IoT in Healthcare: Implementation, Challenges, and Proposed Model
VerifiedAdded on 2023/06/14
|9
|7876
|124
Report
AI Summary
This report provides a comprehensive analysis of the Internet of Things (IoT) in the healthcare domain, focusing on current and previous implementations, challenges, and a proposed model for future development. It begins with an introduction to IoT and its applications in healthcare, particularly remote health monitoring and emergency notifications. The report identifies key problems such as the lack of electronic health record integration, security threats, multiple device integration issues, inferring results from immense data, constant changes in hardware and connectivity, and interoperability challenges. It reviews current and previous methodologies, highlighting the slow evolution of medical instruments and the need for advancements in machine learning to handle heterogeneous sensory inputs. A literature review summarizes research on chronic disease monitoring, body movement analysis during sleep, and the use of artificial intelligence in healthcare. The report concludes by proposing a model for further development, emphasizing the importance of leveraging clinical records for machine learning training and addressing the challenges of big data in healthcare. Desklib offers this and many other solved assignments to aid students in their studies.

IoT IN HEALTH CARE DOMAIN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT – Internet of Things or Iot can be defined as the system of physical things which are associated or embedded
with a number of sensors, software’s, connectivity and electronics. This allows a better exchanging of information with other
devices which are connected to the network. Or in simple terms IoT can be defined as the network of physical devices which are
capable exchanging information. It is an emerging technology and has been applied in various fields. One such field is the
healthcare. IoT has greatly helped the process of providing medical care. This report consists of the current and previous
implementations of IoT in the field of healthcare. The report also consists of a literature review which shows the research work
of differ researchers in this fields. Lastly, the report proposes a model for further development. IoT or Internet of Things
generally refers to the ever growing network consisting of physical objects which featured with an IP address for connecting
with the internet. Along with this IoT also refers to the communication, which generally occurs between all this objects and
other devices or systems, which are internet enabled. IoT is used in various domains and one such domain is the healthcare
domain. This is used for various purposes in the healthcare domain like monitoring of health, notification during any kind of
medical emergency and many more.
1. INTRODUCTION (15 MARKS)
IoT is an emerging an emerging technology and has various
advantages as well as disadvantages. Various domains have
already started the use of IoT. One such domain is the
healthcare domain. IoT is generally used in healthcare domain
for monitoring the health remotely and provide notifications
whenever there is an emergency [9]. The IoT devices used in
healthcare for the purpose of monitoring the health might
range from simple devices like blood monitoring devices or
heart rate monitors to highly advanced monitoring devices
which are implanted like the pacemakers, Fitbit electronic
wrist bands or advanced hearing aids. However, along with
the advantages there are various challenges that are faced by
the IoT in the field of healthcare [1]. Healthcare is a complex
sector, there exists different stakeholders who are having
different objectives, and this structure differs in each country,
as there exists different government regulations different
countries [12]. IoT is still an unknown area and healthcare
sector is one of the complex sector having involvement of the
government. The current and the previous state of remote
health monitoring has been presented.
2. PROBLEMS FACED BY IOT
2.1 Lack of Electronic Health Care integration System
Data which are collected from the IoT devices maignt
include certain things like the vital sign’s of the patient,
physical activities or glucose level while the patien is present
at home and many more dose not travel typically to the
electronic health record system [3]. It has also been seen that
is most cases the data is not centralized and can be easily
availale for the providers, which is initially responsible for
limiting the information value as the adat is not presented to
the provider always in context to the clinics. Along with this
there exists certain electronic health recording systems where
the patient is allowed to import the data directly into their
record despite of this there still exists some limitations for few
of the dominant EHR players [7]. Initially, this leaves many of
the providers to remain uncertain about the way in which the
information (outside their record system) is to be handled.
2.2 Security threats
Security threats is a primary concern for the regulatory
bodies present at the healthcare industry. The concern mainly
includes the security of the privacy of the personal healthcare
information, which are stored and conveyed by making use of
the connected devices [2]. Many of the organizations
associated with the healthcare makes sure that the soring of
the sensitive data is done in a secure and encrypted manner.
Along with they are also not having any type of control over
the safety and the security for the data access points, which
are used for the purpose of transmission of the data. Initially
this acts as the significant threat, which increases gradually
depending on the number of devices, which gets connected
network [1].
2.3 Multiple device integration
Integration of multiple devices stands out to be an obstacle
in the path of success of IoT in healthcare. Most of the devices
that are present in the hospitals along with the health devices
need to be connected to the network for collecting data from
the patients [3]. The most prominent challenge that exists is
today’s world is that the manufactures of IoT devices for
healthcare have not agreed upon any set of protocols or
standards. Therefore, whenever multiple number of mobile
devices is connected to the network for collecting the data
then it becomes a very complicated process of grouping all the
information collected. This is because the mobile devices are
having different protocols [5]. Due to lack of homogeneity
between the medical devices or the IoT devices used for
medical process reduces the chances of success while
implementation of the IoT technology in healthcare domain.
2.4 Inferring results from immense data
Different and numerous types of complexities are attached
with the process of aggregation and collection of data. Despite
of the fact that combined results helps in deriving of new
conclusions by inferring the records of the patient, the results
which comes up can be very much challenging and might not
have been checked by any data expert or night not have
undergone any type of analytic program so as to get refined
[4]. Along with this, the identification of valuable as well as
actionable data is one of the critical factor and this is because
medical specialists and physicians find it very difficult to
reach the conclusion regarding the growth of the data. There is
lack of quality due to increased amount of data in the process
of decision-making [6]. Besides this, the concern is becoming
much bigger due to the involvement of new devices, which is
connected to the network that is associated with continuous
with a number of sensors, software’s, connectivity and electronics. This allows a better exchanging of information with other
devices which are connected to the network. Or in simple terms IoT can be defined as the network of physical devices which are
capable exchanging information. It is an emerging technology and has been applied in various fields. One such field is the
healthcare. IoT has greatly helped the process of providing medical care. This report consists of the current and previous
implementations of IoT in the field of healthcare. The report also consists of a literature review which shows the research work
of differ researchers in this fields. Lastly, the report proposes a model for further development. IoT or Internet of Things
generally refers to the ever growing network consisting of physical objects which featured with an IP address for connecting
with the internet. Along with this IoT also refers to the communication, which generally occurs between all this objects and
other devices or systems, which are internet enabled. IoT is used in various domains and one such domain is the healthcare
domain. This is used for various purposes in the healthcare domain like monitoring of health, notification during any kind of
medical emergency and many more.
1. INTRODUCTION (15 MARKS)
IoT is an emerging an emerging technology and has various
advantages as well as disadvantages. Various domains have
already started the use of IoT. One such domain is the
healthcare domain. IoT is generally used in healthcare domain
for monitoring the health remotely and provide notifications
whenever there is an emergency [9]. The IoT devices used in
healthcare for the purpose of monitoring the health might
range from simple devices like blood monitoring devices or
heart rate monitors to highly advanced monitoring devices
which are implanted like the pacemakers, Fitbit electronic
wrist bands or advanced hearing aids. However, along with
the advantages there are various challenges that are faced by
the IoT in the field of healthcare [1]. Healthcare is a complex
sector, there exists different stakeholders who are having
different objectives, and this structure differs in each country,
as there exists different government regulations different
countries [12]. IoT is still an unknown area and healthcare
sector is one of the complex sector having involvement of the
government. The current and the previous state of remote
health monitoring has been presented.
2. PROBLEMS FACED BY IOT
2.1 Lack of Electronic Health Care integration System
Data which are collected from the IoT devices maignt
include certain things like the vital sign’s of the patient,
physical activities or glucose level while the patien is present
at home and many more dose not travel typically to the
electronic health record system [3]. It has also been seen that
is most cases the data is not centralized and can be easily
availale for the providers, which is initially responsible for
limiting the information value as the adat is not presented to
the provider always in context to the clinics. Along with this
there exists certain electronic health recording systems where
the patient is allowed to import the data directly into their
record despite of this there still exists some limitations for few
of the dominant EHR players [7]. Initially, this leaves many of
the providers to remain uncertain about the way in which the
information (outside their record system) is to be handled.
2.2 Security threats
Security threats is a primary concern for the regulatory
bodies present at the healthcare industry. The concern mainly
includes the security of the privacy of the personal healthcare
information, which are stored and conveyed by making use of
the connected devices [2]. Many of the organizations
associated with the healthcare makes sure that the soring of
the sensitive data is done in a secure and encrypted manner.
Along with they are also not having any type of control over
the safety and the security for the data access points, which
are used for the purpose of transmission of the data. Initially
this acts as the significant threat, which increases gradually
depending on the number of devices, which gets connected
network [1].
2.3 Multiple device integration
Integration of multiple devices stands out to be an obstacle
in the path of success of IoT in healthcare. Most of the devices
that are present in the hospitals along with the health devices
need to be connected to the network for collecting data from
the patients [3]. The most prominent challenge that exists is
today’s world is that the manufactures of IoT devices for
healthcare have not agreed upon any set of protocols or
standards. Therefore, whenever multiple number of mobile
devices is connected to the network for collecting the data
then it becomes a very complicated process of grouping all the
information collected. This is because the mobile devices are
having different protocols [5]. Due to lack of homogeneity
between the medical devices or the IoT devices used for
medical process reduces the chances of success while
implementation of the IoT technology in healthcare domain.
2.4 Inferring results from immense data
Different and numerous types of complexities are attached
with the process of aggregation and collection of data. Despite
of the fact that combined results helps in deriving of new
conclusions by inferring the records of the patient, the results
which comes up can be very much challenging and might not
have been checked by any data expert or night not have
undergone any type of analytic program so as to get refined
[4]. Along with this, the identification of valuable as well as
actionable data is one of the critical factor and this is because
medical specialists and physicians find it very difficult to
reach the conclusion regarding the growth of the data. There is
lack of quality due to increased amount of data in the process
of decision-making [6]. Besides this, the concern is becoming
much bigger due to the involvement of new devices, which is
connected to the network that is associated with continuous
collection of the data along with the generation of big data as
well.
