Understanding Access Control Models
VerifiedAdded on 2020/02/24
|11
|2081
|107
AI Summary
This assignment delves into the world of access control models, providing a comprehensive overview of four primary models: Discretionary Access Control (DAC), Mandatory Access Control (MAC), Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). Students will examine the strengths and weaknesses of each model, explore real-world applications, and gain insights into how these models contribute to securing information systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IT RISK MANAGEMENT
Assessment 1
[Student Name Here]
[Institution’s Name Here]
[Professor’s Name Here]
[Date Here]
Assessment 1
[Student Name Here]
[Institution’s Name Here]
[Professor’s Name Here]
[Date Here]
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT RISK MANAGEMENT 2
Table of Contents
Contents Page
Introduction........................................................................................3
IT security and Technology landscape......................................................3
Vulnerabilities and threats......................................................................4
Mitigation and the benefits.....................................................................5
IT Security Models & Access Controls....................................................5
Threats, vulnerabilities and access control.............................................5
Mitigation: Access control models (3 common types)...........................6
Benefits...................................................................................................6
IT Security Threat and risk assessment.....................................................7
IT risk assessment of threats..................................................................7
Mitigation procedures and benefits........................................................8
Conclusion...........................................................................................8
References............................................................................................9
Table of Contents
Contents Page
Introduction........................................................................................3
IT security and Technology landscape......................................................3
Vulnerabilities and threats......................................................................4
Mitigation and the benefits.....................................................................5
IT Security Models & Access Controls....................................................5
Threats, vulnerabilities and access control.............................................5
Mitigation: Access control models (3 common types)...........................6
Benefits...................................................................................................6
IT Security Threat and risk assessment.....................................................7
IT risk assessment of threats..................................................................7
Mitigation procedures and benefits........................................................8
Conclusion...........................................................................................8
References............................................................................................9

IT RISK MANAGEMENT 3
Introduction
Information technology and its affiliated components are today identified as important capital
tools that offer valid information for business success. This outcome has influenced the
application of IT components in different aspects of life, which has also contributed to the
prevalence of security issues (Teymouri & Ashoori, 2011). This report, therefore, offers an
assessment of the various security issues experienced in IT and their relation to the existing
technological landscape. Furthermore, the existing models and control mechanisms of these
security issues are highlighted, together with the commonly experienced threats and risks. In
all, the report gives a thorough evaluation of the security elements in IT including system
vulnerabilities and mitigation procedures.
IT security and Technology landscape
Technology has always held a common objective despite the advances and inventions that
have been seen throughout the years. In essence, the term will outline any element that makes
life easier, and none of these elements is more profound and effective as IT. Now, in the past,
the technological landscape focused on mainframe systems that delivered services to users
through complicated connections (Kuc, 2015). However, the modern landscape as shown in
the diagram below is predominantly user centred including the applications themselves that
use cognitive designs to enhance usability. Nevertheless, the same structure that enhances the
usability of technological components creates many vulnerabilities that affect the security of
modern technological systems (DSTO, 2016).
Introduction
Information technology and its affiliated components are today identified as important capital
tools that offer valid information for business success. This outcome has influenced the
application of IT components in different aspects of life, which has also contributed to the
prevalence of security issues (Teymouri & Ashoori, 2011). This report, therefore, offers an
assessment of the various security issues experienced in IT and their relation to the existing
technological landscape. Furthermore, the existing models and control mechanisms of these
security issues are highlighted, together with the commonly experienced threats and risks. In
all, the report gives a thorough evaluation of the security elements in IT including system
vulnerabilities and mitigation procedures.
IT security and Technology landscape
Technology has always held a common objective despite the advances and inventions that
have been seen throughout the years. In essence, the term will outline any element that makes
life easier, and none of these elements is more profound and effective as IT. Now, in the past,
the technological landscape focused on mainframe systems that delivered services to users
through complicated connections (Kuc, 2015). However, the modern landscape as shown in
the diagram below is predominantly user centred including the applications themselves that
use cognitive designs to enhance usability. Nevertheless, the same structure that enhances the
usability of technological components creates many vulnerabilities that affect the security of
modern technological systems (DSTO, 2016).
