Implementing IoT for Secure Smart Transportation Systems
VerifiedAdded on 2023/06/07
|6
|4624
|210
Report
AI Summary
This report explores the implementation of IoT in smart transportation, focusing on the critical aspects of security and authentication. It begins by introducing the problem domain, emphasizing the need for secure IoT devices and data communication. The literature review examines various technologies, including RFID tags for device authentication, private cloud solutions for data storage security, IPv6 protocol for secure communication, and group authentication keys. It also addresses legal compliance and data security laws, proposing solutions like hash algorithms and Constrained Application Protocol (CoAP). The report further analyzes existing research, comparing different approaches to IoT implementation and highlighting the importance of RFID for tracking and authentication. It concludes by discussing the challenges, limitations, and future research directions for enhancing the security and reliability of IoT in smart transportation, recommending improvements for better security and user privacy. Desklib offers a wealth of resources, including past papers and solved assignments, to aid students in their studies.

Abstract—The purpose of the report is to discuss the
implication of IOT in the smart transportation and what are
the challenges for the implementations. The topic chosen for
the report is IOT in smart transportation. In order to
construct the report will follow a set format. The report first
introduces the problem domain in the introduction section to
form an overview of the report. The report then discusses
about the present and current issues in the domain for
implementing IOT in the smart transportation. The past and
current technologies used to solve those issues has also been
discussed as well in the literature review section. Based on the
literature review the most appropriate technology is figured
out. The most appropriate technology has been chosen with
proper justification which is supported with diagram and
table. The report also contain the annotated bibliography
which considers five quality articles including journals and
book from different sources such as google scholar , research
gate and other reputed resources. The report along with the
limitations and future research scope presents
recommendations for improving the way IOT is applied in
smart transportation with better security and reliability
I. INTRODUCTION
The report will consider the problem domain of security
and authenticity in IOT. The task of securing the IOT
devices is often considered as the key issues is
implementing IOT in practical applications. Hence proper
mechanism and technology is needed for ensuring that the
devices are authenticated to the network and data that is
communicated through the network is secured properly.
However while formulating the mechanism and the
technology, it is important to consider the constraints of the
IOT environment such as processing power , device
memory and the power consumption of the devices so that
the technology works properly.
II.LITERATURE REVIEW
According to Farooq et al. (2017) one of the important
aspect of the IOT connected smart transportation is the
need for authentication. In the IOT environment millions of
devices are connected in the network. Hence it becomes
important to have some mechanism for the device
authentication. The authors here proposed for the RFID tag
for the authentication. RFID tag works on the radio
frequency wave. The RFID tag stores the information in the
embedded chip and when the tag is activated with the radio
frequency wave, it then sends the information. The
information is collected and interpreted with the radio
frequency reader. It is possible to track the device on which
the RFID tag is attached. The authors claims that it is one
of the efficient technology available to track devices in the
IOT network.
Dorri et al. (2017) also suggested the RFID tag for the
device authentication. The authors makes it clear that in the
IOT environment one of the primary need is to have some
reliable and efficient techniques that helps to properly
authenticate the devices. The authentication is particularly
important as without authentication it is not possible to
control the cars properly and if the control is not proper it
will create issue in the transportation. Hence for effective
execution of the smart transportation system with the IOT it
is important to have proper authentication technique and
RFID tag is one of the efficient techniques in this purpose
according to the authors.
Zhang et al. (2016) argues that although the barcode
technique is very popular in the traditional system, but it is
not effective in the IOT context. In order to barcode
technique to work the device have to be in the line of sight
of the barcode reader means that physical access is needed
which is not possible for the cars that is connected in the
IOT network. The one and only feasible solution is to have
some reliable technique that helps to track and identify
devices wirelessly. RFID technology is currently one of the
popular technique that is currently available in the industry.
The authors have also suggested for the same.
Although Fradrich et al. (2016) have admitted that the
authentication is important for successful implementation
of IOT in the smart transportation, it is not the only aspect
of the implementation strategy. Organization should look
beyond the authentication as there are other issues too for
the integration of IOT in the transportation. Even before
authentication mechanism is implemented it is important to
make sure that privacy of the users are maintained in the
IOT environment. The author has suggested although the
use of the cloud computing for data storage is an efficient
technique considering the vast amount of data, what even
more important is the privacy of these data. In order to
ensure that the data that is stored in the cloud storage
remotely is secured it is suggested to opt for the private
cloud as it offers more control and security over the public
cloud.
Tappler et al. (2015) has also suggested for the use of the
private cloud for better data security.
Li et al. (2015) in the article have taken more detailed
approach like how to increase data security for the IOT
devices while opting for the private cloud. according to the
author in order to make sure that the private cloud is
actually secure , the VLAN has to be secured first as the
communication of the data have to be done through this
VLAN. In order to protect the data the authors have here
actually suggested for the use of the firewall along with the
virtual server. It will make sure that the access to the data is
restricted to the users that are not authorized for accessing
the data in the server.
Implementation of IOT in Smart Transportation
Abstract—The purpose of the report is to discuss the
implication of IOT in the smart transportation and what are
the challenges for the implementations. The topic chosen for
the report is IOT in smart transportation. In order to
construct the report will follow a set format. The report first
introduces the problem domain in the introduction section to
form an overview of the report. The report then discusses
about the present and current issues in the domain for
implementing IOT in the smart transportation. The past and
current technologies used to solve those issues has also been
discussed as well in the literature review section. Based on the
literature review the most appropriate technology is figured
out. The most appropriate technology has been chosen with
proper justification which is supported with diagram and
table. The report also contain the annotated bibliography
which considers five quality articles including journals and
book from different sources such as google scholar , research
gate and other reputed resources. The report along with the
limitations and future research scope presents
recommendations for improving the way IOT is applied in
smart transportation with better security and reliability
I. INTRODUCTION
The report will consider the problem domain of security
and authenticity in IOT. The task of securing the IOT
devices is often considered as the key issues is
implementing IOT in practical applications. Hence proper
mechanism and technology is needed for ensuring that the
devices are authenticated to the network and data that is
communicated through the network is secured properly.
