Analyzing Cybersecurity Attacks and Risk Management in IS Security
VerifiedAdded on 2023/06/12
|12
|3177
|391
Report
AI Summary
This report provides a comprehensive analysis of information security, focusing on cybersecurity attacks and risk management. It begins by outlining various types of cybersecurity attacks, including network intrusion, malware, DDoS attacks, ransomware, and brute force attacks, detailing their mechanisms and potential impact. The report then categorizes organizational assets into people, procedures, data, software, hardware, and networks, explaining their importance and vulnerabilities. A prioritized list of threats against each asset type is presented, followed by an examination of fundamental security principles such as layering, limiting, diversity, obscurity, and simplicity. The report concludes by discussing strategies for preventing malware delivery and limiting cybersecurity incidents, including application whitelisting and other preventative measures. Desklib offers similar solved assignments and past papers for students.

IS SECURITY AND RISK
MANAGEMENT
MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENT
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
1.Cybersecurity attacks................................................................................................................3
2. Categorising the assets that involve organisational elements..................................................5
3. identifying and prioritising the threats against every type of the asset identified...................6
4. Fundamental security principles for limiting the malware delivery and cyber security
incidents.......................................................................................................................................6
CONCLUSION................................................................................................................................9
REFERENCE................................................................................................................................10
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
1.Cybersecurity attacks................................................................................................................3
2. Categorising the assets that involve organisational elements..................................................5
3. identifying and prioritising the threats against every type of the asset identified...................6
4. Fundamental security principles for limiting the malware delivery and cyber security
incidents.......................................................................................................................................6
CONCLUSION................................................................................................................................9
REFERENCE................................................................................................................................10

INTRODUCTION
Network have changed many things it changes the way of business conducts but it also
causes the cyber related threats. As it is found that the internet has open the doors for the threat
actors, they hack the system and access all the information and turns it into the biggest crime.
Information security refer as the collection of practices which are used to secure the data from
unauthorised access and other alterations (Pandey and et.al 2020). It is also referring as the data
security to provide the encryption of data so it can be prevented from any malicious activities.
Following report will cover the recent type of the information security attacks and protect
mechanism along with the risk management. It also discusses the identification of the major
cyber security attacks and its activities. It further categorises the assets which mainly involves
the organisational system elements, and prioritising the threats in a table form. It also lay out the
security defences on fundamental safety principles.
MAIN BODY
1.Cybersecurity attacks
Cybersecurity attacks refer as any kind of malicious activity which usually targets the IT system
to achieve the unauthorised access to the system to steal the information. Cyber attackers are the
criminals in most cases as they develop the life threatening situation for the one whose data is
theft.
Many cybersecurity attacks are as follows:
Network have changed many things it changes the way of business conducts but it also
causes the cyber related threats. As it is found that the internet has open the doors for the threat
actors, they hack the system and access all the information and turns it into the biggest crime.
Information security refer as the collection of practices which are used to secure the data from
unauthorised access and other alterations (Pandey and et.al 2020). It is also referring as the data
security to provide the encryption of data so it can be prevented from any malicious activities.
Following report will cover the recent type of the information security attacks and protect
mechanism along with the risk management. It also discusses the identification of the major
cyber security attacks and its activities. It further categorises the assets which mainly involves
the organisational system elements, and prioritising the threats in a table form. It also lay out the
security defences on fundamental safety principles.
MAIN BODY
1.Cybersecurity attacks
Cybersecurity attacks refer as any kind of malicious activity which usually targets the IT system
to achieve the unauthorised access to the system to steal the information. Cyber attackers are the
criminals in most cases as they develop the life threatening situation for the one whose data is
theft.
