IT Risk Management: Conducting a Risk Assessment and Developing a Security Policy
VerifiedAdded on 2023/04/22
|12
|3074
|482
AI Summary
This report discusses the issue of malware attack and highlights the key factors associated with it. It also provides a risk assessment matrix and a security policy for CSIRO.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: IT RISK MANAGEMENT 0
IT risk management
Report
Student name
IT risk management
Report
Student name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT RISK MANAGEMENT
1
Table of Contents
Introduction................................................................................................................................2
Part One: Conducting a Risk Assessment..................................................................................2
Description of the malware attack..........................................................................................2
Impact of malware attack.......................................................................................................2
Inherent risk assessment.........................................................................................................3
Key controls to mitigate the malware attack..........................................................................3
Residual risk assessment........................................................................................................4
ANSI B11.0.TR3 Risk Assessment Matrix............................................................................4
Part Two: Developing a Security Policy....................................................................................5
System security policy............................................................................................................5
Conclusion..................................................................................................................................7
References..................................................................................................................................8
1
Table of Contents
Introduction................................................................................................................................2
Part One: Conducting a Risk Assessment..................................................................................2
Description of the malware attack..........................................................................................2
Impact of malware attack.......................................................................................................2
Inherent risk assessment.........................................................................................................3
Key controls to mitigate the malware attack..........................................................................3
Residual risk assessment........................................................................................................4
ANSI B11.0.TR3 Risk Assessment Matrix............................................................................4
Part Two: Developing a Security Policy....................................................................................5
System security policy............................................................................................................5
Conclusion..................................................................................................................................7
References..................................................................................................................................8

IT RISK MANAGEMENT
2
Introduction
In this modern era, security of the data or information is very crucial or difficult and
every person uses internet connectivity that increases the rate of security risk. A recent study
evaluated that the Australian Universities are facing numerous security risks and issues such
as denial of service attack, hacking, data breaching, and malware and so on (Mathur, &
Hiranwal, 2013). This study will describe only malware attack and their impacts on the data
of Australian university and mitigation tools to control such kind of risks. Malware is a type
of computer software, which is developed to damage computer networks, servers, and
devices. In which hackers generate a large complex algorithm to generate the virus and
unwanted signals and transfer to the user's networks. The aim of this report is to analysis the
issue of malware attack and highlights the key factors, which are associated with the
malware. This study is divided into the main two parts such as conduction a risk assessment
for Australian university and developing a security policy for CSIRO.
Part One: Conducting a Risk Assessment
Description of the malware attack
Malware is defined as the security risk where malware software performs activities on
the consumer computer device without her knowledge. Today, it is one of the biggest issue or
risk faced by Australian university because they use the internet and computer networks for
communication purpose that are associated with the cyber-crimes. The recent investigation
identified that in 2015 the rate of malware attack has increased by 45% due to lack of security
and many Australian universities are using the computer systems to handle student’s datasets
which increase the issue of hacking (Egele, Scholte, Kirda, & Kruegel, 2012). Mainly
attackers use the botnet process to produce a huge amount of viruses and signals to reduce the
performance of the university networks.
Impact of malware attack
Malware is one of the danger security risk and threat that is growing rapidly and its
impacts on the personal data files or computer networks. First hackers send the virus or
unwanted signals to the users that create uncertainty in the system and hackers enter into the
university server to hack the data or information of students (Marpaung, Sain, & Lee, 2012).
2
Introduction
In this modern era, security of the data or information is very crucial or difficult and
every person uses internet connectivity that increases the rate of security risk. A recent study
evaluated that the Australian Universities are facing numerous security risks and issues such
as denial of service attack, hacking, data breaching, and malware and so on (Mathur, &
Hiranwal, 2013). This study will describe only malware attack and their impacts on the data
of Australian university and mitigation tools to control such kind of risks. Malware is a type
of computer software, which is developed to damage computer networks, servers, and
devices. In which hackers generate a large complex algorithm to generate the virus and
unwanted signals and transfer to the user's networks. The aim of this report is to analysis the
issue of malware attack and highlights the key factors, which are associated with the
malware. This study is divided into the main two parts such as conduction a risk assessment
for Australian university and developing a security policy for CSIRO.
