Forensic Investigation Report: Melbourne Airport Baggage Devices
VerifiedAdded on 2020/03/16
|17
|2568
|60
Report
AI Summary
This report details a forensic investigation of digital devices (laptop and external HDD) confiscated from Mrs. Waugh at Melbourne International Airport. The investigation involved imaging the devices using ProDiscover and analyzing the data to recover deleted files and hidden information. The analysis revealed potential malicious activities, including email addresses, company names, and credit card numbers. The report outlines the custody of the exhibits, the analysis conducted, and the findings, which suggest evidence that could be used to build a case against Mrs. Waugh and potentially uncover other involved parties. The investigation also involved recovering hidden files within images using S-Tools, revealing further evidence of planned malicious actions. The devices were copied using logical copy mode with bit by bit operation and the images were kept in high security after the imaging process. The recovered data included email addresses, company names, and credit card numbers.

[Document Title]
[Document Subtitle]
ABSTRACT
[Type the abstract of the document here. The abstract is typically a short summary of the
contents of the document.]
[Document Subtitle]
ABSTRACT
[Type the abstract of the document here. The abstract is typically a short summary of the
contents of the document.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The current project is about the investigation of the laptop that was being held at the airport
baggage scanning process at the Melbourne International Airport. The person under investigation
is Mrs. Waugh. The baggage had digital devices of which we would be taking care of the
investigation, the devices that were being confiscated are Laptop and External HDD drive. The
culprit was on the way back from Pakistan hence the suspicion was on higher side.
2
The current project is about the investigation of the laptop that was being held at the airport
baggage scanning process at the Melbourne International Airport. The person under investigation
is Mrs. Waugh. The baggage had digital devices of which we would be taking care of the
investigation, the devices that were being confiscated are Laptop and External HDD drive. The
culprit was on the way back from Pakistan hence the suspicion was on higher side.
2

Table of Contents
Introduction............................................................................................................................4
CUSTODY OF EXHIBIT.......................................................................................................................4
Analysis Conducted..........................................................................................................................4
Findings.........................................................................................................................................16
Conclusion.....................................................................................................................................16
Summary of the report and results obtained.........................................................................16
References.............................................................................................................................17
3
Introduction............................................................................................................................4
CUSTODY OF EXHIBIT.......................................................................................................................4
Analysis Conducted..........................................................................................................................4
Findings.........................................................................................................................................16
Conclusion.....................................................................................................................................16
Summary of the report and results obtained.........................................................................16
References.............................................................................................................................17
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The devices under the investigation are Laptop and External HDD which were confiscated from
the Mrs. Waugh at the Airport baggage scanner. The Malicious looking Mrs. Waugh looked
tensed at the airport reporting stations, the baggage under the scanner looked suspicious and was
immediately taken into investigation by the authorities. The Laptop and the External HDD being
the digital devices then were confiscated and were handed over to the investigation team and rest
of the baggage was left to the crime police for further investigations.
CUSTODY OF EXHIBIT
On 26th September 2017 at 1:15 am the flight from Pakistan landed Adelaide International airport
having the number TR354, the during the routine baggage scan the baggage had some malicious
packets along with the digital devices. The digital evidences include a Laptop of Model No.:
YT98987 and Serial No.: YT786393650300752 and External HDD with the serial No.
GHDD7868667 were found and confiscated. Officer Maxwell confiscated and sealed the devices
into the baggage number ID4533 for the case and were handed over to the Digital Investigator
Officer Mr. Zampa. The initial investigation revealed that the External HDD size was 500 GB.
Analysis Conducted
The digital evidences include a Laptop of Model No.: YT98987 and Serial No.:
YT786393650300752 and External HDD with the serial No. GHDD7868667. The devices were
given to the investigation team in the sealed envelope No. ID34244. The office of digital devices
is situated at the Adelaide. The devices were being digitally copied and all the digital evidences
then being secured, the copy mode used is logical copy with bit by bit operation so as to make
the exact copy using special software like ProDiscover. The extra hardware protects the any
write operation on the devices. (Zhicong, Delin & Shunxiang, 2008)
The images being created are kept and their backup as well being created and stored on other
external devices as well as on cloud so that in case of any haphazard the evidences are secured.
The Laptop that was being confiscated had the following configuration:
Intel Core2Duo dual core
500 GB HDD with different size partition
4
The devices under the investigation are Laptop and External HDD which were confiscated from
the Mrs. Waugh at the Airport baggage scanner. The Malicious looking Mrs. Waugh looked
tensed at the airport reporting stations, the baggage under the scanner looked suspicious and was
immediately taken into investigation by the authorities. The Laptop and the External HDD being
the digital devices then were confiscated and were handed over to the investigation team and rest
of the baggage was left to the crime police for further investigations.
CUSTODY OF EXHIBIT
On 26th September 2017 at 1:15 am the flight from Pakistan landed Adelaide International airport
having the number TR354, the during the routine baggage scan the baggage had some malicious
packets along with the digital devices. The digital evidences include a Laptop of Model No.:
YT98987 and Serial No.: YT786393650300752 and External HDD with the serial No.
GHDD7868667 were found and confiscated. Officer Maxwell confiscated and sealed the devices
into the baggage number ID4533 for the case and were handed over to the Digital Investigator
Officer Mr. Zampa. The initial investigation revealed that the External HDD size was 500 GB.
