Cyber Security Assessment and Countermeasures for JL Company
VerifiedAdded on 2023/03/17
|13
|3064
|80
Report
AI Summary
This report presents a comprehensive investigation into the cyber security posture of JL Company, a small accounting firm in Perth, Western Australia. The report begins with an overview of the company, its recent transition to online services, and the resulting security challenges. Key issues identified include vulnerabilities in the operating systems, lack of security software, insecure internet access methods, and insufficient employee awareness. The report highlights five major issues requiring immediate attention, including privacy concerns, information misuse, internet service vulnerabilities, compromised confidentiality, and ethical/legal implications. To address these issues, the report recommends countermeasures such as information classification, data loss prevention (DLP), and hardware-centric security. The primary solution proposed is the adoption of a cloud-based security platform, detailing its features like data-at-rest encryption, cloud directory services, and a top-line perimeter firewall. The report also includes a detailed cost breakdown for implementing the proposed solutions, a comparison with alternative approaches, and further recommendations to enhance JL Company's cyber security. The report concludes by emphasizing the importance of proactive measures to protect the company's data assets and ensure business continuity in the face of evolving cyber threats.

Running head: INVESTIGATION INTO CYBER SECURITY
Investigation into cyber security
Name of the student:
Name of the university:
Author note:
Investigation into cyber security
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INVESTIGATION INTO CYBER SECURITY
Table of Contents
Introduction:...............................................................................................................................2
Overview of the company:.....................................................................................................2
Issues related to cyber security within the organisation:...........................................................3
5 Major issues that need immediate attention:.......................................................................4
Measure to address the identified issues:...................................................................................6
Proposed security platform too countermeasure the identified issues:..................................6
Detailed cost breakdown structure to provide solution to mitigate the issues:......................9
Comparison between the proposed solution and other alternatives:......................................9
Other recommendation:..........................................................................................................9
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11
Table of Contents
Introduction:...............................................................................................................................2
Overview of the company:.....................................................................................................2
Issues related to cyber security within the organisation:...........................................................3
5 Major issues that need immediate attention:.......................................................................4
Measure to address the identified issues:...................................................................................6
Proposed security platform too countermeasure the identified issues:..................................6
Detailed cost breakdown structure to provide solution to mitigate the issues:......................9
Comparison between the proposed solution and other alternatives:......................................9
Other recommendation:..........................................................................................................9
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11

2INVESTIGATION INTO CYBER SECURITY
Introduction:
With the increase in the number of cyber advancements, cyber risks are also gradually
growing in modern world. This gives rise to the importance of securing information and
important credentials that are associated with everyday life. The term information security is
precisely defined as the process of securing data from unauthorized access or disclosure,
disruption or modification as a result of some major data breach. Information security can be
applied physically or by electrical methods. The term information security refers to many
research areas such as online social media, mobile computing, cryptography, cyber forensics
and many more. Data assets are some of the important assets within organisation and are very
much critical for the survival of any business. Attackers or black hat people are likely to
attack different data assets of a company. One of the greatest challenges that is faced by any
organisation is identifying the risks associated with the organization’s data assets. Cyber
security is a constant growing area and thus targets towards identifying the major risks within
organizations. In this modern world of cyber advancement, it is important for every business
organisations to perform a cyber risk assessment based on the major data assets and
identifying and mitigating the major vulnerabilities or threats associated within the
organisation. The following report is prepared so as to investigate upon the security analysis
of the company of JL and to provide some countermeasures based on the threats identified
within the company.
