Spring 2018/2019: IT Infrastructure & Enterprise Architecture Report
VerifiedAdded on 2023/01/18
|9
|1828
|21
Report
AI Summary
This report provides a detailed analysis of IT infrastructure and enterprise architecture, focusing on the design of a corporate network for a global company with branches in Paris, Tokyo, New York, and headquarters in Los Angeles. The report recommends a hybrid network architecture, leveraging VPNs, active directory, and centralized security measures to connect the four offices efficiently. It explores the use of backbone networks, VLANs, and routers to ensure high availability and efficient data transfer. The report emphasizes the importance of security, proposing organizational units within active directory to control user access and implementing policies to protect sensitive data. The architectural framework includes Multiprotocol Label Switching services, gigabit connections, and a remote site for backup and disaster recovery, ensuring scalability, robustness, and efficient management of the network. The solution also discusses the implementation of Citrix with Microsoft's active directory service to ensure all the users and computers of the company are controlled and under one administrator. The report concludes that the hybrid IT infrastructure is the most suitable solution for the company to ensure that all branches are controlled and robust in terms of performance.

Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 1
IT Infrastructure & Enterprise Architecture
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
IT Infrastructure & Enterprise Architecture
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 2
Introduction
Enterprise architecture is important for an organization to establish their IT infrastructure
as it provides the blueprint from which application and systems get deployed on an enterprise
scale. Choosing the best architecture that suits a particular business model is the sole
responsibility of the IT architect. It involves rationalizing what type of enterprise application the
business shall utilize, whether the application shall be centralized or decentralized, the
geographical location covered by the enterprise, the number of the employee who occupies a
different niche within the enterprise [1]. The aim of having this architectural overviews of the
enterprise IT environment is to reduce the complexity of the system by only focusing on the
abstract and high-level view which is key for improvement and decision making. In this report,
we have given a methodological approach that IT architects undergo to arrive at the best
enterprise architecture that is suitable for a given scenario. Different architectures are based on
different frameworks which are just guides to building an optimized architecture that meets
business needs, the key among the includes, centralized, decentralized, distributed and hybrid
[2]