Analysis Conducted
The digital evidences include a Laptop of Model No.: YT98987 and Serial No.:
YT786393650300752 and External HDD with the serial No. GHDD7868667. The devices were
given to the investigation team in the sealed envelope No. ID34244. The office of digital devices
is situated at the Adelaide. The devices were being digitally copied and all the digital evidences
then being secured, the copy mode used is logical copy with bit by bit operation so as to make
the exact copy using special software like ProDiscover. The extra hardware protects the any
write operation on the devices. (Zhicong, Delin & Shunxiang, 2008)
The images being created are kept and their backup as well being created and stored on other
external devices as well as on cloud so that in case of any haphazard the evidences are secured.
The Laptop that was being confiscated had the following configuration:
Intel Core2Duo dual core
500 GB HDD with different size partition
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
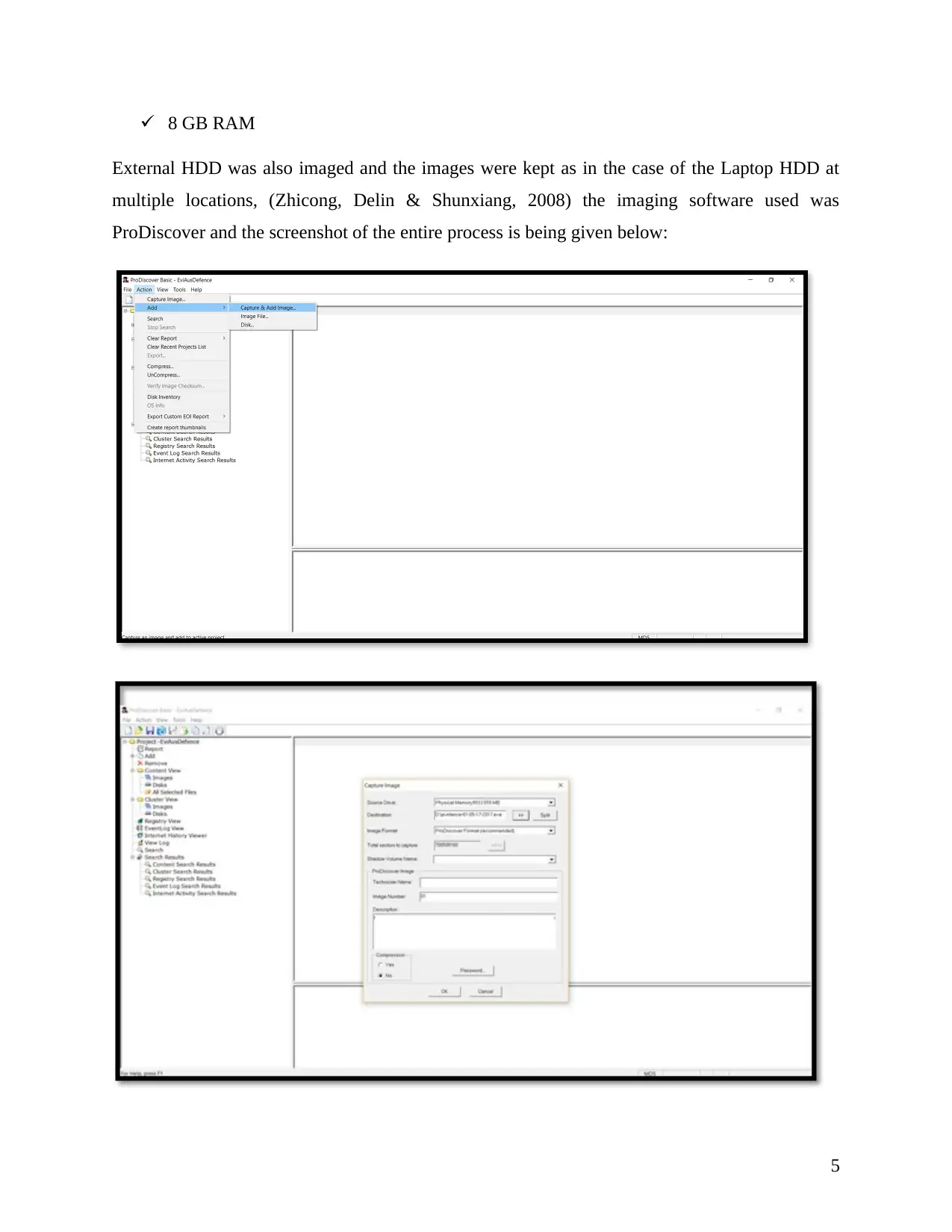
8 GB RAM
