Virtualization and Cloud Infrastructure: Enhancing IT Efficiency
VerifiedAdded on 2020/10/05
|13
|3457
|149
AI Summary
The research paper explores virtualization within IT infrastructure, emphasizing its integration with cloud computing. It examines how this synergy enhances resource allocation and operational efficiency across data centers. The paper outlines foundational network architecture principles, detailing IP addressing's role in providing unique system identities. Moreover, it contrasts the Microsoft Azure platform with Amazon Web Services (AWS), illustrating distinct service offerings tailored to organizational needs. Through a layered communication framework, virtualization is positioned as a strategic tool for simulating non-physical resources effectively. The document aims to offer comprehensive insights into these technologies' transformative impact on IT management.

IT Infrastructure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Task I...............................................................................................................................................1
1. Discuss geographical scope of network along with network backbone devices and
categorisation of network segments.......................................................................................1
2. Development of logic design based on three-layer hierarchical model. Give details of
required network devices and servers.....................................................................................4
3. Identification of type of IP addresses along with their subnet mask..................................5
Task II..............................................................................................................................................6
1. Propose two organisations which provide cloud services for hosting email and web servers.
................................................................................................................................................6
2. Outline techniques for usage of service virtualisation and implementation of cloud
platforms.................................................................................................................................7
3. How cloud computing support dynamic scaling of CBA applications..............................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................1
Task I...............................................................................................................................................1
1. Discuss geographical scope of network along with network backbone devices and
categorisation of network segments.......................................................................................1
2. Development of logic design based on three-layer hierarchical model. Give details of
required network devices and servers.....................................................................................4
3. Identification of type of IP addresses along with their subnet mask..................................5
Task II..............................................................................................................................................6
1. Propose two organisations which provide cloud services for hosting email and web servers.
................................................................................................................................................6
2. Outline techniques for usage of service virtualisation and implementation of cloud
platforms.................................................................................................................................7
3. How cloud computing support dynamic scaling of CBA applications..............................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
IT infrastructure is generally referred to set of a component which acts as foundation for
IT services. Information technology refers to anything which is associated with computing
technology like software, networking, internet, hardware or people who are making use of
technology (Ajamieh and et. al, 2016). This assignment is based on Commonwealth Bank of
Australia also known by CommBank or CBA. It is a public bank which provides banking and
financial services. It is an Australian multinational bank which is headquartered in Darling
Harbour, Sydney, Australia. It provides its services worldwide with around 1100 branches and
approx. 4300 ATM's. This report includes geographical scope of network, three layer
hierarchical model, IP addresses along with subnet mask. Furthermore, two organisations are
taken which renders cloud services, techniques of virtualisation and dynamic scaling of cloud
computing.
Task I
1. Discuss geographical scope of network along with network backbone devices and
categorisation of network segments.
Geographical scope of CBA (Commonwealth Bank of Australia) in given context that is
they are about to start their branch which will have 8 floors and each PC will be connected to
network point. As it covers small area than LAN is the best option which can be taken into
consideration. It is explained below:
Local area network (LAN): It is is defined as a computer number which is restricted to small
office or a building. It is basically owned maintained and owned by individual organisation
(Gardner, Boyer and Gray, 2015). CBA can opt for this network as it provides high bandwidth
which ranges from 100 Mbps, 1 Gbps to 10 Gbps.
1
IT infrastructure is generally referred to set of a component which acts as foundation for
IT services. Information technology refers to anything which is associated with computing
technology like software, networking, internet, hardware or people who are making use of
technology (Ajamieh and et. al, 2016). This assignment is based on Commonwealth Bank of
Australia also known by CommBank or CBA. It is a public bank which provides banking and
financial services. It is an Australian multinational bank which is headquartered in Darling
Harbour, Sydney, Australia. It provides its services worldwide with around 1100 branches and
approx. 4300 ATM's. This report includes geographical scope of network, three layer
hierarchical model, IP addresses along with subnet mask. Furthermore, two organisations are
taken which renders cloud services, techniques of virtualisation and dynamic scaling of cloud
computing.
Task I
1. Discuss geographical scope of network along with network backbone devices and
categorisation of network segments.