However while formulating the mechanism and the
technology, it is important to consider the constraints of the
IOT environment such as processing power , device
memory and the power consumption of the devices so that
the technology works properly.
II.LITERATURE REVIEW
According to Farooq et al. (2017) one of the important
aspect of the IOT connected smart transportation is the
need for authentication. In the IOT environment millions of
devices are connected in the network. Hence it becomes
important to have some mechanism for the device
authentication. The authors here proposed for the RFID tag
for the authentication. RFID tag works on the radio
frequency wave. The RFID tag stores the information in the
embedded chip and when the tag is activated with the radio
frequency wave, it then sends the information. The
information is collected and interpreted with the radio
frequency reader. It is possible to track the device on which
the RFID tag is attached. The authors claims that it is one
of the efficient technology available to track devices in the
IOT network.
Dorri et al. (2017) also suggested the RFID tag for the
device authentication. The authors makes it clear that in the
IOT environment one of the primary need is to have some
reliable and efficient techniques that helps to properly
authenticate the devices. The authentication is particularly
important as without authentication it is not possible to
control the cars properly and if the control is not proper it
will create issue in the transportation. Hence for effective
execution of the smart transportation system with the IOT it
is important to have proper authentication technique and
RFID tag is one of the efficient techniques in this purpose
according to the authors.
Zhang et al. (2016) argues that although the barcode
technique is very popular in the traditional system, but it is
not effective in the IOT context. In order to barcode
technique to work the device have to be in the line of sight
of the barcode reader means that physical access is needed
which is not possible for the cars that is connected in the
IOT network. The one and only feasible solution is to have
some reliable technique that helps to track and identify
devices wirelessly. RFID technology is currently one of the
popular technique that is currently available in the industry.
The authors have also suggested for the same.
Although Fradrich et al. (2016) have admitted that the
authentication is important for successful implementation
of IOT in the smart transportation, it is not the only aspect
of the implementation strategy. Organization should look
beyond the authentication as there are other issues too for
the integration of IOT in the transportation. Even before
authentication mechanism is implemented it is important to
make sure that privacy of the users are maintained in the
IOT environment. The author has suggested although the
use of the cloud computing for data storage is an efficient
technique considering the vast amount of data, what even
more important is the privacy of these data. In order to
ensure that the data that is stored in the cloud storage
remotely is secured it is suggested to opt for the private
cloud as it offers more control and security over the public
cloud.
Tappler et al. (2015) has also suggested for the use of the
private cloud for better data security.
Li et al. (2015) in the article have taken more detailed
approach like how to increase data security for the IOT
devices while opting for the private cloud. according to the
author in order to make sure that the private cloud is
actually secure , the VLAN has to be secured first as the
communication of the data have to be done through this
VLAN. In order to protect the data the authors have here
actually suggested for the use of the firewall along with the
virtual server. It will make sure that the access to the data is
restricted to the users that are not authorized for accessing
the data in the server.
Implementation of IOT in Smart Transportation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In the IOT environment, it is required that the
communication in the network is fast, secure and reliable.
The IOT, when implemented in the transportation, it should
be take into account that any delay in communication
might often lead to miscommunication and the aspect of
proper communication is not necessary, it is mandatory for
proper execution of the process. Huang et al. (2015) have
suggested for the IPv6 protocol. This is the latest version of
the internet protocol and IOT use the internet protocol for
the communication over internet. The feature that makes
IPv6 appropriate for the secure communication along with
speed is the level of encryption used for the
communication. This version of the internet protocol uses
supports 2128 address mode and hence it is difficult to
temper with the data that is communicated through the
network.
According to Tayeb, Latifi and Kim (2015) as a lot of
devices are connected in the IOT network, it is likely that
the devices will overlap with each other and this should be
avoided to ensure the privacy. Hence it is important to
categorize devices in the group. Additionally a group
authentication key must be assigned. The technique is
based on the “Shamir’s secret sharing scheme”. In the
group there is a primary device that is responsible to
monitor the activity of other devices in the group. Every
time a new device is included in the group, a new key pair
is formed which is then communicated to other devices that
are part of the group. This makes all the devices aware that
any new device is added in the. If any other devices that are
not part of the devices will not be able to join the group and
communicate. Hence it is effective technique to make sure
that the communication is secured and only restricted to the
devices that are part of the group.
Dobrescu et al. (2015) argues that in order to successfully
implement IOT in the transportation system, the legal
compliance is also important. In the IOT based smart
transportation system, cars as well as owners of the cars are
tracked continuously to inform them about traffic
information. However according to international data
security laws, it is mandatory to protect the security of the
data and every organization should provide necessary
means to secure this data. The authors have argued that if
the information like location of car, transportation path of
the car are significant in nature. It is possible to trace the
car through hacking this information. In order to protect the
digital data the author has proposed for the hash algorithm.
The algorithm is based on the digital cryptography. The
digital content is first hashed and an encryption key is
generated. This value is only made available to the users
who are authorized to access the information. Without
providing the encryption key it is not possible to read or
modify the content. Hence it provides an efficient method
for securing the digital information that is collected through
the network.
Al-Sarawi et al. (2014) have however suggested for
Constrained Application Protocol or CoAP for securing the
information. In the algorithm the system first verifies the
identity of the user. In order to verify the identity the user
need to provide the correct system credentials like
username and password for that was generated during the
registration. After the credentials are verified, the system
then only grants the access. Only after the system grants the
access, it is possible to access the server and access the data
stored in it. Hence it is an efficient technique for securing
the information and protecting the identity of the owner of
the data.
Li, C. T., Lee, C. C., Weng, C. Y., & Chen, C. M. (2018).
Towards secure authenticating of cache in the reader
for RFID-based IoT systems. Peer-to-Peer Networking
and Applications, 11(1), 198-208.