related things from the chapters
Several concepts can be drawn from the chapters already covered to make the best
decision in setting up the architecture. Firs, the concept of the backbone network is key in setting
up enterprise architecture as it simplify how data will be travel from the enterprise within the
various department and remote global branches. The backbone network setup ensures high
availability of bandwidth between different enterprise applications. Second, the concept of VPN
is highly referenced in the report as it explains how the enterprise architecture will handle remote
Introduction
Enterprise architecture is important for an organization to establish their IT infrastructure
as it provides the blueprint from which application and systems get deployed on an enterprise
scale. Choosing the best architecture that suits a particular business model is the sole
responsibility of the IT architect. It involves rationalizing what type of enterprise application the
business shall utilize, whether the application shall be centralized or decentralized, the
geographical location covered by the enterprise, the number of the employee who occupies a
different niche within the enterprise [1]. The aim of having this architectural overviews of the
enterprise IT environment is to reduce the complexity of the system by only focusing on the
abstract and high-level view which is key for improvement and decision making. In this report,
we have given a methodological approach that IT architects undergo to arrive at the best
enterprise architecture that is suitable for a given scenario. Different architectures are based on
different frameworks which are just guides to building an optimized architecture that meets
business needs, the key among the includes, centralized, decentralized, distributed and hybrid
[2]
related things from the chapters
Several concepts can be drawn from the chapters already covered to make the best
decision in setting up the architecture. Firs, the concept of the backbone network is key in setting
up enterprise architecture as it simplify how data will be travel from the enterprise within the
various department and remote global branches. The backbone network setup ensures high
availability of bandwidth between different enterprise applications. Second, the concept of VPN
is highly referenced in the report as it explains how the enterprise architecture will handle remote
Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 3
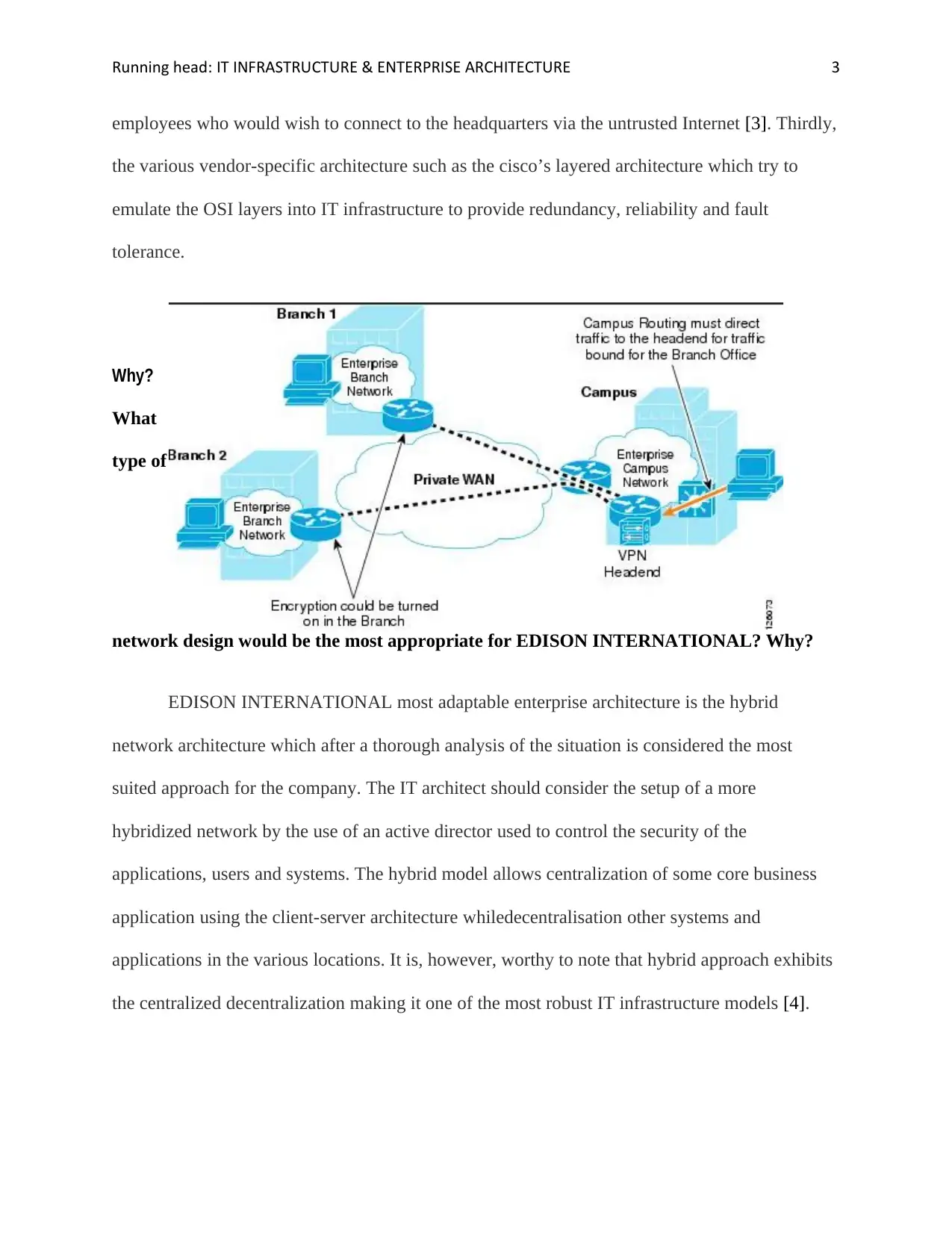
employees who would wish to connect to the headquarters via the untrusted Internet [3]. Thirdly,
the various vendor-specific architecture such as the cisco’s layered architecture which try to
emulate the OSI layers into IT infrastructure to provide redundancy, reliability and fault
tolerance.
Why?
What
type of
network design would be the most appropriate for EDISON INTERNATIONAL? Why?
