IT Threats and Risk Mitigation in VIC
VerifiedAdded on 2020/03/02
|15
|3646
|65
AI Summary
This assignment delves into the specific IT threats facing the Victorian (VIC) government and outlines effective risk mitigation strategies. It explores various types of risks, including project, product, and business risks, emphasizing the importance of communication, work integration, and proactive planning. The assignment also provides a detailed framework for risk mitigation, outlining steps such as identifying risks, assessing their impact, prioritizing them, and implementing control measures to minimize potential losses.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Executive Summary
The relevant data have been provided in the field of information technology risk and its
management process as per the case study. The security environment is associated with the
exponential growth of personal mobile, tablets and computers. It also needed to protect the
personal and confidential data. The threats are also another kind of reasons behind this
security and risk management. IT threat and securities are discussed considering the case
study of Victorian protective data security.
The relevant data have been provided in the field of information technology risk and its
management process as per the case study. The security environment is associated with the
exponential growth of personal mobile, tablets and computers. It also needed to protect the
personal and confidential data. The threats are also another kind of reasons behind this
security and risk management. IT threat and securities are discussed considering the case
study of Victorian protective data security.

Contents
1. Pictorial representation of current security risks which are considered by the VIC
government.................................................................................................................................3
2. Diagram explanation and recognising the areas of high, medium, medium-low, and low
risk exposure..............................................................................................................................4
4. VIC government facing challenges while carrying out security or risk management within
internally or externally via outsourcing.....................................................................................8
5. Comparison between the concepts of ‘’Risk’’ and ‘’Uncertainty’’ with the help of case
study of Victorian Data security..............................................................................................10
6. Discussion and evaluation of different approaches which are available to the VIC
government for risk control and mitigation.............................................................................12
Conclusion................................................................................................................................14
Reference..................................................................................................................................14
1. Pictorial representation of current security risks which are considered by the VIC
government.................................................................................................................................3
2. Diagram explanation and recognising the areas of high, medium, medium-low, and low
risk exposure..............................................................................................................................4