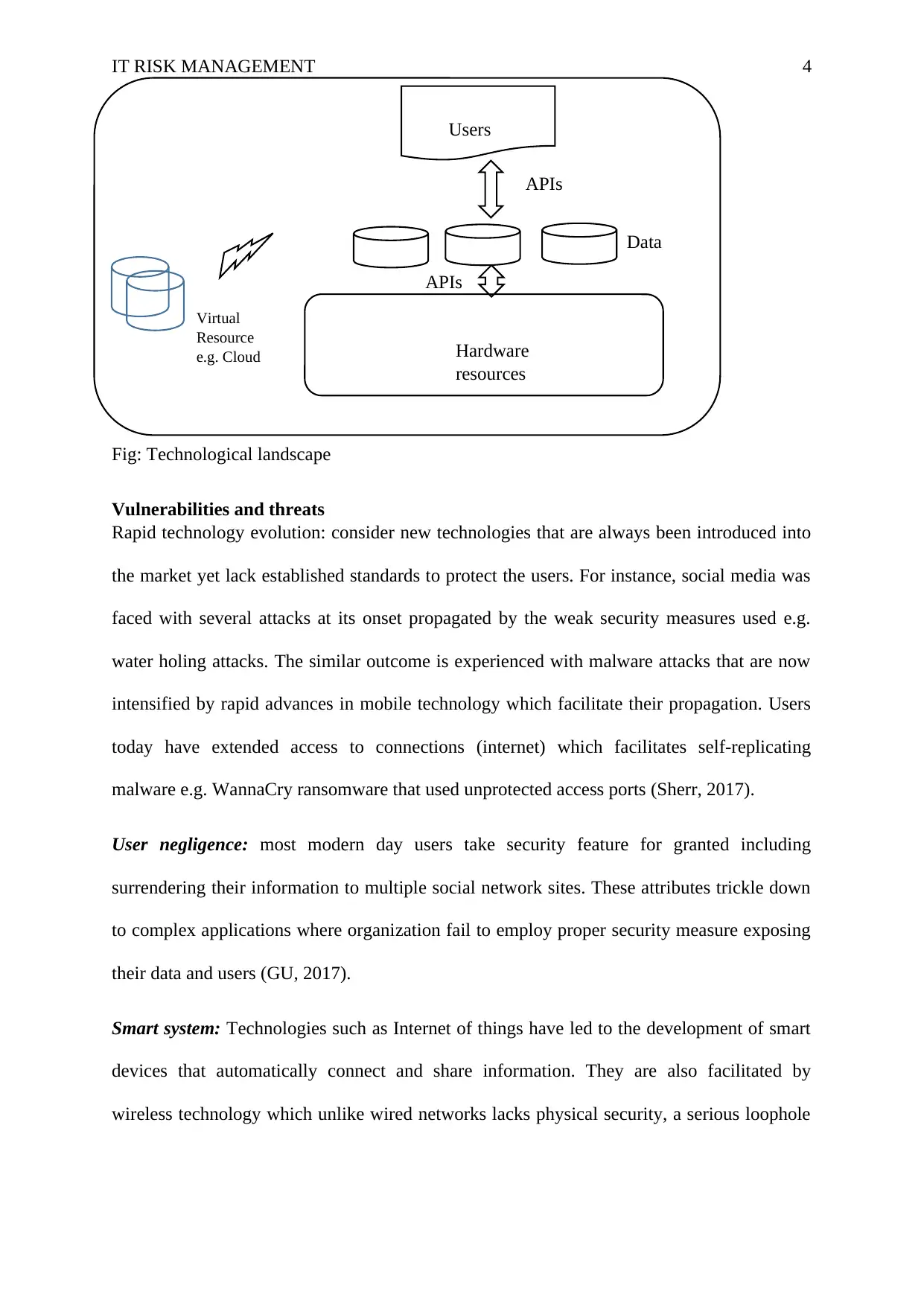
IT RISK MANAGEMENT 4
Fig: Technological landscape
Vulnerabilities and threats
Rapid technology evolution: consider new technologies that are always been introduced into
the market yet lack established standards to protect the users. For instance, social media was
faced with several attacks at its onset propagated by the weak security measures used e.g.
water holing attacks. The similar outcome is experienced with malware attacks that are now
intensified by rapid advances in mobile technology which facilitate their propagation. Users
today have extended access to connections (internet) which facilitates self-replicating
malware e.g. WannaCry ransomware that used unprotected access ports (Sherr, 2017).