External HDD was also imaged and the images were kept as in the case of the Laptop HDD at
multiple locations, (Zhicong, Delin & Shunxiang, 2008) the imaging software used was
ProDiscover and the screenshot of the entire process is being given below:
5
External HDD was also imaged and the images were kept as in the case of the Laptop HDD at
multiple locations, (Zhicong, Delin & Shunxiang, 2008) the imaging software used was
ProDiscover and the screenshot of the entire process is being given below:
5
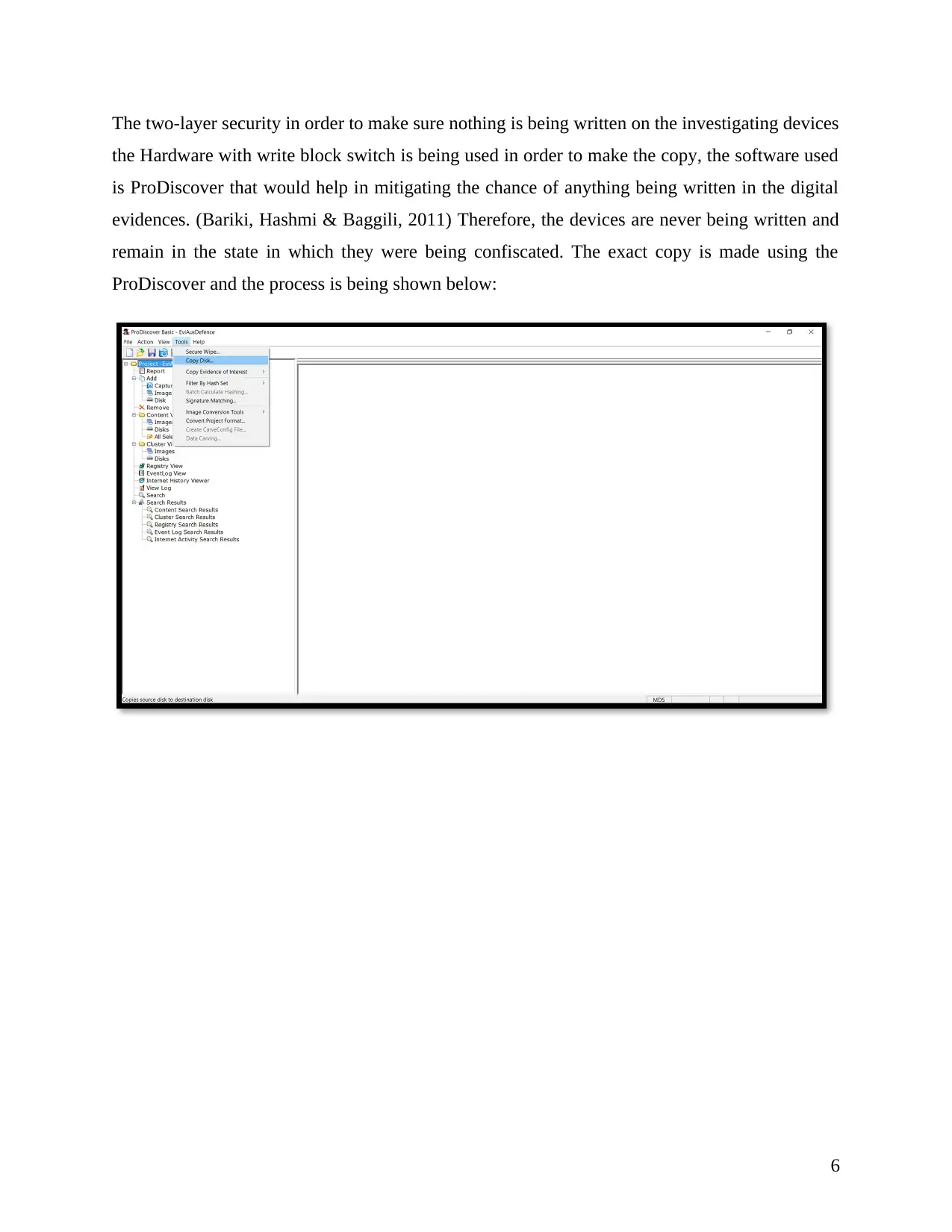
The two-layer security in order to make sure nothing is being written on the investigating devices
the Hardware with write block switch is being used in order to make the copy, the software used
is ProDiscover that would help in mitigating the chance of anything being written in the digital
evidences. (Bariki, Hashmi & Baggili, 2011) Therefore, the devices are never being written and
remain in the state in which they were being confiscated. The exact copy is made using the
ProDiscover and the process is being shown below:
6