EDISON INTERNATIONAL most adaptable enterprise architecture is the hybrid
network architecture which after a thorough analysis of the situation is considered the most
suited approach for the company. The IT architect should consider the setup of a more
hybridized network by the use of an active director used to control the security of the
applications, users and systems. The hybrid model allows centralization of some core business
application using the client-server architecture whiledecentralisation other systems and
applications in the various locations. It is, however, worthy to note that hybrid approach exhibits
the centralized decentralization making it one of the most robust IT infrastructure models [4].
employees who would wish to connect to the headquarters via the untrusted Internet [3]. Thirdly,
the various vendor-specific architecture such as the cisco’s layered architecture which try to
emulate the OSI layers into IT infrastructure to provide redundancy, reliability and fault
tolerance.
Why?
What
type of
network design would be the most appropriate for EDISON INTERNATIONAL? Why?
EDISON INTERNATIONAL most adaptable enterprise architecture is the hybrid
network architecture which after a thorough analysis of the situation is considered the most
suited approach for the company. The IT architect should consider the setup of a more
hybridized network by the use of an active director used to control the security of the
applications, users and systems. The hybrid model allows centralization of some core business
application using the client-server architecture whiledecentralisation other systems and
applications in the various locations. It is, however, worthy to note that hybrid approach exhibits
