Tata Consultancy Services: IT Infrastructure for Business Processes
VerifiedAdded on 2023/06/14
|12
|3118
|362
Report
AI Summary
This report examines the application and use of information technology within Tata Consultancy Services (TCS), focusing on how IT infrastructure addresses and achieves organizational business processes. It details the technological equipment used across various departments to support these processes, including operating systems and application software employed in both client and server systems. The report also discusses the movement of email messages over the Internet Protocol (IP), the types of organizational networks in use, and a proposed application architecture for the Human Resources department. Key aspects covered include TCS's support for telecom companies in setting up scalable cloud-based services, its centralized management system for system development, and its DPL cyber security solution. The analysis extends to TCS's data handling capabilities, the structure of its information systems, and the security measures implemented to protect organizational data. Furthermore, the report outlines the network equipment used, such as routers, firewalls, and switches, and specifies the software requirements for both staff and clients to ensure secure access to TCS systems. The report concludes by discussing the TCP/IP model layers and the types of organizational networks, including LAN and WAN, used within TCS.

IT infrastructure
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Information technology has dominated today’s world and every organization is looking
forward to incorporate technology in its operations (Kyriazis et al 2018, p. 10). Technology
incorporation in organization’s business has been an up-hill task that requires specialized
organizations to help in setting up the services. Despite setting up IT infrastructure, maintenance
remains a key part that has been disguising many organizations that require IT services (Kyriazis
et al 2018, p. 18). This project will focus on the following sections; application and use of
information technology in Tata Consultancy Services (TCS), uses of IT infrastructure to address
and achieve its business organizational business processes, available technological equipment
used in various departments to support business processes and operating systems and other
application software that TCS uses in both client and servers systems (Oshri, Kotlarsky &
Willcocks 2008, p. 289). Similarly, the project would address movement of email messages on
the Internet Protocol (IP), the type of organizational networks in use and application architecture
proposal in Human resources department. In this regard, the main objective of the report would
be to access use information technology in the organization. To achieve this, the following aspect
would be analyzed; the context of services offered by TCS, services offered by at the TCS, ease
of accessing TCS services by both staff and clients and organizational ability to sustain its
business as well as support other organizations run on scalable IT infrastructure.
Information Technology use at TCS
Tata Consultancy Services (TCS) has a range of services that it offers to other
organizations in their bid to incorporate IT services in the business operations. First, TCS offer
support to major telecom companies to set up cloud-based services that are both scalable and
Information technology has dominated today’s world and every organization is looking
forward to incorporate technology in its operations (Kyriazis et al 2018, p. 10). Technology
incorporation in organization’s business has been an up-hill task that requires specialized
organizations to help in setting up the services. Despite setting up IT infrastructure, maintenance
remains a key part that has been disguising many organizations that require IT services (Kyriazis
et al 2018, p. 18). This project will focus on the following sections; application and use of
information technology in Tata Consultancy Services (TCS), uses of IT infrastructure to address
and achieve its business organizational business processes, available technological equipment
used in various departments to support business processes and operating systems and other
application software that TCS uses in both client and servers systems (Oshri, Kotlarsky &
Willcocks 2008, p. 289). Similarly, the project would address movement of email messages on
the Internet Protocol (IP), the type of organizational networks in use and application architecture
proposal in Human resources department. In this regard, the main objective of the report would
be to access use information technology in the organization. To achieve this, the following aspect
would be analyzed; the context of services offered by TCS, services offered by at the TCS, ease
of accessing TCS services by both staff and clients and organizational ability to sustain its
business as well as support other organizations run on scalable IT infrastructure.
Information Technology use at TCS
Tata Consultancy Services (TCS) has a range of services that it offers to other
organizations in their bid to incorporate IT services in the business operations. First, TCS offer
support to major telecom companies to set up cloud-based services that are both scalable and

robust in order to help them boost IT productivity (Oshri, Kotlarsky & Willcocks 2008, p. 300).
