IT Audit Report for Telecommunication Industry
VerifiedAdded on 2022/11/19
|13
|2808
|107
AI Summary
This report provides an overview of the security threats faced by the telecommunication industry and suggests various techniques for administrative, physical, and technical protection. It also discusses incident handling and the importance of following legal and regulatory frameworks for securing data and business processes.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Running Head: IT Audit 0
IT Audit
Report
Student name
IT Audit
Report
Student name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Audit 1
Table of Contents
Introduction......................................................................................................................................2
Administrative Protection:...............................................................................................................5
Physical Protection:.........................................................................................................................6
Technical Protection:.......................................................................................................................7
Incident handling:........................................................................................................................7
Public-key infrastructure (PKI)...................................................................................................8
Summary..........................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................2
Administrative Protection:...............................................................................................................5
Physical Protection:.........................................................................................................................6
Technical Protection:.......................................................................................................................7
Incident handling:........................................................................................................................7
Public-key infrastructure (PKI)...................................................................................................8
Summary..........................................................................................................................................9
References......................................................................................................................................11

IT Audit 2
Introduction
ABC Company is a well-known company in the field of telecommunication from the last
two decades. Therefore, it is necessary to make a good image in the marketplace. There are many
threats in a network, which is making a huge impact on the organization in term of damage to
reputation and financial losses (Jadoun, 2018). In addition, those threats make a huge impact on
the organization for a long time. Therefore, the organization should maintain proper security
policies and arrangement too secure all the business process and its data and information from
the attacker (Security-trails, 2018).
In addition, most of the common reason of security breach is computer viruses in the
system because of human mistakes. According to many surveys and research, various types of
computer viruses affect more than 33 % of computer systems. Therefore, it is necessary to secure
computer systems first then a secure network and other devices from malware. Trojan horse is
another reason of security losses. It is a program that id hiding behind a program as well. Those
malicious programs can theft passwords, and any data from computer systems.
A denial-of-service attack is a common thing in computer and telecommunication sector
in which all the services will stop by a program. There is much another attack on the computer
system, which is phishing; rootkit, SQL Injection, and man-in-the-middle attack are common in
this industry.
There are some physical threats that make a huge impact on the financial conditions of an
organization. These can be divided into parts, which areas:
Internal threats: Power supply issue, fire, humidity, and others
External threats: earthquakes, floods, and lightning, and many others
Human mistakes: vandalism, theft, accidental issues, hardware disruption, and
more
Moreover, security issues have arisen in the telecommunication industry because of
various other reasons, such as hacking of PBX, adware, spyware, and many other malfunctions.
In addition, phone hacking, H.323 toll fraud, and Session Initiation Protocol (SIP) make a huge
loss, which is not affordable by an organization. All those frauds make a huge cost, which is not
good for all those organizations. It makes an impact on their financial and reputation factor,
which is direct, affects their business and growth in the market (Vyopta, 2018).
Introduction
ABC Company is a well-known company in the field of telecommunication from the last
two decades. Therefore, it is necessary to make a good image in the marketplace. There are many
threats in a network, which is making a huge impact on the organization in term of damage to
reputation and financial losses (Jadoun, 2018). In addition, those threats make a huge impact on
the organization for a long time. Therefore, the organization should maintain proper security
policies and arrangement too secure all the business process and its data and information from
the attacker (Security-trails, 2018).
In addition, most of the common reason of security breach is computer viruses in the
system because of human mistakes. According to many surveys and research, various types of
computer viruses affect more than 33 % of computer systems. Therefore, it is necessary to secure
computer systems first then a secure network and other devices from malware. Trojan horse is
another reason of security losses. It is a program that id hiding behind a program as well. Those
malicious programs can theft passwords, and any data from computer systems.
A denial-of-service attack is a common thing in computer and telecommunication sector
in which all the services will stop by a program. There is much another attack on the computer
system, which is phishing; rootkit, SQL Injection, and man-in-the-middle attack are common in
this industry.
There are some physical threats that make a huge impact on the financial conditions of an
organization. These can be divided into parts, which areas:
Internal threats: Power supply issue, fire, humidity, and others
External threats: earthquakes, floods, and lightning, and many others
Human mistakes: vandalism, theft, accidental issues, hardware disruption, and
more
Moreover, security issues have arisen in the telecommunication industry because of
various other reasons, such as hacking of PBX, adware, spyware, and many other malfunctions.
In addition, phone hacking, H.323 toll fraud, and Session Initiation Protocol (SIP) make a huge
loss, which is not affordable by an organization. All those frauds make a huge cost, which is not
good for all those organizations. It makes an impact on their financial and reputation factor,
which is direct, affects their business and growth in the market (Vyopta, 2018).