Overview of the company:
The company of JL is a small company who mainly does accounting works resides in
Perth, Western Australia. The company is a small startup and currently employs about five
people. JL company is progressively making a giant move by planning to move its business
into the online market. As a part in doing so the company now has started sending its
Introduction:
With the increase in the number of cyber advancements, cyber risks are also gradually
growing in modern world. This gives rise to the importance of securing information and
important credentials that are associated with everyday life. The term information security is
precisely defined as the process of securing data from unauthorized access or disclosure,
disruption or modification as a result of some major data breach. Information security can be
applied physically or by electrical methods. The term information security refers to many
research areas such as online social media, mobile computing, cryptography, cyber forensics
and many more. Data assets are some of the important assets within organisation and are very
much critical for the survival of any business. Attackers or black hat people are likely to
attack different data assets of a company. One of the greatest challenges that is faced by any
organisation is identifying the risks associated with the organization’s data assets. Cyber
security is a constant growing area and thus targets towards identifying the major risks within
organizations. In this modern world of cyber advancement, it is important for every business
organisations to perform a cyber risk assessment based on the major data assets and
identifying and mitigating the major vulnerabilities or threats associated within the
organisation. The following report is prepared so as to investigate upon the security analysis
of the company of JL and to provide some countermeasures based on the threats identified
within the company.
Overview of the company:
The company of JL is a small company who mainly does accounting works resides in
Perth, Western Australia. The company is a small startup and currently employs about five
people. JL company is progressively making a giant move by planning to move its business
into the online market. As a part in doing so the company now has started sending its
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INVESTIGATION INTO CYBER SECURITY
confidential files via means of various online services. However, in recent years, it is seen
that the company and its employees are facing a number of security challenges within their
operating systems and other machine systems and thus it is necessary for JL company to
perform a risk assessment based on the current practices and use of their computer system
and data assets.
Issues related to cyber security within the organisation:
As per report, the company of JL, is recently facing some major cyber security risks
which are mentioned as follows:
1. The company of JL, uses the latest updates of Microsoft within their operating
system. As per recent reports, there exists some vulnerability with the latest update of
Microsoft within Windows 10 operating systems and causes some major security
risks.
2. None of the laptops consists of any software security installed in them. This a major
security issue as attackers might take advantage of this operating system in spreading
malware.
3. The internet access method of the company is via ADSL which uses a D-Link DSL-
2740B wireless router. Besides the company uses the Q Nap TS -412 NAS in order to
backup the data in the workstation using the WinSCP. With the use of this type of
internet access, a risk may occur where the whole system may get disrupted if there
occur some major cyber risks within the organisation.
4. Apart from the above-mentioned issues, other issues that exists within the
organization includes, lack in the use of Windows 2000 server within the
organisation, lack of awareness within the organisation as a result of which the
company failed to mitigate the ransomware attack that they faced in the year 2018.
confidential files via means of various online services. However, in recent years, it is seen
that the company and its employees are facing a number of security challenges within their
operating systems and other machine systems and thus it is necessary for JL company to
perform a risk assessment based on the current practices and use of their computer system
and data assets.
Issues related to cyber security within the organisation:
As per report, the company of JL, is recently facing some major cyber security risks
which are mentioned as follows:
1. The company of JL, uses the latest updates of Microsoft within their operating
system. As per recent reports, there exists some vulnerability with the latest update of
Microsoft within Windows 10 operating systems and causes some major security
risks.
2. None of the laptops consists of any software security installed in them. This a major
security issue as attackers might take advantage of this operating system in spreading
malware.
3. The internet access method of the company is via ADSL which uses a D-Link DSL-
2740B wireless router. Besides the company uses the Q Nap TS -412 NAS in order to
backup the data in the workstation using the WinSCP. With the use of this type of
internet access, a risk may occur where the whole system may get disrupted if there
occur some major cyber risks within the organisation.
4. Apart from the above-mentioned issues, other issues that exists within the
organization includes, lack in the use of Windows 2000 server within the
organisation, lack of awareness within the organisation as a result of which the
company failed to mitigate the ransomware attack that they faced in the year 2018.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INVESTIGATION INTO CYBER SECURITY
5. Another issue that is identified within the organisation is that all confidential data
stored within the company’s data set are not transferred with confidentiality as a result
of which any one can access the data that are transferred through emails.