The authors have first discussed the concept of IOT in
effective manner. Although the discussion is not detailed,
but the discussion is simple and easy to follow. After the
introduction the author sets the discussion for the issues of
IOT in the various application with the majority of the
discussion focused on the issues of IOT in transportation.
The research method selected by the authors is the
comparison of literature review. The author have identified
the relevant literatures and analyzed the previous works of
the authors of those literatures. The authors have then
identified the most appropriate solution to the problem on
which the authors was working and that is the
authentication of device in the IOT environment. The
solution that has been proposed by the authors is the
application of RFID for tracking and authenticating the
devices in the network. This journal is basically focused on
the technique that is used for implementation of the internet
of thing. The basic concept of the entire terminology of
implementation of internet of things is provided in this
journal. The data that is present in the journal is very well
structured and the researchers find it easy to surf the
journal. This acts as one of the main reason behind the
prosecution of the journal and this is also one of the major
reason that ensures that the journal is very famous among
the researchers. The data that is present in the journal is
very precise in nature this is the reason that the journal
helps in time saving of the researchers.
Lopes, A.P.G. and Hilgert, L.D.O., 2017. Group
authentication protocols for Internet of Things (IoT)–
QoS and Security Properties Evaluation.
The authors have followed a very detailed approach while
discussing the concept of IOT. The authors have not opted
for any general discussion like what is meant by IOT and
what are the application of it. Instead from the starting of
the article the authors are very specific in terms of the
discussion, application of IOT in the smart transportation.
The authors have first discussed the various problems and
the importance for successful implementation of the IOT in
transportation system. However instead of discussing the
solution for each of the listed problem the sub sequent
sections are dedicated to the solution for the problem
domain that the authors have considered, the need and
technique for secure communication over the internet.
communication in the network is fast, secure and reliable.
The IOT, when implemented in the transportation, it should
be take into account that any delay in communication
might often lead to miscommunication and the aspect of
proper communication is not necessary, it is mandatory for
proper execution of the process. Huang et al. (2015) have
suggested for the IPv6 protocol. This is the latest version of
the internet protocol and IOT use the internet protocol for
the communication over internet. The feature that makes
IPv6 appropriate for the secure communication along with
speed is the level of encryption used for the
communication. This version of the internet protocol uses
supports 2128 address mode and hence it is difficult to
temper with the data that is communicated through the
network.
According to Tayeb, Latifi and Kim (2015) as a lot of
devices are connected in the IOT network, it is likely that
the devices will overlap with each other and this should be
avoided to ensure the privacy. Hence it is important to
categorize devices in the group. Additionally a group
authentication key must be assigned. The technique is
based on the “Shamir’s secret sharing scheme”. In the
group there is a primary device that is responsible to
monitor the activity of other devices in the group. Every
time a new device is included in the group, a new key pair
is formed which is then communicated to other devices that
are part of the group. This makes all the devices aware that
any new device is added in the. If any other devices that are
not part of the devices will not be able to join the group and
communicate. Hence it is effective technique to make sure
that the communication is secured and only restricted to the
devices that are part of the group.
Dobrescu et al. (2015) argues that in order to successfully
implement IOT in the transportation system, the legal
compliance is also important. In the IOT based smart
transportation system, cars as well as owners of the cars are
tracked continuously to inform them about traffic
information. However according to international data
security laws, it is mandatory to protect the security of the
data and every organization should provide necessary
means to secure this data. The authors have argued that if
the information like location of car, transportation path of
the car are significant in nature. It is possible to trace the
car through hacking this information. In order to protect the
digital data the author has proposed for the hash algorithm.
The algorithm is based on the digital cryptography. The
digital content is first hashed and an encryption key is
generated. This value is only made available to the users
who are authorized to access the information. Without
providing the encryption key it is not possible to read or
modify the content. Hence it provides an efficient method
for securing the digital information that is collected through
the network.
Al-Sarawi et al. (2014) have however suggested for
Constrained Application Protocol or CoAP for securing the
information. In the algorithm the system first verifies the
identity of the user. In order to verify the identity the user
need to provide the correct system credentials like
username and password for that was generated during the
registration. After the credentials are verified, the system
then only grants the access. Only after the system grants the
access, it is possible to access the server and access the data
stored in it. Hence it is an efficient technique for securing
the information and protecting the identity of the owner of
the data.
Li, C. T., Lee, C. C., Weng, C. Y., & Chen, C. M. (2018).
Towards secure authenticating of cache in the reader
for RFID-based IoT systems. Peer-to-Peer Networking
and Applications, 11(1), 198-208.
The authors have first discussed the concept of IOT in
effective manner. Although the discussion is not detailed,
but the discussion is simple and easy to follow. After the
introduction the author sets the discussion for the issues of
IOT in the various application with the majority of the
discussion focused on the issues of IOT in transportation.
The research method selected by the authors is the
comparison of literature review. The author have identified
the relevant literatures and analyzed the previous works of
the authors of those literatures. The authors have then
identified the most appropriate solution to the problem on
which the authors was working and that is the
authentication of device in the IOT environment. The
solution that has been proposed by the authors is the
application of RFID for tracking and authenticating the
devices in the network. This journal is basically focused on
the technique that is used for implementation of the internet
of thing. The basic concept of the entire terminology of
implementation of internet of things is provided in this
journal. The data that is present in the journal is very well
structured and the researchers find it easy to surf the
journal. This acts as one of the main reason behind the
prosecution of the journal and this is also one of the major
reason that ensures that the journal is very famous among
the researchers. The data that is present in the journal is
very precise in nature this is the reason that the journal
helps in time saving of the researchers.
Lopes, A.P.G. and Hilgert, L.D.O., 2017. Group
authentication protocols for Internet of Things (IoT)–
QoS and Security Properties Evaluation.
The authors have followed a very detailed approach while
discussing the concept of IOT. The authors have not opted
for any general discussion like what is meant by IOT and
what are the application of it. Instead from the starting of
the article the authors are very specific in terms of the
discussion, application of IOT in the smart transportation.