2.5 Constant changes in the Hardware and Connectivity
More than one device is required by the patients for the
collection of data that the provider needs. For this purpose,
there might exist a need of more than one sensors and in most
cases, it has been seen that this sensors is used along with a
hub where the data gets pushed [8]. These pubs are designed
for processing the information. It has also been seen that these
hubs are not compatible with the different types of sensors,
which are available, and lacks in common hardware or
wireless connectivity. This will initially lead the patients to
have an extensive hardware with them, which would be
overwhelming as well as costly.
2.6 Interoperability challenges
The patients prefer collection of different sets of data by
making use of different types of medical devices. The usage
of such medical devices depends on the purpose of each
device or according to the instructions of the physicians. In
many cases, it has been seen that the data, which is captured
by the IoT device, stays within the boundaries of each system
and the IoT vendors [8]. This collected information is not
visible to any other systems. However, it is unfortunate that
lack of wider adaptation of the adequate interoperability has
led to the lock down of the data from different IoT devices in
each individual system. This initially leads to the loss of
potential values for the rest of the team associated with
patients care. Current and previous methodologies
3. Current and previous methodologies
The evolution of the medical instruments is evolving at a
slow pace. There exists the need of regulatory approval as
well as training for the medical personnel so as to use to new
equipment’s and the measuring devices. This initially results
in limiting the rate of growth of the new innovations.
According to Moore’s law, the rate of development of the
electronic is growing at a much faster rate and is generally
dictated by the economic considerations. The wearable
sensors generally represents a much more dynamically
evolving set of measurements devices than the conventional
medical instruments. Along with the addition of new sensor
modules updated sensors and obsoleted ones a heterogeneous
mix is to be deployed at any point of time. There is a need of
further development in the machine learning process so as to
deal with the heterogeneous sensory inputs which are
continuously developing. There is also a need of coping up
with the streaming data data of varying dimensionality and
semantics as sensor designs change over time and inevitably
missing values of the data by the analytics which are done on
the data gathered from the wearable sensors. Operating in this
type of environment makes the learning task face significant
challenges despite of the advances made in this area along
with the emergence of big data applications. Big Data consists
of massive volumes of high-dimensional observations, which
are often available at the modes of streaming. The
development of sequential algorithms have taken place in both
domains that is in the primal and dual domains. This are
generally associated with targeting the online supporting
vector machines. This type of algorithms are not designed for
the purpose of dealing with various feature dimensionalities
which varies according to time, the incomplete vectors due to
the absence of the features or failure of the acquisition and in
case if this is not treated properly then it might lead to serious
impairment of the classified performance. It is possible to
input the missing values so as to cope up with the missing data
by making use of the linear or non-linear functions of the
features which are available. This is followed by proceeding
with the clairvoyant learning scheme which is based on the
full data.
Second of all as the data of the sensors are plentiful and
they are completely untagged. So there exists the need of
getting this data associated with the “ground truth
schematics”(diagnosis of the physician) so as to make them
usable in the process of training for machine learning
algorithms. However it is infeasible while requiting for the
additional inputs from the overloaded physicians. So the need
of new creative method arises which would be acting as an
alternative for this. One of the attractive possibility is the
ability to leverage the clinical records and this is becoming
readily accessible by the deployment of the Electronic Health
Record System.
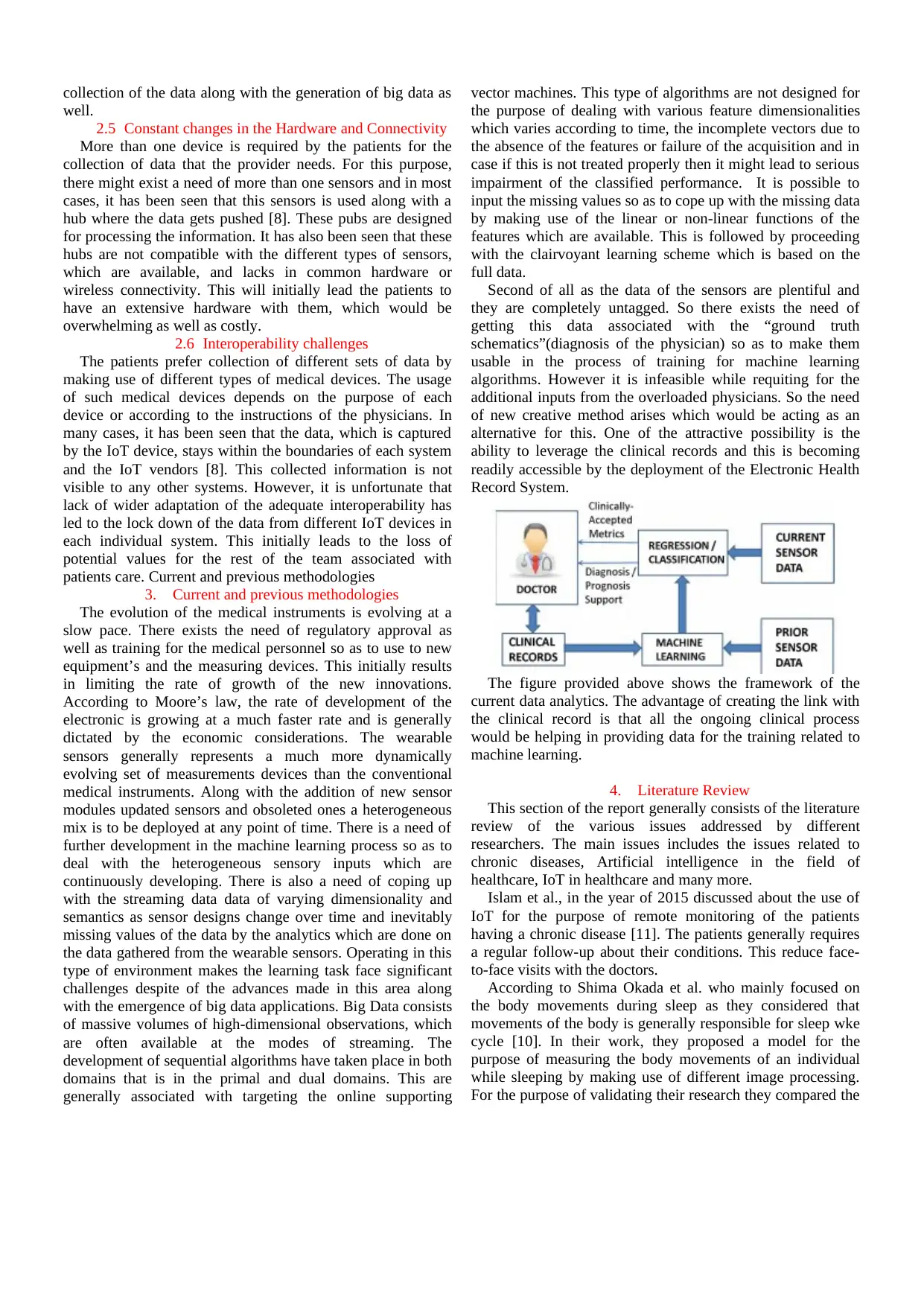
The figure provided above shows the framework of the
current data analytics. The advantage of creating the link with
the clinical record is that all the ongoing clinical process
would be helping in providing data for the training related to
machine learning.
4. Literature Review
This section of the report generally consists of the literature
review of the various issues addressed by different
researchers. The main issues includes the issues related to
chronic diseases, Artificial intelligence in the field of
healthcare, IoT in healthcare and many more.
Islam et al., in the year of 2015 discussed about the use of
IoT for the purpose of remote monitoring of the patients
having a chronic disease [11]. The patients generally requires
a regular follow-up about their conditions. This reduce face-
to-face visits with the doctors.
According to Shima Okada et al. who mainly focused on
the body movements during sleep as they considered that
movements of the body is generally responsible for sleep wke
cycle [10]. In their work, they proposed a model for the
purpose of measuring the body movements of an individual
while sleeping by making use of different image processing.
For the purpose of validating their research they compared the
well.
2.5 Constant changes in the Hardware and Connectivity
More than one device is required by the patients for the
collection of data that the provider needs. For this purpose,
there might exist a need of more than one sensors and in most
cases, it has been seen that this sensors is used along with a
hub where the data gets pushed [8]. These pubs are designed
for processing the information. It has also been seen that these
hubs are not compatible with the different types of sensors,
which are available, and lacks in common hardware or
wireless connectivity. This will initially lead the patients to
have an extensive hardware with them, which would be
overwhelming as well as costly.
2.6 Interoperability challenges
The patients prefer collection of different sets of data by
making use of different types of medical devices. The usage
of such medical devices depends on the purpose of each
device or according to the instructions of the physicians. In
many cases, it has been seen that the data, which is captured
by the IoT device, stays within the boundaries of each system
and the IoT vendors [8]. This collected information is not
visible to any other systems. However, it is unfortunate that
lack of wider adaptation of the adequate interoperability has
led to the lock down of the data from different IoT devices in
each individual system. This initially leads to the loss of
potential values for the rest of the team associated with
patients care. Current and previous methodologies
3. Current and previous methodologies
The evolution of the medical instruments is evolving at a
slow pace. There exists the need of regulatory approval as
well as training for the medical personnel so as to use to new
equipment’s and the measuring devices. This initially results
in limiting the rate of growth of the new innovations.
