Security and Risk Management: Amcor
VerifiedAdded on 2021/06/18
|15
|3379
|242
AI Summary
IS SECURITY AND RISK MANAGEMENT IS SECURITY AND RISK MANAGEMENT 1 IS Security and Risk Management: Amcor Student ID: Author’s note: Introduction 2 1. 5 types of network security devices 9 Conclusion 10 References 12 Introduction The development of the information system has resulted in forming the effective utilization of the operations and alignment of the improved activity development (Willcocks, 2013). The information system is the significant and important organized system that is eventually used for the sole purpose of any type of data
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management: Amcor
Name of the Student:
Student ID:
Name of the University:
Author’s note:
IS Security and Risk Management: Amcor
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
1. Most Common Malwares and Threats.............................................................................2
2. Three types of network devices and their vulnerabilities................................................3
3. Reliability and Availability of Windows Server 2012....................................................4
4. Methods of Confidentiality and Integrity for email services...........................................5
5. Types of malware and security threats............................................................................5
6. Two Approaches of improving web and email servers...................................................6
7. Impact of human factor and organizational issues on IS security...................................8
8. Role of log records in security.........................................................................................8
9. Use of audit log for email and web server.......................................................................9
10. 5 types of network security devices...............................................................................9
Conclusion.........................................................................................................................10
References..........................................................................................................................12
Table of Contents
Introduction..........................................................................................................................2
1. Most Common Malwares and Threats.............................................................................2
2. Three types of network devices and their vulnerabilities................................................3
3. Reliability and Availability of Windows Server 2012....................................................4
4. Methods of Confidentiality and Integrity for email services...........................................5
5. Types of malware and security threats............................................................................5
6. Two Approaches of improving web and email servers...................................................6
7. Impact of human factor and organizational issues on IS security...................................8
8. Role of log records in security.........................................................................................8
9. Use of audit log for email and web server.......................................................................9
10. 5 types of network security devices...............................................................................9
Conclusion.........................................................................................................................10
References..........................................................................................................................12

2IS SECURITY AND RISK MANAGEMENT
Introduction
The development of the information system has resulted in forming the effective
utilization of the operations and alignment of the improved activity development (Willcocks,
2013). The utilization of the improved operations had helped in forming the implication of the
activities for forming the alignment of the successive alignment of the operations. The
information system is the significant and important organized system that is eventually used for
the sole purpose of any type of data or information operation. This information system is the
collection of several components for interaction with each other and thus producing information
(Stair & Reynolds, 2013). The development of the internet based platform has resulted in
forming the growth of various issues and problems. Information system can only work if it is
properly connected to the internet connection. The business operations or processes of any
specific organization become extremely easier with the proper incorporation of information
system within it. However, in spite of having all these advantages, there are some of the
significant risks. This report will be outlining a brief description on the information system of an
Australian organization, Amcor Ltd. The alignment of the operations had also resulted in
forming the major issues and risks (Lee, 2014). The organization of the Amcor Ltd. has been
facing the various risk factors for the development of the effective operation development.
1. Most Common Malwares and Threats
The most common malwares and threats that Amcor industry has to face are viruses and
worms, Trojans, adware, botnets, and RAM scrappers. These are some of the most common
malwares and threats that the ecommerce platform of Amcor would have to face. The RAM
scraping is a method of stealing information from the PoS devices (Ifinedo, 2014). The PoS
Introduction
The development of the information system has resulted in forming the effective
utilization of the operations and alignment of the improved activity development (Willcocks,
2013). The utilization of the improved operations had helped in forming the implication of the
activities for forming the alignment of the successive alignment of the operations. The
information system is the significant and important organized system that is eventually used for
the sole purpose of any type of data or information operation. This information system is the
collection of several components for interaction with each other and thus producing information
(Stair & Reynolds, 2013). The development of the internet based platform has resulted in
forming the growth of various issues and problems. Information system can only work if it is
properly connected to the internet connection. The business operations or processes of any
specific organization become extremely easier with the proper incorporation of information
system within it. However, in spite of having all these advantages, there are some of the
significant risks. This report will be outlining a brief description on the information system of an
Australian organization, Amcor Ltd. The alignment of the operations had also resulted in
forming the major issues and risks (Lee, 2014). The organization of the Amcor Ltd. has been
facing the various risk factors for the development of the effective operation development.
