Inventory Storage System: Cloud Design, Security & Implementation
VerifiedAdded on 2023/06/04
|14
|2596
|338
Report
AI Summary
This report provides a comprehensive analysis and design of an inventory storage system for ABC organization, emphasizing cloud-based deployment for accessibility across various geographical locations. It explores system components, including the recommendation of Platform-as-a-Service (PaaS) for its security framework and cost-effectiveness, as well as a hybrid cloud model to manage varied data sensitivity levels. The report details user-interface design concepts, focusing on user experience, consistency, and interactivity, and addresses security concerns such as malware attacks, data breaches, and denial-of-service attacks, proposing mitigation measures like access control, encryption, and secure transactions. Furthermore, it outlines the planning and management of the project, covering implementation, testing, deployment, data conversion, user training, and change/version control using GitHub.

Inventory Storage System
System Analysis & Design
Name
Email
System Analysis & Design
Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Inventory Storage System
Table of Contents
Introduction...........................................................................................................................................2
System Components & Environment.....................................................................................................2
Platform-as-a-Service........................................................................................................................2
Hybrid Cloud Model..........................................................................................................................3
Best-Practice User-Interface Design Concepts......................................................................................4
Security Concerns & Controls...............................................................................................................8
Access control...................................................................................................................................8
Encryption.........................................................................................................................................9
Digital signatures...............................................................................................................................9
Secure transactions..........................................................................................................................10
Planning & Managing the Project: Implementation, Testing & Deployment.......................................10
Converting and initializing data.......................................................................................................10
References...........................................................................................................................................12
1
Table of Contents
Introduction...........................................................................................................................................2
System Components & Environment.....................................................................................................2
Platform-as-a-Service........................................................................................................................2
Hybrid Cloud Model..........................................................................................................................3
Best-Practice User-Interface Design Concepts......................................................................................4
Security Concerns & Controls...............................................................................................................8
Access control...................................................................................................................................8
Encryption.........................................................................................................................................9
Digital signatures...............................................................................................................................9
Secure transactions..........................................................................................................................10
Planning & Managing the Project: Implementation, Testing & Deployment.......................................10
Converting and initializing data.......................................................................................................10
References...........................................................................................................................................12
1

Inventory Storage System
Introduction
The report has been developed for the inventory storage system being developed and
implemented for ABC organization. There are several phases and activities that are involved
in the system design, development, execution, implementation, and deployment phases. The
details of the system components and user-interface design concepts are included in the
report. The security concerns and mitigation measures are included along with the planning
and management of implementation, testing, and deployment phases.
System Components & Environment
The cloud-based platforms will be used for the system deployment and delivery. It is because
ABC organization operates from varied geographical locations. The deployment of cloud-
based system will ensure that the easier access is provided to the users and the remote
monitoring and control is also made possible. The delivery and deployment models of the
cloud are as explained below.
Platform-as-a-Service
There are primarily three types of cloud delivery models that have been developed as
Platform as a Service (PaaS), Infrastructure as a Service (IaaS), and Software as a Service
(SaaS). The delivery model that is recommended for the inventory storage system of ABC
organization is PaaS. The systems tasks and activities will be performed with the PaaS cloud
framework. The model has been recommended for the system due to the security framework
and platform that it will provide (Comendador & Guillo, 2014). There will be built-in
security protocols that will be integrated in this platform which will enhance the overall
security of the inventory storage system. The requirements of the system will be met by PaaS
cloud model along with cost-savings and cost effectiveness.
2
Introduction
The report has been developed for the inventory storage system being developed and
implemented for ABC organization. There are several phases and activities that are involved
in the system design, development, execution, implementation, and deployment phases. The
details of the system components and user-interface design concepts are included in the
report. The security concerns and mitigation measures are included along with the planning
and management of implementation, testing, and deployment phases.
System Components & Environment
The cloud-based platforms will be used for the system deployment and delivery. It is because
ABC organization operates from varied geographical locations. The deployment of cloud-
based system will ensure that the easier access is provided to the users and the remote
monitoring and control is also made possible. The delivery and deployment models of the
cloud are as explained below.