In order to offer efficient system development services, TCS has put in place centralized
management system lifecycle and documentation that is used to develop customers’ system. In
its API platform that offers system, TCS uses three based approach in developing its
applications; API lifecycles, developing and testing application pipeline and developing systems
advanced features such as API analytics and integrating system monitoring with external tools.
To prove TCS services worth and scalable, organizations such as Telia were able to steer their
business by improving its productivity, it also improved its market time and made its services
cost efficiency. Secondly, TCS has put in place measures to help other organizations to secure
their data. Increase in cyber security threats have made it challenging for organizations to secure
their data and business operations. To solve cyber security challenges, TCS has come up with a
DPL cyber security solution which is SDLC compliant (Oshri, Kotlarsky & Willcocks 2008, p.
306). The security program offered was able to save organization from all vicious activities that
seemed threat to organizational operations. To authenticate its security measures on cyber threat,
TCS has helped a European bank to automate its services by helping it to restructure its
management incident processes, lowered its manual operational efforts and boost data security as
well as minimize data leaks and false positivity. Additionally, TCS through its technology
application has made many organizations data driven-enterprises. It has made data accessible and
secure by making organizations access big data. Generally, big data is believed to open door and
other avenues for organizational success by making organizations access and secure their data.
Data structures and usage of IT infrastructure
TCS is an organization that has a leverage of capabilities and can handle data in many
forms. In order to capture a diverse market, TCS has employed various methodologies to store
In order to offer efficient system development services, TCS has put in place centralized
management system lifecycle and documentation that is used to develop customers’ system. In
its API platform that offers system, TCS uses three based approach in developing its
applications; API lifecycles, developing and testing application pipeline and developing systems
advanced features such as API analytics and integrating system monitoring with external tools.
To prove TCS services worth and scalable, organizations such as Telia were able to steer their
business by improving its productivity, it also improved its market time and made its services
cost efficiency. Secondly, TCS has put in place measures to help other organizations to secure
their data. Increase in cyber security threats have made it challenging for organizations to secure
their data and business operations. To solve cyber security challenges, TCS has come up with a
DPL cyber security solution which is SDLC compliant (Oshri, Kotlarsky & Willcocks 2008, p.
306). The security program offered was able to save organization from all vicious activities that
seemed threat to organizational operations. To authenticate its security measures on cyber threat,
TCS has helped a European bank to automate its services by helping it to restructure its
management incident processes, lowered its manual operational efforts and boost data security as
well as minimize data leaks and false positivity. Additionally, TCS through its technology
application has made many organizations data driven-enterprises. It has made data accessible and
secure by making organizations access big data. Generally, big data is believed to open door and
other avenues for organizational success by making organizations access and secure their data.
Data structures and usage of IT infrastructure
TCS is an organization that has a leverage of capabilities and can handle data in many
forms. In order to capture a diverse market, TCS has employed various methodologies to store
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and retrieve required data. The methodology chosen depends with subject client need as well as
TCS capability to offer similar service efficiently. To offer convenient services, TCS has to store
and maintain some information about its clients. To make this practical, it has created
information system that helps it store clients’ information and services they provide to them
(Breitgand et al 2018, p. 95). The subject information system is meant for TCS only. It offers
both storage and retrieval capabilities. First, it has implemented database which I capable to store
all forms of data such as images inform of blobs, raw integers and strings. Its database is
segmented in relation to services offered to the subject organization. In an example, if subject
organization requires services from the TCS, it is categorized as service client under consultation
department. To makes its services secure, it does not require a third party to manage its database.
