Comprehensive Report: IS Security and Risk Management for Telstra
VerifiedAdded on 2021/06/16
|16
|3835
|67
Report
AI Summary
This report provides a comprehensive analysis of Information System (IS) security and risk management within Telstra Corporation Ltd. It begins by defining IS and its role in organizations, then delves into the specific threats and malware affecting Telstra's operations, including adware, bots, bugs, and ransomware. The report identifies and examines three types of network devices used by Telstra: routers, modems, and Ethernet hubs, highlighting their vulnerabilities. It then assesses the reliability and availability of Telstra's web services, hosted on Windows Server 2012, and discusses strategies for ensuring confidentiality and integrity in staff email using Microsoft Exchange. The report prioritizes threats, malware types, and security issues, proposing approaches to improve web and email server availability. It also examines the impact of organizational issues and human factors on IS management, illustrates log records, and discusses the utilization of audit log records. Finally, it outlines five types of network security devices used to control security and provides conclusions and recommendations for improving Telstra's IS security and risk management practices.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management: Telstra
Name of the Student
Name of the University
Author’s Note:
IS Security and Risk Management: Telstra
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................3
1. Most Common Malware Affecting Organizational Operations.........................................3
2. Three Types of Network Devices Used by Telstra............................................................4
3. Reliability and Availability of Web Service......................................................................5
4. Ensuring Confidentiality and Integrity for Staff Email......................................................6
5. Prioritization of Threats, Malware Types and Security Issues..........................................7
6. Two Approaches for Improving Availability of Web and Email Servers.........................7
7. Impact of Organizational Issues and Human Factors on IS Management.........................9
8. Illustration of Log Records..............................................................................................10
9. Utilization of Audit Log Records for Email and Web Server Issues...............................10
10. Five types of Network Security Devices for Controlling Security................................11
Conclusions and Recommendations........................................................................................11
References................................................................................................................................13
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................3
1. Most Common Malware Affecting Organizational Operations.........................................3
2. Three Types of Network Devices Used by Telstra............................................................4
3. Reliability and Availability of Web Service......................................................................5
4. Ensuring Confidentiality and Integrity for Staff Email......................................................6
5. Prioritization of Threats, Malware Types and Security Issues..........................................7
6. Two Approaches for Improving Availability of Web and Email Servers.........................7
7. Impact of Organizational Issues and Human Factors on IS Management.........................9
8. Illustration of Log Records..............................................................................................10
9. Utilization of Audit Log Records for Email and Web Server Issues...............................10
10. Five types of Network Security Devices for Controlling Security................................11
Conclusions and Recommendations........................................................................................11
References................................................................................................................................13

2
IS SECURITY AND RISK MANAGEMENT
Introduction
An IS or information system is the specific organized system that is utilized for the
purposes of collection, organization, communication, storing and finally manipulation of data
or information (Laudon & Laudon, 2016). It is the proper collection of various
complementary networks, which any organization or individual utilizes to filter, create,
process, collect and distribute information. This particular group of elements interact with
each other for properly producing information. The internal information is mainly focused
with this information system and not the external information. This software is used for
running a fully computerized database or any computer system. All types of data operations
are much easier with IS or information system (Bajdor & Grabara, 2014). The overall
management, business operations and decision making process is supported with information
system and it is the subset of information and communications technology.
The following report outlines a brief discussion on the entire concept of information
system for the popular Australian telecommunications organization, Telstra Corporation Ltd.
This organization is eventually responsible for building as well as operating several
telecommunication networks, internet access, mobile, television services, entertainment
services, products and many more. It is considered as the largest organization of
telecommunications in Australia. It provides information system services to its employees
and customers. This report will be demonstrating on the various threats and malware that
affect the operations of this organization. Moreover, the various network devices and relevant
details will be eventually provided here. Various recommendations will also be provided in
this report.
IS SECURITY AND RISK MANAGEMENT
Introduction
An IS or information system is the specific organized system that is utilized for the
purposes of collection, organization, communication, storing and finally manipulation of data
or information (Laudon & Laudon, 2016). It is the proper collection of various
complementary networks, which any organization or individual utilizes to filter, create,
process, collect and distribute information. This particular group of elements interact with
each other for properly producing information. The internal information is mainly focused
with this information system and not the external information. This software is used for
running a fully computerized database or any computer system. All types of data operations
are much easier with IS or information system (Bajdor & Grabara, 2014). The overall
management, business operations and decision making process is supported with information
system and it is the subset of information and communications technology.
