IT Risk Management for Aztek: Case Study Analysis and Report
VerifiedAdded on 2019/11/14
|17
|5482
|245
Case Study
AI Summary
This report presents an IT risk assessment for Aztek, an Australian finance company, focusing on the implementation of a Bring Your Own Device (BYOD) scheme. The report examines the financial services review, security posture, and potential vulnerabilities associated with BYOD, including data security concerns. It analyzes relevant government regulations like the NSW Act and Workplace Privacy Act 2011, and uses a cybersecurity framework for risk assessment. Findings highlight the feasibility of BYOD from operational, technical, and political perspectives, while also identifying potential risks. The report recommends countermeasures and security programs, emphasizing data classification and security analysis. It concludes with an executive summary, findings, and recommendations, providing a detailed analysis of the BYOD project's impact on Aztek's security and operations. The case study emphasizes the importance of addressing security risks and leveraging BYOD for enhanced productivity and cost reduction.

1
IT Risk Assessment Case Study
September 26
2017
Aztek
IT Risk Assessment Case Study
September 26
2017
Aztek
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
Table of Contents
Financial Services Review.....................................................................................................................5
Security Posture of Aztek......................................................................................................................6
Securing Devices and Information.....................................................................................................7
Addressing the Application specific Risks........................................................................................8
Risk Assessment....................................................................................................................................8
TVA Analysis....................................................................................................................................9
Countermeasures & Security Programs...........................................................................................10
Data Security.......................................................................................................................................12
Data Classification & Security Analysis..........................................................................................13
Conclusion...........................................................................................................................................14
References...........................................................................................................................................16
2
Table of Contents
Financial Services Review.....................................................................................................................5
Security Posture of Aztek......................................................................................................................6
Securing Devices and Information.....................................................................................................7
Addressing the Application specific Risks........................................................................................8
Risk Assessment....................................................................................................................................8
TVA Analysis....................................................................................................................................9
Countermeasures & Security Programs...........................................................................................10
Data Security.......................................................................................................................................12
Data Classification & Security Analysis..........................................................................................13
Conclusion...........................................................................................................................................14
References...........................................................................................................................................16
2

IT Risk Management for Aztek
Executive Summary
The report has been prepared to carry out IT risk assessment for Aztek which is a finance company
from Australia. The finance review and security posture for the organization has been covered in the
report in association with a new concept that the company will implement in association with the
Bring You Own Device (BYOD) scheme. The challenges associated with this scheme and the security
risks that may emerge have been covered.
The initial section of the report will focus upon the government policies and regulations that may have
an impact on the decision of the organization to allow the employees to bring their devices in office.
The report covers the acts and standards, such as NSW Act along with the Workplace Privacy Act
2011 in association with the BYOD scheme.
The next section of the report will cover the various forms of security threats and vulnerabilities that
emerge along with the data security issues with the decision to implement the BYOD scheme. A
Cybersecurity framework has been used for the purpose of risk assessment so that the core functions
are explored and the security controls are highlighted for each of these categories.
The strategies associated with the protection of the data have been covered from the point of view of
several data classification schemes along with the associated measures that can be used for the
security of the data.
Findings & Recommendations
The BYOD project has been analyzed from various aspects to understand its feasibility and utility to
Aztek.
Aztek has a large network of employees, customers, partners, vendors and stakeholders. The primary
goal of the organization is to enhance its customer base by providing better, accurate and secure
financial services along with the enhancements of revenues. BYOD will allow the use of employee-
owned devices which will lead to better productivity of the employees and will assist in the
achievement of the goals. The project is feasible from the organizational point of view.
The operations that will be carried out by the employees will be tracked and monitored using remote
tracking and management. The employees will also be able to access the organizational tools and
applications from their homes and outside of office premises to gain hands-on on the applications.
This will lead to lesser occurrence of operational mistakes. The BYOD scheme will therefore be
feasible from the operational point of view.
3
Executive Summary
The report has been prepared to carry out IT risk assessment for Aztek which is a finance company
from Australia. The finance review and security posture for the organization has been covered in the
report in association with a new concept that the company will implement in association with the
Bring You Own Device (BYOD) scheme. The challenges associated with this scheme and the security
risks that may emerge have been covered.
The initial section of the report will focus upon the government policies and regulations that may have
an impact on the decision of the organization to allow the employees to bring their devices in office.
The report covers the acts and standards, such as NSW Act along with the Workplace Privacy Act
2011 in association with the BYOD scheme.
The next section of the report will cover the various forms of security threats and vulnerabilities that
emerge along with the data security issues with the decision to implement the BYOD scheme. A
Cybersecurity framework has been used for the purpose of risk assessment so that the core functions
are explored and the security controls are highlighted for each of these categories.
The strategies associated with the protection of the data have been covered from the point of view of
several data classification schemes along with the associated measures that can be used for the
security of the data.
Findings & Recommendations
The BYOD project has been analyzed from various aspects to understand its feasibility and utility to
Aztek.
Aztek has a large network of employees, customers, partners, vendors and stakeholders. The primary
goal of the organization is to enhance its customer base by providing better, accurate and secure
financial services along with the enhancements of revenues. BYOD will allow the use of employee-
owned devices which will lead to better productivity of the employees and will assist in the
achievement of the goals. The project is feasible from the organizational point of view.
The operations that will be carried out by the employees will be tracked and monitored using remote
tracking and management. The employees will also be able to access the organizational tools and
applications from their homes and outside of office premises to gain hands-on on the applications.