4. VIC government facing challenges while carrying out security or risk management within
internally or externally via outsourcing.....................................................................................8
5. Comparison between the concepts of ‘’Risk’’ and ‘’Uncertainty’’ with the help of case
study of Victorian Data security..............................................................................................10
6. Discussion and evaluation of different approaches which are available to the VIC
government for risk control and mitigation.............................................................................12
Conclusion................................................................................................................................14
Reference..................................................................................................................................14
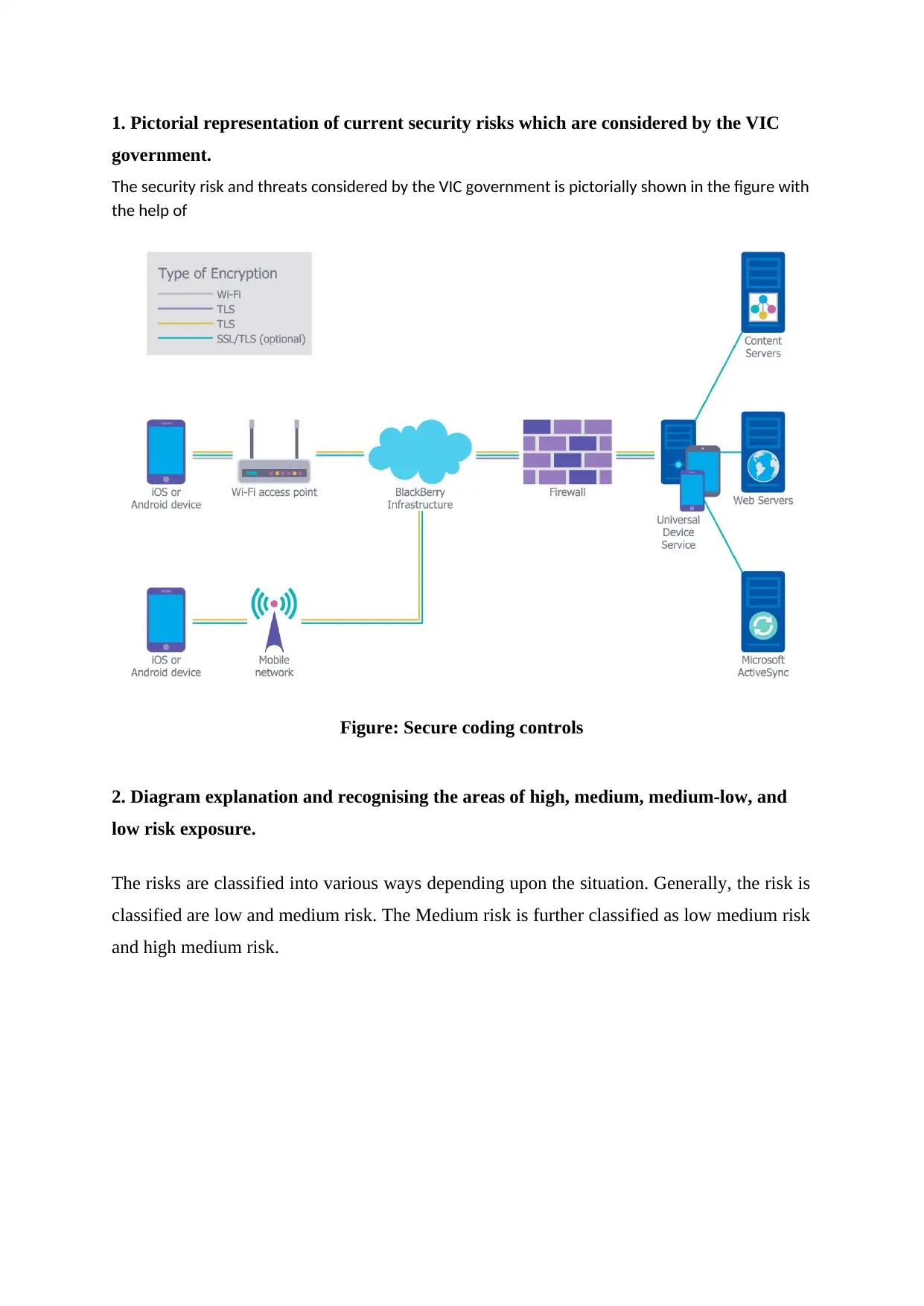
1. Pictorial representation of current security risks which are considered by the VIC
government.
The security risk and threats considered by the VIC government is pictorially shown in the figure with
the help of
Figure: Secure coding controls
2. Diagram explanation and recognising the areas of high, medium, medium-low, and
low risk exposure.
The risks are classified into various ways depending upon the situation. Generally, the risk is
classified are low and medium risk. The Medium risk is further classified as low medium risk
and high medium risk.
government.
The security risk and threats considered by the VIC government is pictorially shown in the figure with
the help of
Figure: Secure coding controls
2. Diagram explanation and recognising the areas of high, medium, medium-low, and
low risk exposure.
The risks are classified into various ways depending upon the situation. Generally, the risk is
classified are low and medium risk. The Medium risk is further classified as low medium risk
and high medium risk.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Figure: The figure showing the level of risks.
The risk bearing firm or management must classify their own risk levels. One must take
preventive steps in all the cases of risk. The further classification of the risks is shown in
below figure.
Figure : Types of risks
The process risk is classified into various forms. The infrastructure risk is the outrage of the
infrastructure related to communication links failure. The second process risk is the
information technology risk. It arises due to the technical errors in the process and becomes
an invalid process. The third process risk is the human error (Tsoumas & Tryfonas, 2004).
The risk bearing firm or management must classify their own risk levels. One must take
preventive steps in all the cases of risk. The further classification of the risks is shown in
below figure.
Figure : Types of risks
The process risk is classified into various forms. The infrastructure risk is the outrage of the
infrastructure related to communication links failure. The second process risk is the
information technology risk. It arises due to the technical errors in the process and becomes
an invalid process. The third process risk is the human error (Tsoumas & Tryfonas, 2004).

It is necessary to create a human error free system and human-friendly system. The fourth
process risk is the work place safety. The risk exposures are basically divided into 3 types.