The following report outlines a brief discussion on the entire concept of information
system for the popular Australian telecommunications organization, Telstra Corporation Ltd.
This organization is eventually responsible for building as well as operating several
telecommunication networks, internet access, mobile, television services, entertainment
services, products and many more. It is considered as the largest organization of
telecommunications in Australia. It provides information system services to its employees
and customers. This report will be demonstrating on the various threats and malware that
affect the operations of this organization. Moreover, the various network devices and relevant
details will be eventually provided here. Various recommendations will also be provided in
this report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IS SECURITY AND RISK MANAGEMENT
Discussion
1. Most Common Malware Affecting Organizational Operations
Malware or malicious software can be defined as the variety of several intrusive
software or hostile forms (Gallagher & Sixsmith, 2014). The basic types of intrusive software
are computer viruses, Trojan horses, spyware, ransom ware and many more. It is considered
as one of the most dangerous software that causes problems for the business operations. This
type of malicious activity could easily task up the form of executable code or scripts. It
comprises of malicious intent that are eventually acting against any type of requirement for
the computer users. Malware is vulnerable to all types of organizations and Telstra is one of
them (Arvidsson, Holmström & Lyytinen, 2014). The basic malware threats that
subsequently affect the information system as well as organizational operations of Telstra are
as follows:
i) Adware: The first and the foremost type of malware that is dangerous for the
organizational operations of Telstra Corporation Ltd. is adware. It is the short form of
advertising supported software. This typical software is responsible for automatically
delivering advertisements (Klukas, Chen & Pape, 2014). The most significant examples of
this adware mainly include several pop up ads that come on the websites or advertisements,
which are displayed by the software. For the added capabilities of the spyware, the bundles
are extremely dangerous than this adware. The organizational operations of Telstra are highly
affected by this malware.
ii) Bots: The second important malware type is bot. These are specific software
programs that are eventually created for performing significant operations. Although, few
bots are created for harmless purposes like internet auctions or video gaming, most of them
IS SECURITY AND RISK MANAGEMENT
Discussion
1. Most Common Malware Affecting Organizational Operations
Malware or malicious software can be defined as the variety of several intrusive
software or hostile forms (Gallagher & Sixsmith, 2014). The basic types of intrusive software
are computer viruses, Trojan horses, spyware, ransom ware and many more. It is considered
as one of the most dangerous software that causes problems for the business operations. This
type of malicious activity could easily task up the form of executable code or scripts. It
comprises of malicious intent that are eventually acting against any type of requirement for
the computer users. Malware is vulnerable to all types of organizations and Telstra is one of
them (Arvidsson, Holmström & Lyytinen, 2014). The basic malware threats that
subsequently affect the information system as well as organizational operations of Telstra are
as follows:
i) Adware: The first and the foremost type of malware that is dangerous for the
organizational operations of Telstra Corporation Ltd. is adware. It is the short form of
advertising supported software. This typical software is responsible for automatically
delivering advertisements (Klukas, Chen & Pape, 2014). The most significant examples of
this adware mainly include several pop up ads that come on the websites or advertisements,
which are displayed by the software. For the added capabilities of the spyware, the bundles
are extremely dangerous than this adware. The organizational operations of Telstra are highly
affected by this malware.
ii) Bots: The second important malware type is bot. These are specific software
programs that are eventually created for performing significant operations. Although, few
bots are created for harmless purposes like internet auctions or video gaming, most of them
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IS SECURITY AND RISK MANAGEMENT
are created for introducing vulnerabilities within the systems (Li, Hsieh & Rai, 2013). These
malware are utilized as botnets for the DDoS attacks.
iii) Bug: A bug is the typical flaw that is responsible for producing an undesired
result. These flaws are human errors and always exist within source code and compiler. The
organizational operations are highly affected by this type of malware (Kadam & Onkar,
2015). The security bugs are the most dangerous types of bugs for allowing the attackers to
stop the authentication of users.
iv) Ransomware: It is the form of malware, holding a system captive for demanding a
ransom. This type of malware eventually restricts the access of the users with the help of
encryption of files within the hard drive or also locking the system (Stojmenovic & Wen,
2014). The user does not get any idea about the malware and gets trapped in the malware
effect.
