INVESTIGATION INTO SECURITY OF MOBILE APPS
Added on 2022-10-17
37 Pages9059 Words259 Views
Running Head: INVESTIGATION INTO SECURITY OF MOBILE APPS 1
An Investigation into the Security of Mobile Phone Communication Apps
Affiliate Institution
Professor’s Name
Student
Date
An Investigation into the Security of Mobile Phone Communication Apps
Affiliate Institution
Professor’s Name
Student
Date

INVESTIGATION INTO SECURITY OF MOBILE APPS 2
1.0 Abstract
Information technology is currently widely used all over the world. Technology has made
everything possible and more so has led to improved business standards. Most companies across
the globe have embraced the use of technology to improve their business productivity.
Technology is advancing at a higher rate such that mobile application which will help us to run
our business anywhere we are in have been developed. For this reason, we can manage our
businesses anywhere on the earth surface so long as we are connected to the internet.
Using mobile applications, we can communicate vividly with our customers and as well with our
company employees. Technology advances from a standalone mobile phone, and now we are in
the era of smartphones. With the use of mobile phones such as tablets, IPad, iPhone or
Smartphones, we can carry on with our usual businesses as if we are in office. Even while
transacting, everything is done over the internet. (Wang & Lau, n.d.)
Internet of Things (IoT) is a technology which has enabled us to manage our businesses
everywhere across the earth surface. Through the technology we are connected as one village
even if we are far from each other. The only thing which IoT has done is building trust that we
can do anything over the internet. (Velu, 2016)
In this project report, we will deal with security issues on the mobile application we are using to
transact our businesses. We will ask ourselves some questions before the implementation of this
project. The kind of questions includes; how secure are we to employ these mobile applications
technologies? Is the mobile application reliable to our day to day business processes? What are
the impacts and benefits of the mobile app to the business processes? Does the mobile
1.0 Abstract
Information technology is currently widely used all over the world. Technology has made
everything possible and more so has led to improved business standards. Most companies across
the globe have embraced the use of technology to improve their business productivity.
Technology is advancing at a higher rate such that mobile application which will help us to run
our business anywhere we are in have been developed. For this reason, we can manage our
businesses anywhere on the earth surface so long as we are connected to the internet.
Using mobile applications, we can communicate vividly with our customers and as well with our
company employees. Technology advances from a standalone mobile phone, and now we are in
the era of smartphones. With the use of mobile phones such as tablets, IPad, iPhone or
Smartphones, we can carry on with our usual businesses as if we are in office. Even while
transacting, everything is done over the internet. (Wang & Lau, n.d.)
Internet of Things (IoT) is a technology which has enabled us to manage our businesses
everywhere across the earth surface. Through the technology we are connected as one village
even if we are far from each other. The only thing which IoT has done is building trust that we
can do anything over the internet. (Velu, 2016)
In this project report, we will deal with security issues on the mobile application we are using to
transact our businesses. We will ask ourselves some questions before the implementation of this
project. The kind of questions includes; how secure are we to employ these mobile applications
technologies? Is the mobile application reliable to our day to day business processes? What are
the impacts and benefits of the mobile app to the business processes? Does the mobile

INVESTIGATION INTO SECURITY OF MOBILE APPS 3
application receive a positive response from the customers? At what cost does it incur to be
developed?
After discussing the questions, the problem is given a solution to ensure that all the requirements
have been achieved. (Thuraisingham, 2001) The project team members will have to use these
research questions to clearly understand the customer requirements and how secure will be the
system after the solution have been provided. Finally, detectives which will help to detect these
threats will be established so that the threats will be blocked before harming the system.
application receive a positive response from the customers? At what cost does it incur to be
developed?
After discussing the questions, the problem is given a solution to ensure that all the requirements
have been achieved. (Thuraisingham, 2001) The project team members will have to use these
research questions to clearly understand the customer requirements and how secure will be the
system after the solution have been provided. Finally, detectives which will help to detect these
threats will be established so that the threats will be blocked before harming the system.