It has developed internally hosted server which is capable to handle this data in a more
convenient way and without delay. To make its services more robust, it has implemented
organizational ERP which helps its client to generate requests for services. This has made it
possible for the company to attract more clients because its services are accessible worldwide. In
case client organizations to transform its services, TCS makes use of remote connection software
to access client’s data. Clients’ services within TCS are subdivided according to the needs of the
customers. In this regard, IT infrastructure differs from department to the other. An example
from development department includes both Linux and windows applications to help
organization to access robust services as required. There is a close collaboration between hosting
and development department because some of the application developed by TCS for clients are
hosted from within the organization in order to facilitate easy maintenance. Finally, TCS has
implemented strong firewalls software to secure organizational data from unauthorized access by
hackers.
TCS capability to offer similar service efficiently. To offer convenient services, TCS has to store
and maintain some information about its clients. To make this practical, it has created
information system that helps it store clients’ information and services they provide to them
(Breitgand et al 2018, p. 95). The subject information system is meant for TCS only. It offers
both storage and retrieval capabilities. First, it has implemented database which I capable to store
all forms of data such as images inform of blobs, raw integers and strings. Its database is
segmented in relation to services offered to the subject organization. In an example, if subject
organization requires services from the TCS, it is categorized as service client under consultation
department. To makes its services secure, it does not require a third party to manage its database.
It has developed internally hosted server which is capable to handle this data in a more
convenient way and without delay. To make its services more robust, it has implemented
organizational ERP which helps its client to generate requests for services. This has made it
possible for the company to attract more clients because its services are accessible worldwide. In
case client organizations to transform its services, TCS makes use of remote connection software
to access client’s data. Clients’ services within TCS are subdivided according to the needs of the
customers. In this regard, IT infrastructure differs from department to the other. An example
from development department includes both Linux and windows applications to help
organization to access robust services as required. There is a close collaboration between hosting
and development department because some of the application developed by TCS for clients are
hosted from within the organization in order to facilitate easy maintenance. Finally, TCS has
implemented strong firewalls software to secure organizational data from unauthorized access by
hackers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network equipment and their functions
To make organizational business process successful, several devices are required. These
devices are used in various TCS departments such as networking department. This is the
department where organizational network is developed and maintained. It is the same department
where clients’ networks are setup and run from. Since network is very sensitive in any
organization, its security is of paramount and should be taken with required weight (Ross,
McEvilley & Ore 2018,p. 845). The first equipment involves routers which are used to segment
and share organizational network. TCS network is divided into administrative and general
network. To divide this network, organization has used router to categorize departments into
either administrative or general (Tate et al 2018, p. 56). Since all departments have
administrative sections, they must be provided with all capabilities. To make organizational
management easy, all departments’ administrative sections are housed under administration
building in order to share common network without restrictions. Without routers, network
segmentation and maintenance would not be possible. Next, firewalls are very significant in the
networking. They are used to filter all signals entering and leaving the organization (Siegal et al
2018, p. 146). It is only through firewall that security of the organization is set and no
unauthorized user would penetrate to organizational network. Additionally, all departments
would require computers which would be used to access organizational data and communicate to
other organizations. It is only through computers that all information system capabilities
achieved. Further, hosting department would require servers to host range of applications so that
they are available to customers as cloud services (Anglin et al 2018, 904). In the same hosting
department, radio transmitters would be of great use since they would be used to receive and sent
network signals to all customers’ destinations. Consequently, switches would be used to in
To make organizational business process successful, several devices are required. These
devices are used in various TCS departments such as networking department. This is the
department where organizational network is developed and maintained. It is the same department
where clients’ networks are setup and run from. Since network is very sensitive in any
organization, its security is of paramount and should be taken with required weight (Ross,
McEvilley & Ore 2018,p. 845). The first equipment involves routers which are used to segment
and share organizational network. TCS network is divided into administrative and general
network. To divide this network, organization has used router to categorize departments into
either administrative or general (Tate et al 2018, p. 56). Since all departments have
administrative sections, they must be provided with all capabilities. To make organizational
management easy, all departments’ administrative sections are housed under administration
building in order to share common network without restrictions. Without routers, network
segmentation and maintenance would not be possible. Next, firewalls are very significant in the
networking. They are used to filter all signals entering and leaving the organization (Siegal et al
2018, p. 146). It is only through firewall that security of the organization is set and no
unauthorized user would penetrate to organizational network. Additionally, all departments
would require computers which would be used to access organizational data and communicate to
other organizations. It is only through computers that all information system capabilities
achieved. Further, hosting department would require servers to host range of applications so that
they are available to customers as cloud services (Anglin et al 2018, 904). In the same hosting
department, radio transmitters would be of great use since they would be used to receive and sent
network signals to all customers’ destinations. Consequently, switches would be used to in

almost all departments but mainly would be in technical support where all signals would be
distributed to the required sections. Switch functionality in this case is very crucial when it
comes to data sharing and nodes communication (Breitgand et al 2018, p. 85). It is able to
analyze data destination and originality address to determine which computer is to have sent and
would receive a given piece of data.