the centralized decentralization making it one of the most robust IT infrastructure models [4].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 4
Most notable methodology to implement this architecture is the implementation of Citrix
with Microsoft’s active directory service to ensure all the users and computers of the company
are controlled and under one administrator [5].
The main reason why this architecture is most important for the company scenario is that,
it will enable all the employees of EDISON INTERNATIONAL to have access to all the
computing resources of the company and services despite their geographical boundaries. No
restriction will exist since all the employees shall be able to access the resources even if not on
their own workstation. All the security measures shall be centralized and to provide a more
robust way of managing security
With this architecture, the various employees working for EDISON INTERNATIONAL
will be able to access the company’s applications and services from the various geographical
Most notable methodology to implement this architecture is the implementation of Citrix
with Microsoft’s active directory service to ensure all the users and computers of the company
are controlled and under one administrator [5].
The main reason why this architecture is most important for the company scenario is that,
it will enable all the employees of EDISON INTERNATIONAL to have access to all the
computing resources of the company and services despite their geographical boundaries. No
restriction will exist since all the employees shall be able to access the resources even if not on
their own workstation. All the security measures shall be centralized and to provide a more
robust way of managing security
With this architecture, the various employees working for EDISON INTERNATIONAL
will be able to access the company’s applications and services from the various geographical
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 5
locations removing the need to be using their own system setups to access the company’s
enterprise applications [6]
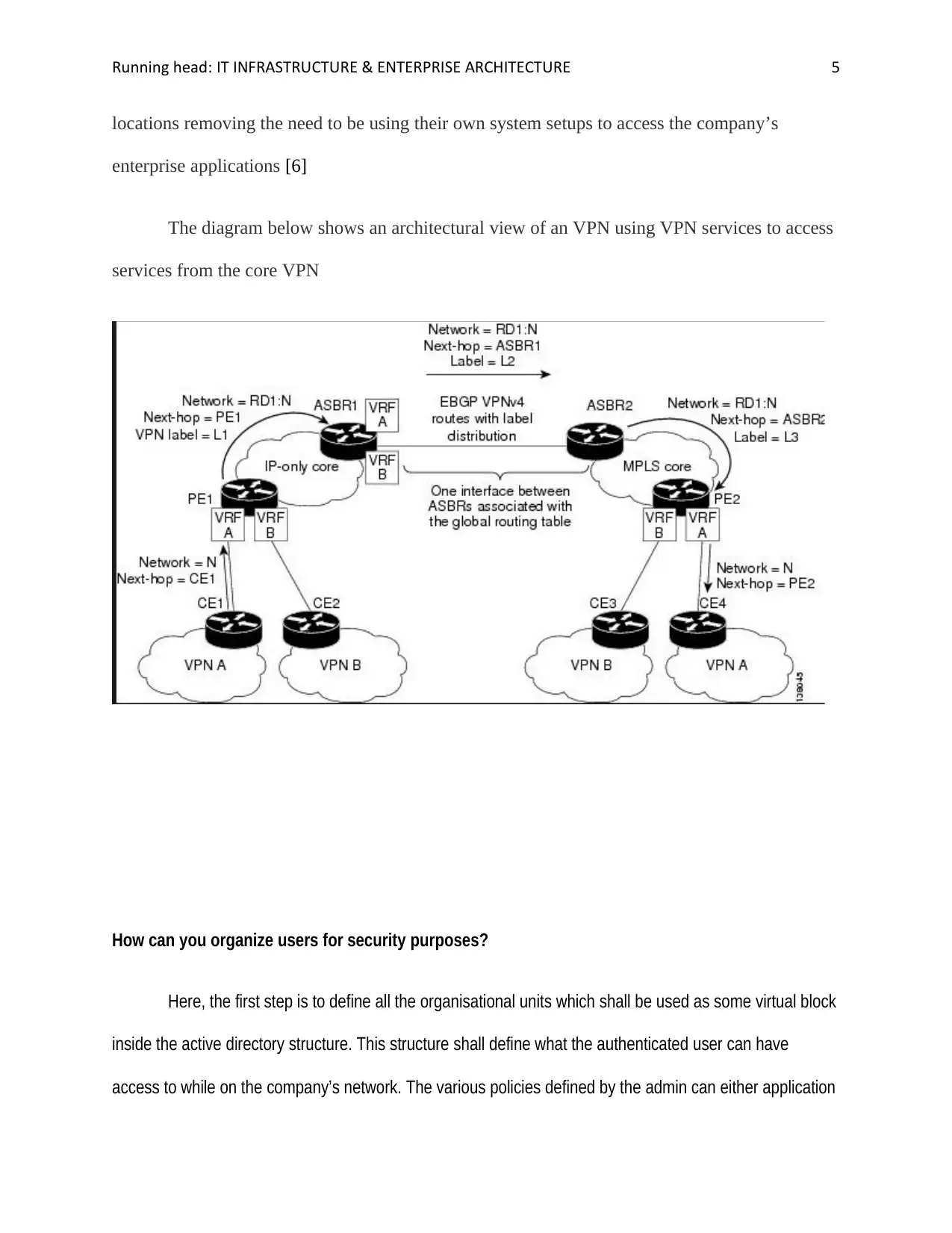
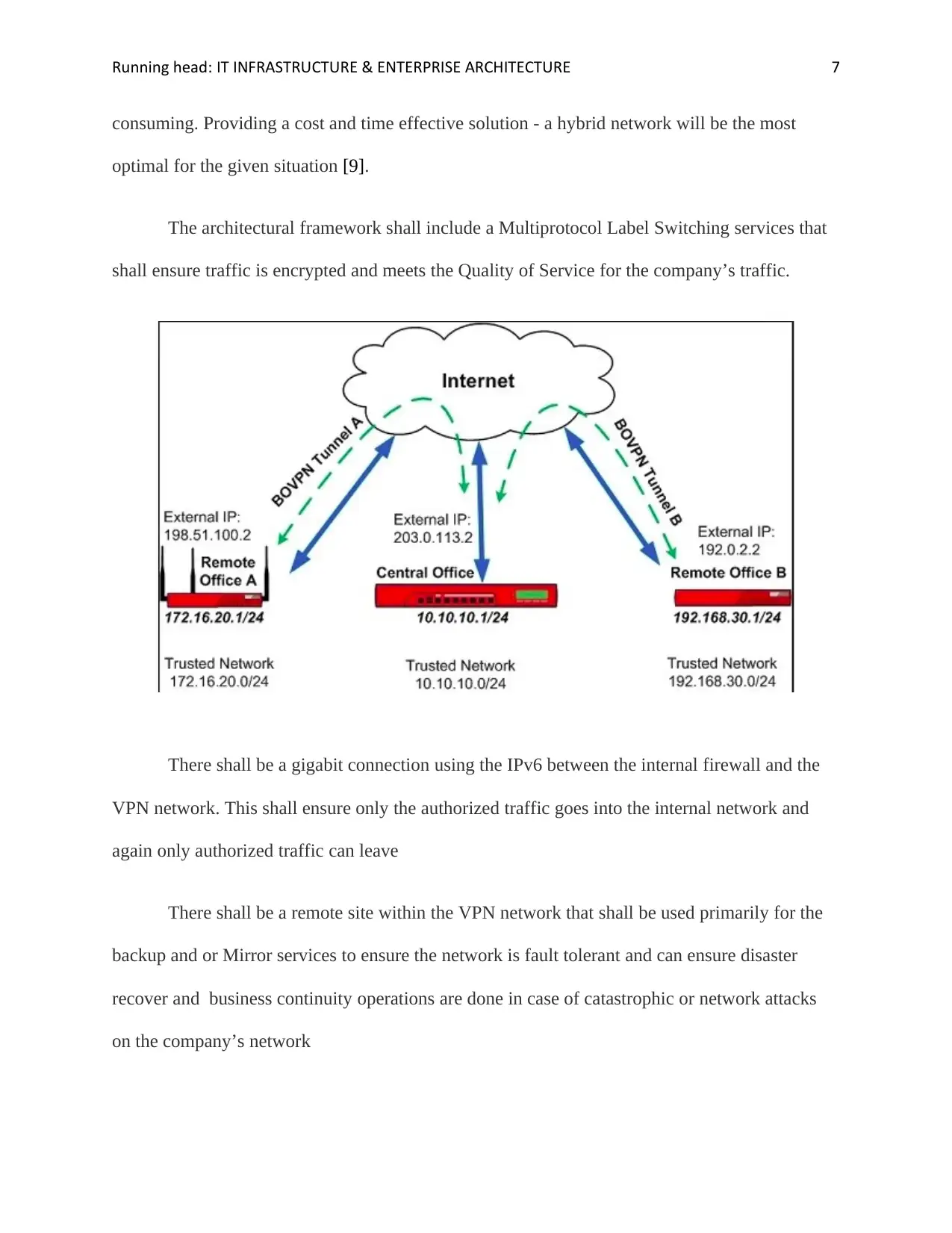
The diagram below shows an architectural view of an VPN using VPN services to access
services from the core VPN
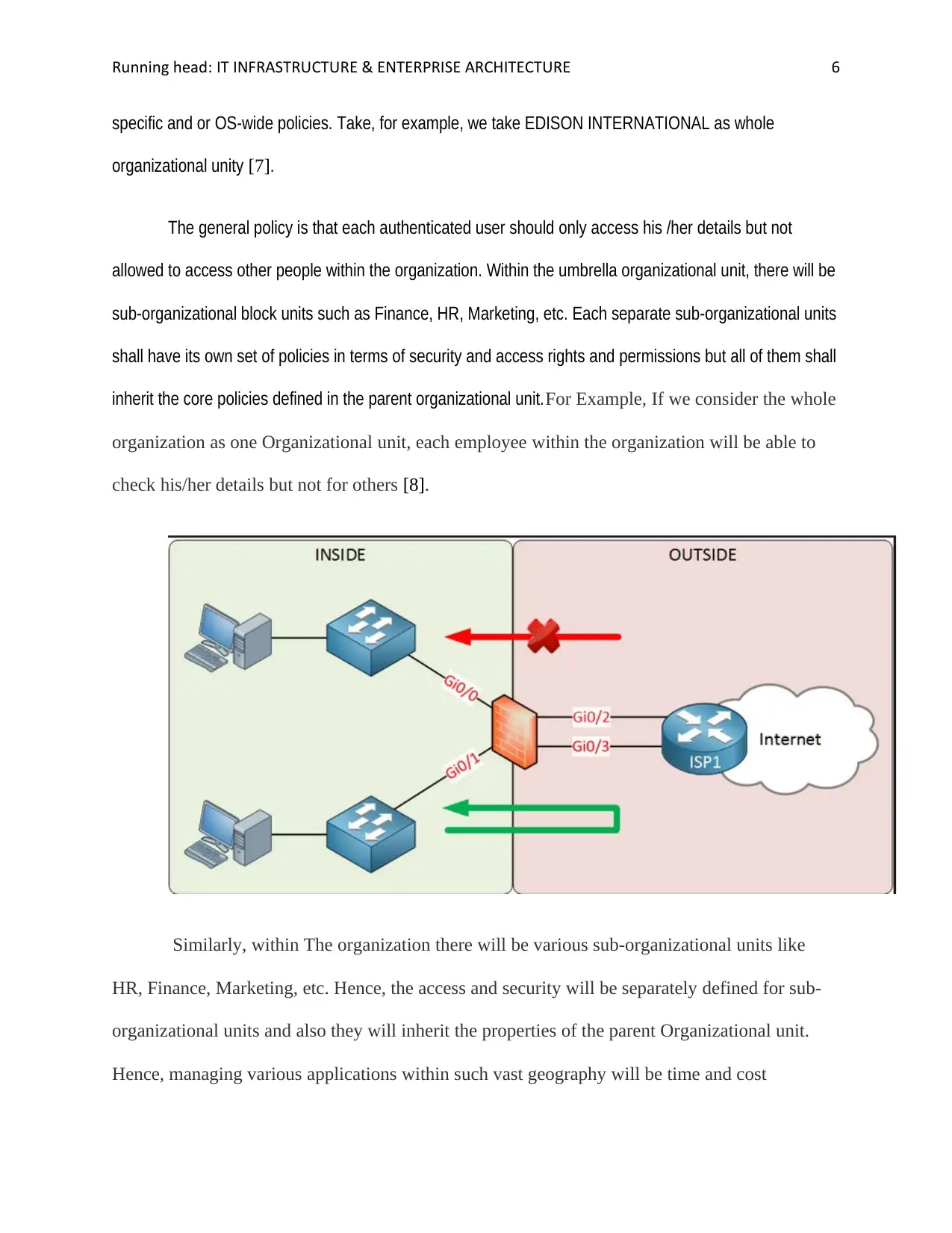
How can you organize users for security purposes?
Here, the first step is to define all the organisational units which shall be used as some virtual block
inside the active directory structure. This structure shall define what the authenticated user can have
access to while on the company’s network. The various policies defined by the admin can either application
locations removing the need to be using their own system setups to access the company’s
enterprise applications [6]
The diagram below shows an architectural view of an VPN using VPN services to access
services from the core VPN
How can you organize users for security purposes?
Here, the first step is to define all the organisational units which shall be used as some virtual block
inside the active directory structure. This structure shall define what the authenticated user can have
access to while on the company’s network. The various policies defined by the admin can either application
Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 6
specific and or OS-wide policies. Take, for example, we take EDISON INTERNATIONAL as whole
organizational unity [7].
The general policy is that each authenticated user should only access his /her details but not
allowed to access other people within the organization. Within the umbrella organizational unit, there will be
sub-organizational block units such as Finance, HR, Marketing, etc. Each separate sub-organizational units
shall have its own set of policies in terms of security and access rights and permissions but all of them shall
inherit the core policies defined in the parent organizational unit.For Example, If we consider the whole
organization as one Organizational unit, each employee within the organization will be able to
check his/her details but not for others [8].
Similarly, within The organization there will be various sub-organizational units like
HR, Finance, Marketing, etc. Hence, the access and security will be separately defined for sub-
organizational units and also they will inherit the properties of the parent Organizational unit.
Hence, managing various applications within such vast geography will be time and cost
specific and or OS-wide policies. Take, for example, we take EDISON INTERNATIONAL as whole
organizational unity [7].
The general policy is that each authenticated user should only access his /her details but not
allowed to access other people within the organization. Within the umbrella organizational unit, there will be
sub-organizational block units such as Finance, HR, Marketing, etc. Each separate sub-organizational units
shall have its own set of policies in terms of security and access rights and permissions but all of them shall
inherit the core policies defined in the parent organizational unit.For Example, If we consider the whole
organization as one Organizational unit, each employee within the organization will be able to
check his/her details but not for others [8].