IT Audit 3
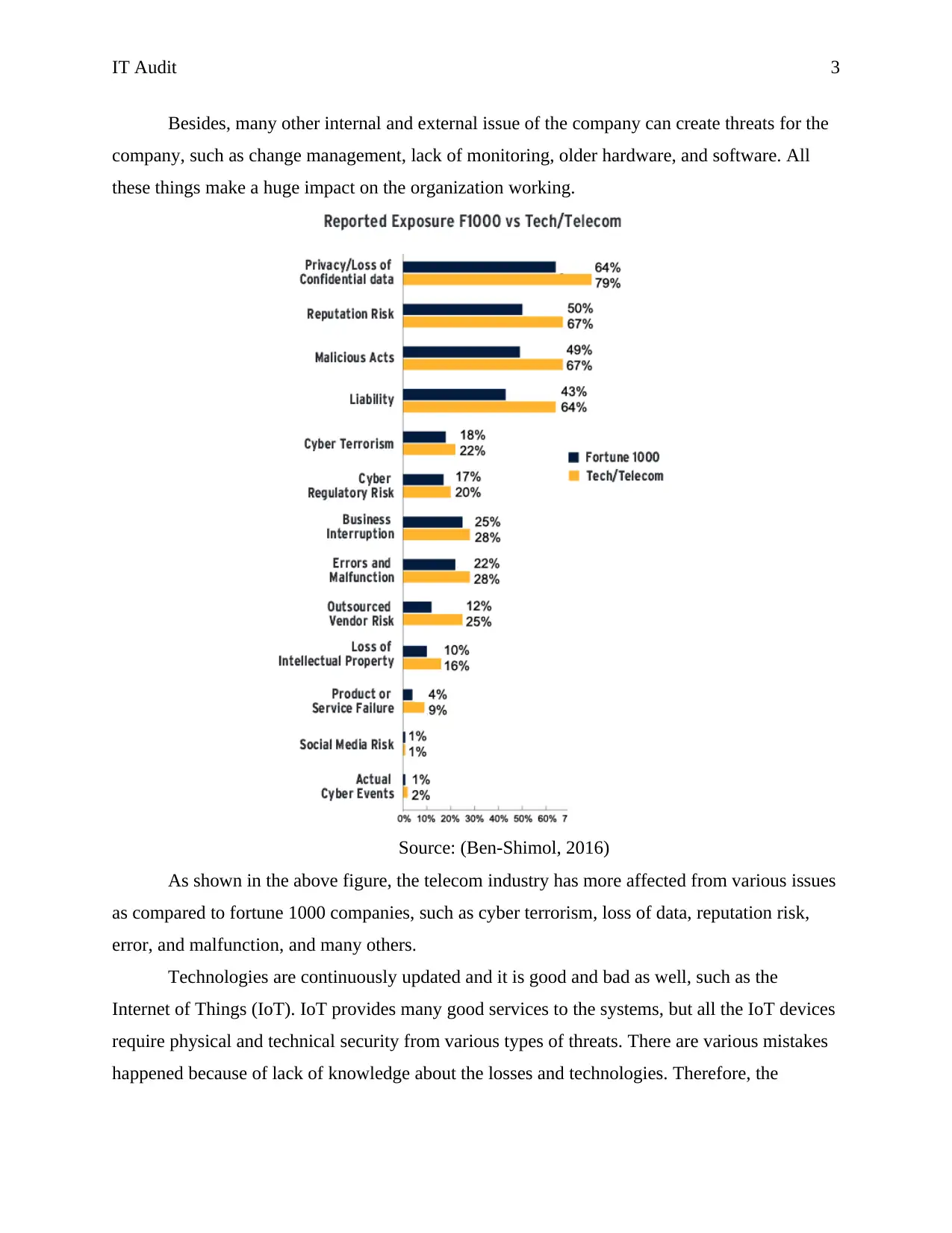
Besides, many other internal and external issue of the company can create threats for the
company, such as change management, lack of monitoring, older hardware, and software. All
these things make a huge impact on the organization working.
Source: (Ben-Shimol, 2016)
As shown in the above figure, the telecom industry has more affected from various issues
as compared to fortune 1000 companies, such as cyber terrorism, loss of data, reputation risk,
error, and malfunction, and many others.
Technologies are continuously updated and it is good and bad as well, such as the
Internet of Things (IoT). IoT provides many good services to the systems, but all the IoT devices
require physical and technical security from various types of threats. There are various mistakes
happened because of lack of knowledge about the losses and technologies. Therefore, the
Besides, many other internal and external issue of the company can create threats for the
company, such as change management, lack of monitoring, older hardware, and software. All
these things make a huge impact on the organization working.
Source: (Ben-Shimol, 2016)
As shown in the above figure, the telecom industry has more affected from various issues
as compared to fortune 1000 companies, such as cyber terrorism, loss of data, reputation risk,
error, and malfunction, and many others.
