Comprehensive Report on IT Risk Management for the Commonwealth Bank
VerifiedAdded on 2022/11/25
|9
|2558
|296
Report
AI Summary
This report delves into the critical aspects of IT risk management, encompassing the development and management of security control policies and a detailed risk assessment process. Part A focuses on the 'My Health Record' system, examining the roles of doctors, nurses, and patients, and outlining specific policies, procedures, and managerial considerations for each user group to ensure data security and privacy. Part B shifts the focus to the Commonwealth Bank of Australia, identifying key IT risks such as cyber threats, online transaction failures, and data loss. The report analyzes the consequences of these risks and proposes mitigation strategies, including the incorporation of firewalls, advanced e-commerce systems, and cloud infrastructure, culminating in a risk register to prioritize and manage these threats effectively. The report utilizes user authentication and role-based access control to enhance security.

Running head: REPORT ON IT RISK MANAGEMENT
REPORT
ON
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
REPORT
ON
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT risk management
Table of Contents
Part A: Plan, Develop and Manage the security control policy.................................................2
Introduction-...........................................................................................................................2
Discussion:.............................................................................................................................2
Doctor-...............................................................................................................................3
Nurse-.................................................................................................................................4
Patients-..............................................................................................................................4
Conclusion:............................................................................................................................5
Part B: Risk Assessment Process...............................................................................................5
Commonwealth Bank Australia & IT system:.......................................................................5
Identify the Risk:....................................................................................................................6
Consequences of the identified Risk:.....................................................................................6
Risk Register:.........................................................................................................................7
Table of Contents
Part A: Plan, Develop and Manage the security control policy.................................................2
Introduction-...........................................................................................................................2
Discussion:.............................................................................................................................2
Doctor-...............................................................................................................................3
Nurse-.................................................................................................................................4
Patients-..............................................................................................................................4
Conclusion:............................................................................................................................5
Part B: Risk Assessment Process...............................................................................................5
Commonwealth Bank Australia & IT system:.......................................................................5
Identify the Risk:....................................................................................................................6
Consequences of the identified Risk:.....................................................................................6
Risk Register:.........................................................................................................................7

2IT risk management
Part A: Plan, Develop and Manage the security control policy
Introduction-
The primary objective of this report is to elaborate the functionalities as well as the
offered features of an information technology system which is incorporated in the Australian
Commonwealth Government in order to monitor and keep the track of eth individual’s health
conditions. Followed by this aspect it has been also noticed that the approached system also
consist several other key functionalities as well as the system will be handled by many of the
users such as the patients, nurse, doctors. Hence, it is highly important to restrict the
information access as per the user consent (Bidargaddi et al., 2018). Being a Chief
Information officer it is essential to develop and elaborate such Information Technology data
access policies due to which the approached system will meet the desired objectives as well
as will also mitigate the risk factors present in the nominated scope.
Discussion:
Followed by the above consideration it has been noticed that in the approached
system there is a significance of several users which includes the Doctor, Patients and the
Nurse. Hence, furthermore in this paper it will briefly discuss about the information
technology data access policies, procedures as well as the purpose for each of the identified
users in order to provide enhancement in the services of the approached IT system.
The information access control in an IT system it nothing but the process to protect
the data from the external threats as well as from the unauthorized access hence, it is highly
important to establish an effective access control policy into an organizational security
infrastructure in order to restrict the informative contents and other personal data from
unauthorized user access. Following this aspect the Government of Australian
Commonwealth has decided to enable an effective security control system by which it will
provide security to the contents as well as it will also provide protection to the contents with
its respective users (Chen et al., 2018).
Doctor-
Purpose: Followed by the above mentioned aspects it has been noticed that there is a
significant impact data access controls on the privacy of the patients. Hence, the primary
purpose behind implementing access control policies for the doctor is to provide more
customized services for a Doctor. As due to the incorporation of the access security control
policies into the My Health Record app will provide the accessibility to the relative contents
about the patients (Mendelson 2018).
