SBM4304 IS Security & Risk Management: Threat Analysis and Solutions
VerifiedAdded on 2023/06/09
|16
|4607
|284
Report
AI Summary
This report examines various aspects of information security management, focusing on ransomware mechanisms and mitigation, threats to network routers, switches, web servers, and email servers. It explores risk management approaches and solutions in the context of Altova, an IS service provider. Topics include ransomware attack tools, network vulnerabilities like session hijacking and ARP spoofing, ensuring web service reliability through WS-Reliability protocols, and securing staff email using S/MIME and DKIM. The report also discusses the impact of human factors and organizational issues on IS security, recommending employee education and clear communication. Finally, it touches on log record analysis for monitoring web and email server problems and proposes network security devices for threat mitigation. Desklib provides access to this document and other solved assignments.

Running head: INFORMATION SYSTEM S SECURITY
IS security and Risk Management
Name of Student:
Name of College:
Authors Note:
1
IS security and Risk Management
Name of Student:
Name of College:
Authors Note:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM S SECURITY
Contents
2. Introduction.........................................................................................................................................2
3. Ransomware malwares threads against organization Information systems........................................2
a. Working mechanism of ransomware...................................................................................................2
b. Three tools to tackle the ransomware attack......................................................................................2
4. Threats against network routers and switches....................................................................................3
- How routers and switches are vulnerable to destruction and abuse....................................................4
5. Discussion on how the organization can ensure the reliability and availability of the web service.....4
6. The ways to ensure confidentiality and integrity of the staff email.....................................................5
7. Impact of human factors and organizational issues on IS-related security and risk management......6
Risk management recommendations......................................................................................................8
8. Illustration the use of logs records including security, access, event in monitoring and analyzing the
web server and email server problems...................................................................................................9
9. Discussion in detail the use of audit log reports for performing auditing analysis, supporting the
organization’s internal investigations, and indenting operational trends and log-term problems. In
particular for the email and web server issues........................................................................................9
10. Proposal of five network security devices to control security and mitigate threats related to the
web and email servers...........................................................................................................................10
13. Conclusions and Recommendations................................................................................................11
References.............................................................................................................................................12
2
Contents
2. Introduction.........................................................................................................................................2
3. Ransomware malwares threads against organization Information systems........................................2
a. Working mechanism of ransomware...................................................................................................2
b. Three tools to tackle the ransomware attack......................................................................................2
4. Threats against network routers and switches....................................................................................3
- How routers and switches are vulnerable to destruction and abuse....................................................4
5. Discussion on how the organization can ensure the reliability and availability of the web service.....4
6. The ways to ensure confidentiality and integrity of the staff email.....................................................5
7. Impact of human factors and organizational issues on IS-related security and risk management......6
Risk management recommendations......................................................................................................8
8. Illustration the use of logs records including security, access, event in monitoring and analyzing the
web server and email server problems...................................................................................................9
9. Discussion in detail the use of audit log reports for performing auditing analysis, supporting the
organization’s internal investigations, and indenting operational trends and log-term problems. In
particular for the email and web server issues........................................................................................9
10. Proposal of five network security devices to control security and mitigate threats related to the
web and email servers...........................................................................................................................10
13. Conclusions and Recommendations................................................................................................11
References.............................................................................................................................................12
2

INFORMATION SYSTEM S SECURITY
2. Introduction
In this report various aspects for information security management has been examined to
understand the various components including working mechanism of ransomware and ways to
deal with them. Also types of threat for routers, switches, web servers and email servers have
been taken into account and proper remedial actions have been examined to understand risk
management approaches and solutions that can prevent from security issues. All these
components have been discussed in context to Altova which is IS service provider firm operating
in US and Austria.
3. Ransomware malwares threads against organization Information systems.
a. Working mechanism of ransomware
According to Paytal, Sampalli & Rahman (2017) ransomware is a kind of malware that gets
installed in PC and starts running without user’s awareness. These are not hidden like malwares
that steals vital information. Ransomware after attacking device of user locks the device and/or
encrypts the files and alerts users of its existence to ask ransom. Ransomware works on either of
these mechanisms i.e. spam and social engineering, direct drive by download or malvertising or
malware installation tools and botnets. The most general working mechanism is phishing spams
attachments or emails that are sent to victim and they impersonate as a reliable file. And once
they are downloaded and opened they control victim’s device. Particularly if victim has in-built
social engineering tools then ransomware tricks victims to allow administrative access and take
control. While some ransomware exploits security walls to affect devices and do not depend on
tricking victims.
b. Three tools to tackle the ransomware attack
As stated by Han, Hoe, Wing & Brohi (2017) in order to tackle with ransomware attack Altova
can use the following tools:
3
2. Introduction
In this report various aspects for information security management has been examined to
understand the various components including working mechanism of ransomware and ways to
deal with them. Also types of threat for routers, switches, web servers and email servers have
been taken into account and proper remedial actions have been examined to understand risk
management approaches and solutions that can prevent from security issues. All these
components have been discussed in context to Altova which is IS service provider firm operating
in US and Austria.