Part One: Conducting a Risk Assessment
Description of the malware attack
Malware is defined as the security risk where malware software performs activities on
the consumer computer device without her knowledge. Today, it is one of the biggest issue or
risk faced by Australian university because they use the internet and computer networks for
communication purpose that are associated with the cyber-crimes. The recent investigation
identified that in 2015 the rate of malware attack has increased by 45% due to lack of security
and many Australian universities are using the computer systems to handle student’s datasets
which increase the issue of hacking (Egele, Scholte, Kirda, & Kruegel, 2012). Mainly
attackers use the botnet process to produce a huge amount of viruses and signals to reduce the
performance of the university networks.
Impact of malware attack
Malware is one of the danger security risk and threat that is growing rapidly and its
impacts on the personal data files or computer networks. First hackers send the virus or
unwanted signals to the users that create uncertainty in the system and hackers enter into the
university server to hack the data or information of students (Marpaung, Sain, & Lee, 2012).

IT RISK MANAGEMENT
3
Due to such kind of security risk, the university can suffer from the financial issues because
criminals demand money from victims to restore their private details. The recent survey
analysed that more than 68% users and Australian universities are facing the issue of malware
that detects the passwords of their system and collects data like pictures, address, financial
documents and many more (Holz, Steiner, Dahl, Biersack, & Freiling, 2008).
Inherent risk assessment
It is very important to identify the inherent risk in the system before looking at the
solution or prevention methods. In the Australian university, there are numerous inherent
risks which are currently facing by the university such as lack of security, use of old
computer networks, spam, jamming, a fraud case, and phishing. All these are the main
internet risk that can be reduced by adopting and developing security plans and strategies
(Idika, & Mathur, 2007). Jamming is a part of malware where hackers generate viruses with
the help of malicious, transfer to the user networks, and block their servers.
Key controls to mitigate the malware attack
Most hackers use the malware software to collect and identify the login ID and
password of the user personal systems and Australian university uses the computer devices to
store data of students. It is observed that lack of security and use of unauthentic networks
both are major key factors which are increasing the issue of malware attack (Bogdanoski, &
Risteski, 2011). To control and monitor such kind of security risk information technology
developed many security related tools such as firewall software, robust technology,
encryption, and antivirus and cryptography technology. All these approaches can be used for
an Australian university to secure and protect their personal data from the attackers and it
helps to reduce the rate of malware attack.
Encryption is a process, which is used to convert the information or data files into a
form of code, which cannot be hacked by the criminals because they required the private key
to decrypt the information. University can develop this technique because they communicate
with students and parents by using Gmail, and other social networks so, they can secure the
information of students by encryption (Humphreys, 2008). Firewall is one of the best
software that has potential to detect the virus and malware from the networks and computer
system and provided notification on the computer screen by which users and management
team can easily block them. To reduce the spam, fraud and unwanted links they can design
the robust technique that provides a way to block spam and virus from the server. Moreover,
3
Due to such kind of security risk, the university can suffer from the financial issues because
criminals demand money from victims to restore their private details. The recent survey
analysed that more than 68% users and Australian universities are facing the issue of malware
that detects the passwords of their system and collects data like pictures, address, financial
documents and many more (Holz, Steiner, Dahl, Biersack, & Freiling, 2008).
Inherent risk assessment
It is very important to identify the inherent risk in the system before looking at the
solution or prevention methods. In the Australian university, there are numerous inherent
risks which are currently facing by the university such as lack of security, use of old
computer networks, spam, jamming, a fraud case, and phishing. All these are the main
internet risk that can be reduced by adopting and developing security plans and strategies
(Idika, & Mathur, 2007). Jamming is a part of malware where hackers generate viruses with
the help of malicious, transfer to the user networks, and block their servers.
Key controls to mitigate the malware attack
Most hackers use the malware software to collect and identify the login ID and
password of the user personal systems and Australian university uses the computer devices to
store data of students. It is observed that lack of security and use of unauthentic networks
both are major key factors which are increasing the issue of malware attack (Bogdanoski, &
Risteski, 2011). To control and monitor such kind of security risk information technology
developed many security related tools such as firewall software, robust technology,
encryption, and antivirus and cryptography technology. All these approaches can be used for
an Australian university to secure and protect their personal data from the attackers and it
helps to reduce the rate of malware attack.