Many cybersecurity attacks are as follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
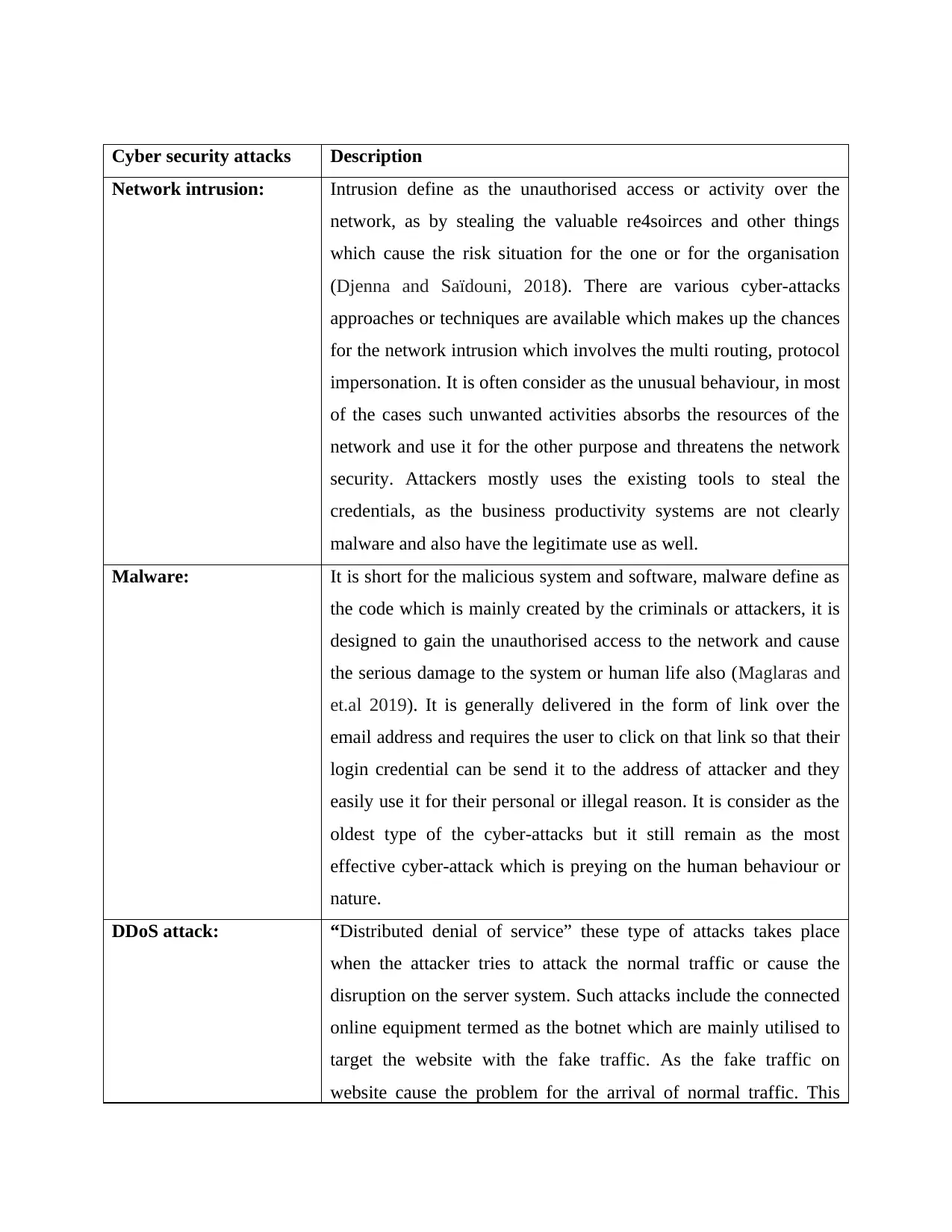
Cyber security attacks Description
Network intrusion: Intrusion define as the unauthorised access or activity over the
network, as by stealing the valuable re4soirces and other things
which cause the risk situation for the one or for the organisation
(Djenna and Saïdouni, 2018). There are various cyber-attacks
approaches or techniques are available which makes up the chances
for the network intrusion which involves the multi routing, protocol
impersonation. It is often consider as the unusual behaviour, in most
of the cases such unwanted activities absorbs the resources of the
network and use it for the other purpose and threatens the network
security. Attackers mostly uses the existing tools to steal the
credentials, as the business productivity systems are not clearly
malware and also have the legitimate use as well.
Malware: It is short for the malicious system and software, malware define as
the code which is mainly created by the criminals or attackers, it is
designed to gain the unauthorised access to the network and cause
the serious damage to the system or human life also (Maglaras and
et.al 2019). It is generally delivered in the form of link over the
email address and requires the user to click on that link so that their
login credential can be send it to the address of attacker and they
easily use it for their personal or illegal reason. It is consider as the
oldest type of the cyber-attacks but it still remain as the most
effective cyber-attack which is preying on the human behaviour or
nature.