3. Ransomware malwares threads against organization Information systems.
a. Working mechanism of ransomware
According to Paytal, Sampalli & Rahman (2017) ransomware is a kind of malware that gets
installed in PC and starts running without user’s awareness. These are not hidden like malwares
that steals vital information. Ransomware after attacking device of user locks the device and/or
encrypts the files and alerts users of its existence to ask ransom. Ransomware works on either of
these mechanisms i.e. spam and social engineering, direct drive by download or malvertising or
malware installation tools and botnets. The most general working mechanism is phishing spams
attachments or emails that are sent to victim and they impersonate as a reliable file. And once
they are downloaded and opened they control victim’s device. Particularly if victim has in-built
social engineering tools then ransomware tricks victims to allow administrative access and take
control. While some ransomware exploits security walls to affect devices and do not depend on
tricking victims.
b. Three tools to tackle the ransomware attack
As stated by Han, Hoe, Wing & Brohi (2017) in order to tackle with ransomware attack Altova
can use the following tools:
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEM S SECURITY
Observation of File system activity (SSDT): ransomware attacks can be tackled by monitoring of
file system activity. This approach hooks into SSDT and filtrates I/O requests and their
characteristics. Whenever a cluster of catious request is made, it is likely that subjected process
is malicious. So Altova can keep a log of SSDT so as to possibly remove virus or ransomware
that has infected devices.
Honeypots: as stated by 1Furnell & Emm (2017) these are used to locate malicious system
activity and can be used by Altova against ransomware attack. Honeypots places files into
systems that no user or application can tamper. So whenever ransomware vectors are sent to
victim devices they can access honeypot files. This will allow Altova’s system devices react to
intrusion and detect attack on files which can be applied to tackle with ransomware attacks.
Antivirus: this is common tool used to tackle with malicious attacks and is combination of
heuristics and signature dependent detection. Altova can use Antivirus which works by
maintaining a database of extorted signatures of familiar attacks. Whenever a file is run antivirus
uses on-access scanner and examines the files and its signatures against its signature database.
Moreover code of files gets examined in heuristic module. This combo permits antivirus to
detect ransomware attacks.
4. Threats against network routers and switches.
Some common threats to network routers of Altova can be:
Session hijacking: it happens when an intruder inserts false IP packets after setting of session
through IP spoofing, sequence number forecast and change or other methods.
Rerouting: as stated by Kreutz et al. (2015) it involves an attack that manipulates router updates
which allows traffic to flow to unauthorised destinations
Masquerading: it can happen when an intruder manipulates IP packets to fake IP address. With
this threat on network routers intruders get unauthorised access or injects forged data into
network.
Other common threats to switches of Altova can be:
4
Observation of File system activity (SSDT): ransomware attacks can be tackled by monitoring of
file system activity. This approach hooks into SSDT and filtrates I/O requests and their
characteristics. Whenever a cluster of catious request is made, it is likely that subjected process
is malicious. So Altova can keep a log of SSDT so as to possibly remove virus or ransomware
that has infected devices.
Honeypots: as stated by 1Furnell & Emm (2017) these are used to locate malicious system
activity and can be used by Altova against ransomware attack. Honeypots places files into
systems that no user or application can tamper. So whenever ransomware vectors are sent to
victim devices they can access honeypot files. This will allow Altova’s system devices react to
intrusion and detect attack on files which can be applied to tackle with ransomware attacks.
Antivirus: this is common tool used to tackle with malicious attacks and is combination of
heuristics and signature dependent detection. Altova can use Antivirus which works by
maintaining a database of extorted signatures of familiar attacks. Whenever a file is run antivirus
uses on-access scanner and examines the files and its signatures against its signature database.
Moreover code of files gets examined in heuristic module. This combo permits antivirus to
detect ransomware attacks.
4. Threats against network routers and switches.
Some common threats to network routers of Altova can be:
Session hijacking: it happens when an intruder inserts false IP packets after setting of session
through IP spoofing, sequence number forecast and change or other methods.
Rerouting: as stated by Kreutz et al. (2015) it involves an attack that manipulates router updates
which allows traffic to flow to unauthorised destinations
Masquerading: it can happen when an intruder manipulates IP packets to fake IP address. With
this threat on network routers intruders get unauthorised access or injects forged data into
network.
Other common threats to switches of Altova can be:
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM S SECURITY
ARP spoofing: In this intruder sends fake ARP messages that link intruder’s MAC address with
IP address of victim device or server. Once MAC address is conjoined to initial IP address
intruders gets data which is planned for IP address. This threat can allow intruders intercept,
modify or stop data in-transmit.