User negligence: most modern day users take security feature for granted including
surrendering their information to multiple social network sites. These attributes trickle down
to complex applications where organization fail to employ proper security measure exposing
their data and users (GU, 2017).
Smart system: Technologies such as Internet of things have led to the development of smart
devices that automatically connect and share information. They are also facilitated by
wireless technology which unlike wired networks lacks physical security, a serious loophole
Users
Data
Hardware
resources
Virtual
Resource
e.g. Cloud
APIs
APIs
Fig: Technological landscape
Vulnerabilities and threats
Rapid technology evolution: consider new technologies that are always been introduced into
the market yet lack established standards to protect the users. For instance, social media was
faced with several attacks at its onset propagated by the weak security measures used e.g.
water holing attacks. The similar outcome is experienced with malware attacks that are now
intensified by rapid advances in mobile technology which facilitate their propagation. Users
today have extended access to connections (internet) which facilitates self-replicating
malware e.g. WannaCry ransomware that used unprotected access ports (Sherr, 2017).
User negligence: most modern day users take security feature for granted including
surrendering their information to multiple social network sites. These attributes trickle down
to complex applications where organization fail to employ proper security measure exposing
their data and users (GU, 2017).
Smart system: Technologies such as Internet of things have led to the development of smart
devices that automatically connect and share information. They are also facilitated by
wireless technology which unlike wired networks lacks physical security, a serious loophole
Users
Data
Hardware
resources
Virtual
Resource
e.g. Cloud
APIs
APIs
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
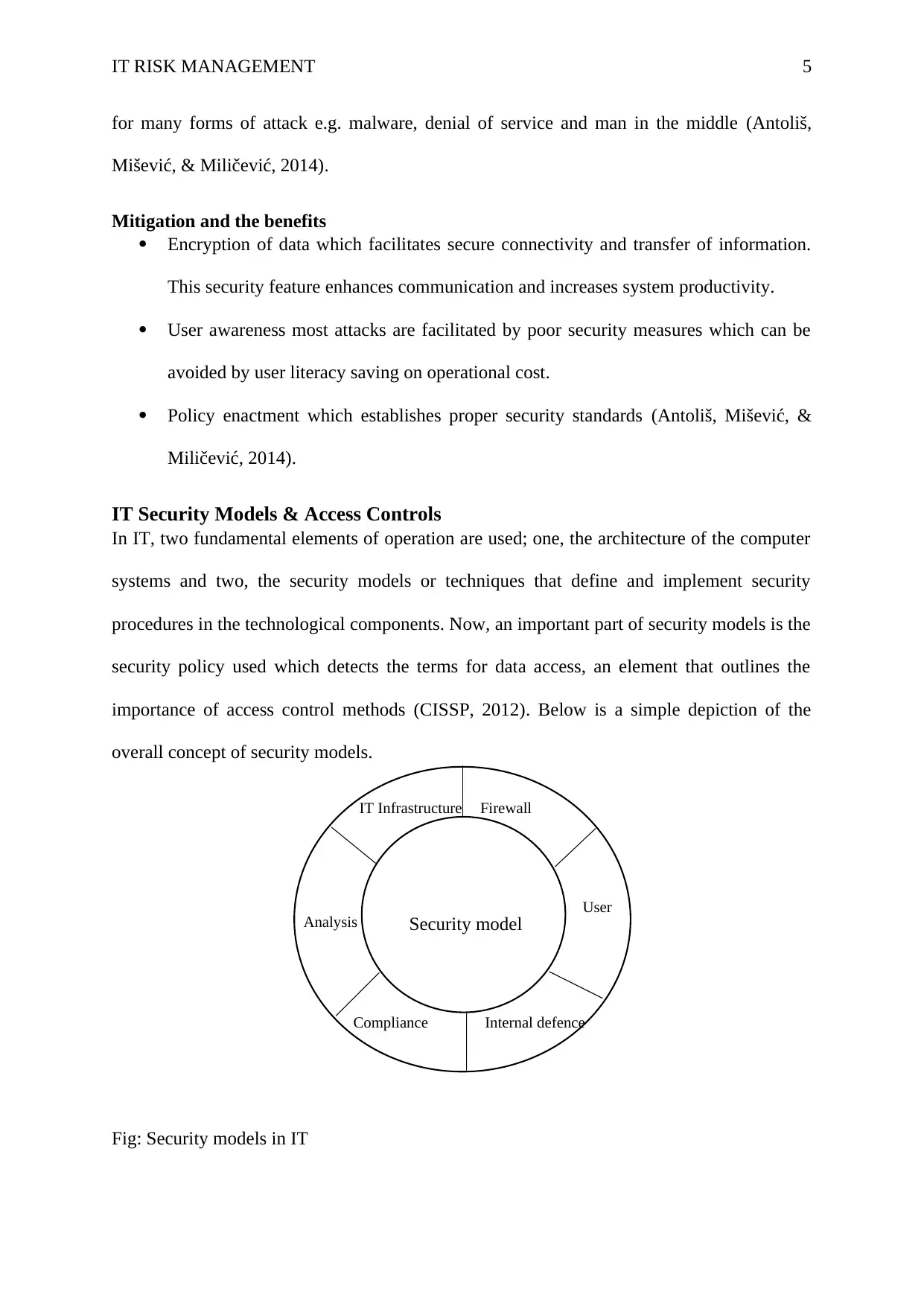
IT RISK MANAGEMENT 5
for many forms of attack e.g. malware, denial of service and man in the middle (Antoliš,
Mišević, & Miličević, 2014).
Mitigation and the benefits
Encryption of data which facilitates secure connectivity and transfer of information.
This security feature enhances communication and increases system productivity.
User awareness most attacks are facilitated by poor security measures which can be
avoided by user literacy saving on operational cost.
Policy enactment which establishes proper security standards (Antoliš, Mišević, &
Miličević, 2014).
IT Security Models & Access Controls
In IT, two fundamental elements of operation are used; one, the architecture of the computer
systems and two, the security models or techniques that define and implement security