They are transaction risk, translation risk and economic risk. The transaction risk is happened
due to the loss of currency due to the change in the stock market values and the share value in
the international value. According to Stoneburner, Goguen, & Feringa (2002), the Economic
risk is one which changes the macroeconomics. This may include things like a stock
exchange, the countries government regulation and instability in the government like political
situation. This is going to affect the investments. This is related to the major or minor
accidents and strains for the human beings. (Purtell, 2008).
The exposures are classified as expected and the exposure and the unexpected exposure. The
expected exposure comes under the low-level of exposure and a medium level of exposure.
The unexpected exposure has the high level of exposure and catastrophic level of exposure.
The low-level of exposure risk solution is yearly profit or internal control. The advantages of
this are operating group focus and efficiency. The medium level of risk exposure solution is
yearly profit analysis with the profit control, the advantage here is cash flow. The high level
of exposure solution has a form of insurance, this may be self-insurance or any risk based
insurance. The advantage of this kind of risk is the diversification, it has various types in it in
which one can divide them into a particular field. The next advantage is pooling. It has an
established mechanism.The final one is catastrophic risk exposure. The risk solution is to
have capital markets and the capital hybrid markets. The solution is to plan for the long term
analysis and it must have acess to larger pool of the capital (Liderman, 2008).
3. A Comparative analysis of the deliberate threats to underdstand their importance.
Accidental threats are one which deletes the files accidentally and some files are sent to
wrong persons like emails to wrong persons. One must take care in sending files like
confidential information to a person. It has a critical impact. The other area where the
threats are possible is smart and mobile hacking. This will target the mobile devices, tablets
and the embedded systems. It will gain access to the personal data, OS and applications.
SQL injection is the next area where the attacks are possible. It will affect the database
servers. The sensitive data may be lost or stole. The data and the programs both can be
prone to accidental threats and the deliberate threats. The internal threats can do in the
form of hardware failure due to internal system failure or man-made an error. Faculty
process risk is the work place safety. The risk exposures are basically divided into 3 types.
They are transaction risk, translation risk and economic risk. The transaction risk is happened
due to the loss of currency due to the change in the stock market values and the share value in
the international value. According to Stoneburner, Goguen, & Feringa (2002), the Economic
risk is one which changes the macroeconomics. This may include things like a stock
exchange, the countries government regulation and instability in the government like political
situation. This is going to affect the investments. This is related to the major or minor
accidents and strains for the human beings. (Purtell, 2008).
The exposures are classified as expected and the exposure and the unexpected exposure. The
expected exposure comes under the low-level of exposure and a medium level of exposure.
The unexpected exposure has the high level of exposure and catastrophic level of exposure.
The low-level of exposure risk solution is yearly profit or internal control. The advantages of
this are operating group focus and efficiency. The medium level of risk exposure solution is
yearly profit analysis with the profit control, the advantage here is cash flow. The high level
of exposure solution has a form of insurance, this may be self-insurance or any risk based
insurance. The advantage of this kind of risk is the diversification, it has various types in it in
which one can divide them into a particular field. The next advantage is pooling. It has an
established mechanism.The final one is catastrophic risk exposure. The risk solution is to
have capital markets and the capital hybrid markets. The solution is to plan for the long term
analysis and it must have acess to larger pool of the capital (Liderman, 2008).
3. A Comparative analysis of the deliberate threats to underdstand their importance.
Accidental threats are one which deletes the files accidentally and some files are sent to
wrong persons like emails to wrong persons. One must take care in sending files like
confidential information to a person. It has a critical impact. The other area where the
threats are possible is smart and mobile hacking. This will target the mobile devices, tablets
and the embedded systems. It will gain access to the personal data, OS and applications.
SQL injection is the next area where the attacks are possible. It will affect the database
servers. The sensitive data may be lost or stole. The data and the programs both can be
prone to accidental threats and the deliberate threats. The internal threats can do in the
form of hardware failure due to internal system failure or man-made an error. Faculty

procedures also must be avoided. Natural disasters are not in the hands of human beings.
This cannot be avoided. The dishonest employees and staff must be tracked from the time
to time. This is one of the precautionary measures to avoid any kind of threats. The hackers
are a primary problem to any kind of system. A powerful security system in necessary for
avoiding problems like threats. Viruses can be eliminated by using some anti-virus software
and filters. The pop-ups and bad websites must not access for the safe maintenance of the
system. The catastrophic issues also must be kept in mind for the system operation.