Technologies are continuously updated and it is good and bad as well, such as the
Internet of Things (IoT). IoT provides many good services to the systems, but all the IoT devices
require physical and technical security from various types of threats. There are various mistakes
happened because of lack of knowledge about the losses and technologies. Therefore, the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IT Audit 4
company should provide proper training to their employees to follow all the rule and regulations
properly.
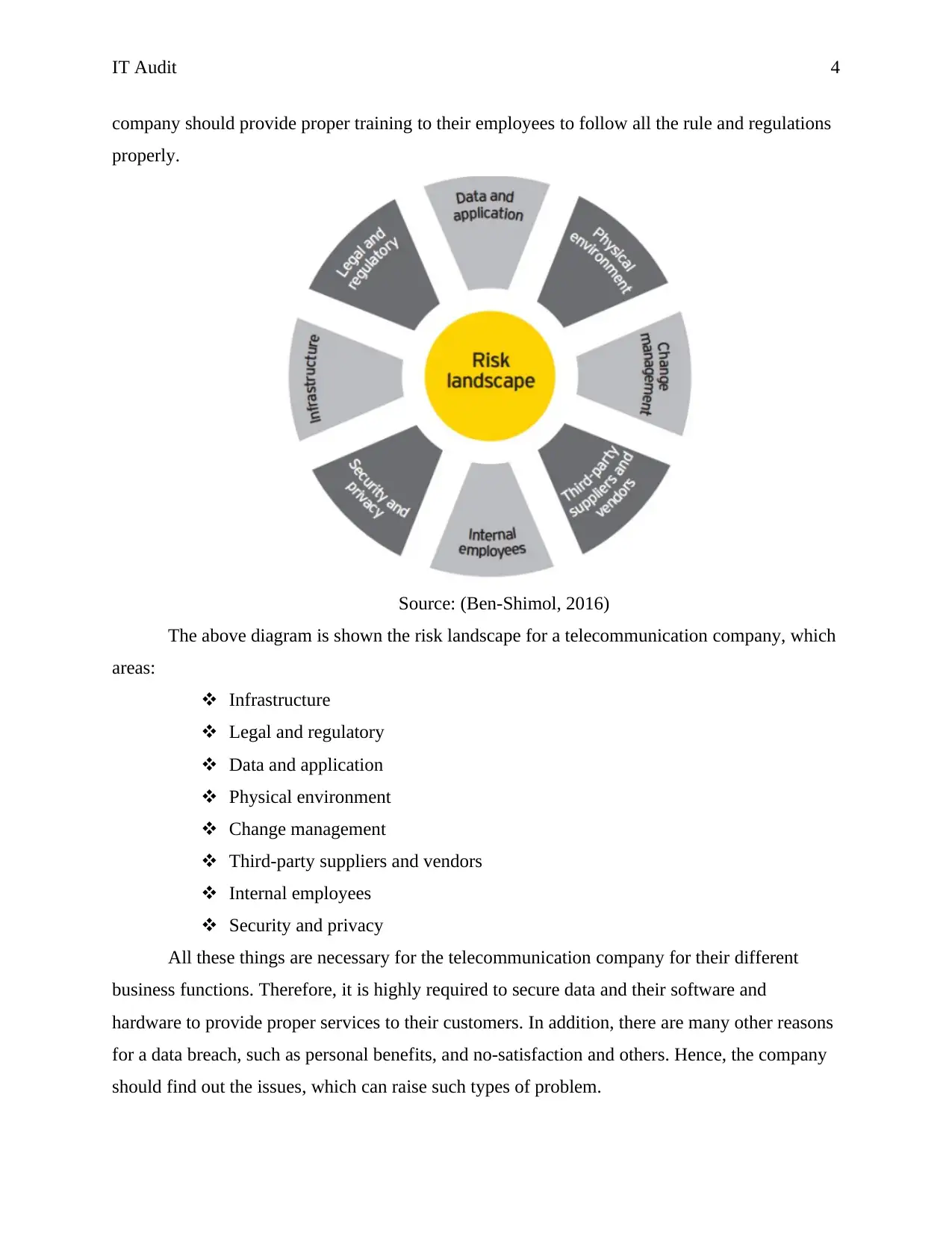
Source: (Ben-Shimol, 2016)
The above diagram is shown the risk landscape for a telecommunication company, which
areas:
Infrastructure
Legal and regulatory
Data and application
Physical environment
Change management
Third-party suppliers and vendors
Internal employees
Security and privacy
All these things are necessary for the telecommunication company for their different
business functions. Therefore, it is highly required to secure data and their software and
hardware to provide proper services to their customers. In addition, there are many other reasons
for a data breach, such as personal benefits, and no-satisfaction and others. Hence, the company
should find out the issues, which can raise such types of problem.
company should provide proper training to their employees to follow all the rule and regulations
properly.
