Internet of Things (IoT) Security: Current Status, Challenges and Prospective Measures
VerifiedAdded on 2023/06/03
|12
|760
|401
AI Summary
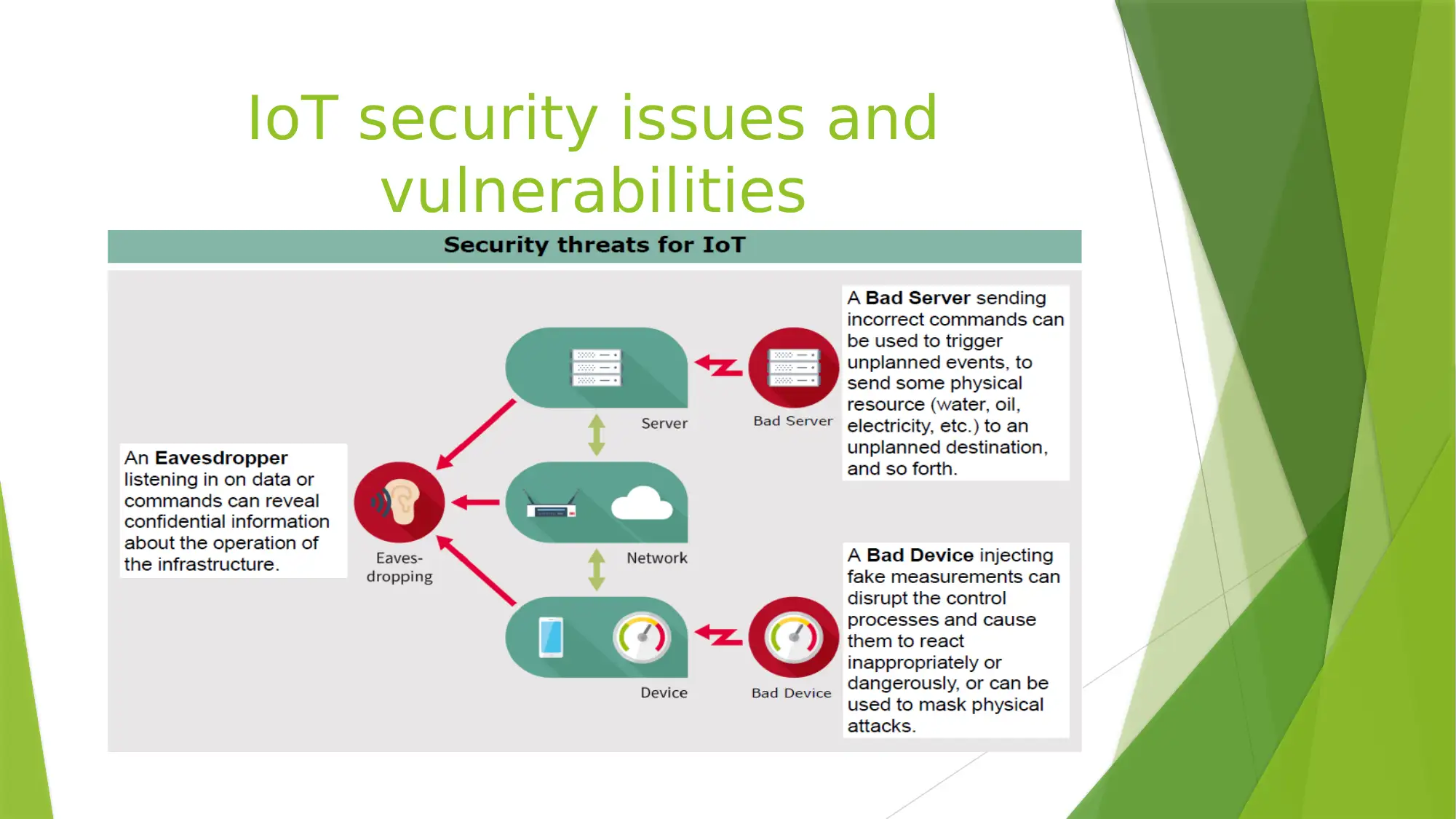