Authentication is also most important precaution. The system authentication in all the levels
of data usage is necessary. The software and best methods should be employed in the
maintenance in the organisation. The qualitative initiation is required in all the areas.
Nowadays electronic access of data has to be carefully managed. The software piracy is the
other area one must concentrate. The best software must be used in the elimination of
threats. The legal rights also must be maintained in all the maintenance aspects
(Orzechowski, 2007). They are incidental disclosure, stopping of work, malfunctioning of the
equipment, errors in the system .
Figure : IT Threat Analysis
This cannot be avoided. The dishonest employees and staff must be tracked from the time
to time. This is one of the precautionary measures to avoid any kind of threats. The hackers
are a primary problem to any kind of system. A powerful security system in necessary for
avoiding problems like threats. Viruses can be eliminated by using some anti-virus software
and filters. The pop-ups and bad websites must not access for the safe maintenance of the
system. The catastrophic issues also must be kept in mind for the system operation.
Authentication is also most important precaution. The system authentication in all the levels
of data usage is necessary. The software and best methods should be employed in the
maintenance in the organisation. The qualitative initiation is required in all the areas.
Nowadays electronic access of data has to be carefully managed. The software piracy is the
other area one must concentrate. The best software must be used in the elimination of
threats. The legal rights also must be maintained in all the maintenance aspects
(Orzechowski, 2007). They are incidental disclosure, stopping of work, malfunctioning of the
equipment, errors in the system .
Figure : IT Threat Analysis
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The deliberate threats are caused by the inactiveness or inaction, misuse of the source, abuse,
Fraudulent, a crime like extortion and vandalism. These deliberate threats occur due to the
unauthorised usage or access of some service like desktops, tablets and servers. It can be
done by bypassing the network or through the hacking. This can also occur through the flaws
of the security system. Only persons who know the flaws in security can do this. There is a
chance that mostly an internal person can do this. The password is the other areas one must
be careful. The password brake or copy can lead to access the system or data. Some
passwords are predictable and some are copied (Halliday, Badenhorst & Solms, 1996).
Security guidelines for other private and public organizations
According to Carr (2004), the preventions of insider threats are to be implemented. The
deliberate insider is difficult. More focus has to be taken in the authorization and access of
the file both soft copies and hard copies which include the devices. The accidental insider
threats are also to be taken care. One has to differentiate between the required action of the
work and the optional work. The typical attacks may in the area of attachments of exe files,
macros in the files and system, the active scripting, HTML scripts. The social phishing
targets the individual users. This is due to the trust maintained in fake social profiles and the
initial infections. Malware will establish the command over the network of devices. The next
areas are passwords and configuration.
The threat agents may be due to human beings, not-human beings or some acts of nature. The
theft and hacking come under the act of human beings. The non-human being threats like
forgot password or device lost. The act of nature is fire accident, earth quake. The human
causes are classified as deliberate threats and the accidental threats. This is passwords will
target the end point systems and servers. The next area is distributed denial of services, the
target area is network applications and any level of infrastructure. This causes operation
disturbance and also leads to threats in other forms.
4. VIC government facing challenges while carrying out security or risk management
within internally or externally via outsourcing.
The management must know the cause and its consequences of the risk. The is likelihood for
the security. The risk level must be analysed and determined. The stakeholder's views must
also keep in mind.The structure of the governance from the top to bottom we must
Fraudulent, a crime like extortion and vandalism. These deliberate threats occur due to the
unauthorised usage or access of some service like desktops, tablets and servers. It can be
done by bypassing the network or through the hacking. This can also occur through the flaws
of the security system. Only persons who know the flaws in security can do this. There is a
chance that mostly an internal person can do this. The password is the other areas one must
be careful. The password brake or copy can lead to access the system or data. Some
passwords are predictable and some are copied (Halliday, Badenhorst & Solms, 1996).
Security guidelines for other private and public organizations
According to Carr (2004), the preventions of insider threats are to be implemented. The
deliberate insider is difficult. More focus has to be taken in the authorization and access of
the file both soft copies and hard copies which include the devices. The accidental insider
threats are also to be taken care. One has to differentiate between the required action of the
work and the optional work. The typical attacks may in the area of attachments of exe files,
macros in the files and system, the active scripting, HTML scripts. The social phishing
targets the individual users. This is due to the trust maintained in fake social profiles and the
initial infections. Malware will establish the command over the network of devices. The next
areas are passwords and configuration.