Source: (Ben-Shimol, 2016)
The above diagram is shown the risk landscape for a telecommunication company, which
areas:
Infrastructure
Legal and regulatory
Data and application
Physical environment
Change management
Third-party suppliers and vendors
Internal employees
Security and privacy
All these things are necessary for the telecommunication company for their different
business functions. Therefore, it is highly required to secure data and their software and
hardware to provide proper services to their customers. In addition, there are many other reasons
for a data breach, such as personal benefits, and no-satisfaction and others. Hence, the company
should find out the issues, which can raise such types of problem.

IT Audit 5
Administrative Protection:
A telecommunication company can affect from these threats, which are a malfunction,
Distributed Denial of Serve (DDoS) attack, phishing, social engineering, internal threats, and
vulnerabilities within customer devices and network. Their attacks can potentially damage many
things including website damages, service interruption, loss of reputation, and data theft.
There are various legal and regularities can be used to control such type of attacks.
However, these threats can be low but not removed from the industry. Moreover, Telecom
Company can prefer more secure software and hardware to improve its performance and
efficiency of services.in addition, there are some external threats for telecommunication, such as
the cost of the devices, and many others (Wolfe, 2018).
The National Information Technology Council of Malaysia has provided many rule and
regulations for the telecommunication company. Computer systems have used in the
telecommunication company, which required proper security of data and other processes.
Communications and Multimedia Act 1998 has created to provide and regulate the
converging communication and multimedia industry. There are some sets of guidelines and
regulations for data and network management (Toh, 2019). After some crucial incidents in this
industry, the government has created different laws for the telecommunication industry, few laws
areas:
Personal Data Protection Act of 2010
Financial Services Act of 2013
Consumer Protection Act of 1999
Computer Crimes Act of 1997
Electronic Commerce Act of 2006
Digital Signature Act of 1997
There are various techniques in administrative protection of the telecommunication
company. In addition, most of the companies have data about their consumers for billing and
other works. CMA is providing security to their data and information. Consumer Protection Act
1999 has been used to make sure all the data of consumers at the end of the company. There is a
security part, which must complete by the company.
Administrative Protection:
A telecommunication company can affect from these threats, which are a malfunction,
Distributed Denial of Serve (DDoS) attack, phishing, social engineering, internal threats, and
vulnerabilities within customer devices and network. Their attacks can potentially damage many
things including website damages, service interruption, loss of reputation, and data theft.
There are various legal and regularities can be used to control such type of attacks.
However, these threats can be low but not removed from the industry. Moreover, Telecom
Company can prefer more secure software and hardware to improve its performance and
efficiency of services.in addition, there are some external threats for telecommunication, such as
the cost of the devices, and many others (Wolfe, 2018).
The National Information Technology Council of Malaysia has provided many rule and
regulations for the telecommunication company. Computer systems have used in the
telecommunication company, which required proper security of data and other processes.
Communications and Multimedia Act 1998 has created to provide and regulate the
converging communication and multimedia industry. There are some sets of guidelines and
regulations for data and network management (Toh, 2019). After some crucial incidents in this
industry, the government has created different laws for the telecommunication industry, few laws
areas:
Personal Data Protection Act of 2010
Financial Services Act of 2013
Consumer Protection Act of 1999
Computer Crimes Act of 1997
Electronic Commerce Act of 2006
Digital Signature Act of 1997
There are various techniques in administrative protection of the telecommunication
company. In addition, most of the companies have data about their consumers for billing and
other works. CMA is providing security to their data and information. Consumer Protection Act
1999 has been used to make sure all the data of consumers at the end of the company. There is a
security part, which must complete by the company.

IT Audit 6
Physical Protection:
Physical safety is the safety of personnel of an organization as well as hardware, software
program, networks, and records from physical actions, which is necessary for the company.
Besides, occasions that could motive extreme loss or harm to an organization. Moreover, this
includes protection from fire, flood, robbery, vandalism, cyber-attacks, DOS, and terrorism.
However, the physical is often left out that is good for the system and its significance
underestimated. Besides, in prefer of greater technical threats consisting of hacking, malware,
and cyber espionage in the company. However, breaches of Physical protection can be
completed with brute pressure that can be happened because of various reasons. Threats can
make the system weaker. Therefore, the company makes better functions to secure all the
systems (Key-factor, 2017).
The internet of things (IoT) is beneficial for data collection using various devices. The
sector of physical safety as smart devices linked to commercial enterprise structures using the
internet. It may be placed outside of hooked up relaxed perimeters. Keeping apart those clever
devices cannot be performed inside the same way as the ones within an employer's physical
access. Therefore, the tool area will play a key position in retaining device secure, comfortable,
and fully purposeful within the outdoor world (Masucci, 2016).
Privacy and security are necessary for a company, which include various types of policies
and rules to make secure all the information assets and personnel. IoT uses motion sensors for
data collection and many other works. In addition, physical security is necessary for assets as
well (Rouse, 2018).
Furthermore, the company should adopt proper security personnel to provide security to
hardware parts of the company from any internal and external issue. It will reduce many issues
of security of the company (Security-trails, 2018).