2. Three Types of Network Devices Used by Telstra
Telstra provides information system services to the users. Thus, they are always
vulnerable to various attacks. Moreover, they utilize three distinct types of network devices
within their organization (Hashizume et al., 2013). These network devices always have the
risk to be exploited by various types of threats or malware. The three types of network
devices that the organization of Telstra is using as follows:
i) Routers: The first type of network device that Telstra uses is router. It is the device,
which helps in forwarding data packets between various computer networks. These routers
are responsible for performing the traffic functions over the Internet (Power, Sharda &
Burstein, 2015). The data packet is eventually forwarded from any one router to the other.
The router is being connected to several data lines from the various networks. It is considered
IS SECURITY AND RISK MANAGEMENT
are created for introducing vulnerabilities within the systems (Li, Hsieh & Rai, 2013). These
malware are utilized as botnets for the DDoS attacks.
iii) Bug: A bug is the typical flaw that is responsible for producing an undesired
result. These flaws are human errors and always exist within source code and compiler. The
organizational operations are highly affected by this type of malware (Kadam & Onkar,
2015). The security bugs are the most dangerous types of bugs for allowing the attackers to
stop the authentication of users.
iv) Ransomware: It is the form of malware, holding a system captive for demanding a
ransom. This type of malware eventually restricts the access of the users with the help of
encryption of files within the hard drive or also locking the system (Stojmenovic & Wen,
2014). The user does not get any idea about the malware and gets trapped in the malware
effect.
2. Three Types of Network Devices Used by Telstra
Telstra provides information system services to the users. Thus, they are always
vulnerable to various attacks. Moreover, they utilize three distinct types of network devices
within their organization (Hashizume et al., 2013). These network devices always have the
risk to be exploited by various types of threats or malware. The three types of network
devices that the organization of Telstra is using as follows:
i) Routers: The first type of network device that Telstra uses is router. It is the device,
which helps in forwarding data packets between various computer networks. These routers
are responsible for performing the traffic functions over the Internet (Power, Sharda &
Burstein, 2015). The data packet is eventually forwarded from any one router to the other.
The router is being connected to several data lines from the various networks. It is considered

5
IS SECURITY AND RISK MANAGEMENT
as one of the most important networking device that is being used by Telstra. Router helps
the organization in successfully performing all the networking operations.
ii) Modems: The second networking device that this organization is using within their
business is modem (Ifinedo, 2014). This particular device eventually modulates each and
every carrier wave signal for the purpose of encoding digital information to transmit as well
as demodulate and finally decoding the original data.
iii) Ethernet Hubs: The third significant network device that Telstra is utilizing for
their business is Ethernet hub. It is the network hardware device to connect several Ethernet
devices for making all of them acting together as the single network segment.
These above mentioned devices are vulnerable to various threats, destruction, abuse,
system quality issues and errors (Crossler et al., 2013). The main reasons of the
vulnerabilities of all these network devices include lack of firewalls within the devices. The
lack of proper security measures of all these devices are the most important reasons for these
vulnerabilities.
3. Reliability and Availability of Web Service
Telstra Corporation Ltd. is utilizing Windows Server 2012 for the purpose of hosting
the specific organizational web site. The most significant requirements of this particular web
server are reliability and availability (Peltier, 2013). The term reliability refers to the
significant capability of any computer related software or hardware for consistently
performing as per the specifications. The reliability of the Windows Server 2012 mainly
depends on the performance of the web site. The most significant factors for the
determination of reliability of this server are as follows:
i) The first factor is that Internet connectivity is constant to the server.
IS SECURITY AND RISK MANAGEMENT
as one of the most important networking device that is being used by Telstra. Router helps
the organization in successfully performing all the networking operations.
ii) Modems: The second networking device that this organization is using within their
business is modem (Ifinedo, 2014). This particular device eventually modulates each and
every carrier wave signal for the purpose of encoding digital information to transmit as well
as demodulate and finally decoding the original data.
iii) Ethernet Hubs: The third significant network device that Telstra is utilizing for
their business is Ethernet hub. It is the network hardware device to connect several Ethernet
devices for making all of them acting together as the single network segment.
These above mentioned devices are vulnerable to various threats, destruction, abuse,
system quality issues and errors (Crossler et al., 2013). The main reasons of the
vulnerabilities of all these network devices include lack of firewalls within the devices. The
lack of proper security measures of all these devices are the most important reasons for these
vulnerabilities.