Geographical scope of CBA (Commonwealth Bank of Australia) in given context that is
they are about to start their branch which will have 8 floors and each PC will be connected to
network point. As it covers small area than LAN is the best option which can be taken into
consideration. It is explained below:
Local area network (LAN): It is is defined as a computer number which is restricted to small
office or a building. It is basically owned maintained and owned by individual organisation
(Gardner, Boyer and Gray, 2015). CBA can opt for this network as it provides high bandwidth
which ranges from 100 Mbps, 1 Gbps to 10 Gbps.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Illustration 1: Local Area Network
They can make use of Gigabit Ethernet 1/10 Gbps or FastEthernet 100 Mbps by which
there bandwidth will be high or will remain almost constant (Knyazkov and et. al, 2012). They
make use of Ethernet as LAN Standard. This can be used to carry out interaction within the
building but when they want to interact with with other branches they can make use of Wide area
network (WAN). CBA can opt for either wired or wireless connections.
Backbone network: It is a part of computer network which interlink different pieces of network
thereby provides a path for transmission of information in between subnetwork or LANs.
Backbone ties up diverse networks which are present within same building (Larsen, Patterson
and El-Geneidy, 2013). This means that CBA can make use of backbone network as this will
assist them to transfer data within a network. They are different backbone devices they are
shown below:
2
They can make use of Gigabit Ethernet 1/10 Gbps or FastEthernet 100 Mbps by which
there bandwidth will be high or will remain almost constant (Knyazkov and et. al, 2012). They
make use of Ethernet as LAN Standard. This can be used to carry out interaction within the
building but when they want to interact with with other branches they can make use of Wide area
network (WAN). CBA can opt for either wired or wireless connections.
Backbone network: It is a part of computer network which interlink different pieces of network
thereby provides a path for transmission of information in between subnetwork or LANs.
Backbone ties up diverse networks which are present within same building (Larsen, Patterson
and El-Geneidy, 2013). This means that CBA can make use of backbone network as this will
assist them to transfer data within a network. They are different backbone devices they are
shown below:
2
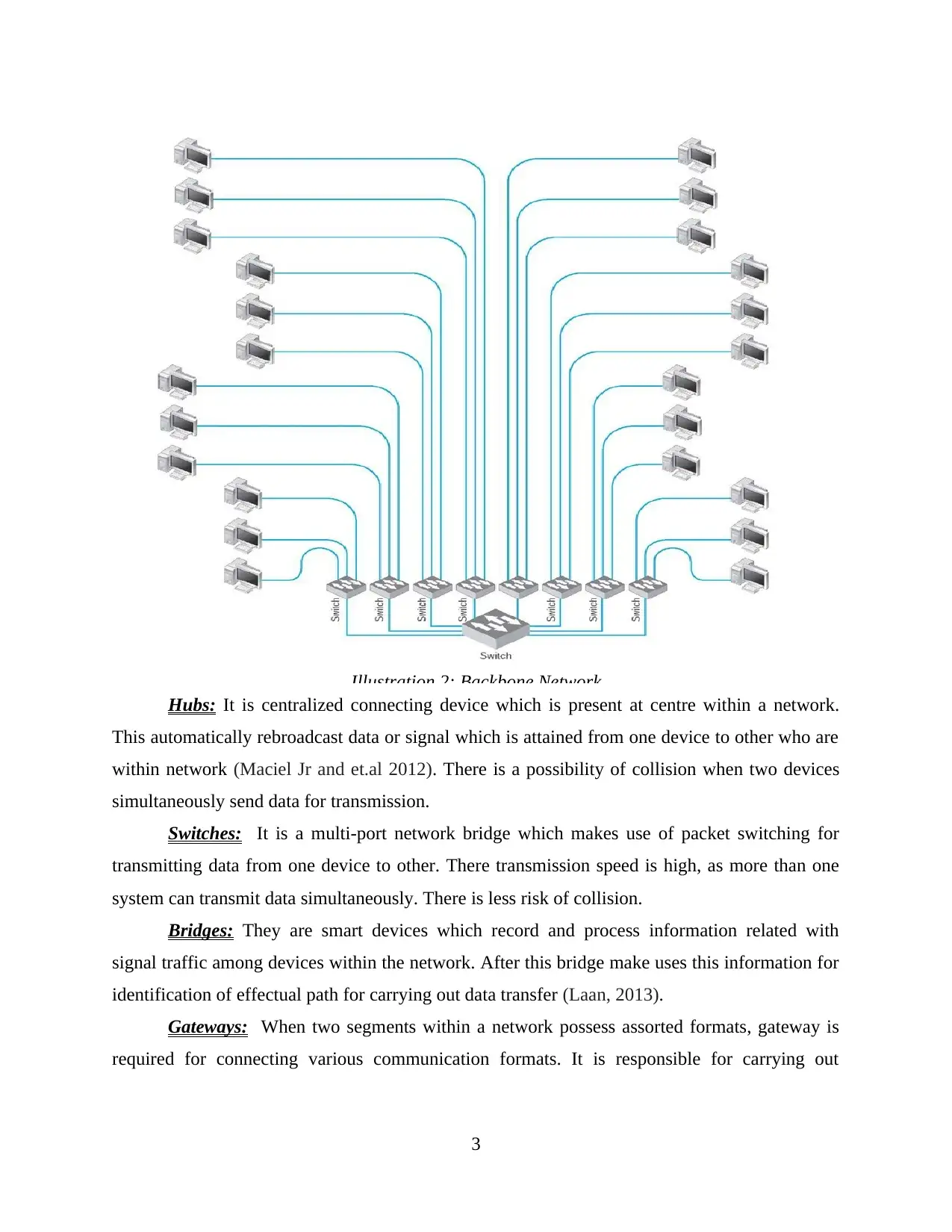
Hubs: It is centralized connecting device which is present at centre within a network.
This automatically rebroadcast data or signal which is attained from one device to other who are
within network (Maciel Jr and et.al 2012). There is a possibility of collision when two devices
simultaneously send data for transmission.
Switches: It is a multi-port network bridge which makes use of packet switching for
transmitting data from one device to other. There transmission speed is high, as more than one
system can transmit data simultaneously. There is less risk of collision.
Bridges: They are smart devices which record and process information related with
signal traffic among devices within the network. After this bridge make uses this information for