Technical Protection:
In general, technical protection is the first step to secure all the information assets and
data and information of the company and their consumers. There are many cryptographic
techniques, which can be used in the telecommunication industry for the protection of data and
network.
Physical Protection:
Physical safety is the safety of personnel of an organization as well as hardware, software
program, networks, and records from physical actions, which is necessary for the company.
Besides, occasions that could motive extreme loss or harm to an organization. Moreover, this
includes protection from fire, flood, robbery, vandalism, cyber-attacks, DOS, and terrorism.
However, the physical is often left out that is good for the system and its significance
underestimated. Besides, in prefer of greater technical threats consisting of hacking, malware,
and cyber espionage in the company. However, breaches of Physical protection can be
completed with brute pressure that can be happened because of various reasons. Threats can
make the system weaker. Therefore, the company makes better functions to secure all the
systems (Key-factor, 2017).
The internet of things (IoT) is beneficial for data collection using various devices. The
sector of physical safety as smart devices linked to commercial enterprise structures using the
internet. It may be placed outside of hooked up relaxed perimeters. Keeping apart those clever
devices cannot be performed inside the same way as the ones within an employer's physical
access. Therefore, the tool area will play a key position in retaining device secure, comfortable,
and fully purposeful within the outdoor world (Masucci, 2016).
Privacy and security are necessary for a company, which include various types of policies
and rules to make secure all the information assets and personnel. IoT uses motion sensors for
data collection and many other works. In addition, physical security is necessary for assets as
well (Rouse, 2018).
Furthermore, the company should adopt proper security personnel to provide security to
hardware parts of the company from any internal and external issue. It will reduce many issues
of security of the company (Security-trails, 2018).
Technical Protection:
In general, technical protection is the first step to secure all the information assets and
data and information of the company and their consumers. There are many cryptographic
techniques, which can be used in the telecommunication industry for the protection of data and
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Audit 7
Cloud computing is the best solution for securing data from hacker and other things
(Kshetri, 2013). There should be internal and external policies must implement in the company
to protect data of customers. The company should follow technical standards for securing data
and other things, such as ITU-T X.800 framework.
In addition, ITU-T X.1086 has provided security using telebiometric systems. It provides
proper authorization for installing and uninstalling of devices in a network. Therefore, the system
in the supervision of authorized personnel. Moreover, cybersecurity is necessary to secure all the
information assets of the company from cyber-attacks. Technical issues can be avoided using
proper security channels.
Source: (Lee, 2015)
Incident handling:
Technical education is necessary for all customers and employees. Therefore, the
company should provide rule and regulation about the uses of various devices and services. If
there is any mistake found by the customers than they should inform the company about it within
minimum time. In addition, people overlook the incidents, which create an issue ( Beaver, 2013).
Rivest, Shamir & Adleman (RSA) cryptographic algorithm is the best way to secure all
the data and information at the end of the company and another method uses a combination of
Hawthorne Facsimile Cipher (HFX), and Hawthorne Key Management (HKM).
Cloud computing is the best solution for securing data from hacker and other things
(Kshetri, 2013). There should be internal and external policies must implement in the company
to protect data of customers. The company should follow technical standards for securing data
and other things, such as ITU-T X.800 framework.
In addition, ITU-T X.1086 has provided security using telebiometric systems. It provides
proper authorization for installing and uninstalling of devices in a network. Therefore, the system
in the supervision of authorized personnel. Moreover, cybersecurity is necessary to secure all the
information assets of the company from cyber-attacks. Technical issues can be avoided using
proper security channels.
Source: (Lee, 2015)
Incident handling:
Technical education is necessary for all customers and employees. Therefore, the
company should provide rule and regulation about the uses of various devices and services. If
there is any mistake found by the customers than they should inform the company about it within
minimum time. In addition, people overlook the incidents, which create an issue ( Beaver, 2013).
Rivest, Shamir & Adleman (RSA) cryptographic algorithm is the best way to secure all
the data and information at the end of the company and another method uses a combination of
Hawthorne Facsimile Cipher (HFX), and Hawthorne Key Management (HKM).
