NIT5140 Information Security Assignment: IoT Security Case Analysis
VerifiedAdded on 2023/06/11
|2
|1166
|378
Case Study
AI Summary
This case study delves into the security vulnerabilities within the Internet of Things (IoT), using the Mirai botnet attack as a prime example. The analysis highlights how devices with weak default passwords and open API interfaces are susceptible to exploitation, leading to large-scale Distributed Denial of Service (DDoS) attacks. The paper emphasizes the importance of robust wireless encryption, secure password configurations, and secure development practices for IoT devices. It concludes that both manufacturers and users must prioritize security to mitigate the risks associated with the increasing integration of IoT devices into everyday life. Desklib offers similar solved assignments and past papers for students.

1
Internet of Things
Security in Internet of Things
Student Name as per 1st Affiliation
Institution
Line 2, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Abstract—Security of Information Systems and Data all
around the universe is now a huge topic that its being talked
about in the field of Information Technology. The security of
Personally Identifiable Information is now the most important
thing that all organizations need to accomplish perfectly for them
to be deemed secure [1]. In this paper, I have chosen to highlight
and address security issues in the field of Internet of Things.
I. INTRODUCTION
The conception of Internet of Things (IoT) was for the first
time made in the 20th century, on the other hand, much more
research on IoT developed over the past 20 years. It was an
idea where conceivably infinite number of 'things' –, like, smart
gadgets and sensors – all networked together while utilizing the
gadget to gadget technologies brought about by Internet or
other IP-based technologies out there.
Be that as it may, attributable to the huge number of
divisions attached and their impact on general everyday
presence, the security issues can have cruel results, causing
hurt, interference to exercises or, in a couple of circumstances,
notwithstanding prompting death of users. Colin Tankard from
Digital Pathways in his recent blog post took a gander at how
we may take off these issues.
II. BUSINESS CASE/JOURNAL ARTICLE
In 2016, a Japanese malware that was widely known as the
MIRAI BOTNET was designed by black hats in Japan. The
mirai botnet was aiming at attacking linux based devises that
are connected to a network and eventally turn them into bots
that are controlled remotely. The botnet was launched in 2016
to make rampant attacks on a huge number of IoT devices that
were mostly home IP cameras, home routers, home smart
devices like smart doors, smart windows, smart air conditioners
and many more. This was a major security attack on Internet of
Things.
The Mirai Botnet was the largets botnet attack that lead to a
widespread Distributed Denial of Service (DDOS) attack as per
the White-hat malware research group. Many online businesses
that were interconnected on internal and external networks
were overwhelmed with traffic from multiple sources. The
home devices that got the malware were hacked and got
controlled remotely like bots. Research concluded that the
mirai botnet looked for devices that were vulnerable through a
table of sixty default usernames and passwords. It thereafter
signed in to infect the devices. Any infected devices would be
controlled by the malware until when it would be rebooted and
its password was changed. This IoT security breach clearly
shows the levels of venerability of IoT devices if the basic
rules of security are not well taken care of.
III. ANALYSIS OF THE BUSINESS CASE
Internet of Things is the next big thing in technology;
however, it has come with a couple of weaknesses that must be