Policy: Considering the above discussed aspect it is essential to implement effective access
control policies which includes the incorporation of User Authentication policy, as due to
this individual user will get to login to the application with an unique password. Along with
the above security control policy it is also important to adopt the Role-Based Access Control
due to which the user will only get to access the data which is available to that particular user
designation (Hu et al., 2015).
Procedure: With the purpose to enable the above mentioned security policy the IT system
needs to adopt the effective user authentication policy as it will help to reduce the
Part A: Plan, Develop and Manage the security control policy
Introduction-
The primary objective of this report is to elaborate the functionalities as well as the
offered features of an information technology system which is incorporated in the Australian
Commonwealth Government in order to monitor and keep the track of eth individual’s health
conditions. Followed by this aspect it has been also noticed that the approached system also
consist several other key functionalities as well as the system will be handled by many of the
users such as the patients, nurse, doctors. Hence, it is highly important to restrict the
information access as per the user consent (Bidargaddi et al., 2018). Being a Chief
Information officer it is essential to develop and elaborate such Information Technology data
access policies due to which the approached system will meet the desired objectives as well
as will also mitigate the risk factors present in the nominated scope.
Discussion:
Followed by the above consideration it has been noticed that in the approached
system there is a significance of several users which includes the Doctor, Patients and the
Nurse. Hence, furthermore in this paper it will briefly discuss about the information
technology data access policies, procedures as well as the purpose for each of the identified
users in order to provide enhancement in the services of the approached IT system.
The information access control in an IT system it nothing but the process to protect
the data from the external threats as well as from the unauthorized access hence, it is highly
important to establish an effective access control policy into an organizational security
infrastructure in order to restrict the informative contents and other personal data from
unauthorized user access. Following this aspect the Government of Australian
Commonwealth has decided to enable an effective security control system by which it will
provide security to the contents as well as it will also provide protection to the contents with
its respective users (Chen et al., 2018).
Doctor-
Purpose: Followed by the above mentioned aspects it has been noticed that there is a
significant impact data access controls on the privacy of the patients. Hence, the primary
purpose behind implementing access control policies for the doctor is to provide more
customized services for a Doctor. As due to the incorporation of the access security control
policies into the My Health Record app will provide the accessibility to the relative contents
about the patients (Mendelson 2018).
Policy: Considering the above discussed aspect it is essential to implement effective access
control policies which includes the incorporation of User Authentication policy, as due to
this individual user will get to login to the application with an unique password. Along with
the above security control policy it is also important to adopt the Role-Based Access Control
due to which the user will only get to access the data which is available to that particular user
designation (Hu et al., 2015).
Procedure: With the purpose to enable the above mentioned security policy the IT system
needs to adopt the effective user authentication policy as it will help to reduce the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT risk management
unauthorized access to the patient’s data. Incorporation of strong password to control the data
access will also significantly help to reduce the unauthorized access (Liu et al., 2017).
Managerial: Thus, it can be stated that after the incorporation of the above mentioned
policies the “My Health Record App” will show only the information which is related to the
Doctor’s consent.
Nurse-
Purpose: The primary object behind incorporating the security access control policies into
the information access of the Nurse is to provide access to the restricted data followed by
which a Nurse will only access to the necessary data to assist a doctor and attend a Patient.
Policy: The Role Based Access Control policy as well as the User authentication policies
needs to be incorporated into the application will surely provide an effective security control
to the user information (Mccullagh et al., 2019).
Procedure: This above mentioned procedure will work by enabling the password
authentication policy if each of the user in this case. Due to this the user can login to the
system and will able to access the related content available in that user designation by the
Role Based Access Control policy.
Managerial: Due to the incorporation of the above selected policies, Nurses will be able to
visit the app and can also get the access of those data which are necessary to keep the health
record of the patients as well as will help to make effective decisions.