The threat agents may be due to human beings, not-human beings or some acts of nature. The
theft and hacking come under the act of human beings. The non-human being threats like
forgot password or device lost. The act of nature is fire accident, earth quake. The human
causes are classified as deliberate threats and the accidental threats. This is passwords will
target the end point systems and servers. The next area is distributed denial of services, the
target area is network applications and any level of infrastructure. This causes operation
disturbance and also leads to threats in other forms.
4. VIC government facing challenges while carrying out security or risk management
within internally or externally via outsourcing.
The management must know the cause and its consequences of the risk. The is likelihood for
the security. The risk level must be analysed and determined. The stakeholder's views must
also keep in mind.The structure of the governance from the top to bottom we must

understand. The organization structure is not same for all the organization. Hence,
organization flow is very important. The policies followed by the system and its objective.
The resources provided in the organization are very important and one must have proper
knowledge on it. The information flow is very confidential in many cases.
In every area, the communication and consultation are required. The context has to be defined
properly for a better understanding of the situation. The risk has to be identified for the better
security. After the risk identification one has to analyse the risk at its best. The risk has to be
evaluated properly for the solution. Before treating the risk one has to accept the risk for the
safety of the system and data. Finally, all the points have to be monitored and review
(Grzywak, 2000).
Figure: IT Organisation Governance and Risk Management
organization flow is very important. The policies followed by the system and its objective.
The resources provided in the organization are very important and one must have proper
knowledge on it. The information flow is very confidential in many cases.
In every area, the communication and consultation are required. The context has to be defined
properly for a better understanding of the situation. The risk has to be identified for the better
security. After the risk identification one has to analyse the risk at its best. The risk has to be
evaluated properly for the solution. Before treating the risk one has to accept the risk for the
safety of the system and data. Finally, all the points have to be monitored and review
(Grzywak, 2000).
Figure: IT Organisation Governance and Risk Management

The relationship with the stake holders must be always good for the matter of trust. One must
adopt the culture of the organization. The standards of the system are fixed and one must
raise the standards. The management must commit to few things for better security and risk
management.
The objectives of Risk management
The primary objective is to understand the business risk. One has to create the opportunity for
avoiding the risks. The resources must be allocated properly in all the areas. One must also
meet the requirements of the stake holders. The risk can be defined as the product of impact
and probability. The elements of risk can be divided into impact and the probability. The
impact is further divided into asset and threat. The threat has three parts. They are threat
source, initiation probability and the success probability. The probability is divided into two
parts. They are a vulnerability and the mitigation. The vulnerability is divided into three cases
they are predisposing conditions, pervasiveness and severity (Bandyopadhyay, Mykytyn &
Mykytyn, 1999). The mitigation leads to effectiveness.
The owners always keep an eye on assets at the same time must take care of threats and
attacks. The owner must always have the counter measures. The revenue generating assets
are different from the profitability assets. So the people have classified them before assigning
the counter attacks. Any organization faces multiple threats. The risks must be manageable at
any given point of time. The threat ranking is the other kind of criterion for the quantitative
and the qualitative analysis. Flaws and weakness in assets must be strengthened. The risk
assessment gives possible numerical value and analysis. The risk assessment required for
providing the security to the calculated risks. Hence the risk can be successfully blocked.
(Tsoumas & Tryfonas, 2004).
5. Comparison between the concepts of ‘’Risk’’ and ‘’Uncertainty’’ with the help of
case study of Victorian Data security.
The risk is the sub set of uncertainty. Five steps are required to deal with the risk and the
uncertainty. The preparation must be improved by gathering the data, creating some standards
and the templates creation. Expanding is the evaluation of the system by conducting the
strategic assessment. One must assess the risk and the uncertainty. We also must conduct the
value based assessment. The decision making must be improved over the period of time with
adopt the culture of the organization. The standards of the system are fixed and one must
raise the standards. The management must commit to few things for better security and risk
management.