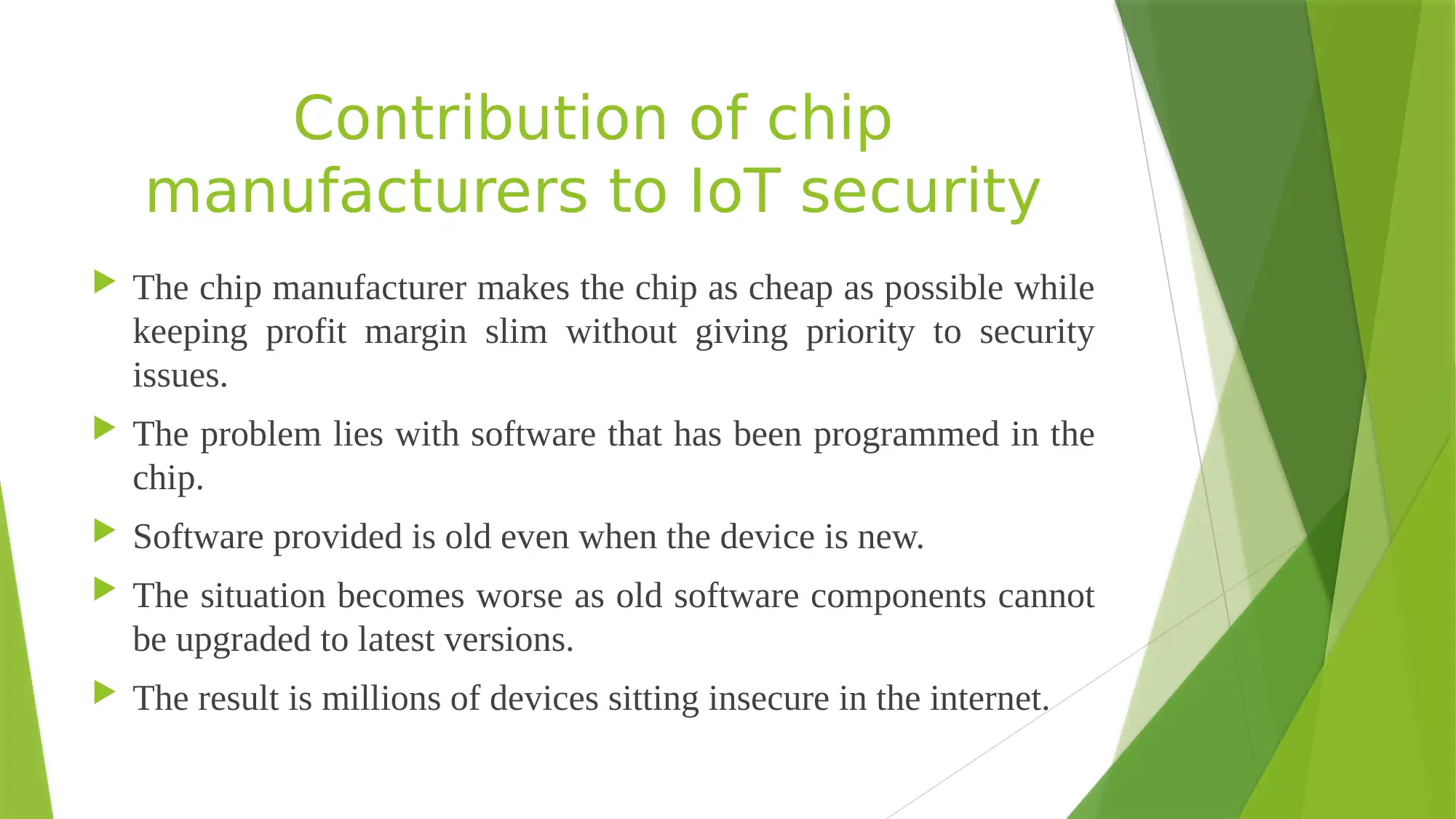
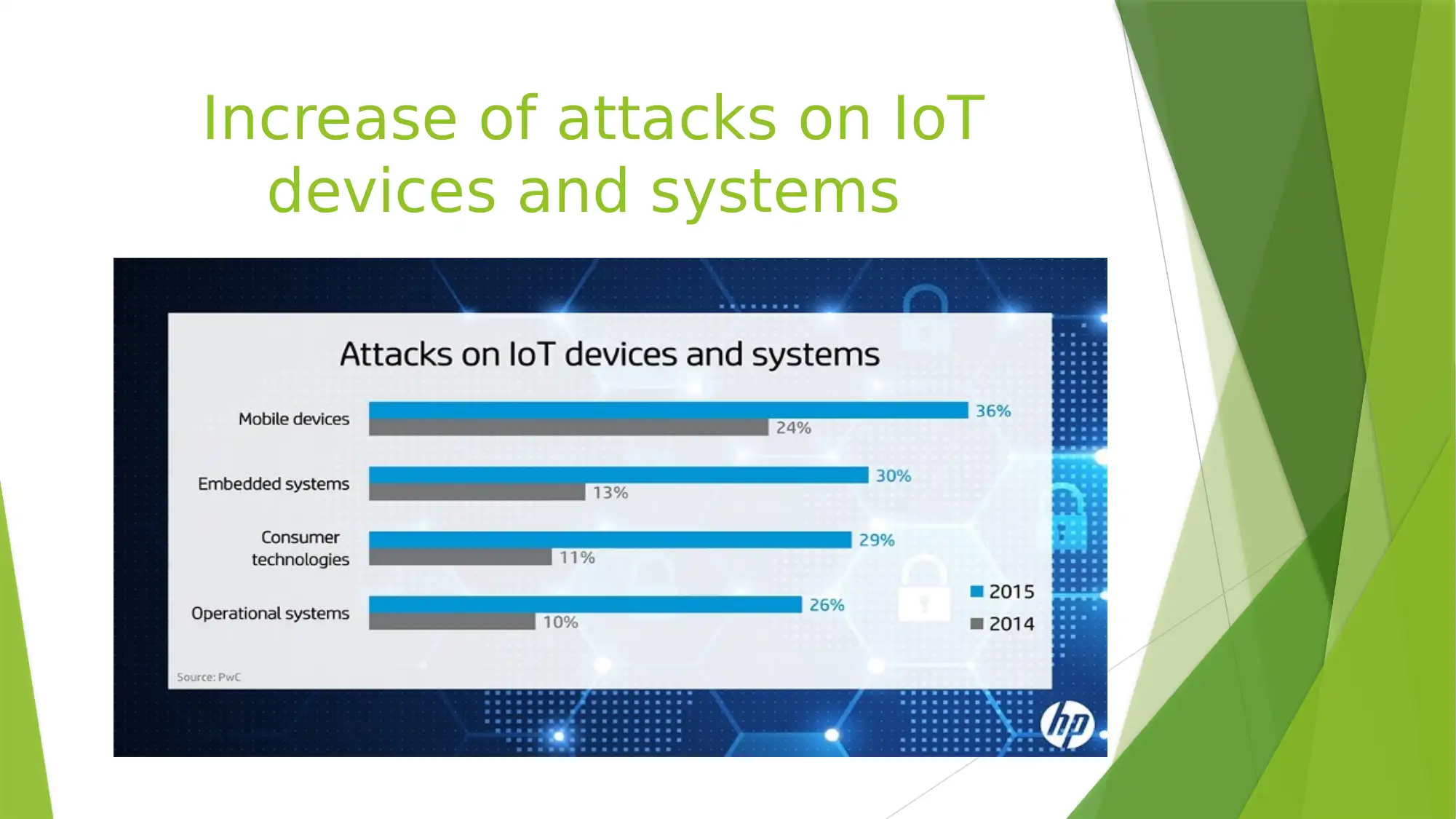
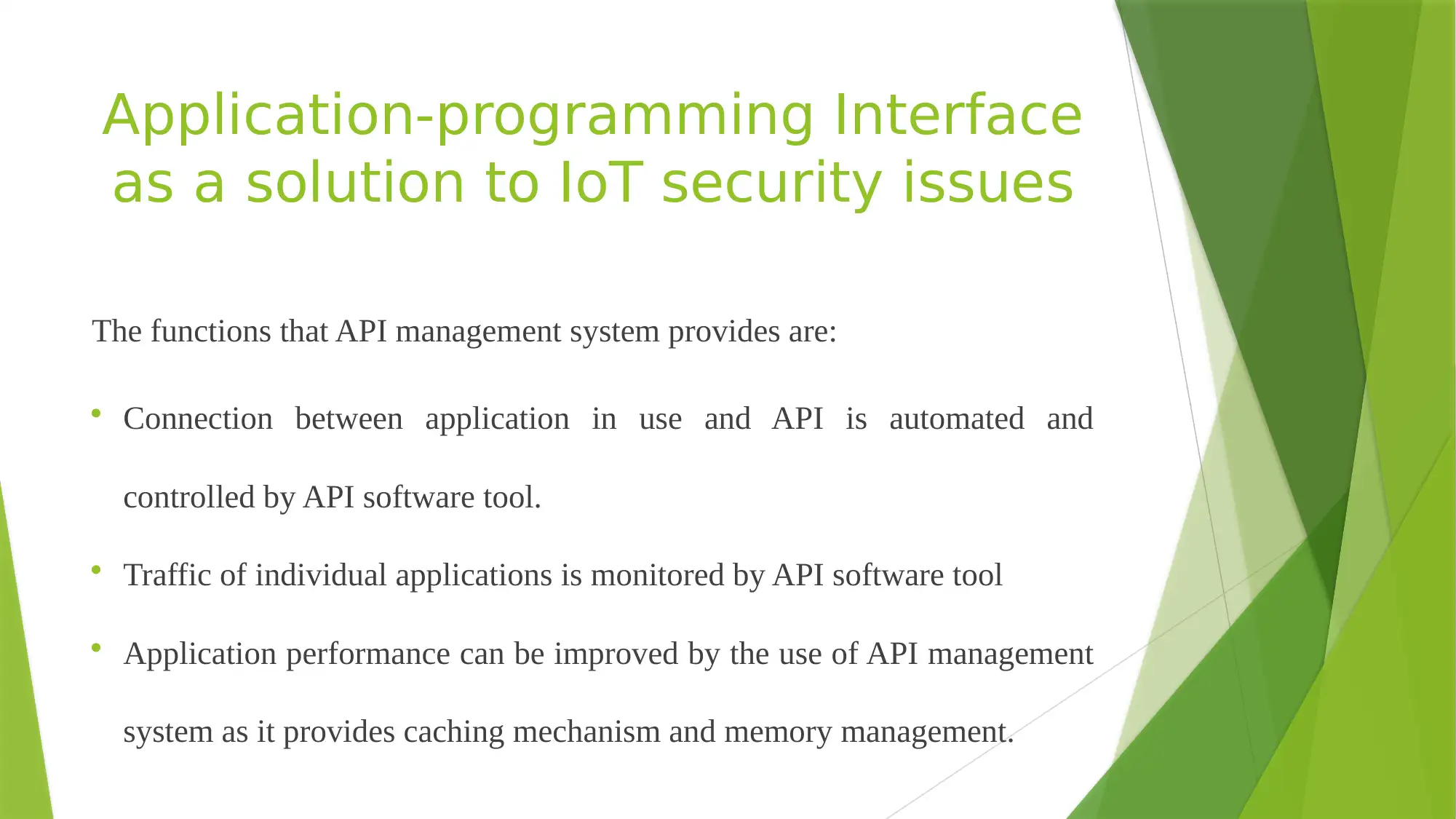
This presentation discusses the importance of IoT security, sources of IoT attacks, vulnerabilities, and contribution of chip manufacturers to IoT security. It also suggests the use of Application-programming Interface (API) as a solution to IoT security issues and emphasizes the need for more priority to be given to IoT security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
1 out of 12









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)