Encryption is a process, which is used to convert the information or data files into a
form of code, which cannot be hacked by the criminals because they required the private key
to decrypt the information. University can develop this technique because they communicate
with students and parents by using Gmail, and other social networks so, they can secure the
information of students by encryption (Humphreys, 2008). Firewall is one of the best
software that has potential to detect the virus and malware from the networks and computer
system and provided notification on the computer screen by which users and management
team can easily block them. To reduce the spam, fraud and unwanted links they can design
the robust technique that provides a way to block spam and virus from the server. Moreover,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT RISK MANAGEMENT
4
they can adopt an IT team which can help to control and manage the performance and
security of their computer networks and devices. There are a few other steps, which can be
used to handle the issues of malware, which are the following:
Avoid the fraud and spam emails from the system
Do not click on any unwanted links because they are developed by the hackers to
access user’s peripheral devices
Use only authentic networks
Follow the proper configuration process to avoid the problem of conflict
Turn on antivirus and firewall software
Update software on a regular basis
Install and enable encryption technology to improve the security of the data
Avoid use of third-party applications
Patches and updates for all the systems
Utility softwares use in administrative systems
If any malware or traffic signal found in the server immediately contact with the IT
team to reduce the rate of cyber-crimes
Residual risk assessment
To access the residual risk the management team of the university requires for
determining the drawbacks of the security tools and above mitigation, tools can reduce the
inherent security risk. Antivirus is a very old security technique, which takes more time to
detect the virus from the computer and it, can automatically turn off which can increase the
residual risk.
Today, most users use the third party applications, which are produced by the
attackers to identify the account details of the users. Therefore, during the communication,
process if university enables the encryption technology and use the unauthentic servers then it
can create a big issue in the system and they can suffer from the security risks. The main
problem of firewall software is that it can affect the performance of the computer system and
hackers can easily enter into the server.
The encryption technique also increasing the suspicion by which the university can
suffer from the further security risks if they use the public key encryption rather than a
4
they can adopt an IT team which can help to control and manage the performance and
security of their computer networks and devices. There are a few other steps, which can be
used to handle the issues of malware, which are the following:
Avoid the fraud and spam emails from the system
Do not click on any unwanted links because they are developed by the hackers to
access user’s peripheral devices
Use only authentic networks
Follow the proper configuration process to avoid the problem of conflict
Turn on antivirus and firewall software
Update software on a regular basis
Install and enable encryption technology to improve the security of the data
Avoid use of third-party applications
Patches and updates for all the systems
Utility softwares use in administrative systems
If any malware or traffic signal found in the server immediately contact with the IT
team to reduce the rate of cyber-crimes
Residual risk assessment
To access the residual risk the management team of the university requires for
determining the drawbacks of the security tools and above mitigation, tools can reduce the
inherent security risk. Antivirus is a very old security technique, which takes more time to
detect the virus from the computer and it, can automatically turn off which can increase the
residual risk.
Today, most users use the third party applications, which are produced by the
attackers to identify the account details of the users. Therefore, during the communication,
process if university enables the encryption technology and use the unauthentic servers then it
can create a big issue in the system and they can suffer from the security risks. The main
problem of firewall software is that it can affect the performance of the computer system and
hackers can easily enter into the server.
The encryption technique also increasing the suspicion by which the university can
suffer from the further security risks if they use the public key encryption rather than a
IT RISK MANAGEMENT
5
private key. Certification problem also occurs in the encryption and most public key uses the
third party systems to certify the reliability of the public key, which can enhance the rate of
malware and data breach problems.
