ITC540 IT Infrastructure Management: Data Governance & Management
VerifiedAdded on 2024/05/20
|8
|1540
|164
Homework Assignment
AI Summary
This ITC540 IT Infrastructure Management assignment focuses on data governance and data management concepts. It defines electronic records management, business intelligence, data and text mining, big data analytics, enterprise architecture, data lifecycle, and cloud computing. It discusses how data and text mining create business value and addresses problems associated with cloud computing, providing solutions for unsecured data transfer and user access control. The assignment also explores the design and implementation of an EIS, its associated problems, and improvements made by the CIO, highlighting the benefits of the new IT architecture and data governance. Finally, it examines Coca-Cola's use of POS data in near real-time, its approach to creating favorable customer experiences, the importance of a trusted view of the data, and the strategic benefit of the Black Book model.

ITC540 - IT Infrastructure Management
Assignment 2: Data Governance and Data Management
Assignment 2: Data Governance and Data Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Question 1: Define and explain the concept of the following terminologies.........................................2
Question 2: How does "data and text mining" create business value?.................................................4
Question 3: What are the problems associated with cloud computing? Give two examples and
provide some solutions.........................................................................................................................4
Question 4.............................................................................................................................................4
Question 5.............................................................................................................................................5
References.............................................................................................................................................7
1
Question 1: Define and explain the concept of the following terminologies.........................................2
Question 2: How does "data and text mining" create business value?.................................................4
Question 3: What are the problems associated with cloud computing? Give two examples and
provide some solutions.........................................................................................................................4
Question 4.............................................................................................................................................4
Question 5.............................................................................................................................................5
References.............................................................................................................................................7
1

Question 1: Define and explain the concept of the following terminologies
Electronic Records Management:
It deals with the field of management that performs the functionality of efficient and
systematic control. With this, various business activities and transactions have processes and
maintenance evidence in the form of records (AIIM, 2018).
Business intelligence (BI) and Analytics
Business intelligence is the set of technologies which helps the large enterprises to support in
decision making. This helps in focusing on executives and management for the company
operations.
Business Analytics is responsible for developing a breakdown structure that supports the
organisation system and helps in understanding the whole system (Caldwell, 2017).
Data and text mining
Text mining techniques belong to set of process in which documents having unstructured text
converted into structured text type information. The content is always annotated which
classified and visualized through link is mapping.
Data mining is a type of process in which algorithms are used for the analysis and extraction
of useful information from a group of data. With this, outcomes can be predicted from data
sets by discovering hidden patterns and data relationships (Expertsystem, 2016).
Big data analytics and data discovery
Big data analytics is the technique used for the examining huge data sets having varied type
of data. It uncovers the hidden patterns, market trends and other useful information. It
develops effective marketing campaigns (Galetto, 2018).
Data discovery is the trend of analytics which is the logical combination of big data, data
discovery and data science (Elliott, 2015).
Enterprise architecture
The objectives of this architecture are to develop a unified environment for a group of many
business units and having a link of symbiotic side. This provides alignment and
standardization of IT assets for project management and software management (Minoli,
2017).
2
Electronic Records Management:
It deals with the field of management that performs the functionality of efficient and
systematic control. With this, various business activities and transactions have processes and
maintenance evidence in the form of records (AIIM, 2018).
Business intelligence (BI) and Analytics
Business intelligence is the set of technologies which helps the large enterprises to support in
decision making. This helps in focusing on executives and management for the company
operations.
Business Analytics is responsible for developing a breakdown structure that supports the
organisation system and helps in understanding the whole system (Caldwell, 2017).
Data and text mining
Text mining techniques belong to set of process in which documents having unstructured text
converted into structured text type information. The content is always annotated which
classified and visualized through link is mapping.
Data mining is a type of process in which algorithms are used for the analysis and extraction
of useful information from a group of data. With this, outcomes can be predicted from data
sets by discovering hidden patterns and data relationships (Expertsystem, 2016).
Big data analytics and data discovery
Big data analytics is the technique used for the examining huge data sets having varied type
of data. It uncovers the hidden patterns, market trends and other useful information. It
develops effective marketing campaigns (Galetto, 2018).