DDoS attack: “Distributed denial of service” these type of attacks takes place
when the attacker tries to attack the normal traffic or cause the
disruption on the server system. Such attacks include the connected
online equipment termed as the botnet which are mainly utilised to
target the website with the fake traffic. As the fake traffic on
website cause the problem for the arrival of normal traffic. This
Network intrusion: Intrusion define as the unauthorised access or activity over the
network, as by stealing the valuable re4soirces and other things
which cause the risk situation for the one or for the organisation
(Djenna and Saïdouni, 2018). There are various cyber-attacks
approaches or techniques are available which makes up the chances
for the network intrusion which involves the multi routing, protocol
impersonation. It is often consider as the unusual behaviour, in most
of the cases such unwanted activities absorbs the resources of the
network and use it for the other purpose and threatens the network
security. Attackers mostly uses the existing tools to steal the
credentials, as the business productivity systems are not clearly
malware and also have the legitimate use as well.
Malware: It is short for the malicious system and software, malware define as
the code which is mainly created by the criminals or attackers, it is
designed to gain the unauthorised access to the network and cause
the serious damage to the system or human life also (Maglaras and
et.al 2019). It is generally delivered in the form of link over the
email address and requires the user to click on that link so that their
login credential can be send it to the address of attacker and they
easily use it for their personal or illegal reason. It is consider as the
oldest type of the cyber-attacks but it still remain as the most
effective cyber-attack which is preying on the human behaviour or
nature.
DDoS attack: “Distributed denial of service” these type of attacks takes place
when the attacker tries to attack the normal traffic or cause the
disruption on the server system. Such attacks include the connected
online equipment termed as the botnet which are mainly utilised to
target the website with the fake traffic. As the fake traffic on
website cause the problem for the arrival of normal traffic. This
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

attacks specifically sends the multiple requests to the attacked web
resource with the purpose of exceeding the capacity of the website
to tackle the request and creates a problem for the website to
function better. But the countermeasures of the technologies have
reduced the chances for this attack.
Ransomware: It is the type of the malware attacks in which the hacker locks the
system and encrypts the data and essential files and information of
the person and then later demands to pay high for unlocking or
decrypting the system. Such attack mainly takes the advantage of
the human, system and the vulnerabilities in the software cause the
severe problems for the victim’s system (Mosteanu, 2020). It is
considering as the most common cyberattack which is normally
seen today, because these type of attacks are successful and results
as in payouts in millions. This attack appears as a notification on
the screen and the data that is available on the system is encrypted it
still not recover when the certain amount is not been sent to the
attacker. Thus most of the people are the victim of such
ransomware attacks.
Brute force attacks: It is often known as the exhaustive search in which the attackers
submits the different patterns for the password and keep
passphrases until get the correct one. It is like thief breaking the
asset safe by trying all possible locks passwords. It is the trial end
mistake which is utilised for decoding the sensitive data. Most basis
applications for the brute force attack is to crack the encryption
keys, other targets for such attack are the API keys and other SSH
logins. Such types of attacks are very slow as the attackers takes the
time to enter the right choice of password to crack the system but in
most cases it is successful and unsuccessful both (Huang, Qin and
Liu, 2018).
resource with the purpose of exceeding the capacity of the website
to tackle the request and creates a problem for the website to
function better. But the countermeasures of the technologies have
reduced the chances for this attack.
Ransomware: It is the type of the malware attacks in which the hacker locks the
system and encrypts the data and essential files and information of
the person and then later demands to pay high for unlocking or
decrypting the system. Such attack mainly takes the advantage of
the human, system and the vulnerabilities in the software cause the
severe problems for the victim’s system (Mosteanu, 2020). It is
considering as the most common cyberattack which is normally
seen today, because these type of attacks are successful and results
as in payouts in millions. This attack appears as a notification on
the screen and the data that is available on the system is encrypted it
still not recover when the certain amount is not been sent to the
attacker. Thus most of the people are the victim of such
ransomware attacks.
Brute force attacks: It is often known as the exhaustive search in which the attackers
submits the different patterns for the password and keep
passphrases until get the correct one. It is like thief breaking the
asset safe by trying all possible locks passwords. It is the trial end
mistake which is utilised for decoding the sensitive data. Most basis
applications for the brute force attack is to crack the encryption
keys, other targets for such attack are the API keys and other SSH
logins. Such types of attacks are very slow as the attackers takes the
time to enter the right choice of password to crack the system but in
most cases it is successful and unsuccessful both (Huang, Qin and
Liu, 2018).

2. Categorising the assets that involve organisational elements
Organisational assets are more likely to phase the threats which the firm required to protect it
from any malicious activities which cause the problem for them.
People: It comes under the human resource category where the HR team manage the people.