INVESTIGATION INTO SECURITY OF MOBILE APPS 4
Table of Contents
1.0 Abstract................................................................................................................ 2
2.0 Introduction.......................................................................................................... 6
2.1 The purpose of the Research............................................................................7
2.2 Research Scope................................................................................................. 8
2.1 Project Background........................................................................................... 8
2.2 Research Questions........................................................................................... 9
3.0 Literature review................................................................................................ 11
4.0 Methodology....................................................................................................... 12
4.1 Waterfall Model............................................................................................... 13
4.1.0 Project Planning........................................................................................ 13
4.1.1 Requirements definition............................................................................ 14
4.1.2 System design........................................................................................... 14
Design view of how weekly report will be done..................................................15
4.1.3 Research development process................................................................15
4.1.4 Integration and Testing............................................................................. 15
4.1.5 Installation and Acceptance......................................................................15
4.1 Work Break-Down Structure and Weekly Plan.................................................16
4.1.6 Communication Plan.................................................................................... 17
5.0 Literature Review Results................................................................................... 18
5.1 Mobile application........................................................................................... 18
5.2 Mobile application system vulnerabilities........................................................19
5.3 Mobile Application Testing Method..................................................................20
5.4 Mobile Application Approval or Rejection........................................................21
5.5 Risks and threats model..................................................................................23
5.6 Results Analysis.............................................................................................. 25
5.7 Tools and Services used..................................................................................26
6.0 Discussion.......................................................................................................... 27
6.1.0 Source Code Testing.................................................................................... 27
6.2.0 Correctness Testing Method.........................................................................28
6.2.0 Managing and Un-mapping Mobile Applications...........................................29
6.3.0 Limitation of Approving or Rejecting the Mobile Apps..................................30
7.0 Reflection of the research.................................................................................. 31
Conclusion................................................................................................................ 34
Table of Contents
1.0 Abstract................................................................................................................ 2
2.0 Introduction.......................................................................................................... 6
2.1 The purpose of the Research............................................................................7
2.2 Research Scope................................................................................................. 8
2.1 Project Background........................................................................................... 8
2.2 Research Questions........................................................................................... 9
3.0 Literature review................................................................................................ 11
4.0 Methodology....................................................................................................... 12
4.1 Waterfall Model............................................................................................... 13
4.1.0 Project Planning........................................................................................ 13
4.1.1 Requirements definition............................................................................ 14
4.1.2 System design........................................................................................... 14
Design view of how weekly report will be done..................................................15
4.1.3 Research development process................................................................15
4.1.4 Integration and Testing............................................................................. 15
4.1.5 Installation and Acceptance......................................................................15
4.1 Work Break-Down Structure and Weekly Plan.................................................16
4.1.6 Communication Plan.................................................................................... 17
5.0 Literature Review Results................................................................................... 18
5.1 Mobile application........................................................................................... 18
5.2 Mobile application system vulnerabilities........................................................19
5.3 Mobile Application Testing Method..................................................................20
5.4 Mobile Application Approval or Rejection........................................................21
5.5 Risks and threats model..................................................................................23
5.6 Results Analysis.............................................................................................. 25
5.7 Tools and Services used..................................................................................26
6.0 Discussion.......................................................................................................... 27
6.1.0 Source Code Testing.................................................................................... 27
6.2.0 Correctness Testing Method.........................................................................28
6.2.0 Managing and Un-mapping Mobile Applications...........................................29
6.3.0 Limitation of Approving or Rejecting the Mobile Apps..................................30
7.0 Reflection of the research.................................................................................. 31
Conclusion................................................................................................................ 34


INVESTIGATION INTO SECURITY OF MOBILE APPS 6
2.0 Introduction
Mobile communication is currently the most rapidly growing technology as the world is
targeting every work will in the near future be done at the palm of your hand. The current market
trend for mobile application technologies such as android applications, apple store for IPhone
and many more to name but few are rapidly growing at an alarming rate. As we can witness that
within a short period of time after the release of the handy cell phones, smartphones, tablets,
iPhone and iPad came into being. This is evidence in the sense that mobile technology is
constantly changing over time. (Thuraisingham, 2001)
The change is growing faster because it has caught the warm in the market where every person is
in high demand for it. When the internet was embedded on mobile devices, so many people gain
a higher preference for purchasing a mobile device rather than buying a desktop or laptop
computer. Smartphones this day serve so many transactions, including online payments.