The authors have first discussed the various problems and
the importance for successful implementation of the IOT in
transportation system. However instead of discussing the
solution for each of the listed problem the sub sequent
sections are dedicated to the solution for the problem
domain that the authors have considered, the need and
technique for secure communication over the internet.

The authors have proposed IPv6 internet protocol for the
communication while maintaining the speed and security.
The authors have reviewed several literature on this topic.
Along with that the authors have also verified the concept
through original work. Instead of collecting presented the
information based on the secondary research the authors
verified the speed and level of encryption on their own
through testing and prototyping. The result of the same
have been presented in the paper as well which makes it
easy to follow. This journal basically deals with the
processing of the implementation of the IPv6. Basic
concept of the data regarding the concept of IPv6 is stated
in this journal. The main processing of the Internet of tings
is stayed in this journal. Researchers find it easy for the
process of the internet of things. The need for the
implementation of internet of things in the platform of data
storage is also discussed in a very conceptual manner.
Another aspect of this journal is that the data that are
present in this journal is not at all in texted and this leads to
the fact that the data that are present in the journal cannot
be used for future purpose. This is the main reason that the
journal is not given much importance and the popularity of
the journal is very low.
Lee, Y. S., Alasaarela, E., & Lee, H. (2014, February).
Secure key management scheme based on ECC
algorithm in transportation system. In Information
Networking (ICOIN), 2014 International Conference on
(pp. 453-457). IEEE.
The authors have discussed about the application and the
security issue of implementing IOT in the transportation
system.
The authors have selected the area of data privacy and data
storage. The authors makes it clear that as the data that is
collected is huge in volume, it is not possible to store the
data in the traditional storage system. Hence cloud
computing or the cloud storage is the alternative option.
However organization should opt for the private cloud over
the public cloud for better security and control over the
data
The authors have opted for the secondary research methods
that is review of existing literature in the domain of data
security in IOT. This journal is basically dependent on the
comparison in between the earlier stage and the post stage.
This journal helps in understanding the advantages that the
people of smart city enjoys after the implementation of the
internet of things. This journal also helps in understanding
the disadvantages that are present in the society after the
implementation of the Internet of things
Hofheinz, D., & Jager, T. (2016). Tightly secure
signatures and public-key encryption. Designs, Codes
and Cryptography, 80(1), 29-61.
The author have discussed the security and application of
IOT for preparing the research paper.
The problem domain chosen for the topic is the security of
the digital content. The author here have proposed for
hashing technique for securing the data. The hashing
algorithm encrypt the data and in order to decrypt the data
the hashing value must be provided. Once the values match
it is then decrypted and it is then possible to read.
The author has here opted for the primary research.
Although relevant literatures were reviewed, the authors
have opted for simulation of the Hashing algorithm and the
result has been discussed in the paper too. This journal
deals with the problems that are present in the processing of
the implementation of the internet of things. After the
implementation of the internet of things the security issues
that are present is well commenced in this journal. This
also shows that the journal that is used is well constructed
and precise in nature and due to this preciseness of the
journal this journal gains very high importance.
Jan, S. R., Khan, F., Ullah, F., Azim, N., & Tahir, M.
(2016). Using CoAP Protocol for Resource Observation
in IoT. International Journal of Emerging Technology
in Computer Science & Electronics, ISSN, 0976-1353.
The authors in this article have discussed for legal issues of
implementing the IOT in the smart transportation system
The authors have discussed that in order to comply with the
legal issue it is important to secure the data that is collected
for controlling and monitoring the traffic through IOT and
provide the correct information to the user to help them
obtain proper information about the traffic and make
effective decision based on that.
In order to secure the information the author have
suggested Constrained Application Protocol or CoAP. It
makes it mandatory for the users to verify the authorization
to the system before accessing the data from the server.
The authors have chosen the secondary research method
that includes analysis and review of previous research
works. The techniques identified in the literatures have
been compared and based on that the authors have
suggested the appropriate method. This journal is termed as
an advanced level textual concept. The data that is present
in the journal generally deals with the processing of the
Constrained Application Protocol or CoAP. This definition
of the conceptual proposing of the data helps in gaining
conceptual knowledge regarding the platform of the
internet of things. The structuring of the data is not very
well performed. This leads to the fact that the time that is
taken to surf the data is very high. The data that are present
in this journal is very well in texted which makes this
journal usable among the researchers. This is the main
reason that this journal is gaining importance
ii) Requirements of the project:
After conducting the literature review the following
requirements have identified for the project
• Proper review and the analysis of the authentication
problem in the IOT connected smart transportation
• Review of the security issues in the smart transportation
• Review and comparison of several algorithms proposed
by the previous works
• Formulating effective algorithm for the authentication
• Review of the effectiveness of the proposed algorithm
communication while maintaining the speed and security.
The authors have reviewed several literature on this topic.
Along with that the authors have also verified the concept
through original work. Instead of collecting presented the
information based on the secondary research the authors
verified the speed and level of encryption on their own
through testing and prototyping. The result of the same
have been presented in the paper as well which makes it
easy to follow. This journal basically deals with the
processing of the implementation of the IPv6. Basic
concept of the data regarding the concept of IPv6 is stated
in this journal. The main processing of the Internet of tings
is stayed in this journal. Researchers find it easy for the
process of the internet of things. The need for the
implementation of internet of things in the platform of data
storage is also discussed in a very conceptual manner.
Another aspect of this journal is that the data that are
present in this journal is not at all in texted and this leads to
the fact that the data that are present in the journal cannot
be used for future purpose. This is the main reason that the
journal is not given much importance and the popularity of
the journal is very low.
Lee, Y. S., Alasaarela, E., & Lee, H. (2014, February).
Secure key management scheme based on ECC
algorithm in transportation system. In Information
Networking (ICOIN), 2014 International Conference on
(pp. 453-457). IEEE.
The authors have discussed about the application and the
security issue of implementing IOT in the transportation
system.