identification of effectual path for carrying out data transfer (Laan, 2013).
Gateways: When two segments within a network possess assorted formats, gateway is
required for connecting various communication formats. It is responsible for carrying out
3
Illustration 2: Backbone Network
This automatically rebroadcast data or signal which is attained from one device to other who are
within network (Maciel Jr and et.al 2012). There is a possibility of collision when two devices
simultaneously send data for transmission.
Switches: It is a multi-port network bridge which makes use of packet switching for
transmitting data from one device to other. There transmission speed is high, as more than one
system can transmit data simultaneously. There is less risk of collision.
Bridges: They are smart devices which record and process information related with
signal traffic among devices within the network. After this bridge make uses this information for
identification of effectual path for carrying out data transfer (Laan, 2013).
Gateways: When two segments within a network possess assorted formats, gateway is
required for connecting various communication formats. It is responsible for carrying out
3
Illustration 2: Backbone Network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

conversion so that computer within Ethernet network which makes use of TCP/IP protocol can
interact with PLC by making use controlnet protocol even if they do not support each other.
Network segment: It is a span or single run of physical connectivity among network interface of
two computer devices (Masa’deh, 2013). This connectivity can be either of fiber-optic cable or
copper or wi-fi link. This network is build by connecting different network segments by making
use of router, switch or bridge.
2. Development of logic design based on three-layer hierarchical model. Give details of required
network devices and servers
Cisco hierarchical three layer is a inter networking model which is used by industry for
purpose of designing as it is cost-efficient, scalable and reliable. It comprises of different layers
and each consists of one or more devices which work across different layers. Cisco hierarchical
model provides enhanced benefits, they are:
By this high performance networks can be created in which some layers are sensitised to
congestion.
It allows management to organise the network as well as isolate trouble network so that
any problem do not arise in working of CBA.
Policies can be created easily including certain rules and filters which will lead to grow
network by dividing it into functional areas (Padhy and Patra, 2012).
Three-layer hierarchical model with respect to CBA is shown below:
Core (Backbone layer): When large number of customers enters into the website of the bank
than traffic will increase due to which it can become unresponsive, it can also occur due to
network problems. It is responsible for switching traffic with high speed. CBA can use it as it
will eliminate redundancy as well as reliability. This will provide employees of bank with high
efficiency. In this speed is high when sharing data even within multiple network connections.
As CBA is using LAN in geographical scope so they can opt for Cisco switches: Cisco Catalyst
6000, 5000, 4000.