the Hardware with write block switch is being used in order to make the copy, the software used
is ProDiscover that would help in mitigating the chance of anything being written in the digital
evidences. (Bariki, Hashmi & Baggili, 2011) Therefore, the devices are never being written and
remain in the state in which they were being confiscated. The exact copy is made using the
ProDiscover and the process is being shown below:
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
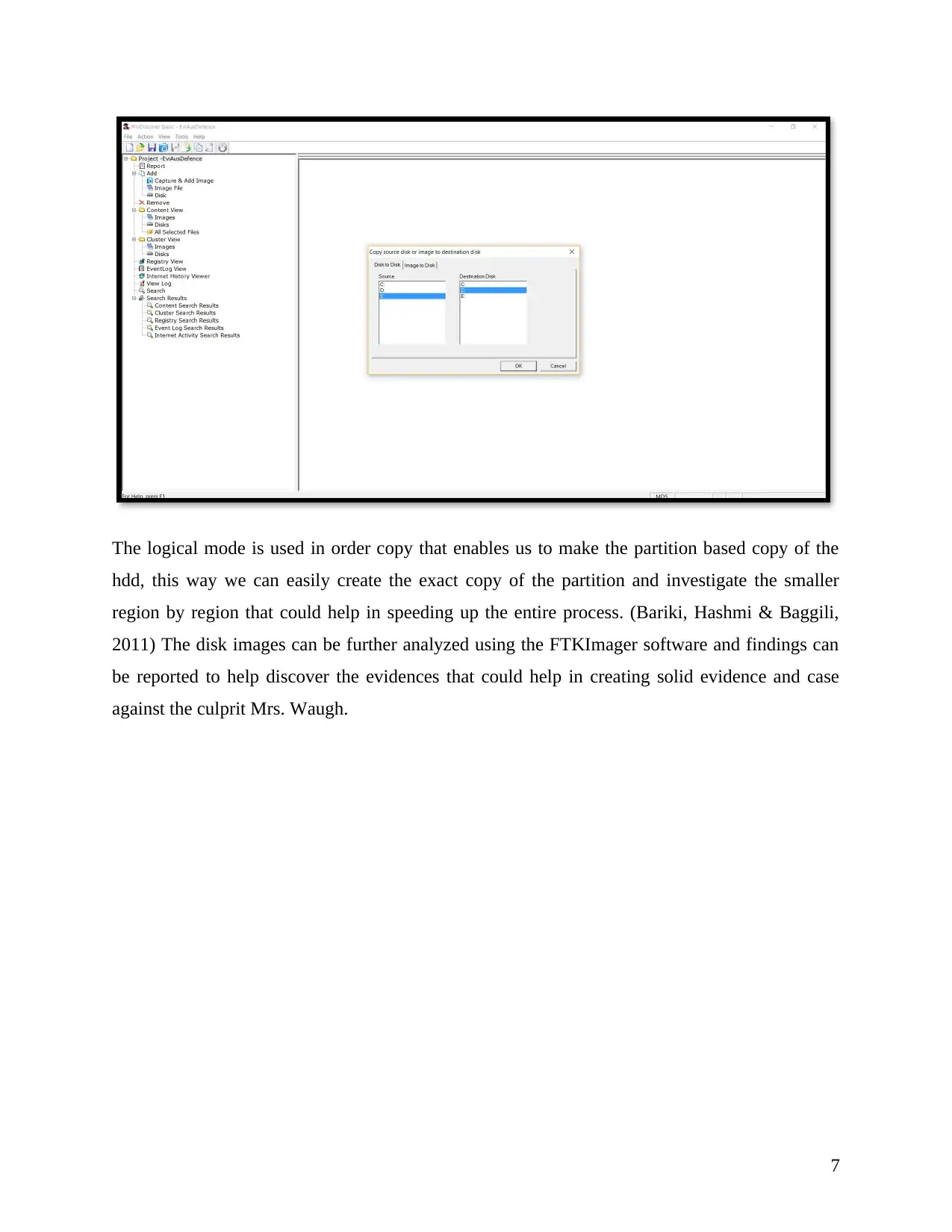
The logical mode is used in order copy that enables us to make the partition based copy of the
hdd, this way we can easily create the exact copy of the partition and investigate the smaller
region by region that could help in speeding up the entire process. (Bariki, Hashmi & Baggili,
2011) The disk images can be further analyzed using the FTKImager software and findings can
be reported to help discover the evidences that could help in creating solid evidence and case
against the culprit Mrs. Waugh.
7
hdd, this way we can easily create the exact copy of the partition and investigate the smaller