This will lead to lesser occurrence of operational mistakes. The BYOD scheme will therefore be
feasible from the operational point of view.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Risk Management for Aztek
Technical tools and applications that are being used by the organization are compatible with most of
the recent and widely used operating systems. These tools will be easily integrated with the devices of
the employees. Also, the security department will install the necessary technical controls and
applications for enhancing the security of the device. The project is feasible from the technical point
of view.
There are no laws or regulations created by the Australian Government regarding the prevention of
employee-owned devices in the offices. There are specific rules to financial industry that will be
adhered during the project along with information privacy laws. The project is feasible from the
political point of view as well.
There are many risks that have been identified from the security aspect in association with the BYOD
scheme. These risks may emerge as the potential disadvantages for the project. However, it is possible
to put a check on these risks and avoid them by using correct set of methods, plans, policies and
controls.
There will be many advantages that will be offered with the implementation of BYOD in the
organization. The first advantage would be in the form of reduced costs. The costs associated with the
procurement of the devices, maintenance of the devices, infrastructural and operations costs will be
reduced. The employees will be allowed to access most of the organizational tools and applications
from any of the remote location which would enhance their operational excellence leading to better
productivity and efficiency levels. The customers will also be satisfied as their demands will be met
and the quality of services will also improve. This would lead to better revenues and market shares as
well.
4
Technical tools and applications that are being used by the organization are compatible with most of
the recent and widely used operating systems. These tools will be easily integrated with the devices of
the employees. Also, the security department will install the necessary technical controls and
applications for enhancing the security of the device. The project is feasible from the technical point
of view.
There are no laws or regulations created by the Australian Government regarding the prevention of
employee-owned devices in the offices. There are specific rules to financial industry that will be
adhered during the project along with information privacy laws. The project is feasible from the
political point of view as well.
There are many risks that have been identified from the security aspect in association with the BYOD
scheme. These risks may emerge as the potential disadvantages for the project. However, it is possible
to put a check on these risks and avoid them by using correct set of methods, plans, policies and
controls.
There will be many advantages that will be offered with the implementation of BYOD in the
organization. The first advantage would be in the form of reduced costs. The costs associated with the
procurement of the devices, maintenance of the devices, infrastructural and operations costs will be
reduced. The employees will be allowed to access most of the organizational tools and applications
from any of the remote location which would enhance their operational excellence leading to better
productivity and efficiency levels. The customers will also be satisfied as their demands will be met
and the quality of services will also improve. This would lead to better revenues and market shares as
well.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
Financial Services Review
Aztek has decided to allow the employees to bring their personal devices at the workplace for the
execution of professional tasks and activities.
The company is based out of Australia and the country does not have any specific laws in place for
the governance and surveillance of the employees making use of any form of application or service
outsourcing. However, the specific business domains do have certain rules and regulations defined.
The business domain and functional area for Aztek is finance. There are two primary jurisdiction
areas in Australia that is, New South Wales and Australian Capital Territory. The use and application
of the electronic communication and networking varies in these areas which shall be followed by
Aztek as per the service territory.
Australian Securities and Investment Commission (ASIC) is a government body that regulates all the
financial transactions and services at the federal, state and territory levels. There are laws that have
been set up under this body for the regulation of electronic payments under the e-payments code and
for the financial access control and management as well. These laws and guidelines shall be followed
(Asic, 2017).
BYOD scheme would allow the employees to make use of their devices for the organizational
activities outside of the office premises as well. NSW is an Act that has been defined for the
surveillance of the employee activities and processes beyond the office premises. The communication
and operational activities will be tracked on the employee device under this act and there would be
restriction on the sharing of information with the resources outside of the office or a particular project.
Aztek may also make use of overt surveillance which would involve automated software for the
purpose of tracking. In this case, the employees must be told about the same 14 days prior to the
conduction process.
The employees may also exchange emails and messages using their devices which may include
financial information and details. Workplace Privacy Act 2011 has been defined by the Australian
government for the email surveillance and tracking. The data that will be exchanged by the employees
on their mail servers will be monitored by Aztek as per the rules of this act (Act, 2016).
Telecommunications Act 1979 has also been defined by the Australian Government to cover the
permissions that are associated with communication interception. It has been established to ensure the
integrity of the communications so that any of the unknown communications do not take place. This
act only covers the content tracking and does not include the tracking of email address or metadata
(Coe, 2011).
5
Financial Services Review
Aztek has decided to allow the employees to bring their personal devices at the workplace for the
execution of professional tasks and activities.
The company is based out of Australia and the country does not have any specific laws in place for
the governance and surveillance of the employees making use of any form of application or service
outsourcing. However, the specific business domains do have certain rules and regulations defined.
The business domain and functional area for Aztek is finance. There are two primary jurisdiction
areas in Australia that is, New South Wales and Australian Capital Territory. The use and application
of the electronic communication and networking varies in these areas which shall be followed by
Aztek as per the service territory.
Australian Securities and Investment Commission (ASIC) is a government body that regulates all the
financial transactions and services at the federal, state and territory levels. There are laws that have
been set up under this body for the regulation of electronic payments under the e-payments code and
for the financial access control and management as well. These laws and guidelines shall be followed
(Asic, 2017).