Distribution Layer: In this focal point is on wiring closets, in this either multilayer switch or
router can be used for segmentation as well as isolation of network problem within building of
CBA. Focus of bank in this layer is on packet filtering and their transmission, router will check
the priority of packets and then they will be transmitted (Rivera-Ruiz and Ferrer-Moreno, 2015).
CBA can make use of Cisco Catalyst switches of series 6500, 4000, 3000
4
interact with PLC by making use controlnet protocol even if they do not support each other.
Network segment: It is a span or single run of physical connectivity among network interface of
two computer devices (Masa’deh, 2013). This connectivity can be either of fiber-optic cable or
copper or wi-fi link. This network is build by connecting different network segments by making
use of router, switch or bridge.
2. Development of logic design based on three-layer hierarchical model. Give details of required
network devices and servers
Cisco hierarchical three layer is a inter networking model which is used by industry for
purpose of designing as it is cost-efficient, scalable and reliable. It comprises of different layers
and each consists of one or more devices which work across different layers. Cisco hierarchical
model provides enhanced benefits, they are:
By this high performance networks can be created in which some layers are sensitised to
congestion.
It allows management to organise the network as well as isolate trouble network so that
any problem do not arise in working of CBA.
Policies can be created easily including certain rules and filters which will lead to grow
network by dividing it into functional areas (Padhy and Patra, 2012).
Three-layer hierarchical model with respect to CBA is shown below:
Core (Backbone layer): When large number of customers enters into the website of the bank
than traffic will increase due to which it can become unresponsive, it can also occur due to
network problems. It is responsible for switching traffic with high speed. CBA can use it as it
will eliminate redundancy as well as reliability. This will provide employees of bank with high
efficiency. In this speed is high when sharing data even within multiple network connections.
As CBA is using LAN in geographical scope so they can opt for Cisco switches: Cisco Catalyst
6000, 5000, 4000.
Distribution Layer: In this focal point is on wiring closets, in this either multilayer switch or
router can be used for segmentation as well as isolation of network problem within building of
CBA. Focus of bank in this layer is on packet filtering and their transmission, router will check
the priority of packets and then they will be transmitted (Rivera-Ruiz and Ferrer-Moreno, 2015).
CBA can make use of Cisco Catalyst switches of series 6500, 4000, 3000
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Access Layer: It grants access to end devices within the network. Within WAN network it will
provide access to corporate network or remote sites. Making use of this for communication with
other organisation CBA can make use of this layer for high availability, virtual access control
lists, spanning tree and address resolution protocol inspection (ARP) (Roberts and Grover,
2012).
3. Identification of type of IP addresses along with their subnet mask.
IP address is defined as a number which uniquely identifies system within a network. It is
either 32 bit or 128 bit number which determines the device which is present within TCP/IP
network. It is a binary number which is written in form of four decimal numbers. Consider an
example to understand this, it is seen as 192.168.123.1- a decimal number and in binary form it
is written as 11000000010100011110111000000001. Here 198 are written in 8 bits and similarly
168 and others it is called octet. IP addresses are classified into five categories but basically three
classes are being used. They are explained below:
Class A: Its range lies in between 1.0.0.0 to 126.0.0.0 and has maximum 224 nodes. In this last 0
is replaced by address of nodes.
Class B: Their range is 128.0.0.0 to 191.0.0.0 and consists of 65000 nodes. In this case last two
zeros are altered by address of node.
Class C: Its range is from 192.0.0.0 to 223.0.0.0 and has utmost 254 nodes. In this range last 3
zeros are changed by address of host.
Each class has their purpose like some are used for unicast, multicast, research and development
and some IP’s are reserved for future purpose. Last node of every class signifies address of
broadcasting. Like if IP of host of CBA is 192.168.1.1 then its broadcast address is
192.168.1.255 as it has maximum 255 nodes and this is address used for transmission within
network. IP subnetting is defined as a process in which IP of network is classified into smaller
networks (Vacca, 2013). CBA can use Cisco 3500 series (basically repeaters and hubs). When
there are large numbers of hosts within a network than subneting will provide technical team
with an option where they can convert them into small networks. In case if all host addresses are
not used then remaining will be wasted. Small networks will ensure that the entire networks are
used.
An example is taken into consideration by which subnetting can be understood. Technical
department of CBA will be responsible for creation of difference in between host and network IP
5
provide access to corporate network or remote sites. Making use of this for communication with
other organisation CBA can make use of this layer for high availability, virtual access control
lists, spanning tree and address resolution protocol inspection (ARP) (Roberts and Grover,
2012).
