IoT Cloud-based Security Issues: Blockchain Technology as a Solution
VerifiedAdded on 2024/05/10
|27
|5671
|406
AI Summary
This report explores the challenges of cloud-based IoT security and how blockchain technology can provide solutions. It covers IoT basics, applications, major components, architecture, and security issues.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
WEEKLY REPORT
Week – 5
IoT Cloud-based security issues: Blockchain technology as a
solution
Name : Kanakadurga Sridevi Maddipati
Student ID : 11606404
Subject : Emerging Technologies and
Innovations
Subject Code : ITC571
Staff : Dr Chandana Withana
Week – 5
IoT Cloud-based security issues: Blockchain technology as a
solution
Name : Kanakadurga Sridevi Maddipati
Student ID : 11606404
Subject : Emerging Technologies and
Innovations
Subject Code : ITC571
Staff : Dr Chandana Withana
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
What is IoT and definition of IoT
Definition of IoT basic terms
IoT device
IoT ecosystem
Entity
Physical layer
Network layer
Application layer
Data storage
Applications of IoT
Health Care
Wearables
Connect Vehicles
Home Automation
Location-based services
Smart Meters
Major components or functional blocks of IoT
Device and sensor
Gateway
Cloud
Analytics
Application/User interface
IoT Architecture layers and its relationship with the components
Challenges associated with cloud-based IoT
Identity Privacy
Location Privacy
Node Compromise Attack
Target-oriented compromise attack
Layer Removing/Adding Attack
Forward and Backward Security
Semi-Trusted or Malicious Cloud Security
Data Breach
What is IoT and definition of IoT
Definition of IoT basic terms
IoT device
IoT ecosystem
Entity
Physical layer
Network layer
Application layer
Data storage
Applications of IoT
Health Care
Wearables
Connect Vehicles
Home Automation
Location-based services
Smart Meters
Major components or functional blocks of IoT
Device and sensor
Gateway
Cloud
Analytics
Application/User interface
IoT Architecture layers and its relationship with the components
Challenges associated with cloud-based IoT
Identity Privacy
Location Privacy
Node Compromise Attack
Target-oriented compromise attack
Layer Removing/Adding Attack
Forward and Backward Security
Semi-Trusted or Malicious Cloud Security
Data Breach

Shared technologies vulnerabilities
Account or service traffic hijacking
Denial of service (DoS) attacks
Malicious insiders
Cloud and what are the different types of clouds
Structure of Cloud
Features of Cloud
Centralized cloud storage and what are its security issues
What is blockchain technology and explain its architecture
Explain the working of blockchain technology and its applications
Compare cloud storage and block storage
Benefits of moving from cloud storage to blockchain
Account or service traffic hijacking
Denial of service (DoS) attacks
Malicious insiders
Cloud and what are the different types of clouds
Structure of Cloud
Features of Cloud
Centralized cloud storage and what are its security issues
What is blockchain technology and explain its architecture
Explain the working of blockchain technology and its applications
Compare cloud storage and block storage
Benefits of moving from cloud storage to blockchain

Everything in its way to be computerized and most of the objects are coming to be
smart in present days. Modern Internet of Thing (IoT) allows these objects to be on
the network by using IoT platforms. The internet of things (IoT) information can
be shared among certain devices through the internet. Such devices are smart-
devices include smartphones, tablets, PCs, wearables, sensors and so on. Many
other smart devices have been introduced recently which can communicate with
each other using the internet and other communication techniques. These
techniques include RFID, near-field communications, various types of barcodes,
and so on. The capabilities of communications in IoT are built-in and allow new
services. The frequent increase in the smart devices connected to the internet lead
to the increase in several issues related to flexibility, security, efficiency and
scalability. According to Sharma, et al. (2017), the blockchain technology is the
solution utilized for resolving the issues as it supports in developing effective
architecture for IoT that help in advancing the security aspects.
Definition of IoT and its basic terms:
There is no universal definition for the term IoT; different definitions are used by
different parties, foundations, and groups to describe a specific view of what IoT
means. The goal that needs to be accomplished for the IoT is integrity,
confidentiality and authentication (Cheng, et al. 2017).
IoT or Internet of Things is defined as a system that permits the devices for
communicating with each other directly without human intervention. IEEE, in its
special report on Internet of things described IoT as "A network of items-each
embedded with sensors which are connected to the Internet" (Special Report: The
Internet of Things). In 2016, The International Telecommunication Union (ITU)
published a requirement of the network for the Internet of things and IoT is defined
smart in present days. Modern Internet of Thing (IoT) allows these objects to be on
the network by using IoT platforms. The internet of things (IoT) information can
be shared among certain devices through the internet. Such devices are smart-
devices include smartphones, tablets, PCs, wearables, sensors and so on. Many
other smart devices have been introduced recently which can communicate with
each other using the internet and other communication techniques. These
techniques include RFID, near-field communications, various types of barcodes,
and so on. The capabilities of communications in IoT are built-in and allow new
services. The frequent increase in the smart devices connected to the internet lead
to the increase in several issues related to flexibility, security, efficiency and
scalability. According to Sharma, et al. (2017), the blockchain technology is the
solution utilized for resolving the issues as it supports in developing effective
architecture for IoT that help in advancing the security aspects.
Definition of IoT and its basic terms:
There is no universal definition for the term IoT; different definitions are used by
different parties, foundations, and groups to describe a specific view of what IoT
means. The goal that needs to be accomplished for the IoT is integrity,
confidentiality and authentication (Cheng, et al. 2017).
IoT or Internet of Things is defined as a system that permits the devices for
communicating with each other directly without human intervention. IEEE, in its
special report on Internet of things described IoT as "A network of items-each
embedded with sensors which are connected to the Internet" (Special Report: The
Internet of Things). In 2016, The International Telecommunication Union (ITU)
published a requirement of the network for the Internet of things and IoT is defined
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

as a global infrastructure for society of information that enables interconnected
things to communicate with each other and performs advance services-based on
existing and evolving interoperable information and communication technologies
(Requirements of the network for the Internet of things, 2016).
According to Cheng, et al. (2017), there is the requirement of cryptographic
primitives and advanced algorithms like advanced encryption standard (AES) with
intention to amplify the confidentiality and security aspects for IoT. The
communication in the IoT needs to be secured with intention to enhance
confidentiality and maintain trustworthiness.
In The Internet of Things: An Overview (2015), IoTis defined as a framework
wherein all things have a representation and existence in the internet. IoT goals for
offering new applications and services bridge both physical and virtual
worlds.Also, IoT is defined as internet of three things: People to people, People to
machine, machine to machine, Interacting through internet.
According to Gil, Ferrández, Mora-Mora, & Peral (2016), there are numerous
visions about IoT starting with various perspectives. As of the viewpoint from
services, IoT implies our current reality, the place where things could naturally
correspond with one another giving the profit to the mankind. From the viewpoint
of connectivity, IoT intends anytime, anywhere connectivity for anyone and
anything. From that viewpoint about communication, IoT alludes a world-wide
system of interconnected things or devices that are particularly addressable
considering standard conventions. Lastly, starting with the viewpoint from
networking, IoT may be the web developed from a system of interconnected
machines with a system of interconnectedness devices.
(Meddeb, 2016) describes the terms as follows:
things to communicate with each other and performs advance services-based on
existing and evolving interoperable information and communication technologies
(Requirements of the network for the Internet of things, 2016).
According to Cheng, et al. (2017), there is the requirement of cryptographic
primitives and advanced algorithms like advanced encryption standard (AES) with
intention to amplify the confidentiality and security aspects for IoT. The
communication in the IoT needs to be secured with intention to enhance
confidentiality and maintain trustworthiness.
In The Internet of Things: An Overview (2015), IoTis defined as a framework
wherein all things have a representation and existence in the internet. IoT goals for
offering new applications and services bridge both physical and virtual
worlds.Also, IoT is defined as internet of three things: People to people, People to
machine, machine to machine, Interacting through internet.
According to Gil, Ferrández, Mora-Mora, & Peral (2016), there are numerous
visions about IoT starting with various perspectives. As of the viewpoint from
services, IoT implies our current reality, the place where things could naturally
correspond with one another giving the profit to the mankind. From the viewpoint
of connectivity, IoT intends anytime, anywhere connectivity for anyone and
anything. From that viewpoint about communication, IoT alludes a world-wide
system of interconnected things or devices that are particularly addressable
considering standard conventions. Lastly, starting with the viewpoint from
networking, IoT may be the web developed from a system of interconnected
machines with a system of interconnectedness devices.
(Meddeb, 2016) describes the terms as follows:

Internet of Things: Network of internet connected devices that gather
information and return information using sensors.
IoT device: Any internet-connected device that could be monitored or
controlled within a remote area.
IoT ecosystem: Components that allow businesses, governments, customers
to connect with IoT devices like remotes, dashboards, networks, gateways,
analytics, information storage, security.
Entity: Businesses, governments, and customers are the entities.
Physical layer: Hardware of an IoT devices.
Network layer: Liable for transmitting the information gathered by the
physical layer.
Application layer: Protocols for devices to communicate with one another.
Data storage: Place where information from IoT devices will be kept.
information and return information using sensors.
IoT device: Any internet-connected device that could be monitored or
controlled within a remote area.
IoT ecosystem: Components that allow businesses, governments, customers
to connect with IoT devices like remotes, dashboards, networks, gateways,
analytics, information storage, security.
Entity: Businesses, governments, and customers are the entities.
Physical layer: Hardware of an IoT devices.
Network layer: Liable for transmitting the information gathered by the
physical layer.
Application layer: Protocols for devices to communicate with one another.
Data storage: Place where information from IoT devices will be kept.