The objectives of Risk management
The primary objective is to understand the business risk. One has to create the opportunity for
avoiding the risks. The resources must be allocated properly in all the areas. One must also
meet the requirements of the stake holders. The risk can be defined as the product of impact
and probability. The elements of risk can be divided into impact and the probability. The
impact is further divided into asset and threat. The threat has three parts. They are threat
source, initiation probability and the success probability. The probability is divided into two
parts. They are a vulnerability and the mitigation. The vulnerability is divided into three cases
they are predisposing conditions, pervasiveness and severity (Bandyopadhyay, Mykytyn &
Mykytyn, 1999). The mitigation leads to effectiveness.
The owners always keep an eye on assets at the same time must take care of threats and
attacks. The owner must always have the counter measures. The revenue generating assets
are different from the profitability assets. So the people have classified them before assigning
the counter attacks. Any organization faces multiple threats. The risks must be manageable at
any given point of time. The threat ranking is the other kind of criterion for the quantitative
and the qualitative analysis. Flaws and weakness in assets must be strengthened. The risk
assessment gives possible numerical value and analysis. The risk assessment required for
providing the security to the calculated risks. Hence the risk can be successfully blocked.
(Tsoumas & Tryfonas, 2004).
5. Comparison between the concepts of ‘’Risk’’ and ‘’Uncertainty’’ with the help of
case study of Victorian Data security.
The risk is the sub set of uncertainty. Five steps are required to deal with the risk and the
uncertainty. The preparation must be improved by gathering the data, creating some standards
and the templates creation. Expanding is the evaluation of the system by conducting the
strategic assessment. One must assess the risk and the uncertainty. We also must conduct the
value based assessment. The decision making must be improved over the period of time with
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

the prediction calculations. We also have to improve the tracking the uncertainty event. This
can be done by performance tracking and conduct assessment (Liderman, 2008).
The risks can be controlled in various possible ways. This is also known as risk management.
The first step is avoidance. The avoidance of any risk will help us to control the loss. The
name says it all, avoiding the risks completely. This is the first and foremost way of avoiding
any threats in the organization. The second step is loss reduction. The loss reduction is in
which it accepts the risk and it analyzes the loss associated with the risk. This method will try
to minimize the loss due to a particular threat. The best example of this method is the
company having flammable and explosive items. The company will read for the risk and uses
water and fire safety measures to prevent the future threats. The next method is the loss
prevention. The loss prevention is one which cannot eliminate the loss but it can minimize the
impact of the loss due to some unknown threats. The example of this technique is to protect a
secret item or inventory from the theft. These can of threats are possible but still one must
take preventive measures to eliminate the loss. The preventive measures like strict security
check up, video surveillance and secured the place of storage.
Figure : Risk and Uncertainty
The next technique is the separation, this deals with separation of data, files and assets into
different places to avoid the threat. This will help to preserve the assets in other places if
there is a catastrophic occur in one place. Duplication is the next management technique in
which the back up of the data, files and other services are done. Hence this back up will allow
recovering the complete loss from the threats. The best examples of these services can be
seen in the organizations associated with the computers and the disaster management. The
can be done by performance tracking and conduct assessment (Liderman, 2008).
The risks can be controlled in various possible ways. This is also known as risk management.
The first step is avoidance. The avoidance of any risk will help us to control the loss. The
name says it all, avoiding the risks completely. This is the first and foremost way of avoiding
any threats in the organization. The second step is loss reduction. The loss reduction is in
which it accepts the risk and it analyzes the loss associated with the risk. This method will try
to minimize the loss due to a particular threat. The best example of this method is the
company having flammable and explosive items. The company will read for the risk and uses
water and fire safety measures to prevent the future threats. The next method is the loss
prevention. The loss prevention is one which cannot eliminate the loss but it can minimize the
impact of the loss due to some unknown threats. The example of this technique is to protect a
secret item or inventory from the theft. These can of threats are possible but still one must
take preventive measures to eliminate the loss. The preventive measures like strict security
check up, video surveillance and secured the place of storage.