3. Reliability and Availability of Web Service
Telstra Corporation Ltd. is utilizing Windows Server 2012 for the purpose of hosting
the specific organizational web site. The most significant requirements of this particular web
server are reliability and availability (Peltier, 2013). The term reliability refers to the
significant capability of any computer related software or hardware for consistently
performing as per the specifications. The reliability of the Windows Server 2012 mainly
depends on the performance of the web site. The most significant factors for the
determination of reliability of this server are as follows:
i) The first factor is that Internet connectivity is constant to the server.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IS SECURITY AND RISK MANAGEMENT
ii) The second factor for determining reliability is the maintenance of stability of
server hardware as well as software systems.
iii) The final factor to properly determine the reliability of Windows Server 2012 is
the environmental as well as power stability in the hosting facility (Cheminod, Durante &
Valenzano, 2013).
For determining the availability of the Windows Server 2012 are as follows:
i) The first factor is that the web server is constantly available for the organization.
ii) The second factor is that the web server is periodically maintained and thus
Windows Server 2012 is utilized by all (Singhal et al., 2013).
4. Ensuring Confidentiality and Integrity for Staff Email
Telstra Corporation Ltd. is using the Microsoft Exchange server for providing the
email services to all of their staffs. It is considered as one of the most effective or popular
mail server that is being developed by Microsoft (Ahmed & Hossain, 2014). The operating
system is Windows Server. There are various versions of this Microsoft Exchange Server.
The most important factors of this mail server are to ensure confidentiality as well as integrity
to the clients.
For ensuring confidentiality amongst the emails of Telstra, there are few factors. The
first and the foremost factor to ensure confidentiality for Microsoft Exchange Server is that
the emails are not read by any unauthorized person (Rong, Nguyen & Jaatun, 2013). The
authorization or authentication is solely maintained by the factor of confidentiality.
Encryption is another significant factor of the confidentiality of this Microsoft Exchange.
Integrity is the second important feature of Microsoft Exchange server. This feature
ensures that the data does not lose its integrity and the hackers do not change the data and
IS SECURITY AND RISK MANAGEMENT
ii) The second factor for determining reliability is the maintenance of stability of
server hardware as well as software systems.
iii) The final factor to properly determine the reliability of Windows Server 2012 is
the environmental as well as power stability in the hosting facility (Cheminod, Durante &
Valenzano, 2013).
For determining the availability of the Windows Server 2012 are as follows:
i) The first factor is that the web server is constantly available for the organization.
ii) The second factor is that the web server is periodically maintained and thus
Windows Server 2012 is utilized by all (Singhal et al., 2013).
4. Ensuring Confidentiality and Integrity for Staff Email
Telstra Corporation Ltd. is using the Microsoft Exchange server for providing the
email services to all of their staffs. It is considered as one of the most effective or popular
mail server that is being developed by Microsoft (Ahmed & Hossain, 2014). The operating
system is Windows Server. There are various versions of this Microsoft Exchange Server.
The most important factors of this mail server are to ensure confidentiality as well as integrity
to the clients.
For ensuring confidentiality amongst the emails of Telstra, there are few factors. The
first and the foremost factor to ensure confidentiality for Microsoft Exchange Server is that
the emails are not read by any unauthorized person (Rong, Nguyen & Jaatun, 2013). The
authorization or authentication is solely maintained by the factor of confidentiality.
Encryption is another significant factor of the confidentiality of this Microsoft Exchange.
Integrity is the second important feature of Microsoft Exchange server. This feature
ensures that the data does not lose its integrity and the hackers do not change the data and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IS SECURITY AND RISK MANAGEMENT
hence the integrity is properly maintained (Willcocks, 2013). Data integrity is extremely
important for any mail server and thus Telstra is benefitted from this server.
5. Prioritization of Threats, Malware Types and Security Issues
The staff members of the IT department of this organization, Telstra have reported
that there are problems in the web mail or web server. There are various threats, malware that
are dangerous for the web server or web mail (Stair & Reynolds, 2013). The several
important threats or malware as per their priorities are as follows:
i) Virus: The most dangerous threat to the web server or web mail is virus. It is the
kind of malicious software program or malware, which when is executed, eventually
replicates itself with the help of modification of any other computer program and thus
insertion of own code.
ii) Phishing: It is the significant attempt for obtaining confidential information or data
like usernames, passwords or mail details by means of disguising as the most trustworthy
entity (Lee, 2014).
iii) Email Spoofing: It is the threat for creating email messages with the help of a
forged sender address. It loses authenticity.
iv) Spamming: Email spam is the e spam where all the unsolicited messages are being
sent.