BYOD scheme would allow the employees to make use of their devices for the organizational
activities outside of the office premises as well. NSW is an Act that has been defined for the
surveillance of the employee activities and processes beyond the office premises. The communication
and operational activities will be tracked on the employee device under this act and there would be
restriction on the sharing of information with the resources outside of the office or a particular project.
Aztek may also make use of overt surveillance which would involve automated software for the
purpose of tracking. In this case, the employees must be told about the same 14 days prior to the
conduction process.
The employees may also exchange emails and messages using their devices which may include
financial information and details. Workplace Privacy Act 2011 has been defined by the Australian
government for the email surveillance and tracking. The data that will be exchanged by the employees
on their mail servers will be monitored by Aztek as per the rules of this act (Act, 2016).
Telecommunications Act 1979 has also been defined by the Australian Government to cover the
permissions that are associated with communication interception. It has been established to ensure the
integrity of the communications so that any of the unknown communications do not take place. This
act only covers the content tracking and does not include the tracking of email address or metadata
(Coe, 2011).
5

IT Risk Management for Aztek
The financial information that will be processed and managed by the devices of the employees under
the BYOD scheme would also be required to abide by the rules under Intellectual Property and
information privacy. The privacy and security of the information will be maintained under these laws
and regulations.
Privacy Act (APP 5) has also been defined for the maintenance and management of the information
privacy. The devices of the employees must not store or process the personal information of other
employees or the customers of Aztek. The access rules and the user privileges shall also be defined
for the purpose of information access. In case of a data breach, the employees must be aware of the
process that they must follow for reporting the matter to the senior management (Oaic, 2014).
Security Posture of Aztek
There are a number of security postures and policies that must be considered and modified in
association with Aztek with the introduction of BYOD scheme. It would include the current state of
security in the organization, use of mobile devices currently in use along with the future use of the
devices, geographical strategies that shall be followed for the deployment of the project.
The finance industries that are present in a particular country need to abide by certain rules and
regulations at the federal and state level along with the territory and industry level. Such financial
constraints and necessities have been discussed in the section above. In case of Aztek, another area of
concern that shall be monitored and handled is the security of the devices, information and networks.
There are certain weaknesses in the current security state of Aztek which are included as follows:
There are numerous obsolete devices and security mechanisms that are being used in the
organization. For instance, there are many of the computer systems and gadgets that are in use
which are more than 5 years old. Some of these systems cannot be updated as per the latest
technological concepts and security frameworks. These systems and components shall be
removed and replaced by the newer systems.
The use of identity and access control is Aztek is still restricted to the magnetic card readers
and identification. There are newer forms of controls that can be used for this purpose, such
as biometric recognition.
There is an excessive use of in-house storage and management of the information that is
associated with the organization. The file servers and database servers are also located in-
house which makes it a single point of failure. In case the attacker succeeds in gaining access
to these locations, then the security breach would be huge.
The legacy systems that are being used by Aztek are also technically not sound and need a lot
many updates to be done.
6
The financial information that will be processed and managed by the devices of the employees under
the BYOD scheme would also be required to abide by the rules under Intellectual Property and
information privacy. The privacy and security of the information will be maintained under these laws
and regulations.
Privacy Act (APP 5) has also been defined for the maintenance and management of the information
privacy. The devices of the employees must not store or process the personal information of other
employees or the customers of Aztek. The access rules and the user privileges shall also be defined
for the purpose of information access. In case of a data breach, the employees must be aware of the
process that they must follow for reporting the matter to the senior management (Oaic, 2014).
Security Posture of Aztek
There are a number of security postures and policies that must be considered and modified in
association with Aztek with the introduction of BYOD scheme. It would include the current state of
security in the organization, use of mobile devices currently in use along with the future use of the
devices, geographical strategies that shall be followed for the deployment of the project.
The finance industries that are present in a particular country need to abide by certain rules and
regulations at the federal and state level along with the territory and industry level. Such financial
constraints and necessities have been discussed in the section above. In case of Aztek, another area of
concern that shall be monitored and handled is the security of the devices, information and networks.
There are certain weaknesses in the current security state of Aztek which are included as follows:
There are numerous obsolete devices and security mechanisms that are being used in the
organization. For instance, there are many of the computer systems and gadgets that are in use
which are more than 5 years old. Some of these systems cannot be updated as per the latest
technological concepts and security frameworks. These systems and components shall be
removed and replaced by the newer systems.
The use of identity and access control is Aztek is still restricted to the magnetic card readers
and identification. There are newer forms of controls that can be used for this purpose, such
as biometric recognition.
There is an excessive use of in-house storage and management of the information that is
associated with the organization. The file servers and database servers are also located in-
house which makes it a single point of failure. In case the attacker succeeds in gaining access
to these locations, then the security breach would be huge.
The legacy systems that are being used by Aztek are also technically not sound and need a lot
many updates to be done.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Risk Management for Aztek
The security loopholes that have been identified above will require a lot of investment to be done to
make sure that the security infrastructure is improved. With the use of the BYOD scheme, there will
be many devices that will be brought by the employees in the organization and the need to procure
additional set of devices will not be required. However, this scheme will have its own security risks
and concerns.
Securing Devices and Information
In the organizations that have a single vendor or manufacturer of the devices, it is easy to control the
security status through unified management. There is a single set of security control and checks that
need to be implemented to attain overall security of the devices.