Platform-as-a-Service
There are primarily three types of cloud delivery models that have been developed as
Platform as a Service (PaaS), Infrastructure as a Service (IaaS), and Software as a Service
(SaaS). The delivery model that is recommended for the inventory storage system of ABC
organization is PaaS. The systems tasks and activities will be performed with the PaaS cloud
framework. The model has been recommended for the system due to the security framework
and platform that it will provide (Comendador & Guillo, 2014). There will be built-in
security protocols that will be integrated in this platform which will enhance the overall
security of the inventory storage system. The requirements of the system will be met by PaaS
cloud model along with cost-savings and cost effectiveness.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Inventory Storage System
Hybrid Cloud Model
There are three categories of cloud deployment models that have been defined as public
cloud, private cloud, and hybrid cloud models. The inventory storage system of ABC
organization will include varied sets of information as critical data sets, non-critical data sets,
private data sets, public information, sensitive, and internal sets of data. The services and
activities performed by the system will make use of these data sets. Some of the applications
may use sensitive and critical data sets and private cloud will be apt for such services (Sood,
2013). The ones utilizing public data sets will work best with private cloud. The hybrid cloud
model will provide a combination of the two. The architectural model shall make use of three
tier network for its implementation.
Figure 1: cloud model (Author)
The office has three clear and distinct areas in the building facility. The first room is the main
office itself, the second is the room where computers are kept and the third one being the
warehouse. The router connects to the ISP using a T1 Router and it remains behind a
hardware Firewall. Connection is split using Ethernet and Network switches and it is
connected to the main server as well. Further ahead, the two facilities are also connected to
3
Hybrid Cloud Model
There are three categories of cloud deployment models that have been defined as public
cloud, private cloud, and hybrid cloud models. The inventory storage system of ABC
organization will include varied sets of information as critical data sets, non-critical data sets,
private data sets, public information, sensitive, and internal sets of data. The services and
activities performed by the system will make use of these data sets. Some of the applications
may use sensitive and critical data sets and private cloud will be apt for such services (Sood,
2013). The ones utilizing public data sets will work best with private cloud. The hybrid cloud
model will provide a combination of the two. The architectural model shall make use of three
tier network for its implementation.
Figure 1: cloud model (Author)
The office has three clear and distinct areas in the building facility. The first room is the main
office itself, the second is the room where computers are kept and the third one being the
warehouse. The router connects to the ISP using a T1 Router and it remains behind a
hardware Firewall. Connection is split using Ethernet and Network switches and it is
connected to the main server as well. Further ahead, the two facilities are also connected to
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Inventory Storage System
one another by Fiber Optic as well as Horizontal cable above ceilings and also within the
walls. After that, yet another switch is placed in the warehouse room as it also has several
workstations there to manage the warehouse.
Best-Practice User-Interface Design Concepts
There are design considerations that have been included while developing the user interface
of the inventory storage system.
User-experience is the primary goal for any of the applications, such as inventory
storage system. The navigation and scrolling that has been included on each of the
system screens is designed in such a manner that the navigation is smooth and over-
scrolling on the screens is avoided.
Consistency is one of the primary design principles that are required to be maintained.
The element of consistency in terms of color scheme and layout has been followed in
all the screens (Javaid, 2013).
The dashboard is updated on the real-time basis and the timestamp is included with
every update on the dashboard. The users will get to access reliable and valid
information at all instances.
Interactivity is one of the primary requirements of the design interface. There is a
search functionality included on the dashboard to make sure that the users can search
for the desired information and updates on the basis of the keywords that are entered.
Users are provided with acknowledgement on the screen, for instance, once the user
clicks on the login screen then the color of the login label changes. Similarly, when
the user clicks on the register option then a visual acknowledgement is provided to the
user with the change in the color of the text (Williams, Lindtner, Anderson &
Dourish, 2013).
4
one another by Fiber Optic as well as Horizontal cable above ceilings and also within the
walls. After that, yet another switch is placed in the warehouse room as it also has several
workstations there to manage the warehouse.
Best-Practice User-Interface Design Concepts
There are design considerations that have been included while developing the user interface
of the inventory storage system.
User-experience is the primary goal for any of the applications, such as inventory
storage system. The navigation and scrolling that has been included on each of the
system screens is designed in such a manner that the navigation is smooth and over-
scrolling on the screens is avoided.
Consistency is one of the primary design principles that are required to be maintained.
The element of consistency in terms of color scheme and layout has been followed in
all the screens (Javaid, 2013).
The dashboard is updated on the real-time basis and the timestamp is included with
every update on the dashboard. The users will get to access reliable and valid
information at all instances.