ARP poisoning: as opined by Daş, Karabade & Tuna (2015) in this threat intruder’s changes
MAC address and strikes LAN switches through tampering targeted device ARP cache with
forged ARP request and reply packets. This threat changes genuine address to intruders
recognised MAC address with an intention to monitor. As such victim’s data and privacy gets
compromised.
P2P traffic: this is used to share large quantity of data directly to specific computer on internet
and it is predicted that for any ISP nearly 80% of traffic is consumed by P2P traffic. These are
used to distribute Bots, spywares, adwares, Trojans, Rootkits by sending malicious files from
P2P environment.
- How routers and switches are vulnerable to destruction and abuse.
According to Daş, Karabade & Tuna (2015) routers and switches are susceptible to destructions
and abuse due to mis-constructed hardware or software, inappropriate network design, inherent
technology flaws, end user negligence and due to voluntary end users actions such as acts of
aggrieved staffs.
5. Discussion on how the organization can ensure the reliability and
availability of the web service.
Altova can insure reliability and availability of web service through Web service Reliable
Messaging (WS-Reliability) protocols. As stated by Liu, Jia, Xue & An (2015) these will insure
effective, asynchronous reliable message distribution. According to Alsaleh, Alarifi, Alqahtani &
Al-Salman (2014) the archetype of WS-Reliability protocol aids composition with other
messaging and web service standards and descriptions. It comprises of WS-Reliable Messaging,
WS-Addressing, WSDL, WS-Policy, WS-Transactions and WS-Coordination, WS-End Point
5
ARP spoofing: In this intruder sends fake ARP messages that link intruder’s MAC address with
IP address of victim device or server. Once MAC address is conjoined to initial IP address
intruders gets data which is planned for IP address. This threat can allow intruders intercept,
modify or stop data in-transmit.
ARP poisoning: as opined by Daş, Karabade & Tuna (2015) in this threat intruder’s changes
MAC address and strikes LAN switches through tampering targeted device ARP cache with
forged ARP request and reply packets. This threat changes genuine address to intruders
recognised MAC address with an intention to monitor. As such victim’s data and privacy gets
compromised.
P2P traffic: this is used to share large quantity of data directly to specific computer on internet
and it is predicted that for any ISP nearly 80% of traffic is consumed by P2P traffic. These are
used to distribute Bots, spywares, adwares, Trojans, Rootkits by sending malicious files from
P2P environment.
- How routers and switches are vulnerable to destruction and abuse.
According to Daş, Karabade & Tuna (2015) routers and switches are susceptible to destructions
and abuse due to mis-constructed hardware or software, inappropriate network design, inherent
technology flaws, end user negligence and due to voluntary end users actions such as acts of
aggrieved staffs.
5. Discussion on how the organization can ensure the reliability and
availability of the web service.
Altova can insure reliability and availability of web service through Web service Reliable
Messaging (WS-Reliability) protocols. As stated by Liu, Jia, Xue & An (2015) these will insure
effective, asynchronous reliable message distribution. According to Alsaleh, Alarifi, Alqahtani &
Al-Salman (2014) the archetype of WS-Reliability protocol aids composition with other
messaging and web service standards and descriptions. It comprises of WS-Reliable Messaging,
WS-Addressing, WSDL, WS-Policy, WS-Transactions and WS-Coordination, WS-End Point
5

INFORMATION SYSTEM S SECURITY
Resolution, WS- Meta Data Exchange, WS-Security Roadmap Protocols, WS-Transmission
Control to permit message to be distributed reliably between web services.
6. The ways to ensure confidentiality and integrity of the staff email.
Approaches Altova can utilise to improve availability, confidentiality and integrity of email
server are:
Secure Multipurpose Internet Email Extensions (S/MIME): according to Islam, Farah & Stafford
(2018) this is an email safeguard standard that can be utilised to provide authentication and
confidentiality of email servers with public key encryption and digital signatures. Verification is
allowed with X.509 digital certificates and confidentiality is through with Public Key
Cryptography Standard (PKCS) encryption.
Fig: Sequence of encrypting email with S/MIME
Source: Technet (2018)
Domain Keys Identified Mail (DKIM): Altova can use DKIM technology to cut down malicious
and unwanted mails from their email servers to improve its availability. According to Kaur,
Gupta & Singh (2018) DKIM is domain level digital signature authentication archetype for email
servers that allow signing domain to assert responsibility using signature based method. It
authenticates identity and reliability of sender and their email for handling delivery. This
authentication for emails servers is validated with cryptography signature and querying signer’s
domain to retrieve public key.
6
Resolution, WS- Meta Data Exchange, WS-Security Roadmap Protocols, WS-Transmission
Control to permit message to be distributed reliably between web services.
6. The ways to ensure confidentiality and integrity of the staff email.
Approaches Altova can utilise to improve availability, confidentiality and integrity of email
server are:
Secure Multipurpose Internet Email Extensions (S/MIME): according to Islam, Farah & Stafford
(2018) this is an email safeguard standard that can be utilised to provide authentication and
confidentiality of email servers with public key encryption and digital signatures. Verification is
allowed with X.509 digital certificates and confidentiality is through with Public Key
Cryptography Standard (PKCS) encryption.