1. Most Common Malwares and Threats
The most common malwares and threats that Amcor industry has to face are viruses and
worms, Trojans, adware, botnets, and RAM scrappers. These are some of the most common
malwares and threats that the ecommerce platform of Amcor would have to face. The RAM
scraping is a method of stealing information from the PoS devices (Ifinedo, 2014). The PoS

3IS SECURITY AND RISK MANAGEMENT
devices can be compromised for being scarped for extracting information. The botnets work
similarly to the spyware and it results in extracting information from the system. The deployment
of the botnets would help in backtracking the information from the system by the hackers. The
adware results in forming the automatic. The adware works as the simple advertisements that
runs as video ads and makes the system slack (Laudon & Laudon, 2016). The adware are the
popups that runs on websites and cause the issues in the deployment of the activities and using
the advertisements for slowing the business operation. The bundles of advertisement are
sponsored by the advertisers for serving as a revenue generation tool. The bugs are deployed for
the forming undesired outcomes and usually aligned for resulting in the formation of the human
error and code (Ahmed & Hossain, 2014). The bugs can result in forming the issues of bypassing
user authentication, overriding the access, and stealing data.
2. Three types of network devices and their vulnerabilities
The three types of network devices in Amcor Ltd. and their vulnerabilities are given
below:
i) Repeater: The repeater acts as a signal regenerator working at the physical layer of
Amcor Ltd. The device results in dealing with the problem of degeneration of the signal and the
signal becoming very weak with the passage of time. The repeaters receive a specific signal
before retransmitting it. These repeaters are then utilized for extending the transmissions for the
purpose that the signal can easily cover up the longer distances over an obstruction (Power,
Sharda & Burstein, 2015). Some of the most significant kinds of repeaters are present within the
networking world of Amcor Ltd. Amongst them; telephone repeater is the most important of all.
It is the amplifier within a telephone line. The second important repeater is the optical repeater.
devices can be compromised for being scarped for extracting information. The botnets work
similarly to the spyware and it results in extracting information from the system. The deployment
of the botnets would help in backtracking the information from the system by the hackers. The
adware results in forming the automatic. The adware works as the simple advertisements that
runs as video ads and makes the system slack (Laudon & Laudon, 2016). The adware are the
popups that runs on websites and cause the issues in the deployment of the activities and using
the advertisements for slowing the business operation. The bundles of advertisement are
sponsored by the advertisers for serving as a revenue generation tool. The bugs are deployed for
the forming undesired outcomes and usually aligned for resulting in the formation of the human
error and code (Ahmed & Hossain, 2014). The bugs can result in forming the issues of bypassing
user authentication, overriding the access, and stealing data.
2. Three types of network devices and their vulnerabilities
The three types of network devices in Amcor Ltd. and their vulnerabilities are given
below:
i) Repeater: The repeater acts as a signal regenerator working at the physical layer of
Amcor Ltd. The device results in dealing with the problem of degeneration of the signal and the
signal becoming very weak with the passage of time. The repeaters receive a specific signal
before retransmitting it. These repeaters are then utilized for extending the transmissions for the
purpose that the signal can easily cover up the longer distances over an obstruction (Power,
Sharda & Burstein, 2015). Some of the most significant kinds of repeaters are present within the
networking world of Amcor Ltd. Amongst them; telephone repeater is the most important of all.
It is the amplifier within a telephone line. The second important repeater is the optical repeater.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4IS SECURITY AND RISK MANAGEMENT
The third repeater is the radio repeater, where the radio transmitter and the radio receiver are
present. The main threats to repeater are Denial of service attacks and repudiation threat.
ii) Network Switches: The second type of network security device within the organization
of Amcor Ltd. is the network switches. It helps in connecting devices on any computer network
with the help of packet switching for the purposes of receiving, processing and finally
forwarding data to the particular destination device (Kadam & Onkar, 2015). It is the multiport
network bridge, which subsequently utilizes the hardware addresses for successfully processing
the data within the data link layer. Network switches could be easily exploited by internal
threats.
iii) Router: This particular networking device helps to forward all the data packets within
the computer networks. This router performs the traffic direction functionalities over the Internet
(Laudon & Laudon, 2016). Any data packet is forwarded form any one router to the other via the
networks for constituting an inter network until it is reached to the destination node. The most
significant threat to the router is denial of service attacks.