Patients-
Purpose: The primary objective behind restricting the access of the information for the
Patients in order to protect the privacy of the other users as well as the stakeholders. As it has
been noticed that due to the less effective access control policies for this types of user will
hold a significant impact on the data privacy of the IT system.
Policy: Similar to the above mentioned users, in this case also the incorporation of the Role
based access control system is effective as it will help to restrict the data accessibility.
Procedure: This policy will work by differentiating the user accounts based on the features
and functionalities needed by that particular user. Followed by this, effective authentication
procedure will also help to enhance this security control process.
Managerial: This process will work by providing the access of the required data which will
help the system as well as the Patients to keep the track of the health condition. Along with
that these types of user will get the access of the extracted doctor’s data followed by which
the patients can book an appointment of take advice from.
Conclusion:
Followed by the above discussion lastly it can be concluded that considering the
application of the approached IT system to keep track of the health record of the patients,
there is a significant impact of the IT management security as well as the access control
policies due to which it will protect the user data from the unauthorized access. Hence, in this
unauthorized access to the patient’s data. Incorporation of strong password to control the data
access will also significantly help to reduce the unauthorized access (Liu et al., 2017).
Managerial: Thus, it can be stated that after the incorporation of the above mentioned
policies the “My Health Record App” will show only the information which is related to the
Doctor’s consent.
Nurse-
Purpose: The primary object behind incorporating the security access control policies into
the information access of the Nurse is to provide access to the restricted data followed by
which a Nurse will only access to the necessary data to assist a doctor and attend a Patient.
Policy: The Role Based Access Control policy as well as the User authentication policies
needs to be incorporated into the application will surely provide an effective security control
to the user information (Mccullagh et al., 2019).
Procedure: This above mentioned procedure will work by enabling the password
authentication policy if each of the user in this case. Due to this the user can login to the
system and will able to access the related content available in that user designation by the
Role Based Access Control policy.
Managerial: Due to the incorporation of the above selected policies, Nurses will be able to
visit the app and can also get the access of those data which are necessary to keep the health
record of the patients as well as will help to make effective decisions.
Patients-
Purpose: The primary objective behind restricting the access of the information for the
Patients in order to protect the privacy of the other users as well as the stakeholders. As it has
been noticed that due to the less effective access control policies for this types of user will
hold a significant impact on the data privacy of the IT system.
Policy: Similar to the above mentioned users, in this case also the incorporation of the Role
based access control system is effective as it will help to restrict the data accessibility.
Procedure: This policy will work by differentiating the user accounts based on the features
and functionalities needed by that particular user. Followed by this, effective authentication
procedure will also help to enhance this security control process.
Managerial: This process will work by providing the access of the required data which will
help the system as well as the Patients to keep the track of the health condition. Along with
that these types of user will get the access of the extracted doctor’s data followed by which
the patients can book an appointment of take advice from.
Conclusion:
Followed by the above discussion lastly it can be concluded that considering the
application of the approached IT system to keep track of the health record of the patients,
there is a significant impact of the IT management security as well as the access control
policies due to which it will protect the user data from the unauthorized access. Hence, in this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT risk management
paper it has effectively discussed about the access control policies for each possible user in
order to provide effective security to the user information.
Part B: Risk Assessment Process
The primary objective behind delivering this discussion is to effectively elaborate the
risk assessment plan for Australian Commonwealth Bank. It has been observed that in the
working procedure of this bank there is a huge impact of the information technology. Hence,
furthermore in this paper it will discuss about the identified IT risk as well as its mitigation
approaches.
Commonwealth Bank Australia & IT system:
The nominated bank in one of the most efficient banks present in Australia which has
expanded their business work wide. Followed by their business expansion it has been also
noticed that the selected bank offers one of the most effective financial services as it has
effective data management system. Considering the business services of the Commonwealth
Bank of Australia it has been noticed that there is a significant application of Information
Technology present which has enhanced the services of the bank. Those system includes the
IT database as well as the mobile banking process. Followed by the above mentioned
business aspects as well as the incorporated IT systems it has been noticed that there are
several significant limitations present related to the application of information technology in
the banking sector (Luo et al., 2016). Furthermore, in this paper a detail elaboration on those
limitations is provided below.