Operating system and application software specifications
To access and get services from TCS Company, all staffs and clients are requested to
meet some software requirements for security measures. To all window operating system users,
they are to run on windows 7 or higher version (Oshri, Kotlarsky & Willcocks 2008, p. 290).
This helps organization to set all required features for users because most of the windows7 or
later versions have no compatibility issues. This makes possible to establish remote desktop
connection when need be. On the same note, those running on Linux should be able to make
required connection secure without compromising systems security (Cha,Pingry & Thatcher
2008, p. 283). Since Linux is very powerful and can be used to sabotage organizational data,
those using Linux are requested to register with TCS security department so that they can be
provided with authentication procedures. Apart from operating systems, applications software is
restricted to some specification in order to connect to TCS data or systems (Jain & Shanbhag
2012, p. 29). All browsers are required to be up to date. This is meant to prevent dubious
activities from taking place. Some browsers are known to be vulnerable to hackers and malwares
and can easily transmit viruses to organizational system. Consequently, all database and API
development are to be done with SQL 2012 versions or later (Davne et al 2014, p. 278). This
improves security parameters because all latest application software is believed to be integrated
with up to date security parameters.
distributed to the required sections. Switch functionality in this case is very crucial when it
comes to data sharing and nodes communication (Breitgand et al 2018, p. 85). It is able to
analyze data destination and originality address to determine which computer is to have sent and
would receive a given piece of data.
Operating system and application software specifications
To access and get services from TCS Company, all staffs and clients are requested to
meet some software requirements for security measures. To all window operating system users,
they are to run on windows 7 or higher version (Oshri, Kotlarsky & Willcocks 2008, p. 290).
This helps organization to set all required features for users because most of the windows7 or
later versions have no compatibility issues. This makes possible to establish remote desktop
connection when need be. On the same note, those running on Linux should be able to make
required connection secure without compromising systems security (Cha,Pingry & Thatcher
2008, p. 283). Since Linux is very powerful and can be used to sabotage organizational data,
those using Linux are requested to register with TCS security department so that they can be
provided with authentication procedures. Apart from operating systems, applications software is
restricted to some specification in order to connect to TCS data or systems (Jain & Shanbhag
2012, p. 29). All browsers are required to be up to date. This is meant to prevent dubious
activities from taking place. Some browsers are known to be vulnerable to hackers and malwares
and can easily transmit viruses to organizational system. Consequently, all database and API
development are to be done with SQL 2012 versions or later (Davne et al 2014, p. 278). This
improves security parameters because all latest application software is believed to be integrated
with up to date security parameters.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internet Model layers
Internet communication protocols are segmented into layers. These layers are structured
to facilitate efficient communication over the internet. In this case, since communication is over
the internet, TCP model would be discussed. TCP model is made up of five layers which
correspond to OSI model 7 layers (Li et al 2018, p. 296). Each layer is made to communicate
with its adjacent layer, either below or above it. The physical layer is used to encode and decode
data bits that are found in the frame and contains transceiver that is used to sends and receives all
signals in the network. The second layer is data link layer which creates required data frames as
they move across the network model. The data frames are used to encapsulate all data bits and
make use of available MAC addresses in the data frames to identify both destination and source
address of the data (Oshri, Fenema & Kotlarsky 2008, p. 612). The next layer is network, which
tasked with creating data packets as messages moves across the network. In this layer, IP
addresses are used to identify data packets both destination and source addresses. Further, the
transport layer in the network is used to establish any required applications running on the other
different hosts (Shaashua, Shaashua & Neura Inc 2018, p. 865). Its main function is to monitor
all applications above it by facilitating them with port numbers as well as use network layer to
communicate with TCP/IP network. Finally, application layer is where all applications that need
network communication reside. Some of the applications that are found in application layer are;
browsers and email clients.