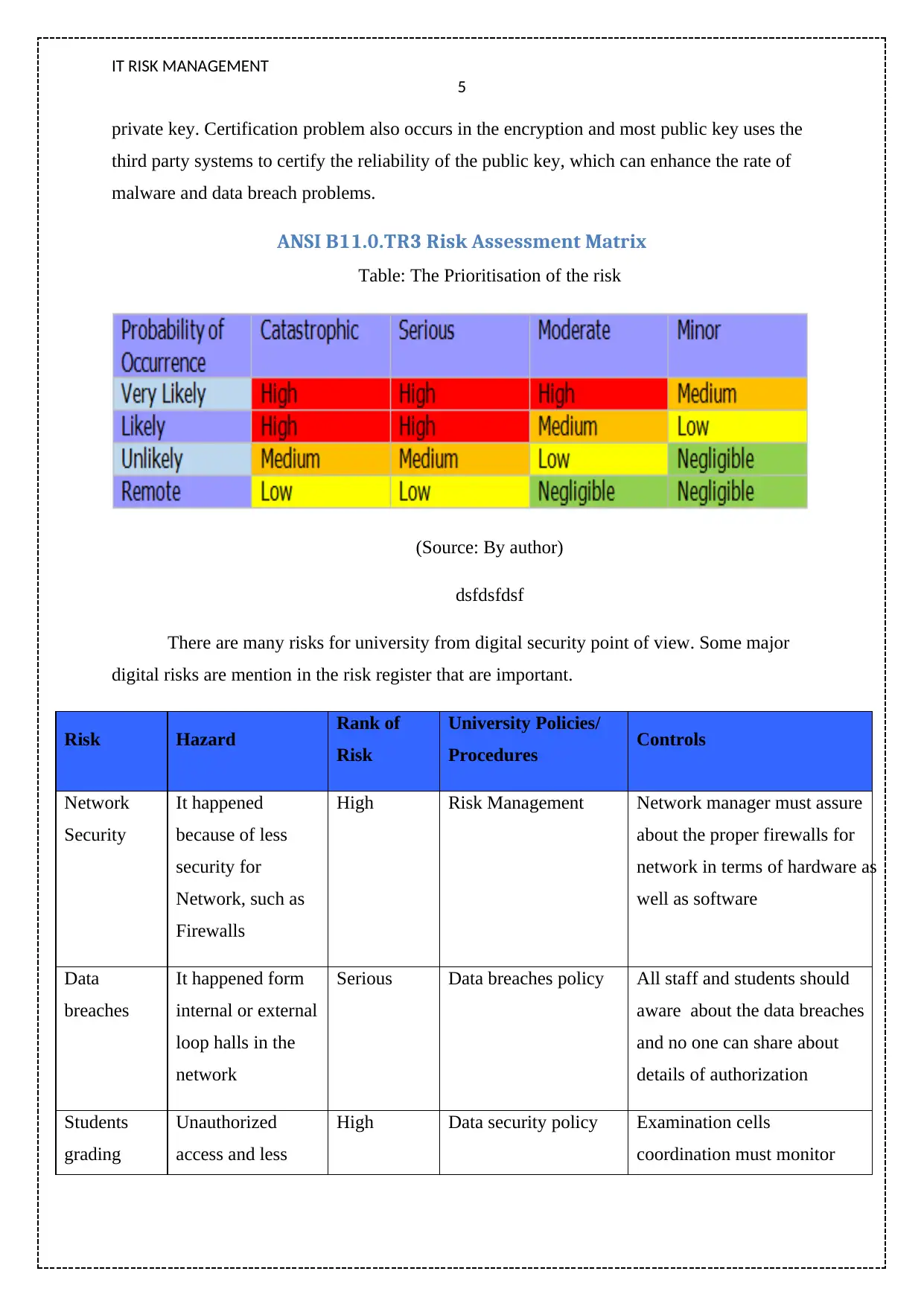
ANSI B11.0.TR3 Risk Assessment Matrix
Table: The Prioritisation of the risk
(Source: By author)
dsfdsfdsf
There are many risks for university from digital security point of view. Some major
digital risks are mention in the risk register that are important.
Risk Hazard Rank of
Risk
University Policies/
Procedures Controls
Network
Security
It happened
because of less
security for
Network, such as
Firewalls
High Risk Management Network manager must assure
about the proper firewalls for
network in terms of hardware as
well as software
Data
breaches
It happened form
internal or external
loop halls in the
network
Serious Data breaches policy All staff and students should
aware about the data breaches
and no one can share about
details of authorization
Students
grading
Unauthorized
access and less
High Data security policy Examination cells
coordination must monitor
5
private key. Certification problem also occurs in the encryption and most public key uses the
third party systems to certify the reliability of the public key, which can enhance the rate of
malware and data breach problems.
ANSI B11.0.TR3 Risk Assessment Matrix
Table: The Prioritisation of the risk
(Source: By author)
dsfdsfdsf
There are many risks for university from digital security point of view. Some major
digital risks are mention in the risk register that are important.