Figure : Risk and Uncertainty
The next technique is the separation, this deals with separation of data, files and assets into
different places to avoid the threat. This will help to preserve the assets in other places if
there is a catastrophic occur in one place. Duplication is the next management technique in
which the back up of the data, files and other services are done. Hence this back up will allow
recovering the complete loss from the threats. The best examples of these services can be
seen in the organizations associated with the computers and the disaster management. The

last step is the diversification of resources and it creates multiple areas in business. This will
help us to control the loss to the firm by avoiding the loss in other areas due to
diversification. The diversification is a long term process. The regular inspections in the work
area of any field will reduce the loss. The proper maintenance is required in all areas for the
best results and least chance of failure. Testing is one of the methods in which the life of the
process, system or machine can increase, this will lead to better reliability. (Purtell, 2008).
6. Discussion and evaluation of different approaches which are available to the VIC
government for risk control and mitigation.
The preliminary step of the risk management is to identify the risk. There are various ways in
doing the risk identification. Automation is the modern day risk avoidance step. The system
automation, cloud data back up, duplication via automation and the human errors can also be
removed in a huge way. There are some physical control techniques also there in which many
preventive measures can be taken. An engineering control is the next kind of step up in which
the damage to the machines can be avoided by the automatical shut down before it
breakdown. Better communication is required in all areas to know the limitations and threats.
The redundancy has to be eliminated in all forms. Training is the best methodology one must
adopt for improving the skills for man power and their strength. One must have a proper
business plan for facing the threats and reducing the risk. Quality also has to be in the product
based environment.
help us to control the loss to the firm by avoiding the loss in other areas due to
diversification. The diversification is a long term process. The regular inspections in the work
area of any field will reduce the loss. The proper maintenance is required in all areas for the
best results and least chance of failure. Testing is one of the methods in which the life of the
process, system or machine can increase, this will lead to better reliability. (Purtell, 2008).
6. Discussion and evaluation of different approaches which are available to the VIC
government for risk control and mitigation.
The preliminary step of the risk management is to identify the risk. There are various ways in
doing the risk identification. Automation is the modern day risk avoidance step. The system
automation, cloud data back up, duplication via automation and the human errors can also be
removed in a huge way. There are some physical control techniques also there in which many
preventive measures can be taken. An engineering control is the next kind of step up in which
the damage to the machines can be avoided by the automatical shut down before it
breakdown. Better communication is required in all areas to know the limitations and threats.
The redundancy has to be eliminated in all forms. Training is the best methodology one must
adopt for improving the skills for man power and their strength. One must have a proper
business plan for facing the threats and reducing the risk. Quality also has to be in the product
based environment.

Figure: Risk management cycle
The risk identification is necessary for any model. The general category of the risk is genetic
risk and product specific risk. This has further classified as project risk, product risk and
business risk. Some of the risk items are a loss of team member, which will decrease the
efficiency of the system and the balance, flow also will be lost. If the team leader is lost them
the future work will definitely lose. The timings of the meetings are also necessary. It is
advised to have common meeting times to increase the efficiency and reduce all kinds of risk.
Lack of communication also a key factor, hence the communication of the idea or the concept
is necessary (Orzechowski, 2007). The work integration is an art and the business firms must
establish the good work integration process.
The risk mitigation is the plan in which the options were developed to increase the
opportunities and at the same time to reduce threats to the system.
The risk identification is necessary for any model. The general category of the risk is genetic
risk and product specific risk. This has further classified as project risk, product risk and
business risk. Some of the risk items are a loss of team member, which will decrease the
efficiency of the system and the balance, flow also will be lost. If the team leader is lost them
the future work will definitely lose. The timings of the meetings are also necessary. It is
advised to have common meeting times to increase the efficiency and reduce all kinds of risk.
Lack of communication also a key factor, hence the communication of the idea or the concept
is necessary (Orzechowski, 2007). The work integration is an art and the business firms must
establish the good work integration process.
The risk mitigation is the plan in which the options were developed to increase the
opportunities and at the same time to reduce threats to the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure: Risk mitigation
The basic step is to identify the risk. The events lead to risk and their relationships. Then one
must access the probability and know the consequences. The next step is to risk impact
assessment. This will include the cost and the technical performances. Then one must access
the risk critically. The next step is to prioritization the risks. In every aspect one must track
the risk, this is known as risk tracking. The final step is the risk mitigation. This can monitor
the situation and leads to progress. It manages the risk in the business to the acceptable level.