Internet communication protocols are segmented into layers. These layers are structured
to facilitate efficient communication over the internet. In this case, since communication is over
the internet, TCP model would be discussed. TCP model is made up of five layers which
correspond to OSI model 7 layers (Li et al 2018, p. 296). Each layer is made to communicate
with its adjacent layer, either below or above it. The physical layer is used to encode and decode
data bits that are found in the frame and contains transceiver that is used to sends and receives all
signals in the network. The second layer is data link layer which creates required data frames as
they move across the network model. The data frames are used to encapsulate all data bits and
make use of available MAC addresses in the data frames to identify both destination and source
address of the data (Oshri, Fenema & Kotlarsky 2008, p. 612). The next layer is network, which
tasked with creating data packets as messages moves across the network. In this layer, IP
addresses are used to identify data packets both destination and source addresses. Further, the
transport layer in the network is used to establish any required applications running on the other
different hosts (Shaashua, Shaashua & Neura Inc 2018, p. 865). Its main function is to monitor
all applications above it by facilitating them with port numbers as well as use network layer to
communicate with TCP/IP network. Finally, application layer is where all applications that need
network communication reside. Some of the applications that are found in application layer are;
browsers and email clients.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
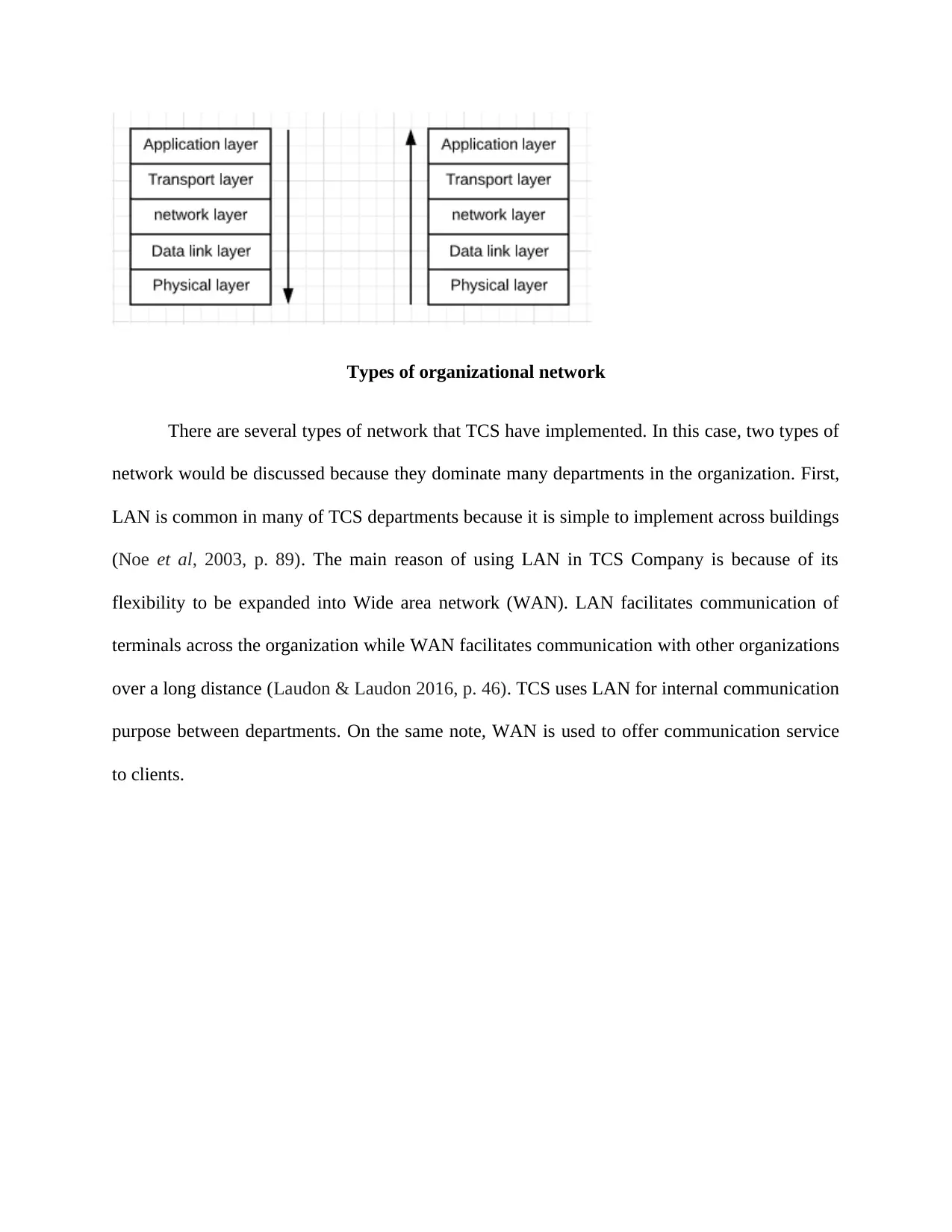
Types of organizational network
There are several types of network that TCS have implemented. In this case, two types of
network would be discussed because they dominate many departments in the organization. First,
LAN is common in many of TCS departments because it is simple to implement across buildings
(Noe et al, 2003, p. 89). The main reason of using LAN in TCS Company is because of its
flexibility to be expanded into Wide area network (WAN). LAN facilitates communication of
terminals across the organization while WAN facilitates communication with other organizations
over a long distance (Laudon & Laudon 2016, p. 46). TCS uses LAN for internal communication
purpose between departments. On the same note, WAN is used to offer communication service
to clients.
There are several types of network that TCS have implemented. In this case, two types of
network would be discussed because they dominate many departments in the organization. First,
LAN is common in many of TCS departments because it is simple to implement across buildings
(Noe et al, 2003, p. 89). The main reason of using LAN in TCS Company is because of its
flexibility to be expanded into Wide area network (WAN). LAN facilitates communication of
terminals across the organization while WAN facilitates communication with other organizations
over a long distance (Laudon & Laudon 2016, p. 46). TCS uses LAN for internal communication
purpose between departments. On the same note, WAN is used to offer communication service
to clients.