Fig: Sequence of encrypting email with S/MIME
Source: Technet (2018)
Domain Keys Identified Mail (DKIM): Altova can use DKIM technology to cut down malicious
and unwanted mails from their email servers to improve its availability. According to Kaur,
Gupta & Singh (2018) DKIM is domain level digital signature authentication archetype for email
servers that allow signing domain to assert responsibility using signature based method. It
authenticates identity and reliability of sender and their email for handling delivery. This
authentication for emails servers is validated with cryptography signature and querying signer’s
domain to retrieve public key.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
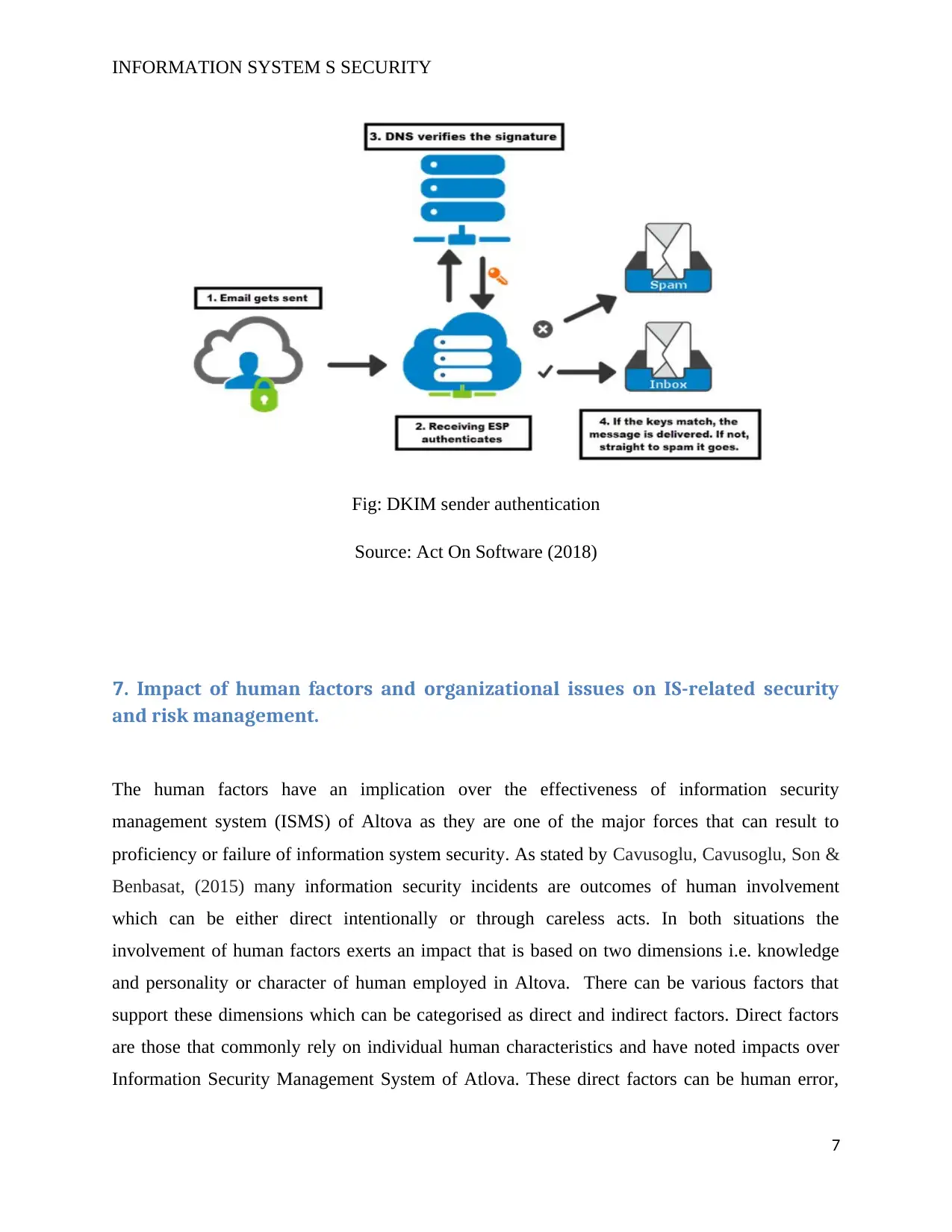
INFORMATION SYSTEM S SECURITY
Fig: DKIM sender authentication
Source: Act On Software (2018)
7. Impact of human factors and organizational issues on IS-related security
and risk management.