procedures in the technological components. Now, an important part of security models is the
security policy used which detects the terms for data access, an element that outlines the
importance of access control methods (CISSP, 2012). Below is a simple depiction of the
overall concept of security models.
Fig: Security models in IT
Security model
IT Infrastructure Firewall
User
Internal defenceCompliance
Analysis
for many forms of attack e.g. malware, denial of service and man in the middle (Antoliš,
Mišević, & Miličević, 2014).
Mitigation and the benefits
Encryption of data which facilitates secure connectivity and transfer of information.
This security feature enhances communication and increases system productivity.
User awareness most attacks are facilitated by poor security measures which can be
avoided by user literacy saving on operational cost.
Policy enactment which establishes proper security standards (Antoliš, Mišević, &
Miličević, 2014).
IT Security Models & Access Controls
In IT, two fundamental elements of operation are used; one, the architecture of the computer
systems and two, the security models or techniques that define and implement security
procedures in the technological components. Now, an important part of security models is the
security policy used which detects the terms for data access, an element that outlines the
importance of access control methods (CISSP, 2012). Below is a simple depiction of the
overall concept of security models.
Fig: Security models in IT
Security model
IT Infrastructure Firewall
User
Internal defenceCompliance
Analysis

IT RISK MANAGEMENT 6
Threats, vulnerabilities and access control
In all the system and technologies used, security models particularly access control methods
denote the process subjects use to conduct certain actions (operations) to a given object (e.g.
files and data). These mechanisms are important when one considers the different
vulnerabilities and threats in place e.g. malware attacks that will interfere with legitimate
programs as they try to further the course of intruders. In other instances, network
vulnerabilities will be exploited to deny users services as a means to disrupt business
operations e.g. DOS. Furthermore, there are those threats that intercept data or traffic to earn
or benefit from other users work (Thion, 2008). Therefore, these threats and risk affect the
systems confidentiality, integrity and availability (CIA), an outcome fixed by access control.
Fig: Access control mechanisms
Mitigation: Access control models (3 common types)
Mandatory access control (MAC)- a static access model that assigns users clearance levels
thus improving accountability based on access levels and labels. Therefore, the model is
based on policy or matching criteria and not identity.