IT Audit 8
Source: (Lee, 2015)
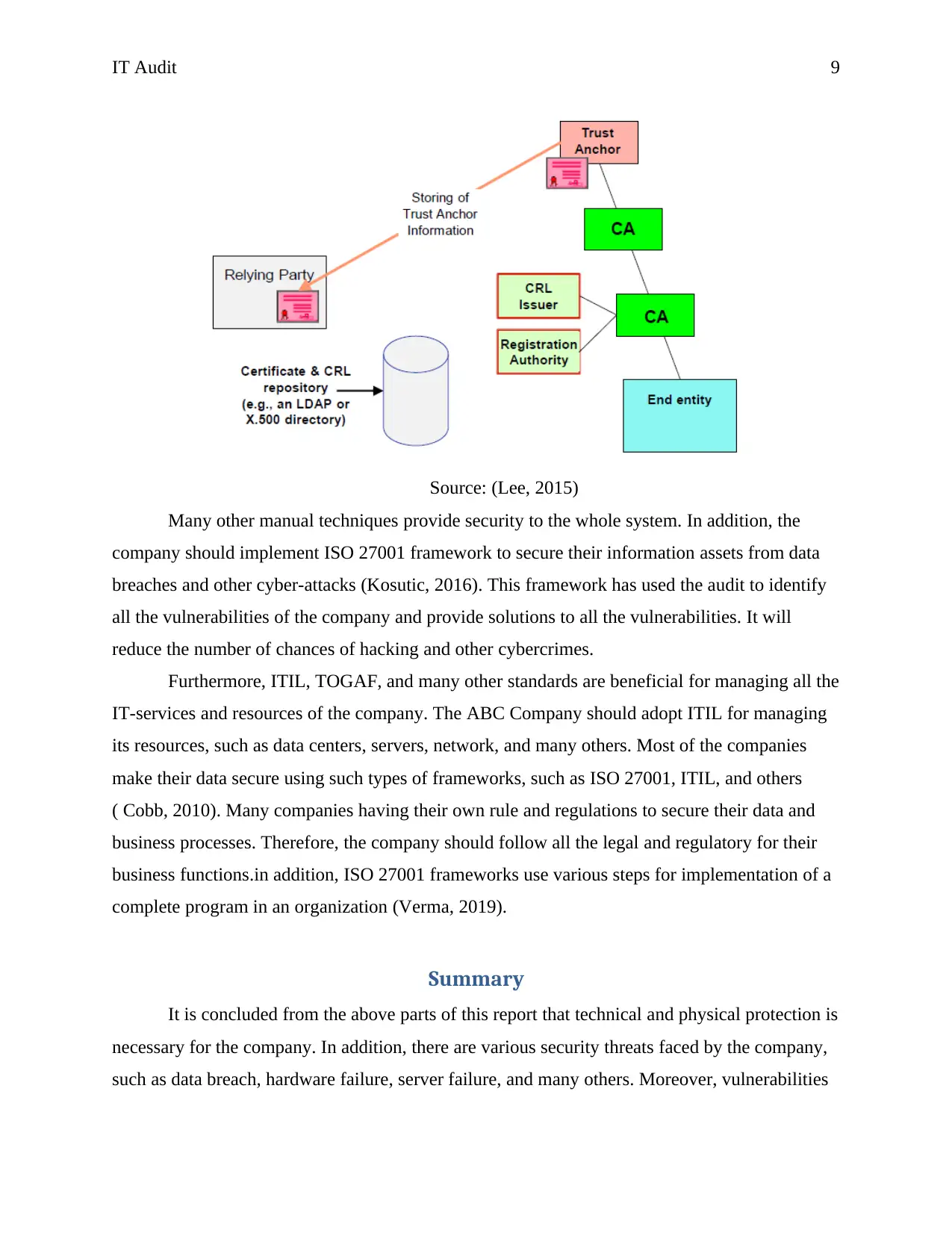
There are various methods for securing data and other processes, which areas:
Public-key infrastructure (PKI)
PKI is the best way to secure data from an intermediary. In addition, it provides authority
to the access to data and information only authorized users of the company. PKI can provide
secure transmission of data and other things, such as audio, video, and others. Certification
Authority (CA) has provided authority to end users to access data and network only authorized
users only. The ABC Company should hire cybersecurity experts for the implementation of
various management skills in employees and in the system. It will improve knowledge of all the
employees, as they are not aware of security and privacy because of technical and physical
issues. In addition, security issues make a system weak. Therefore, all the threats should manage
by the company using various approaches (Sanchez, 2010).
Source: (Lee, 2015)
There are various methods for securing data and other processes, which areas:
Public-key infrastructure (PKI)
PKI is the best way to secure data from an intermediary. In addition, it provides authority
to the access to data and information only authorized users of the company. PKI can provide
secure transmission of data and other things, such as audio, video, and others. Certification
Authority (CA) has provided authority to end users to access data and network only authorized
users only. The ABC Company should hire cybersecurity experts for the implementation of
various management skills in employees and in the system. It will improve knowledge of all the
employees, as they are not aware of security and privacy because of technical and physical
issues. In addition, security issues make a system weak. Therefore, all the threats should manage
by the company using various approaches (Sanchez, 2010).
IT Audit 9
Source: (Lee, 2015)
Many other manual techniques provide security to the whole system. In addition, the
company should implement ISO 27001 framework to secure their information assets from data
breaches and other cyber-attacks (Kosutic, 2016). This framework has used the audit to identify
all the vulnerabilities of the company and provide solutions to all the vulnerabilities. It will
reduce the number of chances of hacking and other cybercrimes.