Identify the Risk:
One of the most significant risk present in the nominated case scenario is related to the
cyber security as it has been identified from the investigation that in the financial
industries there is a significant impact of the privacy of the financial data which holds the
ability to steal the money from the customer bank account.
There is also a significant impact present related to the threat present in the transaction
process as it is identified that in case of online financial transaction the money can get
hacked by the hackers.
Along with it due to the failure of the IT systems the work process of the bank can get
impacted (Ly 2015).
Apart from the above identified risk there is also a significant risk present related to the
data loss.
Along with it there is a huge risk present related to the cyber-attacks in the bank which
can harm the entire bank operations.
Consequences of the identified Risk:
Followed by the risks which has been identified from the above investigation it has been
noticed that there is several impactful consequences present in the business scope of the
nominated banking sector. Those determined consequences are listed below:
Due to the possibilities of cyber-attacks there are several impactful consequences present
which holds the capabilities to harm the entire banking process. After analyzing the
paper it has effectively discussed about the access control policies for each possible user in
order to provide effective security to the user information.
Part B: Risk Assessment Process
The primary objective behind delivering this discussion is to effectively elaborate the
risk assessment plan for Australian Commonwealth Bank. It has been observed that in the
working procedure of this bank there is a huge impact of the information technology. Hence,
furthermore in this paper it will discuss about the identified IT risk as well as its mitigation
approaches.
Commonwealth Bank Australia & IT system:
The nominated bank in one of the most efficient banks present in Australia which has
expanded their business work wide. Followed by their business expansion it has been also
noticed that the selected bank offers one of the most effective financial services as it has
effective data management system. Considering the business services of the Commonwealth
Bank of Australia it has been noticed that there is a significant application of Information
Technology present which has enhanced the services of the bank. Those system includes the
IT database as well as the mobile banking process. Followed by the above mentioned
business aspects as well as the incorporated IT systems it has been noticed that there are
several significant limitations present related to the application of information technology in
the banking sector (Luo et al., 2016). Furthermore, in this paper a detail elaboration on those
limitations is provided below.
Identify the Risk:
One of the most significant risk present in the nominated case scenario is related to the
cyber security as it has been identified from the investigation that in the financial
industries there is a significant impact of the privacy of the financial data which holds the
ability to steal the money from the customer bank account.
There is also a significant impact present related to the threat present in the transaction
process as it is identified that in case of online financial transaction the money can get
hacked by the hackers.
Along with it due to the failure of the IT systems the work process of the bank can get
impacted (Ly 2015).
Apart from the above identified risk there is also a significant risk present related to the
data loss.
Along with it there is a huge risk present related to the cyber-attacks in the bank which
can harm the entire bank operations.
Consequences of the identified Risk:
Followed by the risks which has been identified from the above investigation it has been
noticed that there is several impactful consequences present in the business scope of the
nominated banking sector. Those determined consequences are listed below:
Due to the possibilities of cyber-attacks there are several impactful consequences present
which holds the capabilities to harm the entire banking process. After analyzing the
5IT risk management
determined risks in has been noticed that in this banking sector the impact of
Ransomware as well as the DDos attack significantly harm the services by blocking or
hacking the entire IT system of the bank (Adusei 2015).
Followed by this it has been also noticed that there is a huge impact of transaction failure
as due to this the overall process as well as the reputation of the bank will get harmed.
Along with the above aspects due to the data loss the organization as well as the
customers will be significantly impacted since, in holds a harmful impact on the privacy
of the customers and the organization (Mardikar & Meyer 2015).
Apart from the above identified consequences there is a huge financial loss due to the
cyber-attacks.
