Unilever's IT Infrastructure: Security Risks, Analysis and Policies
VerifiedAdded on 2023/06/12
|14
|5143
|101
Report
AI Summary
This report provides a comprehensive analysis of Unilever's IT infrastructure security, focusing on the proposed upgrade to cloud computing. It identifies issues with the existing blockchain-based infrastructure, such as lack of distributed computing, high energy consumption, immutable data, and security vulnerabilities. The report compares various technologies like IoT, cloud computing, content-centric networking, and software-defined networking, recommending cloud computing for its big data management capabilities. Critical assets needing protection, including computer hardware/software, spreadsheets, documents, images, and databases, are identified along with their respective vulnerabilities. The importance of risk analysis in IT projects is discussed, outlining the risk analysis process and the security risks posed by cloud computing, such as data loss, leakage, hijacking, and insecure interfaces. The report also touches upon Unilever's security policy, cryptographic approaches, and legal, social, and ethical issues related to the proposed IT infrastructure. Desklib offers similar past papers and solved assignments for students.

Computer Systems
Security
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1...............................................................................................................................................1
Profile of Unilever..................................................................................................................1
Existing IT infrastructure of Unilever....................................................................................1
Issues with the current infrastructure to justify the need for an infrastructure upgrade.........1
Compare technologies proposed to upgrade the Unilever's IT Infrastructure with justification
................................................................................................................................................2
Discuss critical assets (including information assets) that will need protection....................2
List vulnerabilities related to each of the identified assets.....................................................3
Task 2...............................................................................................................................................3
Importance of risk analysis phase in any IT project...............................................................3
Discuss what risk analysis process in relation to IT infrastructure projects entails...............4
Range security risks posed to Unilever while developing the technology of cloud computing
................................................................................................................................................5
Briefly discuss the proposed protection against those risks...................................................6
Conduct a risk analysis of Unilever based on the risks evaluated in Task 2b........................6
Task 3...............................................................................................................................................6
Key aspects of the security policy of Unilever.......................................................................6
How effective the policy is in protecting against security risks evaluated in Task 2b...........7
Cryptographic approach for Unilever with justification comparing with other approaches. .8
Use of cryptographic approach in Unilever's future IT infrastructure...................................9
Task 4...............................................................................................................................................9
Assessment of the security of proposed IT infrastructure using layered security approach. .9
Legal, social and ethical issues in relation to the security of proposed IT infrastructure....10
References......................................................................................................................................11
Task 1...............................................................................................................................................1
Profile of Unilever..................................................................................................................1
Existing IT infrastructure of Unilever....................................................................................1
Issues with the current infrastructure to justify the need for an infrastructure upgrade.........1
Compare technologies proposed to upgrade the Unilever's IT Infrastructure with justification
................................................................................................................................................2
Discuss critical assets (including information assets) that will need protection....................2
List vulnerabilities related to each of the identified assets.....................................................3
Task 2...............................................................................................................................................3
Importance of risk analysis phase in any IT project...............................................................3
Discuss what risk analysis process in relation to IT infrastructure projects entails...............4
Range security risks posed to Unilever while developing the technology of cloud computing
................................................................................................................................................5
Briefly discuss the proposed protection against those risks...................................................6
Conduct a risk analysis of Unilever based on the risks evaluated in Task 2b........................6
Task 3...............................................................................................................................................6
Key aspects of the security policy of Unilever.......................................................................6
How effective the policy is in protecting against security risks evaluated in Task 2b...........7
Cryptographic approach for Unilever with justification comparing with other approaches. .8
Use of cryptographic approach in Unilever's future IT infrastructure...................................9
Task 4...............................................................................................................................................9
Assessment of the security of proposed IT infrastructure using layered security approach. .9
Legal, social and ethical issues in relation to the security of proposed IT infrastructure....10
References......................................................................................................................................11

Task 1
Profile of Unilever
Unilever is one of the leading international company which deals with consumer goods
headquartered in the United Kingdom and established in 1929. It deals with the products and
services like beauty and personal care along with the food and refreshment and many more.
Existing IT infrastructure of Unilever
Information technology of Unilever is majorly in the supply chain management of the company
which uses the high level of blockchain Technology (Suradingura, 2019).
Issues with the current infrastructure to justify the need for an infrastructure upgrade
There are certain issues faced by the Unilever in its supply chain management using
block chain technology. Such as Lack in distributed computing system is one of the issue which
encourages the infrastructure upgrade. Blockching Technology hinders the company in the
distributed computing system which is the reason that company are highly restricted in sharing
the information anywhere. Consumption of huge energy is also one of the issues which
encourage the infrastructure upgrade. Blockchain Technology uses high energy of the
organisation in terms of electricity which results in a high cost and that is why it is considered
one of the major issue of blockchain Technology faced by Unilever. Immutable data is also an
another issue which encourages the infrastructure upgrade. Blocking Technology stores the data
which is immutable in nature. It means that it cannot get changed and modified easily because of
its high authentication and authorisation. Not a complete security is one of the issues which
encourage the infrastructure upgrade. Blockchain Technology does not provide the entire
security which means there is a still chance of getting data breaches and losses. Cost and
implementation difficulty is an another issue which encourages the infrastructure upgrade.
installing and updating the blockchain technology in the supply chain management within
Unilever has the huge cost and the complications in implementation as well. Lack of expertise
knowledge is also one of the issues which encourage the infrastructure upgrade. Unilever is
lacking the technical expertise who has the good knowledge of blockchain Technology and that
is why it's management and maintenance is becoming difficult for the company (Venkatesh,
Kang, Wang and Zhang, 2020).
