IT Infrastructure Report: Cosboa Sydney Branch Network Design
VerifiedAdded on 2023/02/01
|17
|3811
|54
Report
AI Summary
This report provides a comprehensive IT infrastructure proposal for Cosboa, a small business development organization planning to open a new branch in Sydney. The report begins with an analysis of the building's floor plan and the number of rooms to determine the geographical scope and logical network design, including IP addressing and subnet masking. It then explores cloud computing solutions, specifically Amazon AWS and Google Drive, for hosting application servers, email services, and data storage. The report also discusses various virtualization techniques, such as network, application, and desktop virtualization, and their application in supporting cloud platforms. Finally, it examines how cloud computing can support dynamic scaling of the organization's applications. The report offers detailed network diagrams, IP address allocation tables, and analyses of cloud providers, providing a practical guide to building a robust and scalable IT infrastructure.

Running head: IT INFRASTRUCTURE
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT INFRASTRUCTURE
Table of Contents
Introduction................................................................................................................................2
1. IT infrastructure proposal.......................................................................................................2
1.1. Geographical scope.........................................................................................................2
1.2. Logical Design of Sydney Branch network....................................................................3
1.3. IP address with Subnet mask...........................................................................................4
2. Hosting application server using virtualization and cloud computing...................................8
2.1. Analysis of cloud providers............................................................................................8
2.2. Techniques for service virtualization..............................................................................9
2.3. Dynamic scaling support...............................................................................................11
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14
IT INFRASTRUCTURE
Table of Contents
Introduction................................................................................................................................2
1. IT infrastructure proposal.......................................................................................................2
1.1. Geographical scope.........................................................................................................2
1.2. Logical Design of Sydney Branch network....................................................................3
1.3. IP address with Subnet mask...........................................................................................4
2. Hosting application server using virtualization and cloud computing...................................8
2.1. Analysis of cloud providers............................................................................................8
2.2. Techniques for service virtualization..............................................................................9
2.3. Dynamic scaling support...............................................................................................11
Conclusion................................................................................................................................13
Bibliography.............................................................................................................................14

2
IT INFRASTRUCTURE
Introduction
The report is prepared for www.cosboa.org.au which was founded in the year 1977
and the goal of the organization is promotion and supporting small business development in
Australia. The company engages the members for providing them opportunity of influencing
outcome of the business. An essential input is provided by the members of the company for
ensuring that the representation quality is met. The company helps the small business
organization to promote their interest with changing their policy and reforming the
regulatory. It increases the awareness and help them to understand the role of small business
in Australia. For the development of the report it is assumed that the organization would open
a new branch in a new building at Sydney city centre.
1. IT infrastructure proposal
For the development of the network infrastructure an analysis is made on the floor
plan of the building and number of rooms per floor. The data points that are needed to be
available per room is analysed for the development of IP addressing plan and creating a
logical design of the network. The geographical scope of the network is discussed with the
use of the diagram and explanation is provided for the network device used as the backbone
for connecting the network with the small business organizational network. In the second part
of the report a discussion is provided on the organisation that provides cloud service and can
be used by the organization for hosting email and web server for the organization. The
techniques that can be used for virtualization of the service and support the implementation of
cloud platform is also given in the report. The support of cloud computing for supporting
dynamic scaling of the organisation application is also discussed in the report.
1.1. Geographical scope
IT INFRASTRUCTURE
Introduction
The report is prepared for www.cosboa.org.au which was founded in the year 1977
and the goal of the organization is promotion and supporting small business development in
Australia. The company engages the members for providing them opportunity of influencing
outcome of the business. An essential input is provided by the members of the company for
ensuring that the representation quality is met. The company helps the small business
organization to promote their interest with changing their policy and reforming the
regulatory. It increases the awareness and help them to understand the role of small business
in Australia. For the development of the report it is assumed that the organization would open
a new branch in a new building at Sydney city centre.
1. IT infrastructure proposal
For the development of the network infrastructure an analysis is made on the floor
plan of the building and number of rooms per floor. The data points that are needed to be
available per room is analysed for the development of IP addressing plan and creating a
logical design of the network. The geographical scope of the network is discussed with the
use of the diagram and explanation is provided for the network device used as the backbone
for connecting the network with the small business organizational network. In the second part
of the report a discussion is provided on the organisation that provides cloud service and can
be used by the organization for hosting email and web server for the organization. The
techniques that can be used for virtualization of the service and support the implementation of
cloud platform is also given in the report. The support of cloud computing for supporting
dynamic scaling of the organisation application is also discussed in the report.