The human factors have an implication over the effectiveness of information security
management system (ISMS) of Altova as they are one of the major forces that can result to
proficiency or failure of information system security. As stated by Cavusoglu, Cavusoglu, Son &
Benbasat, (2015) many information security incidents are outcomes of human involvement
which can be either direct intentionally or through careless acts. In both situations the
involvement of human factors exerts an impact that is based on two dimensions i.e. knowledge
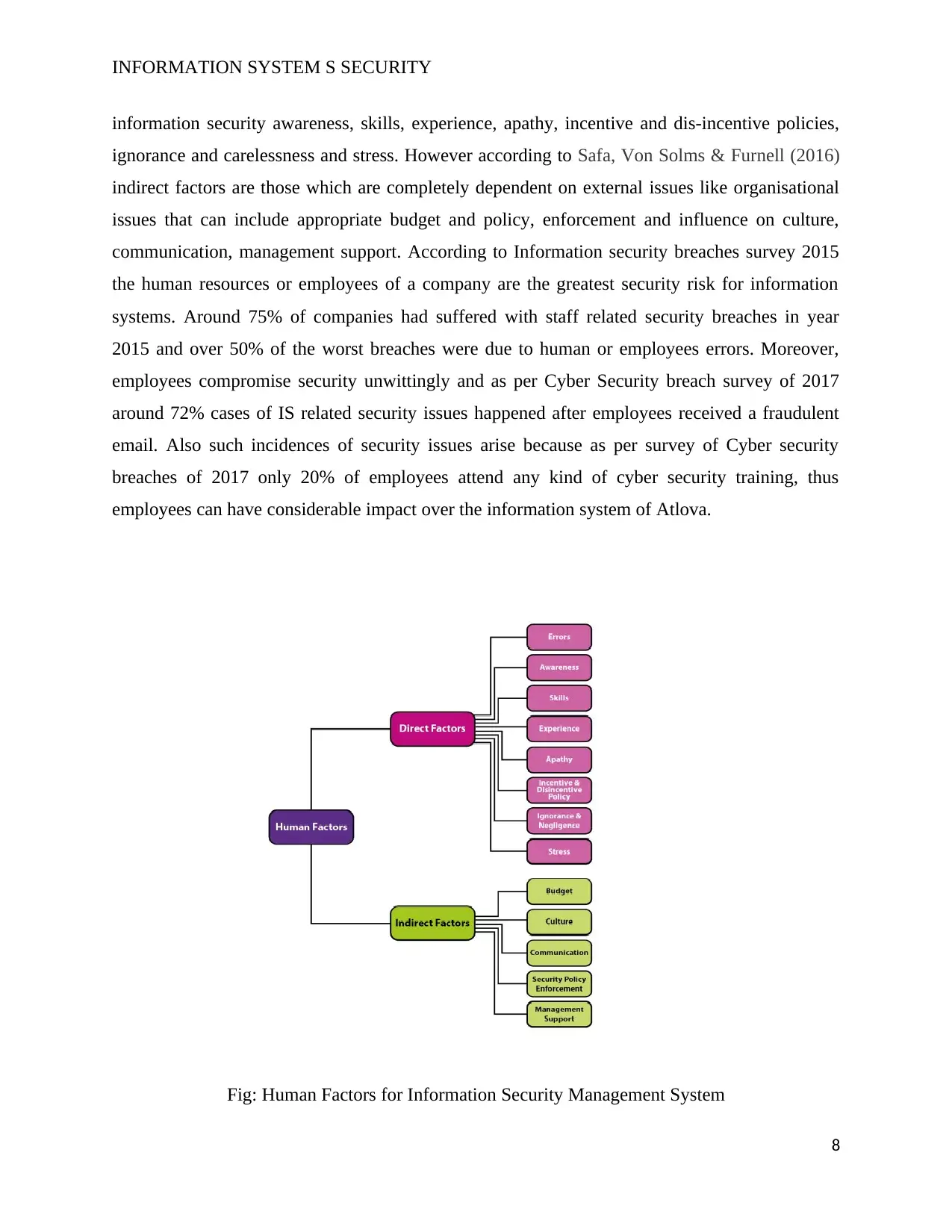
and personality or character of human employed in Altova. There can be various factors that
support these dimensions which can be categorised as direct and indirect factors. Direct factors
are those that commonly rely on individual human characteristics and have noted impacts over
Information Security Management System of Atlova. These direct factors can be human error,
7
Fig: DKIM sender authentication
Source: Act On Software (2018)
7. Impact of human factors and organizational issues on IS-related security
and risk management.