This category involves the employees and non-employees. As the employees are the trusted asset
for the business who contributes in the business productivity, they are accountable for many
changes that are drives in the business, they have the great responsibility to move the
organisation in a forward direction to fulfil the desired goals and objectives. Thus non employees
are consider as the contractors and other consultants or the partner of other company which have
the good and trustable relation with the organisations. Asset for the people are position name,
specific skills, manager, owner.
Procedures: In this there are mainly two categories which are IT(information technology) team
and business standards and IT and business sensitive. As the business sensitive mainly contains
the threat agent in framing the attacks against business and also contains the information that
cause the risks for the organisation. As the asset for the procedures are description, intended
connectivity with the software and hardware for the update.
Data: It is the useful information which is comes under the most valuable asset for the business
in terms of increasing revenues. As the data components are accounts for transforming and
storing or analysing. Asset for the data are creator, location, data structure which is utilised
(Dibaei and et.al 2019.).
Software: It can be of three type which are application, security elements and operating system.
Software element who provides the range of security controls are often seen as spanning the OS
range and application process, but they can be differentiated easily because they are part of the
Information security system and must be prevented from other threats.
Hardware: In this usual peripheral hardware devices are fall into this category and other devices
which are the part of the IS system.
Network: Thus for the network components which are intranet and internet elements.
3. identifying and prioritising the threats against every type of the asset identified
Assets Threat
Organisational assets are more likely to phase the threats which the firm required to protect it
from any malicious activities which cause the problem for them.
People: It comes under the human resource category where the HR team manage the people.
This category involves the employees and non-employees. As the employees are the trusted asset
for the business who contributes in the business productivity, they are accountable for many
changes that are drives in the business, they have the great responsibility to move the
organisation in a forward direction to fulfil the desired goals and objectives. Thus non employees
are consider as the contractors and other consultants or the partner of other company which have
the good and trustable relation with the organisations. Asset for the people are position name,
specific skills, manager, owner.
Procedures: In this there are mainly two categories which are IT(information technology) team
and business standards and IT and business sensitive. As the business sensitive mainly contains
the threat agent in framing the attacks against business and also contains the information that
cause the risks for the organisation. As the asset for the procedures are description, intended
connectivity with the software and hardware for the update.
Data: It is the useful information which is comes under the most valuable asset for the business
in terms of increasing revenues. As the data components are accounts for transforming and
storing or analysing. Asset for the data are creator, location, data structure which is utilised
(Dibaei and et.al 2019.).
Software: It can be of three type which are application, security elements and operating system.
Software element who provides the range of security controls are often seen as spanning the OS