1.1. Geographical scope
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT INFRASTRUCTURE
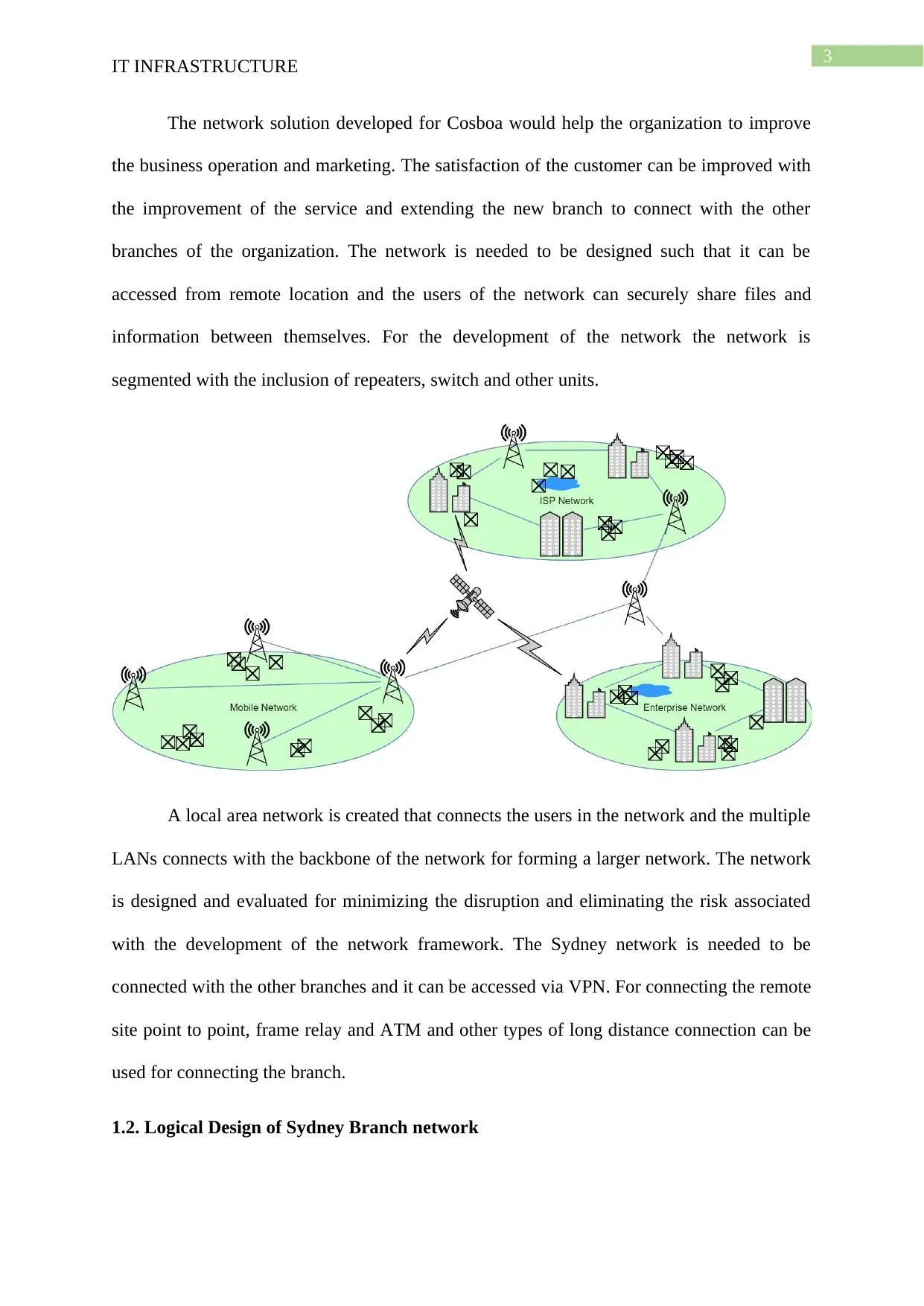
The network solution developed for Cosboa would help the organization to improve
the business operation and marketing. The satisfaction of the customer can be improved with
the improvement of the service and extending the new branch to connect with the other
branches of the organization. The network is needed to be designed such that it can be
accessed from remote location and the users of the network can securely share files and
information between themselves. For the development of the network the network is
segmented with the inclusion of repeaters, switch and other units.
A local area network is created that connects the users in the network and the multiple
LANs connects with the backbone of the network for forming a larger network. The network