Data discovery is the trend of analytics which is the logical combination of big data, data
discovery and data science (Elliott, 2015).
Enterprise architecture
The objectives of this architecture are to develop a unified environment for a group of many
business units and having a link of symbiotic side. This provides alignment and
standardization of IT assets for project management and software management (Minoli,
2017).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
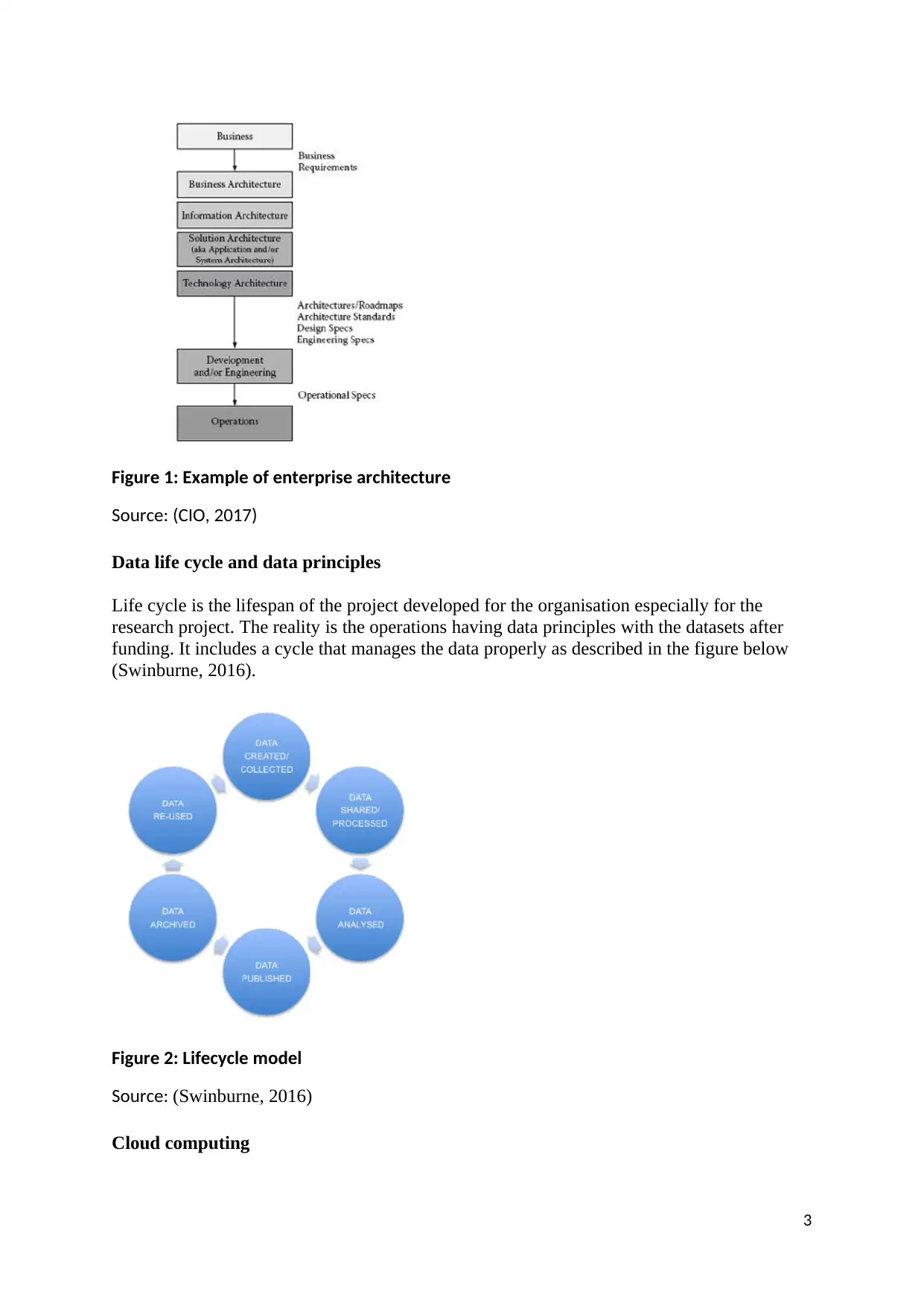
Figure 1: Example of enterprise architecture
Source: (CIO, 2017)
Data life cycle and data principles
Life cycle is the lifespan of the project developed for the organisation especially for the
research project. The reality is the operations having data principles with the datasets after
funding. It includes a cycle that manages the data properly as described in the figure below
(Swinburne, 2016).