range and application process, but they can be differentiated easily because they are part of the
Information security system and must be prevented from other threats.
Hardware: In this usual peripheral hardware devices are fall into this category and other devices
which are the part of the IS system.
Network: Thus for the network components which are intranet and internet elements.
3. identifying and prioritising the threats against every type of the asset identified
Assets Threat
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
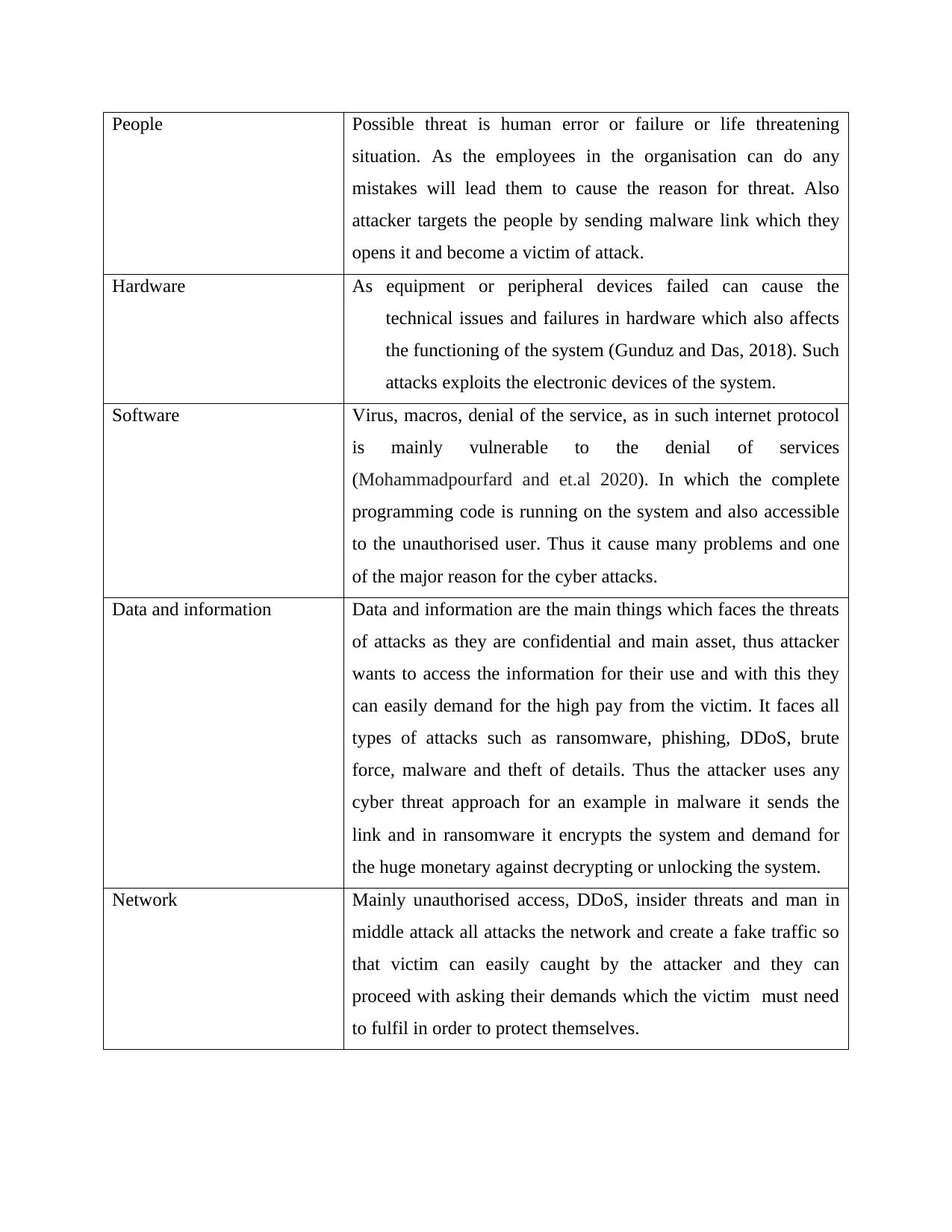
People Possible threat is human error or failure or life threatening
situation. As the employees in the organisation can do any
mistakes will lead them to cause the reason for threat. Also
attacker targets the people by sending malware link which they
opens it and become a victim of attack.
Hardware As equipment or peripheral devices failed can cause the
technical issues and failures in hardware which also affects
the functioning of the system (Gunduz and Das, 2018). Such
attacks exploits the electronic devices of the system.
Software Virus, macros, denial of the service, as in such internet protocol
is mainly vulnerable to the denial of services
(Mohammadpourfard and et.al 2020). In which the complete
programming code is running on the system and also accessible
to the unauthorised user. Thus it cause many problems and one
of the major reason for the cyber attacks.
Data and information Data and information are the main things which faces the threats
of attacks as they are confidential and main asset, thus attacker
wants to access the information for their use and with this they
can easily demand for the high pay from the victim. It faces all
types of attacks such as ransomware, phishing, DDoS, brute
force, malware and theft of details. Thus the attacker uses any
cyber threat approach for an example in malware it sends the
link and in ransomware it encrypts the system and demand for
the huge monetary against decrypting or unlocking the system.
Network Mainly unauthorised access, DDoS, insider threats and man in
middle attack all attacks the network and create a fake traffic so
that victim can easily caught by the attacker and they can
proceed with asking their demands which the victim must need
to fulfil in order to protect themselves.
situation. As the employees in the organisation can do any
mistakes will lead them to cause the reason for threat. Also
attacker targets the people by sending malware link which they
opens it and become a victim of attack.
Hardware As equipment or peripheral devices failed can cause the
technical issues and failures in hardware which also affects
the functioning of the system (Gunduz and Das, 2018). Such
attacks exploits the electronic devices of the system.
Software Virus, macros, denial of the service, as in such internet protocol
is mainly vulnerable to the denial of services
(Mohammadpourfard and et.al 2020). In which the complete
programming code is running on the system and also accessible
to the unauthorised user. Thus it cause many problems and one
of the major reason for the cyber attacks.
Data and information Data and information are the main things which faces the threats
of attacks as they are confidential and main asset, thus attacker
wants to access the information for their use and with this they
can easily demand for the high pay from the victim. It faces all
types of attacks such as ransomware, phishing, DDoS, brute
force, malware and theft of details. Thus the attacker uses any
cyber threat approach for an example in malware it sends the
link and in ransomware it encrypts the system and demand for
the huge monetary against decrypting or unlocking the system.