1
Profile of Unilever
Unilever is one of the leading international company which deals with consumer goods
headquartered in the United Kingdom and established in 1929. It deals with the products and
services like beauty and personal care along with the food and refreshment and many more.
Existing IT infrastructure of Unilever
Information technology of Unilever is majorly in the supply chain management of the company
which uses the high level of blockchain Technology (Suradingura, 2019).
Issues with the current infrastructure to justify the need for an infrastructure upgrade
There are certain issues faced by the Unilever in its supply chain management using
block chain technology. Such as Lack in distributed computing system is one of the issue which
encourages the infrastructure upgrade. Blockching Technology hinders the company in the
distributed computing system which is the reason that company are highly restricted in sharing
the information anywhere. Consumption of huge energy is also one of the issues which
encourage the infrastructure upgrade. Blockchain Technology uses high energy of the
organisation in terms of electricity which results in a high cost and that is why it is considered
one of the major issue of blockchain Technology faced by Unilever. Immutable data is also an
another issue which encourages the infrastructure upgrade. Blocking Technology stores the data
which is immutable in nature. It means that it cannot get changed and modified easily because of
its high authentication and authorisation. Not a complete security is one of the issues which
encourage the infrastructure upgrade. Blockchain Technology does not provide the entire
security which means there is a still chance of getting data breaches and losses. Cost and
implementation difficulty is an another issue which encourages the infrastructure upgrade.
installing and updating the blockchain technology in the supply chain management within
Unilever has the huge cost and the complications in implementation as well. Lack of expertise
knowledge is also one of the issues which encourage the infrastructure upgrade. Unilever is
lacking the technical expertise who has the good knowledge of blockchain Technology and that
is why it's management and maintenance is becoming difficult for the company (Venkatesh,
Kang, Wang and Zhang, 2020).
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
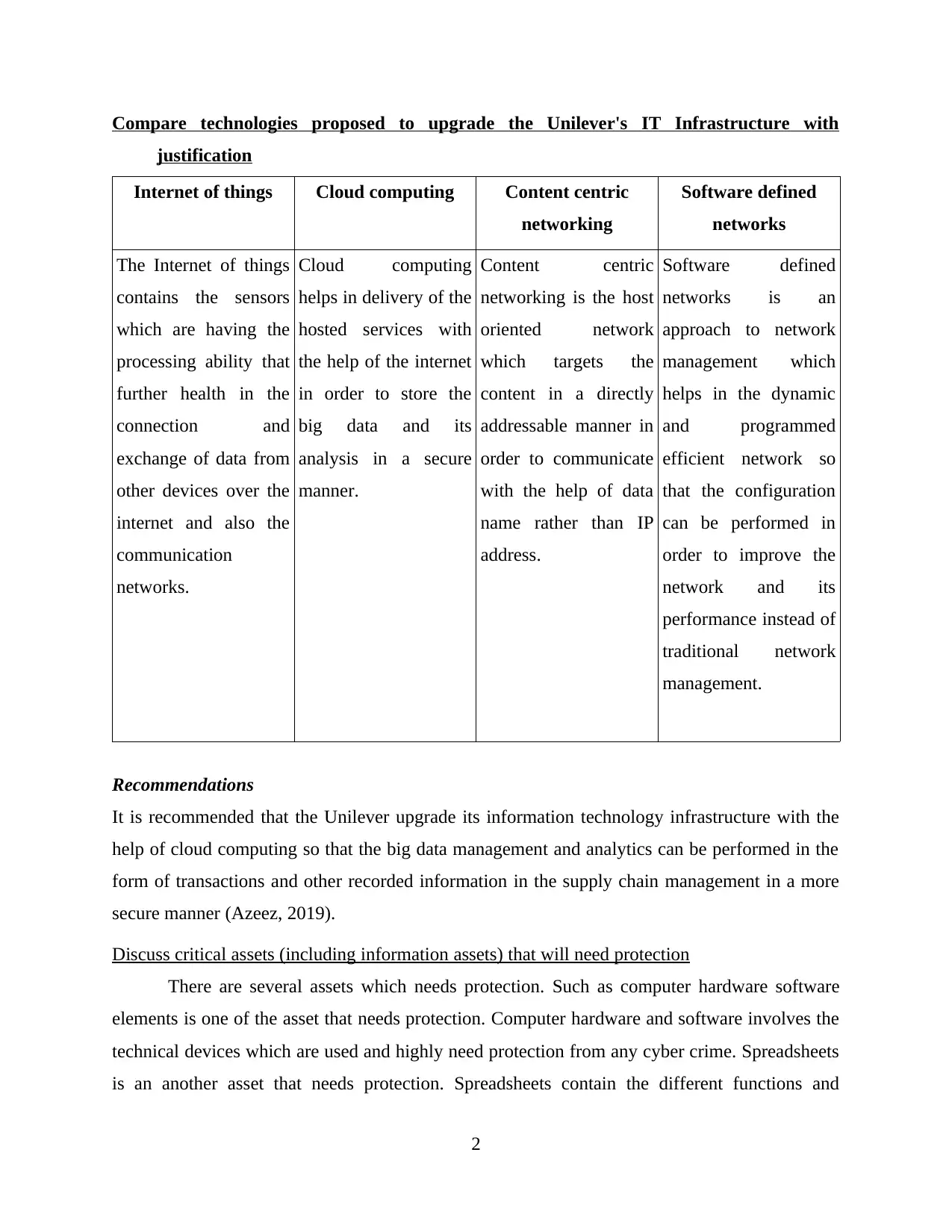
Compare technologies proposed to upgrade the Unilever's IT Infrastructure with
justification
Internet of things Cloud computing Content centric
networking
Software defined
networks
The Internet of things
contains the sensors
which are having the
processing ability that
further health in the
connection and
exchange of data from
other devices over the
internet and also the
communication
networks.