All these mentioned cyber risks are identified within the organisation after an incident
that took place in the recent year where one of the employees inserted an USB drive into
the computer system of the company that he founded from the parking area. It is being
reported that from then the computer systems within the company started to have “a mind
of its own”.
5 Major issues that need immediate attention:
Among the major identified issues, some of the issues that need urgent attention and
needs to establish countermeasures are mentioned as below:
1. Issue related to privacy: As the company is using the latest update of Microsoft
within their operating system, major security issues are faced within their systems. As
reported, the recent update of Microsoft that came in the year 2019, has some serious
security vulnerabilities. As a result of which most the systems are prompted to install
the new windows update. But actually, these patches from Microsoft consists of bugs
that can cause malicious attacks to the computer systems
2. Issue related to information misuse: The employees within the company of JL, has
not got any IT expertise and thus lacks knowledge of cyber related issues. The
employees of the company have free access to each other’s computers and email
accounts. Thus, here the company lacks implementation of security policies within the
organisation (Vaniea, & Rashidi, 2016). Also, the confidential information of the
company is transferred through online methods without any cryptographic security
5. Another issue that is identified within the organisation is that all confidential data
stored within the company’s data set are not transferred with confidentiality as a result
of which any one can access the data that are transferred through emails.
All these mentioned cyber risks are identified within the organisation after an incident
that took place in the recent year where one of the employees inserted an USB drive into
the computer system of the company that he founded from the parking area. It is being
reported that from then the computer systems within the company started to have “a mind
of its own”.
5 Major issues that need immediate attention:
Among the major identified issues, some of the issues that need urgent attention and
needs to establish countermeasures are mentioned as below:
1. Issue related to privacy: As the company is using the latest update of Microsoft
within their operating system, major security issues are faced within their systems. As
reported, the recent update of Microsoft that came in the year 2019, has some serious
security vulnerabilities. As a result of which most the systems are prompted to install
the new windows update. But actually, these patches from Microsoft consists of bugs
that can cause malicious attacks to the computer systems
2. Issue related to information misuse: The employees within the company of JL, has
not got any IT expertise and thus lacks knowledge of cyber related issues. The
employees of the company have free access to each other’s computers and email
accounts. Thus, here the company lacks implementation of security policies within the
organisation (Vaniea, & Rashidi, 2016). Also, the confidential information of the
company is transferred through online methods without any cryptographic security

5INVESTIGATION INTO CYBER SECURITY
measures. As a result of this security issues and also as the systems lacks
implementation of security software, the employees of the company receive about 40
spam messages every day. This type of incidents may lead to some huge attack in
future like that of phishing, DDoS and many more.
3. Issue related to internet services: As reported the company is using the D-Link
DSL-2740B to access its internet usage. The first generation of ADSL type of routers
are reported to have many flaws which allows connection of remote devices with the
internet (Nikolai & Wang, 2014). In the year 2019, malware attack report has been
found with the ADSL routers. So, it is a great risk for the company of JL to use this
kind of internet access method even after they move towards to online platform where
more security concerns are necessary.
4. Issue related to the compromise of the confidentiality within the organisation:
As the company of JL has not got any major security policies in place hence, hence
the confidentiality of information within the organisation is greatly compromised
(Gupta, Agrawal & Yamaguchi, 2016). The company uses the email method to
transfer its files which is not at all a secured way and thus immediate action needs to
be taken in implementing proper security platforms so that the business can run
smoothly on their online platform via cryptographic techniques (Srinivasan, 2014).
5. Ethical and legal issues with the use of information assets within the
organisation: Thus, from the scenario it can be gathered that the organisation of JL
suffers from greater risks related to privacy, data gathering, security measures and
accessibility which falls under the ethical and legal issues of the organisation. Thus,
all these issues need immediate attention so as to provide countermeasures to mitigate
the issues.
measures. As a result of this security issues and also as the systems lacks
implementation of security software, the employees of the company receive about 40
spam messages every day. This type of incidents may lead to some huge attack in
future like that of phishing, DDoS and many more.