Applications of IoT:
With the fast improvement of IoT, there are various IoT applications, which help in
our ordinary existence. Starting with accepted supplies or equipment’s to
household appliances these devices assist the mankind (Wang, Hu, Hu, Zhou, &
Zhao, 2016). IoT is applied broadly over different areas such as environment
monitoring, energy management, medical healthcare systems (Deng, Chen, Tsaur,
Tang, & Chen, 2017), wearables, building automation, transportation, vehicles,
industries, schools (Gromovs & Lammi, 2017), smart home and agriculture. Gil,
Ferrández, Mora-Mora, & Peral (2016) says that, these are various potential
applications of IoT which is further derived from health domain, industrial domain,
smart city domain.
The following applications and examples are popular IoT products. Figure 1
illustrates IoT applications:
Health Care: IoT Healthcare applications are built to serve the people,
which innately raise the necessities of reliability, security and safety.
Moreover, the applications must provide notifications and responses with
respect to the status of patients. A healthcare management system must
ascertain the safety of patients by observing patients' activities and key
signs. A healthcare management system should offer precise results in a
timely fashion and should provide secure and reliable services for
caregivers, physicians and patients (Miranda, et al., 2016).
Wearables: These are device-to-device developments that are part of health
domain. Many wearable products have been implemented. For example:
wearable healthcare devices. One of the newest wearable items is Google
With the fast improvement of IoT, there are various IoT applications, which help in
our ordinary existence. Starting with accepted supplies or equipment’s to
household appliances these devices assist the mankind (Wang, Hu, Hu, Zhou, &
Zhao, 2016). IoT is applied broadly over different areas such as environment
monitoring, energy management, medical healthcare systems (Deng, Chen, Tsaur,
Tang, & Chen, 2017), wearables, building automation, transportation, vehicles,
industries, schools (Gromovs & Lammi, 2017), smart home and agriculture. Gil,
Ferrández, Mora-Mora, & Peral (2016) says that, these are various potential
applications of IoT which is further derived from health domain, industrial domain,
smart city domain.
The following applications and examples are popular IoT products. Figure 1
illustrates IoT applications:
Health Care: IoT Healthcare applications are built to serve the people,
which innately raise the necessities of reliability, security and safety.
Moreover, the applications must provide notifications and responses with
respect to the status of patients. A healthcare management system must
ascertain the safety of patients by observing patients' activities and key
signs. A healthcare management system should offer precise results in a
timely fashion and should provide secure and reliable services for
caregivers, physicians and patients (Miranda, et al., 2016).
Wearables: These are device-to-device developments that are part of health
domain. Many wearable products have been implemented. For example:
wearable healthcare devices. One of the newest wearable items is Google
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Glass device which is enabled people to use numerous Internet applications
on the go.
Connect Vehicles: These are part of vehicles and transportation
applications. For example, the car navigation system or mapping
applications of the smartphones that enabled people to find their way for
unfamiliar places (Zhang, Chen, Chen, & Chen, 2016).
Home Automation: usually, these systems use small data packets of
information satisfy the communication between devices with relatively low
data rate requirements. Smart thermostats, smart appliances, intelligent
lighting, and many other smarted house devices are automation scenarios.
Location-based services: many useful services of location-based can also
provide by Internet of Things. Automate notifications, tracking children,
eldercare, and location-based marketing are examples of location-based
services (Dinh, Kim, & Lee, 2017).
Smart Meters: Smart meters are advanced smart home facilities which are
built with network connectivity that permit investigation and examination of
the energy consumed and produced toward individual dwellings, in
distinctive circuits and comparing appliances inside every dwelling, for
example, water heaters and solar panels. Information gathered using smart
meters can be evaluated on request of both clients and distributors. Thus,
smart meters let distributors to set their prices based on these analyses
(Lloret, Tomas, Canovas, & Parra, 2016).
on the go.
Connect Vehicles: These are part of vehicles and transportation
applications. For example, the car navigation system or mapping
applications of the smartphones that enabled people to find their way for
unfamiliar places (Zhang, Chen, Chen, & Chen, 2016).
Home Automation: usually, these systems use small data packets of
information satisfy the communication between devices with relatively low
data rate requirements. Smart thermostats, smart appliances, intelligent
lighting, and many other smarted house devices are automation scenarios.
Location-based services: many useful services of location-based can also
provide by Internet of Things. Automate notifications, tracking children,
eldercare, and location-based marketing are examples of location-based
services (Dinh, Kim, & Lee, 2017).
Smart Meters: Smart meters are advanced smart home facilities which are
built with network connectivity that permit investigation and examination of
the energy consumed and produced toward individual dwellings, in
distinctive circuits and comparing appliances inside every dwelling, for
example, water heaters and solar panels. Information gathered using smart
meters can be evaluated on request of both clients and distributors. Thus,
smart meters let distributors to set their prices based on these analyses
(Lloret, Tomas, Canovas, & Parra, 2016).
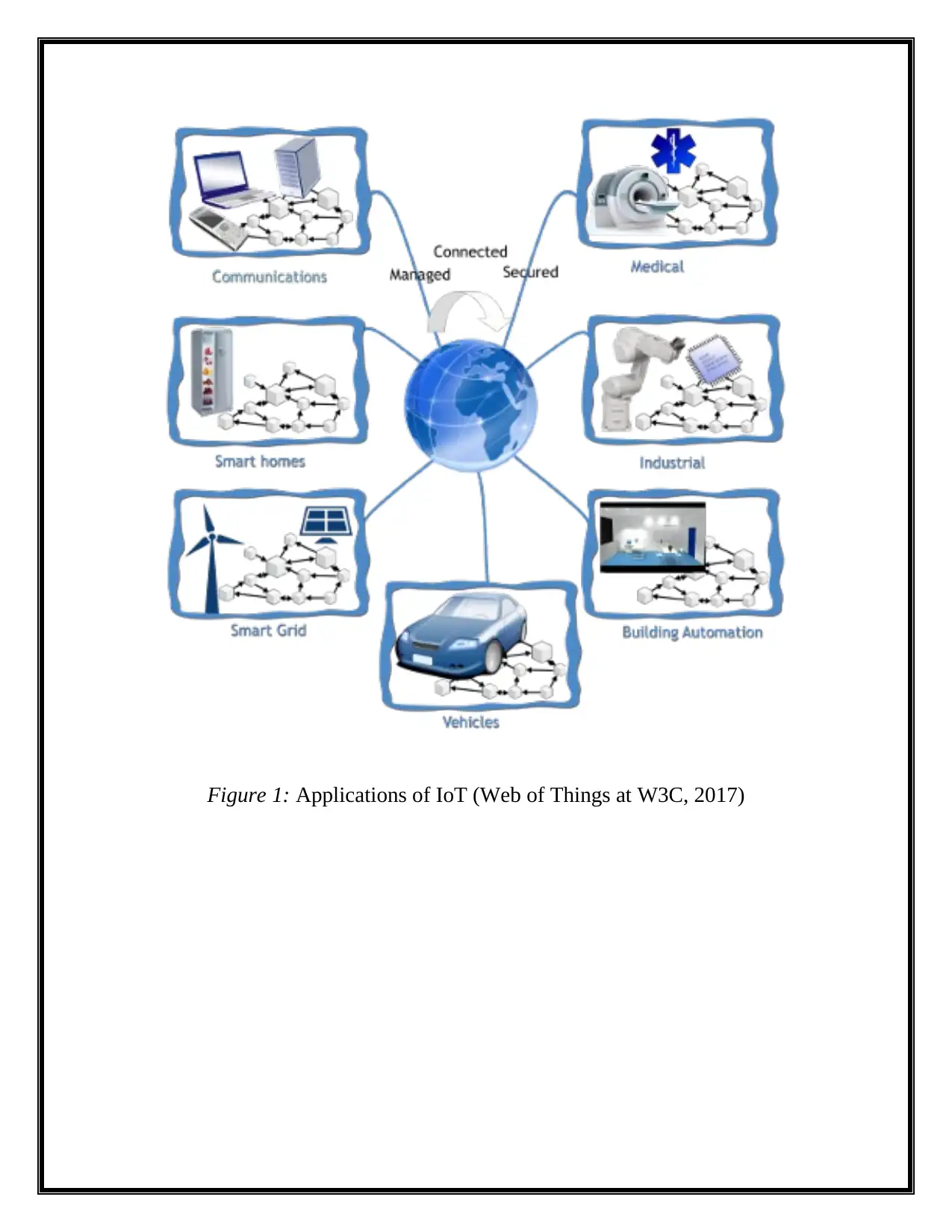
Figure 1: Applications of IoT (Web of Things at W3C, 2017)