However, in the case of outsourcing, the security policies and plans that are required to be followed
are different. The employees in this case will bring their own devices to the organization which will
have different security framework, different operating systems, different data and information
capabilities etc. There is no uniform security scheme that can be designed and implemented so that the
overall security of all the devices is ensured. The device portfolio will also expand with the BYOD
scheme with the inclusion of Smartphones, laptops, tablets etc. from different sources. The current
security policy will therefore require many updates to be done and installed (Curran, Maynes and
Harkin, 2015).
The approach such as locking down of the devices outside of the company networks would not work
as the devices are personally owned by the employees and the practice would discourage them to
adapt to the BYOD scheme. A flexible approach which is also secure would be required for the
management of the risks. The use of access control on the official applications that include critical and
sensitive information can be done outside of the office network (Gillies, 2016).
There are many risks that are associated with the device itself. For instance, the device of the
employee may get lost or may get stolen by an entity that may get access to the organizational
information if the device would be connected to the VPN. The confidential information would then
get exposed to such unauthorized entities and for this device tracking and security would be of utmost
importance.
There may also be ownership issues that may crop up. The employees will be the owners of their
devices and would like to have a complete ownership on their data and information. They may
attempt to jailbreak the devices which may have an extremely negative impact on the device security.
The terms and conditions under the BYOD scheme shall therefore be clearly explained to the
employees before they agree to bring their devices at the workplace (Tokuyoshi, 2013).
7
The security loopholes that have been identified above will require a lot of investment to be done to
make sure that the security infrastructure is improved. With the use of the BYOD scheme, there will
be many devices that will be brought by the employees in the organization and the need to procure
additional set of devices will not be required. However, this scheme will have its own security risks
and concerns.
Securing Devices and Information
In the organizations that have a single vendor or manufacturer of the devices, it is easy to control the
security status through unified management. There is a single set of security control and checks that
need to be implemented to attain overall security of the devices.
However, in the case of outsourcing, the security policies and plans that are required to be followed
are different. The employees in this case will bring their own devices to the organization which will
have different security framework, different operating systems, different data and information
capabilities etc. There is no uniform security scheme that can be designed and implemented so that the
overall security of all the devices is ensured. The device portfolio will also expand with the BYOD
scheme with the inclusion of Smartphones, laptops, tablets etc. from different sources. The current
security policy will therefore require many updates to be done and installed (Curran, Maynes and
Harkin, 2015).
The approach such as locking down of the devices outside of the company networks would not work
as the devices are personally owned by the employees and the practice would discourage them to
adapt to the BYOD scheme. A flexible approach which is also secure would be required for the
management of the risks. The use of access control on the official applications that include critical and
sensitive information can be done outside of the office network (Gillies, 2016).
There are many risks that are associated with the device itself. For instance, the device of the
employee may get lost or may get stolen by an entity that may get access to the organizational
information if the device would be connected to the VPN. The confidential information would then
get exposed to such unauthorized entities and for this device tracking and security would be of utmost
importance.
There may also be ownership issues that may crop up. The employees will be the owners of their
devices and would like to have a complete ownership on their data and information. They may
attempt to jailbreak the devices which may have an extremely negative impact on the device security.
The terms and conditions under the BYOD scheme shall therefore be clearly explained to the
employees before they agree to bring their devices at the workplace (Tokuyoshi, 2013).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
There are also certain basic mechanisms that can be used for the protection of the devices and the
information present in these devices.
The security team must investigate the devices to highlight the alignment with the security
policies of Aztek.
Mobile device management must be carried out by the team of the auditors and reviewers.
Device encryption, remote wiping and the use of PIN codes shall be done for device and
information security.
The use of certified software and critical information sets must be restricted on the office
networks only (Beckett, 2014).
Addressing the Application specific Risks
With the use of BYOD scheme, there can be two categories of application specific risks that may be
observed. These risks include the malware attacks through the applications that are installed which
would demand the highest level of malware protection. There may also be exploitation of the security
vulnerabilities present in the application which may lead to the compromise of the security of
sensitive and confidential information. Enhanced application management will be necessary for this
purpose so that such risks are avoided and controlled (Romer, 2014).
There shall also be upgrades and security updates that must be installed in the devices and for the
applications that are present in the devices to make sure that the security risks specific to device
version or application version are avoided.
Risk Assessment
The Cybersecurity framework that is followed in this case is based upon the flexible and high
performance mechanisms that can be used for the enhancement of the security posture in an
organization.
The core of the framework includes the definitions for the functions along with the categories and
sub-categories along with the references that come under the security checklist. The set of functions
comprise of the risk identification, asset protection, incident identification, planning of the responses
along with the recovery of the data. There are different categories that are used including asset
management and control, access management and control, detection and prevention systems. The
information security mechanisms against the security risks that are defined have been done for the
information in transition along with the information at rest.
8
There are also certain basic mechanisms that can be used for the protection of the devices and the
information present in these devices.
The security team must investigate the devices to highlight the alignment with the security
policies of Aztek.
Mobile device management must be carried out by the team of the auditors and reviewers.
Device encryption, remote wiping and the use of PIN codes shall be done for device and
information security.
The use of certified software and critical information sets must be restricted on the office
networks only (Beckett, 2014).
Addressing the Application specific Risks
With the use of BYOD scheme, there can be two categories of application specific risks that may be
observed. These risks include the malware attacks through the applications that are installed which
would demand the highest level of malware protection. There may also be exploitation of the security
vulnerabilities present in the application which may lead to the compromise of the security of
sensitive and confidential information. Enhanced application management will be necessary for this
purpose so that such risks are avoided and controlled (Romer, 2014).