3. Issue related to internet services: As reported the company is using the D-Link
DSL-2740B to access its internet usage. The first generation of ADSL type of routers
are reported to have many flaws which allows connection of remote devices with the
internet (Nikolai & Wang, 2014). In the year 2019, malware attack report has been
found with the ADSL routers. So, it is a great risk for the company of JL to use this
kind of internet access method even after they move towards to online platform where
more security concerns are necessary.
4. Issue related to the compromise of the confidentiality within the organisation:
As the company of JL has not got any major security policies in place hence, hence
the confidentiality of information within the organisation is greatly compromised
(Gupta, Agrawal & Yamaguchi, 2016). The company uses the email method to
transfer its files which is not at all a secured way and thus immediate action needs to
be taken in implementing proper security platforms so that the business can run
smoothly on their online platform via cryptographic techniques (Srinivasan, 2014).
5. Ethical and legal issues with the use of information assets within the
organisation: Thus, from the scenario it can be gathered that the organisation of JL
suffers from greater risks related to privacy, data gathering, security measures and
accessibility which falls under the ethical and legal issues of the organisation. Thus,
all these issues need immediate attention so as to provide countermeasures to mitigate
the issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INVESTIGATION INTO CYBER SECURITY
Measure to address the identified issues:
In order to mitigate the identified issues within the organization of JL, the following
countermeasures need to be taken in terms of the following terms:
Information classification: Information classification is an important aspect that every
organisation needs to follow in order to determine the information according to their classes
(Elgazzar, Hassanein & Martin, 2014). The information system according to the US
classification level include three levels including-Top secret, Secret and Confidential
information. Doing so will help the company to analyses its information and maintain the
confidentiality of each of the data assets.
DLP or Data Loss Prevention: As the company is now planning to move its business to
online platform, so it is extremely important for the organisation to implement measures so as
to prevent the data loss within organisation (Sutikno, Stiawan & Subroto, 2014). There are
various types of DLP present each focused on a specific goal of preventing data loss. With
the advancement of competing technologies, DLP helps in offering a clear image of
preventing data from getting lost.
Hardware centric security: Hardware centric security is a type of security approach that
needs to be taken in order to secure the networks, servers and other applications (Lesjak,
Hein & Winter, 2015). Applying this type of data security measure will help the company in
overcoming the disconnection between IT security technology aligning with the business
strategy objectives.
Proposed security platform too countermeasure the identified issues:
Apart from the above-mentioned security measure, it is also recommended for the
organisation to opt for a cloud-based platform in order to proceed with their online business
(Liao et al., 2016). As the company of JL is tending to move its business to online platforms,
Measure to address the identified issues:
In order to mitigate the identified issues within the organization of JL, the following
countermeasures need to be taken in terms of the following terms:
Information classification: Information classification is an important aspect that every
organisation needs to follow in order to determine the information according to their classes
(Elgazzar, Hassanein & Martin, 2014). The information system according to the US
classification level include three levels including-Top secret, Secret and Confidential
information. Doing so will help the company to analyses its information and maintain the
confidentiality of each of the data assets.
DLP or Data Loss Prevention: As the company is now planning to move its business to
online platform, so it is extremely important for the organisation to implement measures so as
to prevent the data loss within organisation (Sutikno, Stiawan & Subroto, 2014). There are
various types of DLP present each focused on a specific goal of preventing data loss. With
the advancement of competing technologies, DLP helps in offering a clear image of
preventing data from getting lost.
Hardware centric security: Hardware centric security is a type of security approach that
needs to be taken in order to secure the networks, servers and other applications (Lesjak,
Hein & Winter, 2015). Applying this type of data security measure will help the company in
overcoming the disconnection between IT security technology aligning with the business
strategy objectives.