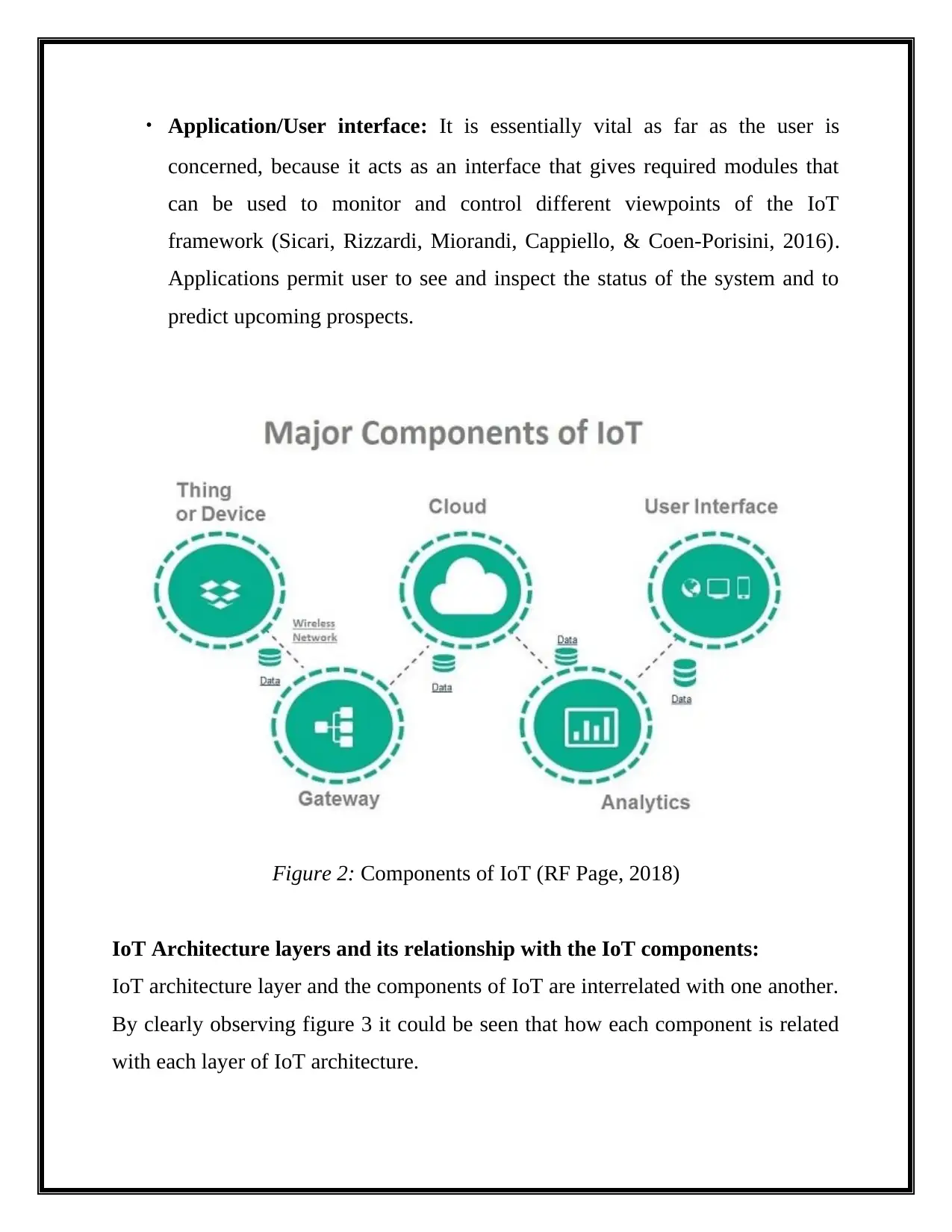
Major components or functional blocks of IoT:
An IoT system is comprised of several functional blocks that enable different
utilities of the framework such as, sensing, identification, actuation,
communication, and management. Lomotey, Pry, & Chai (2017) explains these
components as in figure 2 displays and they are described beneath:
Device and sensor: IoT framework is dependent upon devices that offer
detecting, actuation, observing, and control events. IoT devices swap
information with other joined devices and application. Else gather
information from different units and process the information. Otherwise
send information to central servers or cloud-based application. Perform few
tasks inside IoT system depending on space imperatives such as memory,
managing capabilities, speed.
Different types of IoT devices exist, for instance wearables, smart watches,
sensor lights, automobiles etc. Nearly all IoT devices provides information
which is transformed for information analytics, will provide prompt and
appropriate data that can be further used in necessary acts (Sicari, Rizzardi,
Miorandi, Cappiello, & Coen-Porisini, 2016). For example, sensor data
provided by a smart appliance like fridge that notifies user that the milk is
below the threshold allows the user to plan ahead for his/her needs.
An IoT device might comprise about numerous interfaces for
communicating with several other devices including both wired and wireless
(Lomotey, Pry, & Chai, 2017). They are:
I/O interfaces for sensors
Interfaces for internet connectivity
Memory and storing interfaces
An IoT system is comprised of several functional blocks that enable different
utilities of the framework such as, sensing, identification, actuation,
communication, and management. Lomotey, Pry, & Chai (2017) explains these
components as in figure 2 displays and they are described beneath:
Device and sensor: IoT framework is dependent upon devices that offer
detecting, actuation, observing, and control events. IoT devices swap
information with other joined devices and application. Else gather
information from different units and process the information. Otherwise
send information to central servers or cloud-based application. Perform few
tasks inside IoT system depending on space imperatives such as memory,
managing capabilities, speed.
Different types of IoT devices exist, for instance wearables, smart watches,
sensor lights, automobiles etc. Nearly all IoT devices provides information
which is transformed for information analytics, will provide prompt and
appropriate data that can be further used in necessary acts (Sicari, Rizzardi,
Miorandi, Cappiello, & Coen-Porisini, 2016). For example, sensor data
provided by a smart appliance like fridge that notifies user that the milk is
below the threshold allows the user to plan ahead for his/her needs.
An IoT device might comprise about numerous interfaces for
communicating with several other devices including both wired and wireless
(Lomotey, Pry, & Chai, 2017). They are:
I/O interfaces for sensors
Interfaces for internet connectivity
Memory and storing interfaces
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Audio/Video interfaces
Gateway: Enormous amount of data will be generated by the sensors which
needs a strong and secured wired or wireless network transport medium.
Existing networks frequently involve with extremely different protocols that
are needed to help machine-to-machine (M2M) networks and applications.
Due to the necessity to serve a wider extent of IOT services several networks
having different technologies and access protocols are required to deal with
one another. These networks could be a private, public or hybrid model.
Cloud: Cloud appears to be the best innovation that could study and store
the information viably. It is sophisticated technology where number of
servers converged on a single cloud platform for offering information
sharing between one another which could be retrieved anytime from all over
the world (Jenson, 2017). Apart from converge the servers, it analyzes the
data gathered from the sensors and stores it for future purpose. This is barely
a start of unleashing the real capability of the system. Cloud could have
enormous uses because of interfacing with smart devices as these devices are
using millions of sensors which could leads to substantial improvement in
IoT.
Analytics: Analytics is the methodology for changing analog information
into service insights gathered from billions of smart devices and sensors
which can be transitioned and used later. Analytic results from smart devices
are certain for the management and development of IoT framework. Real-
time smart analytics is a significant advantage of IoT system as it helps to
figure out anomalies in the gathered information and allows reacting quickly
before an undesired situation occurs.
Gateway: Enormous amount of data will be generated by the sensors which
needs a strong and secured wired or wireless network transport medium.
Existing networks frequently involve with extremely different protocols that
are needed to help machine-to-machine (M2M) networks and applications.
Due to the necessity to serve a wider extent of IOT services several networks
having different technologies and access protocols are required to deal with
one another. These networks could be a private, public or hybrid model.
Cloud: Cloud appears to be the best innovation that could study and store
the information viably. It is sophisticated technology where number of
servers converged on a single cloud platform for offering information
sharing between one another which could be retrieved anytime from all over
the world (Jenson, 2017). Apart from converge the servers, it analyzes the
data gathered from the sensors and stores it for future purpose. This is barely
a start of unleashing the real capability of the system. Cloud could have
enormous uses because of interfacing with smart devices as these devices are
using millions of sensors which could leads to substantial improvement in
IoT.
Analytics: Analytics is the methodology for changing analog information
into service insights gathered from billions of smart devices and sensors
which can be transitioned and used later. Analytic results from smart devices
are certain for the management and development of IoT framework. Real-
time smart analytics is a significant advantage of IoT system as it helps to
figure out anomalies in the gathered information and allows reacting quickly
before an undesired situation occurs.
Application/User interface: It is essentially vital as far as the user is
concerned, because it acts as an interface that gives required modules that
can be used to monitor and control different viewpoints of the IoT
framework (Sicari, Rizzardi, Miorandi, Cappiello, & Coen-Porisini, 2016).
Applications permit user to see and inspect the status of the system and to
predict upcoming prospects.
Figure 2: Components of IoT (RF Page, 2018)
IoT Architecture layers and its relationship with the IoT components:
IoT architecture layer and the components of IoT are interrelated with one another.
By clearly observing figure 3 it could be seen that how each component is related
with each layer of IoT architecture.
concerned, because it acts as an interface that gives required modules that
can be used to monitor and control different viewpoints of the IoT
framework (Sicari, Rizzardi, Miorandi, Cappiello, & Coen-Porisini, 2016).
Applications permit user to see and inspect the status of the system and to
predict upcoming prospects.
Figure 2: Components of IoT (RF Page, 2018)
IoT Architecture layers and its relationship with the IoT components:
IoT architecture layer and the components of IoT are interrelated with one another.
By clearly observing figure 3 it could be seen that how each component is related
with each layer of IoT architecture.