3. Identification of type of IP addresses along with their subnet mask.
IP address is defined as a number which uniquely identifies system within a network. It is
either 32 bit or 128 bit number which determines the device which is present within TCP/IP
network. It is a binary number which is written in form of four decimal numbers. Consider an
example to understand this, it is seen as 192.168.123.1- a decimal number and in binary form it
is written as 11000000010100011110111000000001. Here 198 are written in 8 bits and similarly
168 and others it is called octet. IP addresses are classified into five categories but basically three
classes are being used. They are explained below:
Class A: Its range lies in between 1.0.0.0 to 126.0.0.0 and has maximum 224 nodes. In this last 0
is replaced by address of nodes.
Class B: Their range is 128.0.0.0 to 191.0.0.0 and consists of 65000 nodes. In this case last two
zeros are altered by address of node.
Class C: Its range is from 192.0.0.0 to 223.0.0.0 and has utmost 254 nodes. In this range last 3
zeros are changed by address of host.
Each class has their purpose like some are used for unicast, multicast, research and development
and some IP’s are reserved for future purpose. Last node of every class signifies address of
broadcasting. Like if IP of host of CBA is 192.168.1.1 then its broadcast address is
192.168.1.255 as it has maximum 255 nodes and this is address used for transmission within
network. IP subnetting is defined as a process in which IP of network is classified into smaller
networks (Vacca, 2013). CBA can use Cisco 3500 series (basically repeaters and hubs). When
there are large numbers of hosts within a network than subneting will provide technical team
with an option where they can convert them into small networks. In case if all host addresses are
not used then remaining will be wasted. Small networks will ensure that the entire networks are
used.
An example is taken into consideration by which subnetting can be understood. Technical
department of CBA will be responsible for creation of difference in between host and network IP
5

address. Both are responsible for giving identity to system and are used concurrently. Each bit is
assigned to an IP address which ensures that bits are not wasted. Consider a range.
IP address: 10.150.32.127
Subnet mask: 255.0.0.0
IP address: 172.168.100.32
Subnet mask: 255.255.0.0
Subnet mask depends upon IP address of a class like in case of 10.150.32.127 is class A address
so last bits signifies broadcast address. But basically Class C address will be used by CBA bank.
Task II
1. Propose two organisations which provide cloud services for hosting email and web servers.
Cloud computing is defined as computer resources which data storage and embrace
computing power and are not handled by user vigorously (Wang, Jie and Chen, 2018). It delivers
hosted services via internet and they are classified into SAAS (software as a service), PAAS
(platform as a service) and IAAS (infrastructure as a service). Here two organisations which are
considered, they are Amazon and Microsoft. They provide services to different organisations and
are basically known as Amazon web services and Microsoft Azure. In context of CBA, they are
illustrated below:
Amazon web services (AWS): It is inclusive and growing cloud computing platform
which is provided by Amazon. Organisations have option to pay as you go cloud computing
model which renders users with compute and storage. AWS possess 140 features they include
storage, networking, management tool, IoT, compute, analytics, database, developer tools,
security and enterprise applications. CBA can opt for these services at the moment it is required.
Switching cost will be saved whenever they need some other services by paying for the same.
Amazon EC2 renders and administers description servers such as applications, storage, security,
etc. It can be used by CBA as they need to carry lots of transactions as they operate their services
in financial and banking, for this high security is required (Ajamieh and et. al, 2016).
Microsoft Azure: It refers to data centre which can be used for deploying, managing,
building and rendering services through global network. They render various services which are
mentioned below:
6
assigned to an IP address which ensures that bits are not wasted. Consider a range.
IP address: 10.150.32.127
Subnet mask: 255.0.0.0
IP address: 172.168.100.32
Subnet mask: 255.255.0.0
Subnet mask depends upon IP address of a class like in case of 10.150.32.127 is class A address
so last bits signifies broadcast address. But basically Class C address will be used by CBA bank.