Human resource architecture proposal
Human resource department makes use of information system to capture organizational
employees’ data and clients that get their services from TCS. To make its information flow
accordingly, its system interact with various sections of the organizations in order to make
service delivery efficient (Green et al 2018, p. 414). Human resource application interfaces with;
clients’ ordering, administration protocol,
Conclusion
IT services are on demand by almost all organizations. This have created need to come up
with specialized organization such as TCS to fill this gap. TCS offers services such as supporting
major telecom companies, providing cyber security services and offering big data solutions to
various organizations. TCS makes use of almost all available major data structures in order to
fulfill all clients’ needs. Due to clients demand, it would be inappropriate to limit its data storage
Human resource department makes use of information system to capture organizational
employees’ data and clients that get their services from TCS. To make its information flow
accordingly, its system interact with various sections of the organizations in order to make
service delivery efficient (Green et al 2018, p. 414). Human resource application interfaces with;
clients’ ordering, administration protocol,
Conclusion
IT services are on demand by almost all organizations. This have created need to come up
with specialized organization such as TCS to fill this gap. TCS offers services such as supporting
major telecom companies, providing cyber security services and offering big data solutions to
various organizations. TCS makes use of almost all available major data structures in order to
fulfill all clients’ needs. Due to clients demand, it would be inappropriate to limit its data storage
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

in a certain type of data structure. Organizations are moving from relational database to OOP due
to growing demand to store images as data. To secure organizational and client data, TCS makes
use of equipment such as routers to segment network, switches, bridges, network firewalls and
radio transceivers. The OS and application software are very important aspect when it comes to
specifications required to access services from TCS Company. It’s a requirement that all
software be up to data as required. To implement its network, TCS has made use of LAN and
WAN because they are highly correlated. The project should continue to help organizations
realize technological use. It should focus on big data access and cyber security threats to big data
in order to make IT implementation more reliable.
Bibliography
Anglin, M.J., Cannon, D.M., Dawson, C.S., Fruchtman, B., Haye, M.A. and Martin, H.N.,
International Business Machines Corp, 2018. Replication of data objects from a source server to
a target server. U.S. Patent 9,910,904.
Breitgand, D., Da Silva, D.M., Epstein, A., Glikson, A., Hines, M.R., Ryu, K.D. and Silva, M.A.,
International Business Machines Corp, 2018. Dynamic virtual machine resizing in a cloud
computing infrastructure. U.S. Patent 9,858,095.
Cha, H.S., Pingry, D.E. and Thatcher, M.E., 2008. Managing the knowledge supply chain: an
organizational learning model of information technology offshore outsourcing. Mis Quarterly,
pp.281-306.
Davne, J., Volkov, A., Yankelevich, M. and Malamud, M., Cloudnexa, 2014. Managing services
in a cloud computing environment. U.S. Patent 8,910,278.
to growing demand to store images as data. To secure organizational and client data, TCS makes
use of equipment such as routers to segment network, switches, bridges, network firewalls and
radio transceivers. The OS and application software are very important aspect when it comes to
specifications required to access services from TCS Company. It’s a requirement that all
software be up to data as required. To implement its network, TCS has made use of LAN and
WAN because they are highly correlated. The project should continue to help organizations
realize technological use. It should focus on big data access and cyber security threats to big data
in order to make IT implementation more reliable.
Bibliography
Anglin, M.J., Cannon, D.M., Dawson, C.S., Fruchtman, B., Haye, M.A. and Martin, H.N.,
International Business Machines Corp, 2018. Replication of data objects from a source server to
a target server. U.S. Patent 9,910,904.
Breitgand, D., Da Silva, D.M., Epstein, A., Glikson, A., Hines, M.R., Ryu, K.D. and Silva, M.A.,
International Business Machines Corp, 2018. Dynamic virtual machine resizing in a cloud
computing infrastructure. U.S. Patent 9,858,095.
Cha, H.S., Pingry, D.E. and Thatcher, M.E., 2008. Managing the knowledge supply chain: an
organizational learning model of information technology offshore outsourcing. Mis Quarterly,
pp.281-306.
Davne, J., Volkov, A., Yankelevich, M. and Malamud, M., Cloudnexa, 2014. Managing services
in a cloud computing environment. U.S. Patent 8,910,278.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Green, J.P., Chandnani, A.D. and Christensen, S.D., Microsoft Technology Licensing LLC,
2018. Detecting script-based malware using emulation and heuristics. U.S. Patent 9,858,414.
Jain, A.K. and Shanbhag, D., 2012. Addressing security and privacy risks in mobile
applications. IT Professional, 14(5), pp.28-33.