Network Mainly unauthorised access, DDoS, insider threats and man in
middle attack all attacks the network and create a fake traffic so
that victim can easily caught by the attacker and they can
proceed with asking their demands which the victim must need
to fulfil in order to protect themselves.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. Fundamental security principles for limiting the malware delivery and cyber security incidents
Cyber attacks are common and they are increasing, on daily basis cyber attacks are found which
can be a malware, ransomware or other attacks, it is causing threat for human life loss of their
valuable assets. As security principles are:
Layering: It helps in providing the most preventive or comprehensive approach for protection.
Instead of one security defence one have the more than single defensive security. As the one
layer of defence is broken then the other layers can protect from attacks, as the different layer
increases the security level. As the organisation uses these approach to ensure that the defence
layer can be backed up by the another layer when there is any chances for the attack is found.
Limiting: People can only authorised to the data or relevant information when they are doing the
task. Access can be prohibited to the minimum (Gunduz and Das, 2020). Thus to limit the
access one can easily prevent the data from being theft or from mishandling.
Diversity: It is nearly related to the layering, as if the organisation is utilising the layers security
then they must required the better security for every layer, as there are more possibilities that the
attacker can use the different approach and techniques in order to crack the protecting layer. As
diversity in the cyber security is must in order to develop the strong security for protecting the
network from any malicious activity.
Obscurity: This cyber security principle mainly creates the difficulties for the outsider to
analyse what is going on inside. Obscurity is the attempt where it enhance the security by
keeping the security for every elements as secret. For an example as to conceal the specific
algorithm with the help of secret password in a cryptographic. But unfortunately it is found that
the obscurity gives the fallacy in the security as it lead to the insecure system.
Simplicity: As to develop the system complex to use might impact the user as they become lazy
and often develops the bypass. Also of the algorithm for the security is complex then it increase
the work of security professionals ad there are many chances that they miss the vulnerability
which later cause big damage (Apruzzese and et.al 2019).
Strategies to prevent malware delivery and limiting cyber security incidents
Application whitelisting: This approach prevents against the malware attacks to execute on the
system, thus it ensures that only authorised application can implement on the system. It is also
beneficial in identifying the number of attempts that are made by the attacker to implement the
Cyber attacks are common and they are increasing, on daily basis cyber attacks are found which
can be a malware, ransomware or other attacks, it is causing threat for human life loss of their
valuable assets. As security principles are:
Layering: It helps in providing the most preventive or comprehensive approach for protection.
Instead of one security defence one have the more than single defensive security. As the one
layer of defence is broken then the other layers can protect from attacks, as the different layer
increases the security level. As the organisation uses these approach to ensure that the defence
layer can be backed up by the another layer when there is any chances for the attack is found.
Limiting: People can only authorised to the data or relevant information when they are doing the
task. Access can be prohibited to the minimum (Gunduz and Das, 2020). Thus to limit the
access one can easily prevent the data from being theft or from mishandling.
Diversity: It is nearly related to the layering, as if the organisation is utilising the layers security
then they must required the better security for every layer, as there are more possibilities that the
attacker can use the different approach and techniques in order to crack the protecting layer. As
diversity in the cyber security is must in order to develop the strong security for protecting the
network from any malicious activity.
Obscurity: This cyber security principle mainly creates the difficulties for the outsider to
analyse what is going on inside. Obscurity is the attempt where it enhance the security by
keeping the security for every elements as secret. For an example as to conceal the specific
algorithm with the help of secret password in a cryptographic. But unfortunately it is found that
the obscurity gives the fallacy in the security as it lead to the insecure system.
Simplicity: As to develop the system complex to use might impact the user as they become lazy
and often develops the bypass. Also of the algorithm for the security is complex then it increase
the work of security professionals ad there are many chances that they miss the vulnerability
which later cause big damage (Apruzzese and et.al 2019).
Strategies to prevent malware delivery and limiting cyber security incidents
Application whitelisting: This approach prevents against the malware attacks to execute on the
system, thus it ensures that only authorised application can implement on the system. It is also
beneficial in identifying the number of attempts that are made by the attacker to implement the

malicious programming code on the system and also protect from installation of malicious or
unauthorised application.
Arrange MS office macro setting: MS office application generally implement the macros for
automating the routine work (Chadd, 2018). However, macros involve the threat of malicious
code which can give entry to the unauthorised access which can be targeted by the hacker. As to
maintain the utilisation of the macro for the organisation all macros that are developed by either
user or third party it can be reviewed by the independent party to the producer and can be safely
assessed before being authorised for use in the business.