Cloud computing
helps in delivery of the
hosted services with
the help of the internet
in order to store the
big data and its
analysis in a secure
manner.
Content centric
networking is the host
oriented network
which targets the
content in a directly
addressable manner in
order to communicate
with the help of data
name rather than IP
address.
Software defined
networks is an
approach to network
management which
helps in the dynamic
and programmed
efficient network so
that the configuration
can be performed in
order to improve the
network and its
performance instead of
traditional network
management.
Recommendations
It is recommended that the Unilever upgrade its information technology infrastructure with the
help of cloud computing so that the big data management and analytics can be performed in the
form of transactions and other recorded information in the supply chain management in a more
secure manner (Azeez, 2019).
Discuss critical assets (including information assets) that will need protection
There are several assets which needs protection. Such as computer hardware software
elements is one of the asset that needs protection. Computer hardware and software involves the
technical devices which are used and highly need protection from any cyber crime. Spreadsheets
is an another asset that needs protection. Spreadsheets contain the different functions and
2
justification
Internet of things Cloud computing Content centric
networking
Software defined
networks
The Internet of things
contains the sensors
which are having the
processing ability that
further health in the
connection and
exchange of data from
other devices over the
internet and also the
communication
networks.
Cloud computing
helps in delivery of the
hosted services with
the help of the internet
in order to store the
big data and its
analysis in a secure
manner.
Content centric
networking is the host
oriented network
which targets the
content in a directly
addressable manner in
order to communicate
with the help of data
name rather than IP
address.
Software defined
networks is an
approach to network
management which
helps in the dynamic
and programmed
efficient network so
that the configuration
can be performed in
order to improve the
network and its
performance instead of
traditional network
management.
Recommendations
It is recommended that the Unilever upgrade its information technology infrastructure with the
help of cloud computing so that the big data management and analytics can be performed in the
form of transactions and other recorded information in the supply chain management in a more
secure manner (Azeez, 2019).
Discuss critical assets (including information assets) that will need protection
There are several assets which needs protection. Such as computer hardware software
elements is one of the asset that needs protection. Computer hardware and software involves the
technical devices which are used and highly need protection from any cyber crime. Spreadsheets
is an another asset that needs protection. Spreadsheets contain the different functions and
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

calculations of large data and that is why it is required to get protected. A document is also one
of the assets that need protection. Any form of document in the organisation contains private
information in a confidential manner so that it cannot be leaked out. Images is also an another
asset that needs protection. Images of business models and flowcharts are important for the
company and that is why it is needed to get protected. Databases is an another asset that needs
protection. Databases contain the large number of records which are required to be managed in
order to process the data and extract the information and therefore for its protection is required
(Luntovskyy and Shubyn, 2020).
List vulnerabilities related to each of the identified assets
Vulnerability related to Computer hardware and software elements is such that. Computer
software and hardware devices can get crashed if any viruses enter and that is why it is
considered a vulnerability to this type of asset. Vulnerability related to spreadsheets is such that.
Spreadsheet contains the data which contains the information regarding finances of the company
which is on the priority for the hackers to hack. Vulnerability related to documents is such that.
Documents contain the important decision making planning and processing and that is why it is
vulnerable to get hacked. Vulnerability related to images is such that. Images contain the
business model which is to be planned in the future and that is why it is considered under the
vulnerability asset because it is private in nature and the hackers have an eye on such information
of the company. Vulnerability related to databases is such that. Database was contains the
personal credentials and information of the customers and therefore it is important to get saved.
Hackers hack such databases in return for money or for some personal reasons (Martin, 2020).
Task 2
Importance of risk analysis phase in any IT project
Identify security vulnerabilities is one of the importance of risk analysis. Risk analysis
helps in identifying the different types of vulnerability which is related to the security of
information Technology projects which means that recognition of the security helps in the proper
mitigation and future considerations of the company. Determining new security requirements is
an another importance of risk analysis. Risk analysis supports in identifying the new security
requirements which helps in better security measures for the Big Data analytics and for the
emerging technology which has been adopted by the organisation. Justifying spending is also one
3
of the assets that need protection. Any form of document in the organisation contains private
information in a confidential manner so that it cannot be leaked out. Images is also an another
asset that needs protection. Images of business models and flowcharts are important for the
company and that is why it is needed to get protected. Databases is an another asset that needs
protection. Databases contain the large number of records which are required to be managed in
order to process the data and extract the information and therefore for its protection is required
(Luntovskyy and Shubyn, 2020).
List vulnerabilities related to each of the identified assets
Vulnerability related to Computer hardware and software elements is such that. Computer
software and hardware devices can get crashed if any viruses enter and that is why it is
considered a vulnerability to this type of asset. Vulnerability related to spreadsheets is such that.