According to Moore’s law, the rate of development of the
electronic is growing at a much faster rate and is generally
dictated by the economic considerations. The wearable
sensors generally represents a much more dynamically
evolving set of measurements devices than the conventional
medical instruments. Along with the addition of new sensor
modules updated sensors and obsoleted ones a heterogeneous
mix is to be deployed at any point of time. There is a need of
further development in the machine learning process so as to
deal with the heterogeneous sensory inputs which are
continuously developing. There is also a need of coping up
with the streaming data data of varying dimensionality and
semantics as sensor designs change over time and inevitably
missing values of the data by the analytics which are done on
the data gathered from the wearable sensors. Operating in this
type of environment makes the learning task face significant
challenges despite of the advances made in this area along
with the emergence of big data applications. Big Data consists
of massive volumes of high-dimensional observations, which
are often available at the modes of streaming. The
development of sequential algorithms have taken place in both
domains that is in the primal and dual domains. This are
generally associated with targeting the online supporting
vector machines. This type of algorithms are not designed for
the purpose of dealing with various feature dimensionalities
which varies according to time, the incomplete vectors due to
the absence of the features or failure of the acquisition and in
case if this is not treated properly then it might lead to serious
impairment of the classified performance. It is possible to
input the missing values so as to cope up with the missing data
by making use of the linear or non-linear functions of the
features which are available. This is followed by proceeding
with the clairvoyant learning scheme which is based on the
full data.
Second of all as the data of the sensors are plentiful and
they are completely untagged. So there exists the need of
getting this data associated with the “ground truth
schematics”(diagnosis of the physician) so as to make them
usable in the process of training for machine learning
algorithms. However it is infeasible while requiting for the
additional inputs from the overloaded physicians. So the need
of new creative method arises which would be acting as an
alternative for this. One of the attractive possibility is the
ability to leverage the clinical records and this is becoming
readily accessible by the deployment of the Electronic Health
Record System.
The figure provided above shows the framework of the
current data analytics. The advantage of creating the link with
the clinical record is that all the ongoing clinical process
would be helping in providing data for the training related to
machine learning.
4. Literature Review
This section of the report generally consists of the literature
review of the various issues addressed by different
researchers. The main issues includes the issues related to
chronic diseases, Artificial intelligence in the field of
healthcare, IoT in healthcare and many more.
Islam et al., in the year of 2015 discussed about the use of
IoT for the purpose of remote monitoring of the patients
having a chronic disease [11]. The patients generally requires
a regular follow-up about their conditions. This reduce face-
to-face visits with the doctors.
According to Shima Okada et al. who mainly focused on
the body movements during sleep as they considered that
movements of the body is generally responsible for sleep wke
cycle [10]. In their work, they proposed a model for the
purpose of measuring the body movements of an individual
while sleeping by making use of different image processing.
For the purpose of validating their research they compared the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

different image processing’s with the sleep stages that were
measured by the PSG along with this they also made use of
video monitoring for the purpose of characterizing the
different body movements while sleeping in normal children’s
as well as in ADHD.
Tracy S, Barger et al., was associated with developing a
Smart-house venture which was customized so as to monitor
the different movements of an individual inside a house by
making use of various sensors [12]. The prototype for the
design they provided is under test so as to see the outputs. The
researchers have examined if the system is capable of
detecting the behavioral patterns of the individuals inside the
house and are discussing on the results of the work.
A novel “Brain-Computer Interface system” has been
presented by Darius Adam Rohani et al., which generally aims
at rehabilitation of the attention deficit hyperactive disorder in
the children’s [13]. This makes use of the P300 potential in a
series of feedback games for the purpose of improving the
attention of the subject. A “Support Vector Machine “has also
been applied by them by making use of the temporal and
template based on the various features so as to detect various
type of disorders.
Dong-Hwan Park and Hyo-Chan Bang conducted their
research which was mainly focused upon the fact that how
technology are responsible for contributing toward the
improvement of the Interpol ability between various IoT
devices as well as how to make the use of IoT device easy
[14]. “Semantic-based IoT information services” and
“semantic interoperability of IoT devices” is afforded by the
anticipated platform technology. Along with this the service
platform is also applicable for a lot of semantic IoT services
and this mainly includes collection of invisible information
present in the tangible environment by making use of various
smart devices. This initially results in providing a smart life
service by the process of sharing, distributing the open sensing
information and many more.
The researchers named Chayan Sarkar and Akshay Uttama
Nambi for various IoT devices presented a unified schematic
knowledge base, which is associated with making use of the
ontology as the building blocks [15]. Most of the ontologies
are for the IoT mainly focuses on the available resources,
services as well as on the information of the location. Both
this researchers were associated with building upon the
existing state-of-ontology as as to provide knowledge
regarding the contextual information’s as well as on the set of
policies so as to execute the various services. Several
ontologies are contained in the Knowledge and this mainly
includes the resources, location, policies, ontology of the
service and context and domain.
Sai Kiran P. et al., were associated with providing an
proposal for the system responsible remote monitoring of the
health. This system consisted of a composed medical data,
which was gathered form, the biomedical sensors and after
this, the data was conveyed to the adjacent gateway for the
processing related to auxiliary [16]. Subsidizing of the
transmitted data takes place up to a substantial amount of the
depleted power. The transmitters and the upsurges that takes
place in the network traffic are responsible for this. This
metrics are responsible for discarding of the analysis of
performance, which helps in saving of power, reduces the
network traffic up to a certain extent. The rule engine
proposed by these researchers contributed a lot in substantial
reduction in the consumption of energy and the generated
network traffic.
A general framework was framed by Iuliana Chiuchisan et
al., for the healthcare system so as to monitor the different
type of threats that existed in the smart intensive care units
[17]. The system was associated with providing counseling
and providing of real time updates about the patients to the
medical assistants or to the doctors. The updates mainly
included the vigorous constraints or the movement of the
patients or some important changes that occurs in the
environment. This was done so as to take certain preventive
measures.
Other researchers like Boyi Xu et al., also proposed sematic
model so as to store and interpret the data in the IoT. This was
followed by the designing of the Data accessing method. This
was developed so as to acquire along with practicing the use
of use of IoT data at an universal basis. This was done so as to
improve the accessibility of the resources fr IoT data [9].
Lastly they also presented an IoT-based system for providing
services in cases of medical emergency and they also
demonstrated the way in which the collection, integration and
interoperation of the IoT data is to be done.
Numo Vasco Lopes et al proposed an IoT architecture for
the disabled persons and this anticipates in describing and
identifying the furthermost appropriate IoT technologies and
the international criterions, which would help in stacking of
the architecture proposed by them [18]. Particularly they
discussed about the empowering IoT technologies along with
the feasibility of the IoT devices for the peoples who are
disable. Lastly, they considered two use cases, which were
formerly being deployed for the peoples.
Various types of algorithms have been provided for the
purpose of providing authentication to the IoT devices. Yang,
Hao and Zhang (2013) in their study provided an enhanced
mutual authentication mosel for the IoT environment [22].
Along with this they also provided some improvements to the
algorithm for the authentication related to Challenge-response
based RFID authentication protocol. This was done for the
distributed database environment. Due to this reason the IoT
control system became much more suitable. Their approach
mainly included three major steps and this includes the adding
of backup for each terminal device which has been used for
controlling, addition of monitoring device in order to take a
follow up and monitor the terminal device and lastly the
adding of push in the alarm mechanism in order to get alarm
for any kind of authentication process [23].
Porambage et al. (2014) in their study proposed a Tw0-
Phase Authentication Protocol for the Wireless sensor
network in distributed IoT applications. This approach can be
considered as a certificate based authentication approach [24].
Along with this the two phase authentication is also associated
with allowing both of the IoT devices and the control stations
measured by the PSG along with this they also made use of
video monitoring for the purpose of characterizing the
different body movements while sleeping in normal children’s
as well as in ADHD.
Tracy S, Barger et al., was associated with developing a
Smart-house venture which was customized so as to monitor
the different movements of an individual inside a house by
making use of various sensors [12]. The prototype for the
design they provided is under test so as to see the outputs. The
researchers have examined if the system is capable of
detecting the behavioral patterns of the individuals inside the
house and are discussing on the results of the work.
A novel “Brain-Computer Interface system” has been
presented by Darius Adam Rohani et al., which generally aims
at rehabilitation of the attention deficit hyperactive disorder in
the children’s [13]. This makes use of the P300 potential in a
series of feedback games for the purpose of improving the
attention of the subject. A “Support Vector Machine “has also
been applied by them by making use of the temporal and
template based on the various features so as to detect various
type of disorders.
Dong-Hwan Park and Hyo-Chan Bang conducted their
research which was mainly focused upon the fact that how
technology are responsible for contributing toward the
improvement of the Interpol ability between various IoT
devices as well as how to make the use of IoT device easy
[14]. “Semantic-based IoT information services” and
“semantic interoperability of IoT devices” is afforded by the
anticipated platform technology. Along with this the service
platform is also applicable for a lot of semantic IoT services
and this mainly includes collection of invisible information
present in the tangible environment by making use of various
smart devices. This initially results in providing a smart life
service by the process of sharing, distributing the open sensing
information and many more.
The researchers named Chayan Sarkar and Akshay Uttama
Nambi for various IoT devices presented a unified schematic
knowledge base, which is associated with making use of the
ontology as the building blocks [15]. Most of the ontologies
are for the IoT mainly focuses on the available resources,
services as well as on the information of the location. Both
this researchers were associated with building upon the
existing state-of-ontology as as to provide knowledge
regarding the contextual information’s as well as on the set of
policies so as to execute the various services. Several
ontologies are contained in the Knowledge and this mainly
includes the resources, location, policies, ontology of the
service and context and domain.
Sai Kiran P. et al., were associated with providing an
proposal for the system responsible remote monitoring of the
health. This system consisted of a composed medical data,
which was gathered form, the biomedical sensors and after
this, the data was conveyed to the adjacent gateway for the
processing related to auxiliary [16]. Subsidizing of the
transmitted data takes place up to a substantial amount of the
depleted power. The transmitters and the upsurges that takes
place in the network traffic are responsible for this. This
metrics are responsible for discarding of the analysis of
performance, which helps in saving of power, reduces the
network traffic up to a certain extent. The rule engine
proposed by these researchers contributed a lot in substantial
reduction in the consumption of energy and the generated
network traffic.