region by region that could help in speeding up the entire process. (Bariki, Hashmi & Baggili,
2011) The disk images can be further analyzed using the FTKImager software and findings can
be reported to help discover the evidences that could help in creating solid evidence and case
against the culprit Mrs. Waugh.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
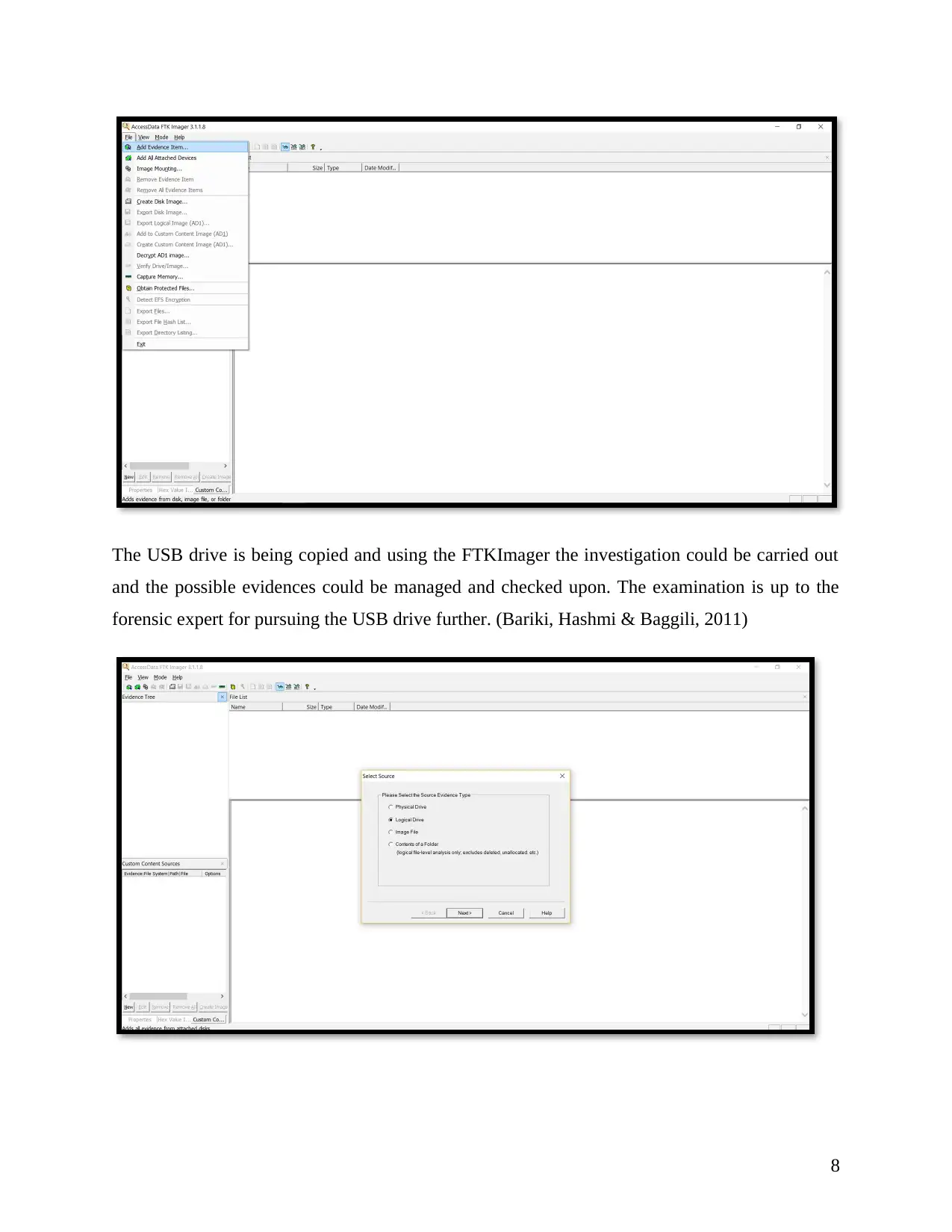
The USB drive is being copied and using the FTKImager the investigation could be carried out
and the possible evidences could be managed and checked upon. The examination is up to the
forensic expert for pursuing the USB drive further. (Bariki, Hashmi & Baggili, 2011)
8
and the possible evidences could be managed and checked upon. The examination is up to the
forensic expert for pursuing the USB drive further. (Bariki, Hashmi & Baggili, 2011)
8
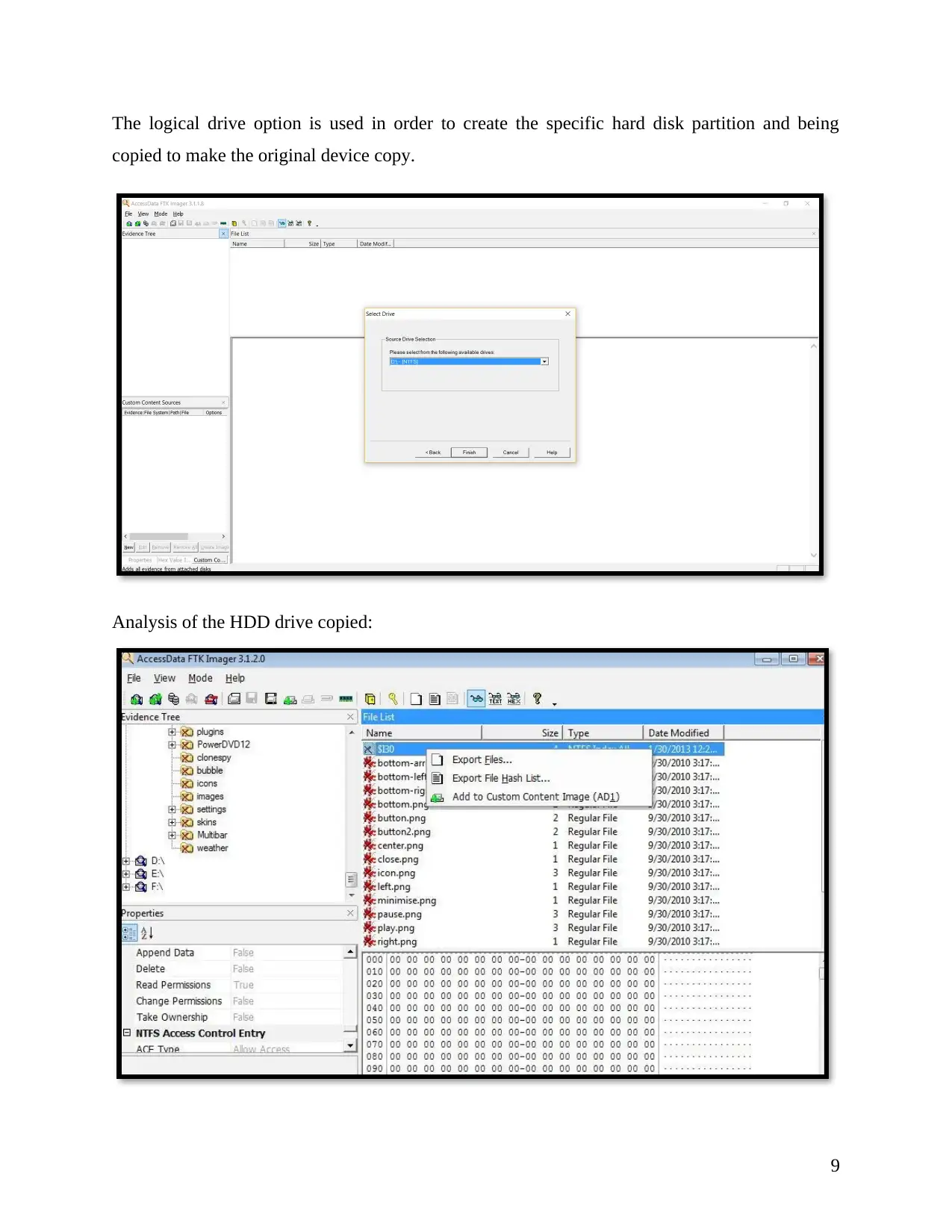
The logical drive option is used in order to create the specific hard disk partition and being
copied to make the original device copy.