Similarly, within The organization there will be various sub-organizational units like
HR, Finance, Marketing, etc. Hence, the access and security will be separately defined for sub-
organizational units and also they will inherit the properties of the parent Organizational unit.
Hence, managing various applications within such vast geography will be time and cost
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 7
consuming. Providing a cost and time effective solution - a hybrid network will be the most
optimal for the given situation [9].
The architectural framework shall include a Multiprotocol Label Switching services that
shall ensure traffic is encrypted and meets the Quality of Service for the company’s traffic.
There shall be a gigabit connection using the IPv6 between the internal firewall and the
VPN network. This shall ensure only the authorized traffic goes into the internal network and
again only authorized traffic can leave
There shall be a remote site within the VPN network that shall be used primarily for the
backup and or Mirror services to ensure the network is fault tolerant and can ensure disaster
recover and business continuity operations are done in case of catastrophic or network attacks
on the company’s network
consuming. Providing a cost and time effective solution - a hybrid network will be the most
optimal for the given situation [9].
The architectural framework shall include a Multiprotocol Label Switching services that
shall ensure traffic is encrypted and meets the Quality of Service for the company’s traffic.
There shall be a gigabit connection using the IPv6 between the internal firewall and the
VPN network. This shall ensure only the authorized traffic goes into the internal network and
again only authorized traffic can leave
There shall be a remote site within the VPN network that shall be used primarily for the
backup and or Mirror services to ensure the network is fault tolerant and can ensure disaster
recover and business continuity operations are done in case of catastrophic or network attacks
on the company’s network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 8
Policies shall be written to ensure the company’s critical data and or SharePoint are only
accessed as used as per the business needs. Once the policies are written for the parent
organization, each of the security zones shall inherit the policies and add their own sub-
organizational security policies that is best suited for the sub-organization. This will create an
architecture that is scalable, robust and efficient to maintain. The VPN core will handle all the
multiple layer switching capabilities for other sub-organizational routers hence will be situated
close to theheadquarters in OSPF area 0 [10]
Conclusion
In enterprise architectures needs careful design choices made o ensure the enterprise
application runs without glitches. This report has analyzed the scenario above and gave the
recommended the company to implement hybrid IT infrastructure enterprise architecture to
ensure that all the branches are not only controlled but also robust and efficient in terms of their
performance. The report has made architectural design layout of the various network
infrastructure devises to ensure proper redundancy and fault tolerance within the network.
Policies shall be written to ensure the company’s critical data and or SharePoint are only
accessed as used as per the business needs. Once the policies are written for the parent
organization, each of the security zones shall inherit the policies and add their own sub-
organizational security policies that is best suited for the sub-organization. This will create an
architecture that is scalable, robust and efficient to maintain. The VPN core will handle all the
multiple layer switching capabilities for other sub-organizational routers hence will be situated
close to theheadquarters in OSPF area 0 [10]
Conclusion
In enterprise architectures needs careful design choices made o ensure the enterprise
application runs without glitches. This report has analyzed the scenario above and gave the
recommended the company to implement hybrid IT infrastructure enterprise architecture to
ensure that all the branches are not only controlled but also robust and efficient in terms of their
performance. The report has made architectural design layout of the various network
infrastructure devises to ensure proper redundancy and fault tolerance within the network.

Running head: IT INFRASTRUCTURE & ENTERPRISE ARCHITECTURE 9
References
[1] Evgeny A. Basinya, “Distributed system of collecting, processing and analysis of security
information events of the enterprise network infrastructure,” Bezopasnostʹ Informacionnyh
Tehnologij, no. 4, p. 43, 2018.
[2] B. Henze, C. Noussair, and B. Willems, “Regulation of network infrastructure investments:
an experimental evaluation,” Journal of Regulatory Economics, vol. 42, no. 1, pp. 1–38,
Aug. 2012.
[3] Houfeng Huang, Qing Ling, Wei Shi, and Jinlin Wang, “Collaborative Resource Allocation
Over a Hybrid Cloud Center and Edge Server Network,” Journal of Computational
Mathematics, vol. 35, no. 4, pp. 421–436, Jul. 2017.