6. Two Approaches for Improving Availability of Web and Email Servers
The IT business continuity is ensured by providing redundancy and fault tolerance.
The availability of the web servers as well as email servers of Telstra Corporation Ltd. could
be easily improved with the help of two significant approaches (Laudon & Laudon, 2016).
The two approaches are as follows:
IS SECURITY AND RISK MANAGEMENT
hence the integrity is properly maintained (Willcocks, 2013). Data integrity is extremely
important for any mail server and thus Telstra is benefitted from this server.
5. Prioritization of Threats, Malware Types and Security Issues
The staff members of the IT department of this organization, Telstra have reported
that there are problems in the web mail or web server. There are various threats, malware that
are dangerous for the web server or web mail (Stair & Reynolds, 2013). The several
important threats or malware as per their priorities are as follows:
i) Virus: The most dangerous threat to the web server or web mail is virus. It is the
kind of malicious software program or malware, which when is executed, eventually
replicates itself with the help of modification of any other computer program and thus
insertion of own code.
ii) Phishing: It is the significant attempt for obtaining confidential information or data
like usernames, passwords or mail details by means of disguising as the most trustworthy
entity (Lee, 2014).
iii) Email Spoofing: It is the threat for creating email messages with the help of a
forged sender address. It loses authenticity.
iv) Spamming: Email spam is the e spam where all the unsolicited messages are being
sent.
6. Two Approaches for Improving Availability of Web and Email Servers
The IT business continuity is ensured by providing redundancy and fault tolerance.
The availability of the web servers as well as email servers of Telstra Corporation Ltd. could