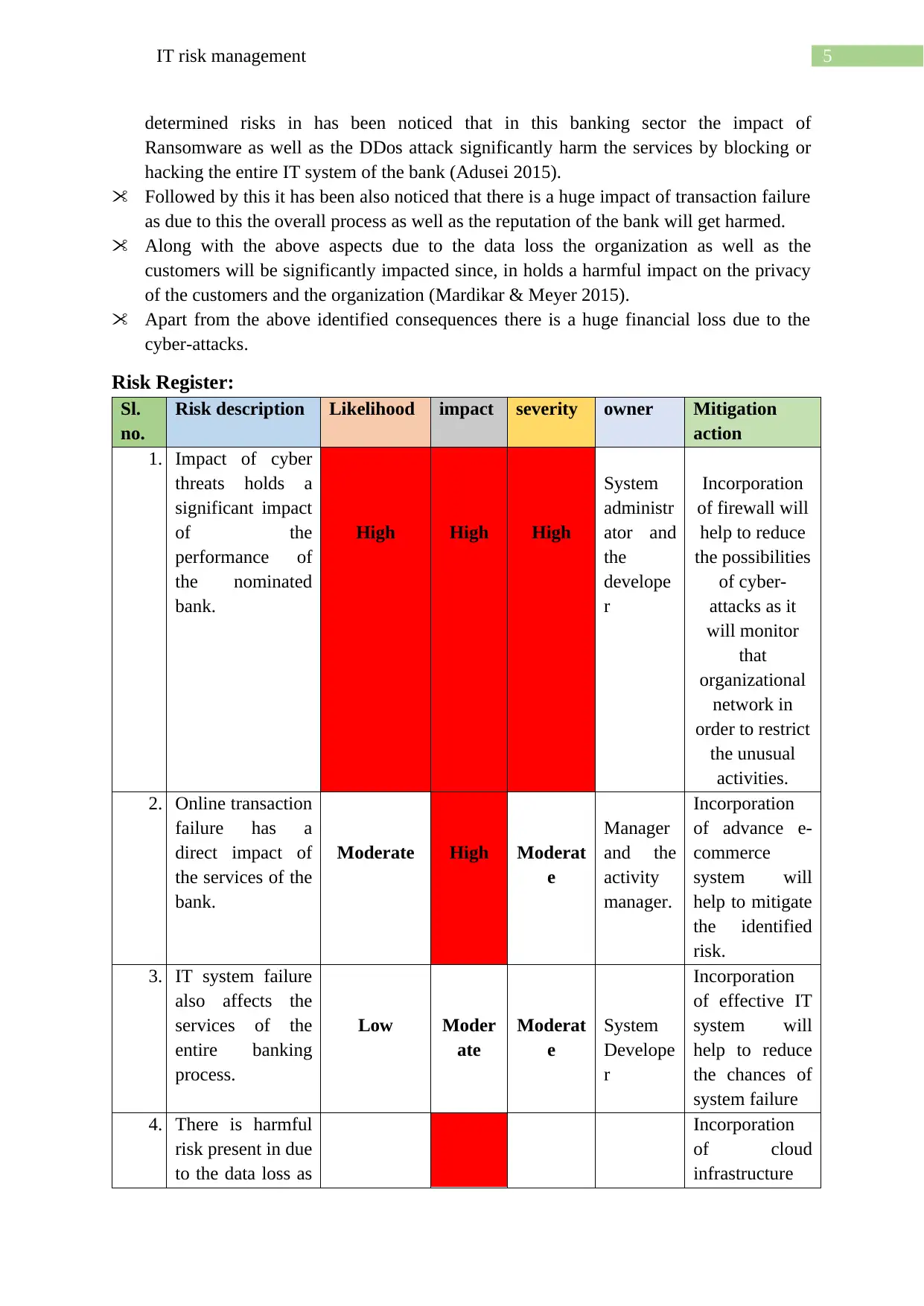
Risk Register:
Sl.
no.
Risk description Likelihood impact severity owner Mitigation
action
1. Impact of cyber
threats holds a
significant impact
of the
performance of
the nominated
bank.