Prohibits administrative privileges: Users with the administrative privileges for the OS and
application are more likely to able to drive the specific changes among their configuration and in
the complex security settings. As prohibits administrative privilege helps in decreasing the
potential destruction of adversary’s malware and also reduce the chances for achieving the keys
to kingdom.
Multi factor validation: As the multi factor validation provides the support to protecting against
the cyber adversary from achieving access to the network for hacking essential or sensitive
information. It decreases the chances for stealing the legitimate and also reduce the further
malicious activities on the system.
Patch operating system: It is the essential and effective mitigation approach to specifically
mitigates the network devices with the intense vulnerabilities within the 48 hours of time period.
And the latest version for the operating system can be used and unsupported version can be
avoided to prevent from some attacks and malicious activities (Apruzzese and et.al 2019).
Implement the firewalls and antivirus software: It is one of the most prominent strategy to
restrict the malicious activity or to prevent the system from being misuse. Usually it involves the
installation of the firewall security solution and other antivirus software. Thus these are able to
give the additional security as they work as a strong barrier to protect the computer network from
cyber attacks. In which the firewall acts as a buffer in the outside world and provide the better
control so that organisation can be able to manage or control the incoming traffic. Similarly
antivirus software acts as searcher as it found the possibility of any attack so that preventive
measures can be taken out in order to protect the network system.
unauthorised application.
Arrange MS office macro setting: MS office application generally implement the macros for
automating the routine work (Chadd, 2018). However, macros involve the threat of malicious
code which can give entry to the unauthorised access which can be targeted by the hacker. As to
maintain the utilisation of the macro for the organisation all macros that are developed by either
user or third party it can be reviewed by the independent party to the producer and can be safely
assessed before being authorised for use in the business.
Prohibits administrative privileges: Users with the administrative privileges for the OS and
application are more likely to able to drive the specific changes among their configuration and in
the complex security settings. As prohibits administrative privilege helps in decreasing the
potential destruction of adversary’s malware and also reduce the chances for achieving the keys
to kingdom.
Multi factor validation: As the multi factor validation provides the support to protecting against
the cyber adversary from achieving access to the network for hacking essential or sensitive
information. It decreases the chances for stealing the legitimate and also reduce the further
malicious activities on the system.
Patch operating system: It is the essential and effective mitigation approach to specifically
mitigates the network devices with the intense vulnerabilities within the 48 hours of time period.
And the latest version for the operating system can be used and unsupported version can be
avoided to prevent from some attacks and malicious activities (Apruzzese and et.al 2019).
Implement the firewalls and antivirus software: It is one of the most prominent strategy to
restrict the malicious activity or to prevent the system from being misuse. Usually it involves the
installation of the firewall security solution and other antivirus software. Thus these are able to
give the additional security as they work as a strong barrier to protect the computer network from
cyber attacks. In which the firewall acts as a buffer in the outside world and provide the better
control so that organisation can be able to manage or control the incoming traffic. Similarly
antivirus software acts as searcher as it found the possibility of any attack so that preventive
measures can be taken out in order to protect the network system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONCLUSION
From the above report it is concluded that the internet have offered many opportunities,
with this audience can easily lay out their work as well as business can easily grow their business
by providing better user experience. But it also associates with the various attacks which is often
termed as cyber attacks in which the attacker theft or steal the information by directly attacking
the system through different approach. It causes a lots of life threatening situation for the
humans. Above report have illustrated the different type of the cyber security attacks which is
mainly seen it covers the ransomware, DDoS, brute force attack, malware and network intrusion.
It further discuss the asset of the organisation which covers the range of assets under the people,
network, data and information, procedure or in software and hardware category. It further
discussed the threats identification for the asset and lastly concluded with the description of
fundamental of security principles and malware prevention strategies.
From the above report it is concluded that the internet have offered many opportunities,
with this audience can easily lay out their work as well as business can easily grow their business
by providing better user experience. But it also associates with the various attacks which is often
termed as cyber attacks in which the attacker theft or steal the information by directly attacking
the system through different approach. It causes a lots of life threatening situation for the
humans. Above report have illustrated the different type of the cyber security attacks which is
mainly seen it covers the ransomware, DDoS, brute force attack, malware and network intrusion.