addressed now and in the future. The IoT devices contain many
loopholes that can be utilized by black hats having the means
and opportunity [4]. As in the aforementioned business case
where a team of Japan’s black hats developed a botnet to attack
IoT devices, it is clear that they were just targeting devices that
interconnect in a wireless network [2].
Many individuals all around the world using these devices
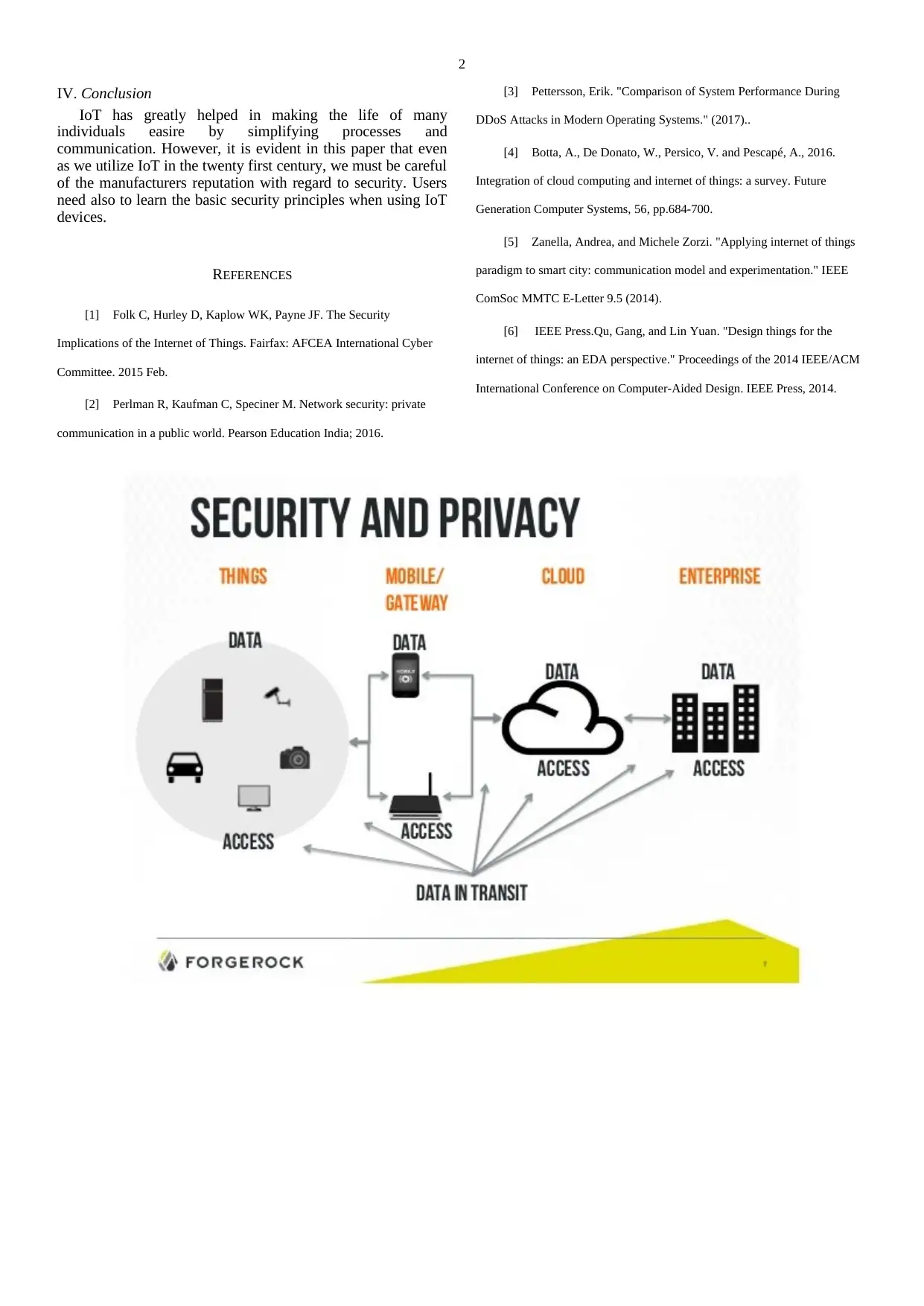
do not care on the security of their devices. When the wireless
network is utilizing the technologies of the past, and it does not
allow for the encryption of data in transit, it will be surely
vulnerable to any attack. All homes and businesses therefore
making use of IoT devices and wireless networks must ensure
that they are utilizing the best wireless encryption technologies
to protect all its data in transit [5]. Many end users of
technology in Japan also did not know or had not received
enough training on basic security tricks they need to practice
while using IoT devices. They should have known how to
configure very secure passwords on all their devices. IoT
devices have this vulnerability of allowing a user to just
provide any password that could not even be secure.
In order to address this, the various IoT manufacturers
must provide for a functionality that does not allow one to set
up weak passwords of their devices. This will prevent the
DDOS attacks as the aforementioned mirai botnet. Moreover,
various IoT devices are designed with open API interfaces
which allow developers to extend the functionality of the
devices [3]. Many IoT designers make devices with these open
APIs and give them public network standards such as Wifi and
Bluetooth without any access control mechanism or privilege
management [6]. This has become a major flau for
IOT(Internet of Things) devices that some people now call it a
Botnet of Things.
Internet of Things
Security in Internet of Things
Student Name as per 1st Affiliation
Institution
Line 2, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Abstract—Security of Information Systems and Data all
around the universe is now a huge topic that its being talked
about in the field of Information Technology. The security of
Personally Identifiable Information is now the most important
thing that all organizations need to accomplish perfectly for them
to be deemed secure [1]. In this paper, I have chosen to highlight
and address security issues in the field of Internet of Things.
I. INTRODUCTION
The conception of Internet of Things (IoT) was for the first
time made in the 20th century, on the other hand, much more
research on IoT developed over the past 20 years. It was an
idea where conceivably infinite number of 'things' –, like, smart
gadgets and sensors – all networked together while utilizing the
gadget to gadget technologies brought about by Internet or
other IP-based technologies out there.
Be that as it may, attributable to the huge number of
divisions attached and their impact on general everyday
presence, the security issues can have cruel results, causing
hurt, interference to exercises or, in a couple of circumstances,
notwithstanding prompting death of users. Colin Tankard from
Digital Pathways in his recent blog post took a gander at how
we may take off these issues.
II. BUSINESS CASE/JOURNAL ARTICLE
In 2016, a Japanese malware that was widely known as the
MIRAI BOTNET was designed by black hats in Japan. The
mirai botnet was aiming at attacking linux based devises that
are connected to a network and eventally turn them into bots
that are controlled remotely. The botnet was launched in 2016
to make rampant attacks on a huge number of IoT devices that
were mostly home IP cameras, home routers, home smart
devices like smart doors, smart windows, smart air conditioners
and many more. This was a major security attack on Internet of
Things.