be easily improved with the help of two significant approaches (Laudon & Laudon, 2016).
The two approaches are as follows:
8
IS SECURITY AND RISK MANAGEMENT
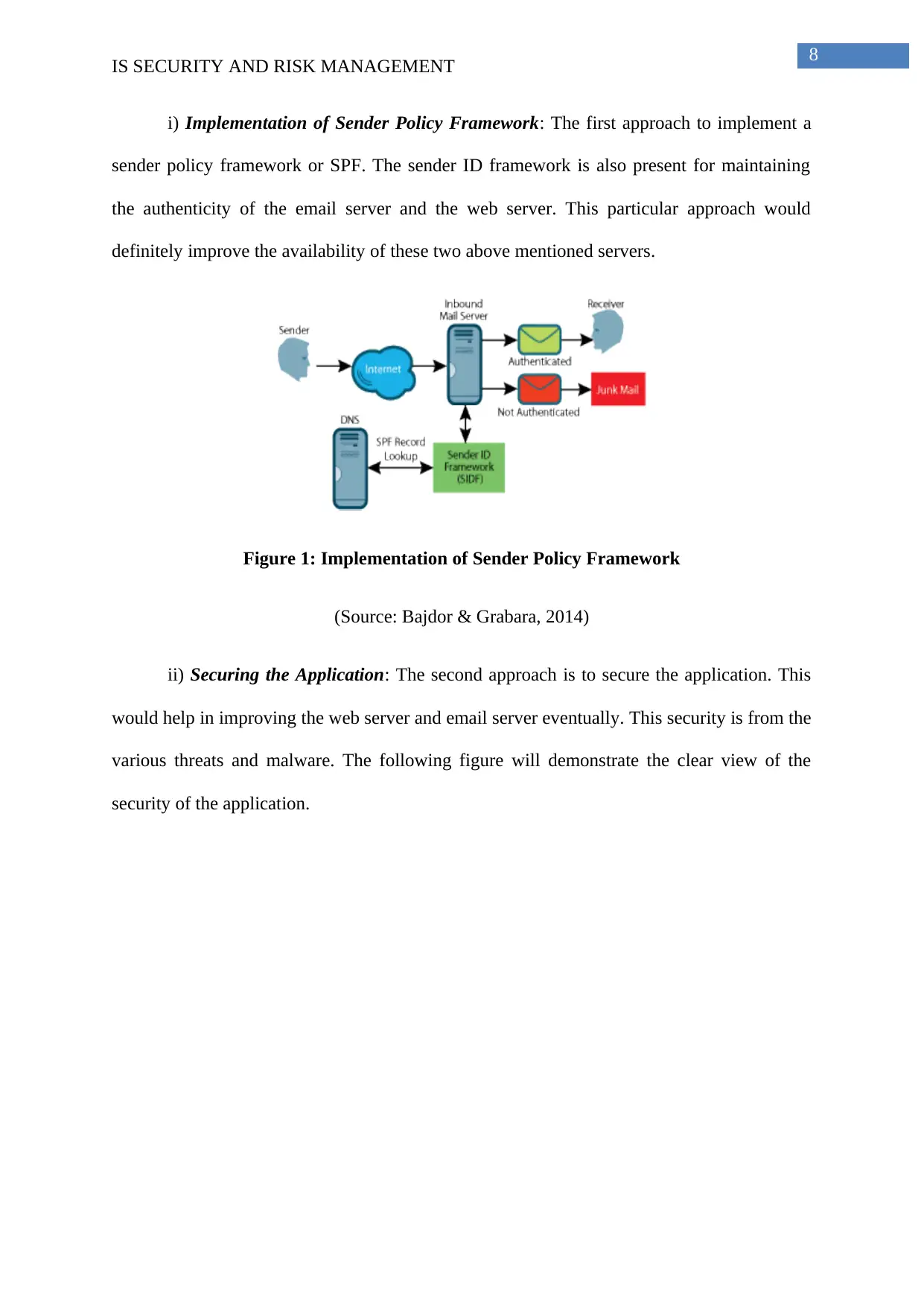
i) Implementation of Sender Policy Framework: The first approach to implement a
sender policy framework or SPF. The sender ID framework is also present for maintaining
the authenticity of the email server and the web server. This particular approach would
definitely improve the availability of these two above mentioned servers.
Figure 1: Implementation of Sender Policy Framework
(Source: Bajdor & Grabara, 2014)
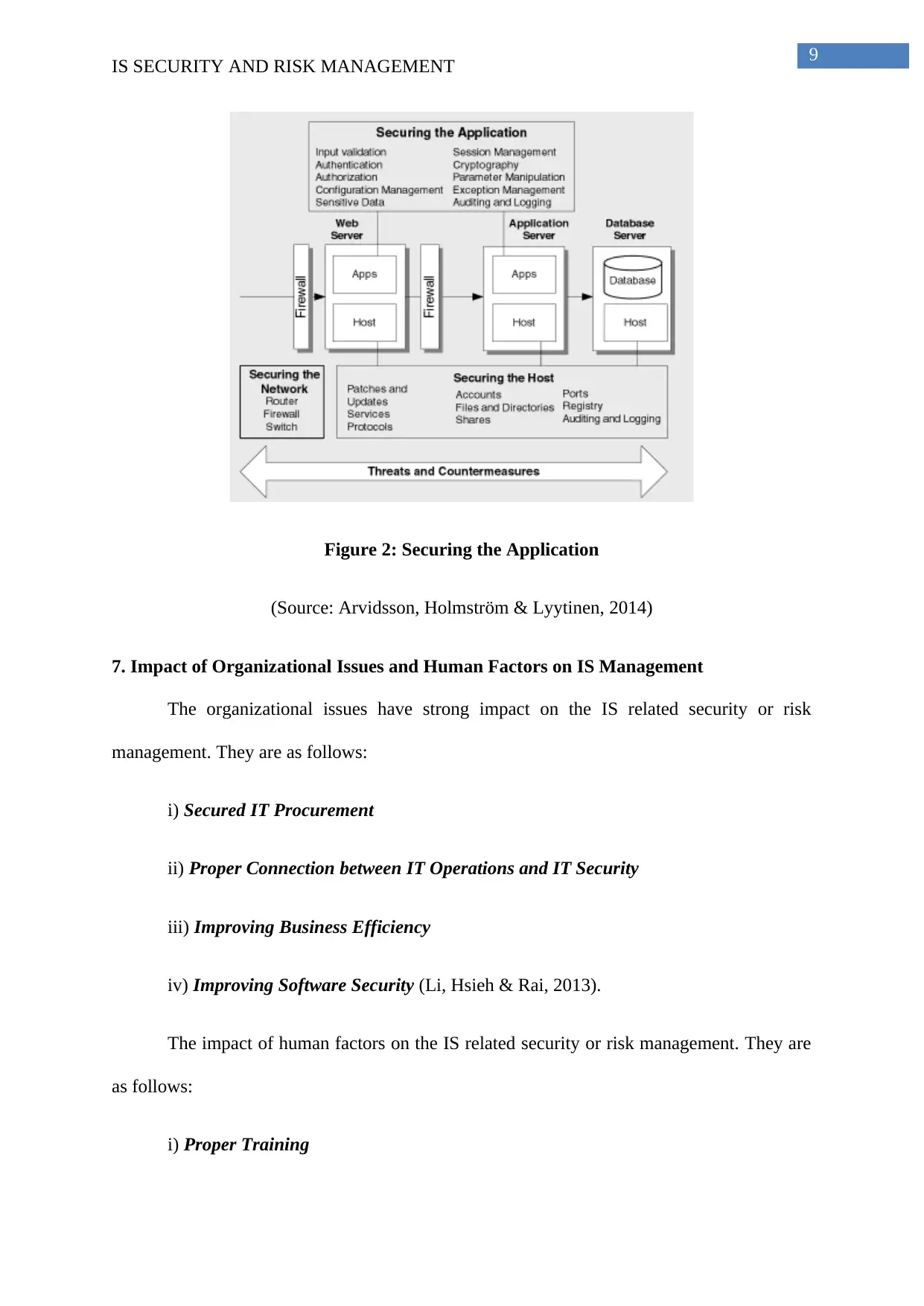
ii) Securing the Application: The second approach is to secure the application. This
would help in improving the web server and email server eventually. This security is from the
various threats and malware. The following figure will demonstrate the clear view of the
security of the application.
IS SECURITY AND RISK MANAGEMENT
i) Implementation of Sender Policy Framework: The first approach to implement a
sender policy framework or SPF. The sender ID framework is also present for maintaining
the authenticity of the email server and the web server. This particular approach would
definitely improve the availability of these two above mentioned servers.
Figure 1: Implementation of Sender Policy Framework
(Source: Bajdor & Grabara, 2014)
ii) Securing the Application: The second approach is to secure the application. This
would help in improving the web server and email server eventually. This security is from the
various threats and malware. The following figure will demonstrate the clear view of the
security of the application.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
IS SECURITY AND RISK MANAGEMENT
Figure 2: Securing the Application
(Source: Arvidsson, Holmström & Lyytinen, 2014)
7. Impact of Organizational Issues and Human Factors on IS Management
The organizational issues have strong impact on the IS related security or risk