Proposed security platform too countermeasure the identified issues:
Apart from the above-mentioned security measure, it is also recommended for the
organisation to opt for a cloud-based platform in order to proceed with their online business
(Liao et al., 2016). As the company of JL is tending to move its business to online platforms,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INVESTIGATION INTO CYBER SECURITY
hence it is also obvious that the organisation will face more issue with its systems related to
cyber security with respect to the issues that are identified within the organization (Ibrahim,
Hamlyn-Harris & Grundy, 2016). With the more advancement in its business, the company
now have to face a greater number of peaks in traffics and thus needs to provide
countermeasures to combat the recent security issues identified (Chang, Kuo &
Ramachandran, 2016). Cloud security platform provides a wide range of security features so
as to provide business organizations with the best possible security measures. The security
features of cloud that will benefit the organisation of JL includes-
Data at rest encryption- This feature of cloud allows data transmission with various
encryption features (Chen & Lee, 2014). As the company of JL do not have any such
encryption feature, this feature of cloud will help the company in combatting the
major issue that it faced in the company while receiving about 40 spam messages in
their computer systems (Kalaiprasath, Elankavi & Udayakumar, 2017).
hence it is also obvious that the organisation will face more issue with its systems related to
cyber security with respect to the issues that are identified within the organization (Ibrahim,
Hamlyn-Harris & Grundy, 2016). With the more advancement in its business, the company
now have to face a greater number of peaks in traffics and thus needs to provide
countermeasures to combat the recent security issues identified (Chang, Kuo &