According to (Jing, Vasilakos, Wan, Lu, & Qiu, 2014) considering each layer, the
sensing layer is correlated with devices and sensors component, network layer is
associated with gateways, support layer is accompanying with cloud and analytics
(i.e. processing unit) and lastly application layer is combination of IoT applications
and user interface.
Ren, Guo, Xu, & Zhang (2017) explanation about the relationship between layers
and components are evidently depicted below:
Perception/Sensing Layer: It is the device and sensor layer in IoT that
provides physical implying for every item. It comprises information sensors
in distinctive structures such as RFID tags, IR sensors and various sensor
networks which are able to sense the temperature, humidity, velocity and
locations of the device. Kim, Lee, & Park (2017) says that, this layer collects
appropriate data of the devices from the sensor connected to them and
translate the data into signals for the ability to pass between layers and
forwarded to the network layer for more activities.
Network Layer: This layer transfers the digital signals received from the
sensing layer to the middleware layer processing system using transmission
mediums such as Wi-Fi, Bluetooth, WiMAX, Zigbee, GSM, and 3G via the
IPv4, IPv6, and DDS protocols.
Data processing/Support Layer: This layer comprises of few technologies
such as cloud computing, ubiquitous computing that process the information
or data received from the sensors and stores it in a database. The data
received will be completely processed, computerized, stored and used for a
necessary action need to be taken.
sensing layer is correlated with devices and sensors component, network layer is
associated with gateways, support layer is accompanying with cloud and analytics
(i.e. processing unit) and lastly application layer is combination of IoT applications
and user interface.
Ren, Guo, Xu, & Zhang (2017) explanation about the relationship between layers
and components are evidently depicted below:
Perception/Sensing Layer: It is the device and sensor layer in IoT that
provides physical implying for every item. It comprises information sensors
in distinctive structures such as RFID tags, IR sensors and various sensor
networks which are able to sense the temperature, humidity, velocity and
locations of the device. Kim, Lee, & Park (2017) says that, this layer collects
appropriate data of the devices from the sensor connected to them and
translate the data into signals for the ability to pass between layers and
forwarded to the network layer for more activities.
Network Layer: This layer transfers the digital signals received from the
sensing layer to the middleware layer processing system using transmission
mediums such as Wi-Fi, Bluetooth, WiMAX, Zigbee, GSM, and 3G via the
IPv4, IPv6, and DDS protocols.
Data processing/Support Layer: This layer comprises of few technologies
such as cloud computing, ubiquitous computing that process the information
or data received from the sensors and stores it in a database. The data
received will be completely processed, computerized, stored and used for a
necessary action need to be taken.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
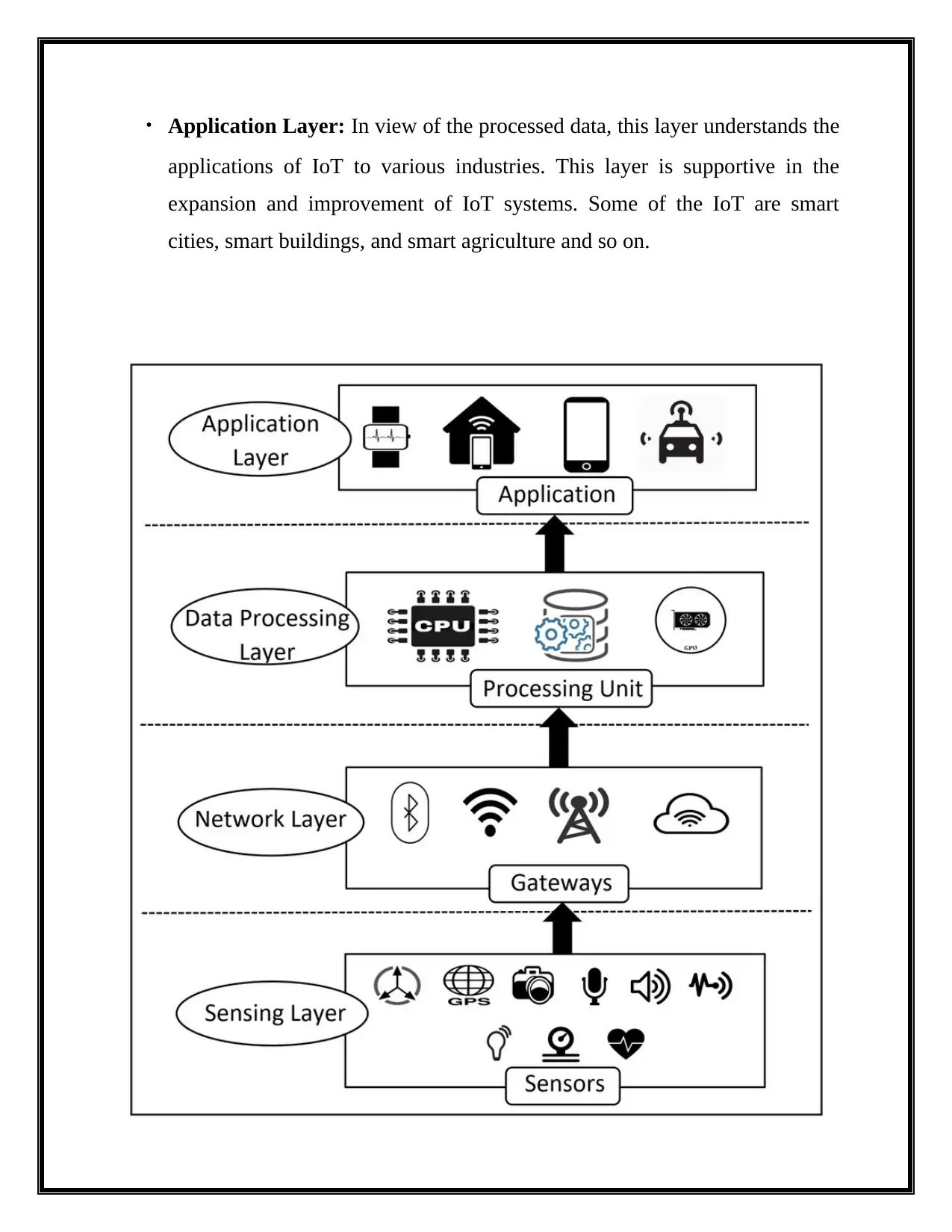
Application Layer: In view of the processed data, this layer understands the
applications of IoT to various industries. This layer is supportive in the
expansion and improvement of IoT systems. Some of the IoT are smart
cities, smart buildings, and smart agriculture and so on.
applications of IoT to various industries. This layer is supportive in the
expansion and improvement of IoT systems. Some of the IoT are smart
cities, smart buildings, and smart agriculture and so on.