Conclusion
The IT threats with the relevnce of VIC government has been discussed throughly. The risk
mitigation is to decrease the impact of loss or damage to the company in risk times. It also
involves the evaluation of the system. The probabilities must also be calculated and
alternatives must be planned. Loss prevention and the loss control are main ideas behind the
risk mitigation. This has to be done in both the quantitative and qualitative way. The final
result must be to avoid the loss as maximum as possible.
The basic step is to identify the risk. The events lead to risk and their relationships. Then one
must access the probability and know the consequences. The next step is to risk impact
assessment. This will include the cost and the technical performances. Then one must access
the risk critically. The next step is to prioritization the risks. In every aspect one must track
the risk, this is known as risk tracking. The final step is the risk mitigation. This can monitor
the situation and leads to progress. It manages the risk in the business to the acceptable level.
Conclusion
The IT threats with the relevnce of VIC government has been discussed throughly. The risk
mitigation is to decrease the impact of loss or damage to the company in risk times. It also
involves the evaluation of the system. The probabilities must also be calculated and
alternatives must be planned. Loss prevention and the loss control are main ideas behind the
risk mitigation. This has to be done in both the quantitative and qualitative way. The final
result must be to avoid the loss as maximum as possible.

Reference
Bandyopadhyay, K., Mykytyn, P.P., & Mykytyn, K., (1999). A framework for integrated risk
management in information technology, Journal: Management Decision, Volume 37,
Issue: 5, Page: 437 – 445.
Carr, N., (2004). Does IT Matter? Information Technology and The Corrosion of
Competitive Advantage, Harvard Business School Press.
Grzywak, A., (2000) (ed.) Security of IT systems (In Polish), Jacek Skalmierski Publishing
House, Gliwice.
Halliday, S., Badenhorst, K., & Von Solms, R., (1996). A business approach to effective
information technology risk analysis and management, Journal of Information
Management & Computer Security, 1996, Volume: 4, Issue: 1, Page: 19 – 31
Liderman, K., (2008). Risk analysis and information security in computer systems (In
Polish), PWN SA, Warsaw.
Orzechowski, R., (2007). Effective application of IT in the enterprise, (In Polish) E-mentor
no 3(20).
Purtell, T., 2008). New View on IT Risk: Building a successful Information Technology risk
management program, The RMA Journal.
Stoneburner, G., Goguen, A., & Feringa, A., (2002). Risk Management Guide for
Information Technology Systems. Recommendations of the National Institute of
Standards and Technology, National Institute of Standards and Technology.
Tsoumas, V., & Tryfonas, T., (2004), From risk analysis to effective security management:
towards an automated approach. Information Management & Computer Security
Vol.12.
Bandyopadhyay, K., Mykytyn, P.P., & Mykytyn, K., (1999). A framework for integrated risk
management in information technology, Journal: Management Decision, Volume 37,
Issue: 5, Page: 437 – 445.
Carr, N., (2004). Does IT Matter? Information Technology and The Corrosion of
Competitive Advantage, Harvard Business School Press.
Grzywak, A., (2000) (ed.) Security of IT systems (In Polish), Jacek Skalmierski Publishing
House, Gliwice.
Halliday, S., Badenhorst, K., & Von Solms, R., (1996). A business approach to effective
information technology risk analysis and management, Journal of Information
Management & Computer Security, 1996, Volume: 4, Issue: 1, Page: 19 – 31
Liderman, K., (2008). Risk analysis and information security in computer systems (In
Polish), PWN SA, Warsaw.
Orzechowski, R., (2007). Effective application of IT in the enterprise, (In Polish) E-mentor
no 3(20).
Purtell, T., 2008). New View on IT Risk: Building a successful Information Technology risk
management program, The RMA Journal.
Stoneburner, G., Goguen, A., & Feringa, A., (2002). Risk Management Guide for
Information Technology Systems. Recommendations of the National Institute of
Standards and Technology, National Institute of Standards and Technology.
Tsoumas, V., & Tryfonas, T., (2004), From risk analysis to effective security management:
towards an automated approach. Information Management & Computer Security
Vol.12.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