Figure 2: Lifecycle model
Source: (Swinburne, 2016)
Cloud computing
3
Source: (CIO, 2017)
Data life cycle and data principles
Life cycle is the lifespan of the project developed for the organisation especially for the
research project. The reality is the operations having data principles with the datasets after
funding. It includes a cycle that manages the data properly as described in the figure below
(Swinburne, 2016).
Figure 2: Lifecycle model
Source: (Swinburne, 2016)
Cloud computing
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It is a technique that helps in storing and accessing the data and programs with the help of
internet connectivity. It involves development of server farm infrastructure for the internet
(Griffith, 2016).
Question 2: How does "data and text mining" create business value?
Data and text mining is used for the analysis of the customer and competitor so that the
competition will increase to increase efficiency.
For data mining
- Leads the efficiency gain
- Addition of new knowledge and resources
- Prevention of realisation of full potential
- Identification of significant barrier
For text mining
- Limited commercial confidentiality
- Active participation
- Limited use of data (McDonald and Kelly, 2012).
Question 3: What are the problems associated with cloud computing? Give two
examples and provide some solutions.
The problems associated to the cloud computing are unsecured data transfer, storage,
communication, separation, unauthorised user access and so on. Two of them are:
1. Unsecure data transfer: As the traffic is high between two network and server in cloud
traverse the internet.
Solution: The channel might be corrupted so the data must be encrypted to secure the
data in addition to its authentication.
2. User access control: Unauthorized users can attack the system at the vulnerability.
The threats can be generated from inside the company due to other employees
(Beckham, 2011).
Solution: The devices and the systems should be authorised properly with single login
or biometric authentication.
Question 4:
Why was an EIS designed and implemented?
EIS is used at the high level management to provide the real time representation information.
It provides set of technology solutions in market as business intelligence software. It helps in
goal setting, planning, goal setting, tracking performance.
4
internet connectivity. It involves development of server farm infrastructure for the internet
(Griffith, 2016).
Question 2: How does "data and text mining" create business value?
Data and text mining is used for the analysis of the customer and competitor so that the
competition will increase to increase efficiency.
For data mining
- Leads the efficiency gain
- Addition of new knowledge and resources
- Prevention of realisation of full potential
- Identification of significant barrier
For text mining
- Limited commercial confidentiality
- Active participation
- Limited use of data (McDonald and Kelly, 2012).
Question 3: What are the problems associated with cloud computing? Give two
examples and provide some solutions.
The problems associated to the cloud computing are unsecured data transfer, storage,
communication, separation, unauthorised user access and so on. Two of them are:
1. Unsecure data transfer: As the traffic is high between two network and server in cloud
traverse the internet.
Solution: The channel might be corrupted so the data must be encrypted to secure the
data in addition to its authentication.
2. User access control: Unauthorized users can attack the system at the vulnerability.
The threats can be generated from inside the company due to other employees
(Beckham, 2011).
Solution: The devices and the systems should be authorised properly with single login
or biometric authentication.
Question 4:
Why was an EIS designed and implemented?
EIS is used at the high level management to provide the real time representation information.
It provides set of technology solutions in market as business intelligence software. It helps in
goal setting, planning, goal setting, tracking performance.
4

What problems did executives have with the EIS?
The problems are:
- Half data is received for analysis
- Improper data
- Creation of different time frames
What were the two reasons for those EIS problems?
Reasons for issues in EIS are:
- Imperfect design of architecture of IT sector
- Complicated user interface
How did the CIO improve the EIS?
Ways to improve EIS by CIO are:
- Design and implement new task force
- Implementation of new procedures and policies for data governance
- Standardization of data formats
What are the benefits of the new IT architecture?
