Victorian Protective Data Security DELL Executive Summary
15 Pages3646 Words65 Views
Charles Sturt University
IT Risk Management (ITC596)
Added on 2020-03-02
About This Document
ITC596 - The relevant data have been provided in the field of information technology risk and its management process as per the case study. The security environment is associated with the exponential growth of personal mobile, tablets, and computers. It also needed to protect personal and confidential data.
Victorian Protective Data Security DELL Executive Summary
Charles Sturt University
IT Risk Management (ITC596)
Added on 2020-03-02
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Victorian Protective Data Security Case Study
|16
|3331
|113
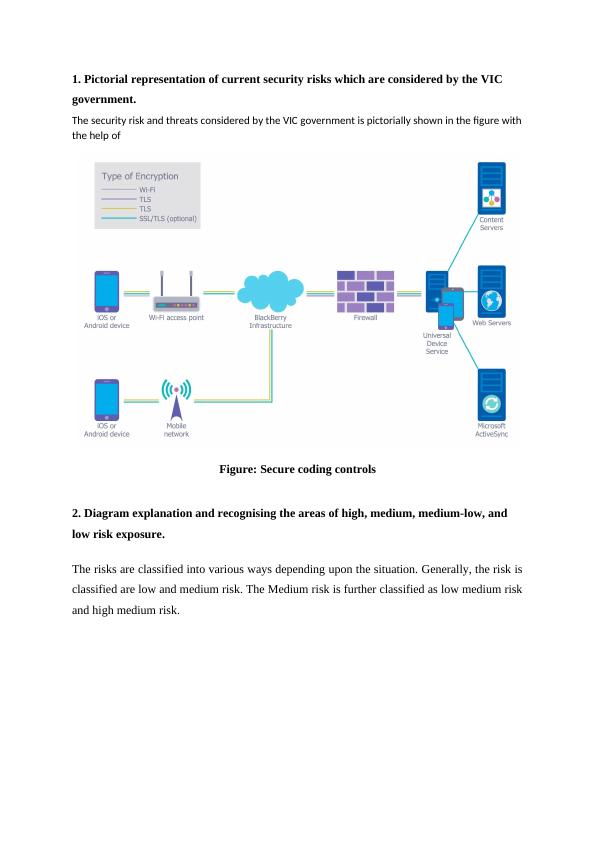
Security Risks and Concerns 8/28/2017 Introduction 3 Security Risks and Concerns Diagram
|11
|3156
|439
(solved) IT Risk Management PDF
|15
|3652
|47
ITC596 - VIC Government - Security Risks and Concerns
|12
|3080
|34
EDUC 448 - Victorian Protective Data Security Framework
|11
|2816
|230
IT Risk Management Security System
|17
|3744
|61