The human factors have an implication over the effectiveness of information security
management system (ISMS) of Altova as they are one of the major forces that can result to
proficiency or failure of information system security. As stated by Cavusoglu, Cavusoglu, Son &
Benbasat, (2015) many information security incidents are outcomes of human involvement
which can be either direct intentionally or through careless acts. In both situations the
involvement of human factors exerts an impact that is based on two dimensions i.e. knowledge
and personality or character of human employed in Altova. There can be various factors that
support these dimensions which can be categorised as direct and indirect factors. Direct factors
are those that commonly rely on individual human characteristics and have noted impacts over
Information Security Management System of Atlova. These direct factors can be human error,
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SYSTEM S SECURITY
information security awareness, skills, experience, apathy, incentive and dis-incentive policies,
ignorance and carelessness and stress. However according to Safa, Von Solms & Furnell (2016)
indirect factors are those which are completely dependent on external issues like organisational
issues that can include appropriate budget and policy, enforcement and influence on culture,
communication, management support. According to Information security breaches survey 2015
the human resources or employees of a company are the greatest security risk for information
systems. Around 75% of companies had suffered with staff related security breaches in year
2015 and over 50% of the worst breaches were due to human or employees errors. Moreover,
employees compromise security unwittingly and as per Cyber Security breach survey of 2017
around 72% cases of IS related security issues happened after employees received a fraudulent
email. Also such incidences of security issues arise because as per survey of Cyber security
breaches of 2017 only 20% of employees attend any kind of cyber security training, thus
employees can have considerable impact over the information system of Atlova.
Fig: Human Factors for Information Security Management System
8
information security awareness, skills, experience, apathy, incentive and dis-incentive policies,
ignorance and carelessness and stress. However according to Safa, Von Solms & Furnell (2016)
indirect factors are those which are completely dependent on external issues like organisational
issues that can include appropriate budget and policy, enforcement and influence on culture,
communication, management support. According to Information security breaches survey 2015
the human resources or employees of a company are the greatest security risk for information
systems. Around 75% of companies had suffered with staff related security breaches in year
2015 and over 50% of the worst breaches were due to human or employees errors. Moreover,
employees compromise security unwittingly and as per Cyber Security breach survey of 2017
around 72% cases of IS related security issues happened after employees received a fraudulent
email. Also such incidences of security issues arise because as per survey of Cyber security
breaches of 2017 only 20% of employees attend any kind of cyber security training, thus
employees can have considerable impact over the information system of Atlova.
Fig: Human Factors for Information Security Management System
8

INFORMATION SYSTEM S SECURITY
Source: Research Gate (2013)
Risk management recommendations
In order to reduce the risk of employees on information system of Atlova education of
employees is the major preventive where employees can be made aware of cyber security and
their threats like phishing mails, insecure network etc. Some recommendation that Atlova can
consider to reduce risk are:
Clear communication of possible impact of cyber accidents: according to Soomro, Shah &
Ahmed (2016) as most staffs are not aware on possible undermining that is directed through
them with poor cyber hygiene so it is advisable for Atlova to communicate to their employees
the implications of cyber incidents and related financial loss or fines to damaged client
confidence. This will help to generate awareness and maintenance of cyber hygiene.
Making cyber security as responsibility for everyone: Atlova can organise education program
and ensure that everyone in company starting from top should be part of training and no one
should be immune of such education programs. According to Frey & Osborne (2017) this will
build responsiveness of everyone towards IT infrastructure of Atlova which will avert the risk of
ignorance or negligence or intentional incidents.
Customising training on organisation need: According to Simmonds (2017) the employees of
Atlova can be trained as per their specific training requisites to boost employee awareness and
immune organisation needs for protecting its IT infrastructure. This training can vary from
confidential waste destructions to encryption of data or emails. This training will allow
employees of Atlova to imply knowledge on their routine roles which makes them more likely to
minimise risks of potential security issues.
Imparting learning on effective password management: According to Tsohou, Karyda &
Kokolakis (2015) as passwords are vital for information security systems so Atlova can execute a
robust password policy by issuing their employees guidelines on password requisites and
stressing need to generate robust and ideal passwords. Also employees should be imparted
teaching on password management and should be warned from not sharing their passwords.
9
Source: Research Gate (2013)
Risk management recommendations
In order to reduce the risk of employees on information system of Atlova education of
employees is the major preventive where employees can be made aware of cyber security and
their threats like phishing mails, insecure network etc. Some recommendation that Atlova can
consider to reduce risk are:
Clear communication of possible impact of cyber accidents: according to Soomro, Shah &
Ahmed (2016) as most staffs are not aware on possible undermining that is directed through
them with poor cyber hygiene so it is advisable for Atlova to communicate to their employees
the implications of cyber incidents and related financial loss or fines to damaged client
confidence. This will help to generate awareness and maintenance of cyber hygiene.
Making cyber security as responsibility for everyone: Atlova can organise education program
and ensure that everyone in company starting from top should be part of training and no one
should be immune of such education programs. According to Frey & Osborne (2017) this will
build responsiveness of everyone towards IT infrastructure of Atlova which will avert the risk of
ignorance or negligence or intentional incidents.