3. Reliability and Availability of Windows Server 2012
Reliability and availability are the two most important factors in any web server. Amcor
Ltd is using the Windows Server 2012 within their business. They are using this for hosting their
web site. Reliability of any web server solely depends on web site performance (Arvidsson,
Holmström & Lyytinen, 2014). The major factors of reliability determination are as follows:
i) The most important factor is to incorporate Internet connection within the organization.
The third repeater is the radio repeater, where the radio transmitter and the radio receiver are
present. The main threats to repeater are Denial of service attacks and repudiation threat.
ii) Network Switches: The second type of network security device within the organization
of Amcor Ltd. is the network switches. It helps in connecting devices on any computer network
with the help of packet switching for the purposes of receiving, processing and finally
forwarding data to the particular destination device (Kadam & Onkar, 2015). It is the multiport
network bridge, which subsequently utilizes the hardware addresses for successfully processing
the data within the data link layer. Network switches could be easily exploited by internal
threats.
iii) Router: This particular networking device helps to forward all the data packets within
the computer networks. This router performs the traffic direction functionalities over the Internet
(Laudon & Laudon, 2016). Any data packet is forwarded form any one router to the other via the
networks for constituting an inter network until it is reached to the destination node. The most
significant threat to the router is denial of service attacks.
3. Reliability and Availability of Windows Server 2012
Reliability and availability are the two most important factors in any web server. Amcor
Ltd is using the Windows Server 2012 within their business. They are using this for hosting their
web site. Reliability of any web server solely depends on web site performance (Arvidsson,
Holmström & Lyytinen, 2014). The major factors of reliability determination are as follows:
i) The most important factor is to incorporate Internet connection within the organization.

5IS SECURITY AND RISK MANAGEMENT
ii) The next factor is the proper determination of reliability in the stability maintenance
for the software systems and server hardware.
iii) The third factor for significantly determining the Windows Server reliability is power
stability with the facility of hosting (Klukas, Chen & Pape, 2014).
Windows Server 2012 could be determined on the basis of its availability. The two
factors are as follows:
i) The most important factor is the proper availability of the web server.
ii) The next factor is web server being periodically maintained, hence there is extremely
less chance of errors or problems.
4. Methods of Confidentiality and Integrity for email services
Confidentiality and integrity are ensured for the email services. Amcor Ltd uses
Microsoft Exchange to give email service for their employees. Confidentiality can be easily
ensured by ensuring the fact that all the emails are not opened by any authenticated person (Li,
Hsieh & Rai, 2013). This authentication and authorization is maintained by confidentiality. The
most important factor of confidentiality of Microsoft Exchange is encryption.
Integrity of Microsoft Exchange server is maintained by ensuring the significant factor of
maintaining integrity within the organization of Amcor Ltd. The hackers or the attackers do not
get the scope to hack or change the data and thus the integrity is maintained properly.
5. Types of malware and security threats
ii) The next factor is the proper determination of reliability in the stability maintenance
for the software systems and server hardware.
iii) The third factor for significantly determining the Windows Server reliability is power
stability with the facility of hosting (Klukas, Chen & Pape, 2014).
Windows Server 2012 could be determined on the basis of its availability. The two
factors are as follows:
i) The most important factor is the proper availability of the web server.
ii) The next factor is web server being periodically maintained, hence there is extremely
less chance of errors or problems.
4. Methods of Confidentiality and Integrity for email services
Confidentiality and integrity are ensured for the email services. Amcor Ltd uses
Microsoft Exchange to give email service for their employees. Confidentiality can be easily
ensured by ensuring the fact that all the emails are not opened by any authenticated person (Li,
Hsieh & Rai, 2013). This authentication and authorization is maintained by confidentiality. The
most important factor of confidentiality of Microsoft Exchange is encryption.