Ramachandran, 2016). Cloud security platform provides a wide range of security features so
as to provide business organizations with the best possible security measures. The security
features of cloud that will benefit the organisation of JL includes-
Data at rest encryption- This feature of cloud allows data transmission with various
encryption features (Chen & Lee, 2014). As the company of JL do not have any such
encryption feature, this feature of cloud will help the company in combatting the
major issue that it faced in the company while receiving about 40 spam messages in
their computer systems (Kalaiprasath, Elankavi & Udayakumar, 2017).
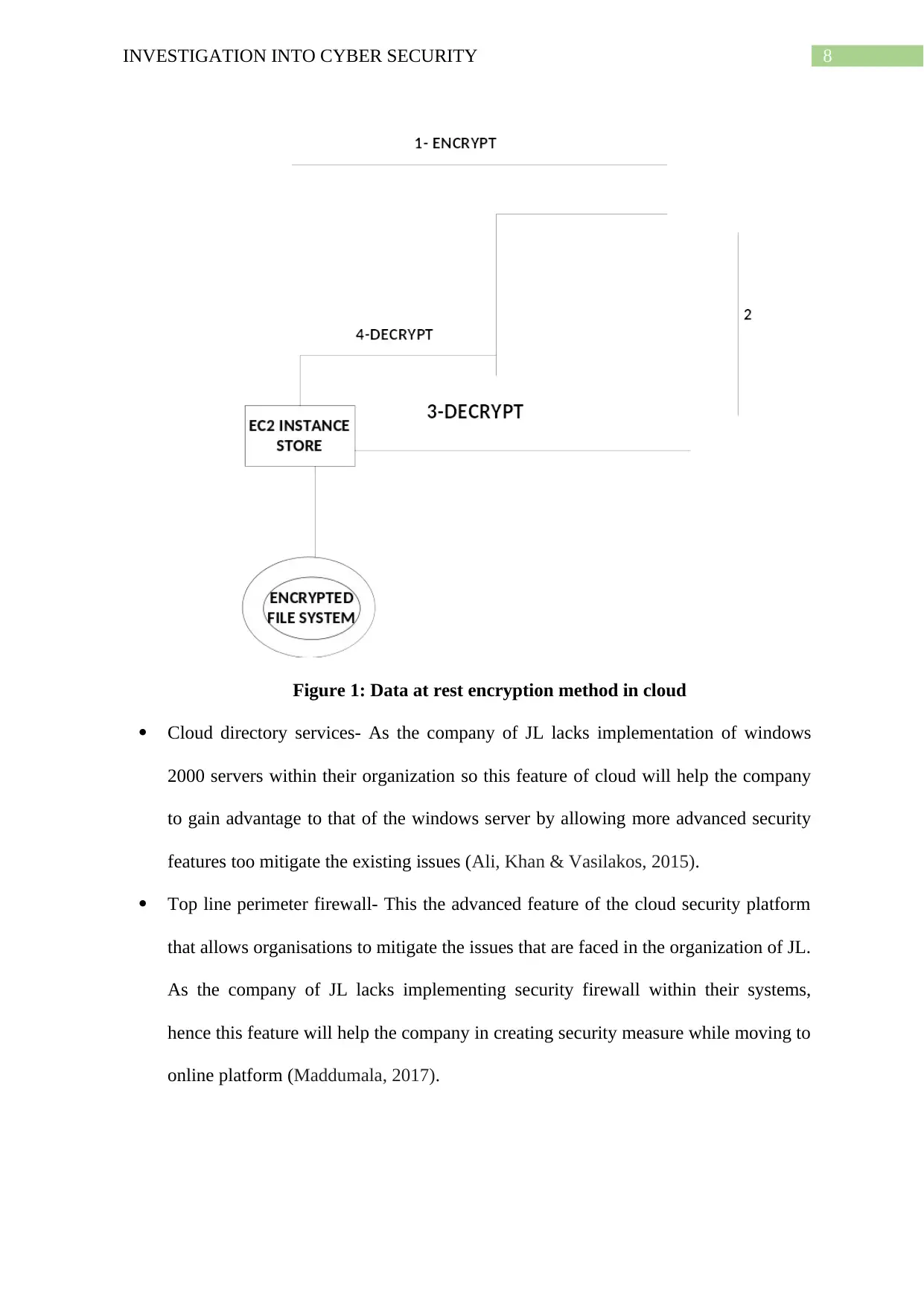
8INVESTIGATION INTO CYBER SECURITY
Figure 1: Data at rest encryption method in cloud
Cloud directory services- As the company of JL lacks implementation of windows
2000 servers within their organization so this feature of cloud will help the company
to gain advantage to that of the windows server by allowing more advanced security
features too mitigate the existing issues (Ali, Khan & Vasilakos, 2015).
Top line perimeter firewall- This the advanced feature of the cloud security platform
that allows organisations to mitigate the issues that are faced in the organization of JL.
As the company of JL lacks implementing security firewall within their systems,
hence this feature will help the company in creating security measure while moving to
online platform (Maddumala, 2017).
Figure 1: Data at rest encryption method in cloud
Cloud directory services- As the company of JL lacks implementation of windows
2000 servers within their organization so this feature of cloud will help the company
to gain advantage to that of the windows server by allowing more advanced security
features too mitigate the existing issues (Ali, Khan & Vasilakos, 2015).
Top line perimeter firewall- This the advanced feature of the cloud security platform
that allows organisations to mitigate the issues that are faced in the organization of JL.