A general framework was framed by Iuliana Chiuchisan et
al., for the healthcare system so as to monitor the different
type of threats that existed in the smart intensive care units
[17]. The system was associated with providing counseling
and providing of real time updates about the patients to the
medical assistants or to the doctors. The updates mainly
included the vigorous constraints or the movement of the
patients or some important changes that occurs in the
environment. This was done so as to take certain preventive
measures.
Other researchers like Boyi Xu et al., also proposed sematic
model so as to store and interpret the data in the IoT. This was
followed by the designing of the Data accessing method. This
was developed so as to acquire along with practicing the use
of use of IoT data at an universal basis. This was done so as to
improve the accessibility of the resources fr IoT data [9].
Lastly they also presented an IoT-based system for providing
services in cases of medical emergency and they also
demonstrated the way in which the collection, integration and
interoperation of the IoT data is to be done.
Numo Vasco Lopes et al proposed an IoT architecture for
the disabled persons and this anticipates in describing and
identifying the furthermost appropriate IoT technologies and
the international criterions, which would help in stacking of
the architecture proposed by them [18]. Particularly they
discussed about the empowering IoT technologies along with
the feasibility of the IoT devices for the peoples who are
disable. Lastly, they considered two use cases, which were
formerly being deployed for the peoples.
Various types of algorithms have been provided for the
purpose of providing authentication to the IoT devices. Yang,
Hao and Zhang (2013) in their study provided an enhanced
mutual authentication mosel for the IoT environment [22].
Along with this they also provided some improvements to the
algorithm for the authentication related to Challenge-response
based RFID authentication protocol. This was done for the
distributed database environment. Due to this reason the IoT
control system became much more suitable. Their approach
mainly included three major steps and this includes the adding
of backup for each terminal device which has been used for
controlling, addition of monitoring device in order to take a
follow up and monitor the terminal device and lastly the
adding of push in the alarm mechanism in order to get alarm
for any kind of authentication process [23].
Porambage et al. (2014) in their study proposed a Tw0-
Phase Authentication Protocol for the Wireless sensor
network in distributed IoT applications. This approach can be
considered as a certificate based authentication approach [24].
Along with this the two phase authentication is also associated
with allowing both of the IoT devices and the control stations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

in order to authenticate and recognize each other. This would
lead to an establishment of a secure connection and the
transferring of the data would be done in a secure way.
Besides this they also made use of the protocol support
resource limitation of the sensor nodes ad also considered the
network stability as well as the heterogeneity. For issuing the
certificates the Certificate Association was used. This made
the existing nodes capable of moving and changing their
location once they get their own certificates. The CA is also
associated with validating the identity of the sensors along
with favoring the communication between different entities
present in the network. The network members firstly connect
with the CA in order to confirm their destination identity this
would help them in initializing a connection. Due to all this
reasons it is considered that the approach is an end-to-end
application layer authentication approach and also depend on
the security features of the other lower layers.
Kalra and Sood (2015) in their study provided a scheme for
secure authentication for the IoT devices and the cloud
servers. This schema was mainly dependent on the Elliptical
Curve Cryptography (ECC) based algorithm [25]. This is
associated with supporting a better security solution as
compared to the other Public Key Cryptography (PKC)
algorithms. This is mainly due to the small size of the keys
[26]. The authentication protocol is associated with using the
EEC for the devices which are embedded to it and makes use
of the HTTP protocol. It is a novel approach to use the
cookies present in the HTTP. There is a need of configuring
this device with the TCP/IP. The authentication protocol
which has been proposed is designed for uing the cookies in
the HTTP which are then implemented in order to fit the
embedded devices which are having a constrained
environment and is mainly controlled by the cloud servers.
There exists three major phases in the propsed protocol and
this includes the registration phase, pre-computed phase and
the login phase. The embedded devices register themselves in
the registration phase with the various cloud servers. This is
followed by sending of cookies and these cookies are stored in
the embedded devices. The pre-computation and the login
phase is associated with sending of request regarding the login
request and it is to be done before connecting to the server.
And lastly in the authentication phase the embedded devices
as well as the cloud servers are associated with mutually
authenticating each other by making use of the EEC
algorithm. However, the size of the encrypted message is
increased significantly despite of having a small encryption
key [27]. The EEC is much more complex and faces a lot of
difficulty while implementing than the other cryptographic
algorithms and also requires a lot of resources for processing.
Mahalle, Prasad, and Prasad (2014) in their study proposed
the Threshold Cryptography based Group authentication
scheme for the IoT devices. This model is associated with
providing an authenticity for all the IoT devices which are
based upon the group communication model [28]. This TCGA
is also designed for the purpose of implementing this in the
Wi-Fi environment. A secret channel or a session is created
for authenticating each group. This can also be used for the
purpose of group applications as well. There exists a group
head for each group and is responsible fo generation of the
keys and distribution of this keys whenever a new member is
added to the group. This is done in order to preserve the
leakage of the group key and this head of the group is often
referred to as the authority of the group. There are five major
models in the proposed algorithm and this includes the
distribution of keys, updating of the keys, generation of the
group credits, listener of the authentication and lastly the
decryption of the messages.
Moosavi et al (2015) proposed the SEA or the Secure and
Efficient Authentication and Authorization Architecture for
the IoT based healthcare by making use of the Smart
Gateways [29]. This architecture was dependent on the credit
based DTLS handshake protocol. The following things are
included in the architecture: Medical sensor network which is
responsible for the collection of the information from a
patient’s body or rooms in order to help them in getting proper
treatment and medical diagnosis. The second one involves the
components present in the Smart e-Health gateways and this
are responsible for enabling the various types of system
communication which would be acting as the intermediate for
the MSN and the internet. And lastly it includes the bank-end
system which is associated with receiving, processing and
storing the collected information.
Jan et al. (2014) proposed a lightweight mutual
authentication schema which is associated with validating the
identity of the IoT devices which generally takes part in the
network [30]. Along with this they also proposed a decreased
communication overhead as well. CoAP or the Constrained
Application Protocol has been chosen as a under layer
protocol in order to establish communication between various
IoT devices. The authentication has been completed by
making use of the 128 bit Advanced Encryption Standard or
the AES. Firstly the identification of the identity of the clients
and server is done. Which is followed by providing of various
types of resources to the clients which are generally based
upon the specific conditions which are determined according
to the request. The conditional specific data transmission is
associated with minimizing the transmitted packets number
which ultimately results in the reduction of the energy
consumed and computation. The utilization of the bandwidth
in the communication is also decreased as well.
Mietz, Abraham and Römer (2104) in their study provided
a new CoAP option [31]. The CoAP which is associated with
working in the application layer generally provides the ability
in order to retrieve the data from the devices and this might
include the metadata or the measurements of the sensors. This
information is also used by the real-time applications. Despite
of this it has been seen that sometimes the information is not a
security requirement to not retrieve raw communication data.
But only the abstractions, mainly includes the high level state
of the observed entities. Additionally, the nature of the
resource constrained device can also be access by anyone on
the internet, reduction mechanism for the consumption of the
energy also plays a very important role. The mechanism
which has been proposed has greatly helped in meeting the
lead to an establishment of a secure connection and the
transferring of the data would be done in a secure way.
Besides this they also made use of the protocol support
resource limitation of the sensor nodes ad also considered the
network stability as well as the heterogeneity. For issuing the
certificates the Certificate Association was used. This made
the existing nodes capable of moving and changing their
location once they get their own certificates. The CA is also
associated with validating the identity of the sensors along
with favoring the communication between different entities
present in the network. The network members firstly connect
with the CA in order to confirm their destination identity this
would help them in initializing a connection. Due to all this
reasons it is considered that the approach is an end-to-end
application layer authentication approach and also depend on
the security features of the other lower layers.
Kalra and Sood (2015) in their study provided a scheme for
secure authentication for the IoT devices and the cloud
servers. This schema was mainly dependent on the Elliptical
Curve Cryptography (ECC) based algorithm [25]. This is
associated with supporting a better security solution as
compared to the other Public Key Cryptography (PKC)
algorithms. This is mainly due to the small size of the keys
[26]. The authentication protocol is associated with using the
EEC for the devices which are embedded to it and makes use
of the HTTP protocol. It is a novel approach to use the
cookies present in the HTTP. There is a need of configuring
this device with the TCP/IP. The authentication protocol
which has been proposed is designed for uing the cookies in
the HTTP which are then implemented in order to fit the
embedded devices which are having a constrained
environment and is mainly controlled by the cloud servers.
There exists three major phases in the propsed protocol and
this includes the registration phase, pre-computed phase and
the login phase. The embedded devices register themselves in
the registration phase with the various cloud servers. This is
followed by sending of cookies and these cookies are stored in
the embedded devices. The pre-computation and the login
phase is associated with sending of request regarding the login
request and it is to be done before connecting to the server.
And lastly in the authentication phase the embedded devices
as well as the cloud servers are associated with mutually
authenticating each other by making use of the EEC
algorithm. However, the size of the encrypted message is
increased significantly despite of having a small encryption
key [27]. The EEC is much more complex and faces a lot of
difficulty while implementing than the other cryptographic
algorithms and also requires a lot of resources for processing.
Mahalle, Prasad, and Prasad (2014) in their study proposed
the Threshold Cryptography based Group authentication
scheme for the IoT devices. This model is associated with
providing an authenticity for all the IoT devices which are
based upon the group communication model [28]. This TCGA
is also designed for the purpose of implementing this in the
Wi-Fi environment. A secret channel or a session is created
for authenticating each group. This can also be used for the
purpose of group applications as well. There exists a group
head for each group and is responsible fo generation of the
keys and distribution of this keys whenever a new member is
added to the group. This is done in order to preserve the
leakage of the group key and this head of the group is often
referred to as the authority of the group. There are five major
models in the proposed algorithm and this includes the
distribution of keys, updating of the keys, generation of the
group credits, listener of the authentication and lastly the
decryption of the messages.