Analysis of the HDD drive copied:
9
copied to make the original device copy.
Analysis of the HDD drive copied:
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

There have been many files and folders that have been deleted from the disk, the software that
have been used is the FTKImager in order to analyze the HDD images for the purpose of
recovering and reading the files that have been deleted. The recovered files then would help in
creating the strong evidences against the culprit so that we can frame the culprit. (Garfinkel,
Malan, Dubec, Stevens & Pham, 2006)
Several files were being found in the image that were deleted and using the FTKImager we were
easily able to the recover them, the many files recovered had nothing much as solid evidence but
there were some files that could have been easily being taken into consideration. (Garfinkel,
Malan, Dubec, Stevens & Pham, 2006)
The following investigation was done and the data found have been given below (small snippet
for the report analysis)
aliquet.nec.imperdiet@loremegetmollis.co.uk,Facilisis Industries,365155-
4986,670670990080386619
pede@odioPhasellusat.ca,Etiam Ligula Incorporated,358700-4601,4911672572360606
euismod.est.arcu@Cras.org,Blandit Mattis PC,346040-0736,30312444432861
sed@quamPellentesquehabitant.net,Sed Hendrerit PC,188798-4860,30340871470658
at.velit@estNunc.edu,Mauris Blandit Consulting,468395-8070,2014 -713763 -89029
nec@augueac.ca,Auctor Associates,619882-9621,670917494635654335
elit.Nulla.facilisi@eusemPellentesque.net,Lobortis Nisi Nibh LLC,347631-7155,3444 -872665 -
73389
malesuada.vel.venenatis@idmagnaet.com,Rutrum Eu Associates,183000-
4055,5401213060534420
ante.ipsum.primis@eleifendCrassed.org,Lobortis Foundation,714092-4338,30200779787985
pharetra.ut@sitametnulla.com,Etiam Vestibulum Massa Industries,673946-
8152,309096838733844
facilisis@est.ca,Aliquam Erat Volutpat Incorporated,594049-4783,213163 -8954912239
bibendum.sed.est@miDuis.com,Eget Odio Aliquam Corp.,729184-4061,658 -94472 -73067 -412
imperdiet.dictum@parturient.org,Duis A Mi LLP,187115-8224,491750 -6860709583
tincidunt.orci.quis@necmalesuada.net,Aliquam Erat Volutpat Inc.,723291-5434,309292 -
2814616551
Praesent.eu.dui@semsempererat.edu,Ac Corporation,186971-0929,375113917802744
ac.tellus@Proinsed.edu,Neque Associates,509657-4404,670646 -9512923336
Vestibulum.accumsan@ornareegestasligula.edu,Diam Luctus Lobortis LLC,779983-
1164,180018084163256
nunc.sit@aliquetPhasellus.net,Aliquam Iaculis Lacus Incorporated,529351-1472,647506 -
5335754210
per.inceptos.hymenaeos@tempusmauris.net,Nibh Enim Inc.,173394-4233,4532827006844893
a@Vestibulumaccumsanneque.net,Vehicula Risus Nulla Company,516522-
8544,67718882521512379
lorem.lorem@magnisdis.net,Ante Iaculis PC,496518-3611,63043300785583106
10
have been used is the FTKImager in order to analyze the HDD images for the purpose of
recovering and reading the files that have been deleted. The recovered files then would help in
creating the strong evidences against the culprit so that we can frame the culprit. (Garfinkel,
Malan, Dubec, Stevens & Pham, 2006)
Several files were being found in the image that were deleted and using the FTKImager we were
easily able to the recover them, the many files recovered had nothing much as solid evidence but
there were some files that could have been easily being taken into consideration. (Garfinkel,
Malan, Dubec, Stevens & Pham, 2006)
The following investigation was done and the data found have been given below (small snippet
for the report analysis)
aliquet.nec.imperdiet@loremegetmollis.co.uk,Facilisis Industries,365155-
4986,670670990080386619
pede@odioPhasellusat.ca,Etiam Ligula Incorporated,358700-4601,4911672572360606
euismod.est.arcu@Cras.org,Blandit Mattis PC,346040-0736,30312444432861
sed@quamPellentesquehabitant.net,Sed Hendrerit PC,188798-4860,30340871470658
at.velit@estNunc.edu,Mauris Blandit Consulting,468395-8070,2014 -713763 -89029
nec@augueac.ca,Auctor Associates,619882-9621,670917494635654335
elit.Nulla.facilisi@eusemPellentesque.net,Lobortis Nisi Nibh LLC,347631-7155,3444 -872665 -
73389
malesuada.vel.venenatis@idmagnaet.com,Rutrum Eu Associates,183000-
4055,5401213060534420
ante.ipsum.primis@eleifendCrassed.org,Lobortis Foundation,714092-4338,30200779787985
pharetra.ut@sitametnulla.com,Etiam Vestibulum Massa Industries,673946-
8152,309096838733844
facilisis@est.ca,Aliquam Erat Volutpat Incorporated,594049-4783,213163 -8954912239