As the company of JL lacks implementing security firewall within their systems,
hence this feature will help the company in creating security measure while moving to
online platform (Maddumala, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
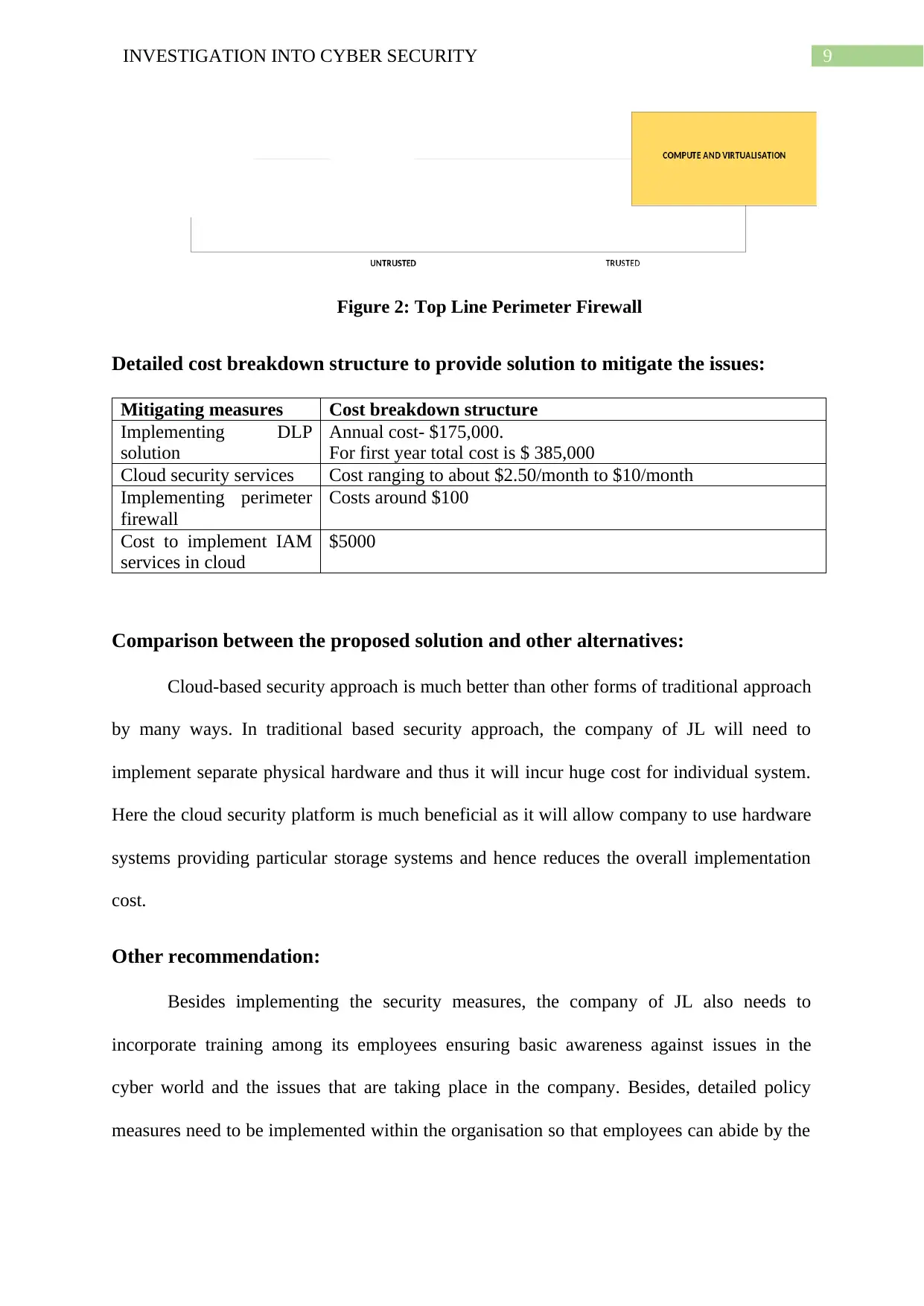
9INVESTIGATION INTO CYBER SECURITY
Figure 2: Top Line Perimeter Firewall
Detailed cost breakdown structure to provide solution to mitigate the issues:
Mitigating measures Cost breakdown structure
Implementing DLP
solution
Annual cost- $175,000.