Integrity of Microsoft Exchange server is maintained by ensuring the significant factor of
maintaining integrity within the organization of Amcor Ltd. The hackers or the attackers do not
get the scope to hack or change the data and thus the integrity is maintained properly.
5. Types of malware and security threats

6IS SECURITY AND RISK MANAGEMENT
There are various important threats and malware within the web server and email server
of Amcor Ltd. The employees of information technology department of the organization have
faced various issues due to this (Peltier, 2013). Several security threats according to the priorities
are given below:
i) Virus: First security threat is virus. The web server and the web mail is extremely
threatened from this threat. The malicious program, the moment it is executed, it replicates
eventually and the program is being modified for inserting their own code.
ii) Email Spoofing: Emails are created by a forged address. Authenticity is lost by this
(Rong, Nguyen & Jaatun, 2013).
iii) Phishing: Confidential data or information that are present within the mail are theft
by this phishing.
6. Two Approaches of improving web and email servers
Two approaches for improving the web server and email server are given below:
i) Implementing SPF: Sender policy framework is properly implemented and this is the
first approach. The SIDF or sender ID framework helps to maintain email server authenticity as
well as the web server authenticity.
There are various important threats and malware within the web server and email server
of Amcor Ltd. The employees of information technology department of the organization have
faced various issues due to this (Peltier, 2013). Several security threats according to the priorities
are given below:
i) Virus: First security threat is virus. The web server and the web mail is extremely
threatened from this threat. The malicious program, the moment it is executed, it replicates
eventually and the program is being modified for inserting their own code.
ii) Email Spoofing: Emails are created by a forged address. Authenticity is lost by this
(Rong, Nguyen & Jaatun, 2013).
iii) Phishing: Confidential data or information that are present within the mail are theft
by this phishing.
6. Two Approaches of improving web and email servers
Two approaches for improving the web server and email server are given below:
i) Implementing SPF: Sender policy framework is properly implemented and this is the
first approach. The SIDF or sender ID framework helps to maintain email server authenticity as
well as the web server authenticity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
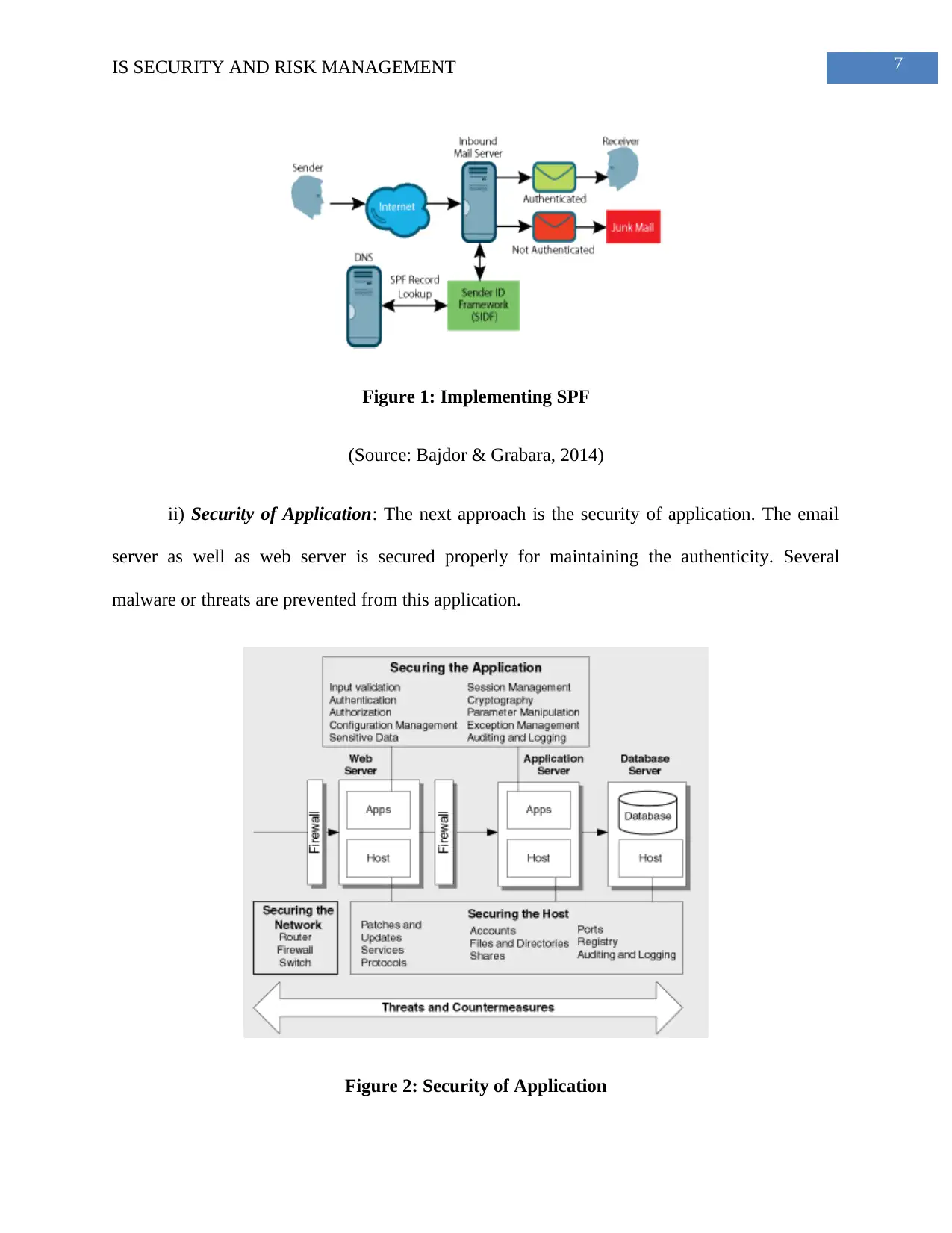
7IS SECURITY AND RISK MANAGEMENT
Figure 1: Implementing SPF
(Source: Bajdor & Grabara, 2014)
ii) Security of Application: The next approach is the security of application. The email
server as well as web server is secured properly for maintaining the authenticity. Several
malware or threats are prevented from this application.
Figure 2: Security of Application
Figure 1: Implementing SPF