High High High
System
administr
ator and
the
develope
r
Incorporation
of firewall will
help to reduce
the possibilities
of cyber-
attacks as it
will monitor
that
organizational
network in
order to restrict
the unusual
activities.
2. Online transaction
failure has a
direct impact of
the services of the
bank.
Moderate High Moderat
e
Manager
and the
activity
manager.
Incorporation
of advance e-
commerce
system will
help to mitigate
the identified
risk.
3. IT system failure
also affects the
services of the
entire banking
process.
Low Moder
ate
Moderat
e
System
Develope
r
Incorporation
of effective IT
system will
help to reduce
the chances of
system failure
4. There is harmful
risk present in due
to the data loss as
Incorporation
of cloud
infrastructure
determined risks in has been noticed that in this banking sector the impact of
Ransomware as well as the DDos attack significantly harm the services by blocking or
hacking the entire IT system of the bank (Adusei 2015).
Followed by this it has been also noticed that there is a huge impact of transaction failure
as due to this the overall process as well as the reputation of the bank will get harmed.
Along with the above aspects due to the data loss the organization as well as the
customers will be significantly impacted since, in holds a harmful impact on the privacy
of the customers and the organization (Mardikar & Meyer 2015).
Apart from the above identified consequences there is a huge financial loss due to the
cyber-attacks.
Risk Register:
Sl.
no.
Risk description Likelihood impact severity owner Mitigation
action
1. Impact of cyber
threats holds a
significant impact
of the
performance of
the nominated
bank.
High High High
System
administr
ator and
the
develope
r
Incorporation
of firewall will
help to reduce
the possibilities
of cyber-
attacks as it
will monitor
that
organizational
network in
order to restrict
the unusual
activities.
2. Online transaction
failure has a
direct impact of
the services of the
bank.
Moderate High Moderat
e
Manager
and the
activity
manager.
Incorporation
of advance e-
commerce
system will
help to mitigate