For first year total cost is $ 385,000
Cloud security services Cost ranging to about $2.50/month to $10/month
Implementing perimeter
firewall
Costs around $100
Cost to implement IAM
services in cloud
$5000
Comparison between the proposed solution and other alternatives:
Cloud-based security approach is much better than other forms of traditional approach
by many ways. In traditional based security approach, the company of JL will need to
implement separate physical hardware and thus it will incur huge cost for individual system.
Here the cloud security platform is much beneficial as it will allow company to use hardware
systems providing particular storage systems and hence reduces the overall implementation
cost.
Other recommendation:
Besides implementing the security measures, the company of JL also needs to
incorporate training among its employees ensuring basic awareness against issues in the
cyber world and the issues that are taking place in the company. Besides, detailed policy
measures need to be implemented within the organisation so that employees can abide by the
Figure 2: Top Line Perimeter Firewall
Detailed cost breakdown structure to provide solution to mitigate the issues:
Mitigating measures Cost breakdown structure
Implementing DLP
solution
Annual cost- $175,000.
For first year total cost is $ 385,000
Cloud security services Cost ranging to about $2.50/month to $10/month
Implementing perimeter
firewall
Costs around $100
Cost to implement IAM
services in cloud
$5000
Comparison between the proposed solution and other alternatives:
Cloud-based security approach is much better than other forms of traditional approach
by many ways. In traditional based security approach, the company of JL will need to
implement separate physical hardware and thus it will incur huge cost for individual system.
Here the cloud security platform is much beneficial as it will allow company to use hardware
systems providing particular storage systems and hence reduces the overall implementation
cost.
Other recommendation:
Besides implementing the security measures, the company of JL also needs to
incorporate training among its employees ensuring basic awareness against issues in the
cyber world and the issues that are taking place in the company. Besides, detailed policy
measures need to be implemented within the organisation so that employees can abide by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INVESTIGATION INTO CYBER SECURITY
rules in order to access the files and other confidential document within the company (Safa,
Von Solm & Furnell, 2016).
Conclusion:
Thus, from the above report it can be concluded that for every organization it is
important to have a security measure implemented within the system. In this respect cloud
security platform plays a vital role in providing security measures allowing companies to
backup files within the offsite while decreasing the hacking potential of the black hat peoples.
For the company of JL, as the organization faces major issues within its systems and as it is
tending to move its business towards online platform, hence cloud security platform will be
the best option to implement countermeasures against the threats.
rules in order to access the files and other confidential document within the company (Safa,
Von Solm & Furnell, 2016).
Conclusion:
Thus, from the above report it can be concluded that for every organization it is
important to have a security measure implemented within the system. In this respect cloud
security platform plays a vital role in providing security measures allowing companies to
backup files within the offsite while decreasing the hacking potential of the black hat peoples.
For the company of JL, as the organization faces major issues within its systems and as it is
tending to move its business towards online platform, hence cloud security platform will be
the best option to implement countermeasures against the threats.

11INVESTIGATION INTO CYBER SECURITY
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chen, H. C., & Lee, P. P. (2014). Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), 407-416.
Elgazzar, K., Hassanein, H. S., & Martin, P. (2014). Daas: Cloud-based mobile web service
discovery. Pervasive and Mobile Computing, 13, 67-84.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
Lesjak, C., Hein, D., & Winter, J. (2015, November). Hardware-security technologies for
industrial IoT: TrustZone and security controller. In IECON 2015-41st Annual
Conference of the IEEE Industrial Electronics Society (pp. 002589-002595). IEEE.
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chen, H. C., & Lee, P. P. (2014). Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), 407-416.
Elgazzar, K., Hassanein, H. S., & Martin, P. (2014). Daas: Cloud-based mobile web service
discovery. Pervasive and Mobile Computing, 13, 67-84.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
Lesjak, C., Hein, D., & Winter, J. (2015, November). Hardware-security technologies for
industrial IoT: TrustZone and security controller. In IECON 2015-41st Annual
Conference of the IEEE Industrial Electronics Society (pp. 002589-002595). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