Figure 3:IoT Architecture Layers and Components (ResearchGate, 2018)
Challenges associated with cloud-based IoT:
Gathering the data from the servers, forwarding the packets to the sensors or
devices all these processes rely on cloud and gateway acts as a medium. During
these actions there are numerous security threats that could be possible. Primarily
concentrating on the security threats to cloud-based IoT there are possible threats
like data confidentiality, integrity, data forgery, spoofing and all the data security
issues (Neville-Neil, 2017).
According to Zhou, Cao, Dong, & Vasilakos (2017), in addition to the traditional
data security issues cloud-based IoT is having few other privacy and security
concerns that are presented below:
Identity Privacy: Identity privacy suggests that in case of IoT user’s the
true identity of the user should be always secured from the public otherwise
it could be misused. Alternatively, it has few benefits as well, when a serious
or emergency incident happens authorities could trace the person based on
the identity. Most of the security issues will have its positive and negative
side it depends on how we use it. The technique adopted to trace the identity
is pseudonyms, yet the occasionally updated pseudonyms and certificates
causing terrible computational expenses to resource-constrained IoT nodes.
Challenges associated with cloud-based IoT:
Gathering the data from the servers, forwarding the packets to the sensors or
devices all these processes rely on cloud and gateway acts as a medium. During
these actions there are numerous security threats that could be possible. Primarily
concentrating on the security threats to cloud-based IoT there are possible threats
like data confidentiality, integrity, data forgery, spoofing and all the data security
issues (Neville-Neil, 2017).
According to Zhou, Cao, Dong, & Vasilakos (2017), in addition to the traditional
data security issues cloud-based IoT is having few other privacy and security
concerns that are presented below:
Identity Privacy: Identity privacy suggests that in case of IoT user’s the
true identity of the user should be always secured from the public otherwise
it could be misused. Alternatively, it has few benefits as well, when a serious
or emergency incident happens authorities could trace the person based on
the identity. Most of the security issues will have its positive and negative
side it depends on how we use it. The technique adopted to trace the identity
is pseudonyms, yet the occasionally updated pseudonyms and certificates
causing terrible computational expenses to resource-constrained IoT nodes.

Location Privacy: Location privacy appears to be particularly dangerous for
IoT users since this could laid open the identity and living habits of the user
by tracking his/her locations. It could uncover all the details of the IoT user.
Pseudonyms are the broadly used technique to mask the locations visited by
the user. But it couldn’t able to stand up to the physically dynamic tracing
attack, because the location information of the user is not secured directly as
it is secured using an external technique. For instance, the IoT user’s actual
identity can be gathered by visiting to the users occasionally visited places,
by observing and monitoring the user activity.
Node Compromise Attack: In this attack opponent extracts all private data
including the secret key that could be used to encrypt the data, private key
that can be used to perform signatures etc. and use these details to rewrite
the program or substitute the IoT device with other device that is under the
control of him.
Target-oriented compromise attack: In this attack the opponent with his
ability to monitor globally choose an IoT node that is having more packets
as these attack only compromises the nodes that is having more traffic.
Because with just one attack the attacker can gather several packets that
could be enough for obtaining the decrypted message or obstructing it from
reaching the destination.
Layer Removing/Adding Attack: The layer removing attack will be
launched to boost their reward credit by decreasing the amount intermediate
transmitters that share the credit. In contrast, layer adding attack will be
launched to boost their reward credit by deviating and by-passing the IoT
user maliciously so that the attacker can receive all the credit.
IoT users since this could laid open the identity and living habits of the user
by tracking his/her locations. It could uncover all the details of the IoT user.
Pseudonyms are the broadly used technique to mask the locations visited by
the user. But it couldn’t able to stand up to the physically dynamic tracing
attack, because the location information of the user is not secured directly as
it is secured using an external technique. For instance, the IoT user’s actual
identity can be gathered by visiting to the users occasionally visited places,
by observing and monitoring the user activity.
Node Compromise Attack: In this attack opponent extracts all private data
including the secret key that could be used to encrypt the data, private key
that can be used to perform signatures etc. and use these details to rewrite
the program or substitute the IoT device with other device that is under the
control of him.
Target-oriented compromise attack: In this attack the opponent with his
ability to monitor globally choose an IoT node that is having more packets
as these attack only compromises the nodes that is having more traffic.
Because with just one attack the attacker can gather several packets that
could be enough for obtaining the decrypted message or obstructing it from
reaching the destination.
Layer Removing/Adding Attack: The layer removing attack will be
launched to boost their reward credit by decreasing the amount intermediate
transmitters that share the credit. In contrast, layer adding attack will be
launched to boost their reward credit by deviating and by-passing the IoT
user maliciously so that the attacker can receive all the credit.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Forward and Backward Security: Forward and backward security is
essential because of the flexibility and changing social group in IoT. The
forward security implies that recently joined IoT clients can decrypt the
encrypted message only after joining those cluster. Backward security
implies that the IoT clients who left the cluster can decrypt the encrypted
message until the leave the cluster.
Semi-Trusted or Malicious Cloud Security: Security and privacy issues of
the cloud had to be considered for the convergence of cloud with IoT. The
semi-trusted model implies that the cloud might obey with the protocol
specification and attempt its best for extracting the confidential details from
the IoT users. In Malicious model, the opponent subjectively obliterates the
protocol execution so that for purpose of computation the subsequent three
security measures had to be achieved:
Input privacy: Data an individual sent must be safeguarded
considerably from the conspiracy between the cloud and the
receiver.
Output privacy: The data an individual sent that passes
through the cloud should only be decrypted by the receiver.
Function privacy: The functioning of sending and receiving
data must be safeguarded from the conspiracy of cloud and
malicious IoT user.
There are different other open issues and challenges that impact on cloud security
which are emphasized below:
Data breaches: The malicious activities and data loss are the reasons that
impacts on user’s data. The data breaching is different than the loss of data
essential because of the flexibility and changing social group in IoT. The
forward security implies that recently joined IoT clients can decrypt the
encrypted message only after joining those cluster. Backward security
implies that the IoT clients who left the cluster can decrypt the encrypted
message until the leave the cluster.
Semi-Trusted or Malicious Cloud Security: Security and privacy issues of
the cloud had to be considered for the convergence of cloud with IoT. The
semi-trusted model implies that the cloud might obey with the protocol
specification and attempt its best for extracting the confidential details from
the IoT users. In Malicious model, the opponent subjectively obliterates the
protocol execution so that for purpose of computation the subsequent three
security measures had to be achieved:
Input privacy: Data an individual sent must be safeguarded
considerably from the conspiracy between the cloud and the
receiver.
Output privacy: The data an individual sent that passes
through the cloud should only be decrypted by the receiver.
Function privacy: The functioning of sending and receiving
data must be safeguarded from the conspiracy of cloud and
malicious IoT user.
There are different other open issues and challenges that impact on cloud security
which are emphasized below:
Data breaches: The malicious activities and data loss are the reasons that
impacts on user’s data. The data breaching is different than the loss of data

as it is a out of scope in regard to it, here the leakage of sensitive information
is depicted as data breaching which is an issues associated with the cloud
security (Coppolino, et al., 2017).
Shared technologies vulnerabilities: Gaining access to the physical host
where other virtual machines (VM) placed results in impacting securities
enhancing vulnerabilities.
Account or service traffic hijacking: Losing control over the self-account
and hampers the effectiveness of transaction process is a major issue. It
results in affecting the integrity and availability of the services
Denial of service (DoS) attacks: This attack which leads to the issues in
processing the legitimate requests due to multiple fake processing is DoS. It
is the most terrible issue when the cloud infrastructure is made unavailable.
Malicious insiders: The activity through which wrong advantage is taken in
order to hamper the sensitive information is the malicious insiders that affect
the security and privacy of the cloud services (Coppolino, et al., 2017).
is depicted as data breaching which is an issues associated with the cloud
security (Coppolino, et al., 2017).
Shared technologies vulnerabilities: Gaining access to the physical host
where other virtual machines (VM) placed results in impacting securities
enhancing vulnerabilities.
Account or service traffic hijacking: Losing control over the self-account
and hampers the effectiveness of transaction process is a major issue. It
results in affecting the integrity and availability of the services
Denial of service (DoS) attacks: This attack which leads to the issues in
processing the legitimate requests due to multiple fake processing is DoS. It
is the most terrible issue when the cloud infrastructure is made unavailable.
Malicious insiders: The activity through which wrong advantage is taken in
order to hamper the sensitive information is the malicious insiders that affect
the security and privacy of the cloud services (Coppolino, et al., 2017).