There shall also be upgrades and security updates that must be installed in the devices and for the
applications that are present in the devices to make sure that the security risks specific to device
version or application version are avoided.
Risk Assessment
The Cybersecurity framework that is followed in this case is based upon the flexible and high
performance mechanisms that can be used for the enhancement of the security posture in an
organization.
The core of the framework includes the definitions for the functions along with the categories and
sub-categories along with the references that come under the security checklist. The set of functions
comprise of the risk identification, asset protection, incident identification, planning of the responses
along with the recovery of the data. There are different categories that are used including asset
management and control, access management and control, detection and prevention systems. The
information security mechanisms against the security risks that are defined have been done for the
information in transition along with the information at rest.
8
IT Risk Management for Aztek
There are different tiers to security that Aztek must follow and consider and it must be ensured that
the security state must move towards the highest tier.
Tier 1 is the state in which there is a partial protection of the organizational assets and the
processes are defined but not formalized in association with security.
Tier 2 is the state in which the risks have been identified and a formal procedure for the
management of the risks has also been created.
Tier 3 is the state in which the management approves of the protection and security measures
that must be used. There is a use of consistent methods in this case.
Tier 4 is the state that includes adaptive risk management to make sure that the organization is
efficient to handle the changing threat landscape.
In case of Aztek, the BYOD scheme will bring with it a lot many new challenges and issues. The
employees of an organization may also change and there may be new devices that may be added in
the set of devices to be managed by the organization. There will be a continuous change in the threat
landscape and therefore, the risk assessment process that is followed in this case shall be in tier-4
(Singh et al., 2014).
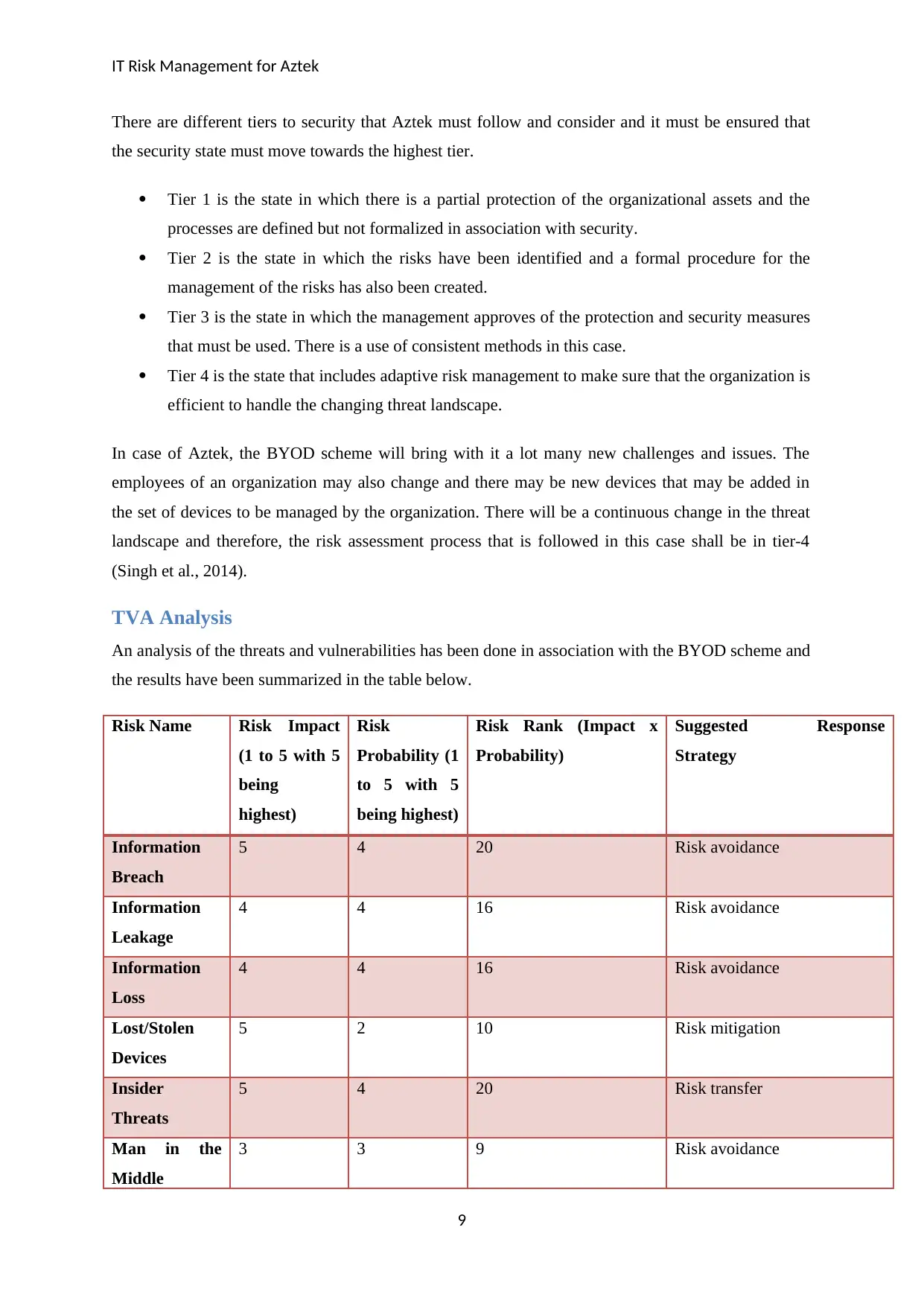
TVA Analysis
An analysis of the threats and vulnerabilities has been done in association with the BYOD scheme and
the results have been summarized in the table below.