Furthermore, ITIL, TOGAF, and many other standards are beneficial for managing all the
IT-services and resources of the company. The ABC Company should adopt ITIL for managing
its resources, such as data centers, servers, network, and many others. Most of the companies
make their data secure using such types of frameworks, such as ISO 27001, ITIL, and others
( Cobb, 2010). Many companies having their own rule and regulations to secure their data and
business processes. Therefore, the company should follow all the legal and regulatory for their
business functions.in addition, ISO 27001 frameworks use various steps for implementation of a
complete program in an organization (Verma, 2019).
Summary
It is concluded from the above parts of this report that technical and physical protection is
necessary for the company. In addition, there are various security threats faced by the company,
such as data breach, hardware failure, server failure, and many others. Moreover, vulnerabilities
Source: (Lee, 2015)
Many other manual techniques provide security to the whole system. In addition, the
company should implement ISO 27001 framework to secure their information assets from data
breaches and other cyber-attacks (Kosutic, 2016). This framework has used the audit to identify
all the vulnerabilities of the company and provide solutions to all the vulnerabilities. It will
reduce the number of chances of hacking and other cybercrimes.
Furthermore, ITIL, TOGAF, and many other standards are beneficial for managing all the
IT-services and resources of the company. The ABC Company should adopt ITIL for managing
its resources, such as data centers, servers, network, and many others. Most of the companies
make their data secure using such types of frameworks, such as ISO 27001, ITIL, and others
( Cobb, 2010). Many companies having their own rule and regulations to secure their data and
business processes. Therefore, the company should follow all the legal and regulatory for their
business functions.in addition, ISO 27001 frameworks use various steps for implementation of a
complete program in an organization (Verma, 2019).
Summary
It is concluded from the above parts of this report that technical and physical protection is
necessary for the company. In addition, there are various security threats faced by the company,
such as data breach, hardware failure, server failure, and many others. Moreover, vulnerabilities
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT Audit 10
make high chances for loss of data and other things. Besides, data breach makes a huge impact
on the reputation of the ABC Company.
Hence, the company should initiate an audit for their resources and information assets to
find out different vulnerabilities after that implement cybersecurity and another standard
framework to secure all the tangible and non-tangible resources and infrastructure using various
types of technical protection, such as RSA, and others. It is necessary to implement cybersecurity
to secure servers and data centers of the company. It will secure all the data and information of
the business process data as well as consumers personal information.
Finally, the company should follow all the standards and regulations to secure data of
their consumers. Hence, the company should implement cloud-based services to secure all the
data and information in the cloud to take competitive advantage as well. It will make a good
image in the market and consumers.
make high chances for loss of data and other things. Besides, data breach makes a huge impact
on the reputation of the ABC Company.
Hence, the company should initiate an audit for their resources and information assets to
find out different vulnerabilities after that implement cybersecurity and another standard
framework to secure all the tangible and non-tangible resources and infrastructure using various
types of technical protection, such as RSA, and others. It is necessary to implement cybersecurity
to secure servers and data centers of the company. It will secure all the data and information of
the business process data as well as consumers personal information.
Finally, the company should follow all the standards and regulations to secure data of
their consumers. Hence, the company should implement cloud-based services to secure all the
data and information in the cloud to take competitive advantage as well. It will make a good
image in the market and consumers.

IT Audit 11
References
Beaver, K. (2013). Top 5 Common Network Security Vulnerabilities that Are Often Overlooked.
Retrieved from acunetix.com: https://www.acunetix.com/blog/articles/the-top-5-network-
security-vulnerabilities/
Cobb, M. (2010). ISO 27001 SoA: Creating an information security policy document. Retrieved
March 12, 2019, from https://www.computerweekly.com/tip/ISO-27001-SoA-Creating-
an-information-security-policy-document
Ben-Shimol, S. (2016, March 23). March 23, 2016 — by Snir Ben-Shimol — 2. Retrieved from
https://blog.radware.com: https://blog.radware.com/security/2016/03/cyber-security-
threats-in-telecom/
Jadoun, M. (2018, March 16). Top 5 challenges and trends in the telecommunication industry in
2019. Retrieved from https://www.racknap.com: https://www.racknap.com/blog/top-5-
challenges-trends-telecommunication-industry/
Key-factor. (2017, January 26). Cyber Threats to Telecom. Retrieved from
https://blog.keyfactor.com: https://blog.keyfactor.com/cyber-threats-to-telecom
Kosutic, D. (2016). What should you write in your Information Security Policy according to ISO
27001? Retrieved March 12, 2019, from
https://advisera.com/27001academy/blog/2016/05/30/what-should-you-write-in-your-
information-security-policy-according-to-iso-27001/
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of institutions and
institutional evolution. Telecommunications Policy, 37(4-5), 372-386.