Spreadsheet contains the data which contains the information regarding finances of the company
which is on the priority for the hackers to hack. Vulnerability related to documents is such that.
Documents contain the important decision making planning and processing and that is why it is
vulnerable to get hacked. Vulnerability related to images is such that. Images contain the
business model which is to be planned in the future and that is why it is considered under the
vulnerability asset because it is private in nature and the hackers have an eye on such information
of the company. Vulnerability related to databases is such that. Database was contains the
personal credentials and information of the customers and therefore it is important to get saved.
Hackers hack such databases in return for money or for some personal reasons (Martin, 2020).
Task 2
Importance of risk analysis phase in any IT project
Identify security vulnerabilities is one of the importance of risk analysis. Risk analysis
helps in identifying the different types of vulnerability which is related to the security of
information Technology projects which means that recognition of the security helps in the proper
mitigation and future considerations of the company. Determining new security requirements is
an another importance of risk analysis. Risk analysis supports in identifying the new security
requirements which helps in better security measures for the Big Data analytics and for the
emerging technology which has been adopted by the organisation. Justifying spending is also one
3

of the importances of risk analysis. Risk analysis provides the worth of spending on the security
measures which justify the efficiency in cost and time investment of the company in the security
analysis within the organisation of information technology projects (Lin, 2019). Making smart
purchases is also an another importance of risk analysis. Risk analysis supports smart purchases
of different technical devices so that it can be secured from the initial point to the end with
proper maintenance and updates of the security systems which are installed in order to support
the other hardware and software devices of the company. Improving planning is one of the
importances of risk analysis. Risk analysis helps the company to improve the planning process
from identifying the goals and objectives to the implementation of it which facilitates the
company in strategic decision making as well. Documenting due diligence is an another
importance of risk analysis. Boosting productivity is also one of the importances of risk analysis.
Risk Analysis helps in documenting the due diligence which further helps the organisation in
proper documentation process within the industry and maintain the stability and reputation in the
marketplace in order to have the better mitigation analysis. Risk analysis boosts the productivity
of the company by following the systematic procedure of identifying the risk and prioritising
them so that the solutions can be drawn out accordingly along with the impact on the company's
technical resources. Helping make budget choices is also an another importance of risk analysis.
Risk analysis supports making the budgets for further investment in the technology so that it can
be identified which software and hardware is required and how much security it needed to
safeguard the big data contained in it (Xu, Lee, Barth and Richey, 2021).
Discuss what risk analysis process in relation to IT infrastructure projects entails
Identifying the risks is the first stage of the risk analysis process. Identification of the
business is necessary so that the further decisions of mitigation can be drawn out by the
company. Deciding who might be harmed and how is the second stage of the risk analysis
process. Decision making in regards with the harmful actions and how they can impact the
technical resources is important for better choosing of the alternatives and deciding at which one
is appropriate for the solutions. Evaluating the risks and taking action to prevent them is the third
stage of the risk analysis process. After making the decision it is important to evaluate the
several risks and identify the proper actions in order to prevent them for better for the analysis
and mitigation of the risk in a potential manner. Recording the findings is the fourth stage of the
risk analysis process. After choosing the appropriate mitigation technique it is important to
4
measures which justify the efficiency in cost and time investment of the company in the security
analysis within the organisation of information technology projects (Lin, 2019). Making smart
purchases is also an another importance of risk analysis. Risk analysis supports smart purchases
of different technical devices so that it can be secured from the initial point to the end with
proper maintenance and updates of the security systems which are installed in order to support
the other hardware and software devices of the company. Improving planning is one of the
importances of risk analysis. Risk analysis helps the company to improve the planning process
from identifying the goals and objectives to the implementation of it which facilitates the
company in strategic decision making as well. Documenting due diligence is an another
importance of risk analysis. Boosting productivity is also one of the importances of risk analysis.
Risk Analysis helps in documenting the due diligence which further helps the organisation in
proper documentation process within the industry and maintain the stability and reputation in the
marketplace in order to have the better mitigation analysis. Risk analysis boosts the productivity
of the company by following the systematic procedure of identifying the risk and prioritising
them so that the solutions can be drawn out accordingly along with the impact on the company's
technical resources. Helping make budget choices is also an another importance of risk analysis.
Risk analysis supports making the budgets for further investment in the technology so that it can
be identified which software and hardware is required and how much security it needed to
safeguard the big data contained in it (Xu, Lee, Barth and Richey, 2021).
Discuss what risk analysis process in relation to IT infrastructure projects entails
Identifying the risks is the first stage of the risk analysis process. Identification of the
business is necessary so that the further decisions of mitigation can be drawn out by the
company. Deciding who might be harmed and how is the second stage of the risk analysis
process. Decision making in regards with the harmful actions and how they can impact the
technical resources is important for better choosing of the alternatives and deciding at which one
is appropriate for the solutions. Evaluating the risks and taking action to prevent them is the third
stage of the risk analysis process. After making the decision it is important to evaluate the
several risks and identify the proper actions in order to prevent them for better for the analysis
and mitigation of the risk in a potential manner. Recording the findings is the fourth stage of the
risk analysis process. After choosing the appropriate mitigation technique it is important to
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

record all the findings so that the outcomes can be used in the further studies of risk associated
with the company technical resources. Reviewing the risk assessment is the fifth stage of the risk
analysis process. At the end it is important to conduct the risk assessment and monitor all the
risks along with the mitigations so that it can help to fight against the current situation and also
the future project of information Technology (Purba, 2021).