Customising training on organisation need: According to Simmonds (2017) the employees of
Atlova can be trained as per their specific training requisites to boost employee awareness and
immune organisation needs for protecting its IT infrastructure. This training can vary from
confidential waste destructions to encryption of data or emails. This training will allow
employees of Atlova to imply knowledge on their routine roles which makes them more likely to
minimise risks of potential security issues.
Imparting learning on effective password management: According to Tsohou, Karyda &
Kokolakis (2015) as passwords are vital for information security systems so Atlova can execute a
robust password policy by issuing their employees guidelines on password requisites and
stressing need to generate robust and ideal passwords. Also employees should be imparted
teaching on password management and should be warned from not sharing their passwords.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SYSTEM S SECURITY
Training employees to identify and respond to attack: Atlova can provide effective training to
their employees before the IS related security arises. They can document a remedial plan and
training can involve particular rules like unplugging device from network in case of attack. Also
employees can be offered channels like urgent numbers to alert administrators’ on any form of
suspected emails or unusual activities.
8. Illustration the use of logs records including security, access, event in
monitoring and analyzing the web server and email server problems.
According to Morton et al. (2018) the log records can aid in observing and examining web and
email server concerns as these generate log files which are entry for every event or exchange that
occurs on hardware or a device and serves as journal of record. Example MS based systems
create Windows event log files and UNIX based servers and networking machines create System
Log or Syslog. These logs can be used to manage compliance with company’s IT policies
through monitoring, audit and report on file ingression, unauthorised act, practise change etc. As
stated by Khan et al. (2016) a1 regular monitoring of distinct log events gives vital information
about the user who has on logged into the network and details their activities. Hence analysis of
event logs is essential for security reasons to interpret Information system vulnerability and
determine if any susceptibility exists in security implementation. By using event and log
management archetype companies can manage staggering amount of log information created in a
system at regular intervals to understand real time access to log data which allows segregating
and locating that specific suspected event which may create security issues or breach.
9. Discussion in detail the use of audit log reports for performing auditing
analysis, supporting the organization’s internal investigations, and indenting
operational trends and log-term problems. In particular for the email and web
server issues
The usage of audit log reports can help in detecting and analysing the intrusion activities that
may go unobserved and it helps in providing evidence of either or not the event resulted into
breach. According to Groomer & Murthy(2018) frequent gathering of audit logs helps to make
vital decisions for firms by supporting their interpretation of nature of security incidents in case
10
Training employees to identify and respond to attack: Atlova can provide effective training to
their employees before the IS related security arises. They can document a remedial plan and
training can involve particular rules like unplugging device from network in case of attack. Also
employees can be offered channels like urgent numbers to alert administrators’ on any form of
suspected emails or unusual activities.
8. Illustration the use of logs records including security, access, event in
monitoring and analyzing the web server and email server problems.
According to Morton et al. (2018) the log records can aid in observing and examining web and
email server concerns as these generate log files which are entry for every event or exchange that
occurs on hardware or a device and serves as journal of record. Example MS based systems
create Windows event log files and UNIX based servers and networking machines create System
Log or Syslog. These logs can be used to manage compliance with company’s IT policies
through monitoring, audit and report on file ingression, unauthorised act, practise change etc. As
stated by Khan et al. (2016) a1 regular monitoring of distinct log events gives vital information
about the user who has on logged into the network and details their activities. Hence analysis of
event logs is essential for security reasons to interpret Information system vulnerability and
determine if any susceptibility exists in security implementation. By using event and log
management archetype companies can manage staggering amount of log information created in a
system at regular intervals to understand real time access to log data which allows segregating
and locating that specific suspected event which may create security issues or breach.
9. Discussion in detail the use of audit log reports for performing auditing
analysis, supporting the organization’s internal investigations, and indenting
operational trends and log-term problems. In particular for the email and web
server issues
The usage of audit log reports can help in detecting and analysing the intrusion activities that
may go unobserved and it helps in providing evidence of either or not the event resulted into
breach. According to Groomer & Murthy(2018) frequent gathering of audit logs helps to make
vital decisions for firms by supporting their interpretation of nature of security incidents in case
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SYSTEM S SECURITY
of active internal investigations and post mortem evaluation. Moreover audit log reports are
important to set baselines and helps in recognising operational trends and log-term problems
during internal investigation including audit and forensic analysis. A proficient audit logging
program in an organisation can detect in earlier hand the security incident and impact to avert
theft of data. Thus enabling low impact of data breach compared to an organisation where
intruders download bulk covered data over long time without being noticed.
In particular for email and web servers logs should cover information in context to specific
events that may take place impacting a covered device. Audit log reports should include OS
events such as record of start and shut down of system, network connectivity change or failure,
attempt to modify security setting and control. These audit log reports should also include OS
audit records such as log on attempts, account change etc along with maintaining report for
Application Account Information that can cover authentication attempts, application account
changes etc. Further audit log reports should also include Application operations over web
servers and emails that can include application start and shutdown, application failure,
configuration change, application transactions. For example, email servers tracking sender,
recipients, subject name and attachment names for all mail, web servers tracking URL requests
and kind of return by server and business functions tracking financial data that were ingress by
usage.
