F. Raji, A. Miri and M. D. Jazi, "Preserving Privacy in Online Social Networks," Springer-
Verlag Berlin Heidelberg 2012, pp. 1-13, 2012.
Trenchard, N. (2013, June 29). 3 Online Privacy Concerns You Should be Worried About.
Retrieved from DashBurst: http://dashburst.com/online-privacy-concerns/
Kabay, M. E. (2010, September 27). Privacy issues in social-networking sites . Retrieved from
Network World : http://www.networkworld.com/newsletters/sec/2010/092710sec1.html
Gross, R., & Acquisti, A. (2005). Information Revelation and Privacy in Online Social Networks
(The Facebook case). ACM Workshop on Privacy in the Electronic Society (WPES), 2005.
Retrieved from http://www.heinz.cmu.edu/~acquisti/papers/privacy-facebook-gross-acquisti.pdf
Dutton, W. H. (2004). Social transformation in an information society: rethinking access to you
and the world. Retrieved from UNESCO Archives English - UNESCO HQ Social Sciences
[1] Blackboxsocialmedia, "blackboxsocialmedia," [Online]. Available:
http://blackboxsocialmedia.com/social-networking/. [Accessed 25 December 2014].
[2] L. A. Cutillo and R. Molva, "Safebook: A Privacy-Preserving Online Social Network
Leveraging on Real-Life Trust," IEEE, pp. 94-101, 2009.
[3] A. Srivastava and G. Geethakumari, "A Framework to Customize Privacy Settings of Online
Social Network Users," IEEE Recent Advances in Intelligent Computational Systems (RAICS),
pp. 187-192, 2013.
[4] A. Srivastava and G. Geethakumari, "Measuring Privacy Leaks in Online Social Networks,"
International Conference on Advances in Computing, Communications and Informatics
(ICACCI), pp. 2095-2100, 2013.
[5] A. Dhami, N. Agarwal, T. K. Chakraborty, B. P. Singh and J. Minj, "Impact of trust, security
and privacy concerns in social networking: An exploratory study to understand the pattern of
information revelation in Facebook," 3rd IEEE International Advance Computing Conference
(IACC), pp. 465-469, 2013.
[6] B2BInternationalInConjunction and KasperskyLab, "CONSUMER SECURITY RISKS
SURVEY 2014: MULTI-DEVICE THREATS IN A MULTI-DEVICE WORLD," Kaspersky
Lab, 2014.
[7] W. Binden, M. Jormae, Z. Zain and J. Ibrahim, "Employing Information Security Awareness
to Minimize Over-Exposure of Average Internet User on Social Networks," International Journal
of Scientific and Research Publications, vol. 4, no. 1, pp. 1-6, 2014.
[8] X. Chen and S. Shi, "A Literature Review of Privacy Research on Social Network Sites,"
International Conference on Multimedia Information Networking and Security, pp. 93-97, 2009.
[9] F. Raji, A. Miri and M. D. Jazi, "Preserving Privacy in Online Social Networks," Springer-
Verlag Berlin Heidelberg 2012, pp. 1-13, 2012.
Trenchard, N. (2013, June 29). 3 Online Privacy Concerns You Should be Worried About.
Retrieved from DashBurst: http://dashburst.com/online-privacy-concerns/
Kabay, M. E. (2010, September 27). Privacy issues in social-networking sites . Retrieved from
Network World : http://www.networkworld.com/newsletters/sec/2010/092710sec1.html
Gross, R., & Acquisti, A. (2005). Information Revelation and Privacy in Online Social Networks
(The Facebook case). ACM Workshop on Privacy in the Electronic Society (WPES), 2005.
Retrieved from http://www.heinz.cmu.edu/~acquisti/papers/privacy-facebook-gross-acquisti.pdf
Dutton, W. H. (2004). Social transformation in an information society: rethinking access to you
and the world. Retrieved from UNESCO Archives English - UNESCO HQ Social Sciences
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SSDCN (stock 2E) - UNESCO Brasilia: http://www.unesco.org/new/en/communication-
andinformation/resources/publications-and-communication-materials/publications/full-list/
socialtransformation-in-an-information-society-rethinking-access-to-you-and-the-world/
Boyd, D., & Ellison, N. (2008). Social Network Sites: Definition, History and Scholarship.
Journal Of ComputerMediated Communication, 13, 210-230.