Range security risks posed to Unilever while developing the technology of cloud computing
Data loss or theft is one of the security risks posed to Unilever while developing the
technology of cloud computing. Loss of the data which is private and important for the company
results in the bad reputation of the organisation in the market place which leads to the large
losses and also even to the shutting down of the company as well. Data leakage is an another
security risks posed to Unilever while developing the technology of cloud computing. Data
leakage is done by the hacker who has a personal problem with the organisation or wants some
money in return in order to take revenge from the organisation. Account or service hijacking is
also one of the security risks posed to Unilever while developing the technology of cloud
computing. Organizations that provide the services to the customers are usually hijacked by the
hacker which results in poor performance of the company and bad relationship with the
customers with poor customer loyalty towards the brand. Insecure interfaces and APIs is also an
another security risks posed to Unilever while developing the technology of cloud computing.
There are interpieces and application programming interfaces which are insecure in cloud
computing which must be used by the organisation while having the security concerns so that
such interfaces cannot affect the proper functioning of the organisation. Denial of service attacks
is one of the security risks posed to Unilever while developing the technology of cloud
computing. There are attacks which deny the service from the organisation to the customers
which are usually performed by the hackers and the motive behind this is that the hackers wants
to take revenge for some personal things and need some money in order to return back the access
control. Technology vulnerabilities on shared environments is an another security risks posed to
Unilever while developing the technology of cloud computing. Adopting technology is highly
vulnerable while sharing it in different environments because it needs the medium and
networking which is insecure and unless the proper firewall is being installed by the organisation
in order to properly share the information among the different environments (Widyastuti, Said,
Siswono and Firmansyah, 2019).
5
with the company technical resources. Reviewing the risk assessment is the fifth stage of the risk
analysis process. At the end it is important to conduct the risk assessment and monitor all the
risks along with the mitigations so that it can help to fight against the current situation and also
the future project of information Technology (Purba, 2021).
Range security risks posed to Unilever while developing the technology of cloud computing
Data loss or theft is one of the security risks posed to Unilever while developing the
technology of cloud computing. Loss of the data which is private and important for the company
results in the bad reputation of the organisation in the market place which leads to the large
losses and also even to the shutting down of the company as well. Data leakage is an another
security risks posed to Unilever while developing the technology of cloud computing. Data
leakage is done by the hacker who has a personal problem with the organisation or wants some
money in return in order to take revenge from the organisation. Account or service hijacking is
also one of the security risks posed to Unilever while developing the technology of cloud
computing. Organizations that provide the services to the customers are usually hijacked by the
hacker which results in poor performance of the company and bad relationship with the
customers with poor customer loyalty towards the brand. Insecure interfaces and APIs is also an
another security risks posed to Unilever while developing the technology of cloud computing.
There are interpieces and application programming interfaces which are insecure in cloud
computing which must be used by the organisation while having the security concerns so that
such interfaces cannot affect the proper functioning of the organisation. Denial of service attacks
is one of the security risks posed to Unilever while developing the technology of cloud
computing. There are attacks which deny the service from the organisation to the customers
which are usually performed by the hackers and the motive behind this is that the hackers wants
to take revenge for some personal things and need some money in order to return back the access
control. Technology vulnerabilities on shared environments is an another security risks posed to
Unilever while developing the technology of cloud computing. Adopting technology is highly
vulnerable while sharing it in different environments because it needs the medium and
networking which is insecure and unless the proper firewall is being installed by the organisation
in order to properly share the information among the different environments (Widyastuti, Said,
Siswono and Firmansyah, 2019).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Briefly discuss the proposed protection against those risks
Cybersecurity is one of the proposed protections against the risk. It is important for the
organisation to implement and install the different types of cyber security in the company so that
the technical resources can get proper protection of big data management and other important
resources. Regulatory compliance is an another proposed protection against the risk. Company
must regulate its ethical and legal practices of managing the technology within the organisation
because regulating such compliances helps in the strong security concerns which helps in
mitigating the risk. Backup and recovery is also one of the proposed protections against the risk.
It is important for the organisation to backup the important and confidential data so that it can be
recovered even after losses. Instituting an end to end cyber risk framework is also an another
proposed protection against the risk. Organisation must formulate the framework which must be
instituting an end to end cyber risk. It means that in depth identification of risk and root cause
solution of it. Platform support is one of the proposed protections against the risk. The
organisation must have the different types of platform which must be compatible for the different
types of security installed in the company for strong risk solutions and every stage of the risk
analysis. Vendor management is an another proposed protection against the risk. There are
different vendors in cloud computing which are to be managed and respected to use services who
are unknown and unauthorised so that the authentication and authorisation can be maintained in
cloud computing services (Vulandari, 2020).
Conduct a risk analysis of Unilever based on the risks evaluated in Task 2b
If Unilever wants to update the information technology infrastructure then they have to install the
cloud computing technique. Therefore there are various risks associated with it which are retailed
in the previous section and also the solutions which can mitigate such as cloud computing
specified in the previous section (Eijkelenboom and Nieuwesteeg, 2021).