The Mirai Botnet was the largets botnet attack that lead to a
widespread Distributed Denial of Service (DDOS) attack as per
the White-hat malware research group. Many online businesses
that were interconnected on internal and external networks
were overwhelmed with traffic from multiple sources. The
home devices that got the malware were hacked and got
controlled remotely like bots. Research concluded that the
mirai botnet looked for devices that were vulnerable through a
table of sixty default usernames and passwords. It thereafter
signed in to infect the devices. Any infected devices would be
controlled by the malware until when it would be rebooted and
its password was changed. This IoT security breach clearly
shows the levels of venerability of IoT devices if the basic
rules of security are not well taken care of.
III. ANALYSIS OF THE BUSINESS CASE
Internet of Things is the next big thing in technology;
however, it has come with a couple of weaknesses that must be
addressed now and in the future. The IoT devices contain many
loopholes that can be utilized by black hats having the means
and opportunity [4]. As in the aforementioned business case
where a team of Japan’s black hats developed a botnet to attack
IoT devices, it is clear that they were just targeting devices that
interconnect in a wireless network [2].
Many individuals all around the world using these devices
do not care on the security of their devices. When the wireless
network is utilizing the technologies of the past, and it does not
allow for the encryption of data in transit, it will be surely
vulnerable to any attack. All homes and businesses therefore
making use of IoT devices and wireless networks must ensure
that they are utilizing the best wireless encryption technologies
to protect all its data in transit [5]. Many end users of
technology in Japan also did not know or had not received
enough training on basic security tricks they need to practice
while using IoT devices. They should have known how to
configure very secure passwords on all their devices. IoT
devices have this vulnerability of allowing a user to just
provide any password that could not even be secure.
In order to address this, the various IoT manufacturers
must provide for a functionality that does not allow one to set
up weak passwords of their devices. This will prevent the
DDOS attacks as the aforementioned mirai botnet. Moreover,
various IoT devices are designed with open API interfaces
which allow developers to extend the functionality of the
devices [3]. Many IoT designers make devices with these open
APIs and give them public network standards such as Wifi and
Bluetooth without any access control mechanism or privilege
management [6]. This has become a major flau for
IOT(Internet of Things) devices that some people now call it a
Botnet of Things.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2
IV. Conclusion
IoT has greatly helped in making the life of many
individuals easire by simplifying processes and
communication. However, it is evident in this paper that even
as we utilize IoT in the twenty first century, we must be careful
of the manufacturers reputation with regard to security. Users
need also to learn the basic security principles when using IoT
devices.
REFERENCES
[1] Folk C, Hurley D, Kaplow WK, Payne JF. The Security
Implications of the Internet of Things. Fairfax: AFCEA International Cyber
Committee. 2015 Feb.
[2] Perlman R, Kaufman C, Speciner M. Network security: private
communication in a public world. Pearson Education India; 2016.
[3] Pettersson, Erik. "Comparison of System Performance During
DDoS Attacks in Modern Operating Systems." (2017)..
[4] Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016.
Integration of cloud computing and internet of things: a survey. Future
Generation Computer Systems, 56, pp.684-700.
[5] Zanella, Andrea, and Michele Zorzi. "Applying internet of things
paradigm to smart city: communication model and experimentation." IEEE
ComSoc MMTC E-Letter 9.5 (2014).
[6] IEEE Press.Qu, Gang, and Lin Yuan. "Design things for the
internet of things: an EDA perspective." Proceedings of the 2014 IEEE/ACM
International Conference on Computer-Aided Design. IEEE Press, 2014.
IV. Conclusion
IoT has greatly helped in making the life of many
individuals easire by simplifying processes and
communication. However, it is evident in this paper that even
as we utilize IoT in the twenty first century, we must be careful
of the manufacturers reputation with regard to security. Users
need also to learn the basic security principles when using IoT
devices.
REFERENCES
[1] Folk C, Hurley D, Kaplow WK, Payne JF. The Security
Implications of the Internet of Things. Fairfax: AFCEA International Cyber
Committee. 2015 Feb.
[2] Perlman R, Kaufman C, Speciner M. Network security: private
communication in a public world. Pearson Education India; 2016.
[3] Pettersson, Erik. "Comparison of System Performance During
DDoS Attacks in Modern Operating Systems." (2017)..
[4] Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016.
Integration of cloud computing and internet of things: a survey. Future
Generation Computer Systems, 56, pp.684-700.
[5] Zanella, Andrea, and Michele Zorzi. "Applying internet of things
paradigm to smart city: communication model and experimentation." IEEE
ComSoc MMTC E-Letter 9.5 (2014).
[6] IEEE Press.Qu, Gang, and Lin Yuan. "Design things for the
internet of things: an EDA perspective." Proceedings of the 2014 IEEE/ACM
International Conference on Computer-Aided Design. IEEE Press, 2014.
1 out of 2
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