It further discuss the asset of the organisation which covers the range of assets under the people,
network, data and information, procedure or in software and hardware category. It further
discussed the threats identification for the asset and lastly concluded with the description of
fundamental of security principles and malware prevention strategies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCE
Books and journals
Apruzzese, G. and et.al 2019, May. Addressing adversarial attacks against security systems
based on machine learning. In 2019 11th international conference on cyber conflict
(CyCon) (Vol. 900, pp. 1-18). IEEE.
Apruzzese, G. and et.al 2019, May. Addressing adversarial attacks against security systems
based on machine learning. In 2019 11th international conference on cyber conflict
(CyCon) (Vol. 900, pp. 1-18). IEEE.
Chadd, A., 2018. DDoS attacks: past, present and future. Network Security. 2018(7). pp.13-15.
Dibaei, M. and et.al 2019. An overview of attacks and defences on intelligent connected
vehicles. arXiv preprint arXiv:1907.07455.
Djenna, A. and Saïdouni, D.E., 2018, October. Cyber attacks classification in IoT-based-
healthcare infrastructure. In 2018 2nd Cyber Security in Networking Conference
(CSNet) (pp. 1-4). IEEE.
Gunduz, M.Z. and Das, R., 2020. Cyber-security on smart grid: Threats and potential
solutions. Computer networks. 169. p.107094.
Huang, X., Qin, Z. and Liu, H., 2018. A survey on power grid cyber security: From component-
wise vulnerability assessment to system-wide impact analysis. IEEE Access. 6.
pp.69023-69035.
Maglaras, L. and et.al 2019. Threats, protection and attribution of cyber attacks on critical
infrastructures. arXiv preprint arXiv:1901.03899.
Books and journals
Apruzzese, G. and et.al 2019, May. Addressing adversarial attacks against security systems
based on machine learning. In 2019 11th international conference on cyber conflict
(CyCon) (Vol. 900, pp. 1-18). IEEE.
Apruzzese, G. and et.al 2019, May. Addressing adversarial attacks against security systems
based on machine learning. In 2019 11th international conference on cyber conflict
(CyCon) (Vol. 900, pp. 1-18). IEEE.
Chadd, A., 2018. DDoS attacks: past, present and future. Network Security. 2018(7). pp.13-15.
Dibaei, M. and et.al 2019. An overview of attacks and defences on intelligent connected
vehicles. arXiv preprint arXiv:1907.07455.
Djenna, A. and Saïdouni, D.E., 2018, October. Cyber attacks classification in IoT-based-
healthcare infrastructure. In 2018 2nd Cyber Security in Networking Conference
(CSNet) (pp. 1-4). IEEE.
Gunduz, M.Z. and Das, R., 2020. Cyber-security on smart grid: Threats and potential
solutions. Computer networks. 169. p.107094.
Huang, X., Qin, Z. and Liu, H., 2018. A survey on power grid cyber security: From component-
wise vulnerability assessment to system-wide impact analysis. IEEE Access. 6.
pp.69023-69035.
Maglaras, L. and et.al 2019. Threats, protection and attribution of cyber attacks on critical
infrastructures. arXiv preprint arXiv:1901.03899.

Mohammadpourfard, M. and et.al 2020. Ensuring cybersecurity of smart grid against data
integrity attacks under concept drift. International Journal of Electrical Power & Energy
Systems. 119. p.105947.
Mosteanu, N.R., 2020. Artificial intelligence and cyber security–face to face with cyber attack–a
maltese case of risk management approach. Ecoforum Journal. 9(2).
Pandey, S. and et.al 2020. Cyber security risks in globalized supply chains: conceptual
framework. Journal of Global Operations and Strategic Sourcing.
Gunduz, M.Z. and Das, R., 2018, September. Analysis of cyber-attacks on smart grid
applications. In 2018 International Conference on Artificial Intelligence and Data
Processing (IDAP) (pp. 1-5). IEEE.
integrity attacks under concept drift. International Journal of Electrical Power & Energy
Systems. 119. p.105947.
Mosteanu, N.R., 2020. Artificial intelligence and cyber security–face to face with cyber attack–a
maltese case of risk management approach. Ecoforum Journal. 9(2).
Pandey, S. and et.al 2020. Cyber security risks in globalized supply chains: conceptual
framework. Journal of Global Operations and Strategic Sourcing.
Gunduz, M.Z. and Das, R., 2018, September. Analysis of cyber-attacks on smart grid
applications. In 2018 International Conference on Artificial Intelligence and Data
Processing (IDAP) (pp. 1-5). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