Discretionary access control – identity is used in this model where the owner decides who
access the content directly based on subject. Access control lists are good examples of tools
applying this model and so is the access seen in many operating systems.
Rule based access control – as the name suggests, access is done based on certain rules that
determine if access is denied or allowed (Cicnavi, 2012).
Subject Operation Object
Carries
out
Acts on
Threats, vulnerabilities and access control
In all the system and technologies used, security models particularly access control methods
denote the process subjects use to conduct certain actions (operations) to a given object (e.g.
files and data). These mechanisms are important when one considers the different
vulnerabilities and threats in place e.g. malware attacks that will interfere with legitimate
programs as they try to further the course of intruders. In other instances, network
vulnerabilities will be exploited to deny users services as a means to disrupt business
operations e.g. DOS. Furthermore, there are those threats that intercept data or traffic to earn
or benefit from other users work (Thion, 2008). Therefore, these threats and risk affect the
systems confidentiality, integrity and availability (CIA), an outcome fixed by access control.
Fig: Access control mechanisms
Mitigation: Access control models (3 common types)
Mandatory access control (MAC)- a static access model that assigns users clearance levels
thus improving accountability based on access levels and labels. Therefore, the model is
based on policy or matching criteria and not identity.
Discretionary access control – identity is used in this model where the owner decides who
access the content directly based on subject. Access control lists are good examples of tools
applying this model and so is the access seen in many operating systems.
Rule based access control – as the name suggests, access is done based on certain rules that
determine if access is denied or allowed (Cicnavi, 2012).
Subject Operation Object
Carries
out
Acts on
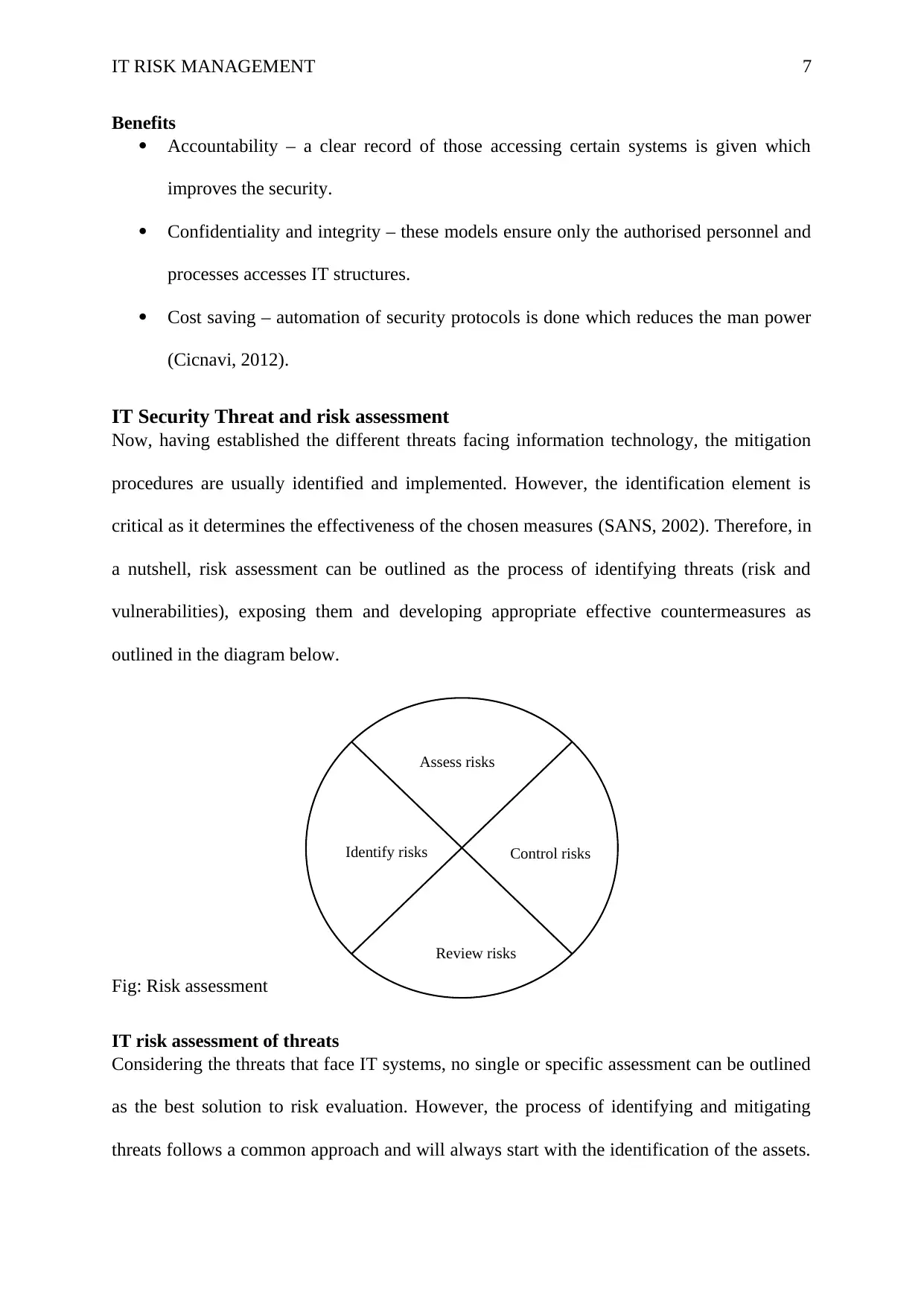
IT RISK MANAGEMENT 7
Benefits
Accountability – a clear record of those accessing certain systems is given which
improves the security.
Confidentiality and integrity – these models ensure only the authorised personnel and
processes accesses IT structures.
Cost saving – automation of security protocols is done which reduces the man power
(Cicnavi, 2012).
IT Security Threat and risk assessment
Now, having established the different threats facing information technology, the mitigation
procedures are usually identified and implemented. However, the identification element is