Task II
1. Propose two organisations which provide cloud services for hosting email and web servers.
Cloud computing is defined as computer resources which data storage and embrace
computing power and are not handled by user vigorously (Wang, Jie and Chen, 2018). It delivers
hosted services via internet and they are classified into SAAS (software as a service), PAAS
(platform as a service) and IAAS (infrastructure as a service). Here two organisations which are
considered, they are Amazon and Microsoft. They provide services to different organisations and
are basically known as Amazon web services and Microsoft Azure. In context of CBA, they are
illustrated below:
Amazon web services (AWS): It is inclusive and growing cloud computing platform
which is provided by Amazon. Organisations have option to pay as you go cloud computing
model which renders users with compute and storage. AWS possess 140 features they include
storage, networking, management tool, IoT, compute, analytics, database, developer tools,
security and enterprise applications. CBA can opt for these services at the moment it is required.
Switching cost will be saved whenever they need some other services by paying for the same.
Amazon EC2 renders and administers description servers such as applications, storage, security,
etc. It can be used by CBA as they need to carry lots of transactions as they operate their services
in financial and banking, for this high security is required (Ajamieh and et. al, 2016).
Microsoft Azure: It refers to data centre which can be used for deploying, managing,
building and rendering services through global network. They render various services which are
mentioned below:
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PAAS (Platform as a service): A platform is rendered to clients where they can deploy
and develop software. By making use of PAAS services CBA can make use of infrastructure and
servers as here they do not need to make extra efforts for their maintenance. Microsoft Azure
maintains issues associated with network, servers at low cost (Gardner, Boyer and Gray, 2015).
These resources will be made available to CBA when they demand for them and pay for it.
IAAS (Infrastructure as a service): By opting for this, CBA can manage and monitor data
centres when they need it. For this they can also opt for virtual machines by which they will be
able to adapt to different requirements. They can shift their database to Azure without any extra
efforts and also make use of web and email server.
2. Outline techniques for usage of service virtualisation and implementation of cloud platforms.
Service virtualisation is defined as a method which imitates functionality of specific
component or behaviour depending upon applications such as service oriented, cloud base and
API driven applications. It can be adopted by CBA to identify updates or new standards
according to standard required. Some techniques of cloud platforms by making use of service
virtualisation are mentioned below:
Network virtualisation: It is defined as process of mixture of hardware and software
network resources by which functionality of network is combined into single unique virtual
network. It includes platform virtualisation which is integrated with virtualisation of resources.
CBA can adopt this technique for managing intricacy of network by separating it into diverse
parts which can be managed easily (Knyazkov and et. al, 2012).
Server virtualisation: It is defined as a process for covering server resources which
consists of processors, physical servers and operating system from different server users.
Software applications are used by administrator of server by dividing physical server into
different isolated virtual machines. CBA can make use of these private servers which are also
called guests by this they can effectually maintain critical servers easily.
Storage virtualisation: It is defined as physical storage from different storage devices into
a device which looks like a single unit. Normally it comprises of devices which are centrally
managed. CBA can make use of this as in this mandatory or confidential details are abstracted
from everyone who is within the network and it is must for them (Laan, 2013).
7
and develop software. By making use of PAAS services CBA can make use of infrastructure and
servers as here they do not need to make extra efforts for their maintenance. Microsoft Azure
maintains issues associated with network, servers at low cost (Gardner, Boyer and Gray, 2015).
These resources will be made available to CBA when they demand for them and pay for it.
IAAS (Infrastructure as a service): By opting for this, CBA can manage and monitor data
centres when they need it. For this they can also opt for virtual machines by which they will be
able to adapt to different requirements. They can shift their database to Azure without any extra
efforts and also make use of web and email server.
2. Outline techniques for usage of service virtualisation and implementation of cloud platforms.
Service virtualisation is defined as a method which imitates functionality of specific
component or behaviour depending upon applications such as service oriented, cloud base and
API driven applications. It can be adopted by CBA to identify updates or new standards
according to standard required. Some techniques of cloud platforms by making use of service
virtualisation are mentioned below:
Network virtualisation: It is defined as process of mixture of hardware and software
network resources by which functionality of network is combined into single unique virtual
network. It includes platform virtualisation which is integrated with virtualisation of resources.
CBA can adopt this technique for managing intricacy of network by separating it into diverse
parts which can be managed easily (Knyazkov and et. al, 2012).
Server virtualisation: It is defined as a process for covering server resources which
consists of processors, physical servers and operating system from different server users.
Software applications are used by administrator of server by dividing physical server into
different isolated virtual machines. CBA can make use of these private servers which are also
called guests by this they can effectually maintain critical servers easily.