The authors have selected the area of data privacy and data
storage. The authors makes it clear that as the data that is
collected is huge in volume, it is not possible to store the
data in the traditional storage system. Hence cloud
computing or the cloud storage is the alternative option.
However organization should opt for the private cloud over
the public cloud for better security and control over the
data
The authors have opted for the secondary research methods
that is review of existing literature in the domain of data
security in IOT. This journal is basically dependent on the
comparison in between the earlier stage and the post stage.
This journal helps in understanding the advantages that the
people of smart city enjoys after the implementation of the
internet of things. This journal also helps in understanding
the disadvantages that are present in the society after the
implementation of the Internet of things
Hofheinz, D., & Jager, T. (2016). Tightly secure
signatures and public-key encryption. Designs, Codes
and Cryptography, 80(1), 29-61.
The author have discussed the security and application of
IOT for preparing the research paper.
The problem domain chosen for the topic is the security of
the digital content. The author here have proposed for
hashing technique for securing the data. The hashing
algorithm encrypt the data and in order to decrypt the data
the hashing value must be provided. Once the values match
it is then decrypted and it is then possible to read.
The author has here opted for the primary research.
Although relevant literatures were reviewed, the authors
have opted for simulation of the Hashing algorithm and the
result has been discussed in the paper too. This journal
deals with the problems that are present in the processing of
the implementation of the internet of things. After the
implementation of the internet of things the security issues
that are present is well commenced in this journal. This
also shows that the journal that is used is well constructed
and precise in nature and due to this preciseness of the
journal this journal gains very high importance.
Jan, S. R., Khan, F., Ullah, F., Azim, N., & Tahir, M.
(2016). Using CoAP Protocol for Resource Observation
in IoT. International Journal of Emerging Technology
in Computer Science & Electronics, ISSN, 0976-1353.
The authors in this article have discussed for legal issues of
implementing the IOT in the smart transportation system
The authors have discussed that in order to comply with the
legal issue it is important to secure the data that is collected
for controlling and monitoring the traffic through IOT and
provide the correct information to the user to help them
obtain proper information about the traffic and make
effective decision based on that.
In order to secure the information the author have
suggested Constrained Application Protocol or CoAP. It
makes it mandatory for the users to verify the authorization
to the system before accessing the data from the server.
The authors have chosen the secondary research method
that includes analysis and review of previous research
works. The techniques identified in the literatures have
been compared and based on that the authors have
suggested the appropriate method. This journal is termed as
an advanced level textual concept. The data that is present
in the journal generally deals with the processing of the
Constrained Application Protocol or CoAP. This definition
of the conceptual proposing of the data helps in gaining
conceptual knowledge regarding the platform of the
internet of things. The structuring of the data is not very
well performed. This leads to the fact that the time that is
taken to surf the data is very high. The data that are present
in this journal is very well in texted which makes this
journal usable among the researchers. This is the main
reason that this journal is gaining importance
ii) Requirements of the project:
After conducting the literature review the following
requirements have identified for the project
• Proper review and the analysis of the authentication
problem in the IOT connected smart transportation
• Review of the security issues in the smart transportation
• Review and comparison of several algorithms proposed
by the previous works
• Formulating effective algorithm for the authentication
• Review of the effectiveness of the proposed algorithm
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
• Suggest the most appropriate algorithm after analyzing
the strength and weakness of the previous proposed
algorithms
iii) Modification of the Problem statement based on the
literature review:
Although IOT is having huge potential there are several
issues with the technology. This issues have to be addressed
for the successful implementation of the technology. There
are several problems for the successful implementation of
IOT in the smart transportation and several authors have
identified different issues with specific solution against
that. However the majority of the articles that have been
reviewed, confirms that the leading problem in the IOT
environment is the lack of proper authentication scheme
and it is required to formulate a robust framework for
authentication in order to realize the potential of IOT in the
transportation system properly.
Recommendation and justification:
Although several authors have suggested different