[4] O. Kwon and S. Jung, “Physical network infrastructure design based on user
communication patterns,” European Physical Journal B -- Condensed Matter, vol. 86, no.
10, pp. 1–4, Oct. 2013.
[5] Pavel V. Romasevich and Elena V. Smirnova, “D-Link Solutions for the Organization of
the Educational Process in the Field of Info-Communications and Telecommunications
Infrastructure of Data Processing Centers,” Sovremennye Informacionnye Tehnologii i IT-
obrazovanie, no. 4, p. 865, 2018.
[6] L. Rusu and A. Smeu, “Managing the Reliable Design of an Enterprise IT Network
Infrastructure,” Information Systems Management, vol. 27, no. 3, pp. 238–246, Summer
2010.
[7] D. Sabella et al., “Designing the 5G network infrastructure: a flexible and reconfigurable
architecture based on context and content information,” EURASIP Journal on Wireless
Communications & Networking, vol. 2018, no. 1, pp. 1–1, Aug. 2018.
[8] M. Alenezi, K. Almustafa, and K. A. Meerja, “Cloud based SDN and NFV architectures for
IoT infrastructure,” Egyptian Informatics Journal, vol. 20, pp. 1–10, Mar. 2019.
[9] B. Fidler and A. Acker, “Metadata, infrastructure, and computer-mediated communication
in historical perspective,” Journal of the Association for Information Science &
Technology, vol. 68, no. 2, pp. 412–422, Feb. 2017.
[10] Marek URBANIK, “Consequences of Failure of Gas Network Infrastructure,” Journal of
Civil Engineering, Environment and Architecture, 2016.
References
[1] Evgeny A. Basinya, “Distributed system of collecting, processing and analysis of security
information events of the enterprise network infrastructure,” Bezopasnostʹ Informacionnyh
Tehnologij, no. 4, p. 43, 2018.
[2] B. Henze, C. Noussair, and B. Willems, “Regulation of network infrastructure investments:
an experimental evaluation,” Journal of Regulatory Economics, vol. 42, no. 1, pp. 1–38,
Aug. 2012.
[3] Houfeng Huang, Qing Ling, Wei Shi, and Jinlin Wang, “Collaborative Resource Allocation
Over a Hybrid Cloud Center and Edge Server Network,” Journal of Computational
Mathematics, vol. 35, no. 4, pp. 421–436, Jul. 2017.
[4] O. Kwon and S. Jung, “Physical network infrastructure design based on user
communication patterns,” European Physical Journal B -- Condensed Matter, vol. 86, no.
10, pp. 1–4, Oct. 2013.
[5] Pavel V. Romasevich and Elena V. Smirnova, “D-Link Solutions for the Organization of
the Educational Process in the Field of Info-Communications and Telecommunications
Infrastructure of Data Processing Centers,” Sovremennye Informacionnye Tehnologii i IT-
obrazovanie, no. 4, p. 865, 2018.
[6] L. Rusu and A. Smeu, “Managing the Reliable Design of an Enterprise IT Network
Infrastructure,” Information Systems Management, vol. 27, no. 3, pp. 238–246, Summer
2010.
[7] D. Sabella et al., “Designing the 5G network infrastructure: a flexible and reconfigurable
architecture based on context and content information,” EURASIP Journal on Wireless
Communications & Networking, vol. 2018, no. 1, pp. 1–1, Aug. 2018.
[8] M. Alenezi, K. Almustafa, and K. A. Meerja, “Cloud based SDN and NFV architectures for
IoT infrastructure,” Egyptian Informatics Journal, vol. 20, pp. 1–10, Mar. 2019.
[9] B. Fidler and A. Acker, “Metadata, infrastructure, and computer-mediated communication
in historical perspective,” Journal of the Association for Information Science &
Technology, vol. 68, no. 2, pp. 412–422, Feb. 2017.
[10] Marek URBANIK, “Consequences of Failure of Gas Network Infrastructure,” Journal of
Civil Engineering, Environment and Architecture, 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