management. They are as follows:
i) Secured IT Procurement
ii) Proper Connection between IT Operations and IT Security
iii) Improving Business Efficiency
iv) Improving Software Security (Li, Hsieh & Rai, 2013).
The impact of human factors on the IS related security or risk management. They are
as follows:
i) Proper Training
IS SECURITY AND RISK MANAGEMENT
Figure 2: Securing the Application
(Source: Arvidsson, Holmström & Lyytinen, 2014)
7. Impact of Organizational Issues and Human Factors on IS Management
The organizational issues have strong impact on the IS related security or risk
management. They are as follows:
i) Secured IT Procurement
ii) Proper Connection between IT Operations and IT Security
iii) Improving Business Efficiency
iv) Improving Software Security (Li, Hsieh & Rai, 2013).
The impact of human factors on the IS related security or risk management. They are
as follows:
i) Proper Training
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IS SECURITY AND RISK MANAGEMENT
ii) Awareness
iii) Security culture influence
iv) Knowing Organizational Strengths and Weaknesses.
8. Illustration of Log Records
The various log records in the organization of Telstra Corporation Ltd. are utilized for
the purpose of monitoring or analyzing the web server as well as email server (Peltier, 2013).
These log records mainly include the security, access and event. The most common functions
of the log records are AlignReservedLog, AllocReservedLog, CreateLogFile, DeleteLogFile
and many more. The AlignReservedLog helps in calculating the aligned reservation size for
various records. AllocReservedLog helps in allocating the aligned space for the set of
reserved records. CreateLogFile and DeleteLogFile are used for creating as well as deleting a
log file (Willcocks, 2013). The security, access and event of the log records help in
monitoring and analyzing the problems of web server and email servers.