Interactivity is one of the primary requirements of the design interface. There is a
search functionality included on the dashboard to make sure that the users can search
for the desired information and updates on the basis of the keywords that are entered.
Users are provided with acknowledgement on the screen, for instance, once the user
clicks on the login screen then the color of the login label changes. Similarly, when
the user clicks on the register option then a visual acknowledgement is provided to the
user with the change in the color of the text (Williams, Lindtner, Anderson &
Dourish, 2013).
4
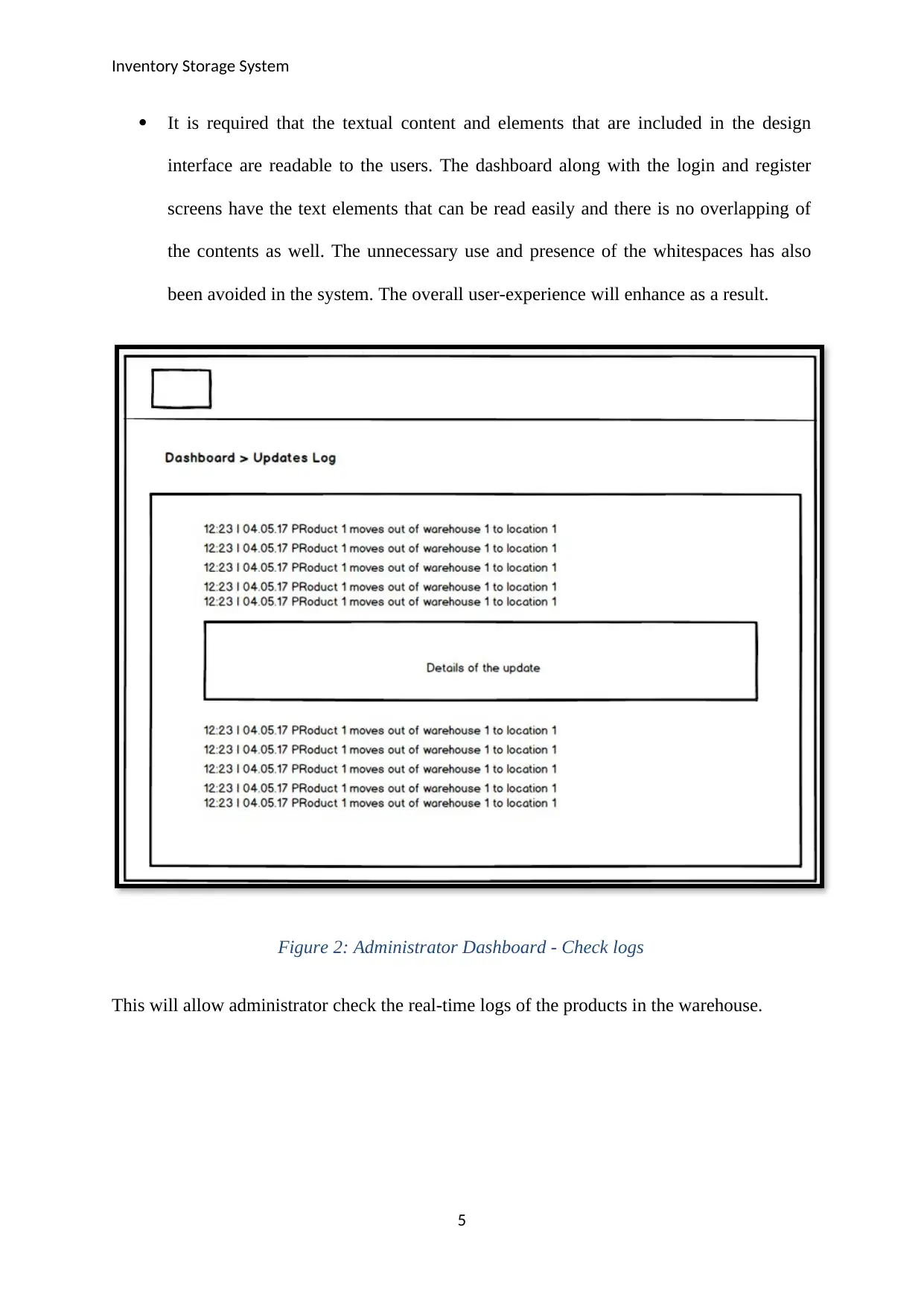
Inventory Storage System
It is required that the textual content and elements that are included in the design
interface are readable to the users. The dashboard along with the login and register
screens have the text elements that can be read easily and there is no overlapping of
the contents as well. The unnecessary use and presence of the whitespaces has also
been avoided in the system. The overall user-experience will enhance as a result.