technology for the device authentication in the IOT
environment, but the majority of the researchers have opted
for the RFID technology and the authors of the literatures
that have been chosen here also suggested for the same.
This particular report also recommend for that as it is
requires less resources and less processing power to
implement which is one of the prime consideration for the
IOT environment.
As the resource constraint need to be included for the IOT
environment and the same applies to the communication
protocol chosen for smart transportation with IOT. Hence
COAP is preferred over the popular HTTP protocol used in
internet communication. Besides this the CoAP protocol is
more secured than the HTTP protocol as it includes higher
encryption level. CoAP protocol uses the ECC
authentication mechanism. The table and figures for the
recommended technologies have been described in the
following section
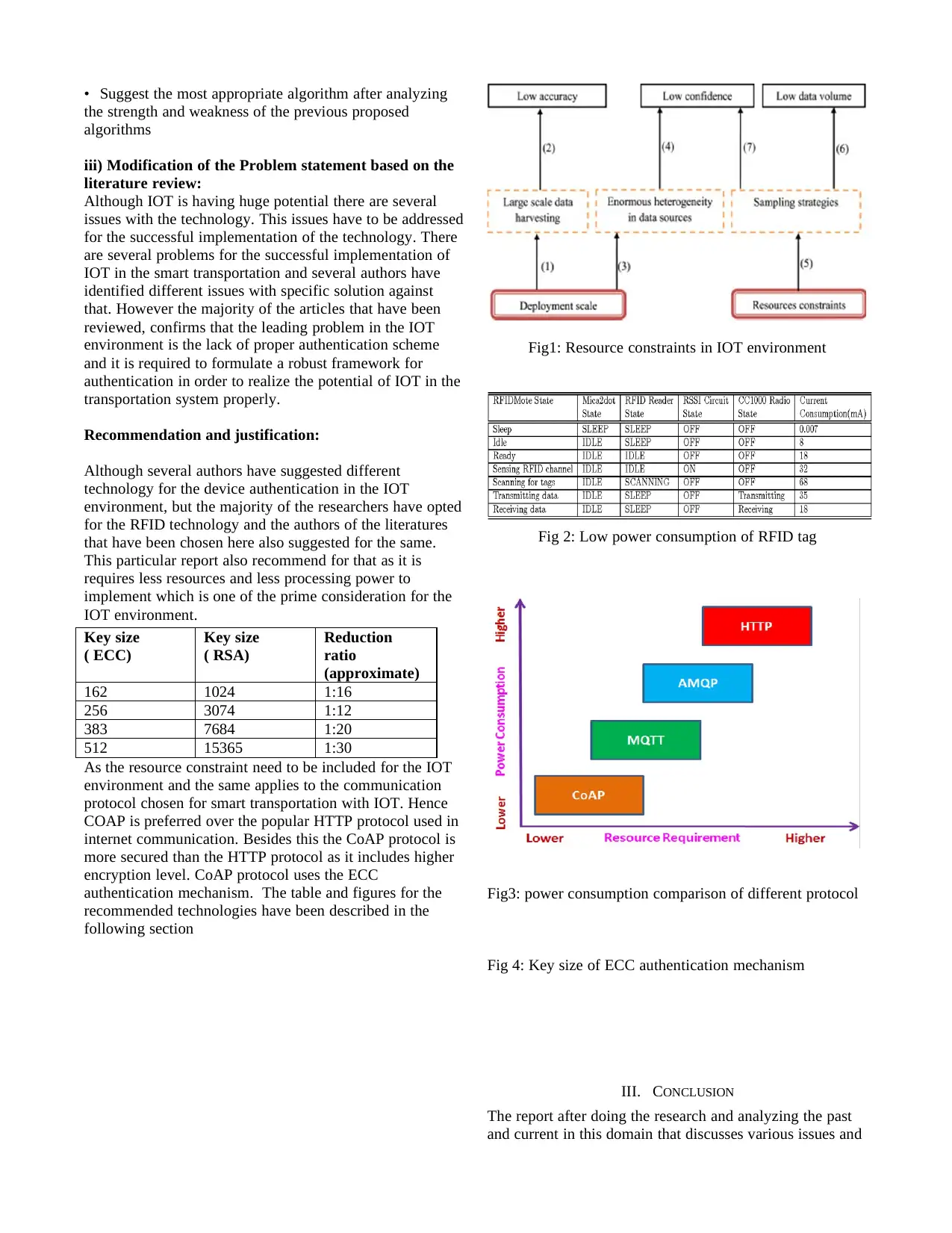
Fig1: Resource constraints in IOT environment
Fig 2: Low power consumption of RFID tag
Fig3: power consumption comparison of different protocol
Fig 4: Key size of ECC authentication mechanism
III. CONCLUSION
The report after doing the research and analyzing the past
and current in this domain that discusses various issues and
Key size
( ECC)
Key size
( RSA)
Reduction
ratio
(approximate)
162 1024 1:16
256 3074 1:12
383 7684 1:20
512 15365 1:30
the strength and weakness of the previous proposed
algorithms
iii) Modification of the Problem statement based on the
literature review:
Although IOT is having huge potential there are several
issues with the technology. This issues have to be addressed
for the successful implementation of the technology. There
are several problems for the successful implementation of
IOT in the smart transportation and several authors have
identified different issues with specific solution against
that. However the majority of the articles that have been
reviewed, confirms that the leading problem in the IOT
environment is the lack of proper authentication scheme
and it is required to formulate a robust framework for
authentication in order to realize the potential of IOT in the
transportation system properly.
Recommendation and justification:
Although several authors have suggested different
technology for the device authentication in the IOT
environment, but the majority of the researchers have opted
for the RFID technology and the authors of the literatures
that have been chosen here also suggested for the same.
This particular report also recommend for that as it is
requires less resources and less processing power to
implement which is one of the prime consideration for the
IOT environment.
As the resource constraint need to be included for the IOT
environment and the same applies to the communication
protocol chosen for smart transportation with IOT. Hence
COAP is preferred over the popular HTTP protocol used in
internet communication. Besides this the CoAP protocol is
more secured than the HTTP protocol as it includes higher
encryption level. CoAP protocol uses the ECC
authentication mechanism. The table and figures for the
recommended technologies have been described in the
following section
Fig1: Resource constraints in IOT environment
Fig 2: Low power consumption of RFID tag
Fig3: power consumption comparison of different protocol
Fig 4: Key size of ECC authentication mechanism
III. CONCLUSION
The report after doing the research and analyzing the past
and current in this domain that discusses various issues and
Key size
( ECC)
Key size
( RSA)
Reduction
ratio
(approximate)
162 1024 1:16
256 3074 1:12
383 7684 1:20
512 15365 1:30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

solutions, the report comes to the conclusion that IOT has a
huge potential in transforming the transportation system.
However there are several challenges as of now to realize
the potential of the technology. The major challenges are
the challenges regarding the authentication the data security
and the communication between devices of the IOT
connected objects in the network. Although there are
several technology for authentication of the device, but not
all are efficient. The most efficient technology for device
authentication in the IOT network is the RFID technology
as it considers the IOT device constraints such as the
limited memory, processing power and the power
consumption. Among the communication protocols that are
popular for communicating over the internet the protocol
that is most appropriate considering the highly constraint
environment of the IOT devices is the COAP protocol as it
is secure, less power consuming and require less memory to
execute which is ideal for IOT applications. However it
should be noted that as technology is getting more and
more advanced and several new technology is being
discovered, there is no fix preference for the ideal
technology and the list is subject to change. Hence it is
appropriate to consider that some technology might be
preferable for now but it is likely to change as new
technology provides solution that better and improved than
the previous technology. Hence there is always scope for
future research in this domain.
REFERENCES
AL-SARAWI, S., ANBAR, M., ALIEYAN, K., & ALZUBAIDI, M.
(2015, MAY). INTERNET OF THINGS (IOT) COMMUNICATION
PROTOCOLS. IN INFORMATION TECHNOLOGY (ICIT), 2017
8TH INTERNATIONAL CONFERENCE ON (PP. 685-690). IEEE.