Task 3
Key aspects of the security policy of Unilever
Password management is one of the security policy of Unilever. Unilever has various
databases and Private data which are confidential in nature and that is why they have created the
policy of password management in which strong passwords are kept so that it can safeguard it
from any password cracked device. Educating employees regarding using the technology is an
6
Cybersecurity is one of the proposed protections against the risk. It is important for the
organisation to implement and install the different types of cyber security in the company so that
the technical resources can get proper protection of big data management and other important
resources. Regulatory compliance is an another proposed protection against the risk. Company
must regulate its ethical and legal practices of managing the technology within the organisation
because regulating such compliances helps in the strong security concerns which helps in
mitigating the risk. Backup and recovery is also one of the proposed protections against the risk.
It is important for the organisation to backup the important and confidential data so that it can be
recovered even after losses. Instituting an end to end cyber risk framework is also an another
proposed protection against the risk. Organisation must formulate the framework which must be
instituting an end to end cyber risk. It means that in depth identification of risk and root cause
solution of it. Platform support is one of the proposed protections against the risk. The
organisation must have the different types of platform which must be compatible for the different
types of security installed in the company for strong risk solutions and every stage of the risk
analysis. Vendor management is an another proposed protection against the risk. There are
different vendors in cloud computing which are to be managed and respected to use services who
are unknown and unauthorised so that the authentication and authorisation can be maintained in
cloud computing services (Vulandari, 2020).
Conduct a risk analysis of Unilever based on the risks evaluated in Task 2b
If Unilever wants to update the information technology infrastructure then they have to install the
cloud computing technique. Therefore there are various risks associated with it which are retailed
in the previous section and also the solutions which can mitigate such as cloud computing
specified in the previous section (Eijkelenboom and Nieuwesteeg, 2021).
Task 3
Key aspects of the security policy of Unilever
Password management is one of the security policy of Unilever. Unilever has various
databases and Private data which are confidential in nature and that is why they have created the
policy of password management in which strong passwords are kept so that it can safeguard it
from any password cracked device. Educating employees regarding using the technology is an
6

another security policy of Unilever. Unilever specially conducts the training and development
sessions for the employees so that they can use the technical resources in an ethical and legal
manner which further helps in avoiding the cyber attacks. Access control is also one of the
security policies of Unilever. Unilever has implemented the access control tools in which only
the person who is authorised can only access the data and information for better security
concerns so that it cannot be leaked or lost for any of the reasons. Encryption and decryption is
also an another security policy of Unilever. Unilever also uses the encryption messages and
decrypted messages for transmitting from one place to another so that any medium in between
cannot recognise what the message means and therefore it transfers in a safe manner.
Authentication and authorization is one of the security policies of Unilever. Unilever also uses
the methods of authentication and authorisation of the private data and Big Data analytics so that
only the people who are authenticated and authorised towards theta can only have the access to
open it and read it and modify it. Updating technical devices frequently is an another security
policy of Unilever. Unilever frequently updates its technical resources so that the software and
hardware can be secured for a long term without any viruses or crash of the resources (Li,
Mehandjiev, James, Shahgholian and Allen, 2019).
How effective the policy is in protecting against security risks evaluated in Task 2b
Keeping away from any penalties and fines is one of the effectiveness of policy in
protecting against security risks evaluated. Unilever is benefited by adopting the risk
management policies because it helps in keeping away any of the penalties or fines which are
concerned with the ethics and laws. Security of reputation of doing business is an another
effectiveness of policy in protecting against security risks evaluated. Such policies help the
company in maintaining the good deputation in the marketplace and the strong security of
technical devices because it helps in safeguarding the data which maintain stability in the
industry. Strengthen the skills in data protection is also one of the effectiveness of policy in
protecting against security risks evaluated. These are the policies which help the employees to
polish their skills in terms of data protection so that any risk occurring on an instant basis can
easily be medicated by using those and capabilities at that point of time. Strengthen the culture of
the business is also an another effectiveness of policy in protecting against security risks
evaluated. These are the policies which also help in maintaining the positive culture of the
business because educating the employees in terms of maintenance of the security helps in
7
sessions for the employees so that they can use the technical resources in an ethical and legal
manner which further helps in avoiding the cyber attacks. Access control is also one of the
security policies of Unilever. Unilever has implemented the access control tools in which only
the person who is authorised can only access the data and information for better security
concerns so that it cannot be leaked or lost for any of the reasons. Encryption and decryption is
also an another security policy of Unilever. Unilever also uses the encryption messages and
decrypted messages for transmitting from one place to another so that any medium in between
cannot recognise what the message means and therefore it transfers in a safe manner.
Authentication and authorization is one of the security policies of Unilever. Unilever also uses
the methods of authentication and authorisation of the private data and Big Data analytics so that
only the people who are authenticated and authorised towards theta can only have the access to
open it and read it and modify it. Updating technical devices frequently is an another security
policy of Unilever. Unilever frequently updates its technical resources so that the software and
hardware can be secured for a long term without any viruses or crash of the resources (Li,
Mehandjiev, James, Shahgholian and Allen, 2019).