Moosavi et al (2015) proposed the SEA or the Secure and
Efficient Authentication and Authorization Architecture for
the IoT based healthcare by making use of the Smart
Gateways [29]. This architecture was dependent on the credit
based DTLS handshake protocol. The following things are
included in the architecture: Medical sensor network which is
responsible for the collection of the information from a
patient’s body or rooms in order to help them in getting proper
treatment and medical diagnosis. The second one involves the
components present in the Smart e-Health gateways and this
are responsible for enabling the various types of system
communication which would be acting as the intermediate for
the MSN and the internet. And lastly it includes the bank-end
system which is associated with receiving, processing and
storing the collected information.
Jan et al. (2014) proposed a lightweight mutual
authentication schema which is associated with validating the
identity of the IoT devices which generally takes part in the
network [30]. Along with this they also proposed a decreased
communication overhead as well. CoAP or the Constrained
Application Protocol has been chosen as a under layer
protocol in order to establish communication between various
IoT devices. The authentication has been completed by
making use of the 128 bit Advanced Encryption Standard or
the AES. Firstly the identification of the identity of the clients
and server is done. Which is followed by providing of various
types of resources to the clients which are generally based
upon the specific conditions which are determined according
to the request. The conditional specific data transmission is
associated with minimizing the transmitted packets number
which ultimately results in the reduction of the energy
consumed and computation. The utilization of the bandwidth
in the communication is also decreased as well.
Mietz, Abraham and Römer (2104) in their study provided
a new CoAP option [31]. The CoAP which is associated with
working in the application layer generally provides the ability
in order to retrieve the data from the devices and this might
include the metadata or the measurements of the sensors. This
information is also used by the real-time applications. Despite
of this it has been seen that sometimes the information is not a
security requirement to not retrieve raw communication data.
But only the abstractions, mainly includes the high level state
of the observed entities. Additionally, the nature of the
resource constrained device can also be access by anyone on
the internet, reduction mechanism for the consumption of the
energy also plays a very important role. The mechanism
which has been proposed has greatly helped in meeting the
two major requirements and this results in a creation of a
high-level state of the readings from the raw sensors. The
proposed option has also helped in the reduction of the
number of messages while observing the resources of the
sensor. This would ultimately result in the reduction of energy
consumption and would also be increasing the lifetime of the
devices.
5. Proposed Methodology
The figure provided below helps in understanding how it is
possible to infer with the information as the knowledge
regarding the chronic disorders from the wearable health care
devices. The tier 1 shows the raw and unrefined data can be
acquired from the wearable smart IoT devices and this devices
consists of sensors like the “ECG Sensor, accelerometer and a
skin temperature sensor and many more. The tier 2 section
consists of the section where the information is inferred from
the data by means of filtering, processing, categorizing,
condensing and contextualizing the data. Elimination of the
irrelevant and reductant information is also done in this stage.
The tier 3 section of this figure shows the analysis or
prediction phase. There is a need of designing algorithms so
as to predicting the purpose of the chronic disease. This would
be done by application of various mining techniques like the
Constraint based mining, periodic pattern mining. Once the
data has been gathered some valid conclusion is reached
which would help in making of decisions and catalogues
which would include situations of the patient in Ideal, Normal,
With Symptoms in real time basis. So as to reach a specified
objective knowledge is inferred by various organizations and
structuring information’s and is ultimately put into action.
6. Proposed authentication Mechanism
Prevention of the resource exhausting in the IoT
environment is one of the major concern of the various
developing approaches. The restrictions in the resources of the
IoT environment requires various authentication mechanism
which are fitted to the limited amount of memory, processing
and the energy of the IoT devices. This mechanism would be
using the CoAP and ECC [32]. CoAP has been designed IETF
working group of the CoRE or the Constrained Restful
Environment. Main goal of the CoRE includes the providing
of the efficient architecture for the network nodes which are
highly constrained. CoAP is associated with providing these
constrained nodes in order to implement the transfer of web
and this can be used for the purpose of IoT communication
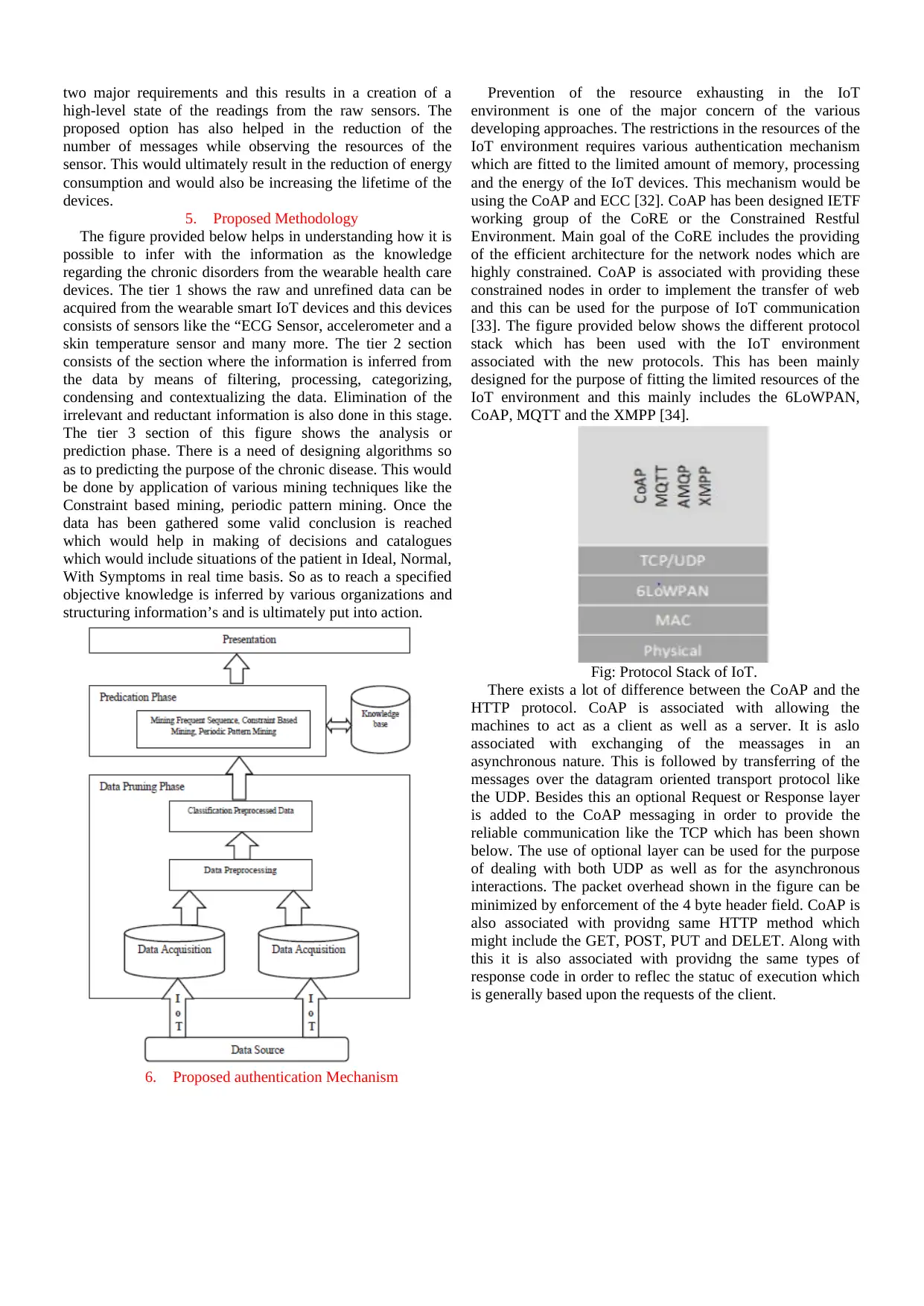
[33]. The figure provided below shows the different protocol
stack which has been used with the IoT environment
associated with the new protocols. This has been mainly
designed for the purpose of fitting the limited resources of the
IoT environment and this mainly includes the 6LoWPAN,
CoAP, MQTT and the XMPP [34].
Fig: Protocol Stack of IoT.
There exists a lot of difference between the CoAP and the
HTTP protocol. CoAP is associated with allowing the
machines to act as a client as well as a server. It is aslo
associated with exchanging of the meassages in an
asynchronous nature. This is followed by transferring of the
messages over the datagram oriented transport protocol like
the UDP. Besides this an optional Request or Response layer
is added to the CoAP messaging in order to provide the
reliable communication like the TCP which has been shown
below. The use of optional layer can be used for the purpose
of dealing with both UDP as well as for the asynchronous
interactions. The packet overhead shown in the figure can be
minimized by enforcement of the 4 byte header field. CoAP is
also associated with providng same HTTP method which
might include the GET, POST, PUT and DELET. Along with
this it is also associated with providng the same types of
response code in order to reflec the statuc of execution which
is generally based upon the requests of the client.
high-level state of the readings from the raw sensors. The
proposed option has also helped in the reduction of the
number of messages while observing the resources of the
sensor. This would ultimately result in the reduction of energy
consumption and would also be increasing the lifetime of the
devices.
5. Proposed Methodology
The figure provided below helps in understanding how it is
possible to infer with the information as the knowledge
regarding the chronic disorders from the wearable health care
devices. The tier 1 shows the raw and unrefined data can be
acquired from the wearable smart IoT devices and this devices
consists of sensors like the “ECG Sensor, accelerometer and a
skin temperature sensor and many more. The tier 2 section
consists of the section where the information is inferred from
the data by means of filtering, processing, categorizing,
condensing and contextualizing the data. Elimination of the
irrelevant and reductant information is also done in this stage.
The tier 3 section of this figure shows the analysis or
prediction phase. There is a need of designing algorithms so
as to predicting the purpose of the chronic disease. This would
be done by application of various mining techniques like the
Constraint based mining, periodic pattern mining. Once the
data has been gathered some valid conclusion is reached
which would help in making of decisions and catalogues
which would include situations of the patient in Ideal, Normal,
With Symptoms in real time basis. So as to reach a specified
objective knowledge is inferred by various organizations and
structuring information’s and is ultimately put into action.