critical as it determines the effectiveness of the chosen measures (SANS, 2002). Therefore, in
a nutshell, risk assessment can be outlined as the process of identifying threats (risk and
vulnerabilities), exposing them and developing appropriate effective countermeasures as
outlined in the diagram below.
Fig: Risk assessment
IT risk assessment of threats
Considering the threats that face IT systems, no single or specific assessment can be outlined
as the best solution to risk evaluation. However, the process of identifying and mitigating
threats follows a common approach and will always start with the identification of the assets.
Assess risks
Control risks
Review risks
Identify risks
Benefits
Accountability – a clear record of those accessing certain systems is given which
improves the security.
Confidentiality and integrity – these models ensure only the authorised personnel and
processes accesses IT structures.
Cost saving – automation of security protocols is done which reduces the man power
(Cicnavi, 2012).
IT Security Threat and risk assessment
Now, having established the different threats facing information technology, the mitigation
procedures are usually identified and implemented. However, the identification element is
critical as it determines the effectiveness of the chosen measures (SANS, 2002). Therefore, in
a nutshell, risk assessment can be outlined as the process of identifying threats (risk and
vulnerabilities), exposing them and developing appropriate effective countermeasures as
outlined in the diagram below.
Fig: Risk assessment
IT risk assessment of threats
Considering the threats that face IT systems, no single or specific assessment can be outlined
as the best solution to risk evaluation. However, the process of identifying and mitigating
threats follows a common approach and will always start with the identification of the assets.
Assess risks
Control risks
Review risks
Identify risks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT RISK MANAGEMENT 8
In this case, the assets are the users, IT infrastructure (hardware and software) and
information. Thereafter, the threats are identified which outline any element that exploits
vulnerabilities or accidents to interfere with an asset. Finally, the vulnerability is identified,
which is the security gap in the operational components. Now, using these three items
(Assets, threats and vulnerability) the risk is developed i.e. A+T+V=R (TAG, 2010).
Examples:
Threats (Unauthorised access), asset (digital document), vulnerability (access control
not defined).
Threat (virus), asset (hard disk), vulnerability (anti-virus is not up to date).