J. Kang. Information privacy in cyberspace transactions. Stanford Law Review, 50(4):1193–
1294, 1998.
L. Palen and P. Dourish. Unpacking ”privacy” for a networked world. In CHI ’03: Proceedings
of the SIGCHI conference on Human factors in computing systems, pages 129–136, New York,
NY, USA, 2003. ACM.
Z. Tufekci. Can you see me now? audience and disclosure regulation in online social network
sites. Bulletin of Science Technology Society, 28(1):20–36, February 2008.
DÖTZER, F. Privacy issues in vehicular ad hoc networks. Lecture Notes in Computer
Science,vol. 3856, Springer, 197-209,2006.
Bouguettaya, A.R.A.; Eltoweissy, M.Y., "Privacy on the Web: facts, challenges, and solutions,"
Security & Privacy, IEEE , vol.1, no.6, pp.40,49, Nov.-Dec. 2003.
Weichao Wang; Cheng Cui, "Achieving configural location privacy in location based routing for
MANET," Military
SADEH, N., HONG, J., CRANOR, L., FETTE, I., KELLEY, P., PRABAKER, M. & RAO, J.
2009. "Understanding and capturing people's privacy policies in a mobile social networking
application,"Personal and Ubiquitous Computing, 13, 401-412.
PASSANT, A., KÄRGER, P., HAUSENBLAS, M., OLMEDILLA, D., POLLERES, A.,
DECKER, S. & TELEFONICA, R. "Enabling trust and privacy on the social web".W3C
workshop on the future of social networking, 2009.pp. 15-16.
Campisi, P.; Maiorana, E.; Neri, A., "Privacy protection in social media networks a dream that
can come true?," Digital Signal Processing, 2009 16th International Conference on , vol., no.,
pp.1,5, 5-7 July 2009.
18 Facebook http://www.facebook.com
19 Wired’s Facebook’s Gone Rogue article
http://www.wired.com/epicenter/2010/05/facebookrogue/
20 Open Graph Protocol http://opengraphprotocol.org/
21 Facebook’s Graph API http://developers.facebook.com/docs/api
22 The Privacy Jungle: On the Market for Data Protection in Social Networks
http://preibusch.de/publications/Bonneau Preibusch Privacy Jungle 2009-05-26.pdf
andinformation/resources/publications-and-communication-materials/publications/full-list/
socialtransformation-in-an-information-society-rethinking-access-to-you-and-the-world/
Boyd, D., & Ellison, N. (2008). Social Network Sites: Definition, History and Scholarship.
Journal Of ComputerMediated Communication, 13, 210-230.
J. Kang. Information privacy in cyberspace transactions. Stanford Law Review, 50(4):1193–
1294, 1998.
L. Palen and P. Dourish. Unpacking ”privacy” for a networked world. In CHI ’03: Proceedings
of the SIGCHI conference on Human factors in computing systems, pages 129–136, New York,
NY, USA, 2003. ACM.
Z. Tufekci. Can you see me now? audience and disclosure regulation in online social network
sites. Bulletin of Science Technology Society, 28(1):20–36, February 2008.
DÖTZER, F. Privacy issues in vehicular ad hoc networks. Lecture Notes in Computer
Science,vol. 3856, Springer, 197-209,2006.
Bouguettaya, A.R.A.; Eltoweissy, M.Y., "Privacy on the Web: facts, challenges, and solutions,"
Security & Privacy, IEEE , vol.1, no.6, pp.40,49, Nov.-Dec. 2003.
Weichao Wang; Cheng Cui, "Achieving configural location privacy in location based routing for
MANET," Military
SADEH, N., HONG, J., CRANOR, L., FETTE, I., KELLEY, P., PRABAKER, M. & RAO, J.
2009. "Understanding and capturing people's privacy policies in a mobile social networking
application,"Personal and Ubiquitous Computing, 13, 401-412.
PASSANT, A., KÄRGER, P., HAUSENBLAS, M., OLMEDILLA, D., POLLERES, A.,
DECKER, S. & TELEFONICA, R. "Enabling trust and privacy on the social web".W3C
workshop on the future of social networking, 2009.pp. 15-16.
Campisi, P.; Maiorana, E.; Neri, A., "Privacy protection in social media networks a dream that
can come true?," Digital Signal Processing, 2009 16th International Conference on , vol., no.,
pp.1,5, 5-7 July 2009.