Cloud and what are the different types of clouds
According to Coppolino, et al. (2017), the mix of market and technology-related
factors results in the increase in momentum of cloud computing. The security
issues of cloud technology can never be overlooked which are data breaches,
shared technologies vulnerabilities, service or account traffic hijacking, denial of
service (DoS) attacks and other malicious insiders.
But the blockchain technology has the capability to revolutionize applications and
empower business functionalities through enhancing security and preventing
vulnerabilities.
According to Vafamehr & Khodayar (2018), a web-based, distributed computing
that uses information, resources and applications is cloud computing. It involves
the establishment of distributed data centers that consumes less energy. The goal of
computing reliability and economic efficiency is achieved through energy
management solutions provided by the data centers. The IT barriers are effectively
handled through the use of this solution (Vafamehr & Khodayar, 2018). IoT based
cloud solutions facilitates different services, it leads to the increase in energy-
efficiency but the problem related to the security features remain unresolved.
The cloud technology facilitates the utilization of underutilized resources through
sharing it and enhances the effective use of energy (Ahmad, et al., 2017). The
effective management and controlling information flow is achieved through this
technology.
Structure of Cloud
According to Coppolino, et al. (2017), the mix of market and technology-related
factors results in the increase in momentum of cloud computing. The security
issues of cloud technology can never be overlooked which are data breaches,
shared technologies vulnerabilities, service or account traffic hijacking, denial of
service (DoS) attacks and other malicious insiders.
But the blockchain technology has the capability to revolutionize applications and
empower business functionalities through enhancing security and preventing
vulnerabilities.
According to Vafamehr & Khodayar (2018), a web-based, distributed computing
that uses information, resources and applications is cloud computing. It involves
the establishment of distributed data centers that consumes less energy. The goal of
computing reliability and economic efficiency is achieved through energy
management solutions provided by the data centers. The IT barriers are effectively
handled through the use of this solution (Vafamehr & Khodayar, 2018). IoT based
cloud solutions facilitates different services, it leads to the increase in energy-
efficiency but the problem related to the security features remain unresolved.
The cloud technology facilitates the utilization of underutilized resources through
sharing it and enhances the effective use of energy (Ahmad, et al., 2017). The
effective management and controlling information flow is achieved through this
technology.
Structure of Cloud
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

On the basis of the varying operational schemes, the different models of cloud
have been effectively classified into public cloud, private cloud, hybrid cloud and
community cloud.
Public Cloud: In this model, the resources are made available to the public
with the privacy and security risks. Organisation that requires high security
and reliability needs cannot use this cloud technology for managing their
organizational functions.
Private Cloud: The resources are exclusively available to a single enterprise
where the extent of control over performance, reliability and security is high.
In this case, operational cost is also considerable that help in providing
major benefits to the end users through cloud technology.
Hybrid Cloud: It involves the integration of the private IT resources
dedicated to a venture with the public cloud. According to Vafamehr &
Khodayar (2018), through the cloud technology, the organisation provides
storage to the protected data on private clouds and manages the
computational resources in the public cloud with intention to execute
applications that depends upon the stored data.
Community Cloud: It involves the mutual sharing of the cloud computing
services along with their consequent costs among different enterprises with
similar privacy, and security necessities within a community.
The four different layers help in presenting the structure of the cloud computing
that layers are as follows:
Hardware Layer
Infrastructure Layer
Platform Layer
have been effectively classified into public cloud, private cloud, hybrid cloud and
community cloud.
Public Cloud: In this model, the resources are made available to the public
with the privacy and security risks. Organisation that requires high security
and reliability needs cannot use this cloud technology for managing their
organizational functions.
Private Cloud: The resources are exclusively available to a single enterprise
where the extent of control over performance, reliability and security is high.
In this case, operational cost is also considerable that help in providing
major benefits to the end users through cloud technology.
Hybrid Cloud: It involves the integration of the private IT resources
dedicated to a venture with the public cloud. According to Vafamehr &
Khodayar (2018), through the cloud technology, the organisation provides
storage to the protected data on private clouds and manages the
computational resources in the public cloud with intention to execute
applications that depends upon the stored data.
Community Cloud: It involves the mutual sharing of the cloud computing
services along with their consequent costs among different enterprises with
similar privacy, and security necessities within a community.
The four different layers help in presenting the structure of the cloud computing
that layers are as follows:
Hardware Layer
Infrastructure Layer
Platform Layer
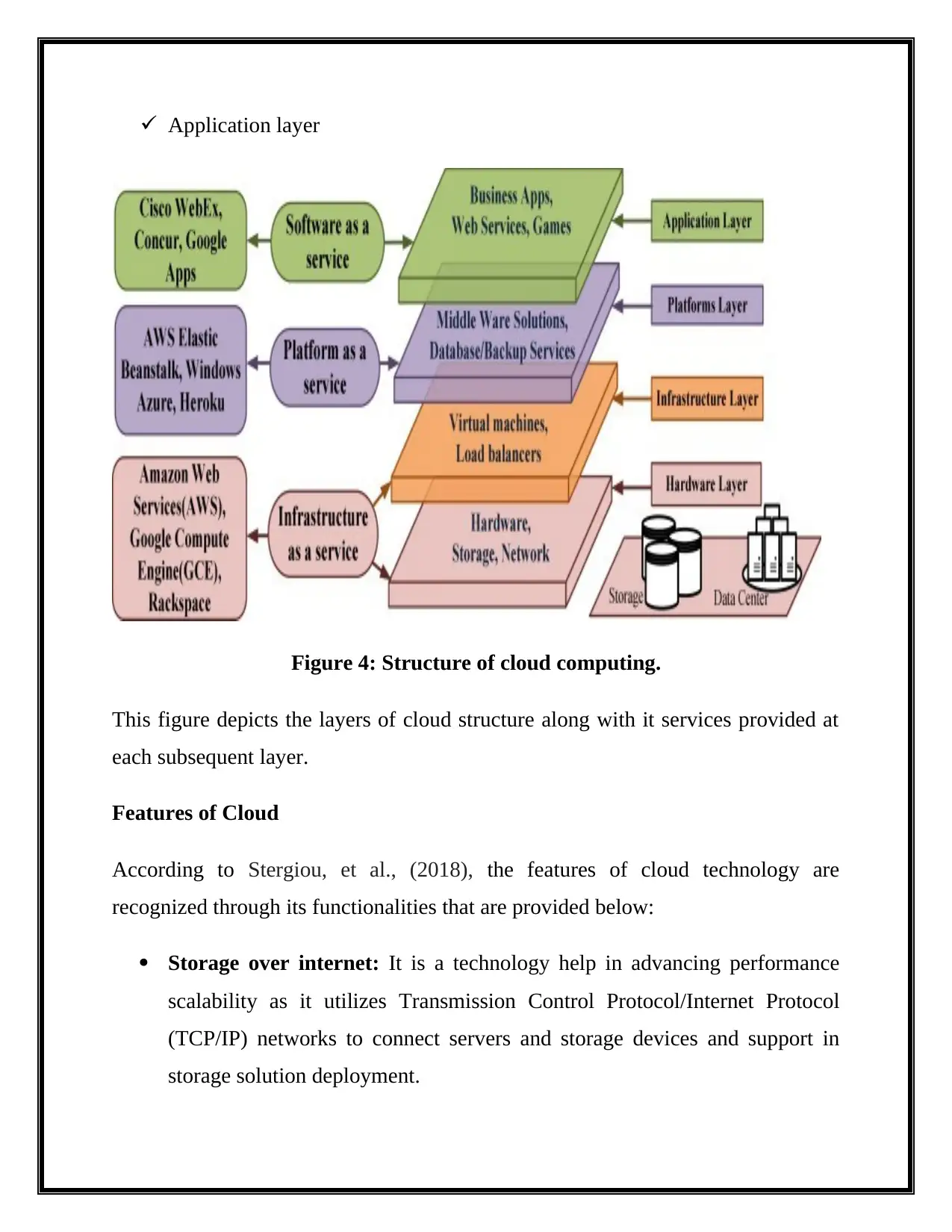
Application layer
Figure 4: Structure of cloud computing.
This figure depicts the layers of cloud structure along with it services provided at
each subsequent layer.
Features of Cloud
According to Stergiou, et al., (2018), the features of cloud technology are
recognized through its functionalities that are provided below:
Storage over internet: It is a technology help in advancing performance
scalability as it utilizes Transmission Control Protocol/Internet Protocol
(TCP/IP) networks to connect servers and storage devices and support in
storage solution deployment.
Figure 4: Structure of cloud computing.
This figure depicts the layers of cloud structure along with it services provided at
each subsequent layer.
Features of Cloud
According to Stergiou, et al., (2018), the features of cloud technology are
recognized through its functionalities that are provided below:
Storage over internet: It is a technology help in advancing performance
scalability as it utilizes Transmission Control Protocol/Internet Protocol
(TCP/IP) networks to connect servers and storage devices and support in
storage solution deployment.