is designed and evaluated for minimizing the disruption and eliminating the risk associated
with the development of the network framework. The Sydney network is needed to be
connected with the other branches and it can be accessed via VPN. For connecting the remote
site point to point, frame relay and ATM and other types of long distance connection can be
used for connecting the branch.
1.2. Logical Design of Sydney Branch network
IT INFRASTRUCTURE
The network solution developed for Cosboa would help the organization to improve
the business operation and marketing. The satisfaction of the customer can be improved with
the improvement of the service and extending the new branch to connect with the other
branches of the organization. The network is needed to be designed such that it can be
accessed from remote location and the users of the network can securely share files and
information between themselves. For the development of the network the network is
segmented with the inclusion of repeaters, switch and other units.
A local area network is created that connects the users in the network and the multiple
LANs connects with the backbone of the network for forming a larger network. The network
is designed and evaluated for minimizing the disruption and eliminating the risk associated
with the development of the network framework. The Sydney network is needed to be
connected with the other branches and it can be accessed via VPN. For connecting the remote
site point to point, frame relay and ATM and other types of long distance connection can be
used for connecting the branch.
1.2. Logical Design of Sydney Branch network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT INFRASTRUCTURE
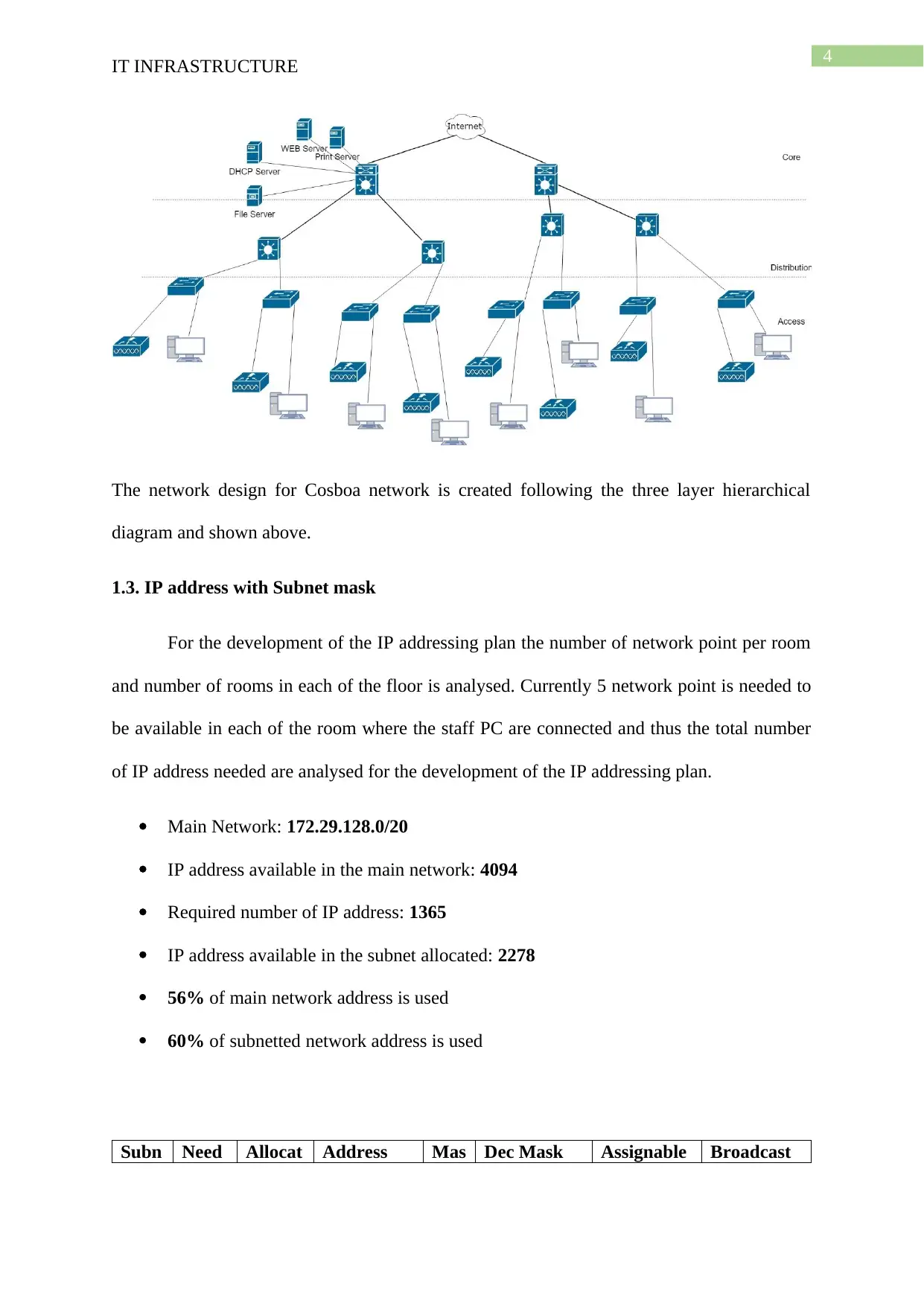
The network design for Cosboa network is created following the three layer hierarchical
diagram and shown above.
1.3. IP address with Subnet mask