DOBRESCU, R., MOCANU, Ş., CRĂCIUNESCU, M., &
ANGHEL, M. (2015, APRIL). USING IOT COMMUNICATION
INFRASTRUCTURE FOR IMPROVING PERFORMANCE OF POWER
MICROGRIDS. IN 2018 5TH INTERNATIONAL CONFERENCE ON
CONTROL, DECISION AND INFORMATION TECHNOLOGIES
(CODIT) (PP. 482-487). IEEE.
DORRI, A., KANHERE, S. S., JURDAK, R., & GAURAVARAM,
P. (2017, MARCH). BLOCKCHAIN FOR IOT SECURITY AND
PRIVACY: THE CASE STUDY OF SMART TRASPOTION. IN
PERVASIVE COMPUTING AND COMMUNICATIONS WORKSHOPS
(PERCOM WORKSHOPS), 2017 IEEE INTERNATIONAL
CONFERENCE ON (PP. 618-623). IEEE.
FAROOQ, M. U., WASEEM, M., KHAIRI, A., & MAZHAR, S.
(2017). A CRITICAL ANALYSIS ON THE SECURITY CONCERNS
OF INTERNET OF THINGS (IOT). INTERNATIONAL JOURNAL OF
COMPUTER APPLICATIONS, 111(7).
FRÄDRICH, C., PÖHLS, H. C., POPP, W., RAKOTONDRAVONY,
N., & SAMELIN, K. (2016, NOVEMBER). INTEGRITY AND
AUTHENTICITY PROTECTION WITH SELECTIVE DISCLOSURE
CONTROL IN THE CLOUD & IOT. IN INTERNATIONAL
CONFERENCE ON INFORMATION AND COMMUNICATIONS
SECURITY (PP. 197-213). SPRINGER, CHAM.
HOFHEINZ, D., & JAGER, T. (2016). TIGHTLY SECURE
SIGNATURES AND PUBLIC-KEY ENCRYPTION. DESIGNS, CODES
AND CRYPTOGRAPHY, 80(1), 29-61.
HUANG, X., CRAIG, P., LIN, H., & YAN, Z. (2015). SECIOT:
A SECURITY FRAMEWORK FOR THE INTERNET OF THINGS.
SECURITY AND COMMUNICATION NETWORKS, 9(16), 3083-
3094.
JAN, S. R., KHAN, F., ULLAH, F., AZIM, N., & TAHIR, M.
(2016). USING COAP PROTOCOL FOR RESOURCE
OBSERVATION IN IOT. INTERNATIONAL JOURNAL OF
EMERGING TECHNOLOGY IN COMPUTER SCIENCE &
ELECTRONICS, ISSN, 0976-1353.
LEE, Y. S., ALASAARELA, E., & LEE, H. (2014, FEBRUARY).
SECURE KEY MANAGEMENT SCHEME BASED ON ECC
ALGORITHM IN TRANSPORTATION SYSTEM. IN INFORMATION
NETWORKING (ICOIN), 2014 INTERNATIONAL CONFERENCE
ON (PP. 453-457). IEEE.
huge potential in transforming the transportation system.
However there are several challenges as of now to realize
the potential of the technology. The major challenges are
the challenges regarding the authentication the data security
and the communication between devices of the IOT
connected objects in the network. Although there are
several technology for authentication of the device, but not
all are efficient. The most efficient technology for device
authentication in the IOT network is the RFID technology
as it considers the IOT device constraints such as the
limited memory, processing power and the power
consumption. Among the communication protocols that are
popular for communicating over the internet the protocol
that is most appropriate considering the highly constraint
environment of the IOT devices is the COAP protocol as it
is secure, less power consuming and require less memory to
execute which is ideal for IOT applications. However it
should be noted that as technology is getting more and
more advanced and several new technology is being
discovered, there is no fix preference for the ideal
technology and the list is subject to change. Hence it is
appropriate to consider that some technology might be
preferable for now but it is likely to change as new
technology provides solution that better and improved than
the previous technology. Hence there is always scope for
future research in this domain.
REFERENCES
AL-SARAWI, S., ANBAR, M., ALIEYAN, K., & ALZUBAIDI, M.
(2015, MAY). INTERNET OF THINGS (IOT) COMMUNICATION
PROTOCOLS. IN INFORMATION TECHNOLOGY (ICIT), 2017
8TH INTERNATIONAL CONFERENCE ON (PP. 685-690). IEEE.
DOBRESCU, R., MOCANU, Ş., CRĂCIUNESCU, M., &
ANGHEL, M. (2015, APRIL). USING IOT COMMUNICATION
INFRASTRUCTURE FOR IMPROVING PERFORMANCE OF POWER
MICROGRIDS. IN 2018 5TH INTERNATIONAL CONFERENCE ON
CONTROL, DECISION AND INFORMATION TECHNOLOGIES
(CODIT) (PP. 482-487). IEEE.
DORRI, A., KANHERE, S. S., JURDAK, R., & GAURAVARAM,
P. (2017, MARCH). BLOCKCHAIN FOR IOT SECURITY AND
PRIVACY: THE CASE STUDY OF SMART TRASPOTION. IN
PERVASIVE COMPUTING AND COMMUNICATIONS WORKSHOPS
(PERCOM WORKSHOPS), 2017 IEEE INTERNATIONAL
CONFERENCE ON (PP. 618-623). IEEE.
FAROOQ, M. U., WASEEM, M., KHAIRI, A., & MAZHAR, S.
(2017). A CRITICAL ANALYSIS ON THE SECURITY CONCERNS
OF INTERNET OF THINGS (IOT). INTERNATIONAL JOURNAL OF
COMPUTER APPLICATIONS, 111(7).
FRÄDRICH, C., PÖHLS, H. C., POPP, W., RAKOTONDRAVONY,
N., & SAMELIN, K. (2016, NOVEMBER). INTEGRITY AND
AUTHENTICITY PROTECTION WITH SELECTIVE DISCLOSURE
CONTROL IN THE CLOUD & IOT. IN INTERNATIONAL
CONFERENCE ON INFORMATION AND COMMUNICATIONS
SECURITY (PP. 197-213). SPRINGER, CHAM.