6. Proposed authentication Mechanism
Prevention of the resource exhausting in the IoT
environment is one of the major concern of the various
developing approaches. The restrictions in the resources of the
IoT environment requires various authentication mechanism
which are fitted to the limited amount of memory, processing
and the energy of the IoT devices. This mechanism would be
using the CoAP and ECC [32]. CoAP has been designed IETF
working group of the CoRE or the Constrained Restful
Environment. Main goal of the CoRE includes the providing
of the efficient architecture for the network nodes which are
highly constrained. CoAP is associated with providing these
constrained nodes in order to implement the transfer of web
and this can be used for the purpose of IoT communication
[33]. The figure provided below shows the different protocol
stack which has been used with the IoT environment
associated with the new protocols. This has been mainly
designed for the purpose of fitting the limited resources of the
IoT environment and this mainly includes the 6LoWPAN,
CoAP, MQTT and the XMPP [34].
Fig: Protocol Stack of IoT.
There exists a lot of difference between the CoAP and the
HTTP protocol. CoAP is associated with allowing the
machines to act as a client as well as a server. It is aslo
associated with exchanging of the meassages in an
asynchronous nature. This is followed by transferring of the
messages over the datagram oriented transport protocol like
the UDP. Besides this an optional Request or Response layer
is added to the CoAP messaging in order to provide the
reliable communication like the TCP which has been shown
below. The use of optional layer can be used for the purpose
of dealing with both UDP as well as for the asynchronous
interactions. The packet overhead shown in the figure can be
minimized by enforcement of the 4 byte header field. CoAP is
also associated with providng same HTTP method which
might include the GET, POST, PUT and DELET. Along with
this it is also associated with providng the same types of
response code in order to reflec the statuc of execution which
is generally based upon the requests of the client.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
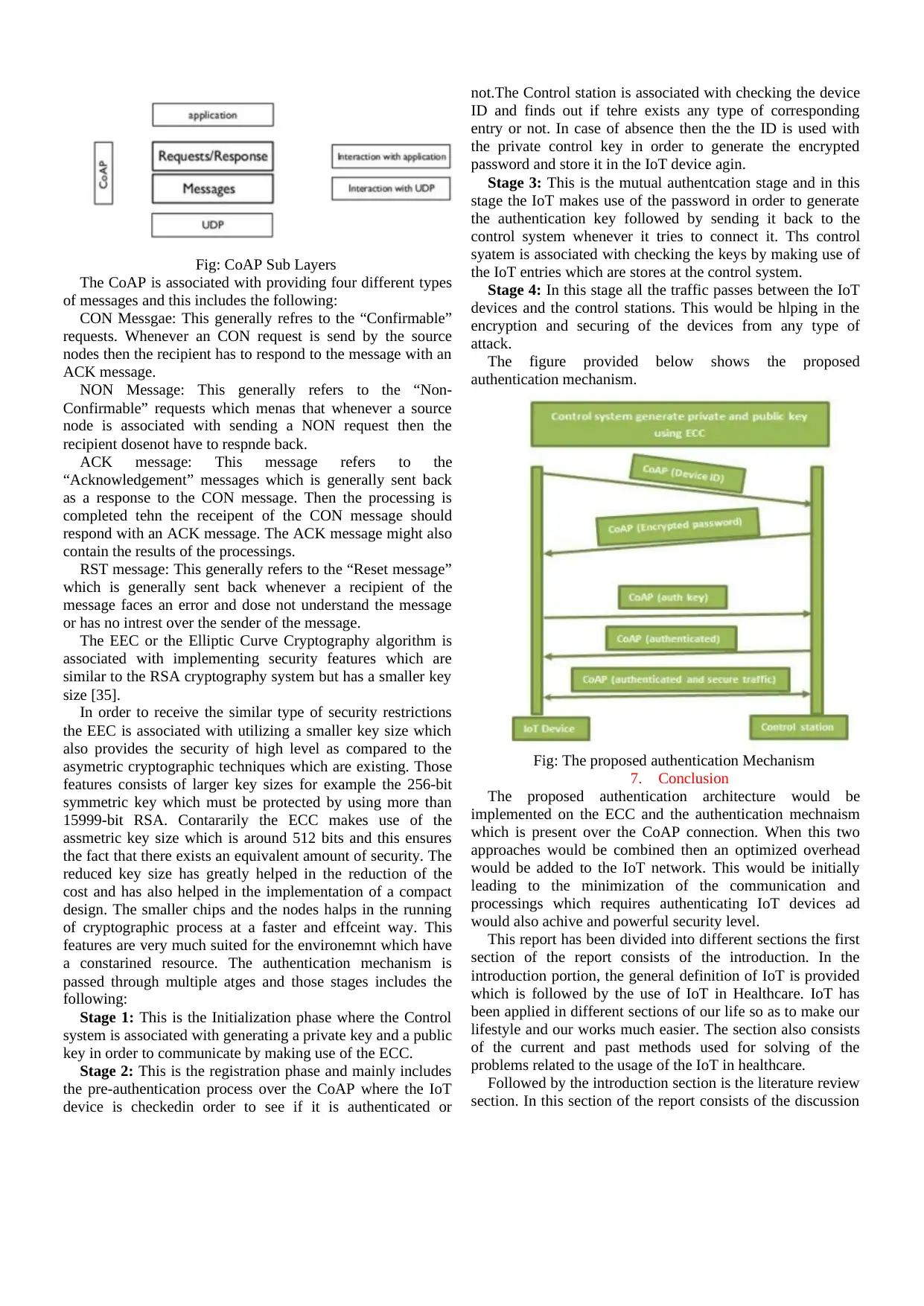
Fig: CoAP Sub Layers
The CoAP is associated with providing four different types
of messages and this includes the following:
CON Messgae: This generally refres to the “Confirmable”
requests. Whenever an CON request is send by the source
nodes then the recipient has to respond to the message with an
ACK message.
NON Message: This generally refers to the “Non-
Confirmable” requests which menas that whenever a source
node is associated with sending a NON request then the
recipient dosenot have to respnde back.
ACK message: This message refers to the
“Acknowledgement” messages which is generally sent back
as a response to the CON message. Then the processing is
completed tehn the receipent of the CON message should
respond with an ACK message. The ACK message might also
contain the results of the processings.
RST message: This generally refers to the “Reset message”
which is generally sent back whenever a recipient of the
message faces an error and dose not understand the message
or has no intrest over the sender of the message.
The EEC or the Elliptic Curve Cryptography algorithm is
associated with implementing security features which are
similar to the RSA cryptography system but has a smaller key
size [35].
In order to receive the similar type of security restrictions
the EEC is associated with utilizing a smaller key size which
also provides the security of high level as compared to the
asymetric cryptographic techniques which are existing. Those
features consists of larger key sizes for example the 256-bit
symmetric key which must be protected by using more than
15999-bit RSA. Contararily the ECC makes use of the
assmetric key size which is around 512 bits and this ensures
the fact that there exists an equivalent amount of security. The
reduced key size has greatly helped in the reduction of the
cost and has also helped in the implementation of a compact
design. The smaller chips and the nodes halps in the running
of cryptographic process at a faster and effceint way. This
features are very much suited for the environemnt which have
a constarined resource. The authentication mechanism is
passed through multiple atges and those stages includes the
following:
Stage 1: This is the Initialization phase where the Control
system is associated with generating a private key and a public
key in order to communicate by making use of the ECC.
Stage 2: This is the registration phase and mainly includes
the pre-authentication process over the CoAP where the IoT
device is checkedin order to see if it is authenticated or
not.The Control station is associated with checking the device
ID and finds out if tehre exists any type of corresponding
entry or not. In case of absence then the the ID is used with
the private control key in order to generate the encrypted
password and store it in the IoT device agin.
Stage 3: This is the mutual authentcation stage and in this
stage the IoT makes use of the password in order to generate
the authentication key followed by sending it back to the
control system whenever it tries to connect it. Ths control
syatem is associated with checking the keys by making use of
the IoT entries which are stores at the control system.
Stage 4: In this stage all the traffic passes between the IoT
devices and the control stations. This would be hlping in the
encryption and securing of the devices from any type of
attack.
The figure provided below shows the proposed
authentication mechanism.
Fig: The proposed authentication Mechanism
7. Conclusion
The proposed authentication architecture would be
implemented on the ECC and the authentication mechnaism
which is present over the CoAP connection. When this two
approaches would be combined then an optimized overhead
would be added to the IoT network. This would be initially
leading to the minimization of the communication and
processings which requires authenticating IoT devices ad
would also achive and powerful security level.
This report has been divided into different sections the first
section of the report consists of the introduction. In the
introduction portion, the general definition of IoT is provided
which is followed by the use of IoT in Healthcare. IoT has
been applied in different sections of our life so as to make our
lifestyle and our works much easier. The section also consists
of the current and past methods used for solving of the
problems related to the usage of the IoT in healthcare.
Followed by the introduction section is the literature review
section. In this section of the report consists of the discussion
The CoAP is associated with providing four different types
of messages and this includes the following:
CON Messgae: This generally refres to the “Confirmable”
requests. Whenever an CON request is send by the source
nodes then the recipient has to respond to the message with an
ACK message.
NON Message: This generally refers to the “Non-
Confirmable” requests which menas that whenever a source
node is associated with sending a NON request then the
recipient dosenot have to respnde back.
ACK message: This message refers to the
“Acknowledgement” messages which is generally sent back
as a response to the CON message. Then the processing is
completed tehn the receipent of the CON message should
respond with an ACK message. The ACK message might also
contain the results of the processings.
RST message: This generally refers to the “Reset message”
which is generally sent back whenever a recipient of the
message faces an error and dose not understand the message
or has no intrest over the sender of the message.
The EEC or the Elliptic Curve Cryptography algorithm is
associated with implementing security features which are
similar to the RSA cryptography system but has a smaller key
size [35].