Risk Hazard Rank of
Risk
University Policies/
Procedures Controls
Network
Security
It happened
because of less
security for
Network, such as
Firewalls
High Risk Management Network manager must assure
about the proper firewalls for
network in terms of hardware as
well as software
Data
breaches
It happened form
internal or external
loop halls in the
network
Serious Data breaches policy All staff and students should
aware about the data breaches
and no one can share about
details of authorization
Students
grading
Unauthorized
access and less
High Data security policy Examination cells
coordination must monitor
IT RISK MANAGEMENT
6
Risk Hazard Rank of
Risk
University Policies/
Procedures Controls
security in terms
of access
about accessing of the system
from unauthorized sources at
weekly basis.
Cyber-
attacks
It happened
because of not
updated system
Medium Software policy All the servers and system
should have their latest
updates and patches.
Server
Updating
It happened at the
time of server
updating process
Low Backup policies A backup server is providing
continuity of university work.
Electric
shock
It cause due to
equipment faults.
High Risk Management Students should guide before
the experiments by the lab
Supervisor
Eyes and
skin
Diseases
It happened
because of
excessive exposure
to non-ionising
radiation
Medium Radiation Safety
Policy
It managed by only Radiation
Safety Officer
Follow these things:
Appropriate Safety
glasses
Appropriate Hearing
protection
Mitigation of risks is requiring different frameworks. There are many standards for
mitigates the risk in a University. Digital risks are serious issues in front of university.
Therefore, they must follow different intends and policies for mitigation of these risks. In
below diagram an example is provided for understanding about the IT-risks.
6
Risk Hazard Rank of
Risk
University Policies/
Procedures Controls
security in terms
of access
about accessing of the system
from unauthorized sources at
weekly basis.
Cyber-
attacks
It happened
because of not
updated system
Medium Software policy All the servers and system
should have their latest
updates and patches.
Server
Updating
It happened at the
time of server
updating process
Low Backup policies A backup server is providing
continuity of university work.
Electric
shock
It cause due to
equipment faults.
High Risk Management Students should guide before
the experiments by the lab
Supervisor
Eyes and
skin
Diseases
It happened
because of
excessive exposure
to non-ionising
radiation
Medium Radiation Safety
Policy
It managed by only Radiation
Safety Officer
Follow these things:
Appropriate Safety
glasses
Appropriate Hearing
protection
Mitigation of risks is requiring different frameworks. There are many standards for
mitigates the risk in a University. Digital risks are serious issues in front of university.
Therefore, they must follow different intends and policies for mitigation of these risks. In
below diagram an example is provided for understanding about the IT-risks.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IT RISK MANAGEMENT
7
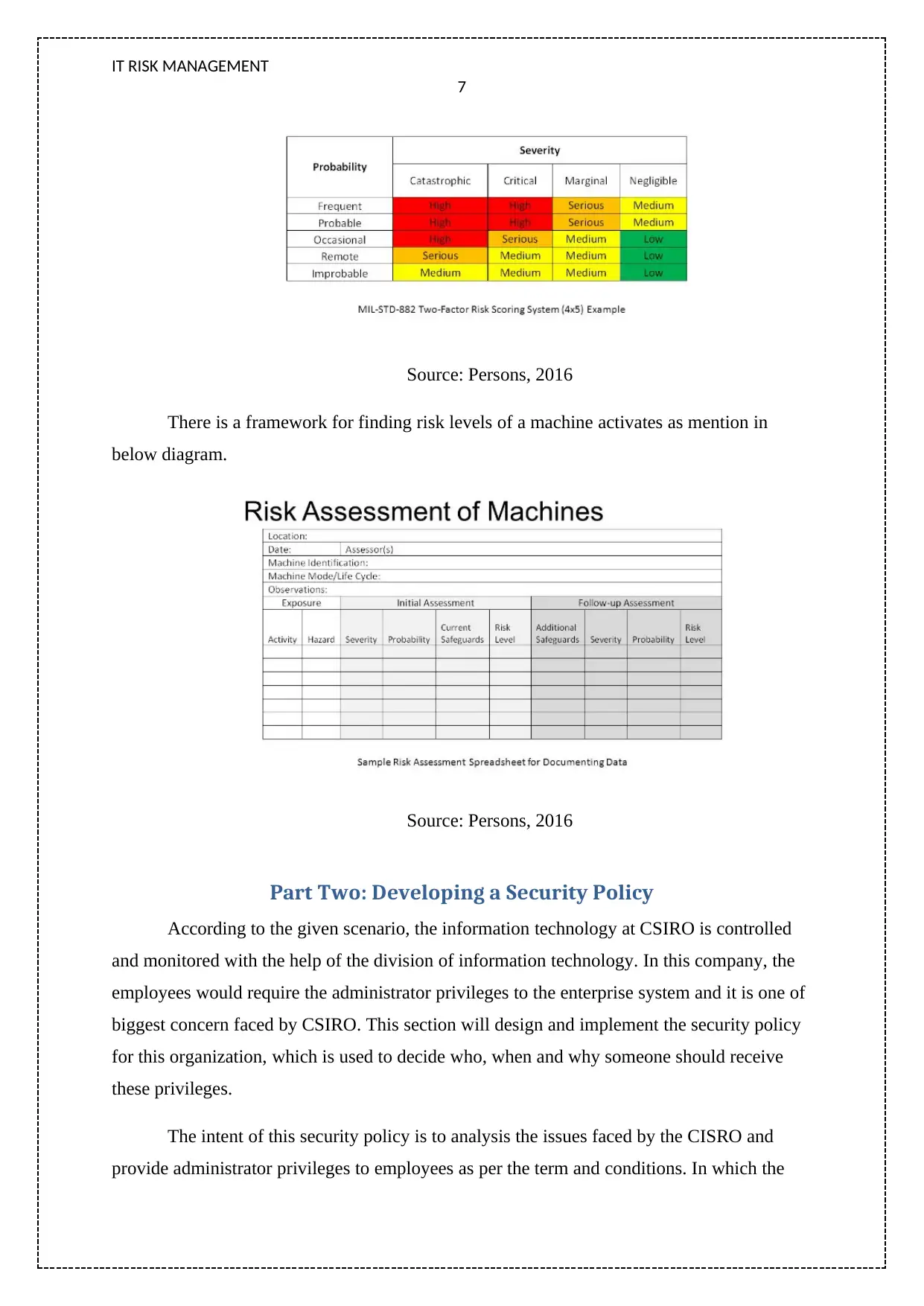
Source: Persons, 2016
There is a framework for finding risk levels of a machine activates as mention in
below diagram.
Source: Persons, 2016