Storage virtualisation: It is defined as physical storage from different storage devices into
a device which looks like a single unit. Normally it comprises of devices which are centrally
managed. CBA can make use of this as in this mandatory or confidential details are abstracted
from everyone who is within the network and it is must for them (Laan, 2013).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. How cloud computing support dynamic scaling of CBA applications.
Scalability can be defined as process which manages growing and diminishing needs of
resources for organisation (Larsen, Patterson and El-Geneidy, 2013). By making use of cloud
computing CBA can enhance their elasticity which means that as per requirements they can add
more number of resources within the network. By opting for this CBA can minimise cost of
ownership of different applications which are used by them. When cost of any software or
hardware is very high than cloud computing is the best option which can be used by CBA bank
for accomplishing any specific project. Dynamic allocation of resources makes it easy to use
them as per demands of customers or organisations keeps on fluctuating by advancement in
technology. Automated scaling listener has been configured by cloud to meet these needs.
Figure 1 Cloud Computing
By this when any kinds of resources are required by CBA then this listener will provide them
access to those services. Cloud has given logic behind determination of ways in which
dynamically resources can be allocated to CBA by service provider. These scaling ranges as:
Dynamic Relocation: When automated scaling listener receives a request than resources
will be relocated by cloud like CBA needs to shift to storage device of 128 bits from 32 GB per
second input output capacity devices (Maciel Jr and et.al 2012).
Dynamic horizontal scaling: Suppose there is variation in workload or usage of website
than resources can be scaled to handle this situation. The automated scaling listener monitor
8
Scalability can be defined as process which manages growing and diminishing needs of
resources for organisation (Larsen, Patterson and El-Geneidy, 2013). By making use of cloud
computing CBA can enhance their elasticity which means that as per requirements they can add
more number of resources within the network. By opting for this CBA can minimise cost of
ownership of different applications which are used by them. When cost of any software or
hardware is very high than cloud computing is the best option which can be used by CBA bank
for accomplishing any specific project. Dynamic allocation of resources makes it easy to use
them as per demands of customers or organisations keeps on fluctuating by advancement in
technology. Automated scaling listener has been configured by cloud to meet these needs.
Figure 1 Cloud Computing
By this when any kinds of resources are required by CBA then this listener will provide them
access to those services. Cloud has given logic behind determination of ways in which
dynamically resources can be allocated to CBA by service provider. These scaling ranges as:
Dynamic Relocation: When automated scaling listener receives a request than resources
will be relocated by cloud like CBA needs to shift to storage device of 128 bits from 32 GB per
second input output capacity devices (Maciel Jr and et.al 2012).
Dynamic horizontal scaling: Suppose there is variation in workload or usage of website
than resources can be scaled to handle this situation. The automated scaling listener monitor
8

request which is made by CBA to acquire more resources and their duplication so that it can be
handled by cloud.
Dynamic vertical scaling: Instances of IT resources are scaled up and down where there
is need to revise capability of every resource. Like CBA bank, if storage space of virtual server is
filled than either they can opt for adding processing core or increasing their memory dynamically
(Masa’deh, 2013).
CONCLUSION
From above it can be concluded that, IT infrastructure is very useful for an organisation
and if network or resources or not managed appropriately than it would be difficult for them to
carry out their operations. LAN is used when connectivity is required in small area it can be
connected by making use of network devices such as hub, switches or routers. Three-layer
architecture is used for effective communication. Furthermore, IP address provides unique
identity to systems within the network. Microsoft and Amazon provide cloud services depending
upon requirements of organisation. Virtualisation is act of imitating resources which do not exist
physically.
9
handled by cloud.
Dynamic vertical scaling: Instances of IT resources are scaled up and down where there
is need to revise capability of every resource. Like CBA bank, if storage space of virtual server is
filled than either they can opt for adding processing core or increasing their memory dynamically
(Masa’deh, 2013).
CONCLUSION
From above it can be concluded that, IT infrastructure is very useful for an organisation
and if network or resources or not managed appropriately than it would be difficult for them to
carry out their operations. LAN is used when connectivity is required in small area it can be
connected by making use of network devices such as hub, switches or routers. Three-layer
architecture is used for effective communication. Furthermore, IP address provides unique
identity to systems within the network. Microsoft and Amazon provide cloud services depending
upon requirements of organisation. Virtualisation is act of imitating resources which do not exist
physically.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