Service over internet: The internet efficiency, speed and ubiquity are
harnessed with intention to transform aspirations into achievements.
Applications over internet: It involves the performing of job on the cloud
server through an internet connection.
Energy-efficiency: The effective management of energy is in order to
reduce the consumption of resource utilization for the attainment of
sustainability and growth.
Computational capability: Through performing correct calculations and
meeting the requirements effectively.
While the several key functions that are supported by the blockchain are
transactional validity, persistence, anonymity, privacy, immediacy and traceability
that help in amplifying trustfulness (Subramanian, 2017).
harnessed with intention to transform aspirations into achievements.
Applications over internet: It involves the performing of job on the cloud
server through an internet connection.
Energy-efficiency: The effective management of energy is in order to
reduce the consumption of resource utilization for the attainment of
sustainability and growth.
Computational capability: Through performing correct calculations and
meeting the requirements effectively.
While the several key functions that are supported by the blockchain are
transactional validity, persistence, anonymity, privacy, immediacy and traceability
that help in amplifying trustfulness (Subramanian, 2017).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

REFERENCES
Ahmad, I., Noor, R. M., Ali, I., Imran, M., &Vasilakos, A. (2017).Characterizing
the role of vehicular cloud computing in road traffic
management. International Journal of Distributed Sensor Networks, 13(5),
1550147717708728 (Q2).
Cheng, C., Lu, R., Petzoldt, A., & Takagi, T. (2017).Securing the Internet of
Things in a quantum world. IEEE Communications Magazine, 55(2), 116-
120 (Q1).
Coppolino, L., D’Antonio, S., Mazzeo, G., & Romano, L. (2017). Cloud security:
Emerging threats and current solutions. Computers & Electrical
Engineering, 59, 126-140 (Q1).
Deng, Y.-Y., Chen, C.-L., Tsaur, W.-J., Tang, Y.-W., & Chen, J.-H. (2017).
Internet of Things (IoT) Based Design of a Secure and Lightweight Body
Area Network (BAN) Healthcare System. Sensors.
doi:doi:10.3390/s17122919 (Q2)
Dinh, T., Kim, Y., & Lee, H. (2017). A Location-Based Interactive Model of
Internet of Things and Cloud (IoT-Cloud) for Mobile Cloud Computing
Applications. Sensors, 17(489). doi:10.3390/s17030489 (Q2)
Gil, D., Ferrández, A., Mora-Mora, H., & Peral, J. (2016). Internet of Things: A
Review of Surveys Based on Context Aware Intelligent Services.
Sensors.doi:10.3390/s16071069 (Q2)
Ahmad, I., Noor, R. M., Ali, I., Imran, M., &Vasilakos, A. (2017).Characterizing
the role of vehicular cloud computing in road traffic
management. International Journal of Distributed Sensor Networks, 13(5),
1550147717708728 (Q2).
Cheng, C., Lu, R., Petzoldt, A., & Takagi, T. (2017).Securing the Internet of
Things in a quantum world. IEEE Communications Magazine, 55(2), 116-
120 (Q1).
Coppolino, L., D’Antonio, S., Mazzeo, G., & Romano, L. (2017). Cloud security:
Emerging threats and current solutions. Computers & Electrical
Engineering, 59, 126-140 (Q1).
Deng, Y.-Y., Chen, C.-L., Tsaur, W.-J., Tang, Y.-W., & Chen, J.-H. (2017).
Internet of Things (IoT) Based Design of a Secure and Lightweight Body
Area Network (BAN) Healthcare System. Sensors.
doi:doi:10.3390/s17122919 (Q2)
Dinh, T., Kim, Y., & Lee, H. (2017). A Location-Based Interactive Model of
Internet of Things and Cloud (IoT-Cloud) for Mobile Cloud Computing
Applications. Sensors, 17(489). doi:10.3390/s17030489 (Q2)
Gil, D., Ferrández, A., Mora-Mora, H., & Peral, J. (2016). Internet of Things: A
Review of Surveys Based on Context Aware Intelligent Services.
Sensors.doi:10.3390/s16071069 (Q2)

Gromovs, G., & Lammi, M. (2017). Blockchain and Internet of Things Require
Innovative Approach to Logistics Education. Transport Problems,
12(Special Edition). doi:DOI: 10.20858/tp.2017.12.se.2 (Q3)
Jenson, S. (2017, February). The Future IoT: Building Better Legos. COMPUTER,
68-71. (Q1)
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the
Internet of Things: perspectives and challenges. Wireless Networks, 20,
2481–2501. doi:10.1007/s11276-014-0761-7 (Q2)
Kim, M., Lee, N. Y., & Park, J. H. (2017). A Security Generic Service Interface of
Internet of Things (IoT) Platforms. Symmetry, 9(171).
doi:10.3390/sym9090171 (Q2)
Kshetri, N. (November 2017). Blockchain's roles in strengthening cybersecurity
and protecting privacy. Telecommunications Policy, 1027-1038.
doi:https://doi.org/10.1016
/j.telpol.2017.09.003 (Q2)
Lee, B., & Lee, J.-H. (2016, September 13). Blockchain-based secure firmware
update for embedded devices in an Internet of Things environment. Journal
of Supercomputing, 73, 1152–1167.doi:DOI 10.1007/s11227-016-1870-0
(Q2)
Lloret, J., Tomas, J., Canovas, A., & Parra, L. (2016, December). An Integrated
IoT Architecture for Smart Metering. IEEE Communications Magazine.
doi:10.1109/MCOM.2016.1600
647CM (Q1)
Innovative Approach to Logistics Education. Transport Problems,
12(Special Edition). doi:DOI: 10.20858/tp.2017.12.se.2 (Q3)
Jenson, S. (2017, February). The Future IoT: Building Better Legos. COMPUTER,
68-71. (Q1)
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the
Internet of Things: perspectives and challenges. Wireless Networks, 20,
2481–2501. doi:10.1007/s11276-014-0761-7 (Q2)
Kim, M., Lee, N. Y., & Park, J. H. (2017). A Security Generic Service Interface of
Internet of Things (IoT) Platforms. Symmetry, 9(171).
doi:10.3390/sym9090171 (Q2)
Kshetri, N. (November 2017). Blockchain's roles in strengthening cybersecurity
and protecting privacy. Telecommunications Policy, 1027-1038.
doi:https://doi.org/10.1016
/j.telpol.2017.09.003 (Q2)
Lee, B., & Lee, J.-H. (2016, September 13). Blockchain-based secure firmware
update for embedded devices in an Internet of Things environment. Journal
of Supercomputing, 73, 1152–1167.doi:DOI 10.1007/s11227-016-1870-0
(Q2)
Lloret, J., Tomas, J., Canovas, A., & Parra, L. (2016, December). An Integrated
IoT Architecture for Smart Metering. IEEE Communications Magazine.
doi:10.1109/MCOM.2016.1600
647CM (Q1)