Risk Name Risk Impact
(1 to 5 with 5
being
highest)
Risk
Probability (1
to 5 with 5
being highest)
Risk Rank (Impact x
Probability)
Suggested Response
Strategy
Information
Breach
5 4 20 Risk avoidance
Information
Leakage
4 4 16 Risk avoidance
Information
Loss
4 4 16 Risk avoidance
Lost/Stolen
Devices
5 2 10 Risk mitigation
Insider
Threats
5 4 20 Risk transfer
Man in the
Middle
3 3 9 Risk avoidance
9
There are different tiers to security that Aztek must follow and consider and it must be ensured that
the security state must move towards the highest tier.
Tier 1 is the state in which there is a partial protection of the organizational assets and the
processes are defined but not formalized in association with security.
Tier 2 is the state in which the risks have been identified and a formal procedure for the
management of the risks has also been created.
Tier 3 is the state in which the management approves of the protection and security measures
that must be used. There is a use of consistent methods in this case.
Tier 4 is the state that includes adaptive risk management to make sure that the organization is
efficient to handle the changing threat landscape.
In case of Aztek, the BYOD scheme will bring with it a lot many new challenges and issues. The
employees of an organization may also change and there may be new devices that may be added in
the set of devices to be managed by the organization. There will be a continuous change in the threat
landscape and therefore, the risk assessment process that is followed in this case shall be in tier-4
(Singh et al., 2014).
TVA Analysis
An analysis of the threats and vulnerabilities has been done in association with the BYOD scheme and
the results have been summarized in the table below.
Risk Name Risk Impact
(1 to 5 with 5
being
highest)
Risk
Probability (1
to 5 with 5
being highest)
Risk Rank (Impact x
Probability)
Suggested Response
Strategy
Information
Breach
5 4 20 Risk avoidance
Information
Leakage
4 4 16 Risk avoidance
Information
Loss
4 4 16 Risk avoidance
Lost/Stolen
Devices
5 2 10 Risk mitigation
Insider
Threats
5 4 20 Risk transfer
Man in the
Middle
3 3 9 Risk avoidance
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Risk Management for Aztek
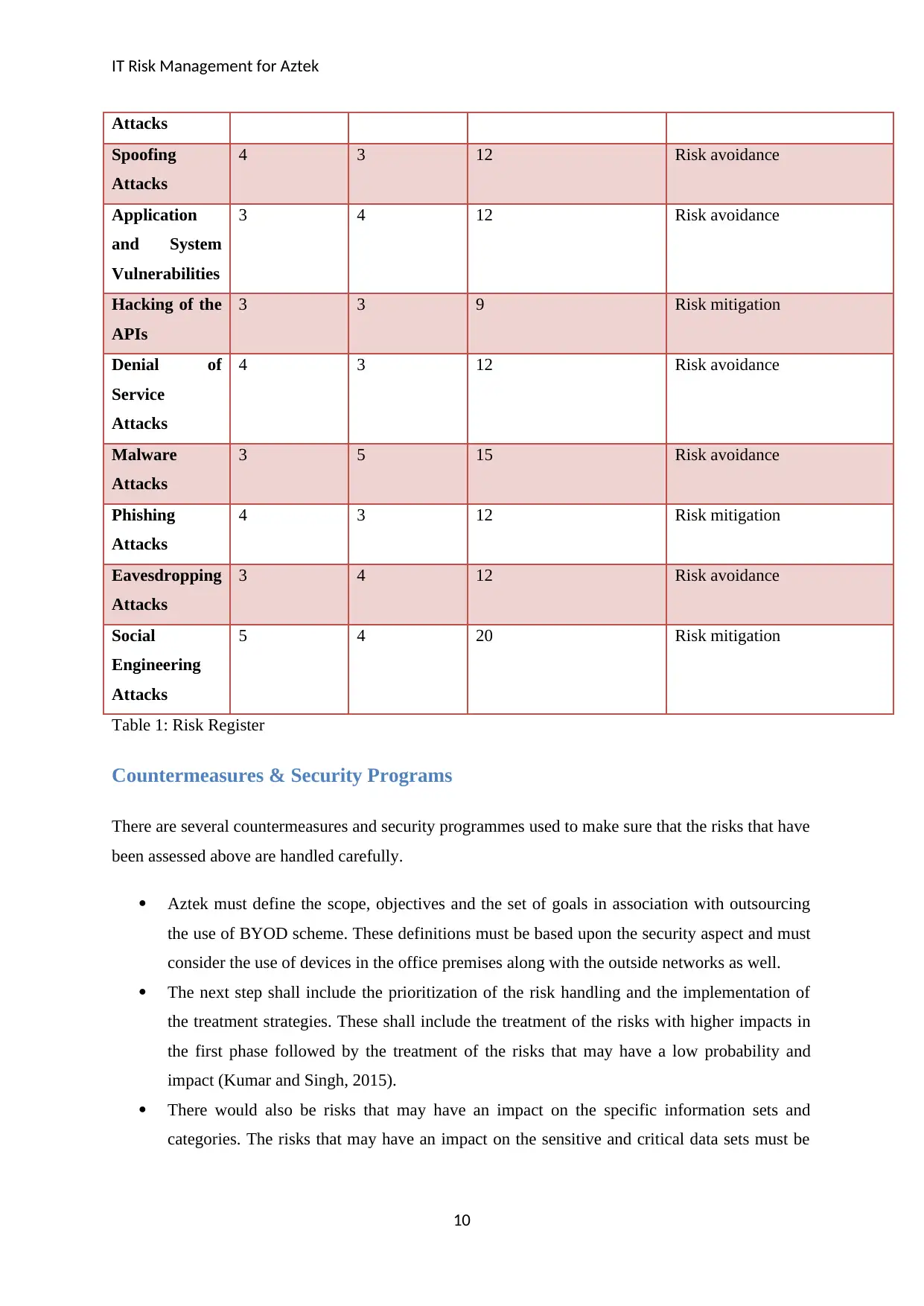
Attacks
Spoofing
Attacks
4 3 12 Risk avoidance
Application
and System
Vulnerabilities
3 4 12 Risk avoidance
Hacking of the
APIs
3 3 9 Risk mitigation
Denial of
Service
Attacks
4 3 12 Risk avoidance
Malware
Attacks
3 5 15 Risk avoidance
Phishing
Attacks
4 3 12 Risk mitigation
Eavesdropping
Attacks
3 4 12 Risk avoidance
Social
Engineering
Attacks
5 4 20 Risk mitigation
Table 1: Risk Register
Countermeasures & Security Programs
There are several countermeasures and security programmes used to make sure that the risks that have
been assessed above are handled carefully.