Part Two: Developing a Security Policy
According to the given scenario, the information technology at CSIRO is controlled
and monitored with the help of the division of information technology. In this company, the
employees would require the administrator privileges to the enterprise system and it is one of
biggest concern faced by CSIRO. This section will design and implement the security policy
for this organization, which is used to decide who, when and why someone should receive
these privileges.
The intent of this security policy is to analysis the issues faced by the CISRO and
provide administrator privileges to employees as per the term and conditions. In which the
7
Source: Persons, 2016
There is a framework for finding risk levels of a machine activates as mention in
below diagram.
Source: Persons, 2016
Part Two: Developing a Security Policy
According to the given scenario, the information technology at CSIRO is controlled
and monitored with the help of the division of information technology. In this company, the
employees would require the administrator privileges to the enterprise system and it is one of
biggest concern faced by CSIRO. This section will design and implement the security policy
for this organization, which is used to decide who, when and why someone should receive
these privileges.
The intent of this security policy is to analysis the issues faced by the CISRO and
provide administrator privileges to employees as per the term and conditions. In which the

IT RISK MANAGEMENT
8
information technology team provide a stable and secure computing environment and
management team requires managing the administration privilege (Carroll, Van Der Merwe,
& Kotze, 2011). The management team can provide the administration account to their
employees according to their performance and criteria that will be decided by the manager.
The main objective of this policy is to protect and secure the administration accounts of the
CISRO and provide the privilege to the employees. The main reason for developing this
policy is to solve the issue of privilege to the enterprise system or workstation and improve
the security of their administration accounts. There are few steps can be used in some policies
that are the following:
System security policy
Security of the system is the very important factor for any organization and CISRO
uses the information technology team to control and manage the security related threats. In
this policy, the management team of CISRO can involve database user management, user
authentication, and operating system security (Starker, 2010). The security administrator can
take responsibility to control and manage the privilege of the accounts and the database
system can be handled by adopting the high level computer devices. The IT team to handle
the security related issues can use an authentication process and it helps them to solve the
issue of the privilege of the administration accounts. In the field of privilege management, the
security of administrative account is very difficult and the employment of the individual
plays a significant role in the administrator account. For example, in the database with
different usernames, it may be beneficial to control and manage the privileges available to
employees.