How effective the policy is in protecting against security risks evaluated in Task 2b
Keeping away from any penalties and fines is one of the effectiveness of policy in
protecting against security risks evaluated. Unilever is benefited by adopting the risk
management policies because it helps in keeping away any of the penalties or fines which are
concerned with the ethics and laws. Security of reputation of doing business is an another
effectiveness of policy in protecting against security risks evaluated. Such policies help the
company in maintaining the good deputation in the marketplace and the strong security of
technical devices because it helps in safeguarding the data which maintain stability in the
industry. Strengthen the skills in data protection is also one of the effectiveness of policy in
protecting against security risks evaluated. These are the policies which help the employees to
polish their skills in terms of data protection so that any risk occurring on an instant basis can
easily be medicated by using those and capabilities at that point of time. Strengthen the culture of
the business is also an another effectiveness of policy in protecting against security risks
evaluated. These are the policies which also help in maintaining the positive culture of the
business because educating the employees in terms of maintenance of the security helps in
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

maintaining the positive working culture while protecting the data on a large basis. Promotion of
transparency and access controls is one of the effectiveness of policy in protecting against
security risks evaluated. policies adopted by Unilever promotes the access control of the big data
management and also the transparency of the information which further helps in converting the
raw data to the relevant information that helps the organisation in decision making. Boost
productivity of the business is an another effectiveness of policy in protecting against security
risks evaluated. Adopting such policies in Unilever helps the company in boosting its
productivity because of the positive culture helps in motivating the employees and also the good
performance due to the protected data without any cyber attack (Bosamia and Patel, 2020).
Cryptographic approach for Unilever with justification comparing with other approaches
Simple Codes is one of the approaches of cryptography. There are personal which are
formulated by the company itself to transfer data in some other form to the receiver which can
only be understood by the sender and receiver of the information. Symmetric encryption is an
another approach of cryptography. This type of encryption has the same word codings from the
initial and from the end of the entire code word which can only be understood by the receiver
and no one else so that any mediator cannot misuse such important information. Asymmetric
encryption is also one of the approaches of cryptography. This is a type of encryption which is
not same from the initial and from the end and are entirely different in order to confuse any type
of mediator who is waiting for the private information and wants to steal it which cannot be
possible due to asymmetric encryption. Steganography is also an another approach of
cryptography. This type of cryptographic approach helps the sender to hide their message
between the different texts so that only the receiver can understand what is to be delivered and
conveyed from the sender. Hashing is an another approach of cryptography of cryptography.
This is a type of cryptographic approach in which the message is written in the form of symbols
which only the receiver can understand and the reply by the receiver is also in the form of
symbols and other forms of text which can only be interested by the people who are actually
communicating.
Recommendations
Symmetric encryption is recommended to Unilever because it is easy to use and has a strong
security. Some of its effectiveness and uses are mentioned in the next action (Arif, Hashim and
Sanudin, 2019).
8
transparency and access controls is one of the effectiveness of policy in protecting against
security risks evaluated. policies adopted by Unilever promotes the access control of the big data
management and also the transparency of the information which further helps in converting the
raw data to the relevant information that helps the organisation in decision making. Boost
productivity of the business is an another effectiveness of policy in protecting against security
risks evaluated. Adopting such policies in Unilever helps the company in boosting its
productivity because of the positive culture helps in motivating the employees and also the good
performance due to the protected data without any cyber attack (Bosamia and Patel, 2020).
Cryptographic approach for Unilever with justification comparing with other approaches
Simple Codes is one of the approaches of cryptography. There are personal which are
formulated by the company itself to transfer data in some other form to the receiver which can
only be understood by the sender and receiver of the information. Symmetric encryption is an
another approach of cryptography. This type of encryption has the same word codings from the
initial and from the end of the entire code word which can only be understood by the receiver
and no one else so that any mediator cannot misuse such important information. Asymmetric
encryption is also one of the approaches of cryptography. This is a type of encryption which is
not same from the initial and from the end and are entirely different in order to confuse any type
of mediator who is waiting for the private information and wants to steal it which cannot be
possible due to asymmetric encryption. Steganography is also an another approach of
cryptography. This type of cryptographic approach helps the sender to hide their message
between the different texts so that only the receiver can understand what is to be delivered and
conveyed from the sender. Hashing is an another approach of cryptography of cryptography.
This is a type of cryptographic approach in which the message is written in the form of symbols
which only the receiver can understand and the reply by the receiver is also in the form of
symbols and other forms of text which can only be interested by the people who are actually
communicating.
Recommendations
Symmetric encryption is recommended to Unilever because it is easy to use and has a strong
security. Some of its effectiveness and uses are mentioned in the next action (Arif, Hashim and
Sanudin, 2019).
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Use of cryptographic approach in Unilever's future IT infrastructure
Simple to use is one of the uses of cryptographic approach of symmetric encryption in
Unilever's future IT infrastructure. This is a type of cryptographic approach which is easy to use
when it is sent from the sender and even when it is received from the receiver and the reply is
also in the form of symmetric encryption for better security concerns. Encrypt and decrypt own
files is an another use of cryptographic approach of symmetric encryption in Unilever's future IT
infrastructure (Loideain and Adams, 2020). This type of approach helps in encrypting and
decrypting the own files without any difficulty and the complications. Faster process is also one
of the uses of cryptographic approach of symmetric encryption in Unilever's future IT
infrastructure. It facilitates Unilever in the faster process of communicating and proper
interaction so that the privacy and confidentiality of the information can be maintained without
any hacking or breaching of the data. Uses less computer resources is also an another use of
cryptographic approach of symmetric encryption in Unilever's future IT infrastructure. This type
of encryption helps Unilever in using the less resources of computers which ultimately save the
energy and cost of the company on a large basis (Malik, 2019).