(Source: Bajdor & Grabara, 2014)
ii) Security of Application: The next approach is the security of application. The email
server as well as web server is secured properly for maintaining the authenticity. Several
malware or threats are prevented from this application.
Figure 2: Security of Application

8IS SECURITY AND RISK MANAGEMENT
(Source: Hashizume et al., 2013)
7. Impact of human factor and organizational issues on IS security
There are various organizational issues or problems within Amcor Ltd. These issues have
stronger impact on the information system related security as well as risk management. The
impacts are given below:
i) Security of IT Procurement
ii) Connection within IT Security and Operations of IT
iii) Improvement of Business Efficiency
iv) Improvement of Software Security (Cheminod, Durante & Valenzano, 2013).
The human factor impacts on the information system risk and security management are
given below:
i) Requirement of Proper Training
ii) Incorporating Awareness
iii) Influence of Security Culture
8. Role of log records in security
There are several log records within the company of Amcor Ltd. These log records
eventually involve the access, security and finally the event of the organization. The significant
and most utilized functionalities of all these log records are AllocReservedLog, which is utilized
for the proper allocation of the aligned space for reserved records set (Singhal et al., 2013). The
(Source: Hashizume et al., 2013)
7. Impact of human factor and organizational issues on IS security
There are various organizational issues or problems within Amcor Ltd. These issues have
stronger impact on the information system related security as well as risk management. The
impacts are given below:
i) Security of IT Procurement
ii) Connection within IT Security and Operations of IT
iii) Improvement of Business Efficiency
iv) Improvement of Software Security (Cheminod, Durante & Valenzano, 2013).
The human factor impacts on the information system risk and security management are
given below:
i) Requirement of Proper Training
ii) Incorporating Awareness
iii) Influence of Security Culture
8. Role of log records in security
There are several log records within the company of Amcor Ltd. These log records
eventually involve the access, security and finally the event of the organization. The significant
and most utilized functionalities of all these log records are AllocReservedLog, which is utilized
for the proper allocation of the aligned space for reserved records set (Singhal et al., 2013). The

9IS SECURITY AND RISK MANAGEMENT
second log record is the AlignReservedLog, which is utilized for calculating the size of aligned
reservation for all the records. The next two important audit log records within the organization
of Amcor Ltd. are CreateLogFile as well as DeleteLogFile. The creation or opening of log file
and the deletion or removal of the log file is properly done with these two log files. Thus, the
security of the email server and web server of Amcor Ltd is properly monitored or analysed with
all these audit log records.