The end user security system can be developed for the CISRO organization, which
provides a platform to decide which employee require to access or privilege the administrator
account. The security administrator can decide which team or group member can be divided
into consumer group and then provide the administrator account to their employees (Li, Mao,
& Chen, 2007).
The information technology team and the employees can handle this security policy or
workers of the CISRO will enforce the guideline. Senior manager should provide the
administration privilege with an authentication technique to secure and private the
administration accounts. In future, this security policy will control and manage the
accessibility of administration accounts in the different departments and it can affect the
8
information technology team provide a stable and secure computing environment and
management team requires managing the administration privilege (Carroll, Van Der Merwe,
& Kotze, 2011). The management team can provide the administration account to their
employees according to their performance and criteria that will be decided by the manager.
The main objective of this policy is to protect and secure the administration accounts of the
CISRO and provide the privilege to the employees. The main reason for developing this
policy is to solve the issue of privilege to the enterprise system or workstation and improve
the security of their administration accounts. There are few steps can be used in some policies
that are the following:
System security policy
Security of the system is the very important factor for any organization and CISRO
uses the information technology team to control and manage the security related threats. In
this policy, the management team of CISRO can involve database user management, user
authentication, and operating system security (Starker, 2010). The security administrator can
take responsibility to control and manage the privilege of the accounts and the database
system can be handled by adopting the high level computer devices. The IT team to handle
the security related issues can use an authentication process and it helps them to solve the
issue of the privilege of the administration accounts. In the field of privilege management, the
security of administrative account is very difficult and the employment of the individual
plays a significant role in the administrator account. For example, in the database with
different usernames, it may be beneficial to control and manage the privileges available to
employees.
The end user security system can be developed for the CISRO organization, which
provides a platform to decide which employee require to access or privilege the administrator
account. The security administrator can decide which team or group member can be divided
into consumer group and then provide the administrator account to their employees (Li, Mao,
& Chen, 2007).
The information technology team and the employees can handle this security policy or
workers of the CISRO will enforce the guideline. Senior manager should provide the
administration privilege with an authentication technique to secure and private the
administration accounts. In future, this security policy will control and manage the
accessibility of administration accounts in the different departments and it can affect the

IT RISK MANAGEMENT
9
personal data or information of other employees if the employee provides the privilege to
their friends and other employees. By this security policy, other employees and the
department may affect which can reduce the performance and productivity of the CISRO
organization (Vacca, 2012). It is suggested that the CISRO can avoid the high-risk activities
by generating and producing a separate administration accounts for the employees and
another department, which do not need the administrative privileges such as reading Gmail,
reading and editing the general documents and using a web browser. CISRO can use the
administrative credentials only for performing application specific functions, which need
administrative privilege and automatically logout from the administrative accounts when not
in use. For security purpose, they can use the two-step verification process in which a specific
code is sent to the user, which is also called as one time password.
Conclusion
In conclusion, Digital risks are impact on the university reputation as well as business
processes in term of enrolment of students. This report is completely based on the security of
information and data and readers can expend their skills in the area of cyber-crimes or
attacks. This report also evaluated the security risk faced by the Australian university and
mitigation techniques to improve the security of the university private data. A security policy
is also developed for the CISRO to solve the issue of privilege for administrative accounts.
Finally, it is conclude that digital risks are considered in a high risks as well as serious
in few cases. Many risks are required serious attention for securing data, information and
many other things.
9
personal data or information of other employees if the employee provides the privilege to
their friends and other employees. By this security policy, other employees and the
department may affect which can reduce the performance and productivity of the CISRO
organization (Vacca, 2012). It is suggested that the CISRO can avoid the high-risk activities
by generating and producing a separate administration accounts for the employees and
another department, which do not need the administrative privileges such as reading Gmail,
reading and editing the general documents and using a web browser. CISRO can use the
administrative credentials only for performing application specific functions, which need
administrative privilege and automatically logout from the administrative accounts when not
in use. For security purpose, they can use the two-step verification process in which a specific
code is sent to the user, which is also called as one time password.
Conclusion
In conclusion, Digital risks are impact on the university reputation as well as business
processes in term of enrolment of students. This report is completely based on the security of
information and data and readers can expend their skills in the area of cyber-crimes or
attacks. This report also evaluated the security risk faced by the Australian university and
mitigation techniques to improve the security of the university private data. A security policy
is also developed for the CISRO to solve the issue of privilege for administrative accounts.