Aztek must define the scope, objectives and the set of goals in association with outsourcing
the use of BYOD scheme. These definitions must be based upon the security aspect and must
consider the use of devices in the office premises along with the outside networks as well.
The next step shall include the prioritization of the risk handling and the implementation of
the treatment strategies. These shall include the treatment of the risks with higher impacts in
the first phase followed by the treatment of the risks that may have a low probability and
impact (Kumar and Singh, 2015).
There would also be risks that may have an impact on the specific information sets and
categories. The risks that may have an impact on the sensitive and critical data sets must be
10
Attacks
Spoofing
Attacks
4 3 12 Risk avoidance
Application
and System
Vulnerabilities
3 4 12 Risk avoidance
Hacking of the
APIs
3 3 9 Risk mitigation
Denial of
Service
Attacks
4 3 12 Risk avoidance
Malware
Attacks
3 5 15 Risk avoidance
Phishing
Attacks
4 3 12 Risk mitigation
Eavesdropping
Attacks
3 4 12 Risk avoidance
Social
Engineering
Attacks
5 4 20 Risk mitigation
Table 1: Risk Register
Countermeasures & Security Programs
There are several countermeasures and security programmes used to make sure that the risks that have
been assessed above are handled carefully.
Aztek must define the scope, objectives and the set of goals in association with outsourcing
the use of BYOD scheme. These definitions must be based upon the security aspect and must
consider the use of devices in the office premises along with the outside networks as well.
The next step shall include the prioritization of the risk handling and the implementation of
the treatment strategies. These shall include the treatment of the risks with higher impacts in
the first phase followed by the treatment of the risks that may have a low probability and
impact (Kumar and Singh, 2015).
There would also be risks that may have an impact on the specific information sets and
categories. The risks that may have an impact on the sensitive and critical data sets must be
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management for Aztek
identified and the mapping response strategies shall be created. These risks shall be handled at
the top priority.
Once the initial round of planning and analysis is completed, there shall be mapping on the type of the
countermeasure that shall be applied. For example, there are certain risks that can be controlled and
avoided by using administrative checks only while there are a few risks that may demand a technical
tool and application for the avoidance and management of the risk (Stoecklin et al., 2016).
There are several countermeasures that have been developed which can be applied in order to
overcome, avoid, prevent, detect and control the security risks that are associated with the decision of
Aztek to provide the employees with the permission to bring their devices at work.
These controls and countermeasures are as described below:
Preventive Controls: These are the control measures that shall make sure that the occurrence
of security risks does not take place by using mechanisms like advanced access control and
authentication. Also, the setting up of firewalls and proxy servers would come under this
category. These controls form the basic approach towards the maintenance and management
of security.
Detective Controls: There may be cases when the preventive controls may fail and the
malevolent entities may succeed in violating the access or basic security measures. In such
cases, these controls shall be applied which shall highlight the activities of the attackers by
making use of integrity checks, security logs and audits along with intrusion detection tools.
Corrective Controls: There are advanced methods that are used by the attackers to give
shape to the security attacks. They may succeed in passing through the preventive and
detective controls. The corrective controls are the ones that shall be used for the control and
minimization of the damage. The use of encryption is one of the examples of such controls
which would protect the information even if it gets exposed to the attackers (Blizzard, 2015).
Deterrent Controls: The attackers must be made aware of the readiness of the organization
to deal with the security risks and attacks. These controls are the measures that send across
this message by using advanced network monitoring and maintenance of the network and
security logs.
Recovery Controls: There are security controls that have been set up with the purpose of
disaster recovery. These controls are similar to the corrective controls but are applied in more
significant damages and impacts. There are various attempts that the organization must make
so that the continuity of the business operations is maintained and the backup of the data is
also created and updated at the regular intervals.
11
identified and the mapping response strategies shall be created. These risks shall be handled at
the top priority.