Task 4
Assessment of the security of proposed IT infrastructure using layered security approach
Layout security approach is defined as the security of the network in the deployment of more
than one security controls so that the protection from the most vulnerable areas of the technology
can be made against any breeches or any cyber attacks. Unilever can propose the information
technology infrastructure in terms of security while developing the information technology
upgrade in regards with cloud computing (Sun and Isa, 2020). It is important to secure the
proposed information Technology infrastructure with the help of email security and encryption
of the information passed from one end to another. Moreover security is also associated with the
web and content filtering against any end or end user protection. It is also having the DNS
filtering and data encryption with allergy which improves the security of mobile applications and
the desktop as well. It also includes the backup and patch management which can be adopted by
the Unilever for better assessment of security of proposed information Technology infrastructure
with the help of layout security approach (Kuznetsov, Reshetnikov, Silvestrov and Pobyvaev,
2021).
9
Simple to use is one of the uses of cryptographic approach of symmetric encryption in
Unilever's future IT infrastructure. This is a type of cryptographic approach which is easy to use
when it is sent from the sender and even when it is received from the receiver and the reply is
also in the form of symmetric encryption for better security concerns. Encrypt and decrypt own
files is an another use of cryptographic approach of symmetric encryption in Unilever's future IT
infrastructure (Loideain and Adams, 2020). This type of approach helps in encrypting and
decrypting the own files without any difficulty and the complications. Faster process is also one
of the uses of cryptographic approach of symmetric encryption in Unilever's future IT
infrastructure. It facilitates Unilever in the faster process of communicating and proper
interaction so that the privacy and confidentiality of the information can be maintained without
any hacking or breaching of the data. Uses less computer resources is also an another use of
cryptographic approach of symmetric encryption in Unilever's future IT infrastructure. This type
of encryption helps Unilever in using the less resources of computers which ultimately save the
energy and cost of the company on a large basis (Malik, 2019).
Task 4
Assessment of the security of proposed IT infrastructure using layered security approach
Layout security approach is defined as the security of the network in the deployment of more
than one security controls so that the protection from the most vulnerable areas of the technology
can be made against any breeches or any cyber attacks. Unilever can propose the information
technology infrastructure in terms of security while developing the information technology
upgrade in regards with cloud computing (Sun and Isa, 2020). It is important to secure the
proposed information Technology infrastructure with the help of email security and encryption
of the information passed from one end to another. Moreover security is also associated with the
web and content filtering against any end or end user protection. It is also having the DNS
filtering and data encryption with allergy which improves the security of mobile applications and
the desktop as well. It also includes the backup and patch management which can be adopted by
the Unilever for better assessment of security of proposed information Technology infrastructure
with the help of layout security approach (Kuznetsov, Reshetnikov, Silvestrov and Pobyvaev,
2021).
9

Legal, social and ethical issues in relation to the security of proposed IT infrastructure
There are various legal and social issues along with the ethical issues in relation to the
security of proposed information Technology infrastructure in Unilever. Misusing of personal
information that is the credentials of the customer is one of the most major ethical issues which
can be faced by the organisation in the near future. It can also face the lack of oversight and
acceptance of the high responsibility in managing the technical resources which ultimately reside
in the ethical and social issue in the company which is also somewhat related to the legal issues
as well. Unilever uses artificial intelligence in its basic functioning in order to identify the
customer demands for better supply chain management (Atiku and Boateng, 2020). Artificial
intelligence involved in cloud computing results in legal issues in which the hackers break laws
in order to steal the data for their own personal use. Unilever also uses autonomous Technology
which are also part of ethical issues. It is important to use the data and resources in a moral
manner so that the responsibility of adoption of the destructive Technology is removed from the
organisation. some of the issues which are also related to the outsourcing of the information
system which is associated with the patent and copyright along with the trademarks and piracy
act which are important for the company to take care while outsourcing the information system
from any other unknown vendors. These are some of the legal and social issues along with the
ethical which the organisation can while having the security proposed of information technology
infrastructure (Padmanabhan, Pant and Raghu, 2020).
10
There are various legal and social issues along with the ethical issues in relation to the
security of proposed information Technology infrastructure in Unilever. Misusing of personal
information that is the credentials of the customer is one of the most major ethical issues which
can be faced by the organisation in the near future. It can also face the lack of oversight and
acceptance of the high responsibility in managing the technical resources which ultimately reside
in the ethical and social issue in the company which is also somewhat related to the legal issues
as well. Unilever uses artificial intelligence in its basic functioning in order to identify the
customer demands for better supply chain management (Atiku and Boateng, 2020). Artificial
intelligence involved in cloud computing results in legal issues in which the hackers break laws
in order to steal the data for their own personal use. Unilever also uses autonomous Technology
which are also part of ethical issues. It is important to use the data and resources in a moral
manner so that the responsibility of adoption of the destructive Technology is removed from the
organisation. some of the issues which are also related to the outsourcing of the information
system which is associated with the patent and copyright along with the trademarks and piracy
act which are important for the company to take care while outsourcing the information system
from any other unknown vendors. These are some of the legal and social issues along with the
ethical which the organisation can while having the security proposed of information technology
infrastructure (Padmanabhan, Pant and Raghu, 2020).
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