18 Facebook http://www.facebook.com
19 Wired’s Facebook’s Gone Rogue article
http://www.wired.com/epicenter/2010/05/facebookrogue/
20 Open Graph Protocol http://opengraphprotocol.org/
21 Facebook’s Graph API http://developers.facebook.com/docs/api
22 The Privacy Jungle: On the Market for Data Protection in Social Networks
http://preibusch.de/publications/Bonneau Preibusch Privacy Jungle 2009-05-26.pdf

23 A summary including links to slides as prepared by the author for the Social Web Incubator
Group at the W3C is available online
:http://www.w3.org/2005/Incubator/socialweb/wiki/InvitedGuestSummaries#Joseph
Bonneau .2C S.C3.B6ren Preibusch : .22The Privacy Jungle: On the Market for Data Protection
in Social Networks.22 - Meeting on July 01 2009
24 Mark Zuckerberg’s Interview: http://www.ustream.tv/recorded/3848950
25 Guardian’s report on the interview
http://www.guardian.co.uk/technology/2010/jan/11/facebookprivacy
26 Pew Report http://www.pewinternet.org/Reports/2010/Reputation-Management.aspx
27 dannah boyd’s summary of the Pew Report
http://www.zephoria.org/thoughts/archives/2010/05/26/pewresearch-confirms-that-youth-care-
about-their-reputation.html
28 Research article detailing the survey http://papers.ssrn.com/sol3/papers.cfm?abstract
id=1589864
29 Elze Dunkels’ PhD thesis http://umu.diva-portal.org/smash/record.jsf?pid=diva2:140705
30 FOSI http://www.fosi.org/
31 CEOP’s Panic button : http://www.ceop.gov.uk/reportabuse/index.asp
32 Bebo http://bebo.com/
33 Blog article about Bebo’s adoption of the Panic Button
http://blog.taragana.com/index.php/archive/bebo-introduces-onscreen-panic-button-to-
reportabuse-instantly/
[36] L. Fang and K. LeFevre. Privacy wizards for social networking sites. In Proceedings of the
19th international conference on World wide web, pages 351–360. ACM, 2010.
[37] B. J. Fogg. Persuasive Technology: Using Computers to Change What We Think and Do.
Morgan Kaufmann, 1 edition, Dec. 2002.
[38] A. Forget, S. Chiasson, P. C. van Oorschot, and R. Biddle. Improving text passwords
through persuasion. In Proceedings of the 4th symposium on Usable privacy and security,
SOUPS ’08, New York, NY, USA, 2008. ACM.
[35] J. C. Brustoloni and R. Villamarín-Salomón. Improving security decisions with
polymorphic and audited dialogs. In Proceedings of the 3rd symposium on Usable privacy and
security, SOUPS ’07, pages 76–85, New York, NY, USA, 2007. ACM.
[40] H. R. Lipford, J. Watson, M. Whitney, N. Carolina, H. Lipford, K. Froiland, and R. W.
Reeder. Visual vs . Compact : A Comparison of Privacy Policy Interfaces. Interfaces, pages
1111–1114, 2010
Group at the W3C is available online
:http://www.w3.org/2005/Incubator/socialweb/wiki/InvitedGuestSummaries#Joseph
Bonneau .2C S.C3.B6ren Preibusch : .22The Privacy Jungle: On the Market for Data Protection
in Social Networks.22 - Meeting on July 01 2009
24 Mark Zuckerberg’s Interview: http://www.ustream.tv/recorded/3848950
25 Guardian’s report on the interview
http://www.guardian.co.uk/technology/2010/jan/11/facebookprivacy
26 Pew Report http://www.pewinternet.org/Reports/2010/Reputation-Management.aspx
27 dannah boyd’s summary of the Pew Report
http://www.zephoria.org/thoughts/archives/2010/05/26/pewresearch-confirms-that-youth-care-
about-their-reputation.html
28 Research article detailing the survey http://papers.ssrn.com/sol3/papers.cfm?abstract
id=1589864
29 Elze Dunkels’ PhD thesis http://umu.diva-portal.org/smash/record.jsf?pid=diva2:140705
30 FOSI http://www.fosi.org/
31 CEOP’s Panic button : http://www.ceop.gov.uk/reportabuse/index.asp
32 Bebo http://bebo.com/
33 Blog article about Bebo’s adoption of the Panic Button
http://blog.taragana.com/index.php/archive/bebo-introduces-onscreen-panic-button-to-
reportabuse-instantly/
[36] L. Fang and K. LeFevre. Privacy wizards for social networking sites. In Proceedings of the
19th international conference on World wide web, pages 351–360. ACM, 2010.