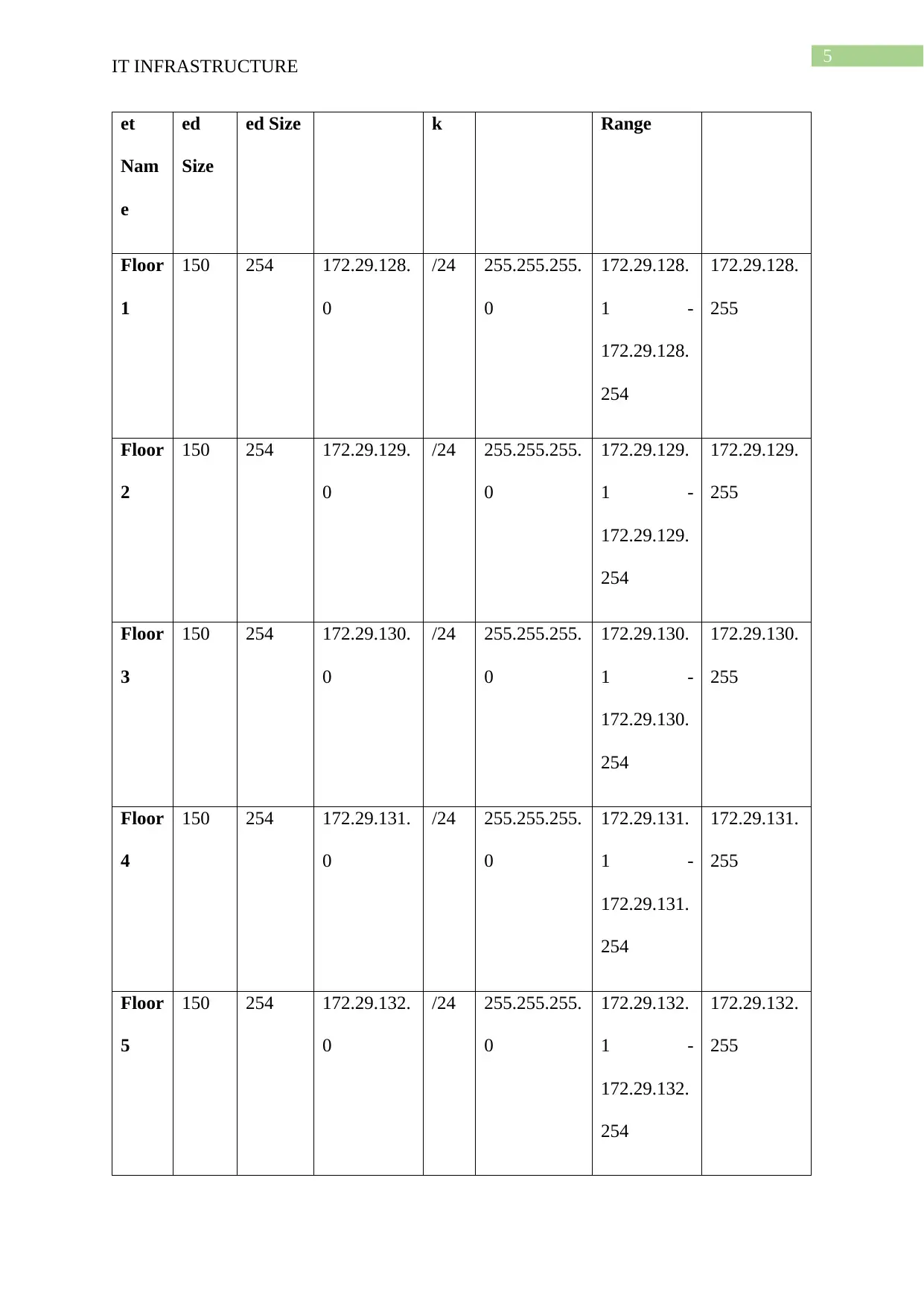
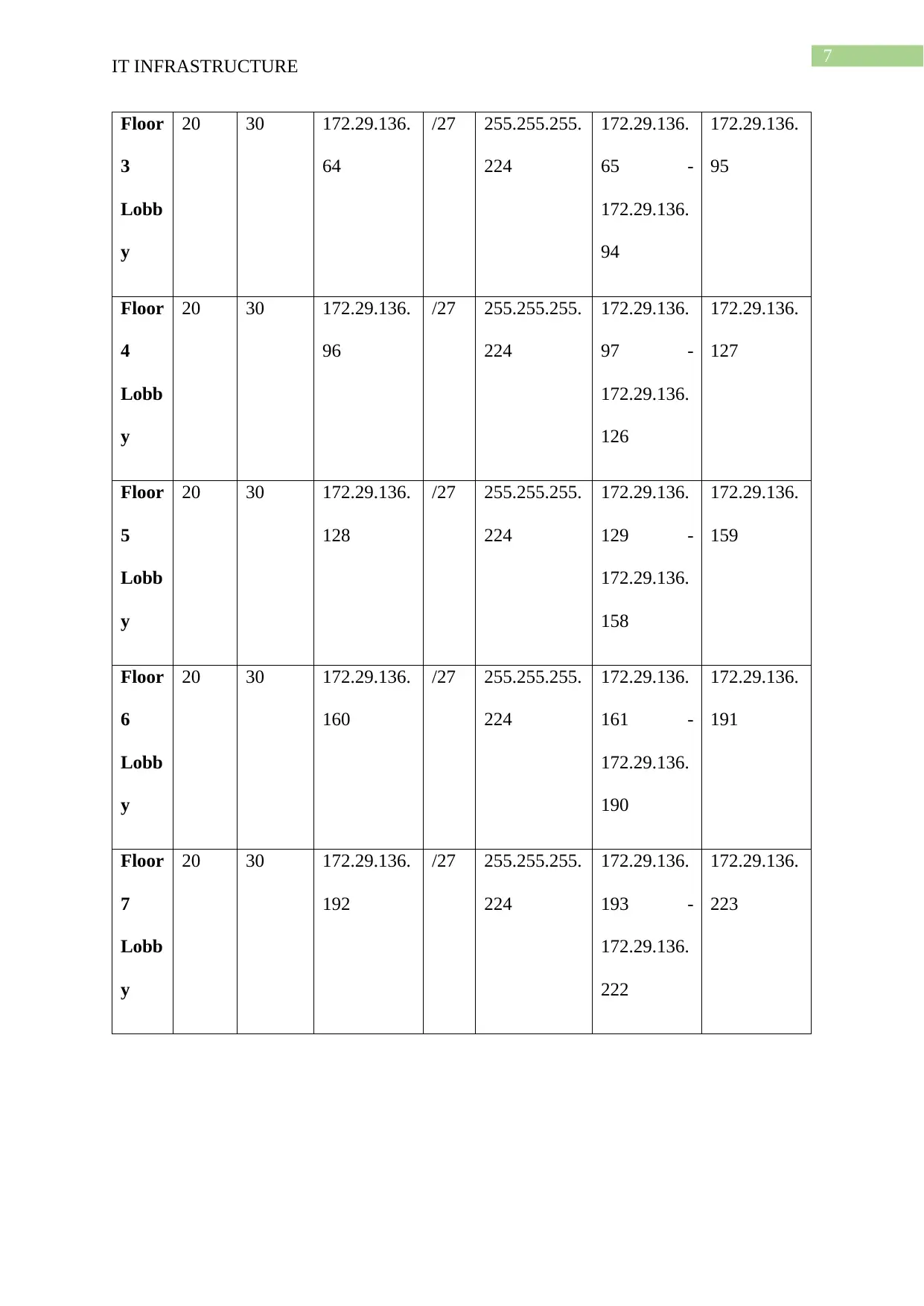
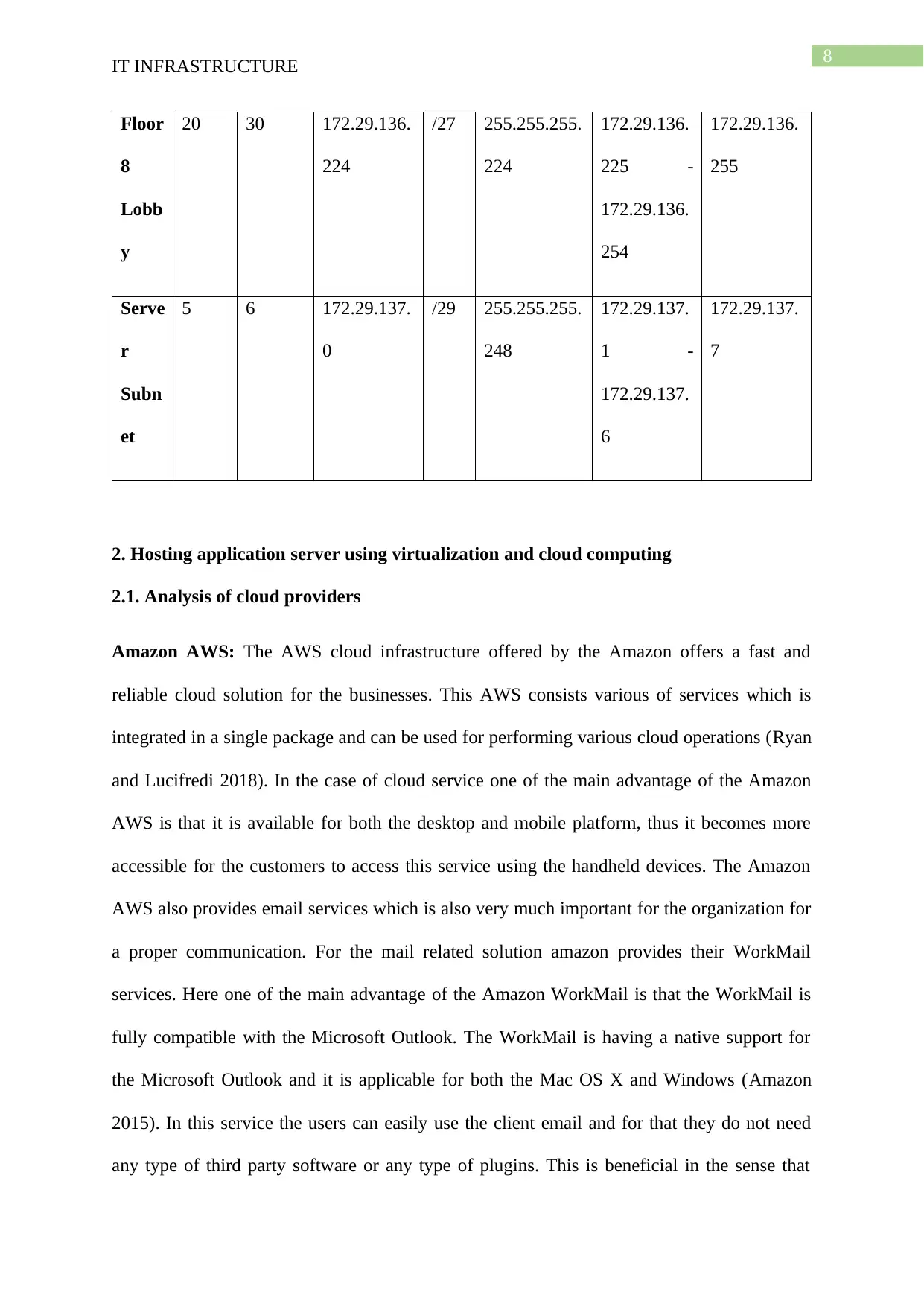
For the development of the IP addressing plan the number of network point per room
and number of rooms in each of the floor is analysed. Currently 5 network point is needed to
be available in each of the room where the staff PC are connected and thus the total number
of IP address needed are analysed for the development of the IP addressing plan.
Main Network: 172.29.128.0/20
IP address available in the main network: 4094
Required number of IP address: 1365
IP address available in the subnet allocated: 2278
56% of main network address is used
60% of subnetted network address is used
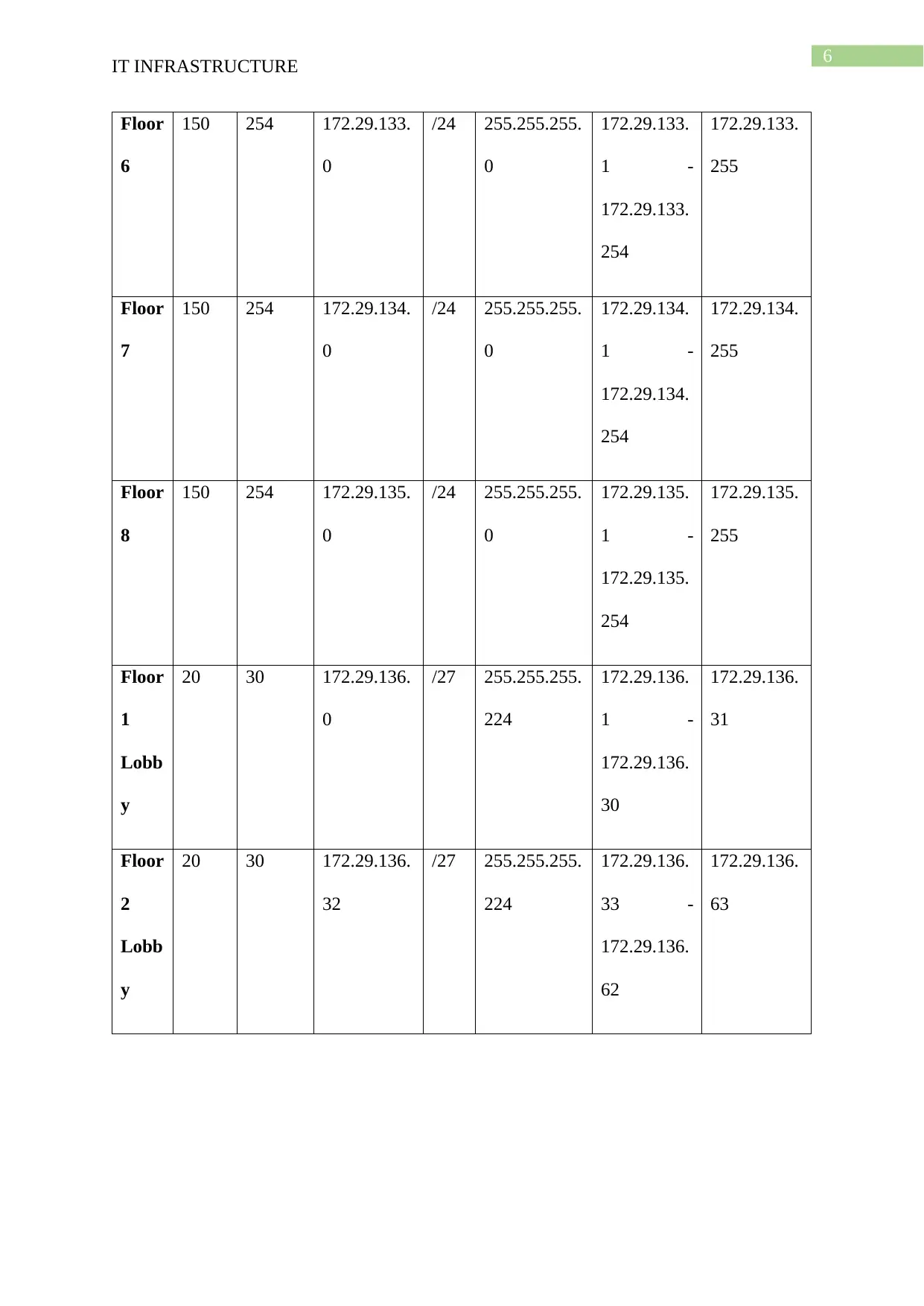
Subn Need Allocat Address Mas Dec Mask Assignable Broadcast
IT INFRASTRUCTURE
The network design for Cosboa network is created following the three layer hierarchical
diagram and shown above.