Figure 2: Administrator Dashboard - Check logs
This will allow administrator check the real-time logs of the products in the warehouse.
5
It is required that the textual content and elements that are included in the design
interface are readable to the users. The dashboard along with the login and register
screens have the text elements that can be read easily and there is no overlapping of
the contents as well. The unnecessary use and presence of the whitespaces has also
been avoided in the system. The overall user-experience will enhance as a result.
Figure 2: Administrator Dashboard - Check logs
This will allow administrator check the real-time logs of the products in the warehouse.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
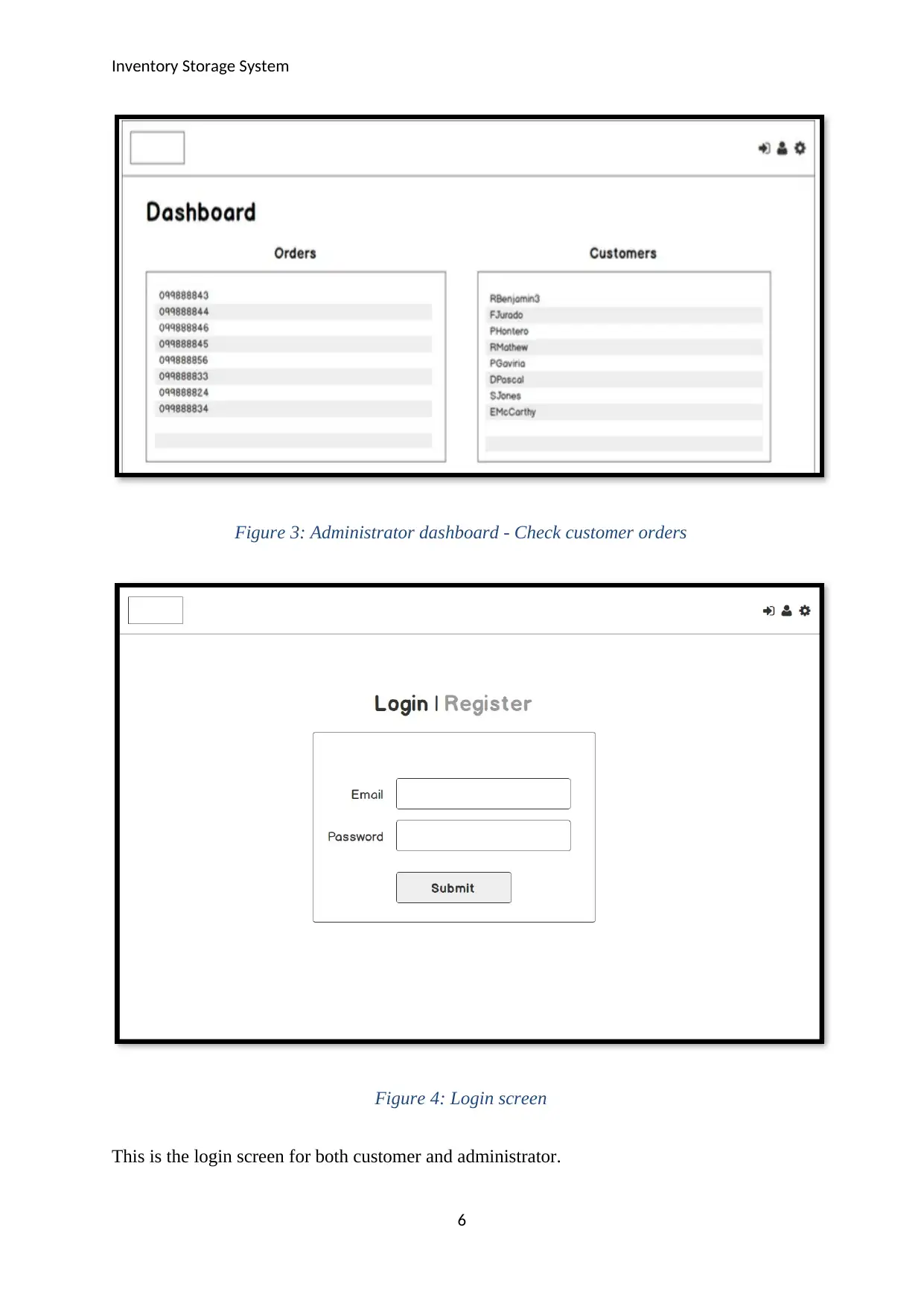
Inventory Storage System
Figure 3: Administrator dashboard - Check customer orders
Figure 4: Login screen
This is the login screen for both customer and administrator.