Mitigation procedures and benefits
After identifying the risk, which in this case can be classified as the probability that a given
activity will occur, the user quantifies the problem based on the existing solutions. For
instance, in the examples above, the user will in the first instance, define a proper access
control procedure including an accurate access policy. This process can be done using access
control list or access control applications. In the second instance, the user would simply
update their existing antivirus. Now, the benefits of this are reduced operational costs as
resources are protected and resource availability. Moreover, the productivity of the user or
organization is increased due to lack of interruptions (Kosutic, 2017).
Conclusion
Information technology is no longer an optional facility but a mandatory component of daily
life. This outcome has facilitated its growth in all the industries across the globe which have
also facilitated the advances seen today such as wireless communication and smart cities.
However, the same technological advances also create many vulnerabilities that facilitate the
security threats experienced. Therefore, IT security is dependent on time as there are too
many variations and factors to consider. So, the user should update their systems regularly
In this case, the assets are the users, IT infrastructure (hardware and software) and
information. Thereafter, the threats are identified which outline any element that exploits
vulnerabilities or accidents to interfere with an asset. Finally, the vulnerability is identified,
which is the security gap in the operational components. Now, using these three items
(Assets, threats and vulnerability) the risk is developed i.e. A+T+V=R (TAG, 2010).
Examples:
Threats (Unauthorised access), asset (digital document), vulnerability (access control
not defined).
Threat (virus), asset (hard disk), vulnerability (anti-virus is not up to date).
Mitigation procedures and benefits
After identifying the risk, which in this case can be classified as the probability that a given
activity will occur, the user quantifies the problem based on the existing solutions. For
instance, in the examples above, the user will in the first instance, define a proper access
control procedure including an accurate access policy. This process can be done using access
control list or access control applications. In the second instance, the user would simply
update their existing antivirus. Now, the benefits of this are reduced operational costs as
resources are protected and resource availability. Moreover, the productivity of the user or
organization is increased due to lack of interruptions (Kosutic, 2017).
Conclusion
Information technology is no longer an optional facility but a mandatory component of daily
life. This outcome has facilitated its growth in all the industries across the globe which have
also facilitated the advances seen today such as wireless communication and smart cities.
However, the same technological advances also create many vulnerabilities that facilitate the
security threats experienced. Therefore, IT security is dependent on time as there are too
many variations and factors to consider. So, the user should update their systems regularly

IT RISK MANAGEMENT 9
including the IT infrastructure and their literacy levels. This operational procedure will
protect the technology landscape, enhance access control models and improve the
effectiveness of risk assessment procedures.
including the IT infrastructure and their literacy levels. This operational procedure will
protect the technology landscape, enhance access control models and improve the
effectiveness of risk assessment procedures.

IT RISK MANAGEMENT 10
References
Antoliš, K., Mišević, P., & Miličević, A. (2014). VULNERABILITIES OF NEW
TECHNOLOGIES AND THE PROTECTION OF CNI. Media, culture and public
relations, Retrieved 25 August, 2017, from: https://hrcak.srce.hr/file/206704.
Cicnavi. (2012). Overview of Four Main Access Control Models. Utilize windows, Retrieved
25 August, 2017, from: http://www.utilizewindows.com/overview-of-four-main-
access-control-models/.
CISSP. (2012). Security Models and architecture. Chapter 5, Retrieved 25 August, 2017,
from: http://media.techtarget.com/searchSecurity/downloads/29667C05.pdf.
DSTO. (2016). Future Cyber Security Landscape. A Perspective on the Future, Retrieved 25
August, 2017, from:
https://www.dst.defence.gov.au/sites/default/files/publications/documents/Future-
Cyber-Security-Landscape.pdf.
GU. (2017). Top 10 Threats to Information Security. Reterieved 25 August, 2017, from:
http://scsonline.georgetown.edu/programs/masters-technology-management/
resources/top-threats-to-information-technology.
Kosutic. (2017). ISO 27001/ISO 22301 Knowledge base. 27001 Academy, Retrieved 25
August, 2017, from: https://advisera.com/27001academy/knowledgebase/iso-27001-
risk-assessment-how-to-match-assets-threats-and-vulnerabilities/.
Kuc, S. (2015). Modern technologies and innovations landscape architecture education at
Cracow University of Technology . World Transactions on Engineering and
Technology Education, Retrieved 25 August, 2017, from:
http://www.wiete.com.au/journals/WTE&TE/Pages/Vol.13,%20No.3%20(2015)/16-
Kuc-S.pdf.