1.3. IP address with Subnet mask
For the development of the IP addressing plan the number of network point per room
and number of rooms in each of the floor is analysed. Currently 5 network point is needed to
be available in each of the room where the staff PC are connected and thus the total number
of IP address needed are analysed for the development of the IP addressing plan.
Main Network: 172.29.128.0/20
IP address available in the main network: 4094
Required number of IP address: 1365
IP address available in the subnet allocated: 2278
56% of main network address is used
60% of subnetted network address is used
Subn Need Allocat Address Mas Dec Mask Assignable Broadcast
5
IT INFRASTRUCTURE
et
Nam
e
ed
Size
ed Size k Range
Floor
1
150 254 172.29.128.
0
/24 255.255.255.
0
172.29.128.
1 -
172.29.128.
254
172.29.128.
255
Floor
2
150 254 172.29.129.
0
/24 255.255.255.
0
172.29.129.
1 -
172.29.129.
254
172.29.129.
255
Floor
3
150 254 172.29.130.
0
/24 255.255.255.
0
172.29.130.
1 -
172.29.130.
254
172.29.130.
255
Floor
4
150 254 172.29.131.
0
/24 255.255.255.
0
172.29.131.
1 -
172.29.131.
254
172.29.131.
255
Floor
5
150 254 172.29.132.
0
/24 255.255.255.
0
172.29.132.
1 -
172.29.132.
254
172.29.132.
255
IT INFRASTRUCTURE
et
Nam
e
ed
Size
ed Size k Range
Floor
1
150 254 172.29.128.
0
/24 255.255.255.
0
172.29.128.
1 -
172.29.128.
254
172.29.128.
255
Floor
2
150 254 172.29.129.
0
/24 255.255.255.
0
172.29.129.
1 -
172.29.129.
254
172.29.129.
255
Floor
3
150 254 172.29.130.
0
/24 255.255.255.
0
172.29.130.
1 -
172.29.130.
254
172.29.130.
255
Floor
4
150 254 172.29.131.
0
/24 255.255.255.
0
172.29.131.
1 -
172.29.131.
254
172.29.131.
255
Floor
5
150 254 172.29.132.
0
/24 255.255.255.
0
172.29.132.
1 -
172.29.132.
254
172.29.132.
255
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT INFRASTRUCTURE
Floor
6
150 254 172.29.133.
0
/24 255.255.255.
0
172.29.133.
1 -
172.29.133.
254
172.29.133.
255
Floor
7
150 254 172.29.134.
0
/24 255.255.255.
0
172.29.134.
1 -
172.29.134.
254
172.29.134.
255
Floor
8
150 254 172.29.135.
0
/24 255.255.255.
0
172.29.135.
1 -
172.29.135.
254
172.29.135.
255
Floor
1
Lobb
y
20 30 172.29.136.
0
/27 255.255.255.
224
172.29.136.
1 -
172.29.136.
30
172.29.136.
31
Floor
2
Lobb
y
20 30 172.29.136.
32
/27 255.255.255.
224
172.29.136.
33 -
172.29.136.
62
172.29.136.
63
IT INFRASTRUCTURE
Floor
6
150 254 172.29.133.
0
/24 255.255.255.
0
172.29.133.
1 -
172.29.133.
254
172.29.133.
255
Floor
7
150 254 172.29.134.
0
/24 255.255.255.
0
172.29.134.
1 -
172.29.134.
254
172.29.134.
255
Floor
8
150 254 172.29.135.
0
/24 255.255.255.
0
172.29.135.
1 -
172.29.135.
254
172.29.135.
255
Floor
1
Lobb
y
20 30 172.29.136.
0
/27 255.255.255.
224
172.29.136.
1 -
172.29.136.
30
172.29.136.
31
Floor
2
Lobb
y
20 30 172.29.136.
32
/27 255.255.255.
224
172.29.136.
33 -
172.29.136.
62
172.29.136.
63
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT INFRASTRUCTURE
Floor
3
Lobb
y
20 30 172.29.136.
64
/27 255.255.255.
224
172.29.136.
65 -
172.29.136.
94
172.29.136.
95
Floor
4
Lobb
y
20 30 172.29.136.
96
/27 255.255.255.
224
172.29.136.
97 -
172.29.136.
126
172.29.136.
127
Floor
5
Lobb
y
20 30 172.29.136.
128
/27 255.255.255.
224
172.29.136.
129 -
172.29.136.
158
172.29.136.
159
Floor
6
Lobb
y
20 30 172.29.136.
160
/27 255.255.255.
224
172.29.136.
161 -
172.29.136.
190
172.29.136.
191
Floor
7
Lobb
y
20 30 172.29.136.
192
/27 255.255.255.
224
172.29.136.
193 -
172.29.136.
222
172.29.136.
223
IT INFRASTRUCTURE
Floor
3
Lobb
y
20 30 172.29.136.
64
/27 255.255.255.
224
172.29.136.
65 -
172.29.136.
94
172.29.136.
95
Floor
4
Lobb
y
20 30 172.29.136.
96
/27 255.255.255.
224
172.29.136.
97 -
172.29.136.
126
172.29.136.
127
Floor
5
Lobb
y
20 30 172.29.136.
128
/27 255.255.255.
224
172.29.136.
129 -
172.29.136.
158
172.29.136.
159
Floor
6
Lobb
y
20 30 172.29.136.
160
/27 255.255.255.
224
172.29.136.