[37] B. J. Fogg. Persuasive Technology: Using Computers to Change What We Think and Do.
Morgan Kaufmann, 1 edition, Dec. 2002.
[38] A. Forget, S. Chiasson, P. C. van Oorschot, and R. Biddle. Improving text passwords
through persuasion. In Proceedings of the 4th symposium on Usable privacy and security,
SOUPS ’08, New York, NY, USA, 2008. ACM.
[35] J. C. Brustoloni and R. Villamarín-Salomón. Improving security decisions with
polymorphic and audited dialogs. In Proceedings of the 3rd symposium on Usable privacy and
security, SOUPS ’07, pages 76–85, New York, NY, USA, 2007. ACM.
[40] H. R. Lipford, J. Watson, M. Whitney, N. Carolina, H. Lipford, K. Froiland, and R. W.
Reeder. Visual vs . Compact : A Comparison of Privacy Policy Interfaces. Interfaces, pages
1111–1114, 2010

Adelola, T., Dawson, R. and Batmaz, F., 2015. Privacy and data protection in e-
commerce in developing nations: evaluation of different data protection
approaches.
Council, S.D., 2015. Data protection act.
Edwards, L., Rauhofer, J. and Yar, M., 2013. Recent developments in UK
cybercrime law. Handbook of Internet Crime, pp.413-436.
commerce in developing nations: evaluation of different data protection
approaches.
Council, S.D., 2015. Data protection act.
Edwards, L., Rauhofer, J. and Yar, M., 2013. Recent developments in UK
cybercrime law. Handbook of Internet Crime, pp.413-436.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.


Flick, U. (1998). An introduction to qualitative research. London: Sage.
Research Design: Qualitative and Quantitative Approaches John W. Creswell. (1996). The
Library Quarterly, 66(2), pp.225-226.
Wilson, R. and Creswell, J. (1996). Research Design: Qualitative and Quantitative Approaches.
Journal of Marketing Research, 33(2), p.252.
Shelton, C., Smith, A. and Mort, M. (2014). Opening up the black box: an introduction to
qualitative research methods in anaesthesia. Anaesthesia, 69(3), pp.270-280.
Hawamdeh, S. and Raigangar, V. (2014). Qualitative interviewing: methodological challenges in
Arab settings. Nurse Researcher, 21(3), pp.27-31.
Guercini, S. (2014). New qualitative research methodologies in management. Management
Decision, 52(4), pp.662-674.
SME Advisor Middle East. (2013). Talent Management in the UAE. [online] Available at:
http://www.smeadvisor.com/news/talent-management-in-the-uae/ [Accessed 7 Apr. 2016].
Haygroup.com. (2016). Talent management. [online] Available at:
http://www.haygroup.com/uae/services/index.aspx?id=12008 [Accessed 7 Apr. 2016].
Research Design: Qualitative and Quantitative Approaches John W. Creswell. (1996). The
Library Quarterly, 66(2), pp.225-226.
Wilson, R. and Creswell, J. (1996). Research Design: Qualitative and Quantitative Approaches.
Journal of Marketing Research, 33(2), p.252.
Shelton, C., Smith, A. and Mort, M. (2014). Opening up the black box: an introduction to
qualitative research methods in anaesthesia. Anaesthesia, 69(3), pp.270-280.
Hawamdeh, S. and Raigangar, V. (2014). Qualitative interviewing: methodological challenges in
Arab settings. Nurse Researcher, 21(3), pp.27-31.
Guercini, S. (2014). New qualitative research methodologies in management. Management
Decision, 52(4), pp.662-674.
SME Advisor Middle East. (2013). Talent Management in the UAE. [online] Available at:
http://www.smeadvisor.com/news/talent-management-in-the-uae/ [Accessed 7 Apr. 2016].
Haygroup.com. (2016). Talent management. [online] Available at:
http://www.haygroup.com/uae/services/index.aspx?id=12008 [Accessed 7 Apr. 2016].
1 out of 42
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