9. Utilization of Audit Log Records for Email and Web Server Issues
The audit log reports are used by Telstra for the better performance of audit analysis
and thus supporting the internal investigations of the organization and indenting the
operational trends or log term problems. The audit log record is the security relevant
chronological set of records, which eventually provide the documentary evidence for the
activity sequence affecting at the specific process, event or operation (Stair & Reynolds,
2013). The web server and the email server issues are easily solved with the help of this audit
log record. There are various activities like scientific research or financial transactions for the
staffs, systems and accounts of the Telstra organization. Since, it is a telecommunication
company, audit log records are extremely important for them for both the attempted as well
IS SECURITY AND RISK MANAGEMENT
ii) Awareness
iii) Security culture influence
iv) Knowing Organizational Strengths and Weaknesses.
8. Illustration of Log Records
The various log records in the organization of Telstra Corporation Ltd. are utilized for
the purpose of monitoring or analyzing the web server as well as email server (Peltier, 2013).
These log records mainly include the security, access and event. The most common functions
of the log records are AlignReservedLog, AllocReservedLog, CreateLogFile, DeleteLogFile
and many more. The AlignReservedLog helps in calculating the aligned reservation size for
various records. AllocReservedLog helps in allocating the aligned space for the set of
reserved records. CreateLogFile and DeleteLogFile are used for creating as well as deleting a
log file (Willcocks, 2013). The security, access and event of the log records help in
monitoring and analyzing the problems of web server and email servers.
9. Utilization of Audit Log Records for Email and Web Server Issues
The audit log reports are used by Telstra for the better performance of audit analysis
and thus supporting the internal investigations of the organization and indenting the
operational trends or log term problems. The audit log record is the security relevant
chronological set of records, which eventually provide the documentary evidence for the
activity sequence affecting at the specific process, event or operation (Stair & Reynolds,
2013). The web server and the email server issues are easily solved with the help of this audit
log record. There are various activities like scientific research or financial transactions for the
staffs, systems and accounts of the Telstra organization. Since, it is a telecommunication
company, audit log records are extremely important for them for both the attempted as well

11
IS SECURITY AND RISK MANAGEMENT
as completed accesses and services. The transactions are also traced by this. Hence, it is
extremely important.
10. Five types of Network Security Devices for Controlling Security
The five types of network security devices that are effective for the proper control of
security and threat mitigation for the organization of Telstra Corporation Ltd. are as follows:
i) Network Switch: This network device works at the layer of LAN for the purpose of
filtering the packets and finally sending them to the interface (Lee, 2014).
ii) Bridge: The second type is the bridge. When any router connects two separate
network types, a specific bridge is used for the connection of two subnetworks. This helps to
control the security.
iii) Repeater: the next network security device is repeater. It amplifies the signal that
it is received. It is extremely effective.
iv) Network Router: It is the network device that helps in routing traffic from one
network to another (Klukas, Chen & Pape, 2014).
v) Modem: It is the combination of modulator and demodulator. It thus, modulates as
well as demodulates the signal.
Conclusions and Recommendations
Therefore, from the above discussion, it can be concluded that information system is
the specific software that is utilized by any organization for the purpose of performing any
type of data operation. There are various kinds of information systems. The most basic
example of information system is the database management system or DBMS, enterprise
resource planning or ERP, expert system or ES, geographic information system or GIS and
IS SECURITY AND RISK MANAGEMENT
as completed accesses and services. The transactions are also traced by this. Hence, it is
extremely important.
10. Five types of Network Security Devices for Controlling Security
The five types of network security devices that are effective for the proper control of
security and threat mitigation for the organization of Telstra Corporation Ltd. are as follows:
i) Network Switch: This network device works at the layer of LAN for the purpose of
filtering the packets and finally sending them to the interface (Lee, 2014).
ii) Bridge: The second type is the bridge. When any router connects two separate
network types, a specific bridge is used for the connection of two subnetworks. This helps to
control the security.
iii) Repeater: the next network security device is repeater. It amplifies the signal that
it is received. It is extremely effective.
iv) Network Router: It is the network device that helps in routing traffic from one
network to another (Klukas, Chen & Pape, 2014).
v) Modem: It is the combination of modulator and demodulator. It thus, modulates as
well as demodulates the signal.
Conclusions and Recommendations
Therefore, from the above discussion, it can be concluded that information system is
the specific software that is utilized by any organization for the purpose of performing any
type of data operation. There are various kinds of information systems. The most basic
example of information system is the database management system or DBMS, enterprise
resource planning or ERP, expert system or ES, geographic information system or GIS and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