161 -
172.29.136.
190
172.29.136.
191
Floor
7
Lobb
y
20 30 172.29.136.
192
/27 255.255.255.
224
172.29.136.
193 -
172.29.136.
222
172.29.136.
223
8
IT INFRASTRUCTURE
Floor
8
Lobb
y
20 30 172.29.136.
224
/27 255.255.255.
224
172.29.136.
225 -
172.29.136.
254
172.29.136.
255
Serve
r
Subn
et
5 6 172.29.137.
0
/29 255.255.255.
248
172.29.137.
1 -
172.29.137.
6
172.29.137.
7
2. Hosting application server using virtualization and cloud computing
2.1. Analysis of cloud providers
Amazon AWS: The AWS cloud infrastructure offered by the Amazon offers a fast and
reliable cloud solution for the businesses. This AWS consists various of services which is
integrated in a single package and can be used for performing various cloud operations (Ryan
and Lucifredi 2018). In the case of cloud service one of the main advantage of the Amazon
AWS is that it is available for both the desktop and mobile platform, thus it becomes more
accessible for the customers to access this service using the handheld devices. The Amazon
AWS also provides email services which is also very much important for the organization for
a proper communication. For the mail related solution amazon provides their WorkMail
services. Here one of the main advantage of the Amazon WorkMail is that the WorkMail is
fully compatible with the Microsoft Outlook. The WorkMail is having a native support for
the Microsoft Outlook and it is applicable for both the Mac OS X and Windows (Amazon
2015). In this service the users can easily use the client email and for that they do not need
any type of third party software or any type of plugins. This is beneficial in the sense that
IT INFRASTRUCTURE
Floor
8
Lobb
y
20 30 172.29.136.
224
/27 255.255.255.
224
172.29.136.
225 -
172.29.136.
254
172.29.136.
255
Serve
r
Subn
et
5 6 172.29.137.
0
/29 255.255.255.
248
172.29.137.
1 -
172.29.137.
6
172.29.137.
7
2. Hosting application server using virtualization and cloud computing
2.1. Analysis of cloud providers
Amazon AWS: The AWS cloud infrastructure offered by the Amazon offers a fast and
reliable cloud solution for the businesses. This AWS consists various of services which is
integrated in a single package and can be used for performing various cloud operations (Ryan
and Lucifredi 2018). In the case of cloud service one of the main advantage of the Amazon
AWS is that it is available for both the desktop and mobile platform, thus it becomes more
accessible for the customers to access this service using the handheld devices. The Amazon
AWS also provides email services which is also very much important for the organization for
a proper communication. For the mail related solution amazon provides their WorkMail
services. Here one of the main advantage of the Amazon WorkMail is that the WorkMail is
fully compatible with the Microsoft Outlook. The WorkMail is having a native support for
the Microsoft Outlook and it is applicable for both the Mac OS X and Windows (Amazon
2015). In this service the users can easily use the client email and for that they do not need
any type of third party software or any type of plugins. This is beneficial in the sense that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT INFRASTRUCTURE
most of the user uses the Microsoft Outlook as their primary email server. Thus by
implementing the Amazon WorkMail, Cosboa will be able to manage its infrastructure
regarding email services in efficient and effective manner also this will eliminate the further
investment regarding the improvement of the cloud services.
Google Cloud Drive: For the standard documentation processes Microsoft Office services is
the most popular office suite in this segment and for that the Cosboa organization can use the
Google Drive cloud computing plugin which is able to synchronize and store the any type of
Microsoft PowerPoint presentations, Word document and the Excel spreadsheet
automatically to the to the Google Docs (Tata et al. 2017). By converting it to the Google
Docs the user can easily view the PowerPoint presentations and the Word document file in
the online environment whenever they want. This will make the data easy available to the
users. A main advantage of the Google Docs is that each of the Google Docs gets updated
automatically when each of the time the Microsoft Office document is saved. Also if the
Microsoft document is edited in the offline environment then it get automatically updated to
the Google Docs when the system will be connected to online again (Blacklock, Curry and
Lilienthal 2017). The cloud service of Google Drive is also capable of storing data of other
formats in the cloud environment. Thus the files will be accessible to all the employees of the
organizations if they have proper credentials for the login. Thus this service can also help the
Cosboa organisation to secure their important files over the cloud.
2.2. Techniques for service virtualization
The virtualization of the service is very much important in the context of cloud
computing as it helps the developers to progress further with the development of applications
though there are some workings are not available. The main feature of the virtualization is the
rapid testing which helps the developer to deliver the applications in an efficient manner
IT INFRASTRUCTURE
most of the user uses the Microsoft Outlook as their primary email server. Thus by
implementing the Amazon WorkMail, Cosboa will be able to manage its infrastructure
regarding email services in efficient and effective manner also this will eliminate the further
investment regarding the improvement of the cloud services.
Google Cloud Drive: For the standard documentation processes Microsoft Office services is
the most popular office suite in this segment and for that the Cosboa organization can use the
Google Drive cloud computing plugin which is able to synchronize and store the any type of
Microsoft PowerPoint presentations, Word document and the Excel spreadsheet
automatically to the to the Google Docs (Tata et al. 2017). By converting it to the Google
Docs the user can easily view the PowerPoint presentations and the Word document file in
the online environment whenever they want. This will make the data easy available to the
users. A main advantage of the Google Docs is that each of the Google Docs gets updated
automatically when each of the time the Microsoft Office document is saved. Also if the
Microsoft document is edited in the offline environment then it get automatically updated to
the Google Docs when the system will be connected to online again (Blacklock, Curry and
Lilienthal 2017). The cloud service of Google Drive is also capable of storing data of other
formats in the cloud environment. Thus the files will be accessible to all the employees of the
organizations if they have proper credentials for the login. Thus this service can also help the
Cosboa organisation to secure their important files over the cloud.