bibendum.sed.est@miDuis.com,Eget Odio Aliquam Corp.,729184-4061,658 -94472 -73067 -412
imperdiet.dictum@parturient.org,Duis A Mi LLP,187115-8224,491750 -6860709583
tincidunt.orci.quis@necmalesuada.net,Aliquam Erat Volutpat Inc.,723291-5434,309292 -
2814616551
Praesent.eu.dui@semsempererat.edu,Ac Corporation,186971-0929,375113917802744
ac.tellus@Proinsed.edu,Neque Associates,509657-4404,670646 -9512923336
Vestibulum.accumsan@ornareegestasligula.edu,Diam Luctus Lobortis LLC,779983-
1164,180018084163256
nunc.sit@aliquetPhasellus.net,Aliquam Iaculis Lacus Incorporated,529351-1472,647506 -
5335754210
per.inceptos.hymenaeos@tempusmauris.net,Nibh Enim Inc.,173394-4233,4532827006844893
a@Vestibulumaccumsanneque.net,Vehicula Risus Nulla Company,516522-
8544,67718882521512379
lorem.lorem@magnisdis.net,Ante Iaculis PC,496518-3611,63043300785583106
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ante@hendrerita.com,Metus Vivamus Euismod Ltd,399458-8725,516461 -154529 -5573
Sed.nulla.ante@gravida.net,Vel Sapien Incorporated,033072-1069,677121121846811670
lobortis@lacus.org,Laoreet Lectus LLC,702356-7105,647096 -648107 -5190
gravida@duiCumsociis.co.uk,Porttitor Scelerisque Neque Corporation,726688-4647,4913 -2452
-3400 -8968
quis.accumsan.convallis@dolorvitaedolor.org,Rutrum Institute,657909-4472,36736134409207
feugiat.nec@posuere.edu,Nunc Sed Libero LLP,242893-7631,4905572567583608825
Phasellus.in@non.ca,A Incorporated,103137-8548,4556279512054
augue.malesuada.malesuada@magnaLorem.ca,Enim Industries,693609-
8695,3098940229638022
aliquet@elit.net,Quis Arcu Vel Consulting,356051-6563,2149 -374019 -97569
Proin.nisl@ornarelectusante.ca,Duis Volutpat Nunc LLC,324682-1007,544455 -581328 -4995
Ut.nec.urna@arcuVivamus.net,Magna Consulting,273685-1805,491791 -816515 -4409
lobortis.mauris.Suspendisse@Sedeu.edu,Lorem PC,176748-4064,4911008051763118303
tincidunt.adipiscing@dolorsitamet.net,Ultricies Ornare Elit Ltd,105023-6346,3736 -791350 -
41556
natoque.penatibus.et@neque.co.uk,Donec Felis Orci Company,994716-3698,6304 -0599 -0183 -
3141
fermentum.metus.Aenean@Sednec.edu,Massa Integer Inc.,837574-9531,649 -03512 -83406 -
743
lacinia.at.iaculis@nectempusmauris.co.uk,Sed Est Ltd,405009-2016,525905 -261826 -3972
molestie@etarcuimperdiet.co.uk,Ante Associates,066614-0058,36601952955212
tempus.eu.ligula@Pellentesqueutipsum.co.uk,Maecenas Malesuada Incorporated,696665-
8707,538867 -3694595138
neque.Nullam@mi.com,Lacus Quisque Imperdiet LLP,205424-6448,30012816650161
Cras.eu@velitegetlaoreet.co.uk,Arcu Aliquam Limited,193243-1891,6304078400147811
Class.aptent@dolor.edu,Sed Consulting,034274-2954,376557577628360
Maecenas.ornare.egestas@vestibulummassa.ca,Ipsum Curabitur Company,674834-0145,1800 -
9118 -2020 -5571
arcu@egestashendrerit.ca,Nisl Inc.,822464-3521,6481 -2028 -7301 -0240
Integer@sagittis.co.uk,Aliquet Limited,804779-8890,455 -68925 -25533 -048
odio.a.purus@lorem.com,Tincidunt Donec Vitae Consulting,314342-
1604,675963856627995334
Proin.dolor.Nulla@laoreetipsum.com,A Arcu Limited,937915-5253,180004950096010
pede@Vivamus.co.uk,Lacus Cras Interdum Corporation,865757-5877,6706759281341384258
at.pede.Cras@imperdiet.net,Scelerisque Sed Sapien LLC,878595-1230,2131324924684493
sed@ac.org,Mauris A Corp.,257350-3618,180054937836889
tincidunt.neque@maurisutmi.co.uk,Dis Parturient Montes Institute,768236-
1170,6706059641623889
malesuada.fringilla.est@nisidictum.ca,Sodales At Velit LLC,655544-3099,4532533635213
tortor.at.risus@Suspendissetristique.com,Nunc In At Corporation,419622-
1412,5528972992083230
eu.ligula@euturpis.net,Diam Vel Corp.,723796-9907,30371330585885
Fusce@etarcuimperdiet.co.uk,Commodo Auctor Velit Ltd,132330-1190,538983 -2513374633
11
Sed.nulla.ante@gravida.net,Vel Sapien Incorporated,033072-1069,677121121846811670
lobortis@lacus.org,Laoreet Lectus LLC,702356-7105,647096 -648107 -5190
gravida@duiCumsociis.co.uk,Porttitor Scelerisque Neque Corporation,726688-4647,4913 -2452
-3400 -8968
quis.accumsan.convallis@dolorvitaedolor.org,Rutrum Institute,657909-4472,36736134409207
feugiat.nec@posuere.edu,Nunc Sed Libero LLP,242893-7631,4905572567583608825
Phasellus.in@non.ca,A Incorporated,103137-8548,4556279512054
augue.malesuada.malesuada@magnaLorem.ca,Enim Industries,693609-
8695,3098940229638022
aliquet@elit.net,Quis Arcu Vel Consulting,356051-6563,2149 -374019 -97569
Proin.nisl@ornarelectusante.ca,Duis Volutpat Nunc LLC,324682-1007,544455 -581328 -4995