the identified
risk.
3. IT system failure
also affects the
services of the
entire banking
process.
Low Moder
ate
Moderat
e
System
Develope
r
Incorporation
of effective IT
system will
help to reduce
the chances of
system failure
4. There is harmful
risk present in due
to the data loss as
Incorporation
of cloud
infrastructure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
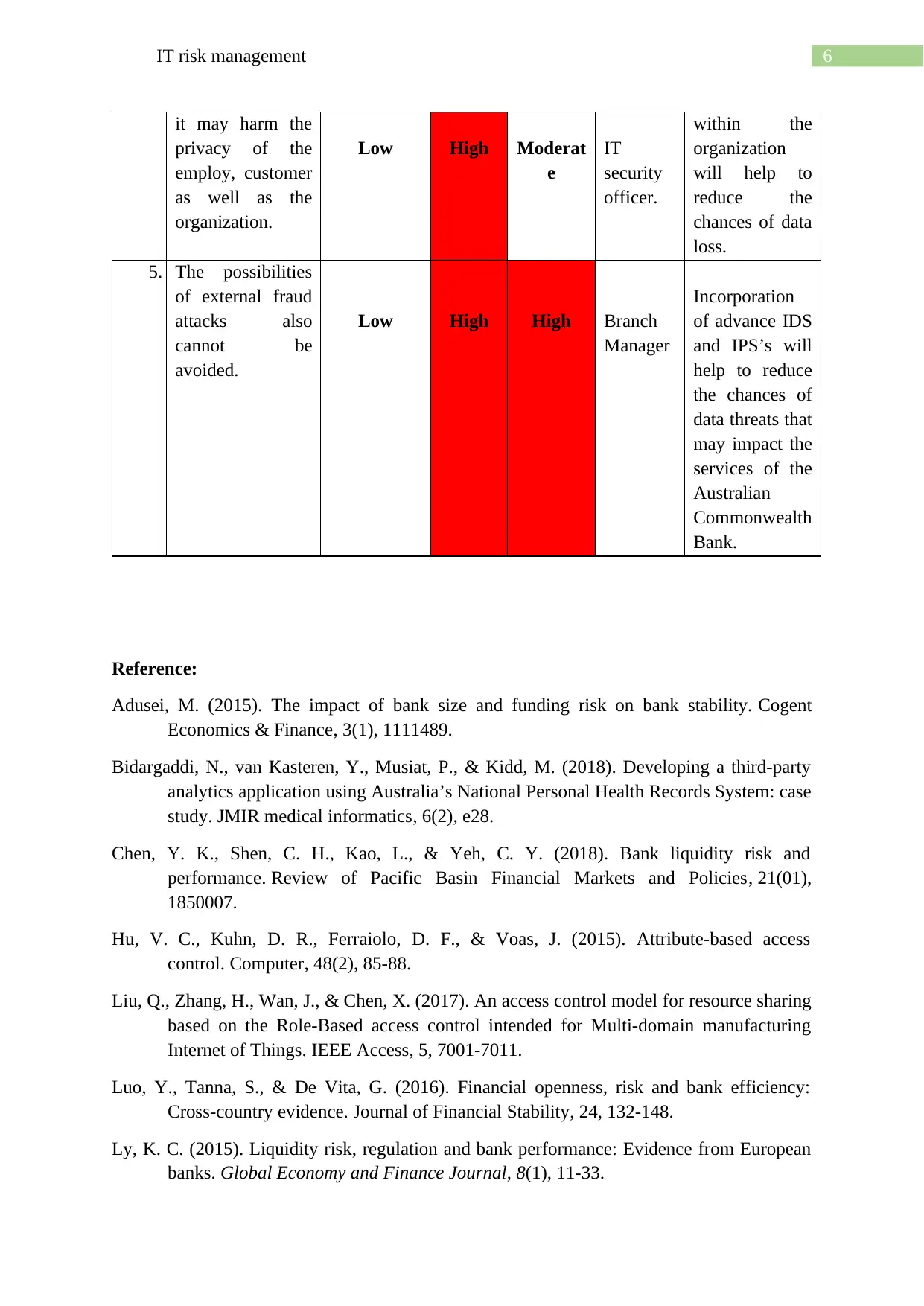
6IT risk management
it may harm the
privacy of the
employ, customer
as well as the
organization.
Low High Moderat
e
IT
security
officer.
within the
organization
will help to
reduce the
chances of data
loss.
5. The possibilities
of external fraud
attacks also
cannot be
avoided.
Low High High Branch
Manager
Incorporation
of advance IDS
and IPS’s will
help to reduce
the chances of
data threats that
may impact the
services of the
Australian
Commonwealth
Bank.
Reference:
Adusei, M. (2015). The impact of bank size and funding risk on bank stability. Cogent
Economics & Finance, 3(1), 1111489.
Bidargaddi, N., van Kasteren, Y., Musiat, P., & Kidd, M. (2018). Developing a third-party
analytics application using Australia’s National Personal Health Records System: case
study. JMIR medical informatics, 6(2), e28.
Chen, Y. K., Shen, C. H., Kao, L., & Yeh, C. Y. (2018). Bank liquidity risk and
performance. Review of Pacific Basin Financial Markets and Policies, 21(01),
1850007.
Hu, V. C., Kuhn, D. R., Ferraiolo, D. F., & Voas, J. (2015). Attribute-based access
control. Computer, 48(2), 85-88.
Liu, Q., Zhang, H., Wan, J., & Chen, X. (2017). An access control model for resource sharing
based on the Role-Based access control intended for Multi-domain manufacturing
Internet of Things. IEEE Access, 5, 7001-7011.
Luo, Y., Tanna, S., & De Vita, G. (2016). Financial openness, risk and bank efficiency:
Cross-country evidence. Journal of Financial Stability, 24, 132-148.
Ly, K. C. (2015). Liquidity risk, regulation and bank performance: Evidence from European
banks. Global Economy and Finance Journal, 8(1), 11-33.
it may harm the
privacy of the
employ, customer
as well as the
organization.