Lee, C. (2015). SECURITY IN TELECOMMUNICATIONS AND INFORMATION
TECHNOLOGY. Switzerland: Telecommunication.
Masucci, M. (2016, April 3). 4 Ways to Ensure Network Physical Security. Retrieved from
https://www.belden.com: https://www.belden.com/blog/smart-building/4-ways-to-ensure-
network-physical-security
Rouse, M. (2018, July 12). physical security. Retrieved from
https://searchsecurity.techtarget.com:
References
Beaver, K. (2013). Top 5 Common Network Security Vulnerabilities that Are Often Overlooked.
Retrieved from acunetix.com: https://www.acunetix.com/blog/articles/the-top-5-network-
security-vulnerabilities/
Cobb, M. (2010). ISO 27001 SoA: Creating an information security policy document. Retrieved
March 12, 2019, from https://www.computerweekly.com/tip/ISO-27001-SoA-Creating-
an-information-security-policy-document
Ben-Shimol, S. (2016, March 23). March 23, 2016 — by Snir Ben-Shimol — 2. Retrieved from
https://blog.radware.com: https://blog.radware.com/security/2016/03/cyber-security-
threats-in-telecom/
Jadoun, M. (2018, March 16). Top 5 challenges and trends in the telecommunication industry in
2019. Retrieved from https://www.racknap.com: https://www.racknap.com/blog/top-5-
challenges-trends-telecommunication-industry/
Key-factor. (2017, January 26). Cyber Threats to Telecom. Retrieved from
https://blog.keyfactor.com: https://blog.keyfactor.com/cyber-threats-to-telecom
Kosutic, D. (2016). What should you write in your Information Security Policy according to ISO
27001? Retrieved March 12, 2019, from
https://advisera.com/27001academy/blog/2016/05/30/what-should-you-write-in-your-
information-security-policy-according-to-iso-27001/
Kshetri, N. (2013). Privacy and security issues in cloud computing: The role of institutions and
institutional evolution. Telecommunications Policy, 37(4-5), 372-386.
Lee, C. (2015). SECURITY IN TELECOMMUNICATIONS AND INFORMATION
TECHNOLOGY. Switzerland: Telecommunication.
Masucci, M. (2016, April 3). 4 Ways to Ensure Network Physical Security. Retrieved from
https://www.belden.com: https://www.belden.com/blog/smart-building/4-ways-to-ensure-
network-physical-security
Rouse, M. (2018, July 12). physical security. Retrieved from
https://searchsecurity.techtarget.com:

IT Audit 12
https://searchsecurity.techtarget.com/definition/physical-security
Sanchez, M. (2010). The 10 most common security threats explained. Retrieved December 12,
2018, from https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained
Security-trails. (2018, October 16). Top 10 Common Network Security Threats Explained.
Retrieved from https://securitytrails.com: https://securitytrails.com/blog/top-10-common-
network-security-threats-explained
Toh, J. (2019, July 11). Overview. Retrieved from https://iclg.com: https://iclg.com/practice-
areas/telecoms-media-and-internet-laws-and-regulations/malaysia
Verma, S. (2019, January 26). ISO 27001 Implementation — Step By Step Guide. Retrieved April
8, 2019, from https://www.sync-resource.com/blog/iso-27001-implementation-guide/
Vyopta. (2018, December 3). Telecommunication Security Issues and Telecom PBX Hacking
Explained. Retrieved from https://www.vyopta.com:
https://www.vyopta.com/blog/business-collaboration/telecommunications-security-
vulnerabilties/
Wolfe, S. (2018, April 26). Top External Digital Threats to the Telecommunications Industry.
Retrieved from https://www.zerofox.com: https://www.zerofox.com/blog/top-threats-
telecommunications/
https://searchsecurity.techtarget.com/definition/physical-security
Sanchez, M. (2010). The 10 most common security threats explained. Retrieved December 12,
2018, from https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained
Security-trails. (2018, October 16). Top 10 Common Network Security Threats Explained.
Retrieved from https://securitytrails.com: https://securitytrails.com/blog/top-10-common-
network-security-threats-explained
Toh, J. (2019, July 11). Overview. Retrieved from https://iclg.com: https://iclg.com/practice-
areas/telecoms-media-and-internet-laws-and-regulations/malaysia
Verma, S. (2019, January 26). ISO 27001 Implementation — Step By Step Guide. Retrieved April
8, 2019, from https://www.sync-resource.com/blog/iso-27001-implementation-guide/
Vyopta. (2018, December 3). Telecommunication Security Issues and Telecom PBX Hacking
Explained. Retrieved from https://www.vyopta.com:
https://www.vyopta.com/blog/business-collaboration/telecommunications-security-
vulnerabilties/
Wolfe, S. (2018, April 26). Top External Digital Threats to the Telecommunications Industry.
Retrieved from https://www.zerofox.com: https://www.zerofox.com/blog/top-threats-
telecommunications/
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