6
Figure 3: Administrator dashboard - Check customer orders
Figure 4: Login screen
This is the login screen for both customer and administrator.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
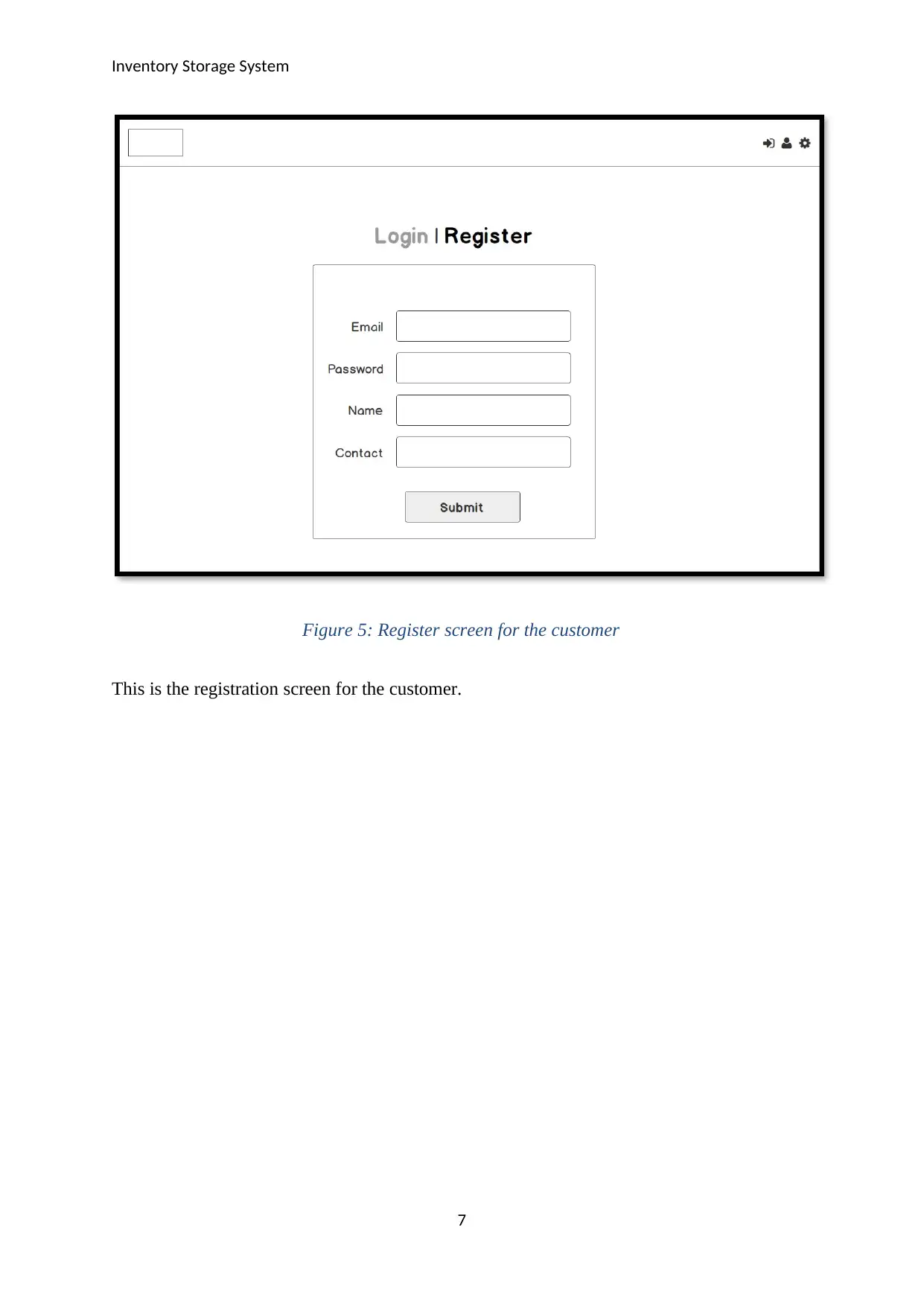
Inventory Storage System
Figure 5: Register screen for the customer
This is the registration screen for the customer.