9. Use of audit log for email and web server
Audit log record is being utilized by the organization of Amcor Ltd. so that they could
easily obtain better performance from the analysis of audit and hence supporting all the
organizational internal investigations (Stair & Reynolds, 2013). This also helps in indent of
operational trend or problem in log term. This record of audit log is the significant collection of
records that is related to the security of the business operations. The audit log record helps in
providing the important documentary proof for the sequence of several activities that is affecting
all the operations, processes and events of the organization. The issues of email server as well as
the web server are properly resolved by the record of audit log. Several activities are present for
the employees of the organization (Crossler et al., 2013). The most important activities are
financial transactions and scientific research. The accounts of the staffs are maintained by this.
10. 5 types of network security devices
Five distinct types of network security devices for properly controlling the security as
well as mitigating the threats within Amcor Ltd. are given below:
second log record is the AlignReservedLog, which is utilized for calculating the size of aligned
reservation for all the records. The next two important audit log records within the organization
of Amcor Ltd. are CreateLogFile as well as DeleteLogFile. The creation or opening of log file
and the deletion or removal of the log file is properly done with these two log files. Thus, the
security of the email server and web server of Amcor Ltd is properly monitored or analysed with
all these audit log records.
9. Use of audit log for email and web server
Audit log record is being utilized by the organization of Amcor Ltd. so that they could
easily obtain better performance from the analysis of audit and hence supporting all the
organizational internal investigations (Stair & Reynolds, 2013). This also helps in indent of
operational trend or problem in log term. This record of audit log is the significant collection of
records that is related to the security of the business operations. The audit log record helps in
providing the important documentary proof for the sequence of several activities that is affecting
all the operations, processes and events of the organization. The issues of email server as well as
the web server are properly resolved by the record of audit log. Several activities are present for
the employees of the organization (Crossler et al., 2013). The most important activities are
financial transactions and scientific research. The accounts of the staffs are maintained by this.
10. 5 types of network security devices
Five distinct types of network security devices for properly controlling the security as
well as mitigating the threats within Amcor Ltd. are given below:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10IS SECURITY AND RISK MANAGEMENT
i) Bridges: The first type is bridge. If any specific router is connecting with two different
types of network, a particular bridge is being utilized to successfully link them. The sub
networks are linked for controlling the security (Stojmenovic & Wen, 2014).
ii) Modems: Modem is the nest type of networking device. It is a perfect amalgamation of
demodulator as well as modulator. The signal is thus modulated and demodulated on time.
iii) Routers: Routers are used in routing the traffic from one point to the other point.
Thus, it is extremely important (Laudon & Laudon, 2016).
iv) Switches: Network switch does its work in the LAN to properly filter all the packets
and significantly send them within the interface.
v) Repeater: The final type of network security device is the repeater. It is responsible for
properly amplifying any signal the moment it is being received (Gallagher & Sixsmith, 2014).
The repeater is more effective than other device for the purpose of controlling security.
Conclusion
Therefore, from the above report, conclusion can be drawn that information system s the
significant software, which is used by a company to successfully perform the data operations.
The processing, filtering, manipulation and even editing of data or information are easily done
with the help of information system. Several kinds of information systems are present within the
cyber world. Amongst all of them, the most significant and important information systems are
DBMS or database management system, ERP or enterprise resource planning system, GIS or
geographic information system, ES or expert system and many others. All of the above
mentioned types of information systems are used by the several users with a similar purpose of
i) Bridges: The first type is bridge. If any specific router is connecting with two different
types of network, a particular bridge is being utilized to successfully link them. The sub
networks are linked for controlling the security (Stojmenovic & Wen, 2014).
ii) Modems: Modem is the nest type of networking device. It is a perfect amalgamation of
demodulator as well as modulator. The signal is thus modulated and demodulated on time.
iii) Routers: Routers are used in routing the traffic from one point to the other point.