Lomotey, R. K., Pry, J. C., & Chai, C. (2017). Traceability and visual analytics for
the Internet-of-Things (IoT) architecture. World Wide Web, 21, 7-32.
doi:DOI 10.1007/s11280-017-0461-1 (Q2)
Meddeb, A. (2016, July). Internet of Things Standards: Who Stands Out from the
Crowd? IEEE Communications Magazine. Retrieved March 08, 2018 (Q1)
Miranda, J., Cabral, J., Wagner, S. R., Pedersen, C. F., Ravelo, B., Memon, M., &
Mathiesen, M. (2016). An Open Platform for Seamless Sensor Support in
Healthcare for the Internet of Things. Sensors, 16(2089).
doi:10.3390/s16122089 (Q2)
Neville-Neil, G. V. (2017, OCTOBER). IoT: The Internet of Terror.
Communications of The ACM, 60(10). doi:10.1145/3132728 (Q1)
Rajiv. (2018, January 10). What are the major components of Internet of
Things[Image]. Retrieved March 22, 2018, from RF Page:
https://www.rfpage.com/what-are-the-major-components-of-internet-of-
things/
Ren, J., Guo, H., Xu, C., & Zhang, Y. (2017). Serving at the Edge: A Scalable IoT
Architecture Based on Transparent Computing. IEEE Networks, 17, 96-105.
doi:10.1109/MNET.2017
.1700030 (Q1)
Requirements of the network for the Internet of things. (2016, SEP 13). Retrieved
March 15, 2018, from International Telecommunication Union (ITU):
https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=13025
the Internet-of-Things (IoT) architecture. World Wide Web, 21, 7-32.
doi:DOI 10.1007/s11280-017-0461-1 (Q2)
Meddeb, A. (2016, July). Internet of Things Standards: Who Stands Out from the
Crowd? IEEE Communications Magazine. Retrieved March 08, 2018 (Q1)
Miranda, J., Cabral, J., Wagner, S. R., Pedersen, C. F., Ravelo, B., Memon, M., &
Mathiesen, M. (2016). An Open Platform for Seamless Sensor Support in
Healthcare for the Internet of Things. Sensors, 16(2089).
doi:10.3390/s16122089 (Q2)
Neville-Neil, G. V. (2017, OCTOBER). IoT: The Internet of Terror.
Communications of The ACM, 60(10). doi:10.1145/3132728 (Q1)
Rajiv. (2018, January 10). What are the major components of Internet of
Things[Image]. Retrieved March 22, 2018, from RF Page:
https://www.rfpage.com/what-are-the-major-components-of-internet-of-
things/
Ren, J., Guo, H., Xu, C., & Zhang, Y. (2017). Serving at the Edge: A Scalable IoT
Architecture Based on Transparent Computing. IEEE Networks, 17, 96-105.
doi:10.1109/MNET.2017
.1700030 (Q1)
Requirements of the network for the Internet of things. (2016, SEP 13). Retrieved
March 15, 2018, from International Telecommunication Union (ITU):
https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=13025
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Sharma, P. K., Singh, S., Jeong, Y. S., & Park, J. H. (2017). DistBlockNet: A
Distributed Blockchains-Based Secure SDN Architecture for IoT
Networks. IEEE Communications Magazine, 55(9), 78-85 (Q1).
Sicari, S., Rizzardi, A., Miorandi, D., Cappiello, C., & Coen-Porisini, A. (2016). A
secure and quality-aware prototypical architecture for the Internet of Things.
Information Systems, 58, 43-55. Retrieved from
http://dx.doi.org/10.1016/j.is.2016.02.003 (Q1)
Sikder, A. K., Petracca, G., Aksu, H., & Uluagac, A. S. (2018, Feb). A Survey on
Sensor-based Threats to Internet-of-Things (IoT) Devices and
Applications[Image]. Retrieved March 23, 2018, from ResearchGate:
https://www.researchgate.net/figure/IoT-Architecture-Layers-and-
Components_fig1_322975901
Special Report: The Internet of Things. (n.d.). Retrieved March 15, 2018, from
IEEE, The Institute: http://theinstitute.ieee.org/static/special-report-the-
internet-of-things
Stergiou, C., Psannis, K. E., Kim, B. G., & Gupta, B. (2018). Secure integration of
IoT and cloud computing. Future Generation Computer Systems, 78, 964-
975 (Q1).
Distributed Blockchains-Based Secure SDN Architecture for IoT
Networks. IEEE Communications Magazine, 55(9), 78-85 (Q1).
Sicari, S., Rizzardi, A., Miorandi, D., Cappiello, C., & Coen-Porisini, A. (2016). A
secure and quality-aware prototypical architecture for the Internet of Things.
Information Systems, 58, 43-55. Retrieved from
http://dx.doi.org/10.1016/j.is.2016.02.003 (Q1)
Sikder, A. K., Petracca, G., Aksu, H., & Uluagac, A. S. (2018, Feb). A Survey on
Sensor-based Threats to Internet-of-Things (IoT) Devices and
Applications[Image]. Retrieved March 23, 2018, from ResearchGate:
https://www.researchgate.net/figure/IoT-Architecture-Layers-and-
Components_fig1_322975901
Special Report: The Internet of Things. (n.d.). Retrieved March 15, 2018, from
IEEE, The Institute: http://theinstitute.ieee.org/static/special-report-the-
internet-of-things
Stergiou, C., Psannis, K. E., Kim, B. G., & Gupta, B. (2018). Secure integration of
IoT and cloud computing. Future Generation Computer Systems, 78, 964-
975 (Q1).

Subramanian, H. (2017). Decentralized blockchain-based electronic
marketplaces. Communications of the ACM, 61(1), 78-84 (Q1).
The Internet of Things (IoT): An Overview. (2015, OCT 15). Retrieved March 15,
2018, from Internet Society:
https://www.internetsociety.org/resources/doc/2015/iot-overview
Vafamehr, A., & Khodayar, M. E. (2018). Energy-aware cloud computing. The
Electricity Journal, 31(2), 40-49 (Q1).
Wang, F., Hu, L., Hu, J., Zhou, J., & Zhao, K. (2016, April 08). Recent Advances
in the Internet of Things:Multiple Perspectives. IETE Technical Review,
34(2), 122-132. doi:DOI: 10.1080/02564602.2016.1155419 (Q2)
Web of Things at W3C. (2017)[Image]. Retrieved March 16, 2018, from W3C:
https://www.w3.org/WoT/
Zhang, N., Chen, H., Chen, X., & Chen, J. (2016). Semantic Framework of Internet
of Things for Smart Cities: Case Studies. Sensors, 16(1501).
doi:10.3390/s16091501 (Q2)
Zhou, J., Cao, Z., Dong, X., & Vasilakos, A. V. (2017, Jan). Security and Privacy
for Cloud-Based IoT: Challenges, Countermeasures, and Future Directions.
IEEE Communications Magazine. doi:10.1109/MCOM.2017.1600363CM
(Q1)
marketplaces. Communications of the ACM, 61(1), 78-84 (Q1).
The Internet of Things (IoT): An Overview. (2015, OCT 15). Retrieved March 15,
2018, from Internet Society:
https://www.internetsociety.org/resources/doc/2015/iot-overview
Vafamehr, A., & Khodayar, M. E. (2018). Energy-aware cloud computing. The
Electricity Journal, 31(2), 40-49 (Q1).
Wang, F., Hu, L., Hu, J., Zhou, J., & Zhao, K. (2016, April 08). Recent Advances
in the Internet of Things:Multiple Perspectives. IETE Technical Review,
34(2), 122-132. doi:DOI: 10.1080/02564602.2016.1155419 (Q2)
Web of Things at W3C. (2017)[Image]. Retrieved March 16, 2018, from W3C:
https://www.w3.org/WoT/
Zhang, N., Chen, H., Chen, X., & Chen, J. (2016). Semantic Framework of Internet
of Things for Smart Cities: Case Studies. Sensors, 16(1501).
doi:10.3390/s16091501 (Q2)
Zhou, J., Cao, Z., Dong, X., & Vasilakos, A. V. (2017, Jan). Security and Privacy
for Cloud-Based IoT: Challenges, Countermeasures, and Future Directions.
IEEE Communications Magazine. doi:10.1109/MCOM.2017.1600363CM
(Q1)
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