7
Figure 5: Register screen for the customer
This is the registration screen for the customer.
7

Inventory Storage System
Figure 6: Administrator dashboard - Activity of customers
This screen is for the administrator where activities performed by the customer on the system
can be checked.
Security Concerns & Controls
Access control
The inventory information system will be implemented using the cloud-based platforms and
models. There will be several risks and security concerns that may emerge and will be
required to be handled. One of the primary concerns will be the occurrence of the malware
attacks. There may be virus attacks or ransomware attacks that may occur. The
confidentiality of the data sets will be compromised as a result. In the ransomware attacks,
8
Figure 6: Administrator dashboard - Activity of customers
This screen is for the administrator where activities performed by the customer on the system
can be checked.
Security Concerns & Controls
Access control
The inventory information system will be implemented using the cloud-based platforms and
models. There will be several risks and security concerns that may emerge and will be
required to be handled. One of the primary concerns will be the occurrence of the malware
attacks. There may be virus attacks or ransomware attacks that may occur. The
confidentiality of the data sets will be compromised as a result. In the ransomware attacks,
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Inventory Storage System
the attackers may lock the user access and demand a ransom amount in return. There will be
several network-based security concerns that the system will be exposed to. These will
include man in the middle attacks and eavesdropping attacks. The network activity will be
captured by the malevolent entities in an unauthorized manner. Data breaches and leakage
will also occur in the inventory storage system due to an unsecure network access point or
malicious user activities (Blandford, 2011). The denial of service attacks may occur on the
system which may result in the compromise of the information availability. The devices that
will be used to access the system may get lost which will also result in the compromise of the
information properties.
Encryption
There are various security controls and mitigations measures that shall be used and integrated
with the inventory storage system. The basic security of the system shall be enhanced using
access control mechanisms. The login screen shall be protected with advanced access control
using role-based and attribute-based access control. Also, the user identity shall be verified
and validated using multi-fold authentication in which one time passwords, single sign on,
and biometric authentication shall be used. The data sets shall be protected using encryption
of the same. With the encryption of the data sets, the textual elements will be converted to
their cipher forms using a security key (Nazir & Rashid, 2013). The receiver will not be able
to access the data sets without applying the security key at their end. As a result, the
malicious user will not be able to misuse the data sets. There are various encryption
algorithms that may be used as triple data encryption standard, advanced data encryption
standard, multi-path encryption standard, and hashing algorithms. The use of cryptography
shall be done with the digital certificates and hashing algorithms.
9
the attackers may lock the user access and demand a ransom amount in return. There will be
several network-based security concerns that the system will be exposed to. These will
include man in the middle attacks and eavesdropping attacks. The network activity will be
captured by the malevolent entities in an unauthorized manner. Data breaches and leakage
will also occur in the inventory storage system due to an unsecure network access point or
malicious user activities (Blandford, 2011). The denial of service attacks may occur on the
system which may result in the compromise of the information availability. The devices that
will be used to access the system may get lost which will also result in the compromise of the
information properties.
Encryption
There are various security controls and mitigations measures that shall be used and integrated
with the inventory storage system. The basic security of the system shall be enhanced using
access control mechanisms. The login screen shall be protected with advanced access control
using role-based and attribute-based access control. Also, the user identity shall be verified
and validated using multi-fold authentication in which one time passwords, single sign on,
and biometric authentication shall be used. The data sets shall be protected using encryption
of the same. With the encryption of the data sets, the textual elements will be converted to
their cipher forms using a security key (Nazir & Rashid, 2013). The receiver will not be able
to access the data sets without applying the security key at their end. As a result, the
malicious user will not be able to misuse the data sets. There are various encryption
algorithms that may be used as triple data encryption standard, advanced data encryption
standard, multi-path encryption standard, and hashing algorithms. The use of cryptography
shall be done with the digital certificates and hashing algorithms.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Inventory Storage System
Digital signatures
There must be identity management and verification done using these certificates and
algorithms to make sure that the information sets are always protected.
Secure transactions
It will also be necessary to make sure that any of the transactions occurring on the system are
secure. Network security will be necessary for this purpose. The system shall be integrated
with the anti-denial and anti-malware tools. There shall also be used of firewalls and proxy
servers that must be done (Zineddine, 2015). The network security tools, such as intrusion
detection and intrusion prevention systems must also be used. With the enhancement of
network security, the network-based risks and attacks will be prevented and the security of
the transactions will be ensured. There shall also be use of network logs and their tracking for
the overall system security.