How Mobile Application works
2.0 Introduction
Mobile communication is currently the most rapidly growing technology as the world is
targeting every work will in the near future be done at the palm of your hand. The current market
trend for mobile application technologies such as android applications, apple store for IPhone
and many more to name but few are rapidly growing at an alarming rate. As we can witness that
within a short period of time after the release of the handy cell phones, smartphones, tablets,
iPhone and iPad came into being. This is evidence in the sense that mobile technology is
constantly changing over time. (Thuraisingham, 2001)
The change is growing faster because it has caught the warm in the market where every person is
in high demand for it. When the internet was embedded on mobile devices, so many people gain
a higher preference for purchasing a mobile device rather than buying a desktop or laptop
computer. Smartphones this day serve so many transactions, including online payments.
How Mobile Application works

INVESTIGATION INTO SECURITY OF MOBILE APPS 7
This report explains various issues which we may encounter with the use of the mobile
application and the countermeasures we can use to control them. (Mukherjea, n.d.) An
investigation will be carried out to check whether the use of mobile application technology to
transact our business is safe or not.
The most crucial aspect of the implementation of technology is security. Developing a mobile
application without considering its security is a waste of time as a resource. We can ensure that
the mobile application is secure enough by employing various techniques such as unit testing or
system testing. Unit testing is a technique done by programmers during the development stage of
the application, while system testing is done after the development process by testers. This kind
of exercise will help to ensure that the programs we will be deploying for first use are safe and
secure. Also, developing mobile applications is not like in the past. The mobile phone is also
changing their compatibility features like 2G, 3G, 4G and currently we are migrating to the fifth-
generation (5G), WPS Wi-Fi security settings, Bluetooth and NFC. All these are the mobile
application technologies to enhance the security and the functionality of mobile devices. (Makan,
2013) This is in conjunction with the internet of things, and that is the reason why we are
regarding them as an IoT device.
Day in day out, we hear of cases of system hacking. This means that these mobile applications
are not secure at all. This project will expound more on these threats that are affecting our mobile
application systems.
2.1 The purpose of the Research
This record characterizes a mobile application checking process and gives direction in planning
and actualizing an application security process, creating security prerequisites for mobile
applications, recognizing suitable instruments for testing mobile applications and deciding
This report explains various issues which we may encounter with the use of the mobile
application and the countermeasures we can use to control them. (Mukherjea, n.d.) An
investigation will be carried out to check whether the use of mobile application technology to
transact our business is safe or not.
The most crucial aspect of the implementation of technology is security. Developing a mobile
application without considering its security is a waste of time as a resource. We can ensure that
the mobile application is secure enough by employing various techniques such as unit testing or
system testing. Unit testing is a technique done by programmers during the development stage of
the application, while system testing is done after the development process by testers. This kind
of exercise will help to ensure that the programs we will be deploying for first use are safe and
secure. Also, developing mobile applications is not like in the past. The mobile phone is also
changing their compatibility features like 2G, 3G, 4G and currently we are migrating to the fifth-
generation (5G), WPS Wi-Fi security settings, Bluetooth and NFC. All these are the mobile
application technologies to enhance the security and the functionality of mobile devices. (Makan,
2013) This is in conjunction with the internet of things, and that is the reason why we are
regarding them as an IoT device.
Day in day out, we hear of cases of system hacking. This means that these mobile applications
are not secure at all. This project will expound more on these threats that are affecting our mobile
application systems.