Finally, it is conclude that digital risks are considered in a high risks as well as serious
in few cases. Many risks are required serious attention for securing data, information and
many other things.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT RISK MANAGEMENT
10
References
Bogdanoski, M., & Risteski, A. (2011). Wireless network behaviour under ICMP ping flood
DOS attack and mitigation techniques. International Journal of Communication
Networks and Information Security (IJCNIS), 3(1), 6-10.
Carroll, M., Van Der Merwe, A., & Kotze, P. (2011). Secure cloud computing: Benefits,
risks, and controls. In Information Security South Africa (ISSA), 2011, 6(2),1-9
Egele, M., Scholte, T., Kirda, E., & Kruegel, C. (2012). A survey on automated dynamic
malware-analysis techniques and tools. ACM computing surveys (CSUR), 44(2), 6.
Holz, T., Steiner, M., Dahl, F., Biersack, E., & Freiling, F. C. (2008). Measurements and
Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm. LEET, 8(1),
1-9.
Humphreys, E. (2008). Information security management standards: Compliance, governance
and risk management. information security technical report, 13(4), 247-255.
Idika, N., & Mathur, A. P. (2007). A survey of malware detection techniques. Purdue
University, 48(2), 6.
Li, N., Mao, Z., & Chen, H. (2007). Usable mandatory integrity protection for operating
systems. In 2007 IEEE Symposium on Security and Privacy (SP, 6(5), 164-178
Marpaung, J. A., Sain, M., & Lee, H. J. (2012). Survey on malware evasion techniques: State
of the art and challenges. In Advanced Communication Technology (ICACT), 2012
14th International Conference on, 12(2), 744-749.
Mathur, K., & Hiranwal, S. (2013). A survey on techniques in detection and analysing
malware executable. International Journal of Advanced Research in Computer
Science and Software Engineering, 3(4), 12-14.
Parsons, E. (2016 , December 21). Risk Assessment: A Practical Guide to Assessing
Operational Risk. Retrieved from slideplayer.com:
https://slideplayer.com/slide/10726147/
10
References
Bogdanoski, M., & Risteski, A. (2011). Wireless network behaviour under ICMP ping flood
DOS attack and mitigation techniques. International Journal of Communication
Networks and Information Security (IJCNIS), 3(1), 6-10.
Carroll, M., Van Der Merwe, A., & Kotze, P. (2011). Secure cloud computing: Benefits,
risks, and controls. In Information Security South Africa (ISSA), 2011, 6(2),1-9
Egele, M., Scholte, T., Kirda, E., & Kruegel, C. (2012). A survey on automated dynamic
malware-analysis techniques and tools. ACM computing surveys (CSUR), 44(2), 6.
Holz, T., Steiner, M., Dahl, F., Biersack, E., & Freiling, F. C. (2008). Measurements and
Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm. LEET, 8(1),
1-9.
Humphreys, E. (2008). Information security management standards: Compliance, governance
and risk management. information security technical report, 13(4), 247-255.
Idika, N., & Mathur, A. P. (2007). A survey of malware detection techniques. Purdue
University, 48(2), 6.
Li, N., Mao, Z., & Chen, H. (2007). Usable mandatory integrity protection for operating
systems. In 2007 IEEE Symposium on Security and Privacy (SP, 6(5), 164-178
Marpaung, J. A., Sain, M., & Lee, H. J. (2012). Survey on malware evasion techniques: State
of the art and challenges. In Advanced Communication Technology (ICACT), 2012
14th International Conference on, 12(2), 744-749.
Mathur, K., & Hiranwal, S. (2013). A survey on techniques in detection and analysing
malware executable. International Journal of Advanced Research in Computer
Science and Software Engineering, 3(4), 12-14.
Parsons, E. (2016 , December 21). Risk Assessment: A Practical Guide to Assessing
Operational Risk. Retrieved from slideplayer.com:
https://slideplayer.com/slide/10726147/

IT RISK MANAGEMENT
11
Sarkar, K. R. (2010). Assessing insider threats to information security using technical,
behavioural and organizational measures. information security technical report, 15(3),
112-133.
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
11
Sarkar, K. R. (2010). Assessing insider threats to information security using technical,
behavioural and organizational measures. information security technical report, 15(3),
112-133.
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
1 out of 12
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)