Thus, it is extremely important (Laudon & Laudon, 2016).
iv) Switches: Network switch does its work in the LAN to properly filter all the packets
and significantly send them within the interface.
v) Repeater: The final type of network security device is the repeater. It is responsible for
properly amplifying any signal the moment it is being received (Gallagher & Sixsmith, 2014).
The repeater is more effective than other device for the purpose of controlling security.
Conclusion
Therefore, from the above report, conclusion can be drawn that information system s the
significant software, which is used by a company to successfully perform the data operations.
The processing, filtering, manipulation and even editing of data or information are easily done
with the help of information system. Several kinds of information systems are present within the
cyber world. Amongst all of them, the most significant and important information systems are
DBMS or database management system, ERP or enterprise resource planning system, GIS or
geographic information system, ES or expert system and many others. All of the above
mentioned types of information systems are used by the several users with a similar purpose of

11IS SECURITY AND RISK MANAGEMENT
simplification of business processes or operations. All the components of the information system
are software, complementary networks, databases, procedures, hardware and many more. The
four basic elements are databases, software, complementary networks and hardware. This report
has highlighted the entire concept of information system for the popular organization of Amcor
Ltd. Being one of the most important and significant organizations in Australia, Amcor Ltd.
provides unique products and services to all of its users. However, there are some of the most
important security threats that are acquiring the entire world by its vulnerabilities. These threats
and malware are required to be mitigated within time, so that there is no chance of data loss.
Significant details are provided in the above report.
The recommendations to the organization of Amcor Ltd are extremely important for them
to mitigate all the problems they are facing. They should implement an information system
within their business for successfully mitigating with significant measures. The web server and
the email server should also be secured properly.
simplification of business processes or operations. All the components of the information system
are software, complementary networks, databases, procedures, hardware and many more. The
four basic elements are databases, software, complementary networks and hardware. This report
has highlighted the entire concept of information system for the popular organization of Amcor
Ltd. Being one of the most important and significant organizations in Australia, Amcor Ltd.
provides unique products and services to all of its users. However, there are some of the most
important security threats that are acquiring the entire world by its vulnerabilities. These threats
and malware are required to be mitigated within time, so that there is no chance of data loss.
Significant details are provided in the above report.
The recommendations to the organization of Amcor Ltd are extremely important for them
to mitigate all the problems they are facing. They should implement an information system
within their business for successfully mitigating with significant measures. The web server and
the email server should also be secured properly.

12IS SECURITY AND RISK MANAGEMENT
References
Ahmed, M., & Hossain, M. A. (2014). Cloud computing and security issues in the
cloud. International Journal of Network Security & Its Applications, 6(1), 25.
Arvidsson, V., Holmström, J., & Lyytinen, K. (2014). Information systems use as strategy
practice: A multi-dimensional view of strategic information system implementation and
use. The Journal of Strategic Information Systems, 23(1), 45-61.
Bajdor, P., & Grabara, I. (2014). The Role of Information System Flows in Fulfilling Customers’
Individual Orders. Journal of Studies in Social Sciences, 7(2).
Cheminod, M., Durante, L., & Valenzano, A. (2013). Review of security issues in industrial
networks. IEEE Transactions on Industrial Informatics, 9(1), 277-293.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32,
90-101.
Gallagher, S., & Sixsmith, A. (2014). Engaging IT undergraduates in non-IT content: Adopting
an eLearning information system in the classroom. Interactive Technology and Smart
Education, 11(2), 99-111.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of internet services and applications, 4(1),
5.
References
Ahmed, M., & Hossain, M. A. (2014). Cloud computing and security issues in the
cloud. International Journal of Network Security & Its Applications, 6(1), 25.
Arvidsson, V., Holmström, J., & Lyytinen, K. (2014). Information systems use as strategy
practice: A multi-dimensional view of strategic information system implementation and
use. The Journal of Strategic Information Systems, 23(1), 45-61.
Bajdor, P., & Grabara, I. (2014). The Role of Information System Flows in Fulfilling Customers’
Individual Orders. Journal of Studies in Social Sciences, 7(2).