In order to receive the similar type of security restrictions
the EEC is associated with utilizing a smaller key size which
also provides the security of high level as compared to the
asymetric cryptographic techniques which are existing. Those
features consists of larger key sizes for example the 256-bit
symmetric key which must be protected by using more than
15999-bit RSA. Contararily the ECC makes use of the
assmetric key size which is around 512 bits and this ensures
the fact that there exists an equivalent amount of security. The
reduced key size has greatly helped in the reduction of the
cost and has also helped in the implementation of a compact
design. The smaller chips and the nodes halps in the running
of cryptographic process at a faster and effceint way. This
features are very much suited for the environemnt which have
a constarined resource. The authentication mechanism is
passed through multiple atges and those stages includes the
following:
Stage 1: This is the Initialization phase where the Control
system is associated with generating a private key and a public
key in order to communicate by making use of the ECC.
Stage 2: This is the registration phase and mainly includes
the pre-authentication process over the CoAP where the IoT
device is checkedin order to see if it is authenticated or
not.The Control station is associated with checking the device
ID and finds out if tehre exists any type of corresponding
entry or not. In case of absence then the the ID is used with
the private control key in order to generate the encrypted
password and store it in the IoT device agin.
Stage 3: This is the mutual authentcation stage and in this
stage the IoT makes use of the password in order to generate
the authentication key followed by sending it back to the
control system whenever it tries to connect it. Ths control
syatem is associated with checking the keys by making use of
the IoT entries which are stores at the control system.
Stage 4: In this stage all the traffic passes between the IoT
devices and the control stations. This would be hlping in the
encryption and securing of the devices from any type of
attack.
The figure provided below shows the proposed
authentication mechanism.
Fig: The proposed authentication Mechanism
7. Conclusion
The proposed authentication architecture would be
implemented on the ECC and the authentication mechnaism
which is present over the CoAP connection. When this two
approaches would be combined then an optimized overhead
would be added to the IoT network. This would be initially
leading to the minimization of the communication and
processings which requires authenticating IoT devices ad
would also achive and powerful security level.
This report has been divided into different sections the first
section of the report consists of the introduction. In the
introduction portion, the general definition of IoT is provided
which is followed by the use of IoT in Healthcare. IoT has
been applied in different sections of our life so as to make our
lifestyle and our works much easier. The section also consists
of the current and past methods used for solving of the
problems related to the usage of the IoT in healthcare.
Followed by the introduction section is the literature review
section. In this section of the report consists of the discussion
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

about the various works done by different researchers by
application of the IoT in the field of healthcare.
Lastly, a methodology is proposed for the further research.
References:
[1] Fernandez, F., & Pallis, G. C. (2014, November). Opportunities and
challenges of the Internet of Things for healthcare: Systems engineering
perspective. In Wireless Mobile Communication and Healthcare
(Mobihealth), 2014 EAI 4th International Conference on (pp. 263-266).
IEEE.
[2] Bhatt, C., Dey, N., & Ashour, A. S. (Eds.). (2017). Internet of things and
big data technologies for next generation healthcare.
[3] Laplante, P. A., & Laplante, N. (2016). The internet of things in
healthcare: Potential applications and challenges. IT Professional, 18(3),
2-4.
[4] Moosavi, S. R., Gia, T. N., Rahmani, A. M., Nigussie, E., Virtanen, S.,
Isoaho, J., & Tenhunen, H. (2015). SEA: a secure and efficient
authentication and authorization architecture for IoT-based healthcare
using smart gateways. Procedia Computer Science, 52, 452-459.
[5] Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C., & Marrocco, G.
(2014). RFID technology for IoT-based personal healthcare in smart
spaces. IEEE Internet of things journal, 1(2), 144-152.
[6] Hassanalieragh, M., Page, A., Soyata, T., Sharma, G., Aktas, M.,
Mateos, G., ... & Andreescu, S. (2015, June). Health monitoring and
management using Internet-of-Things (IoT) sensing with cloud-based
processing: Opportunities and challenges. In Services Computing (SCC),
2015 IEEE International Conference on (pp. 285-292). IEEE.
[7] Xu, B., Da Xu, L., Cai, H., Xie, C., Hu, J., & Bu, F. (2014). Ubiquitous
data accessing method in IoT-based information system for emergency
medical services. IEEE Transactions on Industrial Informatics, 10(2),
1578-1586.
[8] Doukas, C., & Maglogiannis, I. (2012, July). Bringing IoT and cloud
computing towards pervasive healthcare. In Innovative Mobile and
Internet Services in Ubiquitous Computing (IMIS), 2012 Sixth
International Conference on (pp. 922-926). IEEE.
[9] Kulkarni, A., & Sathe, S. (2014). Healthcare applications of the Internet
of Things: A Review. International Journal of Computer Science and
Information Technologies, 5(5), 6229-6232.
[10] Okada, S., Shiozawa, N., & Makikawa, M. (2012, January). Body
movement in children with ADHD calculated using video images.
In Biomedical and Health Informatics (BHI), 2012 IEEE-EMBS
International Conference on (pp. 60-61). IEEE.
[11] Rohani, D. A., Sorensen, H. B., & Puthusserypady, S. (2014, August).
Brain-computer interface using P300 and virtual reality: A gaming
approach for treating ADHD. In Engineering in Medicine and Biology
Society (EMBC), 2014 36th Annual International Conference of the
IEEE (pp. 3606-3609). IEEE.
[12] Barger, T. S., Brown, D. E., & Alwan, M. (2005). Health-status
monitoring through analysis of behavioral patterns. IEEE Transactions
on systems, man, and cybernetics-part A: systems and humans, 35(1),
22-27.
[13] Liu, T., & Lu, D. (2012, August). The application and development of
IoT. In Information Technology in Medicine and Education (ITME),
2012 International Symposium on (Vol. 2, pp. 991-994). IEEE.
[14] Park, D. H., Bang, H. C., Pyo, C. S., & Kang, S. J. (2014, March).
Semantic open IoT service platform technology. In Internet of Things
(WF-IoT), 2014 IEEE World Forum on (pp. 85-88). IEEE.
[15] Sarkar, C., Nambi, S. A. U., Prasad, R. V., & Rahim, A. (2014, March).
A scalable distributed architecture towards unifying IoT applications.
In Internet of Things (WF-IoT), 2014 IEEE World Forum on (pp. 508-
513). IEEE.
[16] Kiran, M. S., Rajalakshmi, P., Bharadwaj, K., & Acharyya, A. (2014,
March). Adaptive rule engine based IoT enabled remote health care data
acquisition and smart transmission system. In Internet of Things (WF-
IoT), 2014 IEEE World Forum on (pp. 253-258). IEEE.
[17] Chiuchisan, I., Costin, H. N., & Geman, O. (2014, October). Adopting
the internet of things technologies in health care systems. In Electrical
and Power Engineering (EPE), 2014 International Conference and
Exposition on (pp. 532-535). IEEE.
[18] Xu, B., Da Xu, L., Cai, H., Xie, C., Hu, J., & Bu, F. (2014). Ubiquitous
data accessing method in IoT-based information system for emergency
medical services. IEEE Transactions on Industrial Informatics, 10(2),
1578-1586.
[19] Lopes, N. V., Pinto, F., Furtado, P., & Silva, J. (2014, October). IoT
architecture proposal for disabled people. In Wireless and Mobile
Computing, Networking and Communications (WiMob), 2014 IEEE
10th International Conference on (pp. 152-158). IEEE.
[20] Islam, S. R., Kwak, D., Kabir, M. H., Hossain, M., & Kwak, K. S.
(2015). The internet of things for health care: a comprehensive
survey. IEEE Access, 3, 678-708.
[21] Gope, P., & Hwang, T. (2016). BSN-Care: A secure IoT-based modern
healthcare system using body sensor network. IEEE Sensors
Journal, 16(5), 1368-1376.
[22] J.-c. YANG, P. Hao, and X. ZHANG, "Enhanced mutual authentication
model of IoT," The Journal of China Universities of Posts and
Telecommunications, vol. 20, pp. 69-74, 2013.
[23] Rhee, K., Kwak, J., Kim, S., & Won, D. (2005, April). Challenge-
response based RFID authentication protocol for distributed database
environment. In International Conference on Security in Pervasive
Computing (pp. 70-84). Springer, Berlin, Heidelberg.
[24] Porambage, P., Schmitt, C., Kumar, P., Gurtov, A., & Ylianttila, M.
(2014, April). Two-phase authentication protocol for wireless sensor
networks in distributed IoT applications. In Wireless Communications
and Networking Conference (WCNC), 2014 IEEE (pp. 2728-2733).
IEEE.
[25] Kalra, S., & Sood, S. K. (2015). Secure authentication scheme for IoT
and cloud servers. Pervasive and Mobile Computing, 24, 210-223.
[26] Batina, L., Guajardo, J., Kerins, T., Mentens, N., Tuyls, P., &
Verbauwhede, I. (2007, March). Public-key cryptography for RFID-
tags. In Pervasive Computing and Communications Workshops, 2007.
PerCom Workshops' 07. Fifth Annual IEEE International Conference on
(pp. 217-222). IEEE.
[27] Liu, J., Xiao, Y., & Chen, C. P. (2012, June). Authentication and access
control in the internet of things. In Distributed Computing Systems
Workshops (ICDCSW), 2012 32nd International Conference on (pp.
588-592). IEEE.
[28] Mahalle, P. N., Prasad, N. R., & Prasad, R. (2014, May). Threshold
cryptography-based group authentication (TCGA) scheme for the
internet of things (IoT). In Wireless Communications, Vehicular
Technology, Information Theory and Aerospace & Electronic Systems
(VITAE), 2014 4th International Conference on (pp. 1-5). IEEE.
[29] Moosavi, S. R., Gia, T. N., Rahmani, A. M., Nigussie, E., Virtanen, S.,
Isoaho, J., & Tenhunen, H. (2015). SEA: a secure and efficient
authentication and authorization architecture for IoT-based healthcare
using smart gateways. Procedia Computer Science, 52, 452-459.
[30] Jan, M. A., Nanda, P., He, X., Tan, Z., & Liu, R. P. (2014, September).