HOFHEINZ, D., & JAGER, T. (2016). TIGHTLY SECURE
SIGNATURES AND PUBLIC-KEY ENCRYPTION. DESIGNS, CODES
AND CRYPTOGRAPHY, 80(1), 29-61.
HUANG, X., CRAIG, P., LIN, H., & YAN, Z. (2015). SECIOT:
A SECURITY FRAMEWORK FOR THE INTERNET OF THINGS.
SECURITY AND COMMUNICATION NETWORKS, 9(16), 3083-
3094.
JAN, S. R., KHAN, F., ULLAH, F., AZIM, N., & TAHIR, M.
(2016). USING COAP PROTOCOL FOR RESOURCE
OBSERVATION IN IOT. INTERNATIONAL JOURNAL OF
EMERGING TECHNOLOGY IN COMPUTER SCIENCE &
ELECTRONICS, ISSN, 0976-1353.
LEE, Y. S., ALASAARELA, E., & LEE, H. (2014, FEBRUARY).
SECURE KEY MANAGEMENT SCHEME BASED ON ECC
ALGORITHM IN TRANSPORTATION SYSTEM. IN INFORMATION
NETWORKING (ICOIN), 2014 INTERNATIONAL CONFERENCE
ON (PP. 453-457). IEEE.

LI, C. T., LEE, C. C., WENG, C. Y., & CHEN, C. M. (2018).
TOWARDS SECURE AUTHENTICATING OF CACHE IN THE
READER FOR RFID-BASED IOT SYSTEMS. PEER-TO-PEER
NETWORKING AND APPLICATIONS, 11(1), 198-208.
LI, X., WANG, H., YU, Y., & QIAN, C. (2017, APRIL). AN
IOT DATA COMMUNICATION FRAMEWORK FOR
AUTHENTICITY AND INTEGRITY. IN INTERNET-OF-THINGS
DESIGN AND IMPLEMENTATION (IOTDI), 2017 IEEE/ACM
SECOND INTERNATIONAL CONFERENCE ON (PP. 159-170).
IEEE.
LOPES, A.P.G. AND HILGERT, L.D.O., 2017. GROUP
AUTHENTICATION PROTOCOLS FOR INTERNET OF THINGS
(IOT)–QOS AND SECURITY PROPERTIES EVALUATION.
TAPPLER, M., AICHERNIG, B. K., & BLOEM, R. (2015,
MARCH). MODEL-BASED TESTING IOT COMMUNICATION VIA
ACTIVE AUTOMATA LEARNING. IN SOFTWARE TESTING,
VERIFICATION AND VALIDATION (ICST), 2017 IEEE
INTERNATIONAL CONFERENCE ON (PP. 276-287). IEEE.
TAYEB, S., LATIFI, S., & KIM, Y. (2015, JANUARY). A
SURVEY ON IOT COMMUNICATION AND COMPUTATION
FRAMEWORKS: AN INDUSTRIAL PERSPECTIVE. IN COMPUTING
AND COMMUNICATION WORKSHOP AND CONFERENCE
(CCWC), 2017 IEEE 7TH ANNUAL (PP. 1-6). IEEE.
ZHANG, Z. K., CHO, M. C. Y., WANG, C. W., HSU, C. W.,
CHEN, C. K., & SHIEH, S. (2016, NOVEMBER). IOT
SECURITY: ONGOING CHALLENGES AND RESEARCH
OPPORTUNITIES. IN SERVICE-ORIENTED COMPUTING AND
APPLICATIONS (SOCA), 2014 IEEE 7TH INTERNATIONAL
CONFERENCE ON (PP. 230-234). IEEE.
TOWARDS SECURE AUTHENTICATING OF CACHE IN THE
READER FOR RFID-BASED IOT SYSTEMS. PEER-TO-PEER
NETWORKING AND APPLICATIONS, 11(1), 198-208.
LI, X., WANG, H., YU, Y., & QIAN, C. (2017, APRIL). AN
IOT DATA COMMUNICATION FRAMEWORK FOR
AUTHENTICITY AND INTEGRITY. IN INTERNET-OF-THINGS
DESIGN AND IMPLEMENTATION (IOTDI), 2017 IEEE/ACM
SECOND INTERNATIONAL CONFERENCE ON (PP. 159-170).
IEEE.
LOPES, A.P.G. AND HILGERT, L.D.O., 2017. GROUP
AUTHENTICATION PROTOCOLS FOR INTERNET OF THINGS
(IOT)–QOS AND SECURITY PROPERTIES EVALUATION.
TAPPLER, M., AICHERNIG, B. K., & BLOEM, R. (2015,
MARCH). MODEL-BASED TESTING IOT COMMUNICATION VIA
ACTIVE AUTOMATA LEARNING. IN SOFTWARE TESTING,
VERIFICATION AND VALIDATION (ICST), 2017 IEEE
INTERNATIONAL CONFERENCE ON (PP. 276-287). IEEE.
TAYEB, S., LATIFI, S., & KIM, Y. (2015, JANUARY). A
SURVEY ON IOT COMMUNICATION AND COMPUTATION
FRAMEWORKS: AN INDUSTRIAL PERSPECTIVE. IN COMPUTING
AND COMMUNICATION WORKSHOP AND CONFERENCE
(CCWC), 2017 IEEE 7TH ANNUAL (PP. 1-6). IEEE.
ZHANG, Z. K., CHO, M. C. Y., WANG, C. W., HSU, C. W.,
CHEN, C. K., & SHIEH, S. (2016, NOVEMBER). IOT
SECURITY: ONGOING CHALLENGES AND RESEARCH
OPPORTUNITIES. IN SERVICE-ORIENTED COMPUTING AND
APPLICATIONS (SOCA), 2014 IEEE 7TH INTERNATIONAL
CONFERENCE ON (PP. 230-234). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