Cheminod, M., Durante, L., & Valenzano, A. (2013). Review of security issues in industrial
networks. IEEE Transactions on Industrial Informatics, 9(1), 277-293.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32,
90-101.
Gallagher, S., & Sixsmith, A. (2014). Engaging IT undergraduates in non-IT content: Adopting
an eLearning information system in the classroom. Interactive Technology and Smart
Education, 11(2), 99-111.
Hashizume, K., Rosado, D. G., Fernández-Medina, E., & Fernandez, E. B. (2013). An analysis of
security issues for cloud computing. Journal of internet services and applications, 4(1),
5.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13IS SECURITY AND RISK MANAGEMENT
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), 69-
79.
Kadam, K. S., & Onkar, V. C. (2015). A review paper on student information supervision
system. International Journal of Research In Science & Engineering, 1, 66-72.
Klukas, C., Chen, D., & Pape, J. M. (2014). Integrated analysis platform: an open-source
information system for high-throughput plant phenotyping. Plant physiology, 165(2),
506-518.
Laudon, K. C., & Laudon, J. P. (2016). Management information system. Pearson Education
India.
Lee, S. S. (2014). Management information systems. Management, 166137(01), 02.
Li, X., Hsieh, J. P. A., & Rai, A. (2013). Motivational differences across post-acceptance
information system usage behaviors: An investigation in the business intelligence
systems context. Information systems research, 24(3), 659-682.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Power, D. J., Sharda, R., & Burstein, F. (2015). Decision support systems. John Wiley & Sons,
Ltd.
Rong, C., Nguyen, S. T., & Jaatun, M. G. (2013). Beyond lightning: A survey on security
challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47-54.
Ifinedo, P. (2014). Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), 69-
79.
Kadam, K. S., & Onkar, V. C. (2015). A review paper on student information supervision
system. International Journal of Research In Science & Engineering, 1, 66-72.
Klukas, C., Chen, D., & Pape, J. M. (2014). Integrated analysis platform: an open-source
information system for high-throughput plant phenotyping. Plant physiology, 165(2),
506-518.
Laudon, K. C., & Laudon, J. P. (2016). Management information system. Pearson Education
India.
Lee, S. S. (2014). Management information systems. Management, 166137(01), 02.
Li, X., Hsieh, J. P. A., & Rai, A. (2013). Motivational differences across post-acceptance
information system usage behaviors: An investigation in the business intelligence
systems context. Information systems research, 24(3), 659-682.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Power, D. J., Sharda, R., & Burstein, F. (2015). Decision support systems. John Wiley & Sons,
Ltd.
Rong, C., Nguyen, S. T., & Jaatun, M. G. (2013). Beyond lightning: A survey on security
challenges in cloud computing. Computers & Electrical Engineering, 39(1), 47-54.

14IS SECURITY AND RISK MANAGEMENT
Singhal, M., Chandrasekhar, S., Ge, T., Sandhu, R., Krishnan, R., Ahn, G. J., & Bertino, E.
(2013). Collaboration in multicloud computing environments: Framework and security
issues. Computer, 46(2), 76-84.
Stair, R., & Reynolds, G. (2013). Principles of information systems. Cengage Learning.
Stojmenovic, I., & Wen, S. (2014, September). The fog computing paradigm: Scenarios and
security issues. In Computer Science and Information Systems (FedCSIS), 2014
Federated Conference on (pp. 1-8). IEEE.
Willcocks, L. (2013). Information management: the evaluation of information systems
investments. Springer.
Singhal, M., Chandrasekhar, S., Ge, T., Sandhu, R., Krishnan, R., Ahn, G. J., & Bertino, E.
(2013). Collaboration in multicloud computing environments: Framework and security
issues. Computer, 46(2), 76-84.
Stair, R., & Reynolds, G. (2013). Principles of information systems. Cengage Learning.
Stojmenovic, I., & Wen, S. (2014, September). The fog computing paradigm: Scenarios and
security issues. In Computer Science and Information Systems (FedCSIS), 2014
Federated Conference on (pp. 1-8). IEEE.
Willcocks, L. (2013). Information management: the evaluation of information systems
investments. Springer.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