A robust authentication scheme for observing resources in the internet
of things environment. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference
on (pp. 205-211). IEEE.
[31] Mietz, R., Abraham, P., & Romer, K. (2014, April). High-level states
with CoAP: Giving meaning to raw sensor values to support IoT
applications. In Intelligent Sensors, Sensor Networks and Information
Processing (ISSNIP), 2014 IEEE Ninth International Conference on (pp.
1-6). IEEE.
[32] Shelby, Z., Hartke, K., & Bormann, C. (2014). The constrained
application protocol (CoAP).
[33] Kapoor, V., Abraham, V. S., & Singh, R. (2008). Elliptic curve
cryptography. Ubiquity, 2008(May), 7.
[34] Ismail, N. H. A., Hassan, R., & Ghazali, K. W. (2012). A study on
protocol stack in 6lowpan model. Journal of Theoretical and Applied
Information Technology, 41(2), 220-229.
application of the IoT in the field of healthcare.
Lastly, a methodology is proposed for the further research.
References:
[1] Fernandez, F., & Pallis, G. C. (2014, November). Opportunities and
challenges of the Internet of Things for healthcare: Systems engineering
perspective. In Wireless Mobile Communication and Healthcare
(Mobihealth), 2014 EAI 4th International Conference on (pp. 263-266).
IEEE.
[2] Bhatt, C., Dey, N., & Ashour, A. S. (Eds.). (2017). Internet of things and
big data technologies for next generation healthcare.
[3] Laplante, P. A., & Laplante, N. (2016). The internet of things in
healthcare: Potential applications and challenges. IT Professional, 18(3),
2-4.
[4] Moosavi, S. R., Gia, T. N., Rahmani, A. M., Nigussie, E., Virtanen, S.,
Isoaho, J., & Tenhunen, H. (2015). SEA: a secure and efficient
authentication and authorization architecture for IoT-based healthcare
using smart gateways. Procedia Computer Science, 52, 452-459.
[5] Amendola, S., Lodato, R., Manzari, S., Occhiuzzi, C., & Marrocco, G.
(2014). RFID technology for IoT-based personal healthcare in smart
spaces. IEEE Internet of things journal, 1(2), 144-152.
[6] Hassanalieragh, M., Page, A., Soyata, T., Sharma, G., Aktas, M.,
Mateos, G., ... & Andreescu, S. (2015, June). Health monitoring and
management using Internet-of-Things (IoT) sensing with cloud-based
processing: Opportunities and challenges. In Services Computing (SCC),
2015 IEEE International Conference on (pp. 285-292). IEEE.
[7] Xu, B., Da Xu, L., Cai, H., Xie, C., Hu, J., & Bu, F. (2014). Ubiquitous
data accessing method in IoT-based information system for emergency
medical services. IEEE Transactions on Industrial Informatics, 10(2),
1578-1586.
[8] Doukas, C., & Maglogiannis, I. (2012, July). Bringing IoT and cloud
computing towards pervasive healthcare. In Innovative Mobile and
Internet Services in Ubiquitous Computing (IMIS), 2012 Sixth
International Conference on (pp. 922-926). IEEE.
[9] Kulkarni, A., & Sathe, S. (2014). Healthcare applications of the Internet
of Things: A Review. International Journal of Computer Science and
Information Technologies, 5(5), 6229-6232.
[10] Okada, S., Shiozawa, N., & Makikawa, M. (2012, January). Body
movement in children with ADHD calculated using video images.
In Biomedical and Health Informatics (BHI), 2012 IEEE-EMBS
International Conference on (pp. 60-61). IEEE.
[11] Rohani, D. A., Sorensen, H. B., & Puthusserypady, S. (2014, August).
Brain-computer interface using P300 and virtual reality: A gaming
approach for treating ADHD. In Engineering in Medicine and Biology
Society (EMBC), 2014 36th Annual International Conference of the
IEEE (pp. 3606-3609). IEEE.
[12] Barger, T. S., Brown, D. E., & Alwan, M. (2005). Health-status
monitoring through analysis of behavioral patterns. IEEE Transactions
on systems, man, and cybernetics-part A: systems and humans, 35(1),
22-27.
[13] Liu, T., & Lu, D. (2012, August). The application and development of
IoT. In Information Technology in Medicine and Education (ITME),
2012 International Symposium on (Vol. 2, pp. 991-994). IEEE.
[14] Park, D. H., Bang, H. C., Pyo, C. S., & Kang, S. J. (2014, March).
Semantic open IoT service platform technology. In Internet of Things
(WF-IoT), 2014 IEEE World Forum on (pp. 85-88). IEEE.
[15] Sarkar, C., Nambi, S. A. U., Prasad, R. V., & Rahim, A. (2014, March).
A scalable distributed architecture towards unifying IoT applications.
In Internet of Things (WF-IoT), 2014 IEEE World Forum on (pp. 508-
513). IEEE.
[16] Kiran, M. S., Rajalakshmi, P., Bharadwaj, K., & Acharyya, A. (2014,
March). Adaptive rule engine based IoT enabled remote health care data
acquisition and smart transmission system. In Internet of Things (WF-
IoT), 2014 IEEE World Forum on (pp. 253-258). IEEE.
[17] Chiuchisan, I., Costin, H. N., & Geman, O. (2014, October). Adopting
the internet of things technologies in health care systems. In Electrical
and Power Engineering (EPE), 2014 International Conference and
Exposition on (pp. 532-535). IEEE.
[18] Xu, B., Da Xu, L., Cai, H., Xie, C., Hu, J., & Bu, F. (2014). Ubiquitous
data accessing method in IoT-based information system for emergency
medical services. IEEE Transactions on Industrial Informatics, 10(2),
1578-1586.
[19] Lopes, N. V., Pinto, F., Furtado, P., & Silva, J. (2014, October). IoT
architecture proposal for disabled people. In Wireless and Mobile
Computing, Networking and Communications (WiMob), 2014 IEEE
10th International Conference on (pp. 152-158). IEEE.
[20] Islam, S. R., Kwak, D., Kabir, M. H., Hossain, M., & Kwak, K. S.
(2015). The internet of things for health care: a comprehensive
survey. IEEE Access, 3, 678-708.
[21] Gope, P., & Hwang, T. (2016). BSN-Care: A secure IoT-based modern
healthcare system using body sensor network. IEEE Sensors
Journal, 16(5), 1368-1376.
[22] J.-c. YANG, P. Hao, and X. ZHANG, "Enhanced mutual authentication
model of IoT," The Journal of China Universities of Posts and
Telecommunications, vol. 20, pp. 69-74, 2013.
[23] Rhee, K., Kwak, J., Kim, S., & Won, D. (2005, April). Challenge-
response based RFID authentication protocol for distributed database
environment. In International Conference on Security in Pervasive
Computing (pp. 70-84). Springer, Berlin, Heidelberg.
[24] Porambage, P., Schmitt, C., Kumar, P., Gurtov, A., & Ylianttila, M.
(2014, April). Two-phase authentication protocol for wireless sensor
networks in distributed IoT applications. In Wireless Communications
and Networking Conference (WCNC), 2014 IEEE (pp. 2728-2733).
IEEE.
[25] Kalra, S., & Sood, S. K. (2015). Secure authentication scheme for IoT
and cloud servers. Pervasive and Mobile Computing, 24, 210-223.
[26] Batina, L., Guajardo, J., Kerins, T., Mentens, N., Tuyls, P., &
Verbauwhede, I. (2007, March). Public-key cryptography for RFID-
tags. In Pervasive Computing and Communications Workshops, 2007.
PerCom Workshops' 07. Fifth Annual IEEE International Conference on
(pp. 217-222). IEEE.
[27] Liu, J., Xiao, Y., & Chen, C. P. (2012, June). Authentication and access
control in the internet of things. In Distributed Computing Systems
Workshops (ICDCSW), 2012 32nd International Conference on (pp.
588-592). IEEE.
[28] Mahalle, P. N., Prasad, N. R., & Prasad, R. (2014, May). Threshold
cryptography-based group authentication (TCGA) scheme for the
internet of things (IoT). In Wireless Communications, Vehicular
Technology, Information Theory and Aerospace & Electronic Systems
(VITAE), 2014 4th International Conference on (pp. 1-5). IEEE.
[29] Moosavi, S. R., Gia, T. N., Rahmani, A. M., Nigussie, E., Virtanen, S.,
Isoaho, J., & Tenhunen, H. (2015). SEA: a secure and efficient
authentication and authorization architecture for IoT-based healthcare
using smart gateways. Procedia Computer Science, 52, 452-459.
[30] Jan, M. A., Nanda, P., He, X., Tan, Z., & Liu, R. P. (2014, September).
A robust authentication scheme for observing resources in the internet
of things environment. In Trust, Security and Privacy in Computing and
Communications (TrustCom), 2014 IEEE 13th International Conference
on (pp. 205-211). IEEE.
[31] Mietz, R., Abraham, P., & Romer, K. (2014, April). High-level states
with CoAP: Giving meaning to raw sensor values to support IoT
applications. In Intelligent Sensors, Sensor Networks and Information
Processing (ISSNIP), 2014 IEEE Ninth International Conference on (pp.
1-6). IEEE.
[32] Shelby, Z., Hartke, K., & Bormann, C. (2014). The constrained
application protocol (CoAP).
[33] Kapoor, V., Abraham, V. S., & Singh, R. (2008). Elliptic curve
cryptography. Ubiquity, 2008(May), 7.
[34] Ismail, N. H. A., Hassan, R., & Ghazali, K. W. (2012). A study on
protocol stack in 6lowpan model. Journal of Theoretical and Applied
Information Technology, 41(2), 220-229.

[35] Marzouqi, H., Al-Qutayri, M., & Salah, K. (2015). Review of elliptic
curve cryptography processor designs. Microprocessors and
Microsystems, 39(2), 97-112.
curve cryptography processor designs. Microprocessors and
Microsystems, 39(2), 97-112.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