The new IT architecture has many benefits and some of them are:
- Reports can be easily modified
- Used time and cost can be eliminated
- System maintenance can reuse the IT resource
What are the benefits of data governance?
- Better decision making
- High operational efficiency
- Greater data quality
- Increased revenue (Cole, 2017).
Question 5:
Why is it important for Coca-Cola to be able to process POS data in near real time?
The process of POD data is important because of the mutual proper planning, prediction and
replenishment at the time of supply chain at the coca-cola company.
How does Coca-Cola attempt to create favorable customer experiences?
5
The problems are:
- Half data is received for analysis
- Improper data
- Creation of different time frames
What were the two reasons for those EIS problems?
Reasons for issues in EIS are:
- Imperfect design of architecture of IT sector
- Complicated user interface
How did the CIO improve the EIS?
Ways to improve EIS by CIO are:
- Design and implement new task force
- Implementation of new procedures and policies for data governance
- Standardization of data formats
What are the benefits of the new IT architecture?
The new IT architecture has many benefits and some of them are:
- Reports can be easily modified
- Used time and cost can be eliminated
- System maintenance can reuse the IT resource
What are the benefits of data governance?
- Better decision making
- High operational efficiency
- Greater data quality
- Increased revenue (Cole, 2017).
Question 5:
Why is it important for Coca-Cola to be able to process POS data in near real time?
The process of POD data is important because of the mutual proper planning, prediction and
replenishment at the time of supply chain at the coca-cola company.
How does Coca-Cola attempt to create favorable customer experiences?
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The experience of the favourable customers is satisfied due to the approach of the Big Data
Coca Cola technique. This can be achieved by cutting cost of overtime up to half during the
analysis of service data.
What is the importance of having a trusted view of the data?
The trusted view of data has importance in operations such as transactions and sales is to
make company quicker and accurate for the response. This response is changes with changing
trend.
What is the Black Book model?
In this model, the connection between variables is identified to decrease the uncertainties.
The blend juice method is used to develop the stable taste.
Explain the strategic benefit of the Black Book model.
The benefits in blending techniques are:
- Optimized supply chain interactions
- Better decision making concepts
- Quick re-plan in case of changed weather (Messmer, 2014).
6
Coca Cola technique. This can be achieved by cutting cost of overtime up to half during the
analysis of service data.
What is the importance of having a trusted view of the data?
The trusted view of data has importance in operations such as transactions and sales is to
make company quicker and accurate for the response. This response is changes with changing
trend.
What is the Black Book model?
In this model, the connection between variables is identified to decrease the uncertainties.
The blend juice method is used to develop the stable taste.
Explain the strategic benefit of the Black Book model.
The benefits in blending techniques are:
- Optimized supply chain interactions
- Better decision making concepts
- Quick re-plan in case of changed weather (Messmer, 2014).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
AIIM. (2018). What is Electronic Records Management (ERM)?. Retrieved from
http://www.aiim.org/What-is-ERM-Electronic-Records-Management#
Beckham, J. (2011). The Top 5 Security Risks of Cloud Computing. Cisco Blogs.
Retrieved from https://blogs.cisco.com/smallbusiness/the-top-5-security-risks-of-
cloud-computing
Caldwell, C. (2017). Comparing Business Intelligence vs. Analytics. Logi Analytics.
Retrieved from https://www.logianalytics.com/bi-trends/business-intelligence-vs-
analytics-whats-the-difference/
CIO. (2017). Enterprise Architecture: The Scarce Skillset in Big Demand. Retrieved
from https://www.cio.com/article/3226444/leadership-management/enterprise-
architecture-the-scarce-skillset-in-big-demand.html
Cole, Z. (2017). The Top 6 Benefits of Data Governance. Erwin. Retrieved from
https://erwin.com/blog/top-6-benefits-of-data-governance/
Elliott, T. (2015). Big Data Discovery Is The Next Big Trend In Analytics. ZDNet.