10. Proposal of five network security devices to control security and mitigate
threats related to the web and email servers.
The network security devices that can be used for web and email servers are:
Scanners: as stated by Kreutz et al. (2015) these can be used to automate and make the process of
web server security easier. These when activated will scan the web server hosts of web
applications and will launch advanced security checks against network services running on web
servers. These scanners insure security of website and web servers by examining for SQL,
Injection, Cross site scripting, configuration issues in server and susceptibilities. These also
validate password tenacity on verification pages and naturally examine websites, contents and
applications.
11
of active internal investigations and post mortem evaluation. Moreover audit log reports are
important to set baselines and helps in recognising operational trends and log-term problems
during internal investigation including audit and forensic analysis. A proficient audit logging
program in an organisation can detect in earlier hand the security incident and impact to avert
theft of data. Thus enabling low impact of data breach compared to an organisation where
intruders download bulk covered data over long time without being noticed.
In particular for email and web servers logs should cover information in context to specific
events that may take place impacting a covered device. Audit log reports should include OS
events such as record of start and shut down of system, network connectivity change or failure,
attempt to modify security setting and control. These audit log reports should also include OS
audit records such as log on attempts, account change etc along with maintaining report for
Application Account Information that can cover authentication attempts, application account
changes etc. Further audit log reports should also include Application operations over web
servers and emails that can include application start and shutdown, application failure,
configuration change, application transactions. For example, email servers tracking sender,
recipients, subject name and attachment names for all mail, web servers tracking URL requests
and kind of return by server and business functions tracking financial data that were ingress by
usage.
10. Proposal of five network security devices to control security and mitigate
threats related to the web and email servers.
The network security devices that can be used for web and email servers are:
Scanners: as stated by Kreutz et al. (2015) these can be used to automate and make the process of
web server security easier. These when activated will scan the web server hosts of web
applications and will launch advanced security checks against network services running on web
servers. These scanners insure security of website and web servers by examining for SQL,
Injection, Cross site scripting, configuration issues in server and susceptibilities. These also
validate password tenacity on verification pages and naturally examine websites, contents and
applications.
11

INFORMATION SYSTEM S SECURITY
Security information and event management (SIEM): as stated by Stojmenovic & Wen (2014)
these devices can be used to combine all information required to enable security of web servers
and networks through identification and response to threats. These are available in virtual and
physical appliances and server software form.
Next Generation Firewall (NGFS): according to Sicari, Rizzardi, Grieco & Coen-Porisini (2015)
these devices set a defence for network and web server attacks by creating a wall between
reliable internal network and unknown outside networks. These can be a hardware or software
device such as Cisco Firepower NGFW that unites proven firewall network with effective IPS
and advanced malware protection. These also allows better visibility, are more lucid and more
protected.
Unified threat management (UTM): these devices offer various security characteristics and
offerings in single device or network that protects customers from strikes. UTM involves multi-
functions like anti-virus, anti-spam, content filtering and web filtering.
Email security: these application devices can be used to block inward attacks and controls
outward messages to protect loss of confidential data.
13. Conclusions and Recommendations
Thus it can be concluded that as information security systems are exposed to vulnerability so a
proper risk management plan should be developed prior in hand. The recommendations include
designing of risk management and mitigation plan as per needs of IT infrastructure and
generating awareness among people in organisation with proper training. Also regular
monitoring should be done to check activities and any suspicious event should be immediately
taken into concern and examined for making effective decision making for security.
12
Security information and event management (SIEM): as stated by Stojmenovic & Wen (2014)
these devices can be used to combine all information required to enable security of web servers
and networks through identification and response to threats. These are available in virtual and
physical appliances and server software form.
Next Generation Firewall (NGFS): according to Sicari, Rizzardi, Grieco & Coen-Porisini (2015)
these devices set a defence for network and web server attacks by creating a wall between
reliable internal network and unknown outside networks. These can be a hardware or software
device such as Cisco Firepower NGFW that unites proven firewall network with effective IPS
and advanced malware protection. These also allows better visibility, are more lucid and more
protected.
Unified threat management (UTM): these devices offer various security characteristics and
offerings in single device or network that protects customers from strikes. UTM involves multi-
functions like anti-virus, anti-spam, content filtering and web filtering.
Email security: these application devices can be used to block inward attacks and controls
outward messages to protect loss of confidential data.
13. Conclusions and Recommendations
Thus it can be concluded that as information security systems are exposed to vulnerability so a
proper risk management plan should be developed prior in hand. The recommendations include
designing of risk management and mitigation plan as per needs of IT infrastructure and
generating awareness among people in organisation with proper training. Also regular
monitoring should be done to check activities and any suspicious event should be immediately
taken into concern and examined for making effective decision making for security.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