SANS. (2002). An Overview of Threat and Risk Assessment. SANS Institute InfoSec Reading
Room, Retrieved 25 August, 2017, from:
https://www.sans.org/reading-room/whitepapers/auditing/overview-threat-risk-
assessment-76.
Sherr, I. (2017). WannaCry ransomware: Everything you need to know. Cnet, Retrieved 25
August, 2017, from: https://www.cnet.com/news/wannacry-wannacrypt-uiwix-
ransomware-everything-you-need-to-know/.
TAG. (2010). Threat, vulnerability, risk – commonly mixed up terms. Retrieved 25 August,
from: https://www.threatanalysis.com/2010/05/03/threat-vulnerability-risk-
commonly-mixed-up-terms/.
Teymouri, M., & Ashoori, M. (2011). The impact of information technology on risk
management. Procedia Computer Science, Retrieved 25 August, 2017, from:
http://www.sciencedirect.com/science/article/pii/S1877050911000573.
Thion. (2008). Access control models. Retrieved 25 August, 2017, from:
http://liris.cnrs.fr/romuald.thion/files/RT_Papers/Thion07:Cyber:Access.pdf.
References
Antoliš, K., Mišević, P., & Miličević, A. (2014). VULNERABILITIES OF NEW
TECHNOLOGIES AND THE PROTECTION OF CNI. Media, culture and public
relations, Retrieved 25 August, 2017, from: https://hrcak.srce.hr/file/206704.
Cicnavi. (2012). Overview of Four Main Access Control Models. Utilize windows, Retrieved
25 August, 2017, from: http://www.utilizewindows.com/overview-of-four-main-
access-control-models/.
CISSP. (2012). Security Models and architecture. Chapter 5, Retrieved 25 August, 2017,
from: http://media.techtarget.com/searchSecurity/downloads/29667C05.pdf.
DSTO. (2016). Future Cyber Security Landscape. A Perspective on the Future, Retrieved 25
August, 2017, from:
https://www.dst.defence.gov.au/sites/default/files/publications/documents/Future-
Cyber-Security-Landscape.pdf.
GU. (2017). Top 10 Threats to Information Security. Reterieved 25 August, 2017, from:
http://scsonline.georgetown.edu/programs/masters-technology-management/
resources/top-threats-to-information-technology.
Kosutic. (2017). ISO 27001/ISO 22301 Knowledge base. 27001 Academy, Retrieved 25
August, 2017, from: https://advisera.com/27001academy/knowledgebase/iso-27001-
risk-assessment-how-to-match-assets-threats-and-vulnerabilities/.
Kuc, S. (2015). Modern technologies and innovations landscape architecture education at
Cracow University of Technology . World Transactions on Engineering and
Technology Education, Retrieved 25 August, 2017, from:
http://www.wiete.com.au/journals/WTE&TE/Pages/Vol.13,%20No.3%20(2015)/16-
Kuc-S.pdf.
SANS. (2002). An Overview of Threat and Risk Assessment. SANS Institute InfoSec Reading
Room, Retrieved 25 August, 2017, from:
https://www.sans.org/reading-room/whitepapers/auditing/overview-threat-risk-
assessment-76.
Sherr, I. (2017). WannaCry ransomware: Everything you need to know. Cnet, Retrieved 25
August, 2017, from: https://www.cnet.com/news/wannacry-wannacrypt-uiwix-
ransomware-everything-you-need-to-know/.
TAG. (2010). Threat, vulnerability, risk – commonly mixed up terms. Retrieved 25 August,
from: https://www.threatanalysis.com/2010/05/03/threat-vulnerability-risk-
commonly-mixed-up-terms/.
Teymouri, M., & Ashoori, M. (2011). The impact of information technology on risk
management. Procedia Computer Science, Retrieved 25 August, 2017, from:
http://www.sciencedirect.com/science/article/pii/S1877050911000573.
Thion. (2008). Access control models. Retrieved 25 August, 2017, from:
http://liris.cnrs.fr/romuald.thion/files/RT_Papers/Thion07:Cyber:Access.pdf.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IT RISK MANAGEMENT 11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