Retrieved from http://www.zdnet.com/article/big-data-discovery-is-the-next-big-
trend-in-analytics/
Expertsystem. (2016). Text mining vs. data mining. Retrieved from
http://www.expertsystem.com/text-mining-vs-data-mining/
Galetto, M. (2018). WHAT IS BIG DATA ANALYTICS?. Ngdata. Retrieved from
https://www.ngdata.com/what-is-big-data-analytics/
Griffith, E. (2016). What Is Cloud Computing?. PCMag Australia. Retrieved from
http://au.pcmag.com/networking-communications-software-products/29902/feature/
what-is-cloud-computing
Ingram, D. (2018). What Is a Management Information System?. Smallbusiness.
Retrieved from http://smallbusiness.chron.com/management-information-system-
2104.html
McDonald, D., & Kelly, U. (2012). Value and benefits of text mining. Jisc. Retrieved
from https://www.jisc.ac.uk/reports/value-and-benefits-of-text-mining
Messmer, E. (2014). Coca-Cola Co.'s 'Black Book' application squeezes best out of
OJ. Network World. Retrieved from
https://www.networkworld.com/article/2176933/applications/coca-cola-co--s--black-
book--application-squeezes-best-out-of-oj.html
Minoli, D. (2016). What Is Enterprise Architecture?. Ittoday. Retrieved from
http://www.ittoday.info/Articles/What_Is_Enterprise_Architecture.htm#.Wq6N58Nub
IU
Swinburne. (2016). The data lifecycle. Retrieved from
http://www.swinburne.edu.au/research/ethics/data-management/the-data-lifecycle/
7
AIIM. (2018). What is Electronic Records Management (ERM)?. Retrieved from
http://www.aiim.org/What-is-ERM-Electronic-Records-Management#
Beckham, J. (2011). The Top 5 Security Risks of Cloud Computing. Cisco Blogs.
Retrieved from https://blogs.cisco.com/smallbusiness/the-top-5-security-risks-of-
cloud-computing
Caldwell, C. (2017). Comparing Business Intelligence vs. Analytics. Logi Analytics.
Retrieved from https://www.logianalytics.com/bi-trends/business-intelligence-vs-
analytics-whats-the-difference/
CIO. (2017). Enterprise Architecture: The Scarce Skillset in Big Demand. Retrieved
from https://www.cio.com/article/3226444/leadership-management/enterprise-
architecture-the-scarce-skillset-in-big-demand.html
Cole, Z. (2017). The Top 6 Benefits of Data Governance. Erwin. Retrieved from
https://erwin.com/blog/top-6-benefits-of-data-governance/
Elliott, T. (2015). Big Data Discovery Is The Next Big Trend In Analytics. ZDNet.
Retrieved from http://www.zdnet.com/article/big-data-discovery-is-the-next-big-
trend-in-analytics/
Expertsystem. (2016). Text mining vs. data mining. Retrieved from
http://www.expertsystem.com/text-mining-vs-data-mining/
Galetto, M. (2018). WHAT IS BIG DATA ANALYTICS?. Ngdata. Retrieved from
https://www.ngdata.com/what-is-big-data-analytics/
Griffith, E. (2016). What Is Cloud Computing?. PCMag Australia. Retrieved from
http://au.pcmag.com/networking-communications-software-products/29902/feature/
what-is-cloud-computing
Ingram, D. (2018). What Is a Management Information System?. Smallbusiness.
Retrieved from http://smallbusiness.chron.com/management-information-system-
2104.html
McDonald, D., & Kelly, U. (2012). Value and benefits of text mining. Jisc. Retrieved
from https://www.jisc.ac.uk/reports/value-and-benefits-of-text-mining
Messmer, E. (2014). Coca-Cola Co.'s 'Black Book' application squeezes best out of
OJ. Network World. Retrieved from
https://www.networkworld.com/article/2176933/applications/coca-cola-co--s--black-
book--application-squeezes-best-out-of-oj.html
Minoli, D. (2016). What Is Enterprise Architecture?. Ittoday. Retrieved from
http://www.ittoday.info/Articles/What_Is_Enterprise_Architecture.htm#.Wq6N58Nub
IU
Swinburne. (2016). The data lifecycle. Retrieved from
http://www.swinburne.edu.au/research/ethics/data-management/the-data-lifecycle/
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