Ut.nec.urna@arcuVivamus.net,Magna Consulting,273685-1805,491791 -816515 -4409
lobortis.mauris.Suspendisse@Sedeu.edu,Lorem PC,176748-4064,4911008051763118303
tincidunt.adipiscing@dolorsitamet.net,Ultricies Ornare Elit Ltd,105023-6346,3736 -791350 -
41556
natoque.penatibus.et@neque.co.uk,Donec Felis Orci Company,994716-3698,6304 -0599 -0183 -
3141
fermentum.metus.Aenean@Sednec.edu,Massa Integer Inc.,837574-9531,649 -03512 -83406 -
743
lacinia.at.iaculis@nectempusmauris.co.uk,Sed Est Ltd,405009-2016,525905 -261826 -3972
molestie@etarcuimperdiet.co.uk,Ante Associates,066614-0058,36601952955212
tempus.eu.ligula@Pellentesqueutipsum.co.uk,Maecenas Malesuada Incorporated,696665-
8707,538867 -3694595138
neque.Nullam@mi.com,Lacus Quisque Imperdiet LLP,205424-6448,30012816650161
Cras.eu@velitegetlaoreet.co.uk,Arcu Aliquam Limited,193243-1891,6304078400147811
Class.aptent@dolor.edu,Sed Consulting,034274-2954,376557577628360
Maecenas.ornare.egestas@vestibulummassa.ca,Ipsum Curabitur Company,674834-0145,1800 -
9118 -2020 -5571
arcu@egestashendrerit.ca,Nisl Inc.,822464-3521,6481 -2028 -7301 -0240
Integer@sagittis.co.uk,Aliquet Limited,804779-8890,455 -68925 -25533 -048
odio.a.purus@lorem.com,Tincidunt Donec Vitae Consulting,314342-
1604,675963856627995334
Proin.dolor.Nulla@laoreetipsum.com,A Arcu Limited,937915-5253,180004950096010
pede@Vivamus.co.uk,Lacus Cras Interdum Corporation,865757-5877,6706759281341384258
at.pede.Cras@imperdiet.net,Scelerisque Sed Sapien LLC,878595-1230,2131324924684493
sed@ac.org,Mauris A Corp.,257350-3618,180054937836889
tincidunt.neque@maurisutmi.co.uk,Dis Parturient Montes Institute,768236-
1170,6706059641623889
malesuada.fringilla.est@nisidictum.ca,Sodales At Velit LLC,655544-3099,4532533635213
tortor.at.risus@Suspendissetristique.com,Nunc In At Corporation,419622-
1412,5528972992083230
eu.ligula@euturpis.net,Diam Vel Corp.,723796-9907,30371330585885
Fusce@etarcuimperdiet.co.uk,Commodo Auctor Velit Ltd,132330-1190,538983 -2513374633
11

The data was being recovered was easy to guess as the first being the email address, second
being the name of the company or organization and then being the credit card numbers. The
further investigation on the data can be done by the police as this would come under the crime
investigation. (Bariki, Hashmi & Baggili, 2011)
The next step is to recover the image files so as to find out the bmp and gif based images, the
tool used to investigate the images is the S-Tool in order to recover the secret files from the
images hidden under them. The files whose resolution is small and size being on the higher side
are being specially investigated. The passphrases for the purpose being selected randomly and S-
Tools are being recovered by the files. To recover the secret text the secret passphrase and
encryption combination are being tried and the data file is being revealed. (Bariki, Hashmi &
Baggili, 2011)
The data revealed from the file and being investigated the following information was being
revealed by the software. The hidden file in the images shows the malicious activities being
planned by Mrs. Waugh. (Bariki, Hashmi & Baggili, 2011)
Purus In LLP,283887 9464,0.4310578482,16421011-2704
Magnis Dis Corp.,132821 8811,-0.1999274303,16300625-4506
12
being the name of the company or organization and then being the credit card numbers. The
further investigation on the data can be done by the police as this would come under the crime
investigation. (Bariki, Hashmi & Baggili, 2011)
The next step is to recover the image files so as to find out the bmp and gif based images, the
tool used to investigate the images is the S-Tool in order to recover the secret files from the
images hidden under them. The files whose resolution is small and size being on the higher side
are being specially investigated. The passphrases for the purpose being selected randomly and S-
Tools are being recovered by the files. To recover the secret text the secret passphrase and
encryption combination are being tried and the data file is being revealed. (Bariki, Hashmi &
Baggili, 2011)
The data revealed from the file and being investigated the following information was being
revealed by the software. The hidden file in the images shows the malicious activities being
planned by Mrs. Waugh. (Bariki, Hashmi & Baggili, 2011)
Purus In LLP,283887 9464,0.4310578482,16421011-2704
Magnis Dis Corp.,132821 8811,-0.1999274303,16300625-4506
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