Planning & Managing the Project: Implementation, Testing & Deployment
Converting and initializing data
Existing information needs to be embedded in the newer database before booting the system.
Additionaly, employee related information should also be integrated. Furthermore, data such
as product images, meta information, description, user data among others should also be
added to the inventory management system.
Training user
Training plays a critical role in how the project is ultimately a success at the organization. In
training, the users will be divided in two classes. First would be system operators and the
second would be end-users. End users would essentially be the bulk of the staff of various
10
Digital signatures
There must be identity management and verification done using these certificates and
algorithms to make sure that the information sets are always protected.
Secure transactions
It will also be necessary to make sure that any of the transactions occurring on the system are
secure. Network security will be necessary for this purpose. The system shall be integrated
with the anti-denial and anti-malware tools. There shall also be used of firewalls and proxy
servers that must be done (Zineddine, 2015). The network security tools, such as intrusion
detection and intrusion prevention systems must also be used. With the enhancement of
network security, the network-based risks and attacks will be prevented and the security of
the transactions will be ensured. There shall also be use of network logs and their tracking for
the overall system security.
Planning & Managing the Project: Implementation, Testing & Deployment
Converting and initializing data
Existing information needs to be embedded in the newer database before booting the system.
Additionaly, employee related information should also be integrated. Furthermore, data such
as product images, meta information, description, user data among others should also be
added to the inventory management system.
Training user
Training plays a critical role in how the project is ultimately a success at the organization. In
training, the users will be divided in two classes. First would be system operators and the
second would be end-users. End users would essentially be the bulk of the staff of various
10

Inventory Storage System
departments such as sales, inventory, marketing, IT etc. The other part of the users i.e., the
system operators would be the ones who would be handling the back-end of the inventory
management system.
The training is scheduled for over 4 days. Both of the class of users would be given a walk-
through tutorial of the entire system which will then be followed by step-by-step instructions.
Furthermore, each of the trainers would then proceed to give hands-on training to each of the
employees in using the system and then they would be asked to execute certain tasks. The
trainers would guide the users wherever they make a mistake and ensure they receive
complete information regarding the system. The trainers would also provide these staffs with
different documentation pertaining to the system such as system documentation, manual,
FAQs and guides among others.
c. Configuration the product environment
The entire inventory system consists of layers of hardware and software that combine to form
a usable system. The system consists of a logic server and the database server. These servers
are connected to the networking infrastructure which are further connected to Hardware
firewalls, switches, routers and workstations. The core IT Team is responsible for managing
the inventory system. They would also be responsible for managing the underlying platform
and operating system that helps run the inventory system such as the CentOS Operating
System, XAMPP, MySQL among others.
d. Packaging, installing and deploying the components
The developers would be deploying the newer system and would also be responsible in
supporting the IT team at the company to feed the initial data into the system. Furthermore,
they will be training and guiding them extensively during the initiation period of the system.
11
departments such as sales, inventory, marketing, IT etc. The other part of the users i.e., the
system operators would be the ones who would be handling the back-end of the inventory
management system.
The training is scheduled for over 4 days. Both of the class of users would be given a walk-
through tutorial of the entire system which will then be followed by step-by-step instructions.
Furthermore, each of the trainers would then proceed to give hands-on training to each of the
employees in using the system and then they would be asked to execute certain tasks. The
trainers would guide the users wherever they make a mistake and ensure they receive
complete information regarding the system. The trainers would also provide these staffs with
different documentation pertaining to the system such as system documentation, manual,
FAQs and guides among others.
c. Configuration the product environment
The entire inventory system consists of layers of hardware and software that combine to form
a usable system. The system consists of a logic server and the database server. These servers
are connected to the networking infrastructure which are further connected to Hardware
firewalls, switches, routers and workstations. The core IT Team is responsible for managing
the inventory system. They would also be responsible for managing the underlying platform
and operating system that helps run the inventory system such as the CentOS Operating
System, XAMPP, MySQL among others.
d. Packaging, installing and deploying the components
The developers would be deploying the newer system and would also be responsible in
supporting the IT team at the company to feed the initial data into the system. Furthermore,
they will be training and guiding them extensively during the initiation period of the system.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