Once the initial round of planning and analysis is completed, there shall be mapping on the type of the
countermeasure that shall be applied. For example, there are certain risks that can be controlled and
avoided by using administrative checks only while there are a few risks that may demand a technical
tool and application for the avoidance and management of the risk (Stoecklin et al., 2016).
There are several countermeasures that have been developed which can be applied in order to
overcome, avoid, prevent, detect and control the security risks that are associated with the decision of
Aztek to provide the employees with the permission to bring their devices at work.
These controls and countermeasures are as described below:
Preventive Controls: These are the control measures that shall make sure that the occurrence
of security risks does not take place by using mechanisms like advanced access control and
authentication. Also, the setting up of firewalls and proxy servers would come under this
category. These controls form the basic approach towards the maintenance and management
of security.
Detective Controls: There may be cases when the preventive controls may fail and the
malevolent entities may succeed in violating the access or basic security measures. In such
cases, these controls shall be applied which shall highlight the activities of the attackers by
making use of integrity checks, security logs and audits along with intrusion detection tools.
Corrective Controls: There are advanced methods that are used by the attackers to give
shape to the security attacks. They may succeed in passing through the preventive and
detective controls. The corrective controls are the ones that shall be used for the control and
minimization of the damage. The use of encryption is one of the examples of such controls
which would protect the information even if it gets exposed to the attackers (Blizzard, 2015).
Deterrent Controls: The attackers must be made aware of the readiness of the organization
to deal with the security risks and attacks. These controls are the measures that send across
this message by using advanced network monitoring and maintenance of the network and
security logs.
Recovery Controls: There are security controls that have been set up with the purpose of
disaster recovery. These controls are similar to the corrective controls but are applied in more
significant damages and impacts. There are various attempts that the organization must make
so that the continuity of the business operations is maintained and the backup of the data is
also created and updated at the regular intervals.
11

IT Risk Management for Aztek
Compensating Controls: There may be cases when the required security control may take
time to be developed and implemented. In such cases, the security of the application, service,
system or device shall be maintained by using an alternative measure, such as use of patches
in case of security updates or installations.
Data Security
Data is one of the biggest assets for Aztek as it is the case with every other organization and there are
various measures that may be used and implemented for making sure that the risks associated with the
data and information are avoided. Some of these measures include access control, incident recording
and resolution, privacy standards, codes of conduct, use of social media, encryption techniques, anti-
denial and anti-malware tools etc. These may also include the employee and user awareness along
with training sessions on the security practices to be followed.
In case of the BYOD scheme, the probability and the types of probable risks increase as there are
different access points that may be used for giving shape to the attack. The attack surface would
increase along with the attack window. Aztek would be required to make use of end-to-end data
protection techniques to make sure that the security risks and attacks are avoided. The
mismanagement of the devices that will be owned by the employees may be the biggest contributor in
the occurrence of the data security attacks and risks. There must be policies that must be created for
data protection in case of employee resignation and transfer. The tools, applications and information
present in the device of the employee shall be allowed to be remotely wiped out and a cross
examination of the same shall also be carried out.
There can be severe implications in terms of financial and legal obligations that may be caused with a
weak data security. There are certain measures that must be used to avoid the same.
There shall be advanced log maintenance maintained in the organization in terms of the
device activity in Aztek and the employee activity on the devices and applications.
The company must take up the responsibility of managing the user passwords and PIN codes.
In case of default passwords and PIN codes usage, there are various security vulnerabilities
that come up. There shall be use of automated password managers along with the alerts on
password change at frequent intervals. The use of common passwords like name, DOB etc.
shall be avoided.
The critical applications associated with Aztek must be installed in the devices owned by the
employees but shall be accessible only when the device is connected to the corporate network.
12
Compensating Controls: There may be cases when the required security control may take
time to be developed and implemented. In such cases, the security of the application, service,
system or device shall be maintained by using an alternative measure, such as use of patches
in case of security updates or installations.
Data Security
Data is one of the biggest assets for Aztek as it is the case with every other organization and there are
various measures that may be used and implemented for making sure that the risks associated with the
data and information are avoided. Some of these measures include access control, incident recording
and resolution, privacy standards, codes of conduct, use of social media, encryption techniques, anti-
denial and anti-malware tools etc. These may also include the employee and user awareness along
with training sessions on the security practices to be followed.
In case of the BYOD scheme, the probability and the types of probable risks increase as there are
different access points that may be used for giving shape to the attack. The attack surface would
increase along with the attack window. Aztek would be required to make use of end-to-end data
protection techniques to make sure that the security risks and attacks are avoided. The
mismanagement of the devices that will be owned by the employees may be the biggest contributor in
the occurrence of the data security attacks and risks. There must be policies that must be created for
data protection in case of employee resignation and transfer. The tools, applications and information
present in the device of the employee shall be allowed to be remotely wiped out and a cross
examination of the same shall also be carried out.
There can be severe implications in terms of financial and legal obligations that may be caused with a
weak data security. There are certain measures that must be used to avoid the same.
There shall be advanced log maintenance maintained in the organization in terms of the
device activity in Aztek and the employee activity on the devices and applications.
The company must take up the responsibility of managing the user passwords and PIN codes.
In case of default passwords and PIN codes usage, there are various security vulnerabilities
that come up. There shall be use of automated password managers along with the alerts on
password change at frequent intervals. The use of common passwords like name, DOB etc.
shall be avoided.
The critical applications associated with Aztek must be installed in the devices owned by the
employees but shall be accessible only when the device is connected to the corporate network.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