Kyriazis, D., Menychtas, A., Kousiouris, G., Boniface, M., Cucinotta, T., Oberle, K., Voith, T.,
Oliveros, E. and Berger, S., 2018. A real-time service oriented infrastructure. GSTF Journal on
Computing (JoC), 1(2).
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson Education
India.
Noe, R.A., Hollenbeck, J.R., Gerhart, B. and Wright, P.M., 2003. Gaining a competitive
advantage. Irwin: McGraw-Hill.
Oshri, I., Kotlarsky, J. and Willcocks, L., 2008. Managing dispersed expertise in IT offshore
outsourcing: lessons from Tata Consultancy Services. In Outsourcing Global Services (pp. 288-
310). Palgrave Macmillan, London.
Oshri, I., Van Fenema, P. and Kotlarsky, J., 2008. Knowledge transfer in globally distributed
teams: the role of transactive memory. Information Systems Journal, 18(6), pp.593-616.
Ross, R.S., McEvilley, M. and Oren, J.C., 2018. Systems Security Engineering: Considerations
for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems [including
updates as of 1-03-2018] (No. Special Publication (NIST SP)-800-860).
Shaashua, T.M. and Shaashua, O., Neura Inc, 2018. Physical environment profiling through
internet of things integration platform. U.S. Patent 9,871,865.
2018. Detecting script-based malware using emulation and heuristics. U.S. Patent 9,858,414.
Jain, A.K. and Shanbhag, D., 2012. Addressing security and privacy risks in mobile
applications. IT Professional, 14(5), pp.28-33.
Kyriazis, D., Menychtas, A., Kousiouris, G., Boniface, M., Cucinotta, T., Oberle, K., Voith, T.,
Oliveros, E. and Berger, S., 2018. A real-time service oriented infrastructure. GSTF Journal on
Computing (JoC), 1(2).
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson Education
India.
Noe, R.A., Hollenbeck, J.R., Gerhart, B. and Wright, P.M., 2003. Gaining a competitive
advantage. Irwin: McGraw-Hill.
Oshri, I., Kotlarsky, J. and Willcocks, L., 2008. Managing dispersed expertise in IT offshore
outsourcing: lessons from Tata Consultancy Services. In Outsourcing Global Services (pp. 288-
310). Palgrave Macmillan, London.
Oshri, I., Van Fenema, P. and Kotlarsky, J., 2008. Knowledge transfer in globally distributed
teams: the role of transactive memory. Information Systems Journal, 18(6), pp.593-616.
Ross, R.S., McEvilley, M. and Oren, J.C., 2018. Systems Security Engineering: Considerations
for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems [including
updates as of 1-03-2018] (No. Special Publication (NIST SP)-800-860).
Shaashua, T.M. and Shaashua, O., Neura Inc, 2018. Physical environment profiling through
internet of things integration platform. U.S. Patent 9,871,865.

Siegal, J., Rowell, S. and Hintz, T., Open Invention Network LLC, 2018. Method and system for
providing online authentication utilizing biometric data. U.S. Patent 9,911,146.
Tate, J., Beck, P., Ibarra, H.H., Kumaravel, S. and Miklas, L., 2018. Introduction to storage area
networks. IBM Redbooks.
Li, P., Chen, Z., Yang, L.T., Zhang, Q. and Deen, M.J., 2018. Deep convolutional computation
model for feature learning on big data in Internet of Things. IEEE Transactions on Industrial
Informatics, 14(2), pp.790-798.
providing online authentication utilizing biometric data. U.S. Patent 9,911,146.
Tate, J., Beck, P., Ibarra, H.H., Kumaravel, S. and Miklas, L., 2018. Introduction to storage area
networks. IBM Redbooks.
Li, P., Chen, Z., Yang, L.T., Zhang, Q. and Deen, M.J., 2018. Deep convolutional computation
model for feature learning on big data in Internet of Things. IEEE Transactions on Industrial
Informatics, 14(2), pp.790-798.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