Low High Moderat
e
IT
security
officer.
within the
organization
will help to
reduce the
chances of data
loss.
5. The possibilities
of external fraud
attacks also
cannot be
avoided.
Low High High Branch
Manager
Incorporation
of advance IDS
and IPS’s will
help to reduce
the chances of
data threats that
may impact the
services of the
Australian
Commonwealth
Bank.
Reference:
Adusei, M. (2015). The impact of bank size and funding risk on bank stability. Cogent
Economics & Finance, 3(1), 1111489.
Bidargaddi, N., van Kasteren, Y., Musiat, P., & Kidd, M. (2018). Developing a third-party
analytics application using Australia’s National Personal Health Records System: case
study. JMIR medical informatics, 6(2), e28.
Chen, Y. K., Shen, C. H., Kao, L., & Yeh, C. Y. (2018). Bank liquidity risk and
performance. Review of Pacific Basin Financial Markets and Policies, 21(01),
1850007.
Hu, V. C., Kuhn, D. R., Ferraiolo, D. F., & Voas, J. (2015). Attribute-based access
control. Computer, 48(2), 85-88.
Liu, Q., Zhang, H., Wan, J., & Chen, X. (2017). An access control model for resource sharing
based on the Role-Based access control intended for Multi-domain manufacturing
Internet of Things. IEEE Access, 5, 7001-7011.
Luo, Y., Tanna, S., & De Vita, G. (2016). Financial openness, risk and bank efficiency:
Cross-country evidence. Journal of Financial Stability, 24, 132-148.
Ly, K. C. (2015). Liquidity risk, regulation and bank performance: Evidence from European
banks. Global Economy and Finance Journal, 8(1), 11-33.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT risk management
Mardikar, U. S., & Meyer, J. (2015). U.S. Patent No. 9,027,091. Washington, DC: U.S.
Patent and Trademark Office.
Mccullagh, C., Altman, L., Dickinson, M., & Williams, B. (2019). My Health Memory-A
lifetime medical record in the hands of patients and carers. International Journal of
Integrated Care (IJIC), 19.
Mendelson, D. (2018). The European Union General Data Protection Regulation (EU
2016/679) and the Australian My Health Record Scheme–A Comparative Study of
Consent to Data Processing Provisions.
Mardikar, U. S., & Meyer, J. (2015). U.S. Patent No. 9,027,091. Washington, DC: U.S.
Patent and Trademark Office.
Mccullagh, C., Altman, L., Dickinson, M., & Williams, B. (2019). My Health Memory-A
lifetime medical record in the hands of patients and carers. International Journal of
Integrated Care (IJIC), 19.
Mendelson, D. (2018). The European Union General Data Protection Regulation (EU
2016/679) and the Australian My Health Record Scheme–A Comparative Study of
Consent to Data Processing Provisions.

8IT risk management
Bibliography:
Neil, J. W., & Dumas, P. C. (2016). U.S. Patent No. 9,336,637. Washington, DC: U.S. Patent
and Trademark Office.
Rexer, P., & Patil, A. (2017). U.S. Patent No. 9,691,051. Washington, DC: U.S. Patent and
Trademark Office.
Tourani, R., Misra, S., Mick, T., & Panwar, G. (2017). Security, privacy, and access control
in information-centric networking: A survey. IEEE communications surveys &
tutorials, 20(1), 566-600.
Bibliography:
Neil, J. W., & Dumas, P. C. (2016). U.S. Patent No. 9,336,637. Washington, DC: U.S. Patent
and Trademark Office.
Rexer, P., & Patil, A. (2017). U.S. Patent No. 9,691,051. Washington, DC: U.S. Patent and
Trademark Office.
Tourani, R., Misra, S., Mick, T., & Panwar, G. (2017). Security, privacy, and access control
in information-centric networking: A survey. IEEE communications surveys &
tutorials, 20(1), 566-600.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