2.2. Techniques for service virtualization
The virtualization of the service is very much important in the context of cloud
computing as it helps the developers to progress further with the development of applications
though there are some workings are not available. The main feature of the virtualization is the
rapid testing which helps the developer to deliver the applications in an efficient manner
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT INFRASTRUCTURE
within the deadline. Currently there are different types of virtualization are available for
supporting the cloud platforms. Virtualization within the cloud platform provides high
scalability, reduction of cost, disaster recovery and it also provides the ability of testing the
kernels of the operating system and with that it also helps to test the software applications in
a safe manner (Taherkordi et al. 2016). The main techniques of the virtualization are the
following.
Network Virtualization: In the aspects of cloud computing the network virtualization is
considered as the process of combining software and the hardware related resources and the
functionality of the networks within a single software based administrative type of entity,
which is also known as the virtual network (Liang and Yu 2015). This network virtualization
also includes platform related virtualization which is combined often with the resource
virtualization. There are total two types of network virtualisation which are the internal
virtualization and the other one is the external virtualization. The internal type of
virtualization provides functionality regarding network services to the software containers
within a single network server. Considering the external virtualization this combines many of
the networks or some network parts within a virtual unit.
Application Virtualization: The application virtualization is also considered as the process
virtualization is actually a technology regarding software which efficiently encapsulates
computer programs from operating system on which it is underlying for the execution
purposes. Actually when an application is virtualized it is not installed within the operating
system following the traditional techniques, but still this application is executed within the
operating system. Here for the full application virtualization a visualization layer is also very
much important (Obasuyi and Sari 2015). Here the application virtualization layer substitute
the runtime environment which is provided normally by the OS itself. This layer of
virtualization is capable of intercepting all the disk operations regarding the virtualised
IT INFRASTRUCTURE
within the deadline. Currently there are different types of virtualization are available for
supporting the cloud platforms. Virtualization within the cloud platform provides high
scalability, reduction of cost, disaster recovery and it also provides the ability of testing the
kernels of the operating system and with that it also helps to test the software applications in
a safe manner (Taherkordi et al. 2016). The main techniques of the virtualization are the
following.
Network Virtualization: In the aspects of cloud computing the network virtualization is
considered as the process of combining software and the hardware related resources and the
functionality of the networks within a single software based administrative type of entity,
which is also known as the virtual network (Liang and Yu 2015). This network virtualization
also includes platform related virtualization which is combined often with the resource
virtualization. There are total two types of network virtualisation which are the internal
virtualization and the other one is the external virtualization. The internal type of
virtualization provides functionality regarding network services to the software containers
within a single network server. Considering the external virtualization this combines many of
the networks or some network parts within a virtual unit.
Application Virtualization: The application virtualization is also considered as the process
virtualization is actually a technology regarding software which efficiently encapsulates
computer programs from operating system on which it is underlying for the execution
purposes. Actually when an application is virtualized it is not installed within the operating
system following the traditional techniques, but still this application is executed within the
operating system. Here for the full application virtualization a visualization layer is also very
much important (Obasuyi and Sari 2015). Here the application virtualization layer substitute
the runtime environment which is provided normally by the OS itself. This layer of
virtualization is capable of intercepting all the disk operations regarding the virtualised

11
IT INFRASTRUCTURE
applications and then it directly referred or redirected to a location which is virtualised
previously.
Desktop Virtualisation: The desktop virtualization is also considered as the software
technology which is used for separating the environment of the desktop and the applications
that are associated with it. The desktop virtualization is mainly used in conjunction with the
user profile management system and with the application virtualization (Michael 2015). In
the mode of desktop virtualization all the components regarding the desktop are virtualized.
This virtualization technique a secure desktop delivery model and a flexible desktop model.
Through this approach a complete desktop disaster recovery system can be developed by
backing up all the data to the data centre and through the traditional redundant maintenance
system.
Storage Virtualization: The storage virtualisation is considered as the technique of
transferring the data from physical hard drives to the virtual storages. This technique is a cost
effective and a hassle free technique of pertaining all the data (Peng et al. 2018). In this
storage virtualization technique for operating the storage effectively a central console is
created which mainly aims to simplify the whole process of management. The cloud storage
used for the backup is can manipulate the storage and can help to archive and recover data.
2.3. Dynamic scaling support
Currently the implementation of cloud computing is helping various of organization
in different ways and Cosboa organization is one of them. For the success the scalability
factor of the cloud computing is an important factor as the organization is currently working
with the web servers. Here the scalability is important factor for the organization as it helps
the organization to expand the area of business requirement to meet the customer and the
market demand (Yu and Cai 2016). The applications that are scalable in nature can use more
IT INFRASTRUCTURE
applications and then it directly referred or redirected to a location which is virtualised
previously.
Desktop Virtualisation: The desktop virtualization is also considered as the software
technology which is used for separating the environment of the desktop and the applications
that are associated with it. The desktop virtualization is mainly used in conjunction with the
user profile management system and with the application virtualization (Michael 2015). In
the mode of desktop virtualization all the components regarding the desktop are virtualized.
This virtualization technique a secure desktop delivery model and a flexible desktop model.
Through this approach a complete desktop disaster recovery system can be developed by
backing up all the data to the data centre and through the traditional redundant maintenance
system.
Storage Virtualization: The storage virtualisation is considered as the technique of
transferring the data from physical hard drives to the virtual storages. This technique is a cost
effective and a hassle free technique of pertaining all the data (Peng et al. 2018). In this
storage virtualization technique for operating the storage effectively a central console is
created which mainly aims to simplify the whole process of management. The cloud storage
used for the backup is can manipulate the storage and can help to archive and recover data.
2.3. Dynamic scaling support
Currently the implementation of cloud computing is helping various of organization
in different ways and Cosboa organization is one of them. For the success the scalability
factor of the cloud computing is an important factor as the organization is currently working
with the web servers. Here the scalability is important factor for the organization as it helps
the organization to expand the area of business requirement to meet the customer and the
market demand (Yu and Cai 2016). The applications that are scalable in nature can use more
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