2.1 The purpose of the Research
This record characterizes a mobile application checking process and gives direction in planning
and actualizing an application security process, creating security prerequisites for mobile
applications, recognizing suitable instruments for testing mobile applications and deciding

INVESTIGATION INTO SECURITY OF MOBILE APPS 8
whether a handy application is satisfactory for arrangement on an association's cell phones. An
outline of methods usually utilized by programming confirmation experts is given, including
techniques for testing for discrete mobile application vulnerabilities and misconfigurations
identified with mobile application software. (Hoog, 2011)
2.2 Research Scope
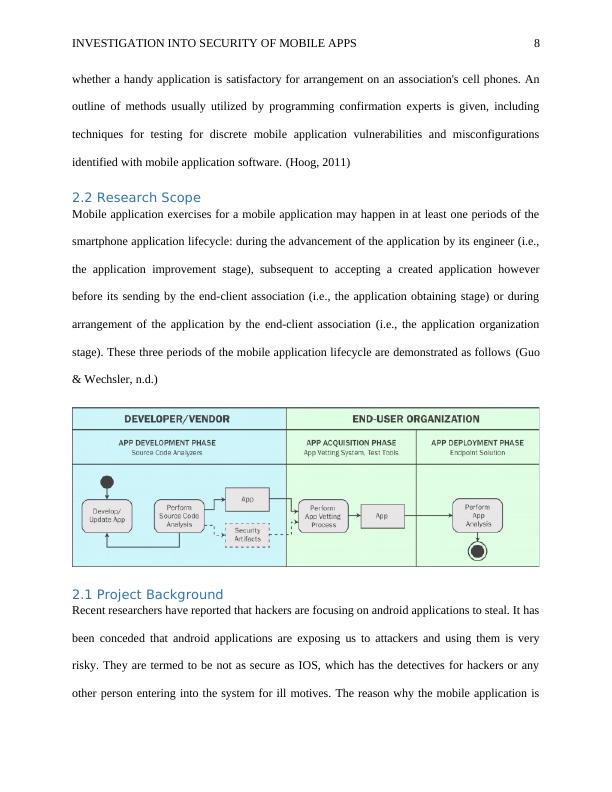
Mobile application exercises for a mobile application may happen in at least one periods of the
smartphone application lifecycle: during the advancement of the application by its engineer (i.e.,
the application improvement stage), subsequent to accepting a created application however
before its sending by the end-client association (i.e., the application obtaining stage) or during
arrangement of the application by the end-client association (i.e., the application organization
stage). These three periods of the mobile application lifecycle are demonstrated as follows (Guo
& Wechsler, n.d.)
2.1 Project Background
Recent researchers have reported that hackers are focusing on android applications to steal. It has
been conceded that android applications are exposing us to attackers and using them is very
risky. They are termed to be not as secure as IOS, which has the detectives for hackers or any
other person entering into the system for ill motives. The reason why the mobile application is
whether a handy application is satisfactory for arrangement on an association's cell phones. An
outline of methods usually utilized by programming confirmation experts is given, including
techniques for testing for discrete mobile application vulnerabilities and misconfigurations
identified with mobile application software. (Hoog, 2011)
2.2 Research Scope
Mobile application exercises for a mobile application may happen in at least one periods of the
smartphone application lifecycle: during the advancement of the application by its engineer (i.e.,
the application improvement stage), subsequent to accepting a created application however
before its sending by the end-client association (i.e., the application obtaining stage) or during
arrangement of the application by the end-client association (i.e., the application organization
stage). These three periods of the mobile application lifecycle are demonstrated as follows (Guo
& Wechsler, n.d.)
2.1 Project Background
Recent researchers have reported that hackers are focusing on android applications to steal. It has
been conceded that android applications are exposing us to attackers and using them is very
risky. They are termed to be not as secure as IOS, which has the detectives for hackers or any
other person entering into the system for ill motives. The reason why the mobile application is
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Internet of Things (IOT) and Home Networklg...
|13
|2239
|301
(PDF) SMART HOME SYSTEM DOCUMENTATIONlg...
|10
|2981
|30
Cloud Based Smart Application Managementlg...
|34
|1529
|47
Mobile Application Security: Malware Threats and Defenseslg...
|7
|6648
|56
Fog and Edge Project Proposal for IoT: Designing a Hybrid Platformlg...
|17
|3487
|307
Internet of Things and Privacylg...
|10
|2731
|193
